Operational Technology Agenda 0 1 Operational Technology vs









- Slides: 32

Operational Technology

Agenda 0 1 Operational Technology vs Information Technology 0 2 Industrial Control Systems (ICS) 0 3 Operation al Technolog y Attacks 0 4 Distribute d Control System (DCS) 0 5 Programmable Logic Controlle r (PLC) 06 DCS vs PLC 2

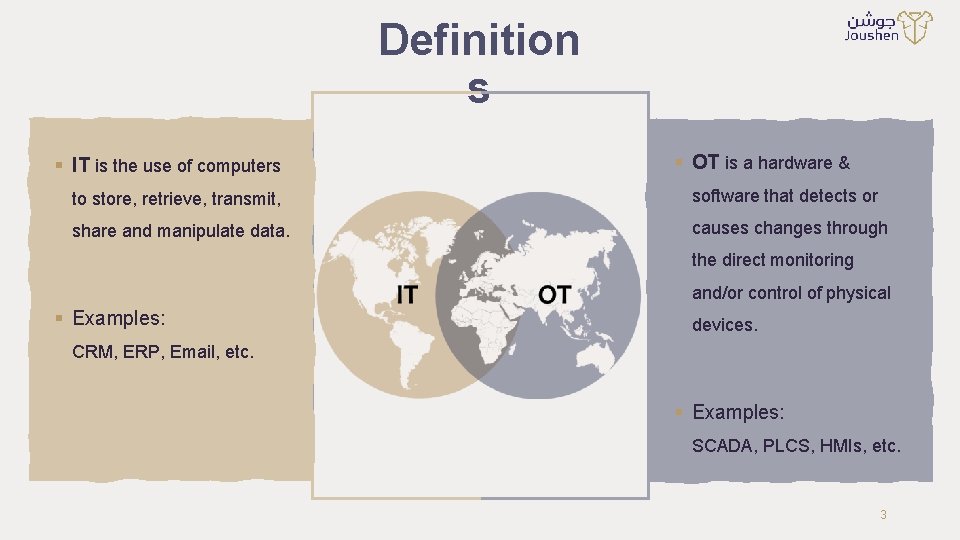
Definition s § IT is the use of computers § OT is a hardware & to store, retrieve, transmit, software that detects or share and manipulate data. causes changes through the direct monitoring and/or control of physical § Examples: devices. CRM, ERP, Email, etc. § Examples: SCADA, PLCS, HMIs, etc. 3

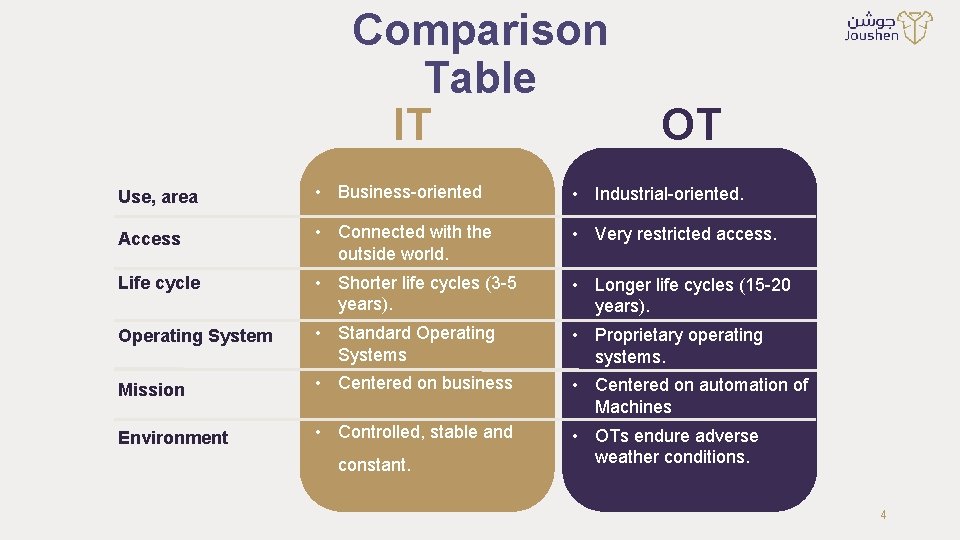
Comparison Table IT OT Use, area • Business-oriented • Industrial-oriented. Access • Connected with the outside world. • Very restricted access. Life cycle • Shorter life cycles (3 -5 years). • Longer life cycles (15 -20 years). Operating System • Standard Operating Systems • Proprietary operating systems. Mission • Centered on business • Centered on automation of Machines Environment • Controlled, stable and • OTs endure adverse weather conditions. constant. 4

