Quality SelfReports Mitigation Plans and Completed Mitigation Plans
























- Slides: 51

Quality Self-Reports, Mitigation Plans, and Completed Mitigation Plans Ruchi Shah, WECC Scott Brooksby, WECC Debra Horvath, WECC W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

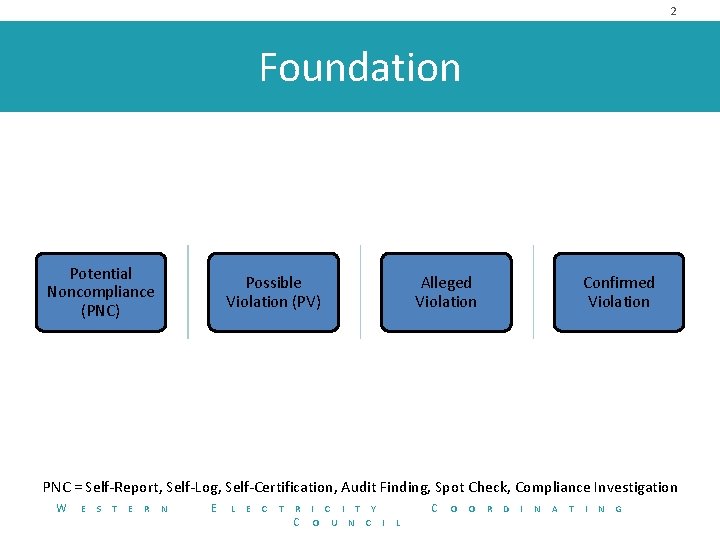
2 Foundation Potential Noncompliance (PNC) Possible Violation (PV) Alleged Violation Confirmed Violation PNC = Self-Report, Self-Log, Self-Certification, Audit Finding, Spot Check, Compliance Investigation W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

3 Terms • Potential Noncompliance (PNC) – Violation – Possible Violation • Compliance Enforcement Authority (CEA), e. g. WECC • Bulk Power System (BPS) – Bulk Electric System (BES) W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

4 Challenge with PNC’s • 81% of people whose job it is to write, agree with the statement, “Poorly written material 1 wastes my time. ” • WECC wants focus on mitigation, not rewriting PNC’s • The content of a PNC is formal communication to WECC/NERC/FERC • 2017: 426 completed PNC • 2018 YTD: 330 completed PNC W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I 1. The State of Business Writing (2016) N A T I N G

5 Quality Reduces Rework • Focus on QUALITY • Get it right the first time • but really … time W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

6 Material • NERC’s Registered Entity Self-Report and Mitigation Plan User Guide • Two cheat sheets (take home) • Six exercise worksheets – Reporting Dates – Detailed Description – Cause and Controls – Mitigation Steps – Risk and Prevention – Mitigation Completion W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

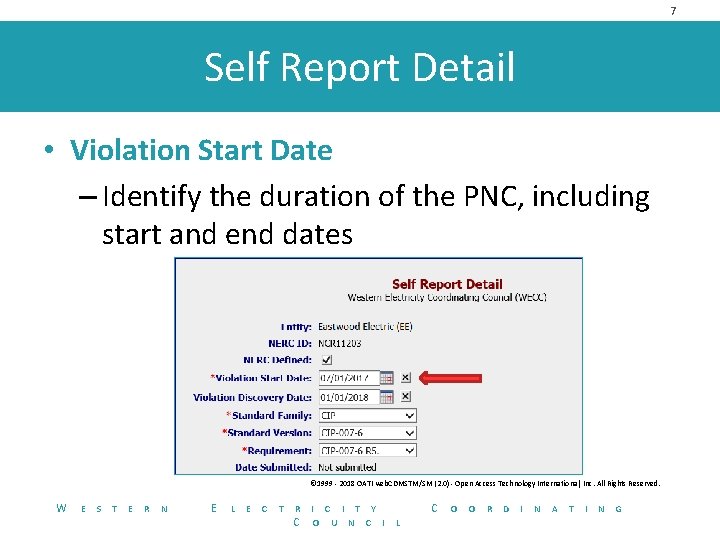
7 Self Report Detail • Violation Start Date – Identify the duration of the PNC, including start and end dates © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

8 Self Report Detail #2 • Discovery Date – What date did the entity discover the PNC? • Explain any gap exceeding three months between discovery and reporting 1 W E S T E R N E © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. L E C T R C I T Y O U N C I C L O O R D I N A T I N G

