SECURITY COMPLIANCE RISK Risk Management and Compliance Addressing



























- Slides: 37

SECURITY – COMPLIANCE – RISK

Risk Management and Compliance: Addressing Uncertainty with Integrity

When you think of Risk Management and Compliance, what words come to mind?

What is Risk Management? The management and strategic process of assessment, identification, and prioritization of risks followed by a coordinated response to minimize, monitor and control unfortunate events.


Risk Management in Higher Ed Why it Matters • Protecting the data of 20. 4 million students (NCES, 2017) • Multiple points of entry • Increased scrutiny by the banks • Staying out of the news

PCI DSS One Standard to Rule them All


Who’s data is HE protecting? • Students • Families • Authorized Payers • Authorized Parties • University employees

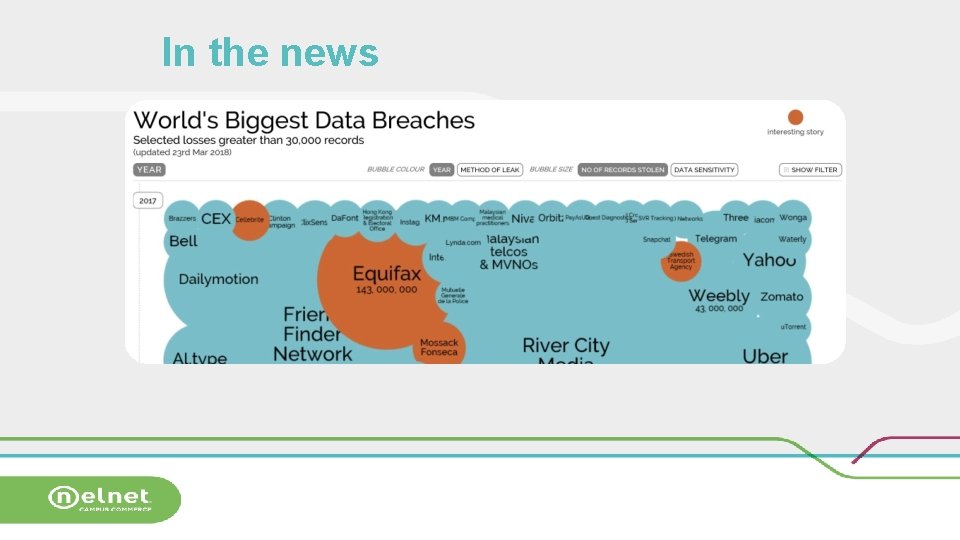
In the news

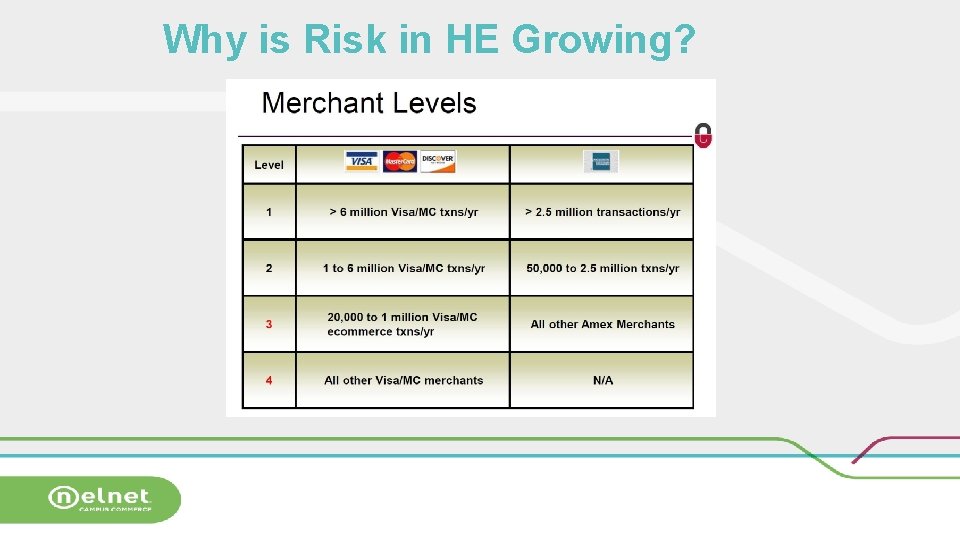
Why is Risk in HE Growing?



