RFID Introduction Introduction What is RFID An automatic











- Slides: 27

RFID Introduction

Introduction • What is RFID An automatic identification technology that relies on radio waves to encode and decode information on a microchip or other storage device. RFID allows computer systems to capture data stored on a special tag without direct contact or line of sight acquisition. • RFID technology was invented in 1948 • The first United States patent for RFID was granted in 1973 • RFID consists of Tags, Tag Readers, Edge Servers and Application Software

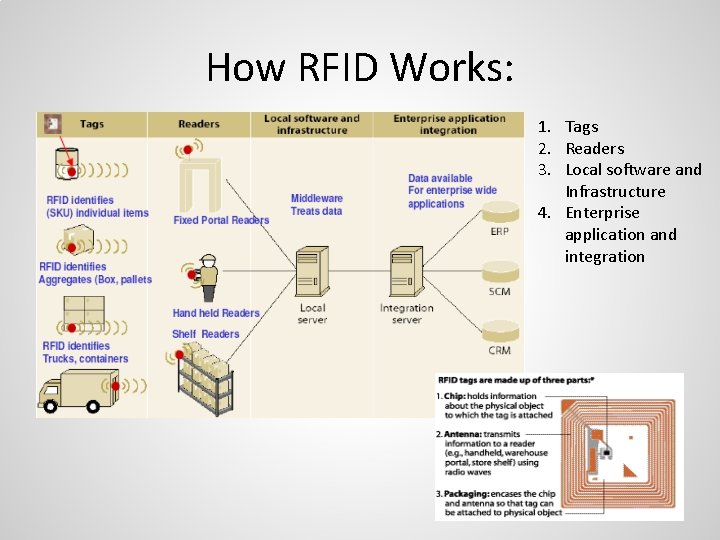
How RFID Works: 1. Tags 2. Readers 3. Local software and Infrastructure 4. Enterprise application and integration

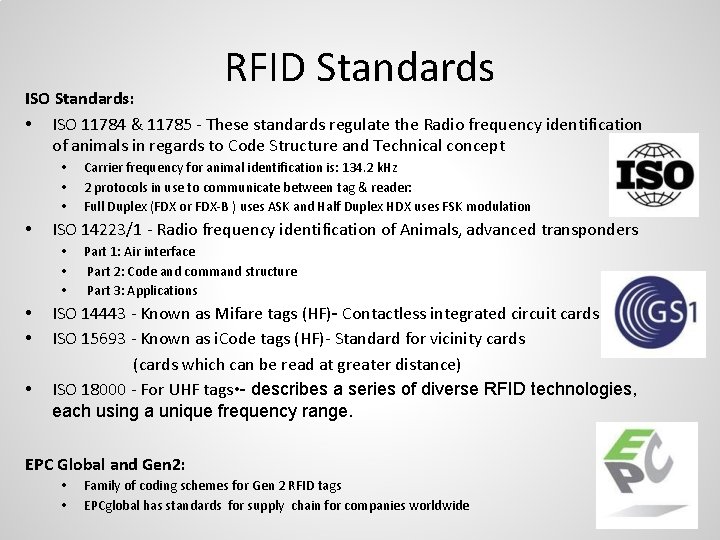
RFID Standards ISO Standards: • ISO 11784 & 11785 - These standards regulate the Radio frequency identification of animals in regards to Code Structure and Technical concept • • ISO 14223/1 - Radio frequency identification of Animals, advanced transponders • • • Carrier frequency for animal identification is: 134. 2 k. Hz 2 protocols in use to communicate between tag & reader: Full Duplex (FDX or FDX-B ) uses ASK and Half Duplex HDX uses FSK modulation Part 1: Air interface Part 2: Code and command structure Part 3: Applications ISO 14443 - Known as Mifare tags (HF)- Contactless integrated circuit cards ISO 15693 - Known as i. Code tags (HF)- Standard for vicinity cards (cards which can be read at greater distance) ISO 18000 - For UHF tags • - describes a series of diverse RFID technologies, each using a unique frequency range. EPC Global and Gen 2: • • Family of coding schemes for Gen 2 RFID tags EPCglobal has standards for supply chain for companies worldwide