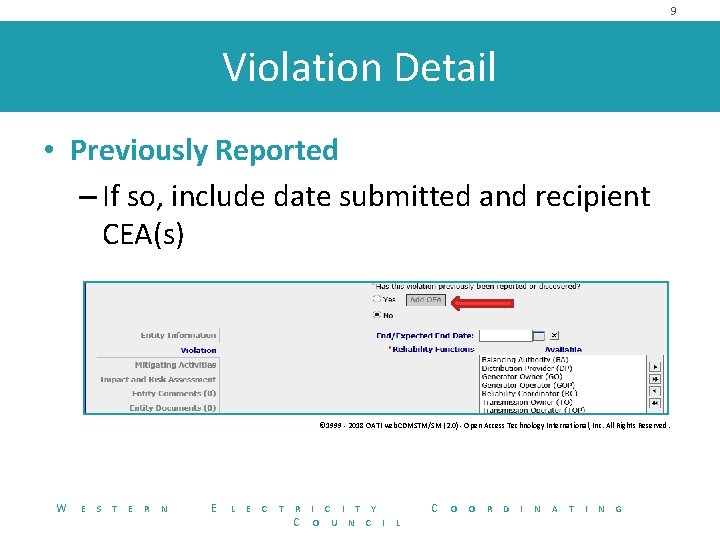
9 Violation Detail • Previously Reported – If so, include date submitted and recipient CEA(s) © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

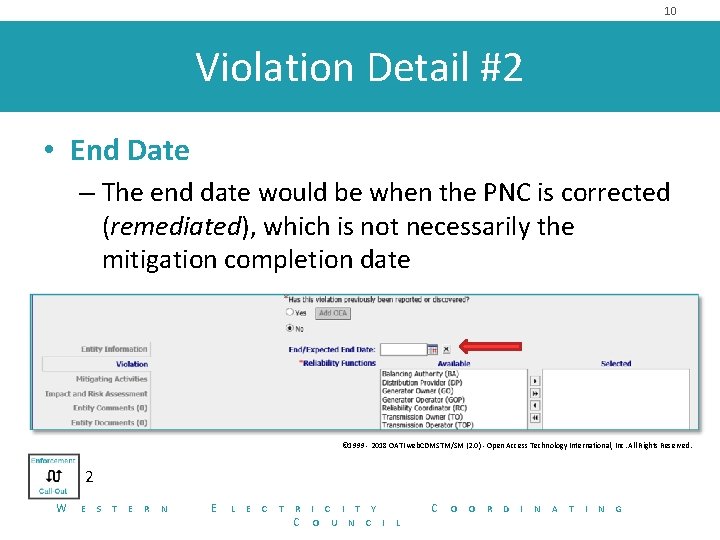
10 Violation Detail #2 • End Date – The end date would be when the PNC is corrected (remediated), which is not necessarily the mitigation completion date © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. 2 W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

11 Remediation and Mitigation • Remediation: noncompliance is back to compliance • Mitigation: remediation + address cause(s) + future prevention W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

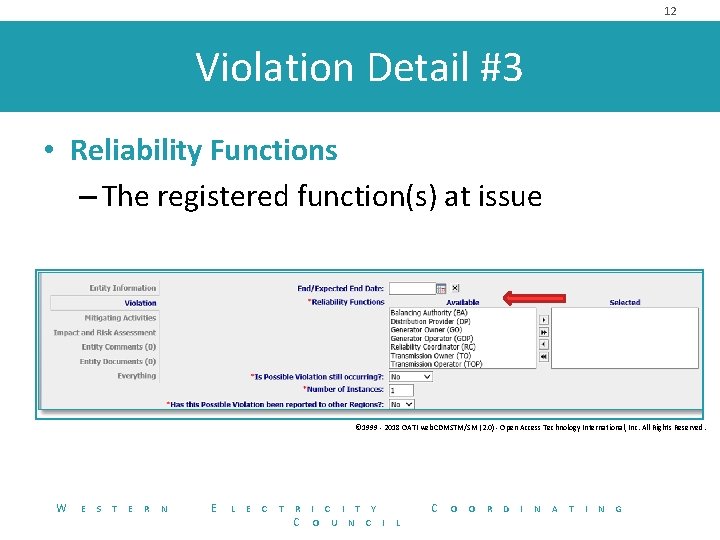
12 Violation Detail #3 • Reliability Functions – The registered function(s) at issue © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