Millennial Generation


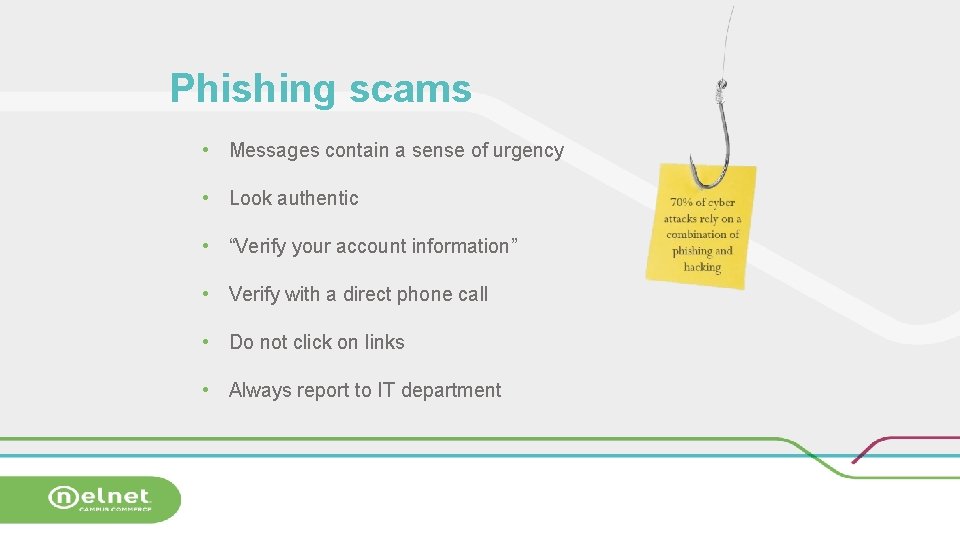
Phishing scams • Messages contain a sense of urgency • Look authentic • “Verify your account information” • Verify with a direct phone call • Do not click on links • Always report to IT department


Multiple Points of Entry

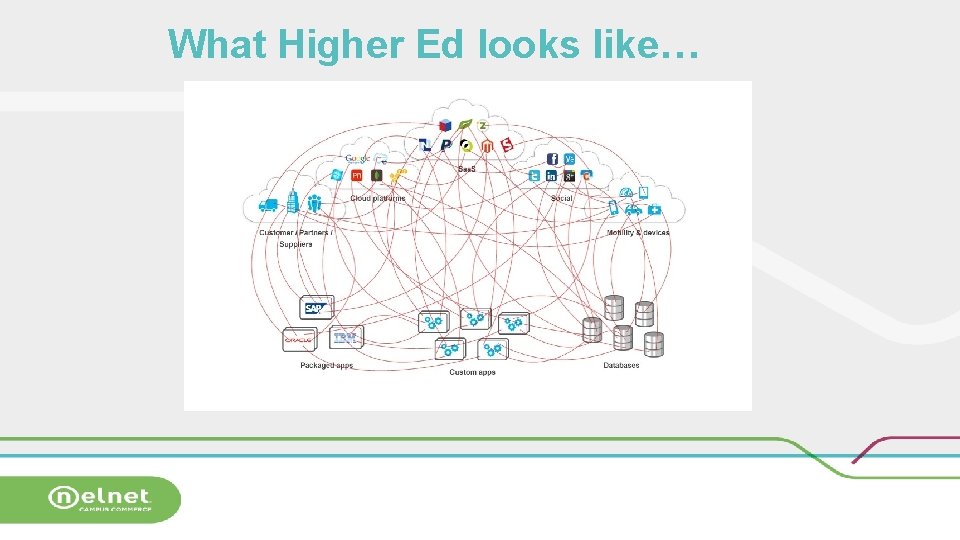
What Higher Ed looks like…

Also known as…

Storage concerns • Storage of paper data • Storing the 3 digit code • Desktop, workstation, keyboard With so much storage and so many payment avenues, so much can go wrong

