OWASP TOP 10 A 1 Injection A 2













![SQL Injection : ﺟﺰﺋﻴﺎﺕ ﺑﻴﺸﺘﺮ ﻛﺪ ﺑﺮﻧﺎﻣﻪ $user= $_POST [“user"]; $pass= $_POST [“pass"]; $query SQL Injection : ﺟﺰﺋﻴﺎﺕ ﺑﻴﺸﺘﺮ ﻛﺪ ﺑﺮﻧﺎﻣﻪ $user= $_POST [“user"]; $pass= $_POST [“pass"]; $query](https://slidetodoc.com/presentation_image_h/11ec2685dbd24d6faea3bc9aa1269cd4/image-20.jpg)







- Slides: 34

















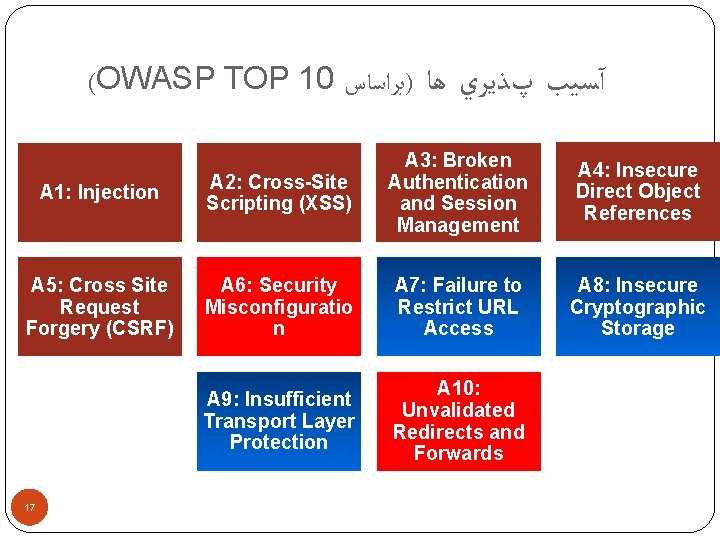
(OWASP TOP 10 )ﺑﺮﺍﺳﺎﺱ آﺴﻴﺐ پﺬﻳﺮﻱ ﻫﺎ A 1: Injection A 2: Cross-Site Scripting (XSS) A 3: Broken Authentication and Session Management A 4: Insecure Direct Object References A 5: Cross Site Request Forgery (CSRF) A 6: Security Misconfiguratio n A 7: Failure to Restrict URL Access A 8: Insecure Cryptographic Storage A 9: Insufficient Transport Layer Protection A 10: Unvalidated Redirects and Forwards 17

A 1 – Injection ﻣﻘﺪﻣﻪ Injection means… • Tricking an application into including unintended commands in the data sent to an interpreter Interpreters… • Take strings and interpret them as commands • SQL, OS Shell, LDAP, XPath, Hibernate, etc… SQL injection is still quite common • Many applications still susceptible (really don’t know why) • Even though it’s usually very simple to avoid Typical Impact • Usually severe. Entire database can usually be read or modified • May also allow full database schema, or account access, or even OS level access

