NIH Login An Overview of Single SignOn Federation





- Slides: 15

NIH Login An Overview of Single Sign-On, Federation, Its Benefits, and Basic Procedures for Integrating Applications

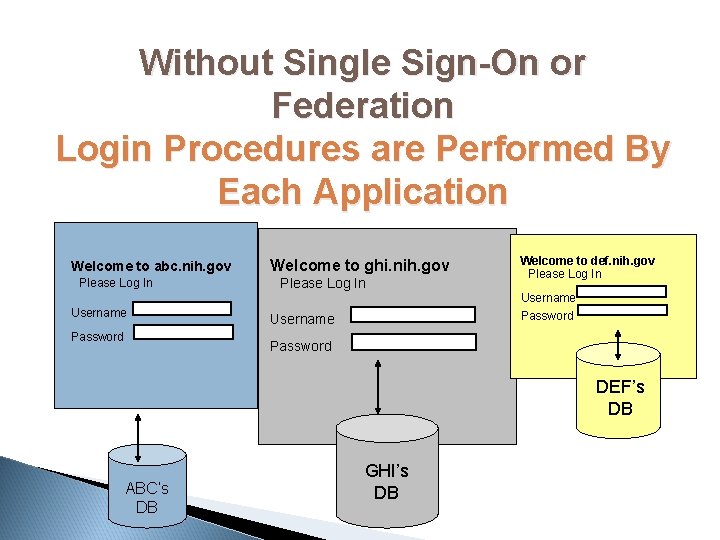
Without Single Sign-On or Federation Login Procedures are Performed By Each Application Welcome to abc. nih. gov Please Log In Username Password Welcome to ghi. nih. gov Please Log In Welcome to def. nih. gov Please Log In Username Password DEF’s DB ABC’s DB GHI’s DB

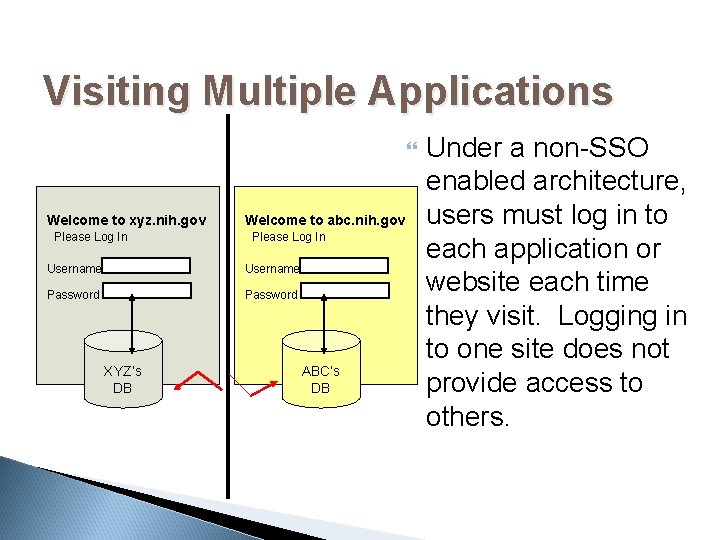
Visiting Multiple Applications Welcome to xyz. nih. gov Please Log In Welcome to abc. nih. gov Please Log In Username Password XYZ’s DB ABC’s DB Under a non-SSO enabled architecture, users must log in to each application or website each time they visit. Logging in to one site does not provide access to others.

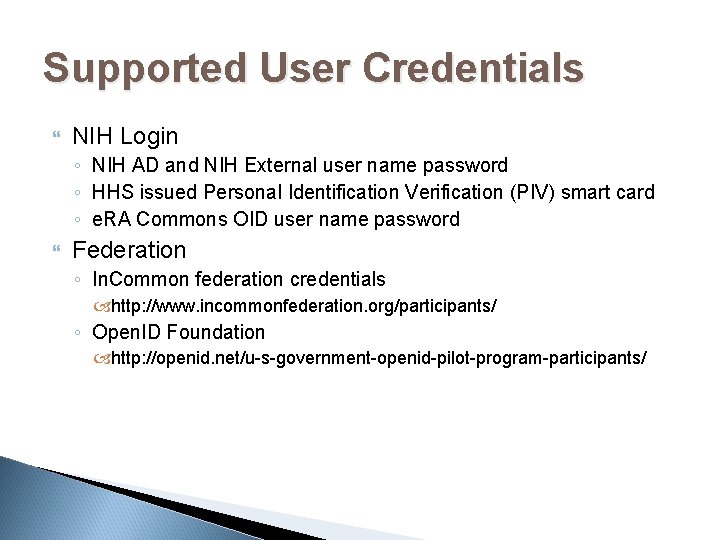
Supported User Credentials NIH Login ◦ NIH AD and NIH External user name password ◦ HHS issued Personal Identification Verification (PIV) smart card ◦ e. RA Commons OID user name password Federation ◦ In. Common federation credentials http: //www. incommonfederation. org/participants/ ◦ Open. ID Foundation http: //openid. net/u-s-government-openid-pilot-program-participants/

