Orphan Source Search Training Radioactive Source and Recovered



































- Slides: 44

Orphan Source Search Training Radioactive Source (and Recovered Orphan Source) Security

Overview • Radiation safety is about protecting people from radiation sources and • Radioactive source security is about protecting sources from people who have malicious intent Radioactive Source (and Recovered Orphan Source) Security 2

Overview • Nuclear and orphan source security • The IAEA activities: – the Code of Conduct – The Nuclear Security Series guidance – The Incident and Trafficking Database – Security measures for recovered orphan sources • Examples of security measures Radioactive Source (and Recovered Orphan Source) Security 3

What are the general concerns of nuclear security? Nuclear explosive device – theft of nuclear weapon – theft of nuclear material Radiological dispersal device – theft of radioactive material/source or use of abandoned radioactive sources. Sabotage – Facility/transport to cause dispersal of radioactivity Radioactive Source (and Recovered Orphan Source) Security 4

Regarding orphan source security • The concern is that an orphan source could be stolen and used as a radiological dispersal device OR • Used to irradiate members of the public (less likely) Radioactive Source (and Recovered Orphan Source) Security 5

The IAEA and radioactive source security • Source security has always been important to the IAEA and never more so than after the 9/11 attacks • One aspect of the IAEA response was the Code of Conduct on the Safety and Security of Radioactive Sources Radioactive Source (and Recovered Orphan Source) Security 7

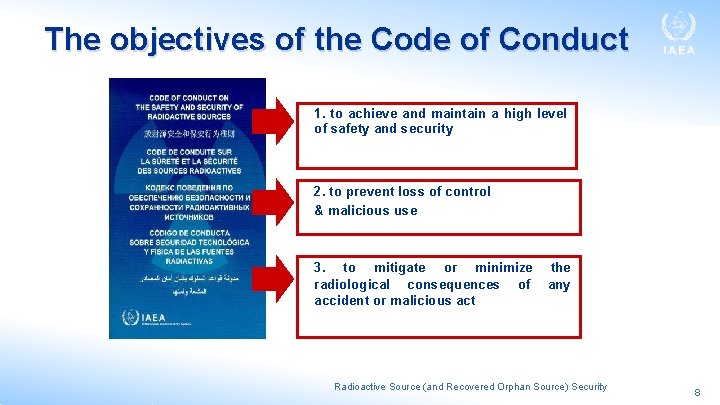
The objectives of the Code of Conduct 1. to achieve and maintain a high level of safety and security 2. to prevent loss of control & malicious use 3. to mitigate or minimize radiological consequences of accident or malicious act the any Radioactive Source (and Recovered Orphan Source) Security 8

The Code of Conduct • • • Designed for national governments Provides guidance on legislation and regulations for the security of radioactive sources Applies to “…all radioactive sources that may pose a significant risk to individuals, society, and the environment…” – These sources are listed in Annex I of the Code – They are Category 1, 2, and 3 “dangerous” sources as determined by RS-G-1. 9 Radioactive Source (and Recovered Orphan Source) Security 9

Commitment to the Code • The Code of Conduct is not legally binding, but most of the IAEA Member States have made a political commitment to work toward implementing of all the provisions of the Code of Conduct Radioactive Source (and Recovered Orphan Source) Security 10

Key Security Provisions of the Code • • Effective national legislative and regulatory system of control Regulatory body to establish and enforce security requirements Prime responsibility for security on the operator Requirement for license, including a security plan Security culture promotion National registry of sources Regular inventory controls by operator Radioactive Source (and Recovered Orphan Source) Security 11

Key Security Provisions of the Code (con’t) • Threat definition and vulnerability assessment • Security measures to deter, detect, and delay theft or removal of sources • Verification of the security of radioactive sources through – Security assessments – Monitoring and verifying compliance • Maintaining appropriate records • Prompt reporting by the operator of a loss of control • Safe management and secure protection of disused sources Radioactive Source (and Recovered Orphan Source) Security 12

In addition to the Code of Conduct, the IAEA has developed several guidance documents that pertain to the security of radioactive sources Radioactive Source (and Recovered Orphan Source) Security 13