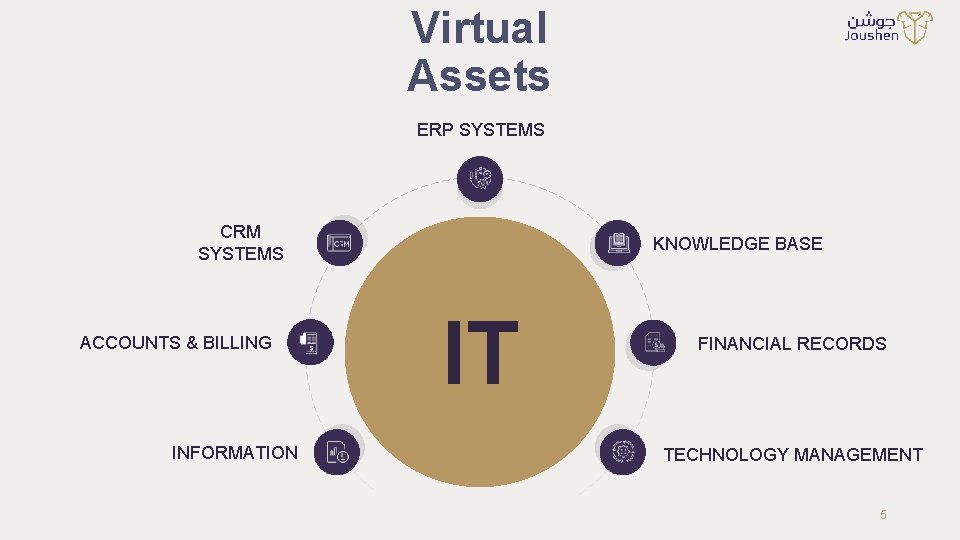
Virtual Assets ERP SYSTEMS CRM SYSTEMS ACCOUNTS & BILLING INFORMATION KNOWLEDGE BASE IT FINANCIAL RECORDS TECHNOLOGY MANAGEMENT 5

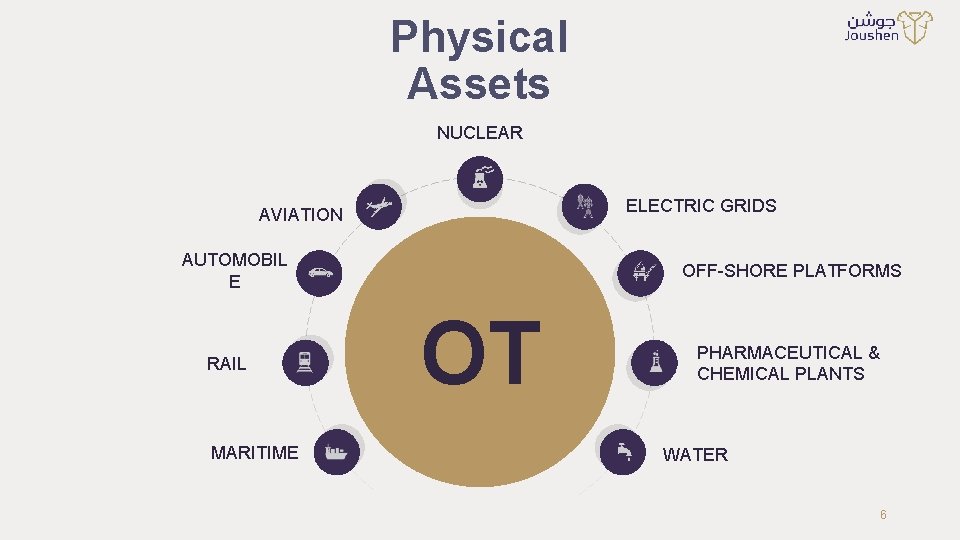
Physical Assets NUCLEAR ELECTRIC GRIDS AVIATION AUTOMOBIL E RAIL MARITIME OFF-SHORE PLATFORMS OT PHARMACEUTICAL & CHEMICAL PLANTS WATER 6

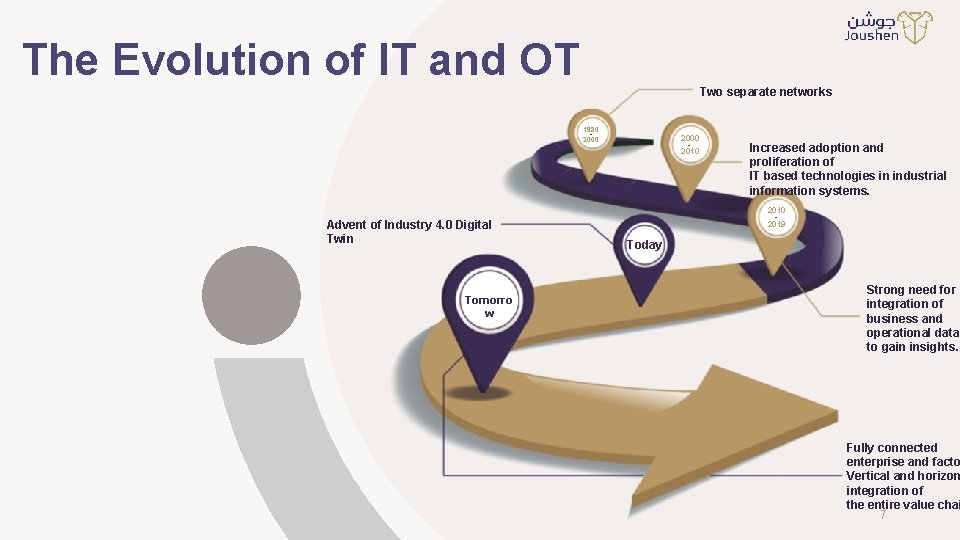
The Evolution of IT and OT Two separate networks 1980 2000 - 2010 Increased adoption and proliferation of IT based technologies in industrial information systems. 2010 Advent of Industry 4. 0 Digital Twin Tomorro w - 2019 Today Strong need for integration of business and operational data to gain insights. Fully connected enterprise and facto Vertical and horizon integration of the entire value chai 7