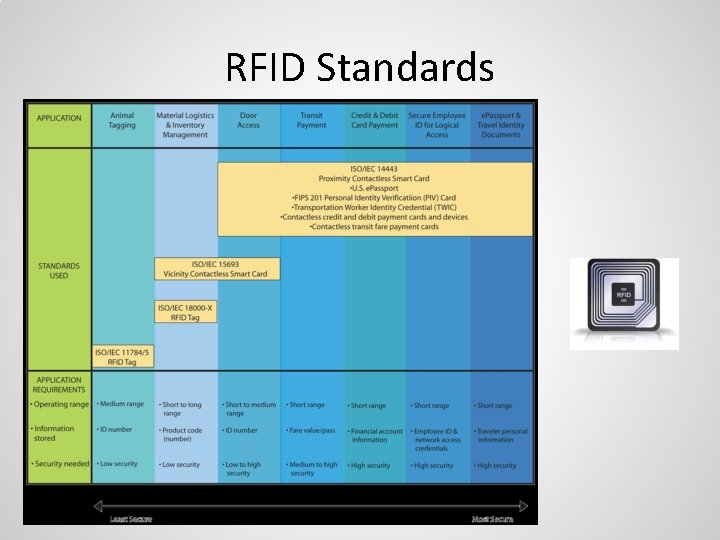
RFID Standards

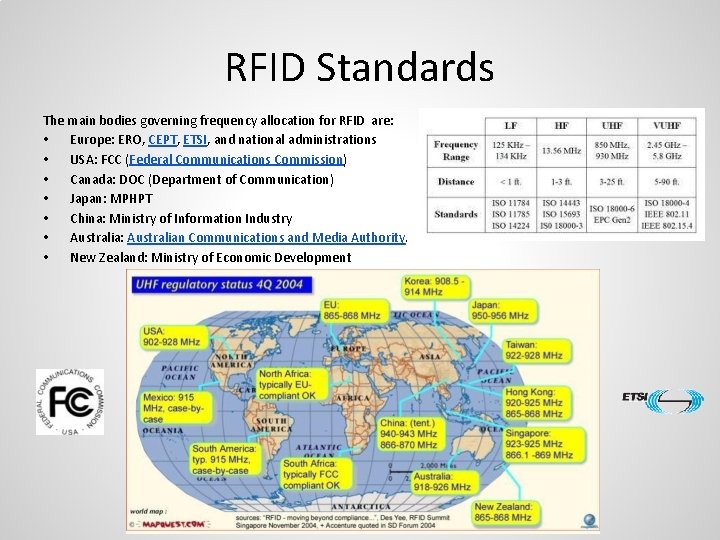
RFID Standards The main bodies governing frequency allocation for RFID are: • Europe: ERO, CEPT, ETSI, and national administrations • USA: FCC (Federal Communications Commission) • Canada: DOC (Department of Communication) • Japan: MPHPT • China: Ministry of Information Industry • Australia: Australian Communications and Media Authority. • New Zealand: Ministry of Economic Development

