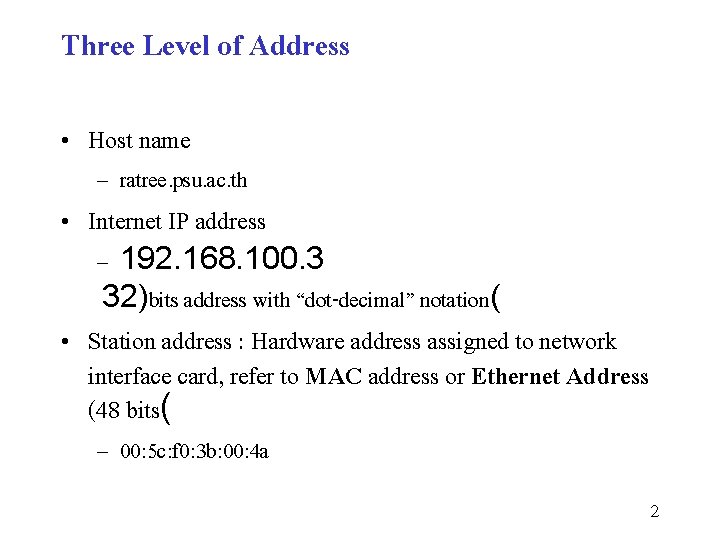
IP Address Sirak Kaewjamnong 1 Three Level of






















![Support Protocols • • ICMPv 6 [RFC 1885] DHCPv 6 DNS extensions to support Support Protocols • • ICMPv 6 [RFC 1885] DHCPv 6 DNS extensions to support](https://slidetodoc.com/presentation_image_h2/b64136b03d6cba1cf05b18028214e088/image-58.jpg)

- Slides: 64

IP Address Sirak Kaewjamnong 1

Three Level of Address • Host name – ratree. psu. ac. th • Internet IP address – 192. 168. 100. 3 32)bits address with “dot-decimal” notation( • Station address : Hardware address assigned to network interface card, refer to MAC address or Ethernet Address (48 bits( – 00: 5 c: f 0: 3 b: 00: 4 a 2

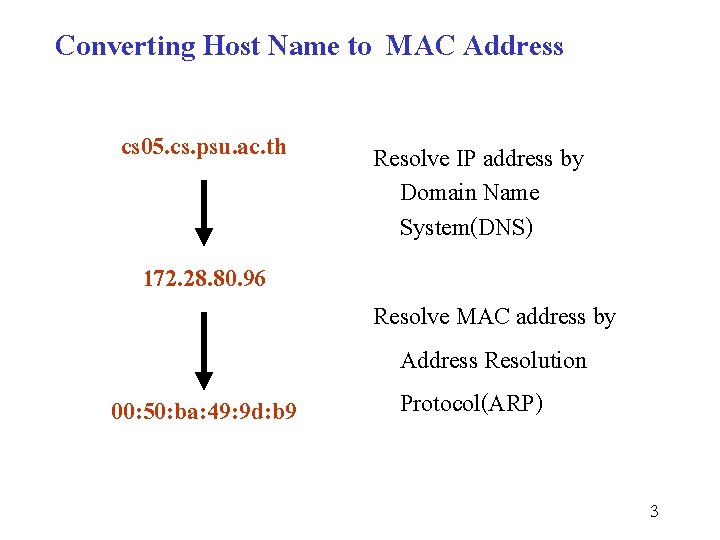
Converting Host Name to MAC Address cs 05. cs. psu. ac. th 172. 28. 80. 96 00: 50: ba: 49: 9 d: b 9 Resolve IP address by Domain Name System(DNS) Resolve MAC address by Address Resolution Protocol(ARP) 3