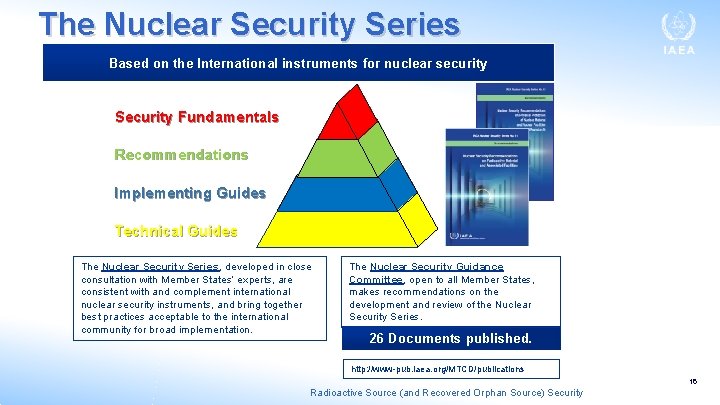
These guidance documents form part of the IAEA Nuclear Security Series Radioactive Source (and Recovered Orphan Source) Security 14

Nuclear Security Series (continued) Radioactive Source (and Recovered Orphan Source) Security 15

The Nuclear Security Series Based on the International instruments for nuclear security Security Fundamentals Recommendations Implementing Guides Technical Guides The Nuclear Security Series, developed in close consultation with Member States’ experts, are consistent with and complement international nuclear security instruments, and bring together best practices acceptable to the international community for broad implementation. The Nuclear Security Guidance Committee, open to all Member States, makes recommendations on the development and review of the Nuclear Security Series. 26 Documents published. http: //www-pub. iaea. org/MTCD/publications 16 Radioactive Source (and Recovered Orphan Source) Security

Nuclear Security Series continued Ø Fundamentals (PRINCIPLES) – Objectives and principles – Essentials from international instruments Ø Recommendations (WHAT) – General approaches, actions, concepts and strategies – Applications of Fundamentals Ø Implementing Guides (HOW) – Ways and means on how Recommendations are to be applied and implemented at systems level Ø Technical Guidance (GUIDANCE) – Reference Manuals, Training Guides, Service Guides Radioactive Source (and Recovered Orphan Source) Security 17

Nuclear Security Series Fundamentals (#20) Ø Purpose - overall objectives and essential elements Ø Intended for a broad audience - national policy makers, legislative, competent authorities, institutions, and individuals Ø Applies to all radioactive material Ø Aims to prevent criminal and intentional unauthorized acts involving radioactive material Radioactive Source (and Recovered Orphan Source) Security 18

Nuclear Security Series Recommendations (#14) Ø Provides guidance to States and competent authorities on establishing a nuclear security regime for radioactive material, including radioactive sources Ø Complements NSS 20 and the Code of Conduct Radioactive Source (and Recovered Orphan Source) Security 19

Nuclear Security Series No. 14 describes the elements of a States Nuclear Security Regime • State Responsibility • Assignment of (nuclear) security responsibilities • Legislative and Regulatory Framework • State • Regulatory Body • Operator, shipper and/or carrier • International Cooperation and Assistance • Identification and Assessment of Threats Radioactive Source (and Recovered Orphan Source) Security 20

Elements of a States Nuclear Security Regime (#14) • Risk based nuclear security systems and measures • Risk Management • Interfaces with other safety systems • Sustaining the nuclear security regime • Planning and preparedness for and response to an event • Import and Export of radioactive material • Detection of nuclear security events 21 Radioactive Source (and Recovered Orphan Source) Security

Nuclear Security Series No. 11 • IAEA Security of Radioactive Sources Implementing Guide (Nuclear Security Series No. 11) provides guidance to States on developing regulations for the security of radioactive sources • This recommended approach is summarized on the following slide Current version is 2009. A revised version is expected Radioactive Source (and Recovered Orphan Source) Security 22

In addition to the Code of Conduct and the Nuclear Security Series of Documents, the IAEA also maintains an Incident and Trafficking Database (ITDB) Radioactive Source (and Recovered Orphan Source) Security 23