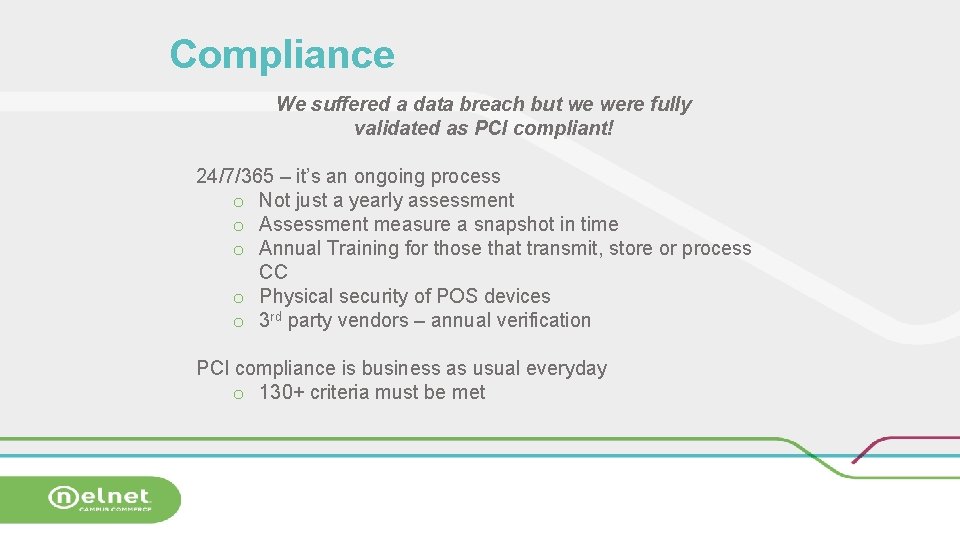
Compliance We suffered a data breach but we were fully validated as PCI compliant! 24/7/365 – it’s an ongoing process o Not just a yearly assessment o Assessment measure a snapshot in time o Annual Training for those that transmit, store or process CC o Physical security of POS devices o 3 rd party vendors – annual verification PCI compliance is business as usual everyday o 130+ criteria must be met

Best Practices • • NEVER email CC info or process payments received by email Secure access to areas where data is stored • Destroy documentation when no longer needed • NEVER store CC numbers in any database or spreadsheet • Document departmental payment • Mask all but the last 4 digits card handling procedures • Keep CC documentation locked in • Segregate duties – keep a safe and secure filing cabinet reconciliation role separate from processing credit cards or refunds • Oversight of the “need-to-know” players

Who is HE accountable to? • Federal Agencies o U. S. Department of Education (ED) o Federal Trade Commission (FTC) o Consumer Financial Protection Bureau (CFPB) • State Agencies • Private/Trade Associations • Credit card associations