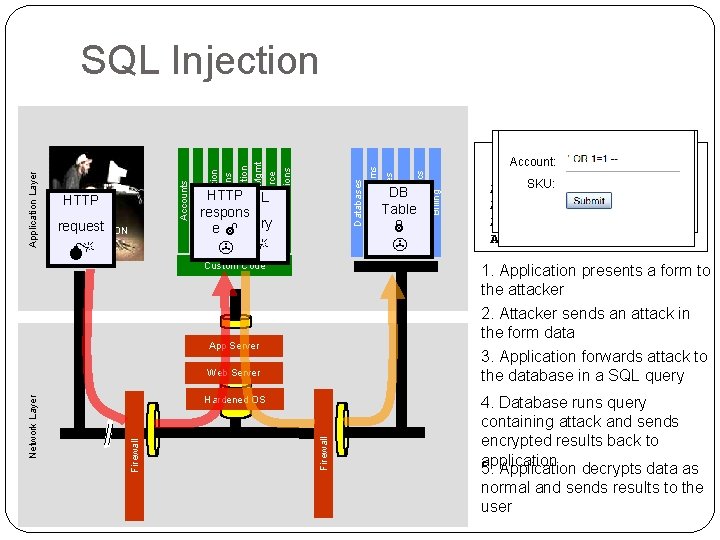
ATTACK Custom Code Billing Acct: 5424 -9383 -2039 -4029 Acct: 4128 -0004 -1234 -0293 3. Application forwards attack to the database in a SQL query Web Server Firewall Hardened OS Firewall DB Table "SELECT * FROM Account Summary Account: accounts WHERE SKU: acct=‘’ OR 1=1 -Acct: 5424 -6066 -2134 -4334 Acct: 4128 -7574 -3921 -0192 ’" 1. Application presents a form to the attacker 2. Attacker sends an attack in the form data App Server Network Layer Human Resrcs Directories request APPLICATION Web Services HTTP SQL respons e query HTTP Legacy Systems Databases Communication Knowledge Mgmt E-Commerce Bus. Functions Administration Transactions Accounts Finance Application Layer SQL Injection 4. Database runs query containing attack and sends encrypted results back to application 5. Application decrypts data as normal and sends results to the user
![SQL Injection ﺟﺰﺋﻴﺎﺕ ﺑﻴﺸﺘﺮ ﻛﺪ ﺑﺮﻧﺎﻣﻪ user POST user pass POST pass query SQL Injection : ﺟﺰﺋﻴﺎﺕ ﺑﻴﺸﺘﺮ ﻛﺪ ﺑﺮﻧﺎﻣﻪ $user= $_POST [“user"]; $pass= $_POST [“pass"]; $query](https://slidetodoc.com/presentation_image_h/11ec2685dbd24d6faea3bc9aa1269cd4/image-20.jpg)
SQL Injection : ﺟﺰﺋﻴﺎﺕ ﺑﻴﺸﺘﺮ ﻛﺪ ﺑﺮﻧﺎﻣﻪ $user= $_POST [“user"]; $pass= $_POST [“pass"]; $query = "select * from users where username = '". $user. "‘ AND password=‘“. $pass. ”’”; $result = mysql_query($query); 20

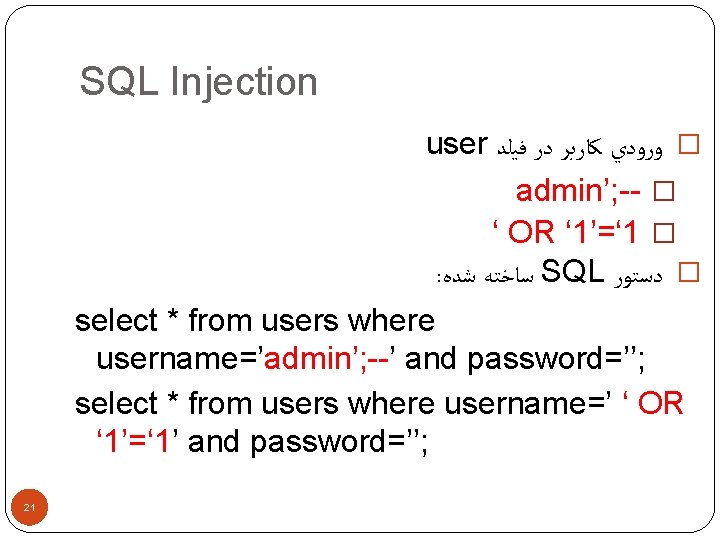
SQL Injection user � ﻭﺭﻭﺩﻱ ﻛﺎﺭﺑﺮ ﺩﺭ ﻓﻴﻠﺪ admin’; -- � ‘ OR ‘ 1’=‘ 1 � : ﺳﺎﺧﺘﻪ ﺷﺪﻩ SQL � ﺩﺳﺘﻮﺭ select * from users where username=’admin’; --’ and password=’’; select * from users where username=’ ‘ OR ‘ 1’=‘ 1’ and password=’’; 21