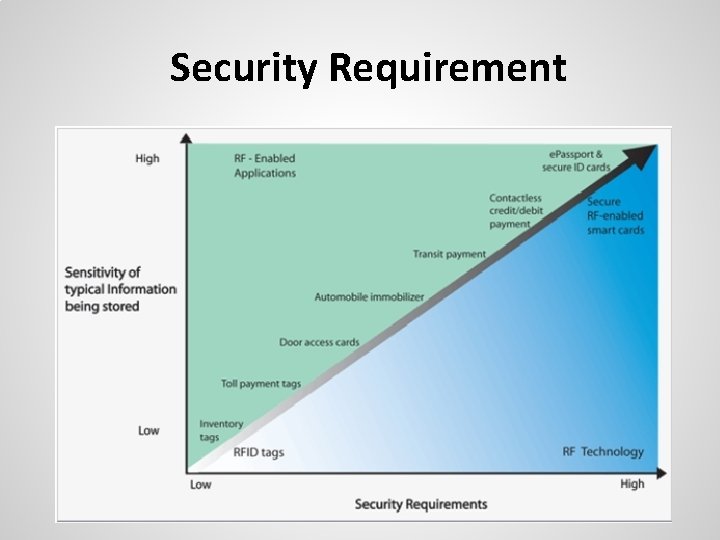
Security Requirement

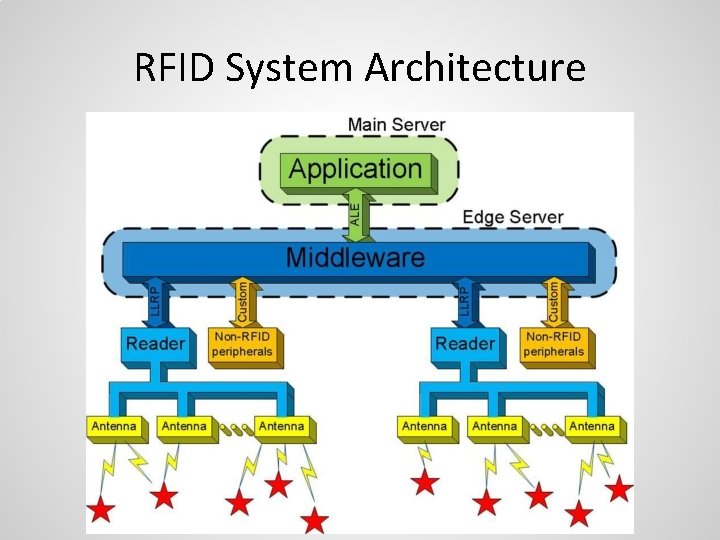
RFID System Architecture

RFID Applications

RFID Data Processing

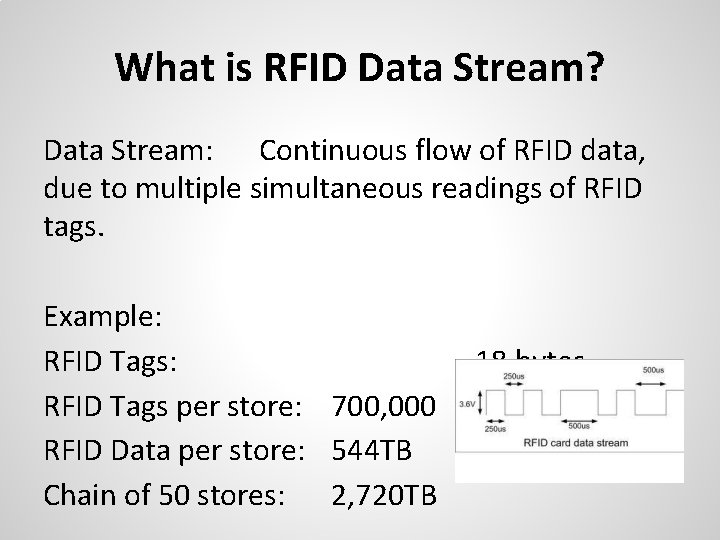
What is RFID Data Stream? Data Stream: Continuous flow of RFID data, due to multiple simultaneous readings of RFID tags. Example: RFID Tags per store: 700, 000 RFID Data per store: 544 TB Chain of 50 stores: 2, 720 TB 18 bytes

Types of RFID Data Stream? Temporal RFID Data Collection: Temporal data collection refers to RFID data collected periodically, or when a predefined event occurs, such as removing a product from a store shelf, or purchasing a product at the point of sale. Real-time RFID Data Collection: Real-time data collection does not wait for a periodic interval, or predefined event to occur to generate the data stream; rather the data stream is generated on a continuous basis.

