UHF RFID security considerations A hardware point of




- Slides: 17

UHF RFID security considerations A hardware point of view November 7 th 2017 Dr. Delphine Bechevet – ICT Institute – hepia – HES-SO

Summary § RFID? § Context § Hardware point of view § To conclude 2

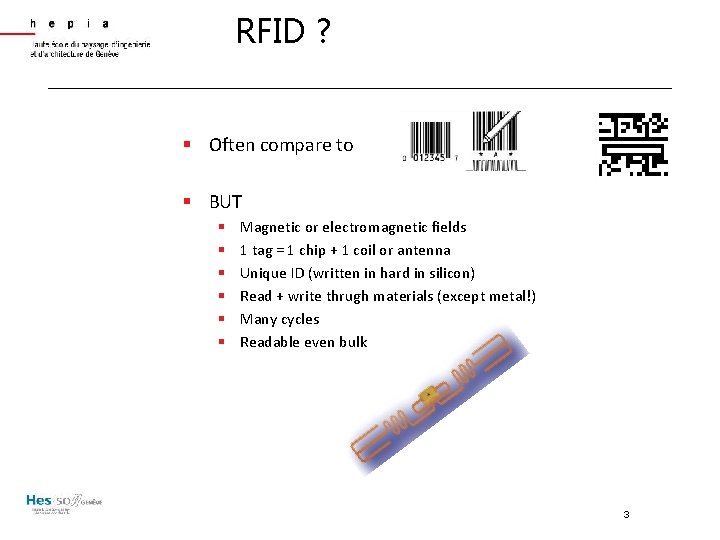
RFID ? § Often compare to § BUT § § § Magnetic or electromagnetic fields 1 tag = 1 chip + 1 coil or antenna Unique ID (written in hard in silicon) Read + write thrugh materials (except metal!) Many cycles Readable even bulk 3

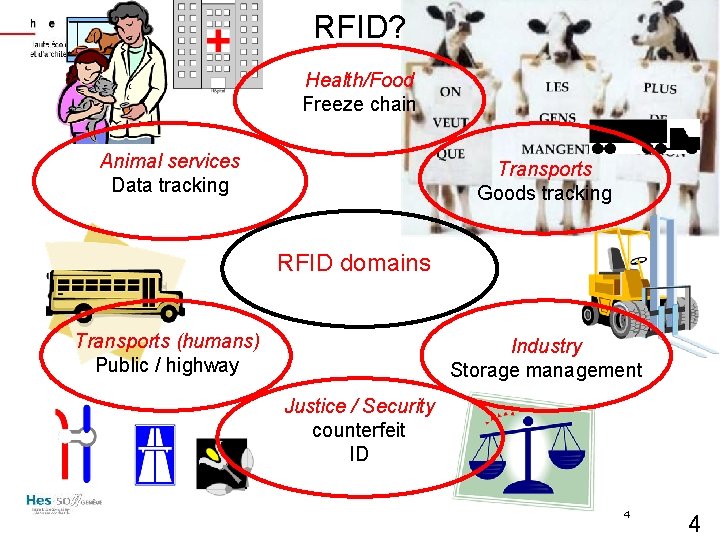
RFID? Health/Food Freeze chain Animal services Data tracking Transports Goods tracking RFID domains Transports (humans) Public / highway Industry Storage management Justice / Security counterfeit ID 4 4

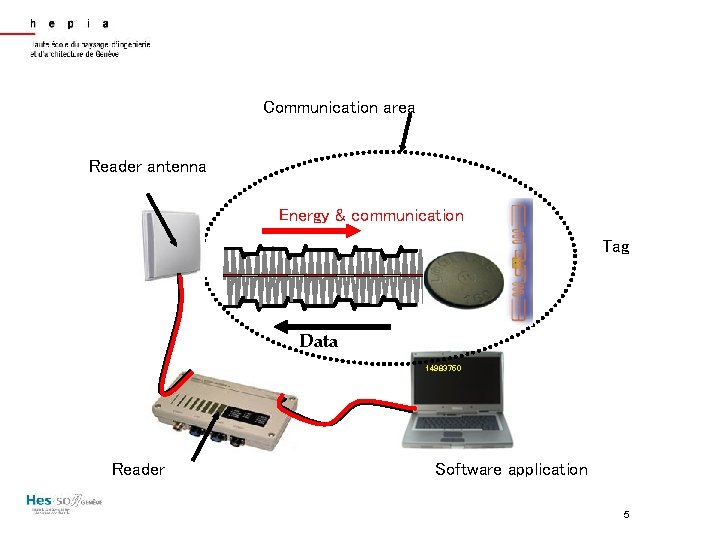
Communication area Reader antenna Energy & communication Tag Data 14983750 Reader Software application 5

