Orchestration Automation Is Your Network Ready for 10














- Slides: 43

Orchestration & Automation: Is Your Network Ready for 10 Billion Connections? John Malzahn – Host, Senior Manager, Cloud and Virtualization Solutions Marketing, Cisco Systems Boštjan Šuštar, Senior IT Architect, NIL Carl Moberg – Technical Director, Cisco Systems May 3, 2017

Today’s Presenters John Malzahn Carl Moberg Senior Manager, Cloud and Virtualization Solutions Marketing, Technology Director, Cloud and Virtualization Group, Cisco Systems Boštjan Šuštar Senior IT Architect NIL, Ltd © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 2

Agenda 1 Orchestration and Scaling Challenges Facing Service Providers 2 Cisco’s NSO Solution and Value Proposition 3 NSO’s Layered Services Architecture Innovation and Demo © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 3

Cisco NSO – Our Industry Leading Automation & Orchestration Platform © 2016 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 4

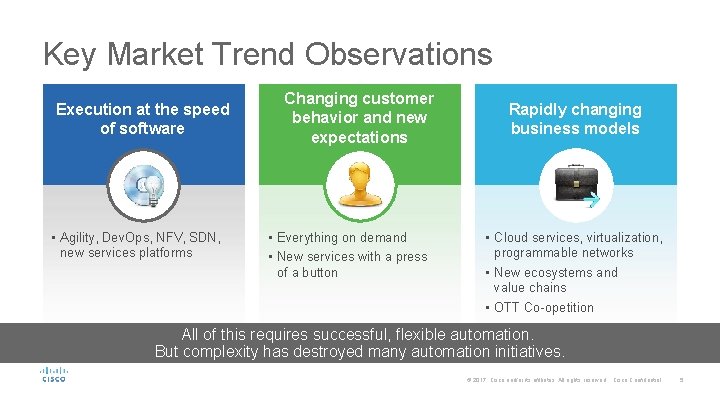
Key Market Trend Observations Execution at the speed of software • Agility, Dev. Ops, NFV, SDN, new services platforms Changing customer behavior and new expectations • Everything on demand • New services with a press of a button Rapidly changing business models • Cloud services, virtualization, programmable networks • New ecosystems and value chains • OTT Co-opetition All of this requires successful, flexible automation. But complexity has destroyed many automation initiatives. © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 5

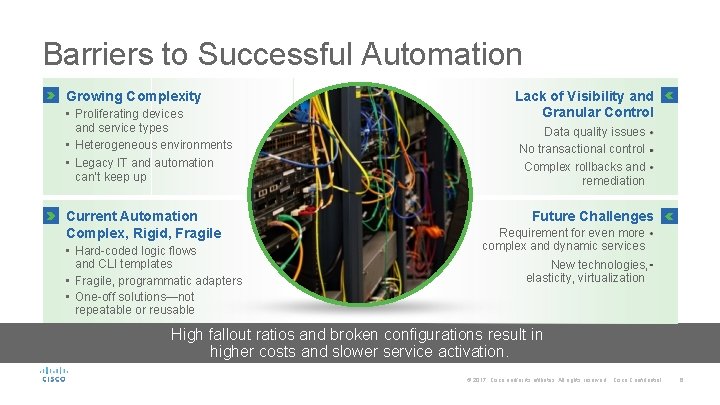
Barriers to Successful Automation Growing Complexity • Proliferating devices and service types • Heterogeneous environments • Legacy IT and automation can’t keep up Current Automation Complex, Rigid, Fragile • Hard-coded logic flows and CLI templates • Fragile, programmatic adapters • One-off solutions—not repeatable or reusable Lack of Visibility and Granular Control Data quality issues No transactional control Complex rollbacks and remediation Future Challenges Requirement for even more complex and dynamic services New technologies, elasticity, virtualization High fallout ratios and broken configurations result in higher costs and slower service activation. © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 6

What If You Could… Break the complexity barrier to enable agility? • Full lifecycle automation (create, update, delete) • Model-driven to reduce code and expand features Reconfigure services with high quality and minimal impact? • Non-disruptive updates of service and device models • Surgical precision and atomic transaction control Support real-world multivendor environments? • Any use case on any device • Hybrid and Brownfield environments • Full stack—beyond Layer 2 and Layer 3 Decouple services from infrastructure? • Physical and virtual networks and service platforms • Minimal dependencies on networking technologies • Minimal dependencies on OSS environments © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 7