The ITDB • The ITDB information is reported by participating States, on incidents involving illicit trafficking and other unauthorized activities involving nuclear and other radioactive materials. • This information is disseminated through the IAEA to participating States and certain international organizations. • Reporting to the ITDB is voluntary. • As of 31 December 2017, 136 States were participating in the ITDB programme • It incorporates incidents in which nuclear and other radioactive material is out of regulatory control. Radioactive Source (and Recovered Orphan Source) Security 24

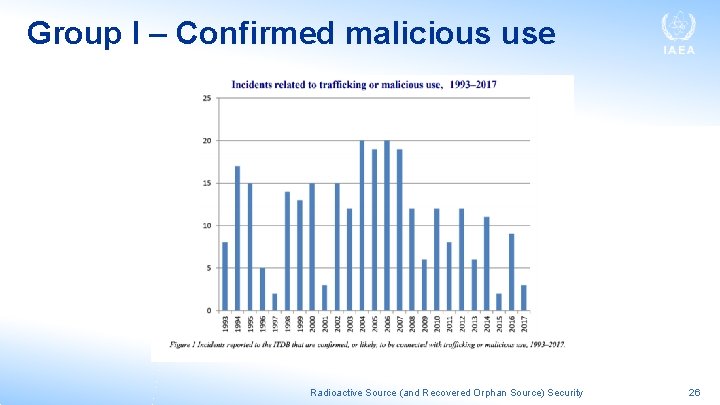
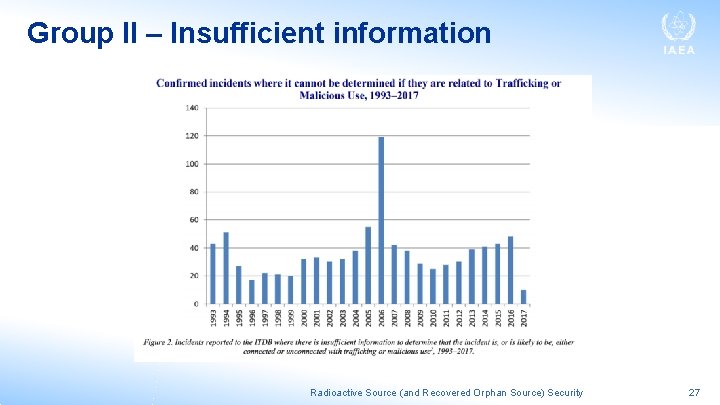
As of 31 December 2017, the ITDB contained a total of 3235 confirmed incidents reported by participating States since 1993 • Of these 3235 confirmed incidents there are 278 incidents that involved a confirmed or likely act of trafficking or malicious use (Group I), 913 incidents for which there is insufficient information to determine if it is related to trafficking or malicious use (Group II) and 2044 incidents that are not related to trafficking or malicious use (Group III). Radioactive Source (and Recovered Orphan Source) Security 25

Group I – Confirmed malicious use Radioactive Source (and Recovered Orphan Source) Security 26

Group II – Insufficient information Radioactive Source (and Recovered Orphan Source) Security 27

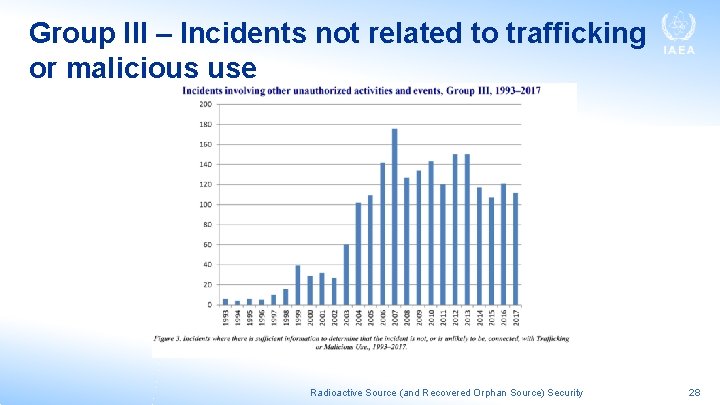
Group III – Incidents not related to trafficking or malicious use Radioactive Source (and Recovered Orphan Source) Security 28