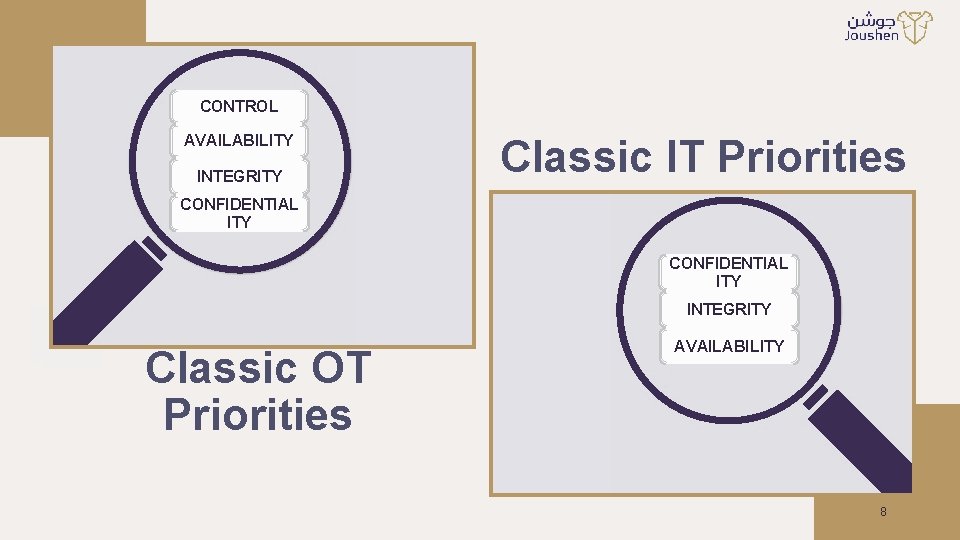
CONTROL AVAILABILITY INTEGRITY Classic IT Priorities CONFIDENTIAL ITY INTEGRITY Classic OT Priorities AVAILABILITY 8

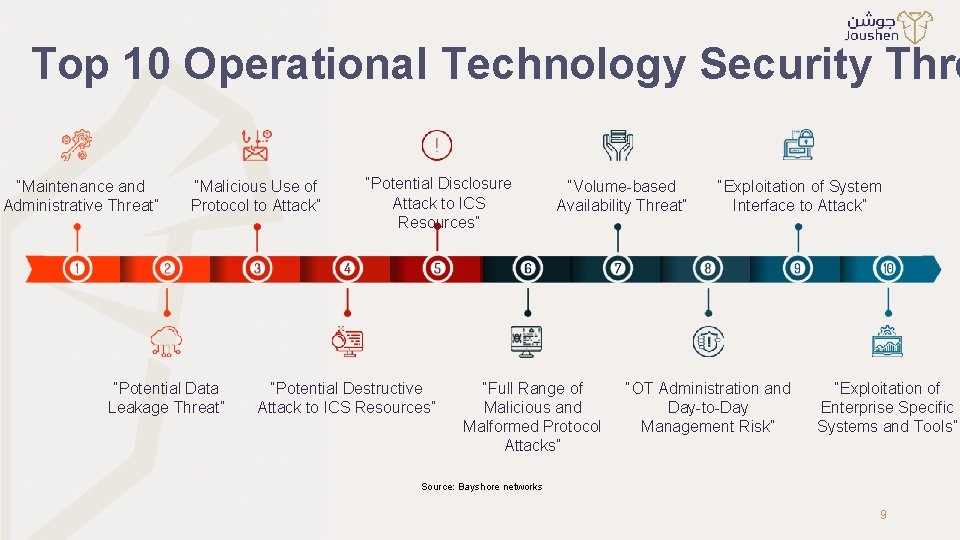
Top 10 Operational Technology Security Thre “Maintenance and Administrative Threat” “Malicious Use of Protocol to Attack” “Potential Data Leakage Threat” “Potential Disclosure Attack to ICS Resources” “Potential Destructive Attack to ICS Resources” “Volume-based Availability Threat” “Full Range of Malicious and Malformed Protocol Attacks” “Exploitation of System Interface to Attack” “OT Administration and Day-to-Day Management Risk” “Exploitation of Enterprise Specific Systems and Tools” Source: Bayshore networks 9

ICS Definition Industrial Control Systems (ICS) are command control network and systems designed to support industrial processes. 10