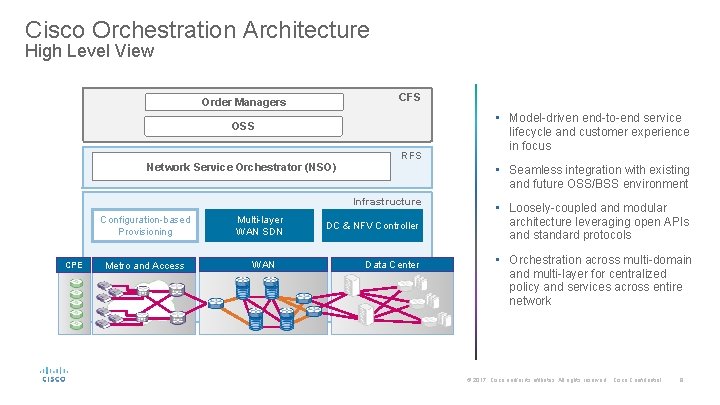
Cisco Orchestration Architecture High Level View CFS Order Managers • Model-driven end-to-end service OSS Network Service Orchestrator (NSO) RFS lifecycle and customer experience in focus • Seamless integration with existing and future OSS/BSS environment Infrastructure Configuration-based Provisioning CPE Metro and Access Multi-layer WAN SDN WAN DC & NFV Controller Data Center • Loosely-coupled and modular architecture leveraging open APIs and standard protocols • Orchestration across multi-domain and multi-layer for centralized policy and services across entire network © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 8

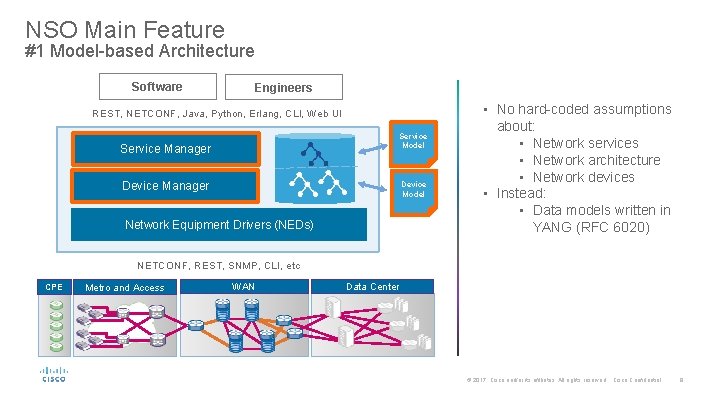
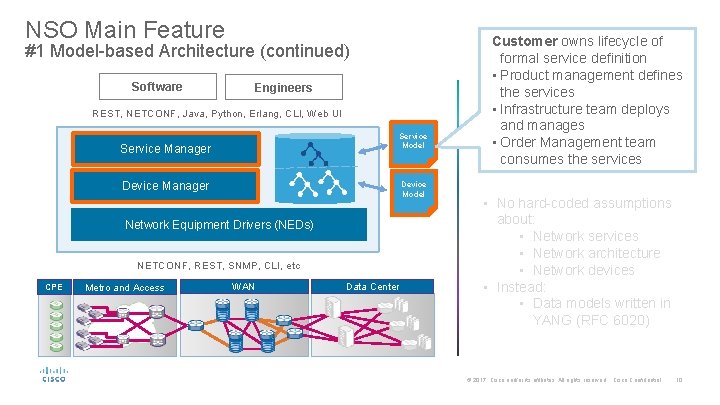
NSO Main Feature #1 Model-based Architecture Software Engineers REST, NETCONF, Java, Python, Erlang, CLI, Web UI Service Model Service Manager Device Model Network Equipment Drivers (NEDs) • No hard-coded assumptions about: • Network services • Network architecture • Network devices • Instead: • Data models written in YANG (RFC 6020) NETCONF, REST, SNMP, CLI, etc CPE Metro and Access WAN Data Center © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 9

NSO Main Feature #1 Model-based Architecture (continued) Software Engineers REST, NETCONF, Java, Python, Erlang, CLI, Web UI Service Model Service Manager Device Model Network Equipment Drivers (NEDs) NETCONF, REST, SNMP, CLI, etc CPE Metro and Access WAN Data Center Customer owns lifecycle of formal service definition • Product management defines the services • Infrastructure team deploys and manages • Order Management team consumes the services • No hard-coded assumptions about: • Network services • Network architecture • Network devices • Instead: • Data models written in YANG (RFC 6020) © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 10

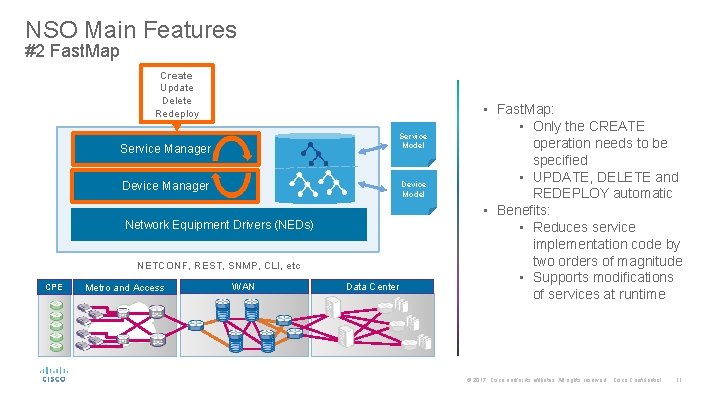
NSO Main Features #2 Fast. Map Create Update Delete Redeploy Service Model Service Manager Device Model Network Equipment Drivers (NEDs) NETCONF, REST, SNMP, CLI, etc CPE Metro and Access WAN Data Center • Fast. Map: • Only the CREATE operation needs to be specified • UPDATE, DELETE and REDEPLOY automatic • Benefits: • Reduces service implementation code by two orders of magnitude • Supports modifications of services at runtime © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 11