Why security/ privacy for RFID? 6

Security context vs. RFID § Context: EU Recommandation vs. Privacy § “RFID technology enables the processing of data, including personal data, over short distances without physical contact or visible interaction between the reader or writer and the tag, such that this interaction can happen without the individual concerned being aware of it. ” § Scope § “Guide to Member States on the design and operation of RFID applications in a lawful, ethical and socially and politically acceptable way, respecting the right to privacy and ensuring protection of personal data”, 7

Security context vs. RFID § Privacy and data protection impact assesments (PIA) § § Operators: demonstration « appropriate technical and organisational measures » => protection of personal data and privacy Information and transparency on RFID use § Presence of an RFID reader § Name of operator (contact, policy) § Type of data processed by application 8

Security context vs. RFID § RFID applications used in the retail trade § Presence of RFID tags: a dedicated sign § Deactivation/removal tags used § unless consumers consents to keep tags operational § immediately and free-of-charge for the consumer § § Final check remove ? Or not remove? § Yes: cut (scissors) or kill bit § No: how to protect communication? § Code § Key § Digital solutions 9

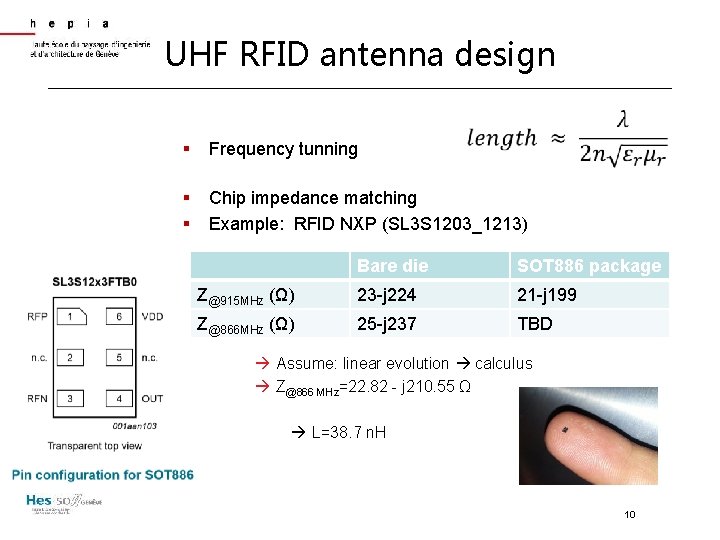
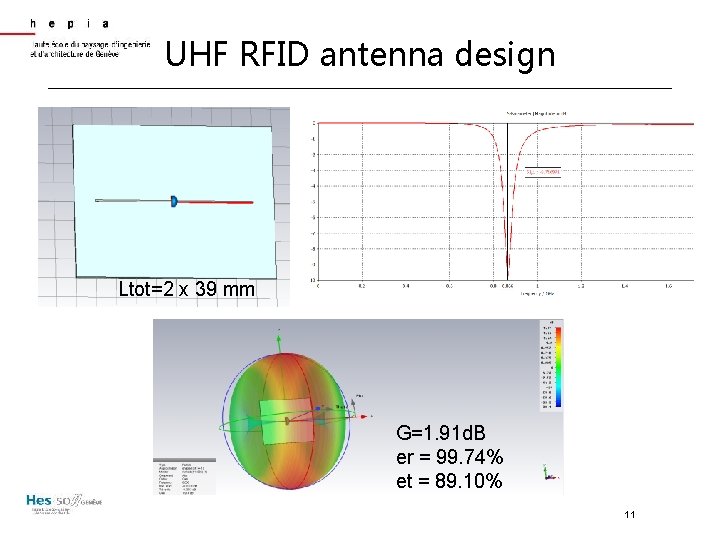
UHF RFID antenna design § Frequency tunning § § Chip impedance matching Example: RFID NXP (SL 3 S 1203_1213) Bare die SOT 886 package Z@915 MHz (Ω) 23 -j 224 21 -j 199 Z@866 MHz (Ω) 25 -j 237 TBD Assume: linear evolution calculus Z@866 MHz=22. 82 - j 210. 55 Ω L=38. 7 n. H 10