Most orphan source discoveries would be Group III • The majority of incidents in Group III fall into one of three categories: the unauthorized disposal (e. g. radioactive sources entering the scrap metal industry); unauthorized shipment (e. g. scrap metals contaminated with radioactive material being shipped across international borders); or the discovery of radioactive material (e. g. uncontrolled radioactive sources). Radioactive Source (and Recovered Orphan Source) Security 29

For more information about the ITDB • https: //www. iaea. org/sites/default/files/18/12/itdbfactsheet-2018. pdf Radioactive Source (and Recovered Orphan Source) Security 30

So what aspects of nuclear security are important to orphan source search and recovery? Radioactive Source (and Recovered Orphan Source) Security 31

Security measures for recovered orphan sources should be considered • For transport • For storage • “Security of Radioactive Sources” (SS # 11) provides the guidance Radioactive Source (and Recovered Orphan Source) Security 32

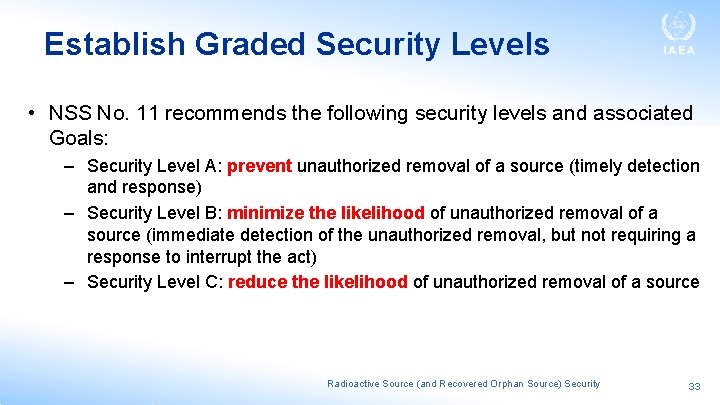
Establish Graded Security Levels • NSS No. 11 recommends the following security levels and associated Goals: – Security Level A: prevent unauthorized removal of a source (timely detection and response) – Security Level B: minimize the likelihood of unauthorized removal of a source (immediate detection of the unauthorized removal, but not requiring a response to interrupt the act) – Security Level C: reduce the likelihood of unauthorized removal of a source Radioactive Source (and Recovered Orphan Source) Security 33

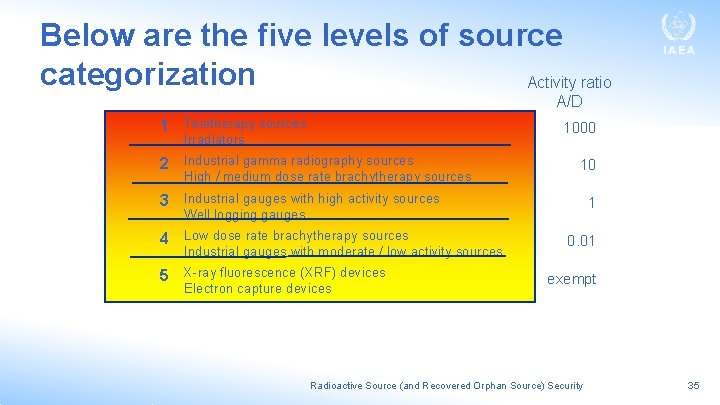
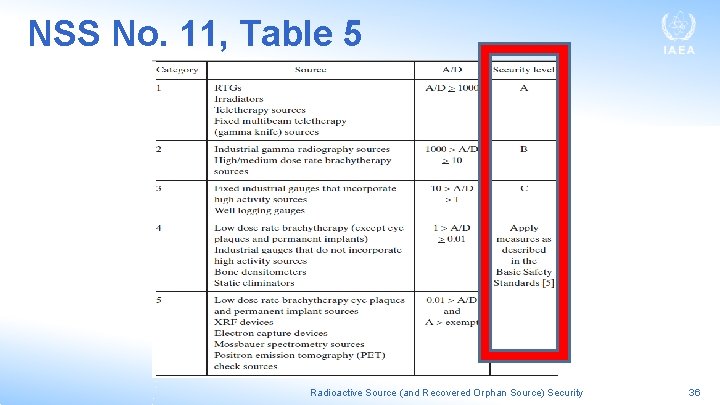
Specify the Security Level Applicable to Given Sources • The security level for a given source should correspond to the potential harm the source could cause if used in a malicious act • A starting point is the categorization system used in the Code of Conduct and presented previously • The Guide notes that as a default arrangement, the regulatory body could use these categories to assign the security level applicable to a given source, as set forth in Table 5 of NSS No. 11 Radioactive Source (and Recovered Orphan Source) Security 34