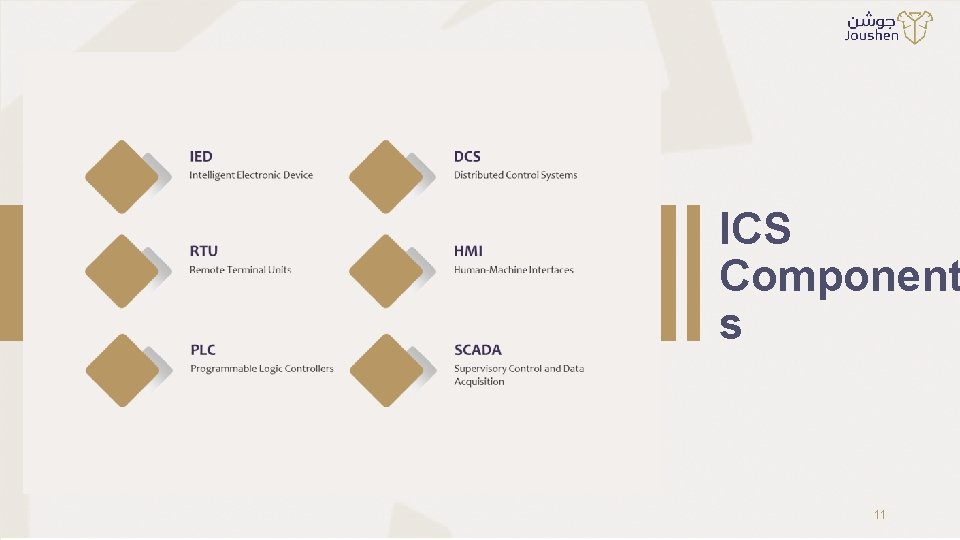
ICS Component s 11

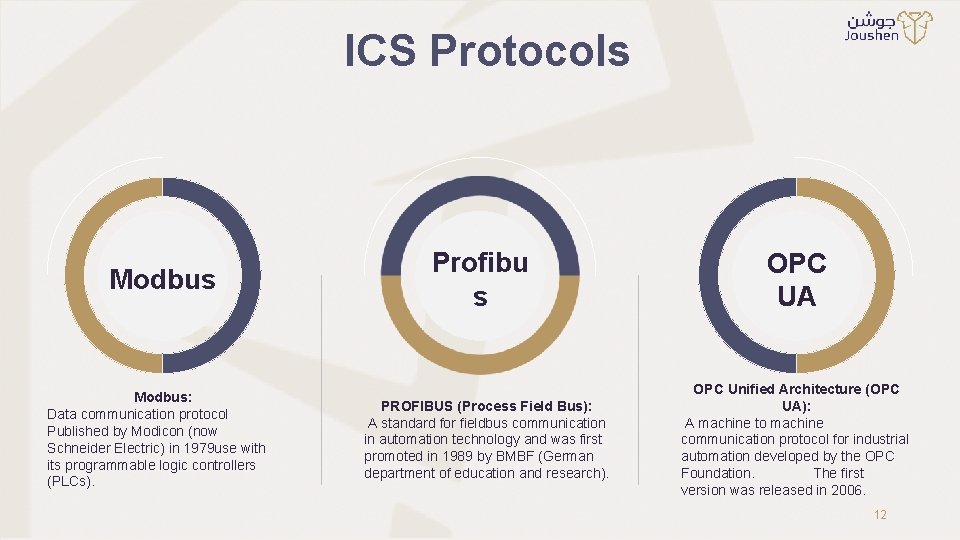
ICS Protocols Modbus: Data communication protocol Published by Modicon (now Schneider Electric) in 1979 use with its programmable logic controllers (PLCs). Profibu s PROFIBUS (Process Field Bus): A standard for fieldbus communication in automation technology and was first promoted in 1989 by BMBF (German department of education and research). OPC UA OPC Unified Architecture (OPC UA): A machine to machine communication protocol for industrial automation developed by the OPC Foundation. The first version was released in 2006. 12

How ICS Security Works? Securing and safeguarding industrial control systems, and the software and hardware used in operating and controlling machinery. Keeping processes and machineries running smoothly. Ensuring that the information and data shown on the control room dashboards and screens are accurate, reflecting what is really happening in the plant or production floor. 13

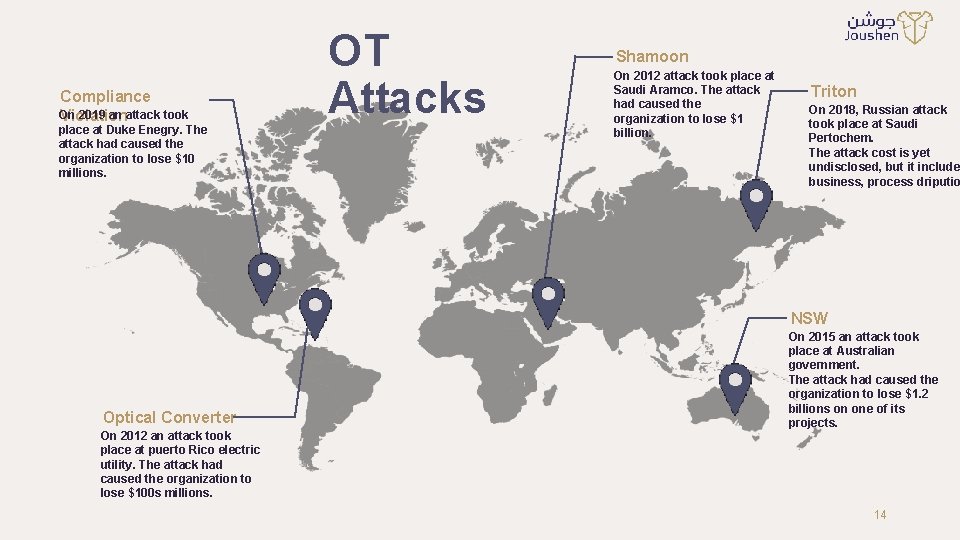
Compliance On 2019 an attack took Violation place at Duke Enegry. The attack had caused the organization to lose $10 millions. OT Attacks Shamoon On 2012 attack took place at Saudi Aramco. The attack had caused the organization to lose $1 billion. Triton On 2018, Russian attack took place at Saudi Pertochem. The attack cost is yet undisclosed, but it include business, process driputio NSW Optical Converter On 2012 an attack took place at puerto Rico electric utility. The attack had caused the organization to lose $100 s millions. On 2015 an attack took place at Australian government. The attack had caused the organization to lose $1. 2 billions on one of its projects. 14