UHF RFID antenna design Ltot=2 x 39 mm G=1. 91 d. B er = 99. 74% et = 89. 10% 11

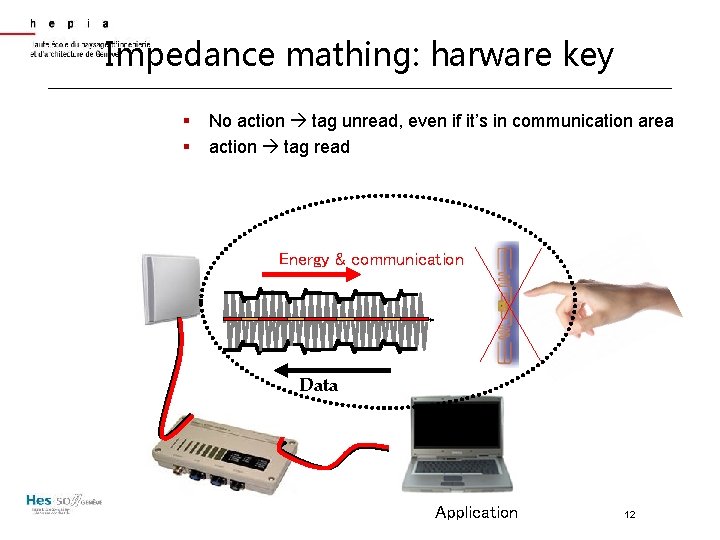
Impedance mathing: harware key § § No action tag unread, even if it’s in communication area action tag read Energy & communication Data 14983750 Application 12

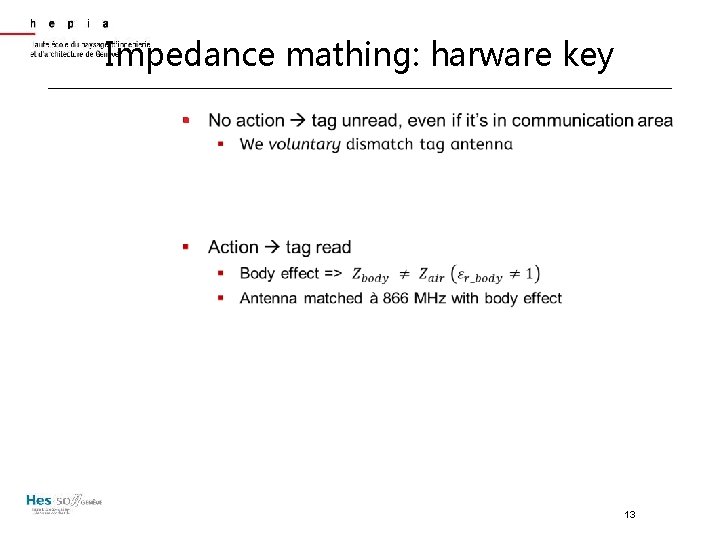
Impedance mathing: harware key § 13

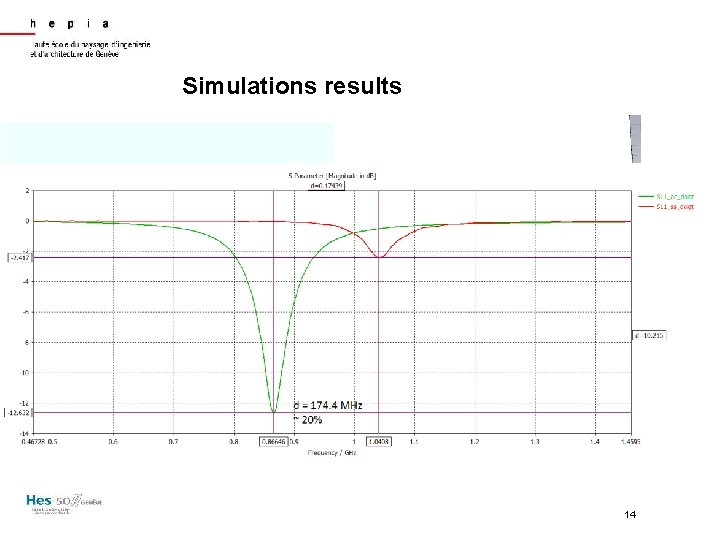
Simulations results 14

To conclude § Another point of view § Hardware solutions still alive! § Communication on user demand § Innovative projects in pipe line 15

Imagine the future with § System point of view § Privacy guarantee § Sustainable developments / enough energy § New technologies / Io. T Freedom 16

Thank you!! Time for questions delphine. bechevet@hesge. ch 17