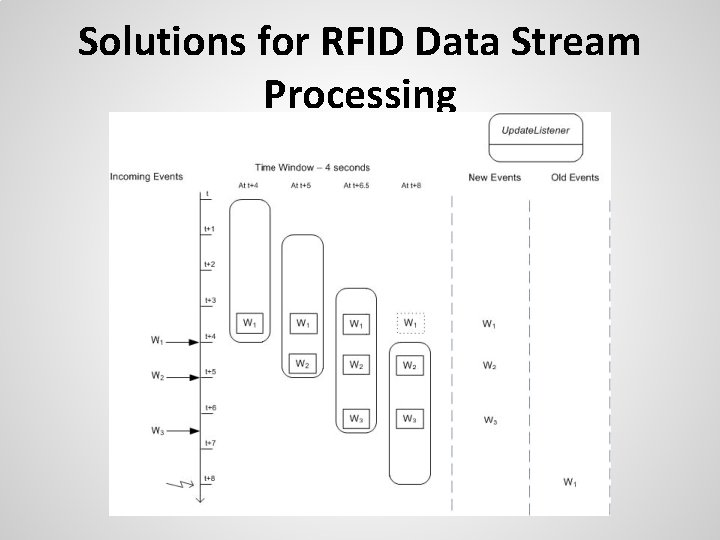
Challenges to RFID Stream False-Negative RFID Readings: RFID Tag reader fails to read a nearby RFID tag. False-Positive RFID Readings: Additional unexpected RFID data (Noise) added to the data stream. Duplicate RFID Readings: Multiple RFID readings of the same RFID tag.

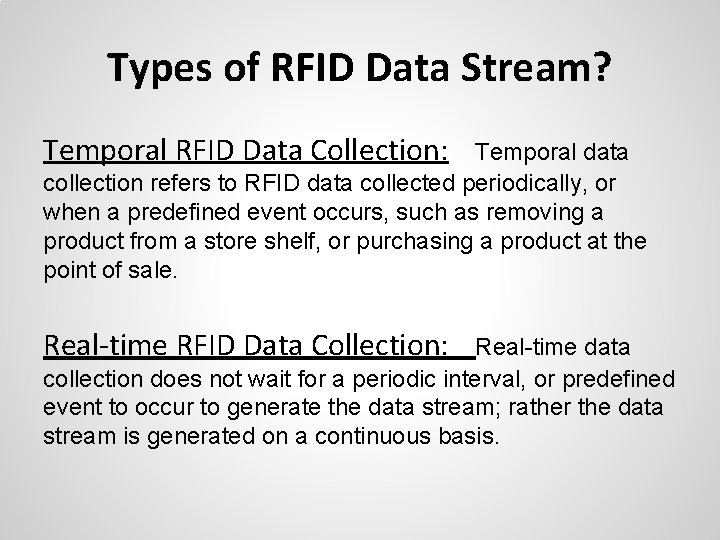
• Solutions for RFID Data Stream Processing Eliminate False RFID Tag Readings. o o • Network RFID Tag Readers. o • Increase scanning cycles Smart RFID Tags for redundancy. Data 'Sharing' among Tag Readers. Filter RFID Data Stream. o Baseline Denoising Algorithm.