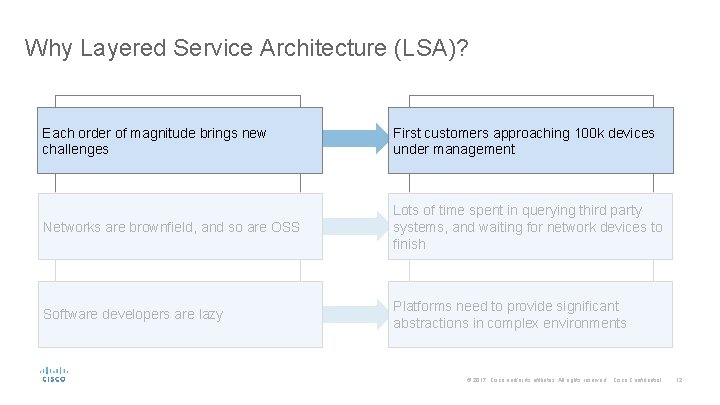
Why Layered Service Architecture (LSA)? Each order of magnitude brings new challenges First customers approaching 100 k devices under management Networks are brownfield, and so are OSS Lots of time spent in querying third party systems, and waiting for network devices to finish Software developers are lazy Platforms need to provide significant abstractions in complex environments © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 12

Why Layered Service Architecture (LSA)? Each order of magnitude brings new challenges First customers approaching 100 k devices under management Networks are brownfield, and so are OSS Lots of time spent in querying third party systems, and waiting for network devices to finish Software developers are lazy Platforms need to provide significant abstractions in complex environments © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 13

Why Layered Service Architecture (LSA)? Each order of magnitude brings new challenges First customers approaching 100 k devices under management Networks are brownfield, and so are OSS Lots of time spent in querying third party systems, and waiting for network devices to finish Software developers are lazy Platforms need to provide significant abstractions in complex environments © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 14

What You Gain with Cisco Automation • Agility throughout service lifecycle • Full automation • Robust and proven in tier-1 deployments • Industry’s broadest multivendor support • Most scalable service orchestration • ETSI MANO compliant NFVO, VNFM • Relevant in today’s and tomorrow’s networks © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 15

NSO’s Layered Services Architecture Innovation and Demo © 2016 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 16

NSO LSA Overview • Addressing Performance and Scalability Limitations • LSA Deployment • LSA Demo © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 17

Addressing Performance and Scalability Limitations • Increase capacity: RAM, CPU • Optimize code: YANG, XPath, Java, Python, northbound applications • Change NSO behavior: commit queues, reactive FASTMAP © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 18

Optimize Code Service Instance Parameters XPath: avoid large and convoluted absolute XPath expressions if possible (e. g. use must statement) Config Mapping Java/Python: avoid all-encompassing loops XML XPath: careful with foreach and when attributes Config Delivery AAA: command authorization on devices can slow down transactions © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 19

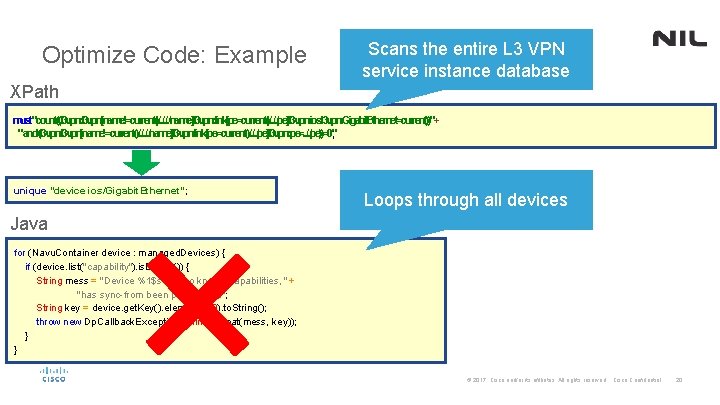
Optimize Code: Example Scans the entire L 3 VPN service instance database XPath must"count((/l 3 vpn: l 3 vpn[name!=current()/. . /name]/l 3 vpn: link[pe=current()/. . /pe]/l 3 vpn: ios/l 3 vpn: Gigabit. Ethernet=current())"+ "and(/l 3 vpn: l 3 vpn[name!=current()/. . /name]/l 3 vpn: link[pe=current()/. . /pe]/l 3 vpn: pe=. . /pe))=0"; unique "device ios/Gigabit. Ethernet"; Loops through all devices Java for (Navu. Container device : managed. Devices) { if (device. list("capability"). is. Empty()) { String mess = "Device %1$s has no known capabilities, " + "has sync-from been performed? "; String key = device. get. Key(). element. At(0). to. String(); throw new Dp. Callback. Exception(String. format(mess, key)); } } © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 20