ﻣﻨﺒﻊ ﺑﺮﺍﻱ ﻣﻄﺎﻟﻌﻪ ﺑﻴﺸﺘﺮ �SQL Injection Attacks and Defense �Justin Clarke �SYNGRESS �Cheatsheet �http: //www. owasp. org/index. php/SQL_Inj ection_Prevention_Cheat_Sheet �Search for: �Oracle SQL Injection Cheatsheet �… �Guidelines from Microsoft, Oracle, … 25

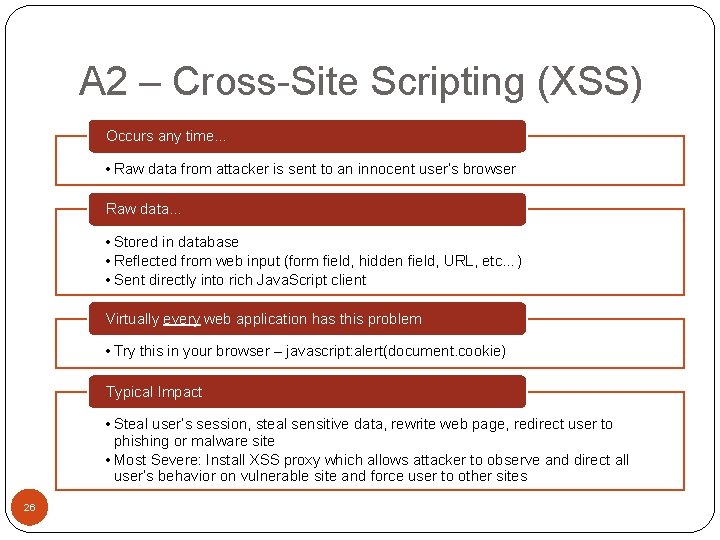
A 2 – Cross-Site Scripting (XSS) Occurs any time… • Raw data from attacker is sent to an innocent user’s browser Raw data… • Stored in database • Reflected from web input (form field, hidden field, URL, etc…) • Sent directly into rich Java. Script client Virtually every web application has this problem • Try this in your browser – javascript: alert(document. cookie) Typical Impact • Steal user’s session, steal sensitive data, rewrite web page, redirect user to phishing or malware site • Most Severe: Install XSS proxy which allows attacker to observe and direct all user’s behavior on vulnerable site and force user to other sites 26

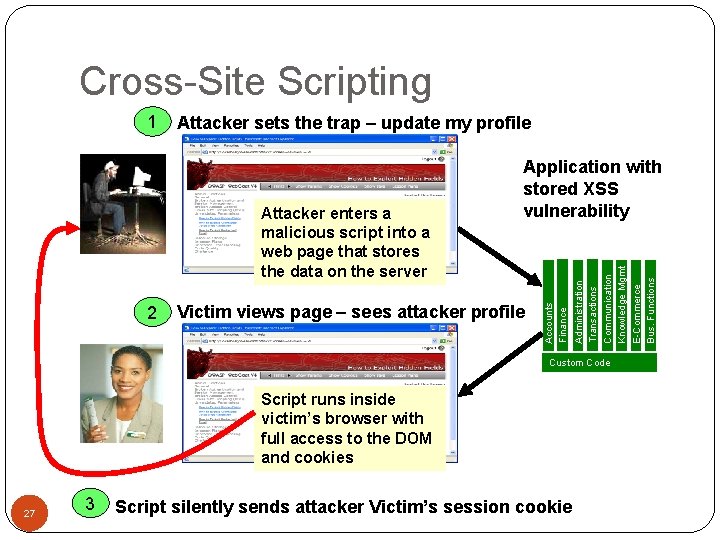
Cross-Site Scripting Attacker sets the trap – update my profile Victim views page – sees attacker profile Communication Knowledge Mgmt E-Commerce Bus. Functions 2 Administration Transactions Attacker enters a malicious script into a web page that stores the data on the server Application with stored XSS vulnerability Accounts Finance 1 Custom Code Script runs inside victim’s browser with full access to the DOM and cookies 27 3 Script silently sends attacker Victim’s session cookie

