Security and Robustness in an Agentbased Network Monitoring

Security and Robustness in an Agent-based Network Monitoring System Plan B Project Koka Muralidhar Advisor: Prof. Tripathi University of Minnesota

Outline 1. 2. 3. 4. 5. 6. Motivation Monitoring System Overview Security Robustness System Capabilities and Experiences Conclusions and Future Work

1. Motivation n Develop tools and techniques that help system administrators monitor computing environments. n Guard against malicious users n n n Attacks and misuse Check for misconfigurations Alert on resource failures
Challenges Involved n Increasing number of components in computing environments: n New hardware/software components are added n n New monitoring tools and policies are required Large amount of monitoring data needs to be collected and digested n n Monitoring data in different formats Delay in administrator’s response to critical events contd…

Challenges Involved (contd…) n A comprehensive monitoring system requires correlation of data from diverse sources related to different aspects of a network system n E. g. user activities, network traffic, file systems …
Goals n Dynamic configurability n n Dynamic extensibility n n Change in configuration of software components, administrative policies Addition of new monitoring functions, tools Active monitoring n Alter detection policies in response to critical events
Goals n Secure n n Robust n n Detect failed components and restore them without stopping the system Scalable n n System itself should be protected from attacks. Scale as the number of nodes in the network increases Acceptable system performance n Should not interfere with the normal functioning of the host.