Service Implementation Guidelines • NSO is a powerful framework: You can code anything with Java or Python … but • You can do many things with XPath … but • You can do most things with standard YANG statements • • Design and development guidelines: Use standard YANG statements as much as possible • Only use XPath expressions when standard YANG statements are insufficient • Only use Java or Python code where YANG/XPath are insufficient • © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 21

Addressing Performance Limitations Using Vertical Scaling Summary • Increase capacity: reached the hard limits • Optimize code: ran out of options • Change NSO behavior: nothing more to be done There is only so much you can do! © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 22

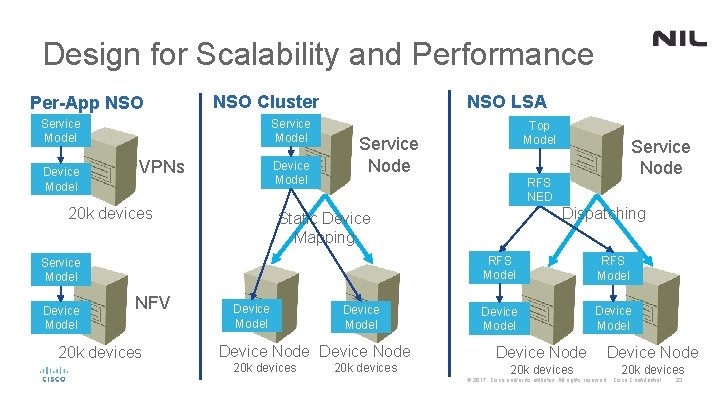
Design for Scalability and Performance Per-App NSO Cluster Service Model Device Model VPNs Device Model 20 k devices NSO LSA Service Node NFV 20 k devices Dispatching Static Device Mapping Device Model Device Node 20 k devices Service Node RFS NED Service Model Device Model Top Model 20 k devices RFS Model Device Node 20 k devices © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 23

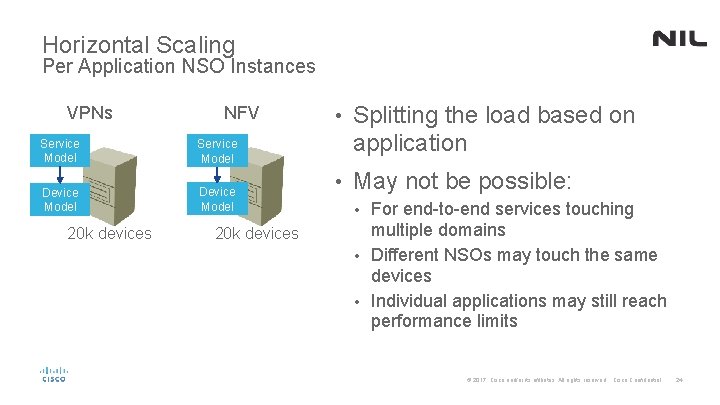
Horizontal Scaling Per Application NSO Instances VPNs NFV Service Model Device Model 20 k devices • Splitting the load based on application • May not be possible: For end-to-end services touching multiple domains • Different NSOs may touch the same devices • Individual applications may still reach performance limits • © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 24

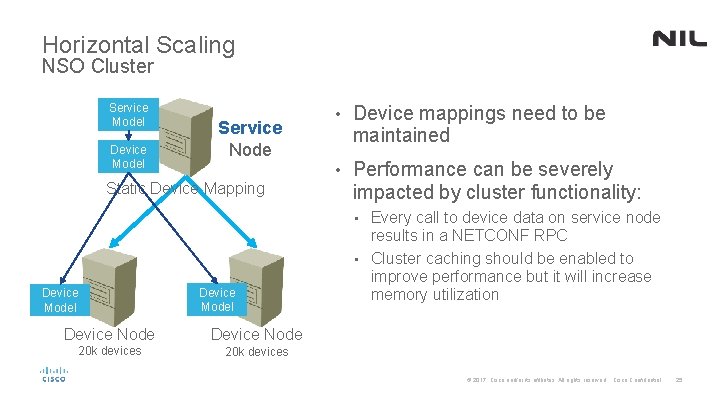
Horizontal Scaling NSO Cluster Service Model Device Model Service Node Static Device Mapping • Device mappings need to be maintained • Performance can be severely impacted by cluster functionality: Every call to device data on service node results in a NETCONF RPC • Cluster caching should be enabled to improve performance but it will increase memory utilization • Device Model Device Node 20 k devices © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 25

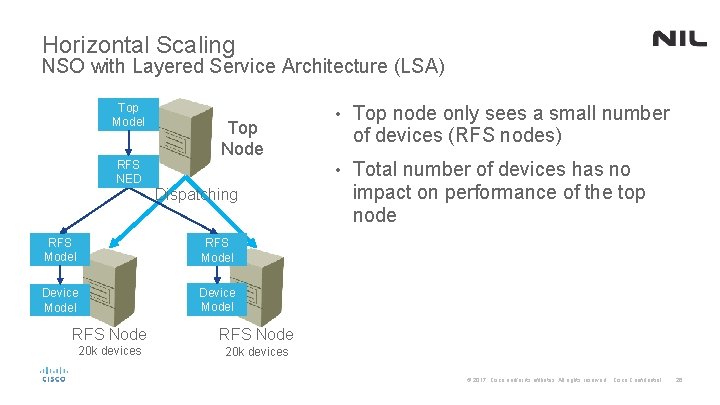
Horizontal Scaling NSO with Layered Service Architecture (LSA) Top Model RFS NED Top Node Dispatching RFS Model Device Model RFS Node 20 k devices • Top node only sees a small number of devices (RFS nodes) • Total number of devices has no impact on performance of the top node © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 26