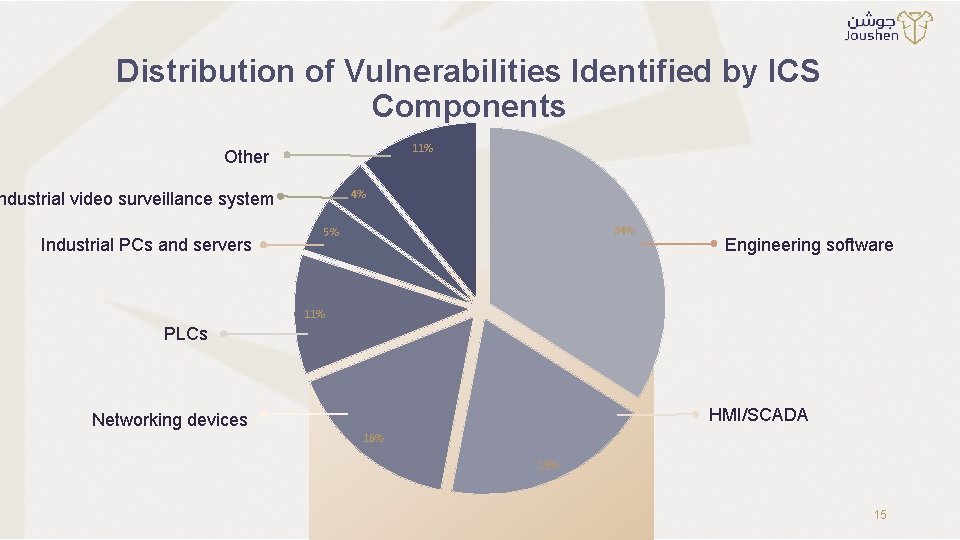
Distribution of Vulnerabilities Identified by ICS Components 11% Other 4% ndustrial video surveillance system Industrial PCs and servers 34% 5% Engineering software 11% PLCs HMI/SCADA Networking devices 16% 19% 15

Industrial Cyber Security Certifications 01. GICSP 02. 03. 04. SSAE CISSP CSSA Global Industrial Cyber Statement on Standards for Certified Information Systems Security Professional (GICSP)Attestation Engagements (SSAE) Security Professional (CISSP) Certified SCADA Security Architect (CSSA) 16

DISTRIBUTED CONTROL SYSTEM DCS is a specially designed automated control system that consists of geographically distributed control elements over the plant or control area. 17

Why DCS ? Total Plant Automation. Management information system Advanced process control 18

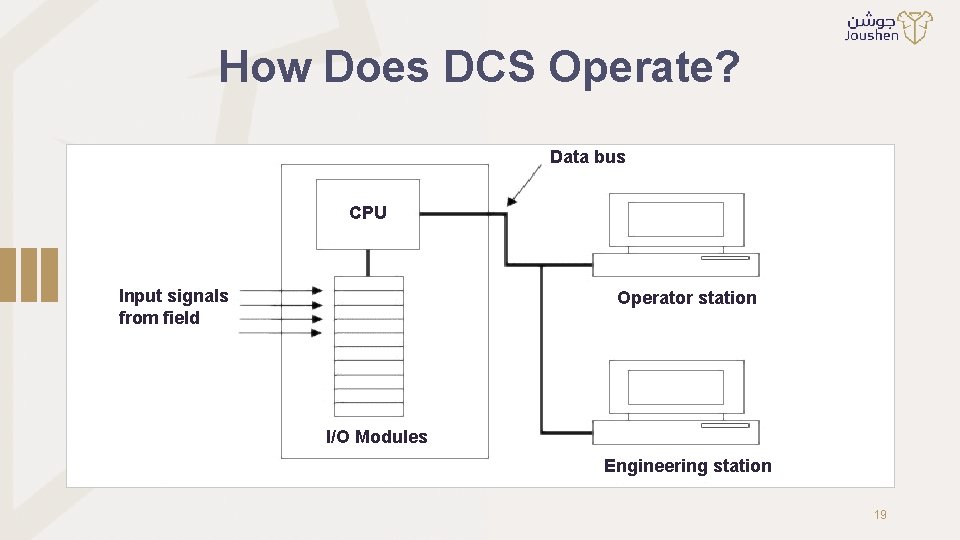
How Does DCS Operate? Data bus CPU Input signals from field Operator station I/O Modules Engineering station 19