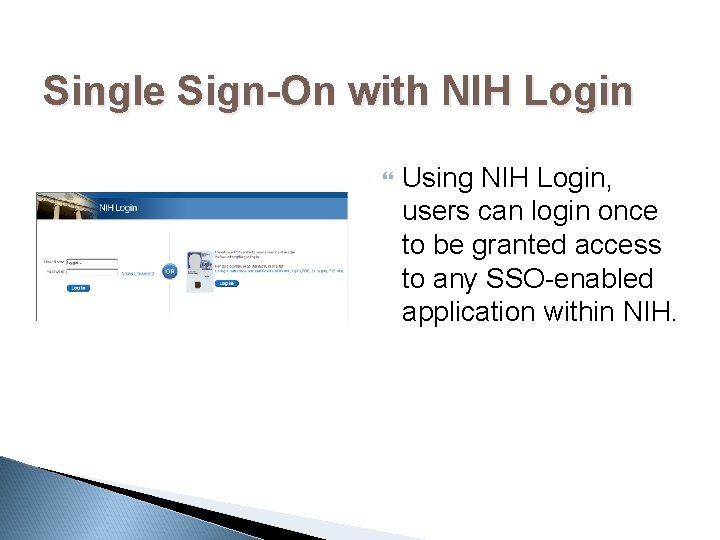
Single Sign-On with NIH Login Using NIH Login, users can login once to be granted access to any SSO-enabled application within NIH.

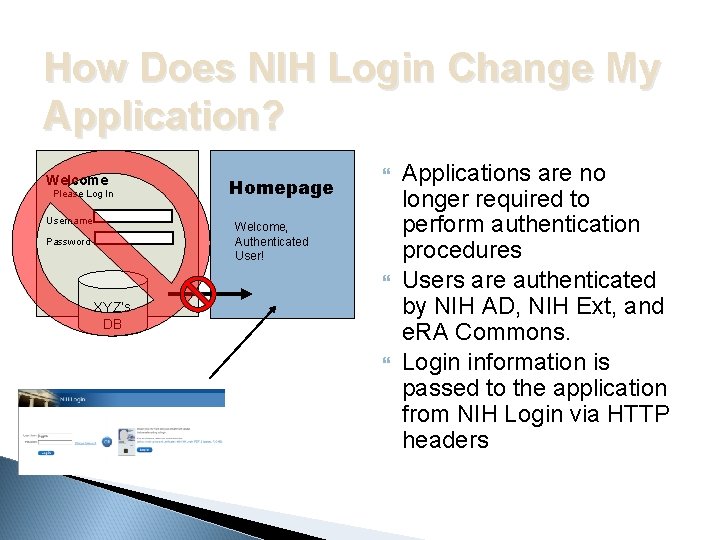
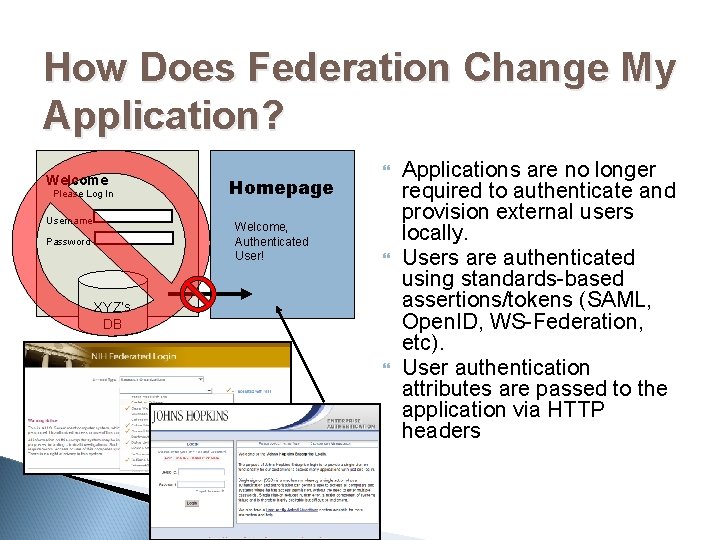
How Does NIH Login Change My Application? Welcome Please Log In Username Homepage Welcome, Authenticated User! Password XYZ’s DB Applications are no longer required to perform authentication procedures Users are authenticated by NIH AD, NIH Ext, and e. RA Commons. Login information is passed to the application from NIH Login via HTTP headers