LSA Design Guidelines • Use LSA for virtually limitless scalability • Make your top-level service model agnostic to device, platform, interface, and technology • Devise the simplest dispatch method possible or at least one easy to maintain • Implement integration with external systems at the top layer • Implement resource allocation at the appropriate layer • Use LSA-ready design today even if you run just one node © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 27

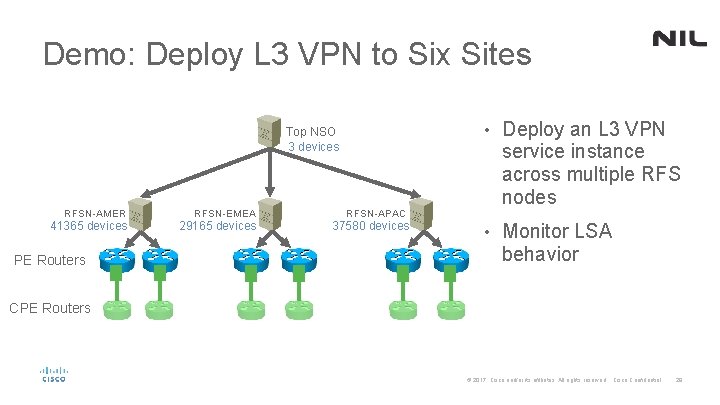
Demo: Deploy L 3 VPN to Six Sites Top NSO 3 devices RFSN-AMER 41365 devices PE Routers RFSN-EMEA 29165 devices • Deploy an L 3 VPN service instance across multiple RFS nodes • Monitor LSA behavior RFSN-APAC 37580 devices CPE Routers © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 28

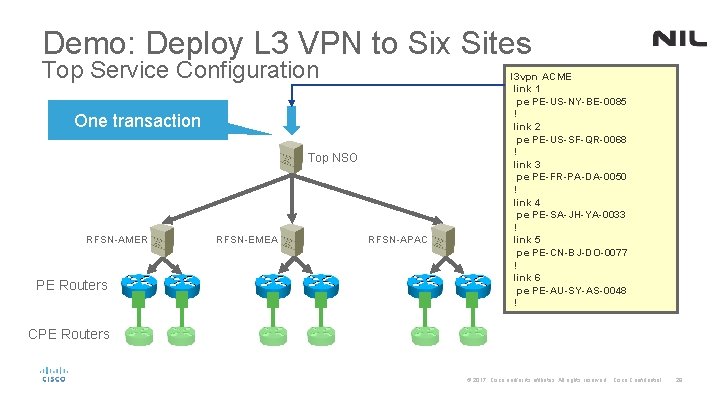
Demo: Deploy L 3 VPN to Six Sites Top Service Configuration One transaction Top NSO RFSN-AMER PE Routers RFSN-EMEA RFSN-APAC l 3 vpn ACME link 1 pe PE-US-NY-BE-0085 ! link 2 pe PE-US-SF-QR-0068 ! link 3 pe PE-FR-PA-DA-0050 ! link 4 pe PE-SA-JH-YA-0033 ! link 5 pe PE-CN-BJ-DO-0077 ! link 6 pe PE-AU-SY-AS-0048 ! CPE Routers © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 29

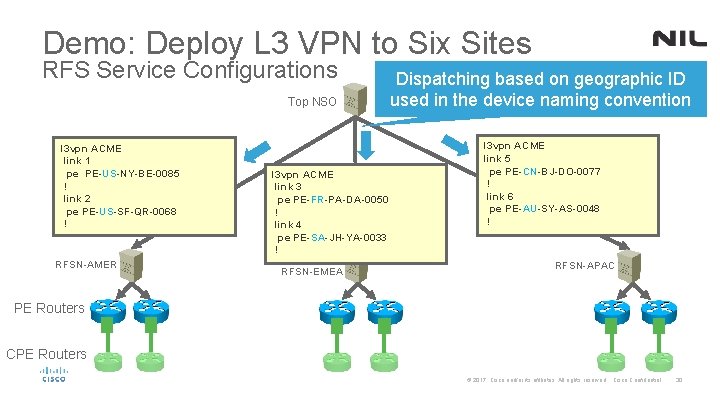
Demo: Deploy L 3 VPN to Six Sites RFS Service Configurations Top NSO l 3 vpn ACME link 1 pe PE-US-NY-BE-0085 ! link 2 pe PE-US-SF-QR-0068 ! RFSN-AMER l 3 vpn ACME link 3 pe PE-FR-PA-DA-0050 ! link 4 pe PE-SA-JH-YA-0033 ! RFSN-EMEA Dispatching based on geographic ID used in the device naming convention l 3 vpn ACME link 5 pe PE-CN-BJ-DO-0077 ! link 6 pe PE-AU-SY-AS-0048 ! RFSN-APAC PE Routers CPE Routers © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 30