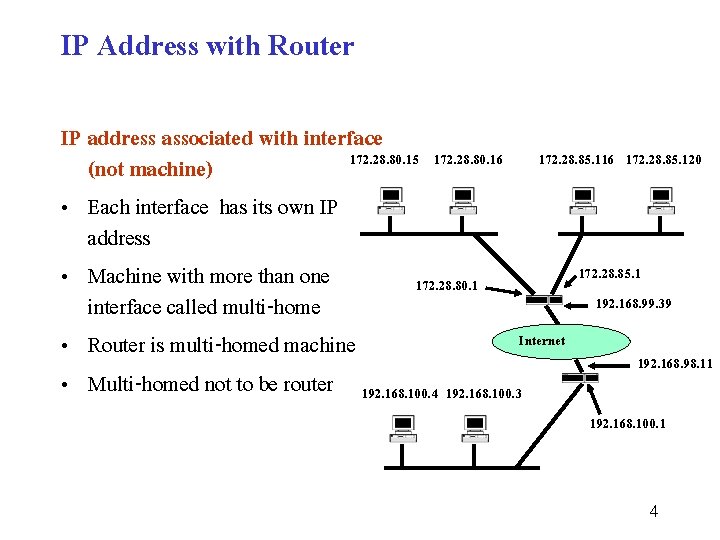
IP Address with Router IP address associated with interface 172. 28. 80. 15 172. 28. 80. 16 172. 28. 85. 120 (not machine) • Each interface has its own IP address 172. 28. 85. 1 • Machine with more than one 172. 28. 80. 1 192. 168. 99. 39 interface called multi-home Internet • Router is multi-homed machine 192. 168. 98. 11 • Multi-homed not to be router 192. 168. 100. 4 192. 168. 100. 3 192. 168. 100. 1 4

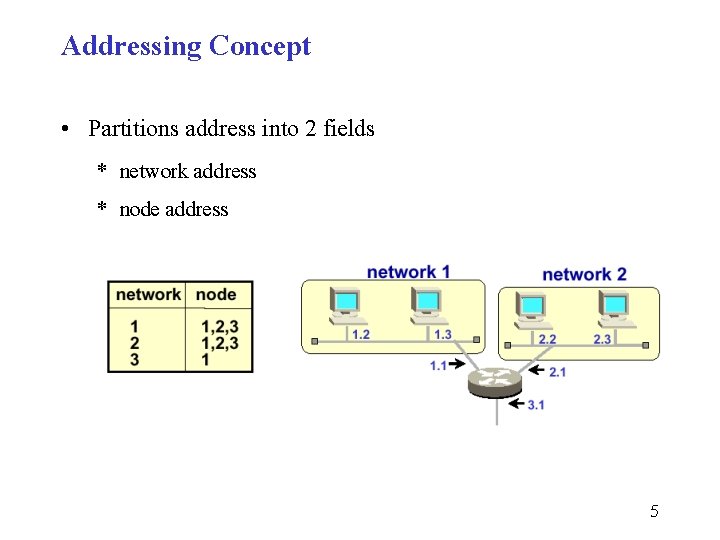
Addressing Concept • Partitions address into 2 fields * network address * node address 5

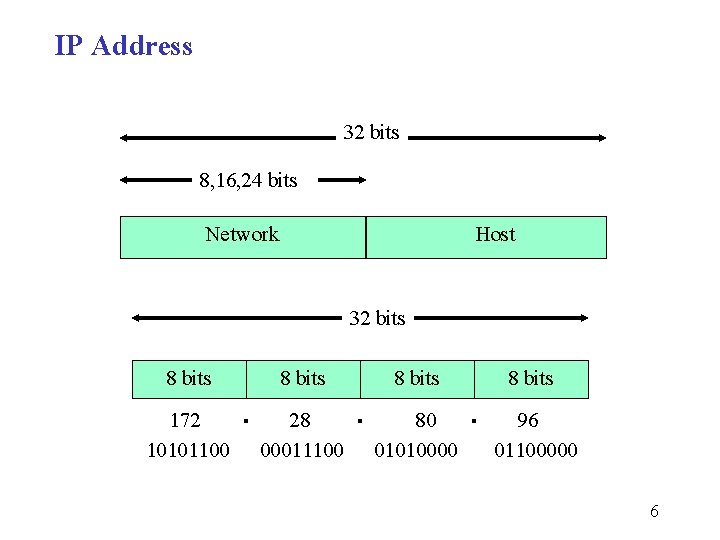
IP Address 32 bits 8, 16, 24 bits Network Host 32 bits 8 bits 172 28 80 10101100 00011100 01010000 . . . 8 bits 96 01100000 6