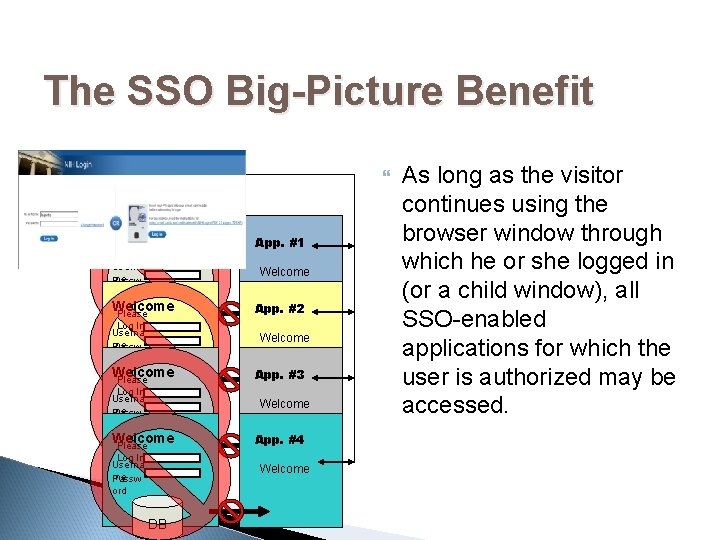
The SSO Big-Picture Benefit Welcome Please Log In Userna me Passw ord App. #1 Welcome Please Log In Userna XY me Z’s Passw ord DB DB App. #2 Welcome App. #3 Welcome App. #4 Welcome As long as the visitor continues using the browser window through which he or she logged in (or a child window), all SSO-enabled applications for which the user is authorized may be accessed.

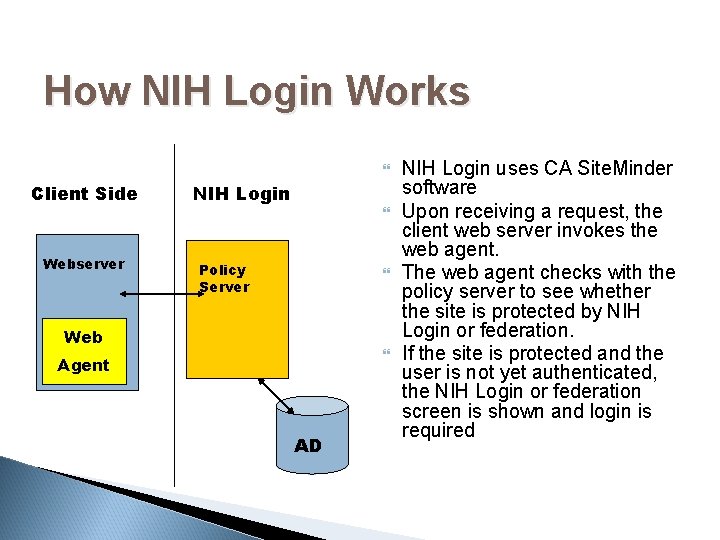
How NIH Login Works Client Side Webserver NIH Login Policy Server Web Agent AD NIH Login uses CA Site. Minder software Upon receiving a request, the client web server invokes the web agent. The web agent checks with the policy server to see whether the site is protected by NIH Login or federation. If the site is protected and the user is not yet authenticated, the NIH Login or federation screen is shown and login is required

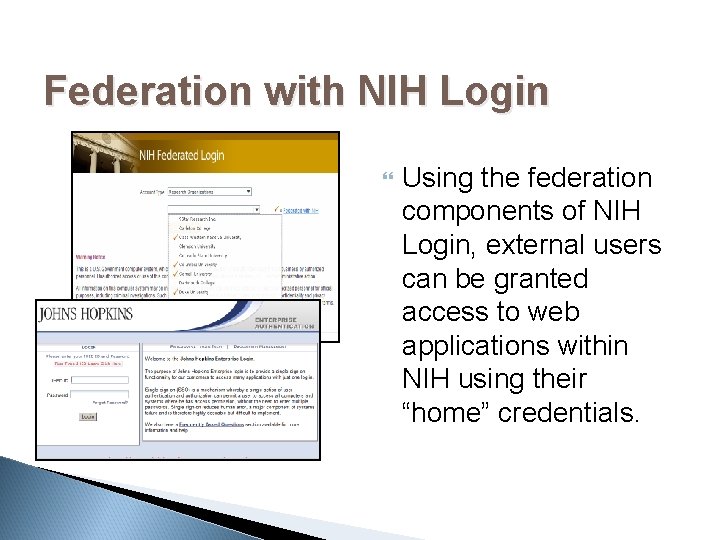
Federation with NIH Login Using the federation components of NIH Login, external users can be granted access to web applications within NIH using their “home” credentials.