Mobile-agent based Implementation n Agents can migrate to the monitored nodes providing local processing of events Agents can encapsulate policies for event monitoring and filtering New monitoring functionalities can be installed dynamically at remote nodes n Agent policies can be securely controlled remotely n Agents can cooperatively monitor the network n Agent can autonomously adapt and react
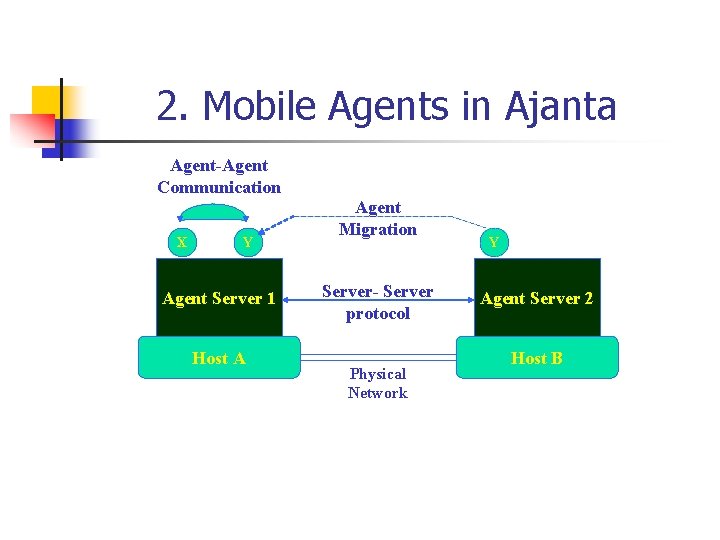
2. Mobile Agents in Ajanta Agent-Agent Communication X Y Agent Server 1 Host A Agent Migration Server- Server protocol Physical Network Y Agent Server 2 Host B
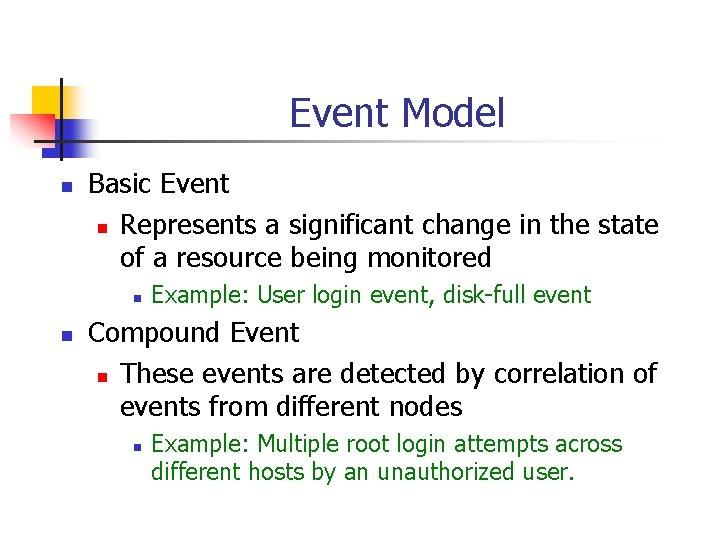
Event Model n Basic Event n Represents a significant change in the state of a resource being monitored n n Example: User login event, disk-full event Compound Event n These events are detected by correlation of events from different nodes n Example: Multiple root login attempts across different hosts by an unauthorized user.
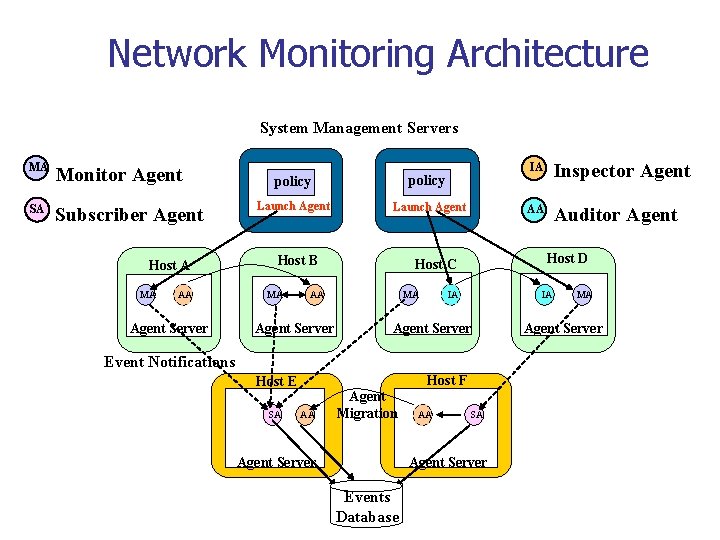