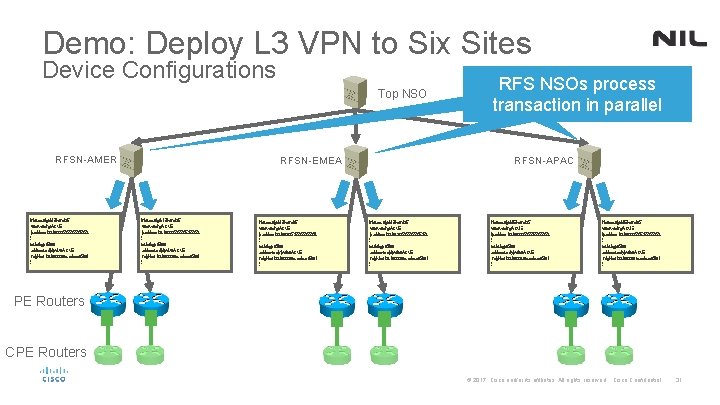
Demo: Deploy L 3 VPN to Six Sites Device Configurations Top NSO RFSN-AMER interface. Gigabit. Ethernet 3/5 vrfforwarding. ACME ipaddress 192. 168. 223. 5255. 252 ! routerbgp 65000 address-familyipv 4 vrf. ACME neighbor 192. 168. 223. 6 remote-as 65001 ! RFSN-EMEA interface. Gigabit. Ethernet 3/5 vrfforwarding. ACME ipaddress 192. 168. 223. 5255. 255. 252 ! routerbgp 65000 address-familyipv 4 vrf. ACME neighbor 192. 168. 223. 6 remote-as 65001 ! RFS NSOs process transaction in parallel RFSN-APAC interface. Gigabit. Ethernet 3/5 vrfforwarding. ACME ipaddress 192. 168. 223. 5255. 255. 252 ! routerbgp 65000 address-familyipv 4 vrf. ACME neighbor 192. 168. 223. 6 remote-as 65001 ! interface. Gigabit. Ethernet 3/5 vrfforwarding. ACME ipaddress 192. 168. 223. 5255. 252 ! routerbgp 65000 address-familyipv 4 vrf. ACME neighbor 192. 168. 223. 6 remote-as 65001 ! PE Routers CPE Routers © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 31

For more information Visit: www. cisco. com/go/nso www. nil. com and contact your Cisco and NIL account representatives © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 32


Support Technical Slides © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 34

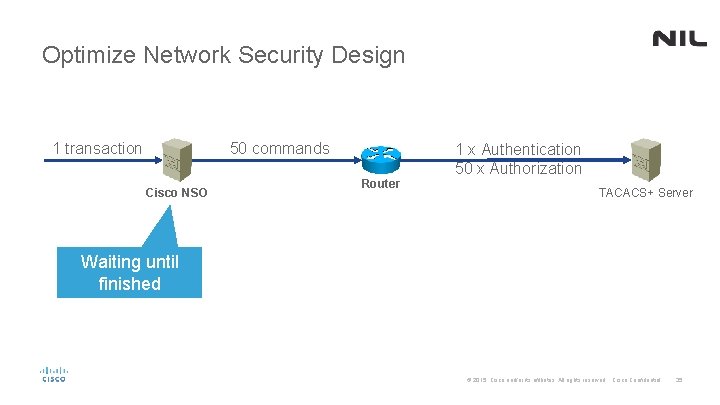
Optimize Network Security Design 1 transaction 50 commands Cisco NSO Router 1 x Authentication 50 x Authorization TACACS+ Server Waiting until finished © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 35

LSA Example: Adding a New L 3 VPN Site • PE Top layer node requires: • Allocate VLAN on trunk Allocate physical interface • RFS node reference RFS nodes require: Device references • Physical interface references • VLAN numbers • CPE © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 36

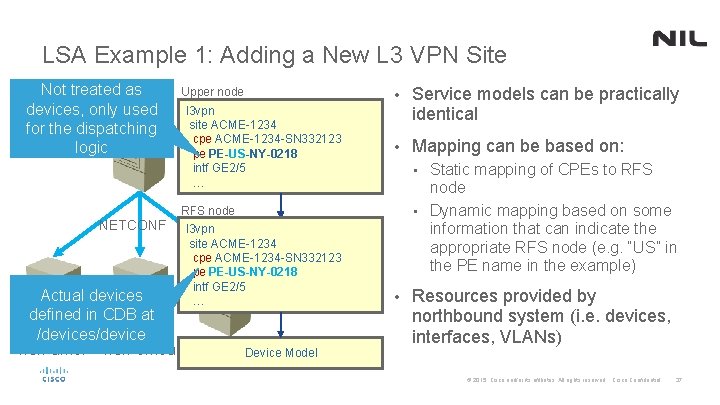
LSA Example 1: Adding a New L 3 VPN Site Not treated as cfsn devices, only used for the dispatching logic NETCONF Actual devices defined in CDB at /devices/device rfsn-amer rfsn-emea Upper node l 3 vpn site ACME-1234 cpe ACME-1234 -SN 332123 pe PE-US-NY-0218 intf GE 2/5 … • Service models can be practically identical • Mapping can be based on: Static mapping of CPEs to RFS node • Dynamic mapping based on some information that can indicate the appropriate RFS node (e. g. “US” in the PE name in the example) • RFS node l 3 vpn site ACME-1234 cpe ACME-1234 -SN 332123 pe PE-US-NY-0218 intf GE 2/5 … rfsn-apac Device Model • Resources provided by northbound system (i. e. devices, interfaces, VLANs) © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 37