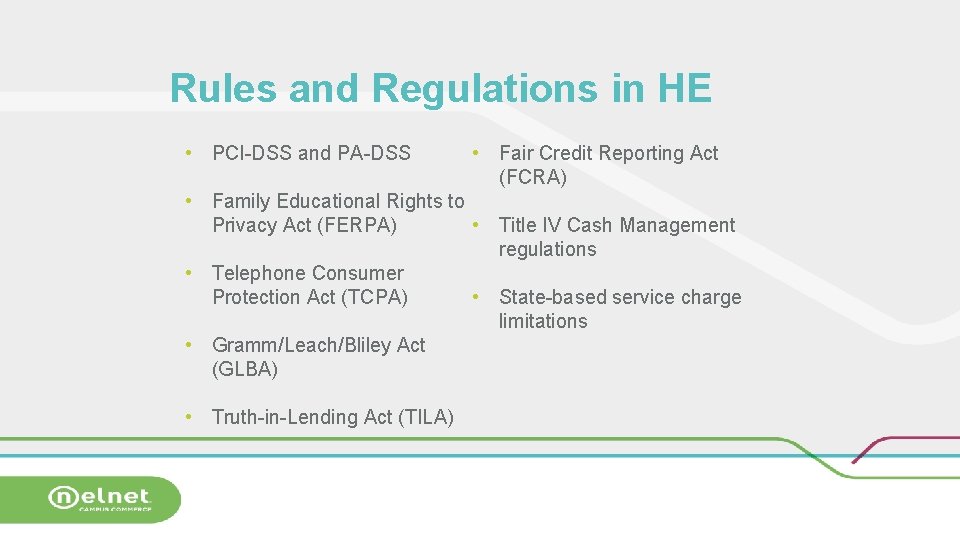
Rules and Regulations in HE • PCI-DSS and PA-DSS • Fair Credit Reporting Act (FCRA) • Family Educational Rights to • Title IV Cash Management Privacy Act (FERPA) regulations • Telephone Consumer • State-based service charge Protection Act (TCPA) limitations • Gramm/Leach/Bliley Act (GLBA) • Truth-in-Lending Act (TILA)

What has Nelnet learned? How do we respond? Team of 30+ security professionals o Partnership with Campus. Guard Security Response Plan o Determine and identify incident o Containment o Eradication o Recover o Lessons learned Client communication— 3 T’s o Transparency o Timely response o Team coordination

Websites of interest Millennials vs. Boomers cybersecurity: http: //www. uzado. com/blog/millennials-are-the-biggest-targets-for-cyber-attacks This is also related and interesting: http: //www. nextgov. com/cybersecurity/2017/07/millennials-pose-greatest-it-securityrisk-any-group-survey-says/139371/ “Krebs on Security”, easy reading that gives a lot of information on some of the latest security news. https: //krebsonsecurity. com/ Data. Breach Today: https: //www. databreachtoday. com Educause Cybersecurity: https: //library. educause. edu/topics/cybersecurity Help. Net. Seurity: https: //www. helpnetsecurity. com/view/news/ World’s Biggest Data Breaches: http: //www. informationisbeautiful. net/visualizations/worlds-biggest-data-breacheshacks/

LAWS THAT REGULATE STUDENT PRIVACY • FERPA: Family Educational Rights and Privacy Act • GLBA: Gramm-Leach-Bliley Privacy Act • FACT-Red Flag Rules • GDPA- General Data Protection Rules

DEPARTMENT OF EDUCATION CYBER SECURITY • Entire section devoted to Cyber Security Compliance on IFAP ‒ GLBA ‒ Red Flags Rule ‒ FERPA ‒ State Privacy Laws (Security Breach Notification Laws) ‒ International Laws ‒ Reporting a Data Breach https: //ifap. ed. gov/eannouncements/Cyber. html

Information Security To Be Part of the Higher Education Single Audit • Compliance with certain provisions of the Gramm-Leach. Bliley Act (GLBA), which are designed to help your institution properly secure sensitive student data, will be tested as part of your single audit • Be prepared for GLBA Compliance Testing • Open comment period coming soon • Implementation TBD

GLBA • GLBA: Gramm-Leach Bliley Act signed into law November 1999. • Regulation: Privacy regulations issued by federal agencies (Compliance required as of 7/1/01) • FTC PART 314 -Standards for Safeguarding Customer Information (Effective 5/23/03) • Scope: Regulates the sharing of: • “Nonpublic personal information” about individuals who obtain “financial products or services” • From “financial institutions” primarily for personal, family or household purposes