Network Monitoring Architecture System Management Servers MA SA Monitor Agent Subscriber Agent Host A MA AA Agent Server policy Launch Agent Host B MA Agent Server MA IA Agent Server Host F SA AA Agent Migration Agent Server AA SA Agent Server Events Database AA Auditor Agent IA Event Notifications Host E Inspector Agent Host D Host C AA IA MA Agent Server
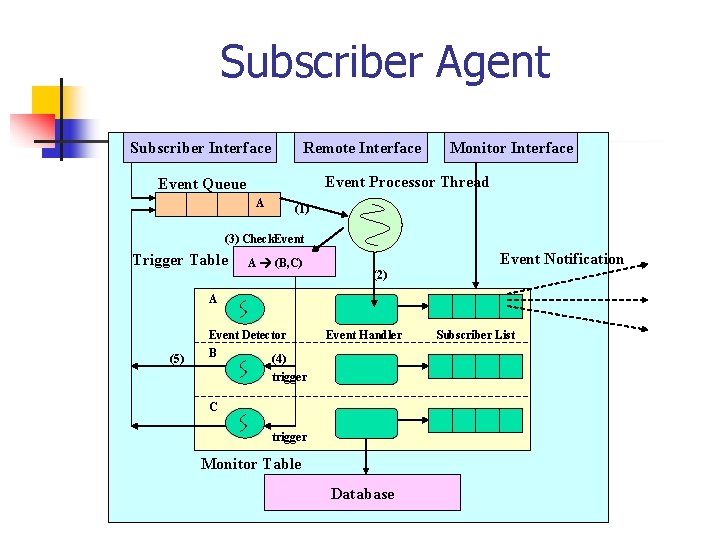
Subscriber Agent Subscriber Interface Remote Interface Monitor Interface Event Processor Thread Event Queue A (1) (3) Check. Event Trigger Table A (B, C) Event Notification (2) A (5) Event Detector B (4) Event Handler trigger C trigger Monitor Table Database Subscriber List
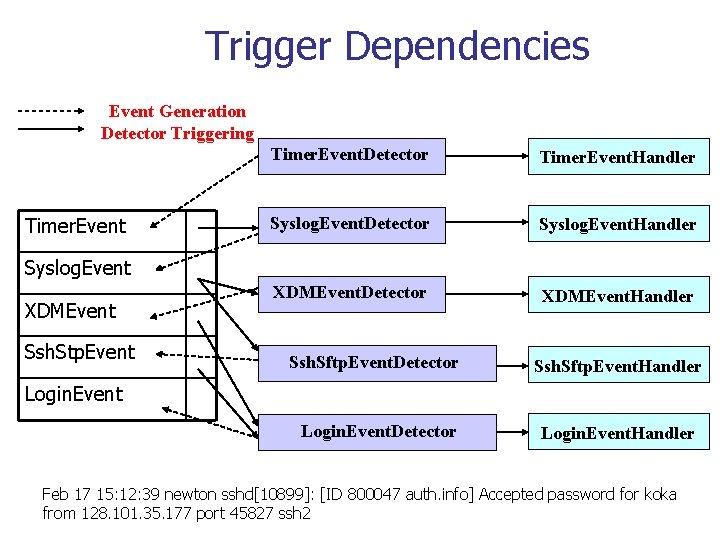
Trigger Dependencies Event Generation Detector Triggering Timer. Event. Detector Timer. Event. Handler Syslog. Event. Detector Syslog. Event. Handler XDMEvent. Detector XDMEvent. Handler Syslog. Event XDMEvent Ssh. Stp. Event Ssh. Sftp. Event. Detector Ssh. Sftp. Event. Handler Login. Event. Detector Login. Event. Handler Login. Event Feb 17 15: 12: 39 newton sshd[10899]: [ID 800047 auth. info] Accepted password for koka from 128. 101. 35. 177 port 45827 ssh 2