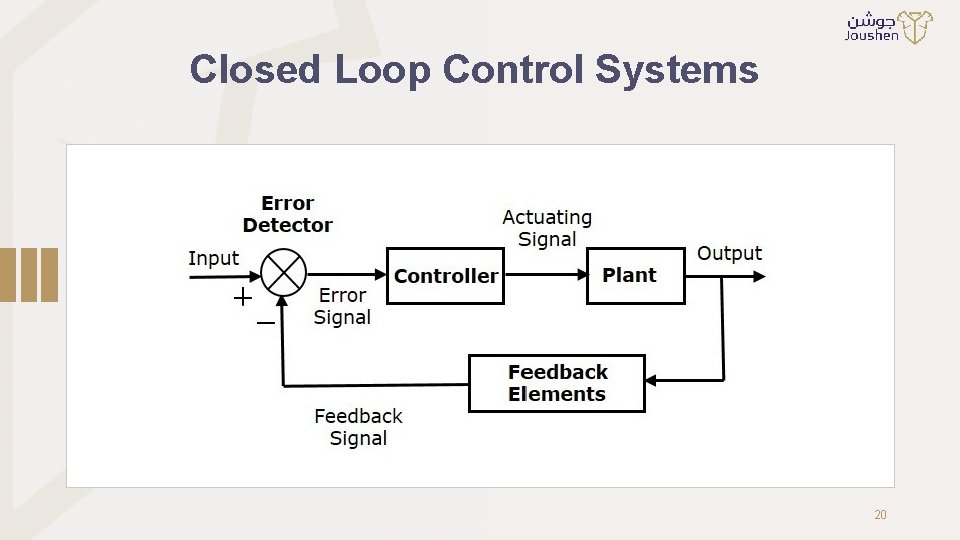
Closed Loop Control Systems 20

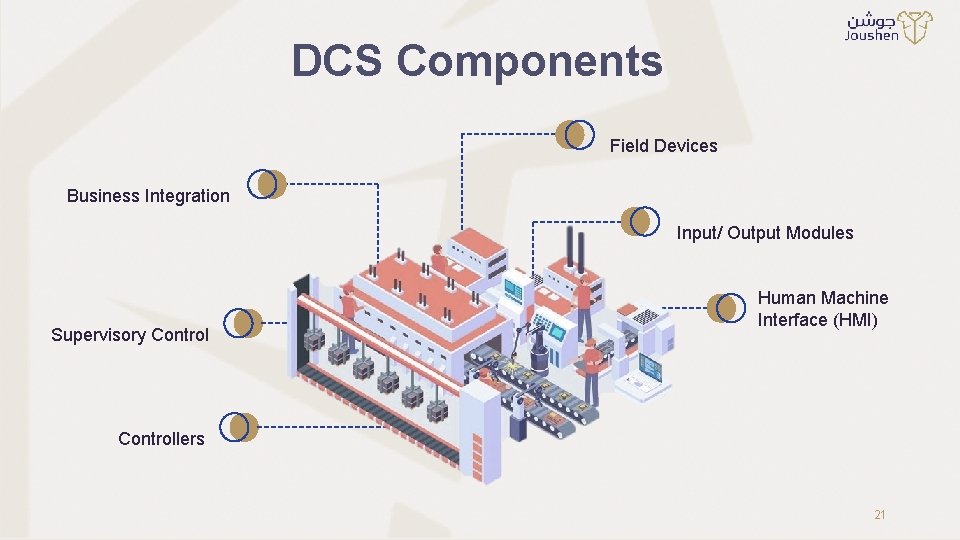
DCS Components Field Devices Business Integration Input/ Output Modules Supervisory Control Human Machine Interface (HMI) Controllers 21

A programmable logic controller (PLC) or programmable controller is an industrial digital computer which has been ruggedized and adapted for the control of manufacturing processes, such as assembly lines, or robotic What is a PLC ? devices, or any activity that requires high reliability, ease of programming and process fault diagnosis. 22

Why should we use PLC? • The most common use of it is in washing machines, controlling traffic signals, elevators, etc. Also, we cannot neglect the use of PLCs in industries to monitor and control building systems and production processes. 23

PLC Programming • Ladder Diagram(LD) • Instruction List(IL) • Structured Text(ST) • Function Block Diagram(FBD) • Sequential Function Charts(SFC) 24

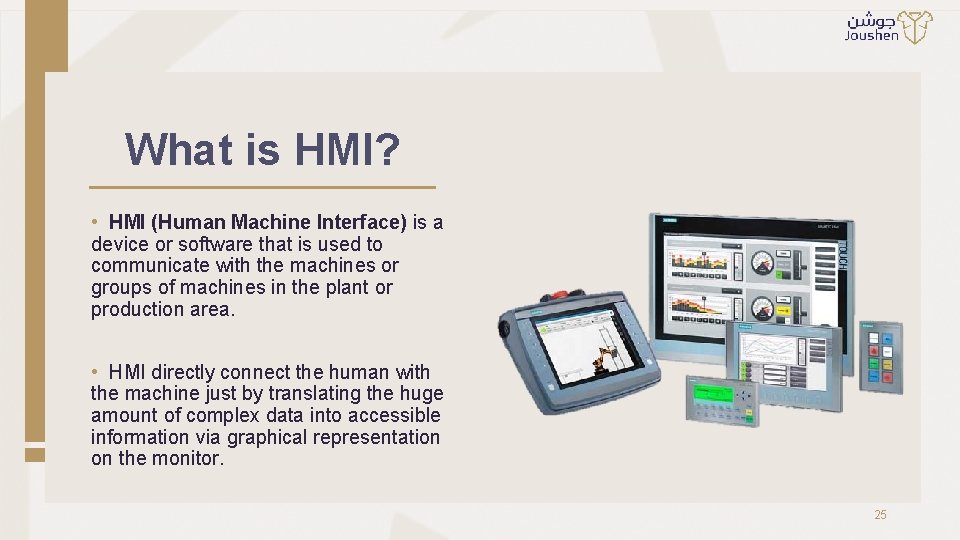
What is HMI? • HMI (Human Machine Interface) is a device or software that is used to communicate with the machines or groups of machines in the plant or production area. • HMI directly connect the human with the machine just by translating the huge amount of complex data into accessible information via graphical representation on the monitor. 25