GLBA • Design and implement a written security plan • Select a group or committee to implement program • Identify all foreseeable risks • Training/Human Resources/Management • Information Systems • System Failures/Intrusions-Disaster Plans • Put together a written program to control these risks • Oversee service providers to make sure they are capable of maintaining appropriate safeguards and require by contract to implement and maintain such safeguards • Evaluate program each year as environment changes

Data Protection for EU Students • EU General Data Protection Regulations • Effective May 25 th 2018 • Even an organization that is not established within the EU can be caught by GDPR if it processes personal data of data subjects who are in the Union where the processing activities are related "to the offering of goods or services”. • Aiming to create more consistent protection of consumer and personal data across EU nations. • Companies that fail to achieve GDPR compliance are subject to stiff penalties and fines. • https: //gdpr-info. eu/

Tips To Remember • Information Security Policy • Do not store sensitive information on workstation or mobile device • Written justification and approval for sensitive data storage • Purge sensitive information as soon as its business need no longer exists • Purge Data • Record retention schedules give useful life of each type of information • Purge info-Wipe, not delete • Security File Deletion Utilities • Cross cut shred, not store

Tips To Remeber • Look at your physical environment • • • Messy vs. clean desk Reports and files stored out of site Locking file cabinets and offices Passwords on post-it notes? USB drives easily available Flash Cards, CDs, and disk lying around in plan site Monitor location/desk direction Are visitors identified, challenged? Public access to business areas? Public Fax? Use Cross Cut Shredders

CONTACT INFORMATION GLBA www. ftc. gov/privacyinitiatives/glbact. html Laura D. Berger, Attorney Division of Financial Practices FTC (202) 326 -3224 Karen Reddick National Credit Management kreddick@ncmstl. com Roy Chernikoff Nelnet Campus Commerce Roy. chernikoff@Nelnet. net

 Flat addressing vs hierarchical addressing
Flat addressing vs hierarchical addressing Private secruity
Private secruity Risk in security analysis and portfolio management
Risk in security analysis and portfolio management Market risk credit risk operational risk
Market risk credit risk operational risk Azure security privacy compliance and trust
Azure security privacy compliance and trust Oracle governance risk and compliance
Oracle governance risk and compliance Ncrq hsd2 assignment 1
Ncrq hsd2 assignment 1 Hr governance risk and compliance
Hr governance risk and compliance Grc meaning
Grc meaning Security compliance monitoring
Security compliance monitoring Oeaa michigan
Oeaa michigan Fiduciary investment risk management association
Fiduciary investment risk management association Risk map
Risk map Wireless security in cryptography and network security
Wireless security in cryptography and network security E commerce security policy
E commerce security policy Compliance risk definition
Compliance risk definition Ocrs score
Ocrs score Addressing concerns and earning commitment
Addressing concerns and earning commitment Classful ip address
Classful ip address Classless subnet
Classless subnet Earning commitment
Earning commitment Classless and classful
Classless and classful Classful and classless addressing
Classful and classless addressing Responsive anticipation and creative anticipation
Responsive anticipation and creative anticipation Supernetting example
Supernetting example Chapter 12 addressing competition and driving growth
Chapter 12 addressing competition and driving growth Aircraft communications addressing and reporting system
Aircraft communications addressing and reporting system Chapter 13 return risk and the security market line
Chapter 13 return risk and the security market line What is the osi security architecture
What is the osi security architecture Security guide to network security fundamentals
Security guide to network security fundamentals Visa international security model diagram
Visa international security model diagram Electronic mail security in network security
Electronic mail security in network security Nstissc model
Nstissc model Software security building security in
Software security building security in Security guide to network security fundamentals
Security guide to network security fundamentals Security guide to network security fundamentals
Security guide to network security fundamentals Residual risk and secondary risk pmp
Residual risk and secondary risk pmp Business risk vs financial risk capital structure
Business risk vs financial risk capital structure