3. Security n n Name Service Agent Servers n n assumed trusted and secure Use Java security policy Give permissions based on code base and principal on whose behalf an agent is running Admission Policy – accept agents coming from authorized entities only “Security in the Ajanta Mobile Agent System”, N. Karnik and A. Tripathi, S P & E, 2001

Agent Admission Policy Spec. n Based on the tuple (host/domain, user/agent server) Specify +ve, and -ve permissions and wild card characters n # accept agents coming from a specific domain n # don’t accept any agents coming from a specific domain n domain = cs. umn. edu, user = * !ip_addr = 128. 101 or !user = * # accept agents coming from a specific host and a specific user n host = plato. cs. umn. edu, user = urn: ans: plato. cs. umn. edu/koka

Security n Monitor/Subscriber Agents n n Migrate/terminate the agent Modify the agent behavior n n n E. g. delete detectors Subscribe to events Delete subscription Send false events Might modify agent control policies Solution: Secure Inter-Agent Communication and allowing only authorized entities to communicate with an agent
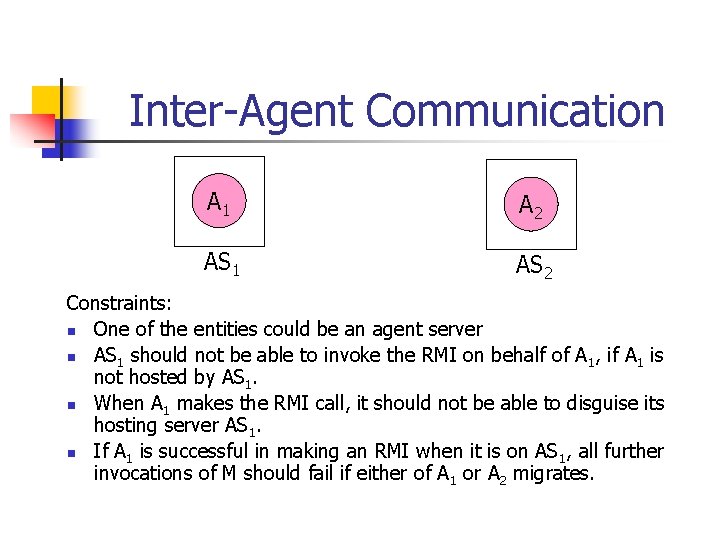
Inter-Agent Communication A 1 A 2 AS 1 AS 2 Constraints: n One of the entities could be an agent server n AS 1 should not be able to invoke the RMI on behalf of A 1, if A 1 is not hosted by AS 1. n When A 1 makes the RMI call, it should not be able to disguise its hosting server AS 1. n If A 1 is successful in making an RMI when it is on AS 1, all further invocations of M should fail if either of A 1 or A 2 migrates.
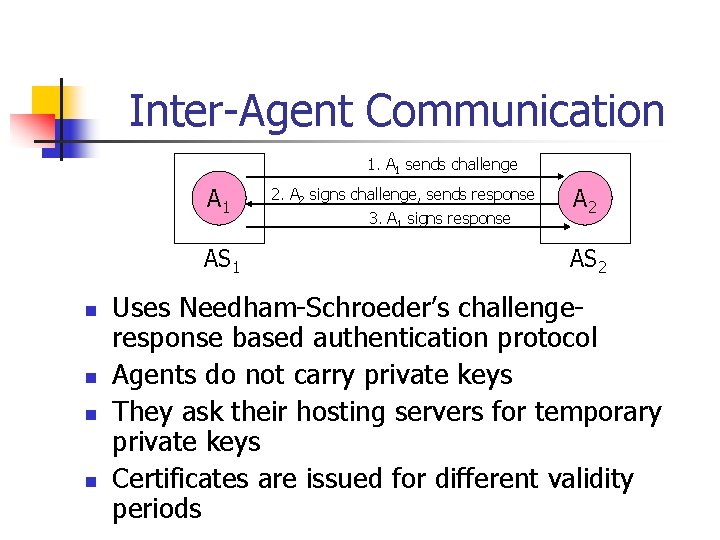
Inter-Agent Communication 1. A 1 sends challenge A 1 AS 1 n n 2. A 2 signs challenge, sends response 3. A 1 signs response A 2 AS 2 Uses Needham-Schroeder’s challengeresponse based authentication protocol Agents do not carry private keys They ask their hosting servers for temporary private keys Certificates are issued for different validity periods
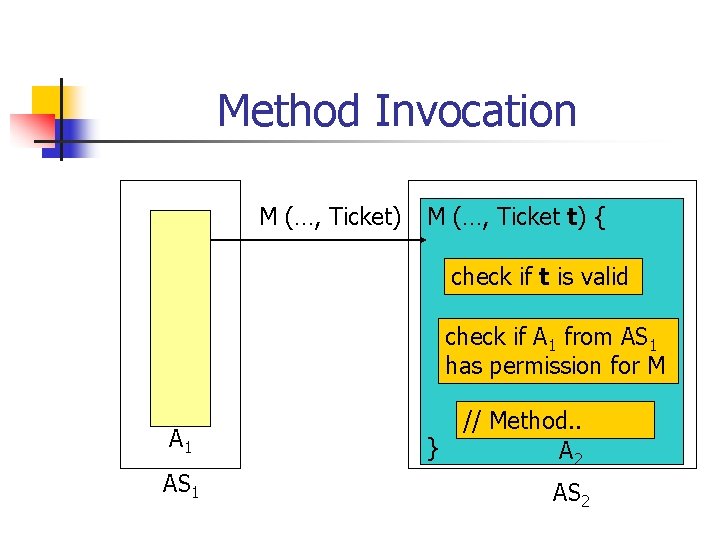
Method Invocation M (…, Ticket) M (…, Ticket t) { check if t is valid check if A 1 from AS 1 has permission for M A 1 AS 1 } // Method. . A 2 AS 2
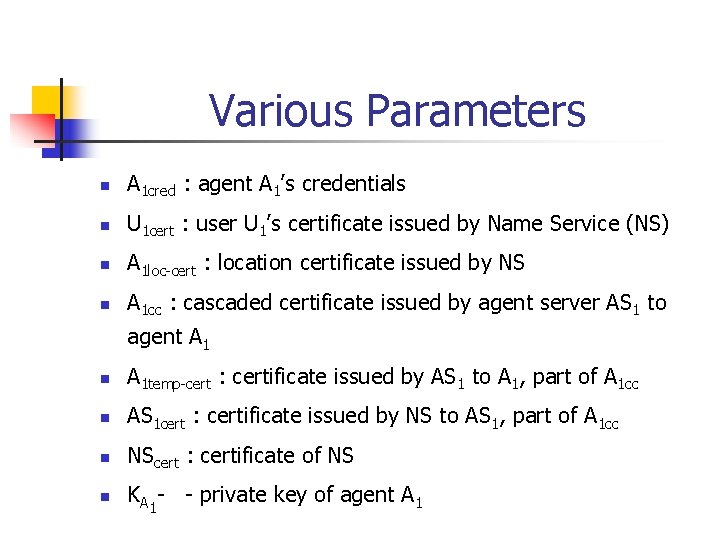
Various Parameters n A 1 cred : agent A 1’s credentials n U 1 cert : user U 1’s certificate issued by Name Service (NS) n A 1 loc-cert : location certificate issued by NS n A 1 cc : cascaded certificate issued by agent server AS 1 to agent A 1 n A 1 temp-cert : certificate issued by AS 1 to A 1, part of A 1 cc n AS 1 cert : certificate issued by NS to AS 1, part of A 1 cc n NScert : certificate of NS n KA 1 - - private key of agent A 1

