Single SignOn and ThirdParty Authentication ESaa S 5




![SQL Injection • View: = text_field_tag 'name' • App: Moviegoer. where("name='#{params[: name]}'") • Evil SQL Injection • View: = text_field_tag 'name' • App: Moviegoer. where("name='#{params[: name]}'") • Evil](https://slidetodoc.com/presentation_image_h/1a1dc13e843a773cbebec50d95e33c66/image-9.jpg)
- Slides: 9

Single Sign-On and Third-Party Authentication (ESaa. S § 5. 2)

Third-Party Authentication • Goal: What are my Facebook friends reading on the NY Times site? • NY Times needs to be able to access your Facebook info • …but you don’t want to reveal your Facebook password to NY Times! • How can we do this? => Third-party authentication

How Does It Work? (Concepts) • Building block: tamper-evident secure token • Using cryptography, I create a string that: – Only I can decrypt (decode) – I can detect if it’s been tampered with – No one else could have created it without knowing my secret key • Usually, string just contains a “handle” to valuable info that I store myself – Receive string => I know I can “trust” the handle

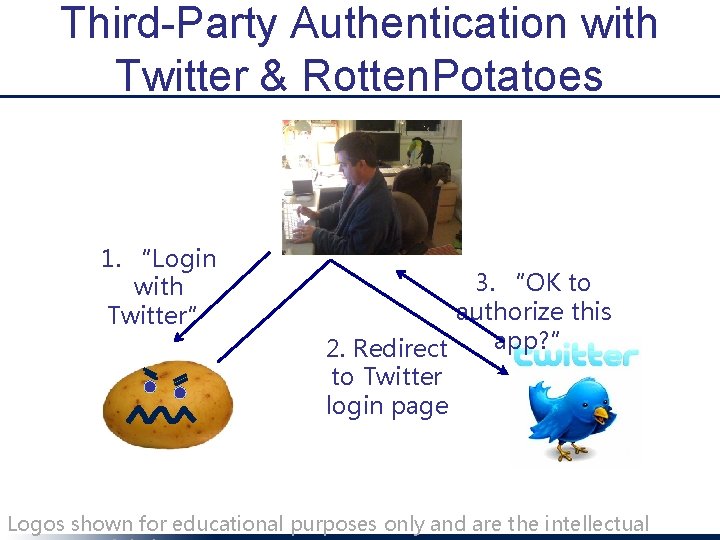
Third-Party Authentication with Twitter & Rotten. Potatoes 1. “Login with Twitter” 3. “OK to authorize this app? ” 2. Redirect to Twitter login page Logos shown for educational purposes only and are the intellectual

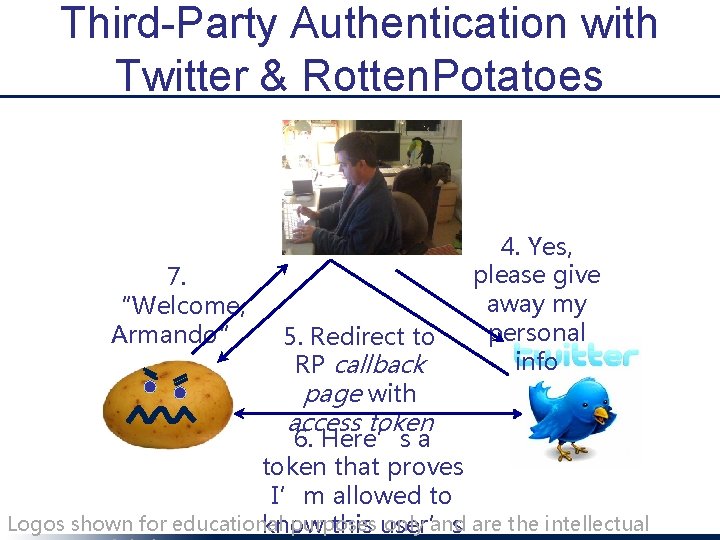
Third-Party Authentication with Twitter & Rotten. Potatoes 7. “Welcome, Armando” 5. Redirect to RP callback page with access token 4. Yes, please give away my personal info 6. Here’s a token that proves I’m allowed to Logos shown for educational purposes only and are the intellectual know this user’s

Which is true about third-party authentication between a requester and a provider? Once completed, the requester can do anything you ☐ can do on the provider ☐ If your credentials on the requester are compromised, your credentials on the provider are also compromised ☐ If the provider revokes access, the requester no longer has any of your info ☐ Access can be time-limited to expire on a preset date 7

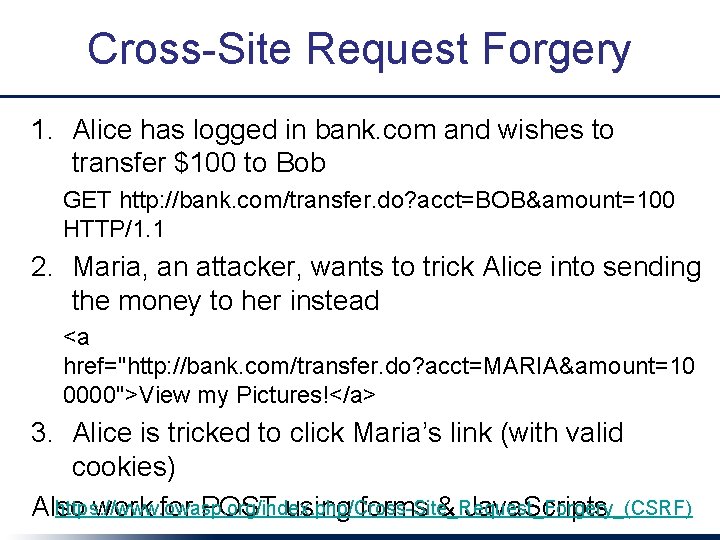
Cross-Site Request Forgery 1. Alice has logged in bank. com and wishes to transfer $100 to Bob GET http: //bank. com/transfer. do? acct=BOB&amount=100 HTTP/1. 1 2. Maria, an attacker, wants to trick Alice into sending the money to her instead <a href="http: //bank. com/transfer. do? acct=MARIA&amount=10 0000">View my Pictures!</a> 3. Alice is tricked to click Maria’s link (with valid cookies) https: //www. owasp. org/index. php/Cross-Site_Request_Forgery_(CSRF) Also work for POST using forms & Java. Scripts

Cross-Site Request Forgery Preventions: • include session nonce (a secret and unique value) with every request – – – in layouts/application. html. haml protect_from_forgery in Application. Controller Rails form helpers automatically include nonce in forms csrf_meta_tags token="Kby. Umh. TLMp. Yj 7 CD 2 di 7 JKP 1 P 3 qm. Llk. Pt" GET http: //bank. com/transfer. do? acct=BOB&amount=100&token HTTP/1. 1
![SQL Injection View textfieldtag name App Moviegoer wherenameparams name Evil SQL Injection • View: = text_field_tag 'name' • App: Moviegoer. where("name='#{params[: name]}'") • Evil](https://slidetodoc.com/presentation_image_h/1a1dc13e843a773cbebec50d95e33c66/image-9.jpg)
SQL Injection • View: = text_field_tag 'name' • App: Moviegoer. where("name='#{params[: name]}'") • Evil user fills in: BOB'); DROP TABLE moviegoers; - • Executes this SQL query: SELECT * FROM moviegoers WHERE (name='BOB'); DROP TABLE moviegoers; --' • Solution: Moviegoer. where("name=? ", params[: name]) xkcd. com/