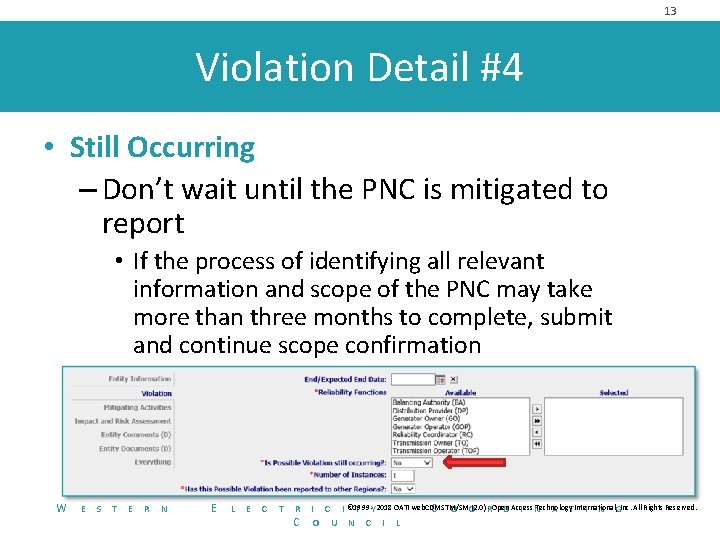
13 Violation Detail #4 • Still Occurring – Don’t wait until the PNC is mitigated to report • If the process of identifying all relevant information and scope of the PNC may take more than three months to complete, submit and continue scope confirmation W E S T E R N E L E C T R C Technology I C I © 1999 T -Y 2018 OATI web. CDMSTM/SM C O O(2. 0) R- Open D Access I N A T International, I N GInc. All Rights Reserved. O U N C I L

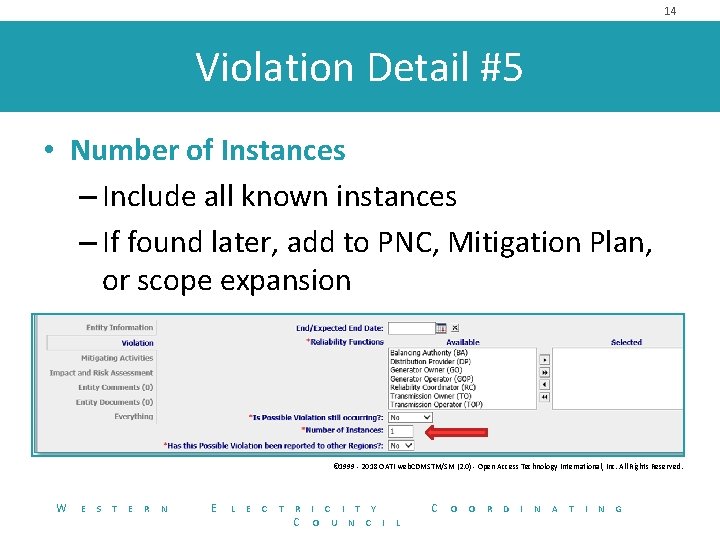
14 Violation Detail #5 • Number of Instances – Include all known instances – If found later, add to PNC, Mitigation Plan, or scope expansion © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

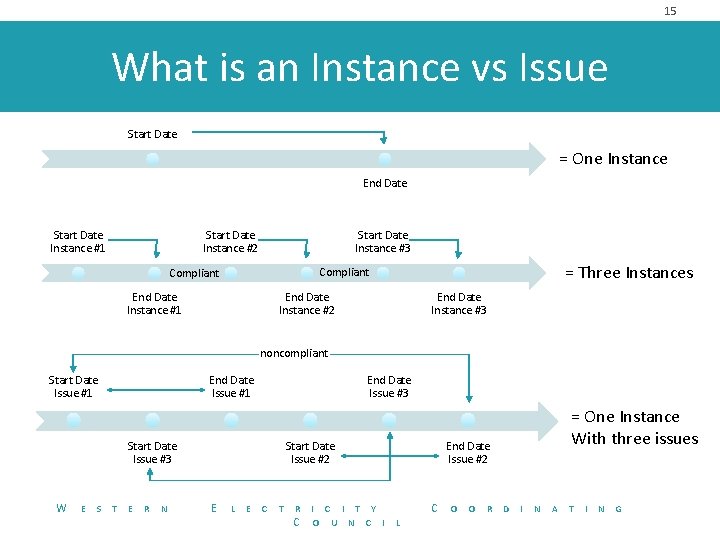
15 What is an Instance vs Issue Start Date = One Instance End Date Start Date Instance #1 Start Date Instance #2 Start Date Instance #3 = Three Instances Compliant End Date Instance #1 End Date Instance #2 End Date Instance #3 noncompliant Start Date Issue #1 End Date Issue #3 Start Date Issue #3 W E S T E R N Start Date Issue #2 E L E C T R C I T Y O U N C I = One Instance With three issues End Date Issue #2 C L O O R D I N A T I N G