Authentication Protocol n A 1 to A 2: n n (A 1 cred, U 1 cert, A 1 loc-cert, A 1 cc, N 1) N 1 is a nonce that A 2 has to sign A 2 makes the following checks: n n n Validity of U 1 cert using NScert Verify A 1 cred using the public key in U 1 cert Validity of A 1 loc-cert using NScert Validity of A 1 cc i. e. , AS 1 cert is valid and that A 1 temp-cert is signed using public key in AS 1 cert Name in AS 1 cert is the same as the one in A 1 loc-cert
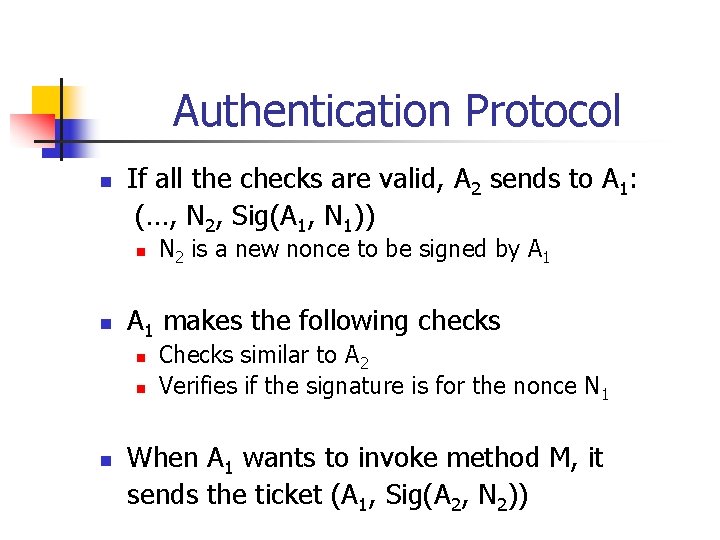
Authentication Protocol n If all the checks are valid, A 2 sends to A 1: (…, N 2, Sig(A 1, N 1)) n n A 1 makes the following checks n n n N 2 is a new nonce to be signed by A 1 Checks similar to A 2 Verifies if the signature is for the nonce N 1 When A 1 wants to invoke method M, it sends the ticket (A 1, Sig(A 2, N 2))