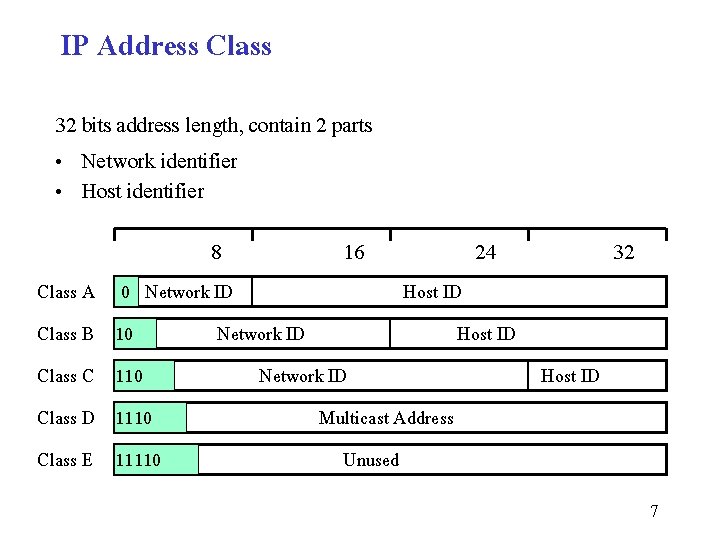
IP Address Class 32 bits address length, contain 2 parts • Network identifier • Host identifier Class A Class B Class C Class D 8 16 24 0 Network ID Host ID 110 Network ID Host ID 1110 Multicast Address Class E 11110 32 Unused 7

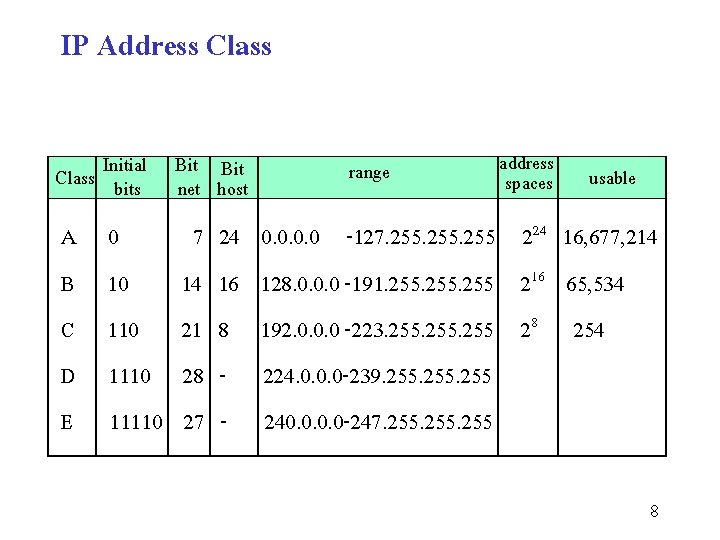
IP Address Class Initial Bit Class bits net host A B C D E 0 10 1110 11110 7 14 21 28 27 24 16 8 - range address spaces usable 0. 0 -127. 255 224 16, 677, 214 128. 0. 0. 0 -191. 255 216 65, 534 192. 0. 0. 0 -223. 255 28 254 224. 0. 0. 0 -239. 255 240. 0 -247. 255 8

Special Address • Host ID “all 0 s” is reserved to refer to network number – 18. 0. 0. 0 , 158. 108. 0. 0 , 192. 168. 100. 0 • Host ID “all 1 s” is reserved to broadcast to all hosts on a specific network – 18. 255 , 158. 108. 255 , 192. 168 • Address 0. 0 means “default route” • Address 127. 0. 0. 0 means “this node” (local loopback). Message sent to this address will never leave the local host • Address 255 is reserve to broadcast to every host on the local network (limited broadcast( 9

Private Address Reserve for Intranet or private network • 10. 0 – 10. 255 (1 class A ) • 172. 16. 0. 0 – 172. 31. 255 (16 class B) • 192. 168. 0. 0 – 192. 128. 255 (256 class C) 10