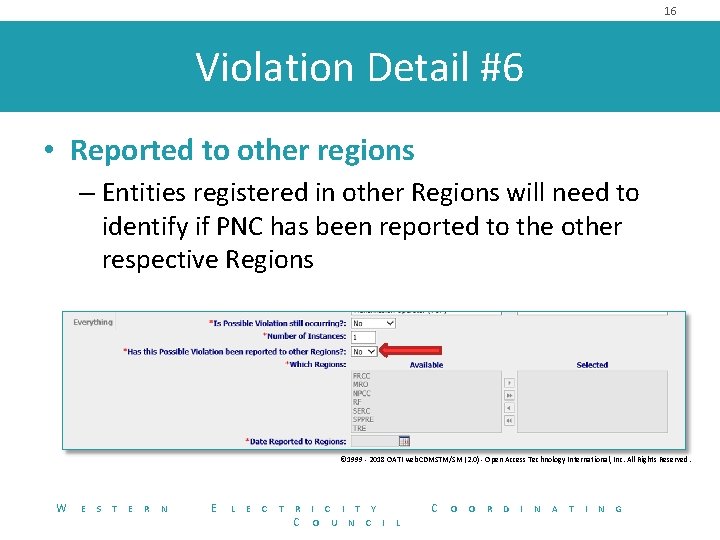
16 Violation Detail #6 • Reported to other regions – Entities registered in other Regions will need to identify if PNC has been reported to the other respective Regions © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

17 Violation Detail #7 • Detailed Description and Cause What happened Where it happened Start / end dates of each issue, or instance, with explanation System conditions at time of the issue Whether the PNC was isolated or a systemic/general control failure potentially impacting multiple processes/systems – – – © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

18 Violation Detail #8 • Detailed Description and Cause, continued Scope or Extent of the PNC – Number of device(s), type(s), and function(s) – What could be impacted: size of transmission, ties, and part of WECC path, generation, load – Detail how scope was confirmed to ensure no other devices were potentially noncompliant © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

19 Violation Detail #9 • Detailed Description and Cause, continued Causes of the PNC – All PNC must have cause(s) identified prior to final disposition • Identify and include all contributing causes to effectively correct the issue and prevent recurrence © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

20 5 Whys for Root Cause Tree touched the line Vegetation not managed Insufficient inspection Visual inspection failed to identify encroachment Inadequate Quality Assurance process Management had not identified the need Management monitoring of activities did not identify problem

21 Violation Detail #10 • Internal Controls – Analysis involves identifying the scope of the issue in conjunction with internal controls (preventive, detective, and corrective), or redundancies (backups or other entities performing the same function) in place at the time of PNC W E S T E R N E © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. L E C T R C I T Y O U N C I C L O O R D I N A T I N G

22 Mitigating Activities • Description and Preventative Measures – Include a comprehensive description of any mitigating activities and whether they have concluded or are still in progress • The mitigating activities must correct (remediate) the root cause of the issue, address the contributing cause(s), and prevent recurrence W E S T E R N E L E C T R C © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. I C I T Y O U N C I C L O O R D I N A T I N G

23 Impact & Risk Assessment • Potential & Actual Impact to BPS – After assessing risk, select the appropriate impact level W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

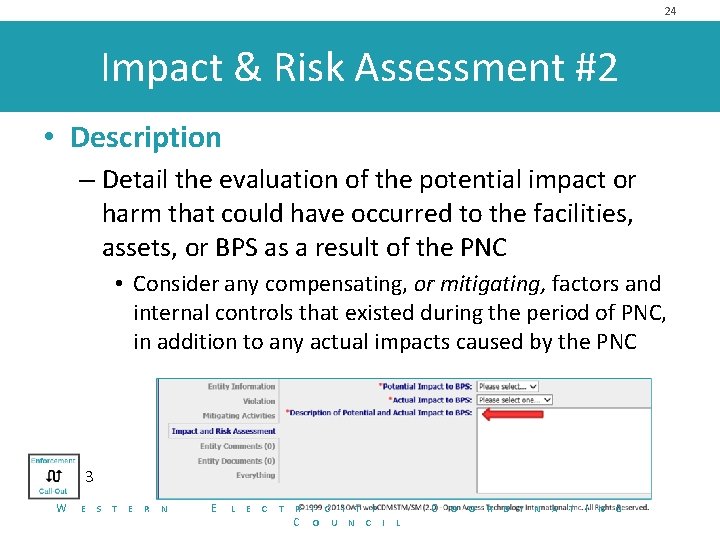
24 Impact & Risk Assessment #2 • Description – Detail the evaluation of the potential impact or harm that could have occurred to the facilities, assets, or BPS as a result of the PNC • Consider any compensating, or mitigating, factors and internal controls that existed during the period of PNC, in addition to any actual impacts caused by the PNC 3 W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

25 Impact & Risk Assessment #3 • Risk Assessment – Provide details about what risks were associated with the PNC at the time it took place • Time of elevated risk • Size and location of the facilities – Detail how the PNC affected the system overall – Risk assessments should be specific to the entity, the BPS, and existing controls mitigating the risk © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved.