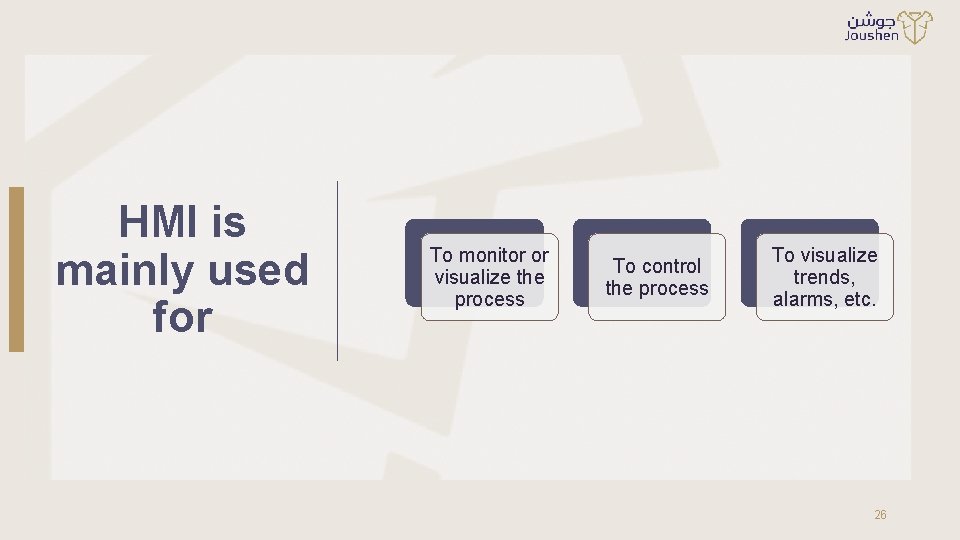
HMI is mainly used for To monitor or visualize the process To control the process To visualize trends, alarms, etc. 26

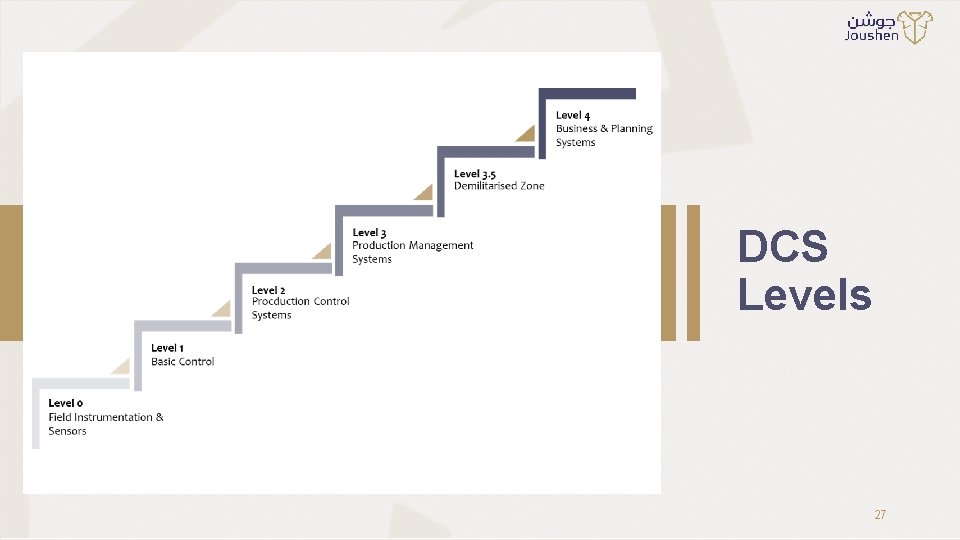
DCS Levels 27

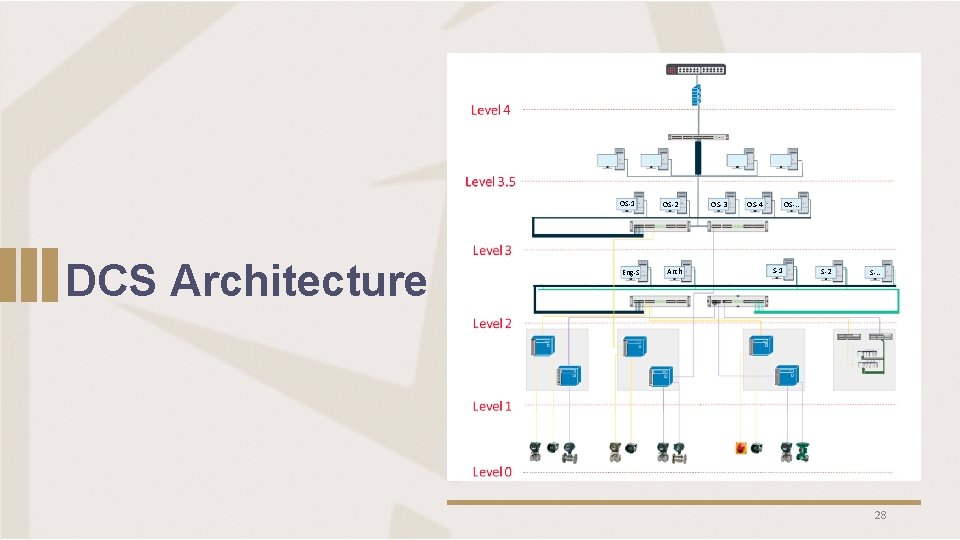
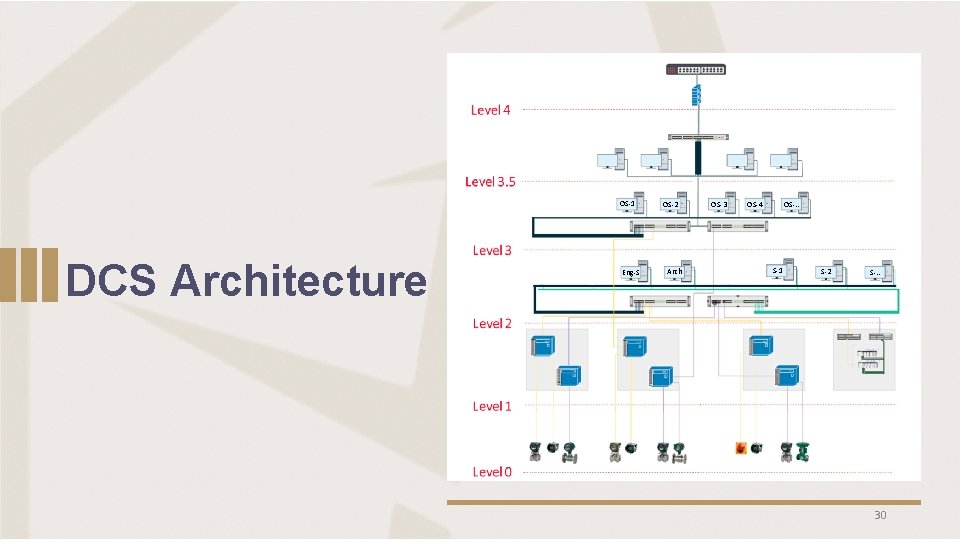
OS-1 DCS Architecture Eng-S OS-2 Arch OS-3 OS-. . OS-4 S-1 S-2 S-. . 28