Solutions for RFID Data Stream Processing

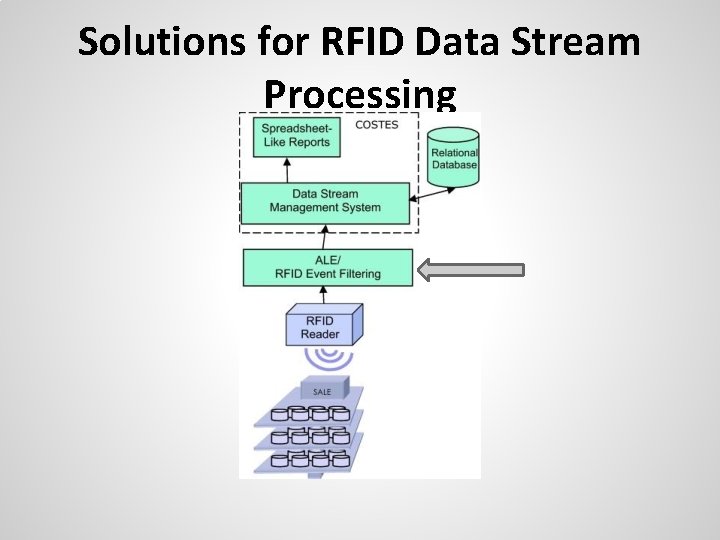
Solutions for RFID Data Stream Processing

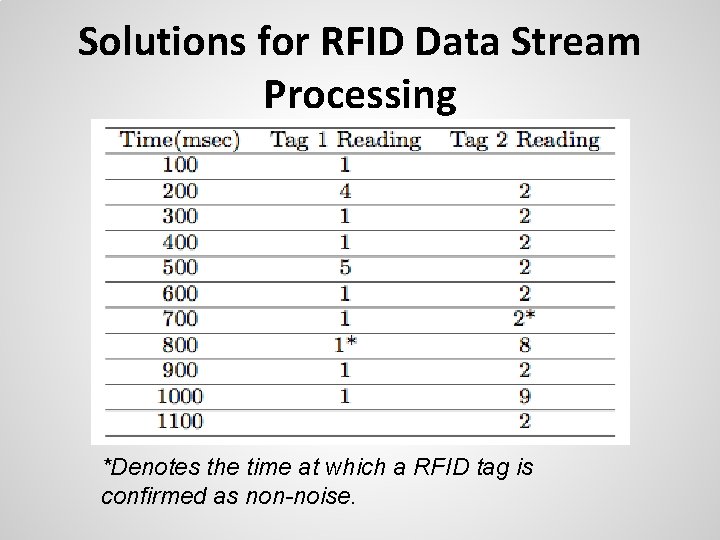
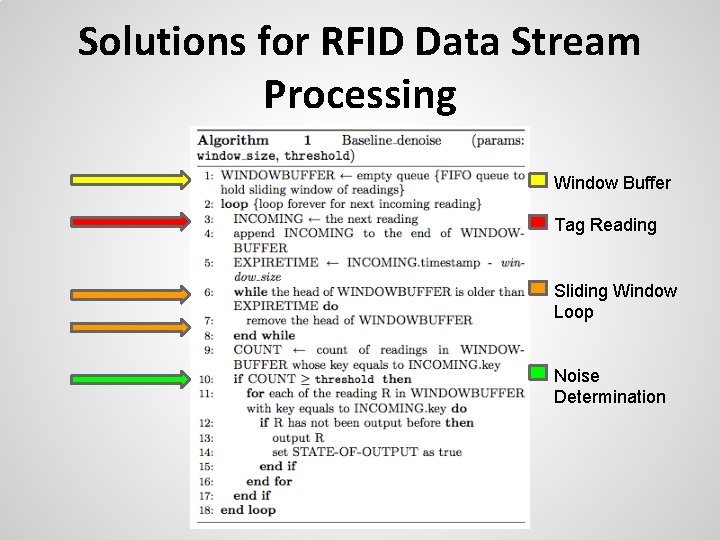
Solutions for RFID Data Stream Processing *Denotes the time at which a RFID tag is confirmed as non-noise.

Solutions for RFID Data Stream Processing Window Buffer Tag Reading Sliding Window Loop Noise Determination

Data Integration

Tag to Application Imagine if an application was plugged into all the device drivers of all connected readers…. What would your application developer have to do to make it work? …

RFID Middleware Software or devices that connect RFID readers and the data they collect to enterprise information systems.