26 Impact & Risk Assessment #4 • Additional Entity Comments (Optional) – Important, relevant information • Related self-reports • Referenced in Reliability Standard Audit Worksheet • “Spoke to WECC…” © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

27 Self-Reports, End Validated Start/End Dates Detailed Description of What/Where/How Strong Scope Validation Defined Root and Contributing Cause(s) Impact and Risk Assessed W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

28 Quality Mitigation Plans While the benefits of registered entities submitting more thorough and timely Mitigation Plans to CEAs include faster determination of how the CEA should process an issue of PNC and faster processing times, it is important for the registered entity to perform the actions necessary to correct the issue as soon as possible in order to protect reliability of the BPS. (NERC Guide) W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

29 Mitigation Plan vs. Mitigating Activities • The formal Mitigation Plan is a documented plan that has specific timing considerations • Mitigating activities do not require formal milestones or duplicative descriptions of discovery, contributing cause, or risk • Both must (1) correct a PNC, (2) address the cause(s), and (3) prevent recurrence W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

30 Mitigation Plan Detail • Contact Detail – Shall be a person (i) responsible for filing the Mitigation Plan, (ii) technically knowledgeable regarding the Mitigation Plan, and (iii) authorized and competent to respond to questions regarding the status of the Mitigation Plan W E S T E R N E L E C T R C © 1999 International, Inc. All I C I - 2018 T YOATI web. CDMSTM/SM C (2. 0) O -OOpen. RAccess D Technology I N A T I N GRights Reserved. O U N C I L

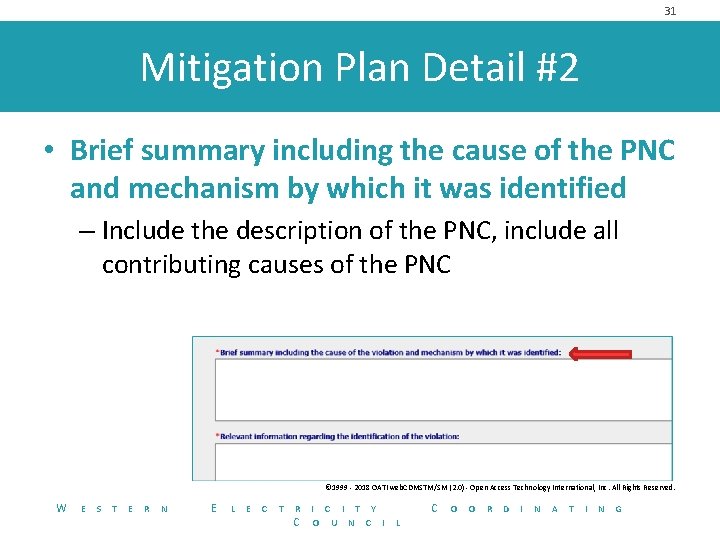
31 Mitigation Plan Detail #2 • Brief summary including the cause of the PNC and mechanism by which it was identified – Include the description of the PNC, include all contributing causes of the PNC © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

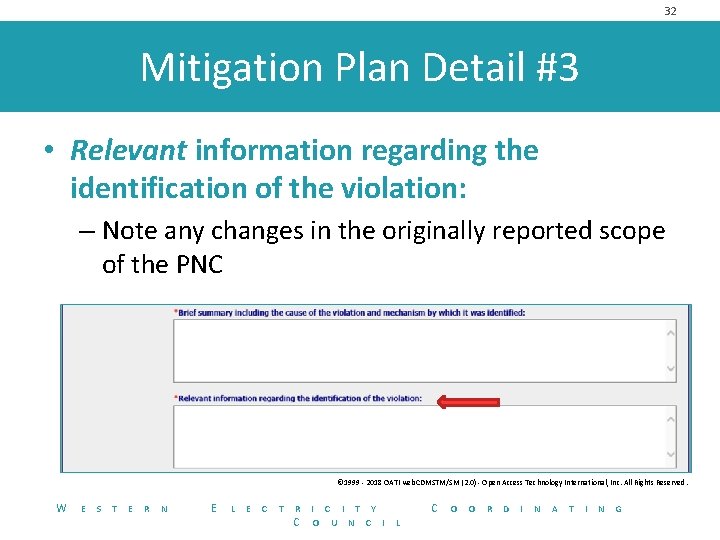
32 Mitigation Plan Detail #3 • Relevant information regarding the identification of the violation: – Note any changes in the originally reported scope of the PNC © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