ISSUES n n n Nonce is incremented instead of authenticating every time A 1 loc-cert can be verified by going to the Name Service every time If an agent server is compromised. .
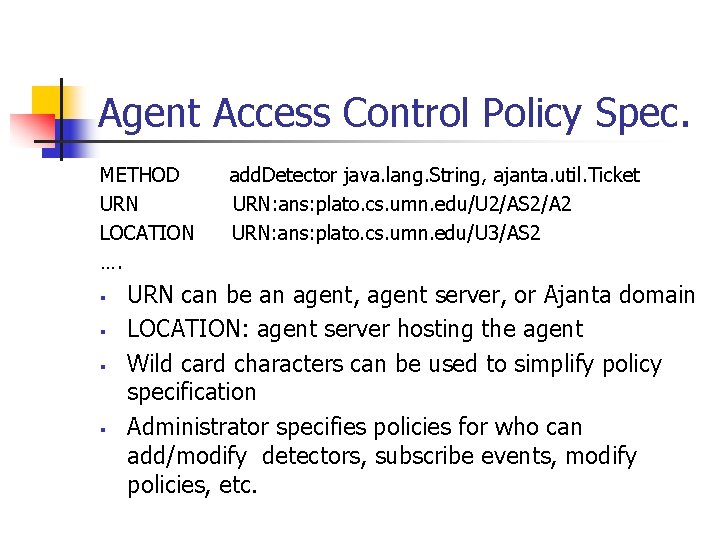
Agent Access Control Policy Spec. METHOD URN LOCATION …. § § add. Detector java. lang. String, ajanta. util. Ticket URN: ans: plato. cs. umn. edu/U 2/AS 2/A 2 URN: ans: plato. cs. umn. edu/U 3/AS 2 URN can be an agent, agent server, or Ajanta domain LOCATION: agent server hosting the agent Wild card characters can be used to simplify policy specification Administrator specifies policies for who can add/modify detectors, subscribe events, modify policies, etc.
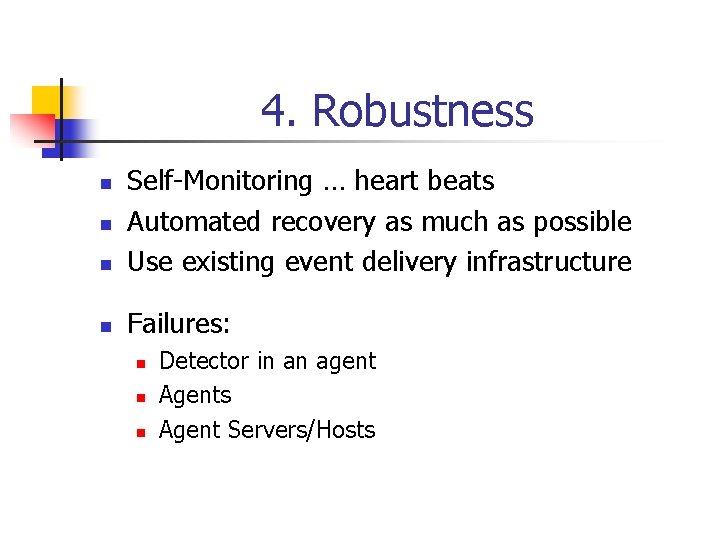
4. Robustness n Self-Monitoring … heart beats Automated recovery as much as possible Use existing event delivery infrastructure n Failures: n n n Detector in an agent Agents Agent Servers/Hosts

Robustness n n Failure events are modeled as regular events Each agent runs an Agent. Alive. Detector which generates heart-beat events Failure. Event. Detector determines failures. They can be run by an agent. Failures are handled by the SMS
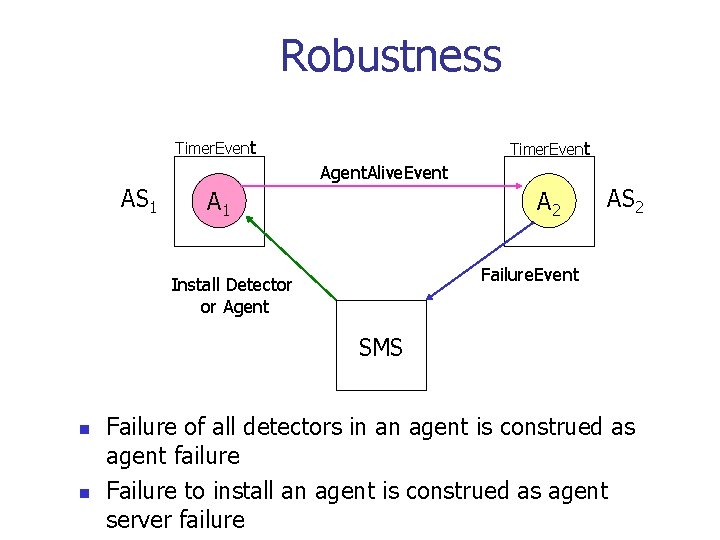
Robustness Timer. Event Agent. Alive. Event AS 1 A 2 AS 2 Failure. Event Install Detector or Agent SMS n n Failure of all detectors in an agent is construed as agent failure Failure to install an agent is construed as agent server failure