How Does Federation Change My Application? Welcome Please Log In Username Homepage Welcome, Authenticated User! Password XYZ’s DB Applications are no longer required to authenticate and provision external users locally. Users are authenticated using standards-based assertions/tokens (SAML, Open. ID, WS-Federation, etc). User authentication attributes are passed to the application via HTTP headers

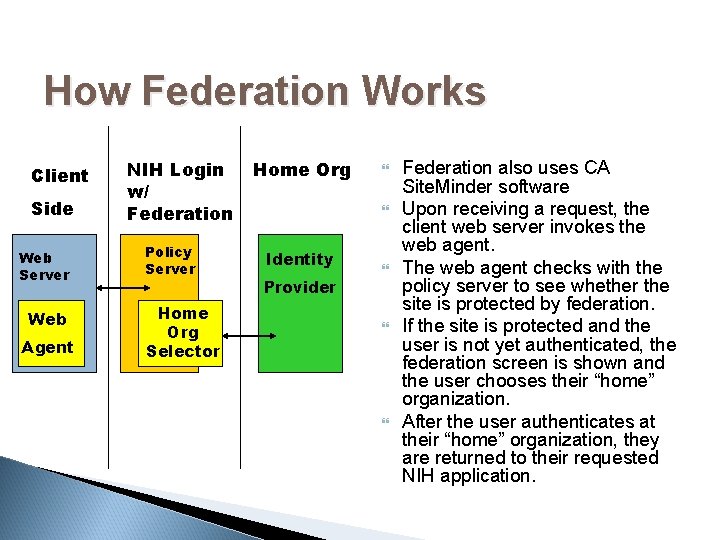
How Federation Works Client Side Web Server Web Agent NIH Login w/ Federation Policy Server Home Org Selector Home Org Identity Provider Federation also uses CA Site. Minder software Upon receiving a request, the client web server invokes the web agent. The web agent checks with the policy server to see whether the site is protected by federation. If the site is protected and the user is not yet authenticated, the federation screen is shown and the user chooses their “home” organization. After the user authenticates at their “home” organization, they are returned to their requested NIH application.

Authentication and Authorization NIH Login will perform the necessary authentication procedures to verify the credentials of the user NIH Login can also perform basic authorization ◦ Authorization is based on active directory groups ◦ Groups must exist or be created in the NIH AD for NIH Login and LDAP_ALL for federation

Getting Started… Your part: In order to use NIH Login, the application’s web server must run an executable known as a web agent. The web agent is available for various operating systems including Windows, Solaris and Linux. The simple installation/configuration process may be performed by your team or by a member of the NIH Login team if granted access to the server. Our part: The NIH Login team must first configure the NIH Login policy server to expect connections from the web agent. We will then send you technical information to allow you to connect your web agent to the policy server. Application owners or technical contacts should provide operating system and web server information to the NIH Login team via the NIH Login Request Form (see contact information below for requests).

Tasks for Application Programmers Applications integrating with NIH Login will need to remove their existing login procedures. This includes: ◦ Altering HTML to remove login screen ◦ Changing code (e. g. ASP, JSP, Cold. Fusion) to receive HTTP header information from NIH Login Values include username, full name, email, etc. These values can be used to populate data that is needed by the application ◦ Using the information received to proceed with your application’s tasks Code change requirements are usually minimal

More Information For more information, please contact: ◦ Jeff Erickson – Erickso. J@mail. nih. gov ◦ NIH Login support group – Support@mail. nih. gov
 Nih login email
Nih login email Web single signon
Web single signon Wellsoffice wellsfargo com ceo signon
Wellsoffice wellsfargo com ceo signon Sas authdomain
Sas authdomain Nih email login
Nih email login Multiple instruction single data
Multiple instruction single data Single instruction single data
Single instruction single data Multi channel multi phase example
Multi channel multi phase example Nih administrative supplement example
Nih administrative supplement example Theresa cruz california
Theresa cruz california Transhare nih
Transhare nih Nih staff scientist
Nih staff scientist Nih other significant contributor
Nih other significant contributor Jonathan pollock nida
Jonathan pollock nida Building 37 nih
Building 37 nih Nih institutes list
Nih institutes list