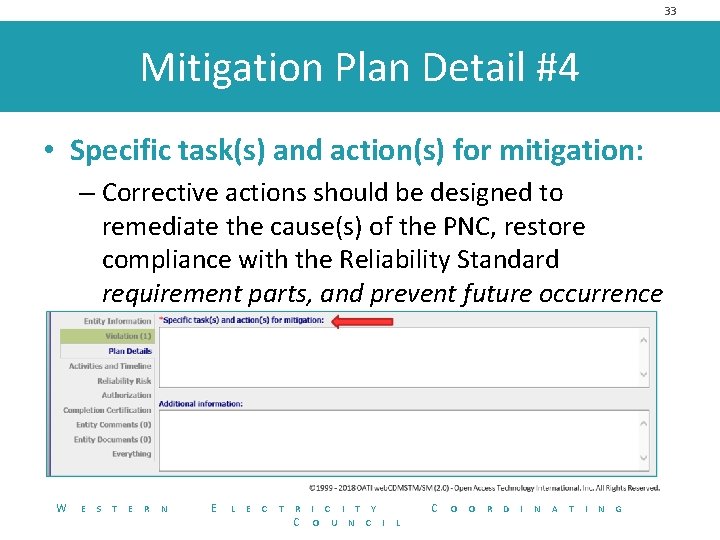
33 Mitigation Plan Detail #4 • Specific task(s) and action(s) for mitigation: – Corrective actions should be designed to remediate the cause(s) of the PNC, restore compliance with the Reliability Standard requirement parts, and prevent future occurrence W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

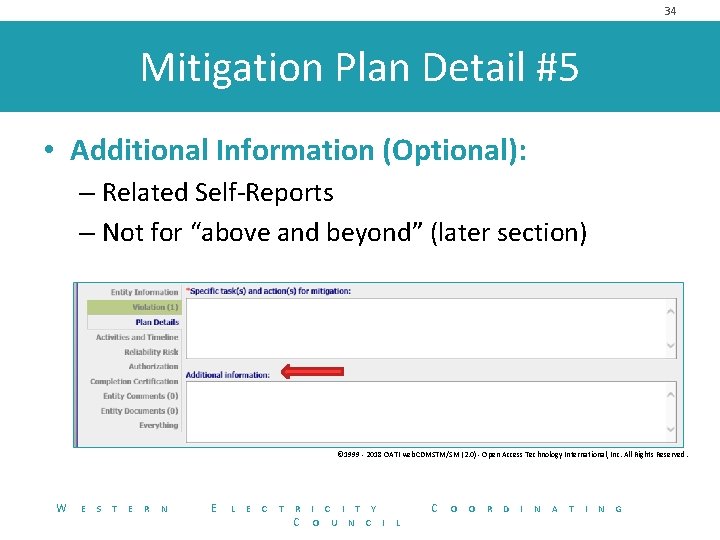
34 Mitigation Plan Detail #5 • Additional Information (Optional): – Related Self-Reports – Not for “above and beyond” (later section) © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

35 Mitigation Plan Detail #6 • Proposed Mitigation Plan Completion Date: – The expected date when all actions in the Mitigation Plan, including any milestones, will be completed W E S T E R N E © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. L E C T R C I T Y O U N C I C L O O R D I N A T I N G

36 Mitigation Plan Detail #7 • Milestone Activity: – Milestones are required for Mitigation Plans when a proposed completion date is more than three months from submission W E S T E R N E L E C T R C © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. I C I T Y O U N C I C L O O R D I N A T I N G

37 Mitigation Plan Detail #8 • (Reliability Risk) while the Mitigation Plan is being implemented: – Must include steps that will reduce or eliminate risk to the BPS while mitigation (remediation) is being implemented. The risk reduction steps must be specific for the risks identified 4 © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved.

38 Mitigation Plan Detail #9 • (Prevention) Describe how successful completion of the plan will prevent: – Detail how the successful completion of the mitigation minimizes the probability that the registered entity will violate the same or similar Reliability Standards again with the same cause(s). © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved.

39 Mitigation Plan Detail #10 • Describe any action that may be taken or planned beyond that listed in the mitigation plan: – Include additional steps that will reduce or eliminate risk to the BPS 5 W E S T E R N E L E C T R C I C © 1999 I T- 2018 Y OATI web. CDMSTM/SM C O(2. 0)O- Open R Access D Technology I N A International, T I NInc. GAll Rights Reserved. O U N C I L