Robustness…constraints n n n Any number of Failure. Event. Detectors could be running Agent. Alive and Failure. Event detectors could run with different frequencies Restoration could take any amount of time Multiple failure events need to be handled simultaneously SMS can be disconnected Don’t install agents/detectors unless it is necessary
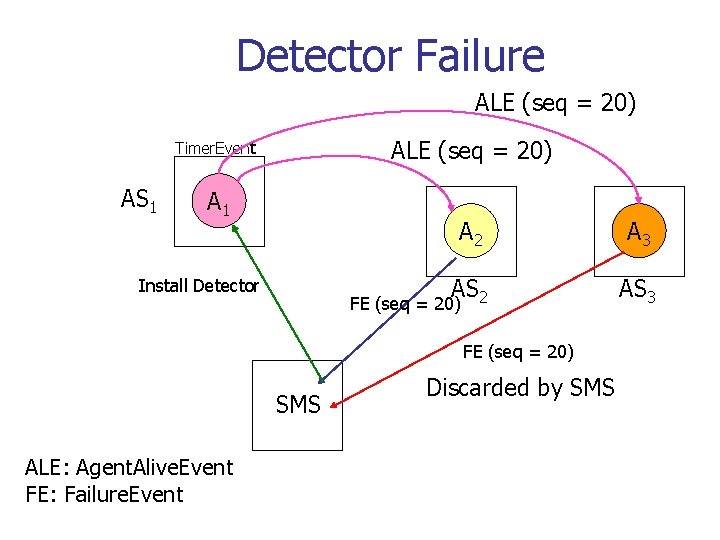
Detector Failure ALE (seq = 20) Timer. Event AS 1 A 1 Install Detector A 2 A 3 AS 2 AS 3 FE (seq = 20) SMS ALE: Agent. Alive. Event FE: Failure. Event Discarded by SMS
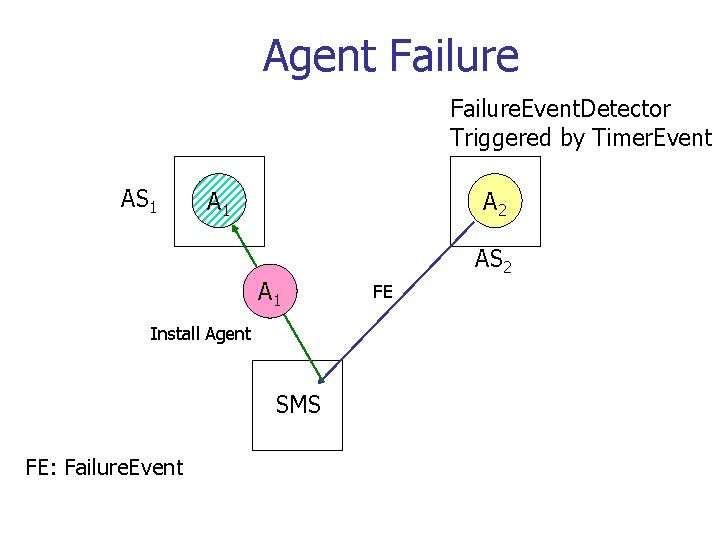
Agent Failure. Event. Detector Triggered by Timer. Event AS 1 A 2 A 1 Install Agent SMS FE: Failure. Event AS 2 FE
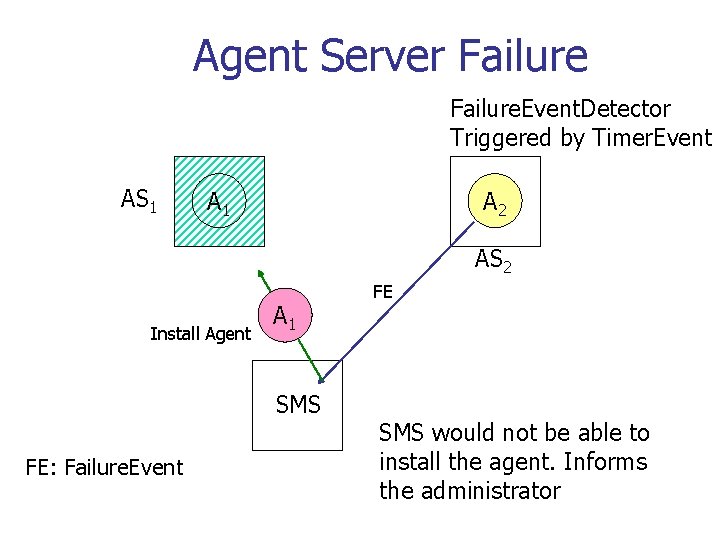
Agent Server Failure. Event. Detector Triggered by Timer. Event AS 1 A 2 AS 2 Install Agent A 1 SMS FE: Failure. Event FE SMS would not be able to install the agent. Informs the administrator