Below are the five levels of source categorization Activity ratio A/D 1 Teletherapy sources 1000 Irradiators 2 Industrial gamma radiography sources High / medium dose rate brachytherapy sources 10 3 Industrial gauges with high activity sources 1 Well logging gauges 4 Low dose rate brachytherapy sources Industrial gauges with moderate / low activity sources 5 X-ray fluorescence (XRF) devices Electron capture devices 0. 01 exempt Radioactive Source (and Recovered Orphan Source) Security 35

NSS No. 11, Table 5 Radioactive Source (and Recovered Orphan Source) Security 36

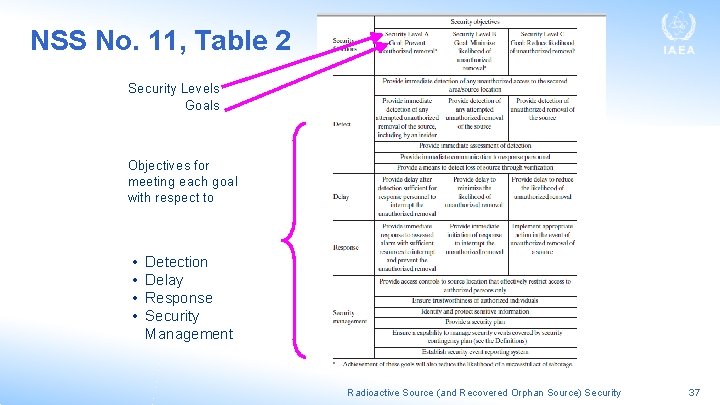
NSS No. 11, Table 2 Security Levels Goals Objectives for meeting each goal with respect to • • Detection Delay Response Security Management Radioactive Source (and Recovered Orphan Source) Security 37

For more information consult: • “Security of Radioactive Sources” (SS # 11) provides the guidance Radioactive Source (and Recovered Orphan Source) Security 38

So what are some examples of applicable security measures? Radioactive Source (and Recovered Orphan Source) Security 39

Administrative security measures include: • alarmed access points (e. g. with radiation detectors); • access control procedures; • key control procedures; • video cameras or personal surveillance; • records related to the management of sources; • source inventories Radioactive Source (and Recovered Orphan Source) Security 40

Technical security measures include: Appropriate technical measures include: • fences; • walls; • cages; • transport packaging; • locks and interlocks for doors (or access points); • locked, shielded containers. Radioactive Source (and Recovered Orphan Source) Security 41

Transport security measures include: • For Security Group A sources: • deterrence through the use of locked and sealed transport packages and the use of a dedicated, locked transport unit; • timely detection through radio communication between the personnel in the vehicle and a security office or organization; • an emergency plan Radioactive Source (and Recovered Orphan Source) Security 42

Transport security measures include: • For Security Group B and C sources: • for a mobile source, administrative controls such as personal surveillance should be rigorously maintained; • satisfy the performance requirements for security for the particular group; • include consideration of a communication link to allow timely response to incidents or potential threats. Radioactive Source (and Recovered Orphan Source) Security 43

Summary • Nuclear and orphan source security • The IAEA activities: – the Code of Conduct – The Nuclear Security Series guidance – The Incident and Trafficking Database – Security measures for recovered orphan sources • Examples of security measures Radioactive Source (and Recovered Orphan Source) Security 44

Thank you for your attention! Questions? Radioactive Source (and Recovered Orphan Source) Security 45