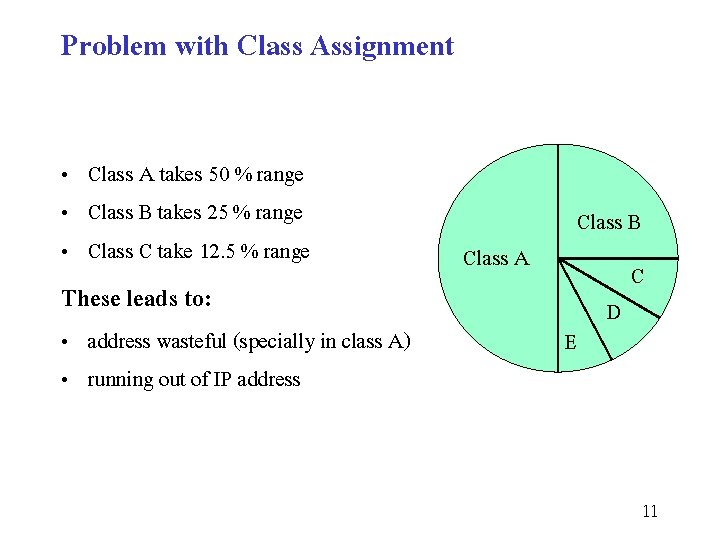
Problem with Class Assignment • Class A takes 50 % range • Class B takes 25 % range • Class C take 12. 5 % range These leads to: • address wasteful (specially in class A) • running out of IP address Class A Class B E D C 11

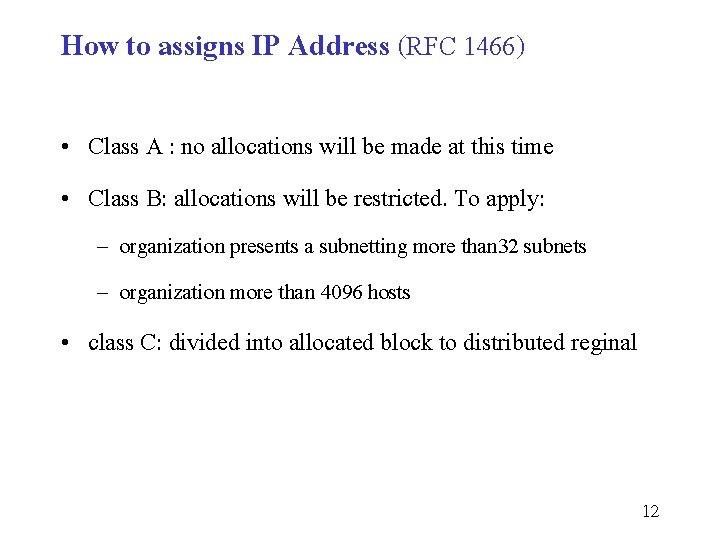
How to assigns IP Address (RFC 1466) • Class A : no allocations will be made at this time • Class B: allocations will be restricted. To apply: – organization presents a subnetting more than 32 subnets – organization more than 4096 hosts • class C: divided into allocated block to distributed reginal 12

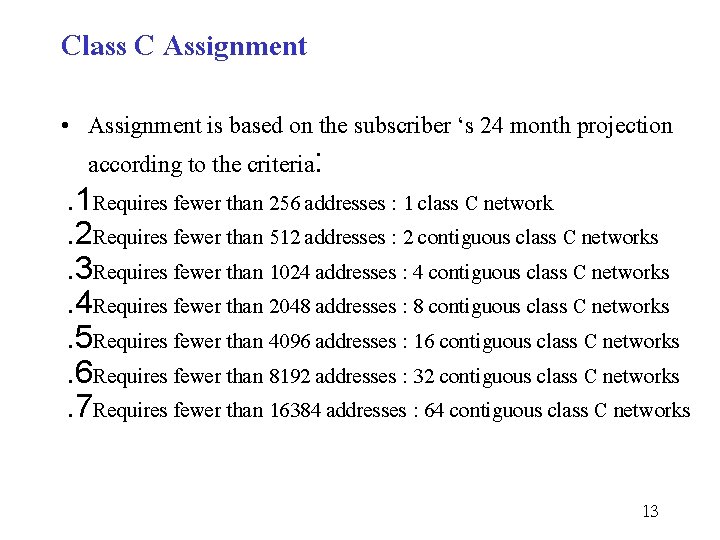
Class C Assignment • Assignment is based on the subscriber ‘s 24 month projection according to the criteria: . 1 Requires fewer than 256 addresses : 1 class C network. 2 Requires fewer than 512 addresses : 2 contiguous class C networks. 3 Requires fewer than 1024 addresses : 4 contiguous class C networks. 4 Requires fewer than 2048 addresses : 8 contiguous class C networks. 5 Requires fewer than 4096 addresses : 16 contiguous class C networks. 6 Requires fewer than 8192 addresses : 32 contiguous class C networks. 7 Requires fewer than 16384 addresses : 64 contiguous class C networks 13