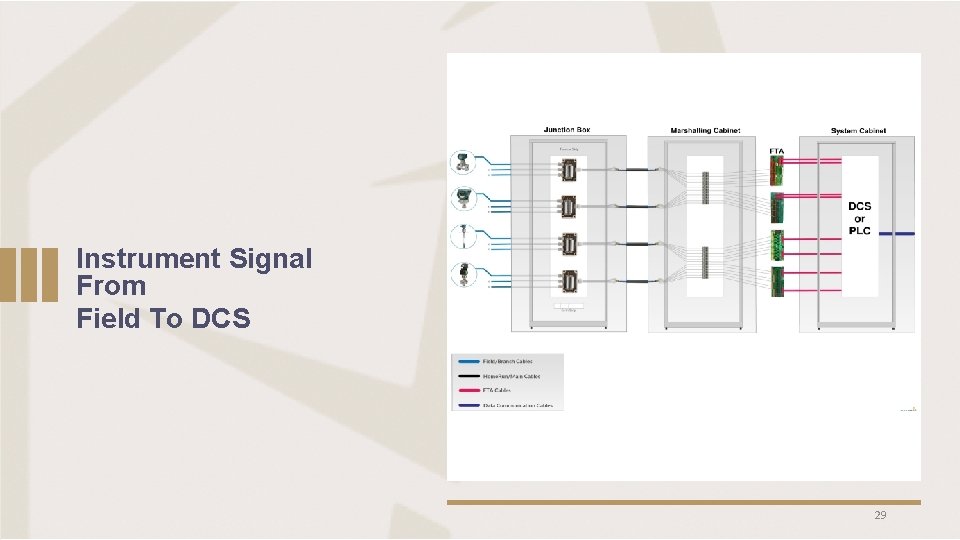
Instrument Signal From Field To DCS 29

OS-1 DCS Architecture Eng-S OS-2 Arch OS-3 OS-. . OS-4 S-1 S-2 S-. . 30

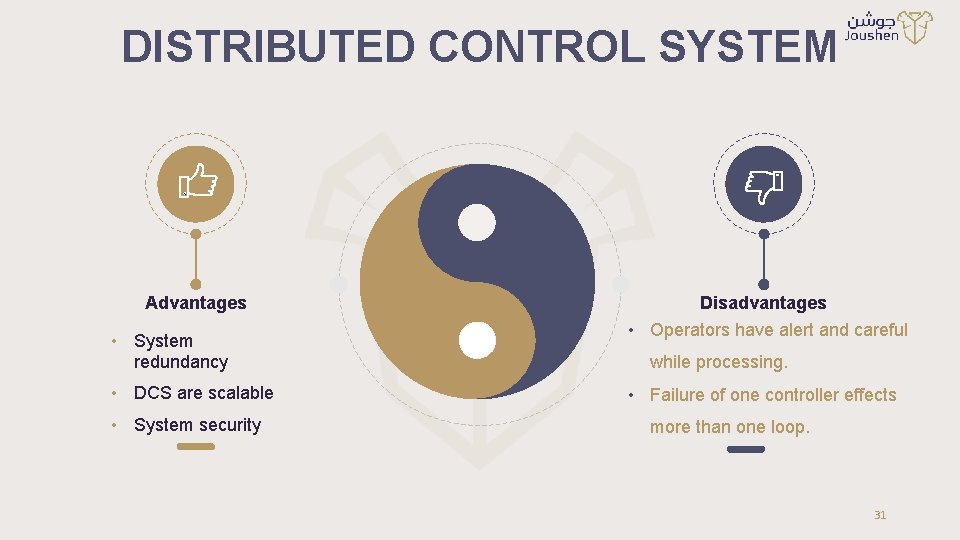
DISTRIBUTED CONTROL SYSTEM Advantages • System redundancy • DCS are scalable • System security Disadvantages • Operators have alert and careful while processing. • Failure of one controller effects more than one loop. 31

THANK YOU JOUSHEN Sara. alolayan@joushen. com Omar. alharbi@joushen. com https: //www. linkedin. com/in/sara-alolayan-4017 a 9181/ https: //www. linkedin. com/in/omar-al-awad-76 b 990168/