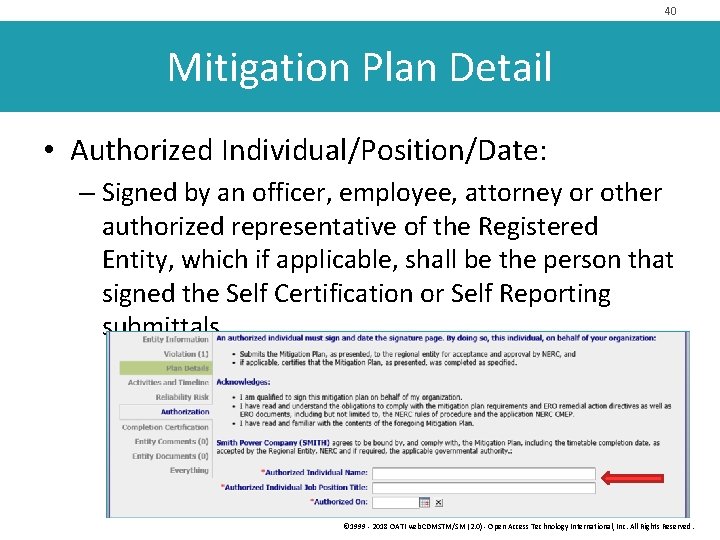
40 Mitigation Plan Detail • Authorized Individual/Position/Date: – Signed by an officer, employee, attorney or other authorized representative of the Registered Entity, which if applicable, shall be the person that signed the Self Certification or Self Reporting submittals © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved.

41 Mitigation Plans, End Mitigation Plan or Activities must correct a PNC, address the cause(s), and prevent reoccurrence. Ensure completion dates for all actions in the Mitigation Plan or activities, including any milestones. Include steps to reduce/eliminate risk while mitigation is implemented Address future prevention of the cause(s) W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

42 Completed Mitigation Plan Detail • Mitigation Completed On: – Actual completion date as demonstrated by evidence © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

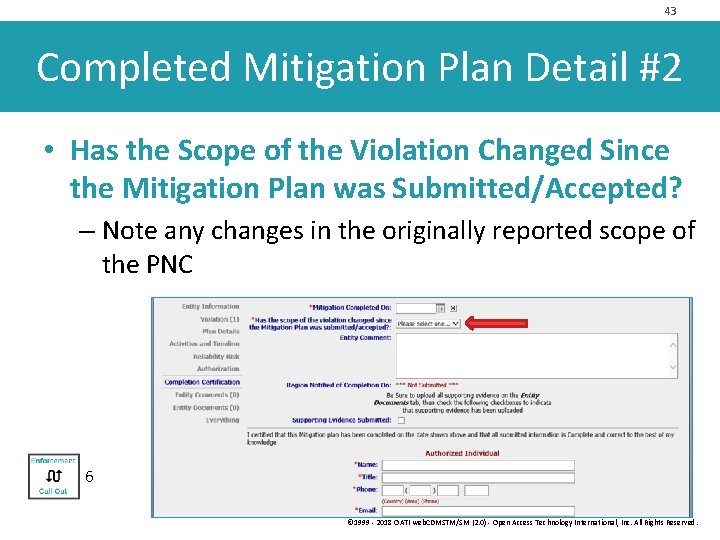
43 Completed Mitigation Plan Detail #2 • Has the Scope of the Violation Changed Since the Mitigation Plan was Submitted/Accepted? – Note any changes in the originally reported scope of the PNC 6 © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved.

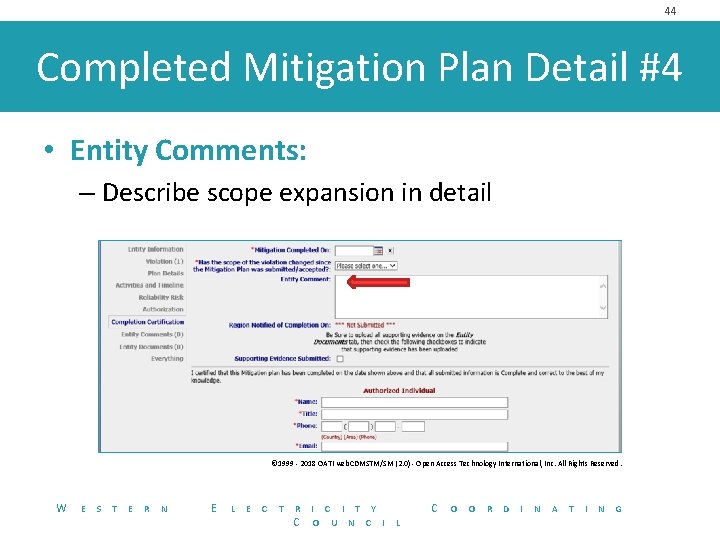
44 Completed Mitigation Plan Detail #4 • Entity Comments: – Describe scope expansion in detail © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