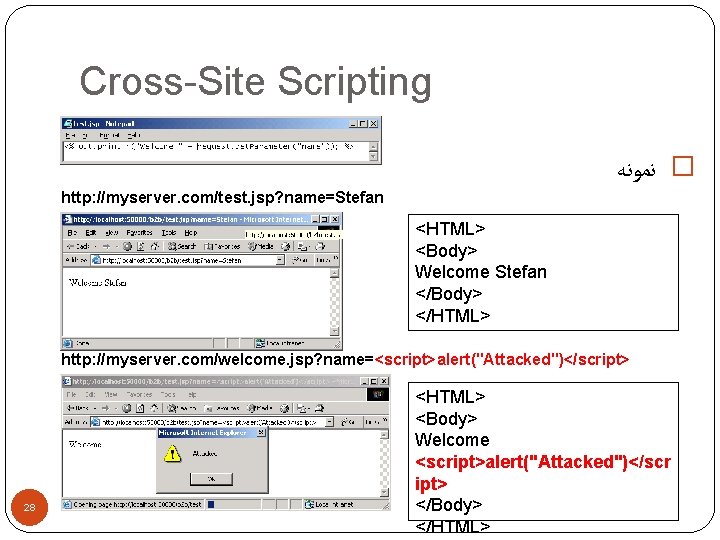
Cross-Site Scripting � ﻧﻤﻮﻧﻪ http: //myserver. com/test. jsp? name=Stefan <HTML> <Body> Welcome Stefan </Body> </HTML> http: //myserver. com/welcome. jsp? name=<script>alert("Attacked")</script> 28 <HTML> <Body> Welcome <script>alert("Attacked")</scr ipt> </Body> </HTML>

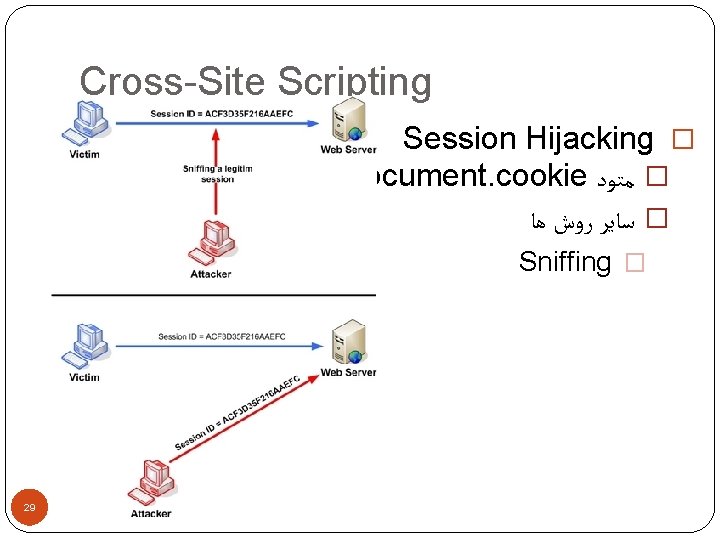
Cross-Site Scripting Session Hijacking � document. cookie � ﻣﺘﻮﺩ � ﺳﺎﻳﺮ ﺭﻭﺵ ﻫﺎ Sniffing � 29





ﺍﺑﺰﺍﺭﻫﺎﻱ ﺗﺴﺖ �Nessus (O. S. and Network Level bugs) �Retina (O. S. and Network Level bugs) �Acunetix (Web Application Bugs) �Web Inspect (Web Application Bugs) 34