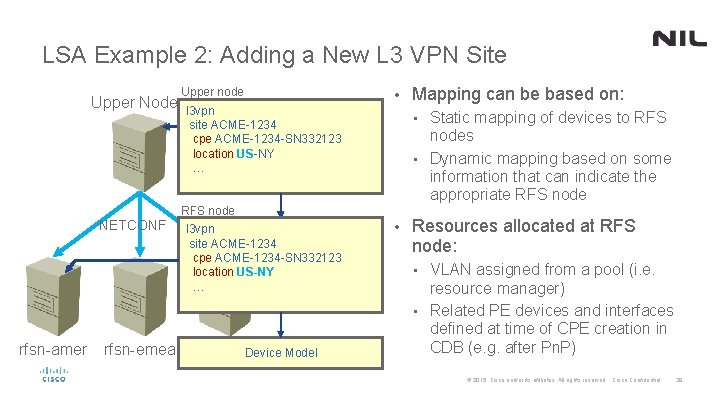
LSA Example 2: Adding a New L 3 VPN Site Upper Node NETCONF rfsn-amer rfsn-emea Upper node • l 3 vpn site ACME-1234 cpe ACME-1234 -SN 332123 location US-NY … Static mapping of devices to RFS nodes • Dynamic mapping based on some information that can indicate the appropriate RFS node • RFS node l 3 vpn site ACME-1234 cpe ACME-1234 -SN 332123 location US-NY … rfsn-apac Device Model Mapping can be based on: • Resources allocated at RFS node: VLAN assigned from a pool (i. e. resource manager) • Related PE devices and interfaces defined at time of CPE creation in CDB (e. g. after Pn. P) • © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 38

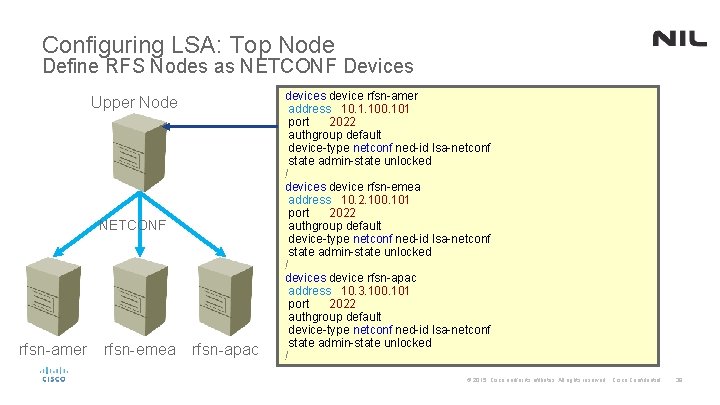
Configuring LSA: Top Node Define RFS Nodes as NETCONF Devices Upper Node NETCONF rfsn-amer rfsn-emea rfsn-apac devices device rfsn-amer address 10. 1. 100. 101 port 2022 authgroup default device-type netconf ned-id lsa-netconf state admin-state unlocked ! devices device rfsn-emea address 10. 2. 100. 101 port 2022 authgroup default device-type netconf ned-id lsa-netconf state admin-state unlocked ! devices device rfsn-apac address 10. 3. 100. 101 port 2022 authgroup default device-type netconf ned-id lsa-netconf state admin-state unlocked ! © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 39

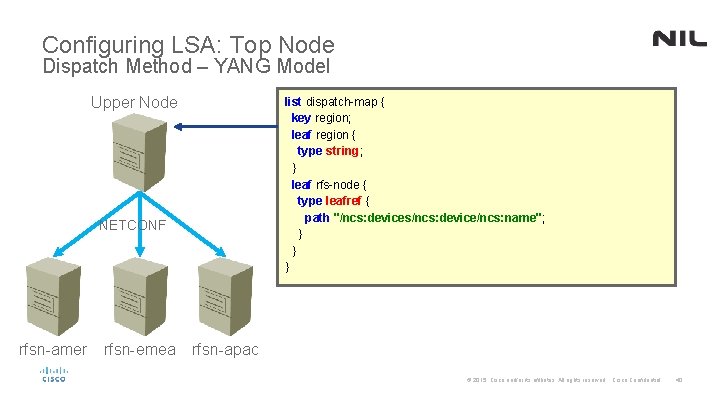
Configuring LSA: Top Node Dispatch Method – YANG Model Upper Node list dispatch-map { key region; leaf region { type string; } leaf rfs-node { type leafref { path "/ncs: devices/ncs: device/ncs: name"; } } } NETCONF rfsn-amer rfsn-emea rfsn-apac © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 40