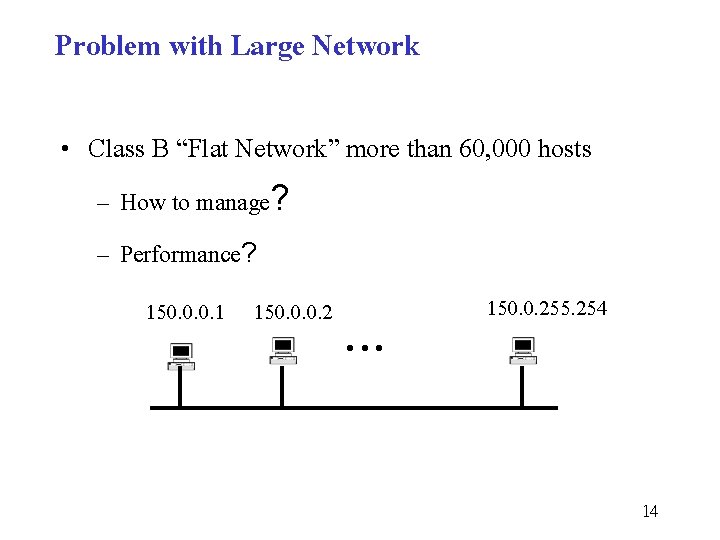
Problem with Large Network • Class B “Flat Network” more than 60, 000 hosts – How to manage? – Performance? 150. 0. 0. 1 150. 0. 0. 2 . . . 150. 0. 255. 254 14

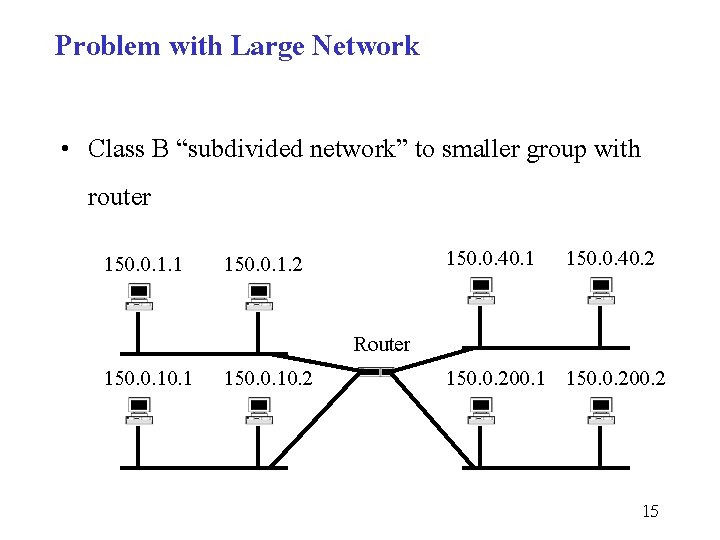
Problem with Large Network • Class B “subdivided network” to smaller group with router 150. 0. 1. 1 150. 0. 40. 2 150. 0. 10. 1 150. 0. 10. 2 Router 150. 0. 200. 1 150. 0. 200. 2 15

Subnetwork Benefits • • Increase the network manager’s control the address space Easy to allocate the address space Better network performance Hide routing structure from remote routers, thus reducing routes in their routing tables • Subdivide on IP network number is an important initial task of network managers 16