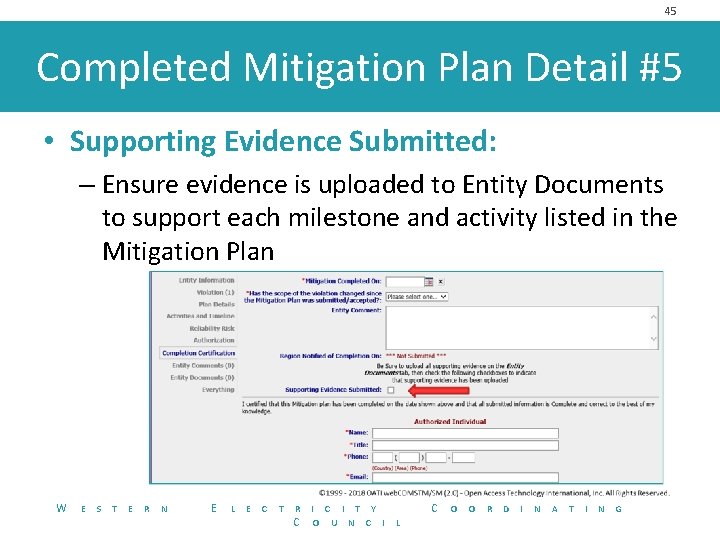
45 Completed Mitigation Plan Detail #5 • Supporting Evidence Submitted: – Ensure evidence is uploaded to Entity Documents to support each milestone and activity listed in the Mitigation Plan W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

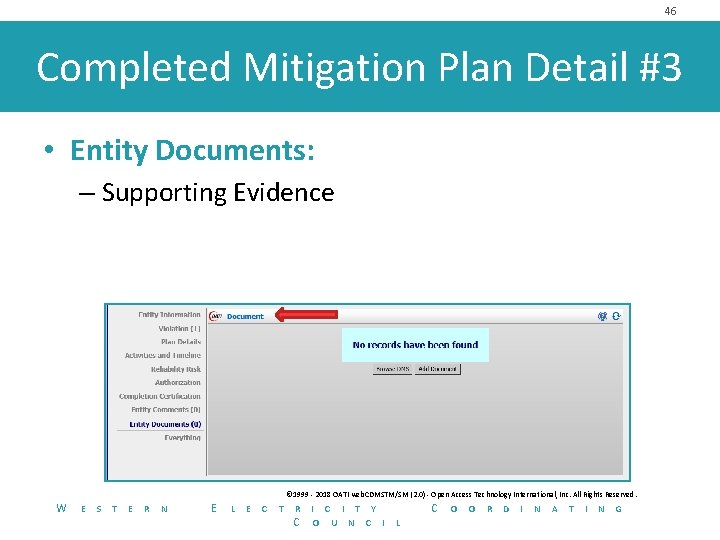
46 Completed Mitigation Plan Detail #3 • Entity Documents: – Supporting Evidence © 1999 - 2018 OATI web. CDMSTM/SM (2. 0) - Open Access Technology International, Inc. All Rights Reserved. W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

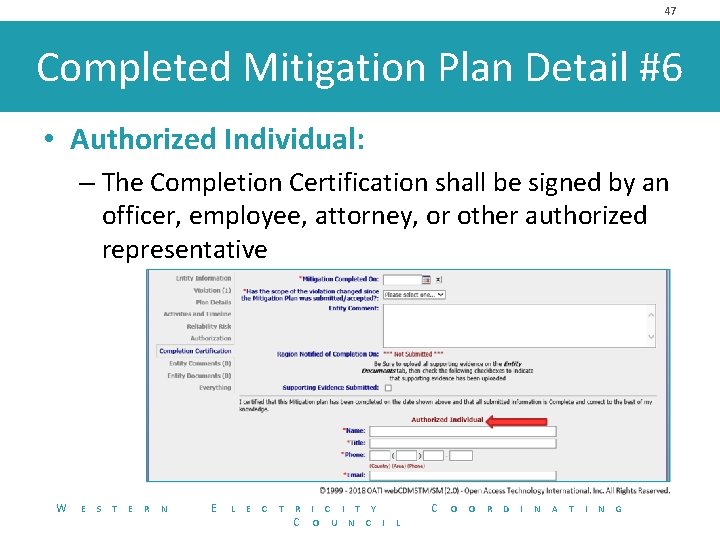
47 Completed Mitigation Plan Detail #6 • Authorized Individual: – The Completion Certification shall be signed by an officer, employee, attorney, or other authorized representative W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

48 Completed Mitigation Plans, End Verify scope Provide evidence for each mitigating milestone/action W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

49 Contact Information Scott Brooksby: Trent Wilson: Debra Horvath: W E S T E R N E L E C T R C I T Y O U N C I 801 -883 -6876 801 -819 -7610 C L O O R D I N A T I N G

50 Overall Review • Getting it right the first time – Saves time and resources – Lets you focus on mitigation – Improves WECC understanding, affecting ultimate disposition • Utilize the NERC Guide and the Cheat Sheet next time you submit a Self-Report, Mitigation Plan, or Completed Mitigation Plan • Contact – RAM@wecc. biz – enforcement@wecc. biz W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G

51 Resource Material W E S T E R N E L E C T R C I T Y O U N C I C L O O R D I N A T I N G