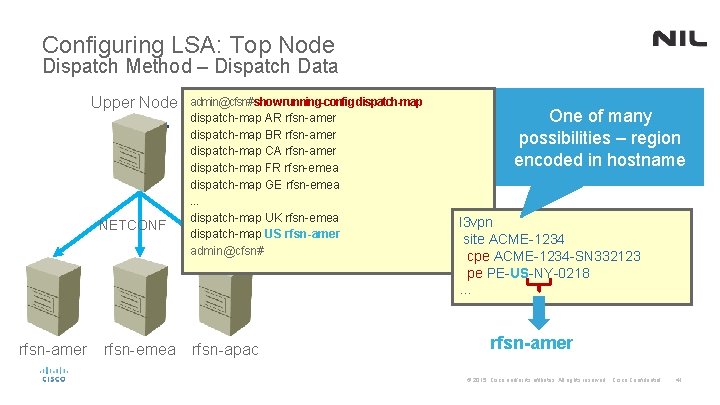
Configuring LSA: Top Node Dispatch Method – Dispatch Data Upper Node NETCONF rfsn-amer rfsn-emea admin@cfsn# show running-config dispatch-map AR rfsn-amer dispatch-map BR rfsn-amer dispatch-map CA rfsn-amer dispatch-map FR rfsn-emea dispatch-map GE rfsn-emea. . . dispatch-map UK rfsn-emea dispatch-map US rfsn-amer admin@cfsn# rfsn-apac One of many possibilities – region encoded in hostname l 3 vpn site ACME-1234 cpe ACME-1234 -SN 332123 pe PE-US-NY-0218 … rfsn-amer © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 41

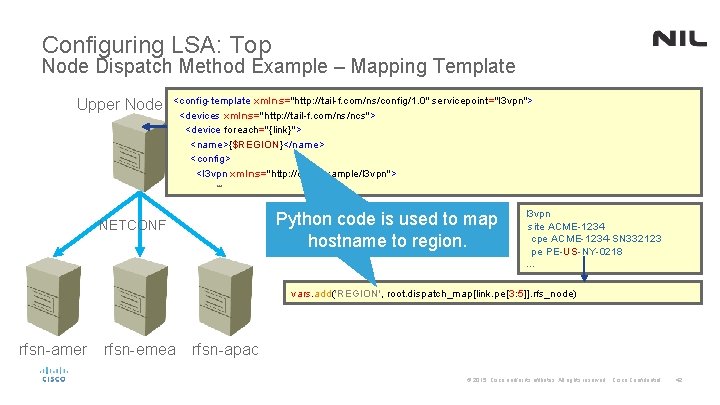
Configuring LSA: Top Node Dispatch Method Example – Mapping Template Upper Node <config-template xmlns="http: //tail-f. com/ns/config/1. 0" servicepoint="l 3 vpn"> <devices xmlns="http: //tail-f. com/ns/ncs"> <device foreach="{link}"> <name>{$REGION}</name> <config> <l 3 vpn xmlns="http: //com/example/l 3 vpn">. . . Python code is used to map hostname to region. NETCONF l 3 vpn site ACME-1234 cpe ACME-1234 -SN 332123 pe PE-US-NY-0218 … vars. add('REGION', root. dispatch_map[link. pe[3: 5]]. rfs_node) rfsn-amer rfsn-emea rfsn-apac © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 42

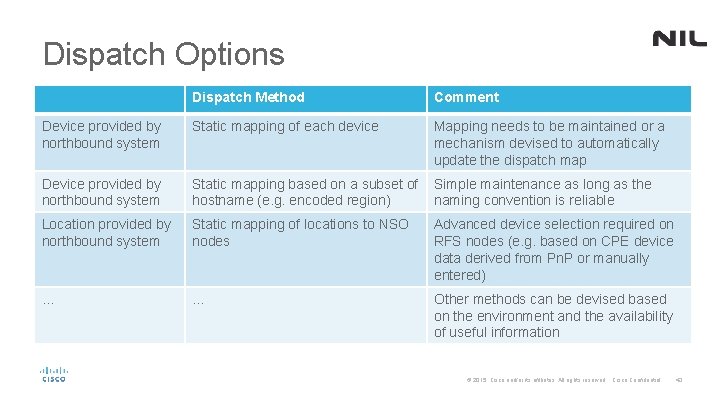
Dispatch Options Dispatch Method Comment Device provided by northbound system Static mapping of each device Mapping needs to be maintained or a mechanism devised to automatically update the dispatch map Device provided by northbound system Static mapping based on a subset of hostname (e. g. encoded region) Simple maintenance as long as the naming convention is reliable Location provided by northbound system Static mapping of locations to NSO nodes Advanced device selection required on RFS nodes (e. g. based on CPE device data derived from Pn. P or manually entered) … … Other methods can be devised based on the environment and the availability of useful information © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 43