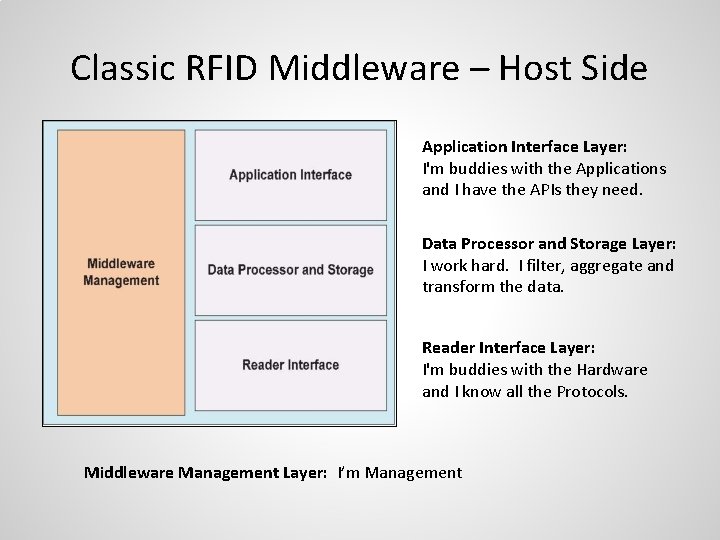
Classic RFID Middleware – Host Side Application Interface Layer: I'm buddies with the Applications and I have the APIs they need. Data Processor and Storage Layer: I work hard. I filter, aggregate and transform the data. Reader Interface Layer: I'm buddies with the Hardware and I know all the Protocols. Middleware Management Layer: I’m Management

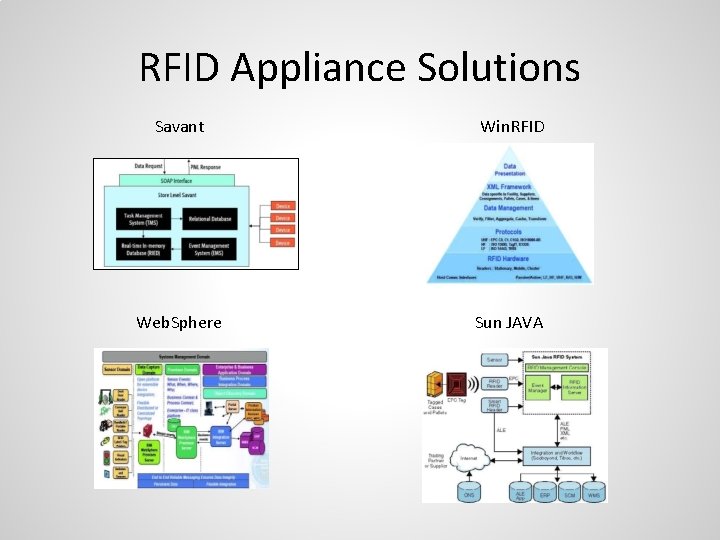
RFID Appliance Solutions Savant Win. RFID Web. Sphere Sun JAVA

Appliance Solutions • Savaunt, Win. RFID, Web. Sphere and Sun Java aim for designs that provide a scalable solution for gathering, filtering and providing clean RFID data. • Issues: • Raw RFID data is not valuable until it’s aggregated and transformed. • Applications with higher security requirements are using RFID. • Leak proprietary information • Ability to track private information such as the spending history of a consumer

Design Considerations Software or Devices that connect RFID readers and the data they collect to enterprise information systems. A major differentiator among RFID middleware products is where they reside in IT architecture: 1. Server Software 2. Middleware bundled into the reader. AKA moved intelligence to the edge of the network.

Edge Intelligence RFTag. Aware Globe. Ranger

Questions