5. System Capabilities n n n System log monitors Process monitors File Consistency inspectors Host fingerprint inspectors Integrated Snort
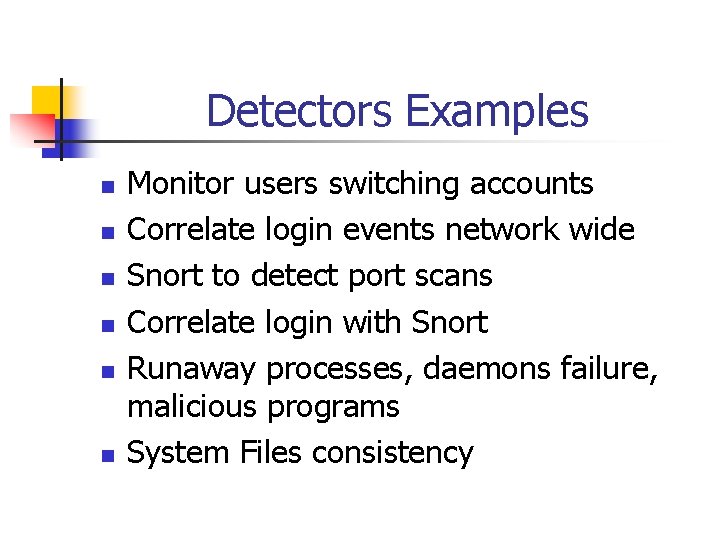
Detectors Examples n n n Monitor users switching accounts Correlate login events network wide Snort to detect port scans Correlate login with Snort Runaway processes, daemons failure, malicious programs System Files consistency
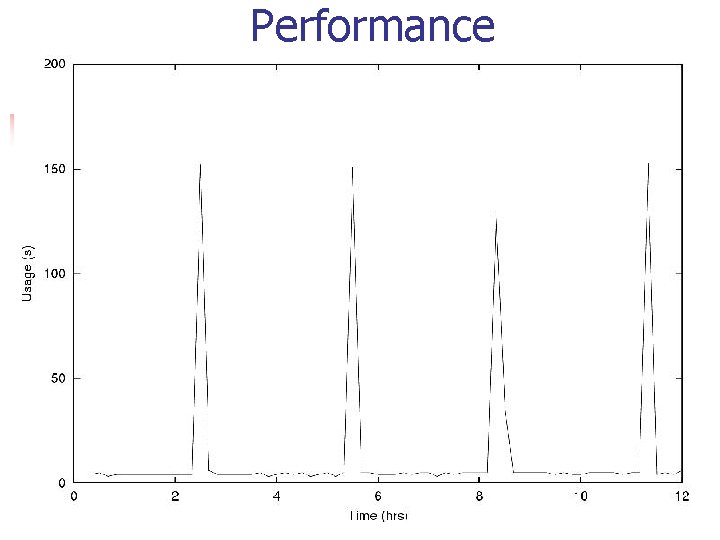
Performance Figure…what can you do to reduce CPU usage n

Experiences n n n Implementation of Syslog detector Dynamic modification of detectors Termination of detectors Deletion and addition of detectors Storage model of detectors Need for a feedback mechanism

6. Conclusions n n Mobile-agents can be used to build network monitoring systems System presented is dynamic configurable and extensible, actively monitors networks, secure, robust and has acceptable resource usage
Future Work n n Test the scalability of the system Test the utility of the system by asking system administrators to use it Develop agents to facilitate software installations Applying data mining concepts
Acknowledgements… n n n Prof. Tripathi Tanvir Ahmed Sumedh Pathak Megan Carney Abhijit Pathak - Overall Initial Implementation , , File System Monitoring
- Slides: 38