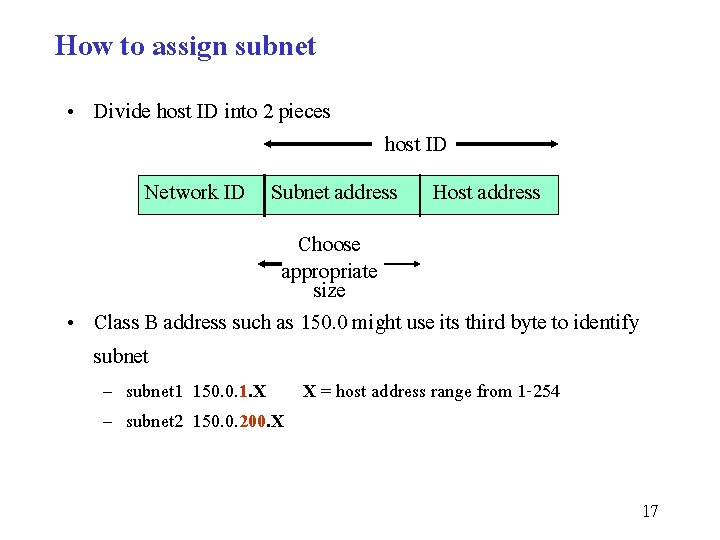
How to assign subnet • Divide host ID into 2 pieces host ID Network ID Subnet address Host address Choose appropriate size • Class B address such as 150. 0 might use its third byte to identify subnet – subnet 1 150. 0. 1. X X = host address range from 1 -254 – subnet 2 150. 0. 200. X 17

Subnet Mask • 32 bit number, tell router to recognize the subnet field, call subnet mask • subnet rule: The bit covering the network and subnet part of address are set to 1 • Example class B with 24 bits mask 1111 1111 0000 subnet mask = 255. 0 * zero bit are used to mask out the host number resulting the network address 18

Subnet Mask Subnet mask 255. 0 for class B tells: • network has been partition to 254 subnets. 150. 1 X to 150. 10. 254. X • logic “and” between IP address with mask yields network address 150. 10. 243150. 1. 55 and 255. 0255. 0. 150. 101. 0 150. 10. 240. 0 19

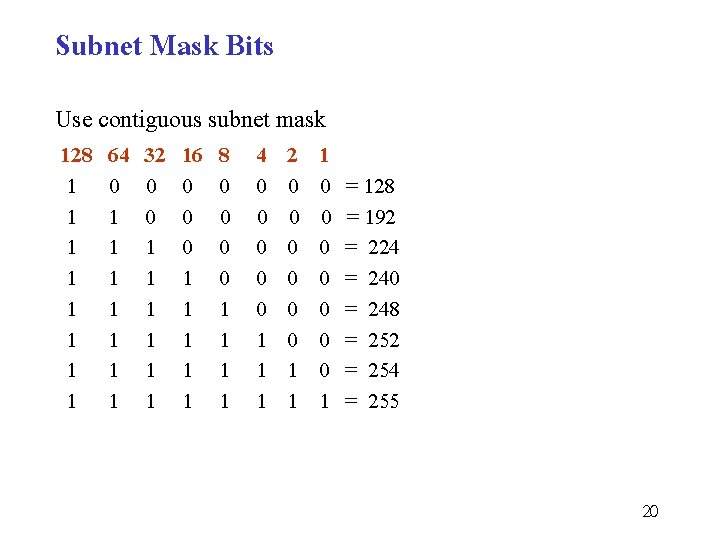
Subnet Mask Bits Use contiguous subnet mask 128 1 1 1 1 64 0 1 1 1 1 32 0 0 1 1 1 16 0 0 0 1 1 1 8 0 0 1 1 4 0 0 0 1 1 1 2 0 0 0 1 1 1 0 0 0 0 1 = 128 = 192 = 224 = 240 = 248 = 252 = 254 = 255 20

Subnet Class B Example • 255. 0. 0 (0000 0000) 0 subnet with 65534 hosts (default subnet) • 255. 192. 0 (1100 0000) 2 subnets with 16382 hosts • 255. 252. 0 (1111 1100 0000) 62 subnets with 1022 hosts • 255. 0 (1111 0000) 254 subnets with 254 hosts • 255. 252 (1111 11000) 16382 subnets with 2 hosts 21

Subnet Class C Example • 255. 0 ( 0000) 0 subnets with 254 hosts (default subnet) • 255. 192 (1100 0000) 2 subnets with 62 hosts • 255. 224 (1110 0000) 6 subnets with 30 hosts • 255. 240 (1111 0000) 14 subnets with 14 hosts 22

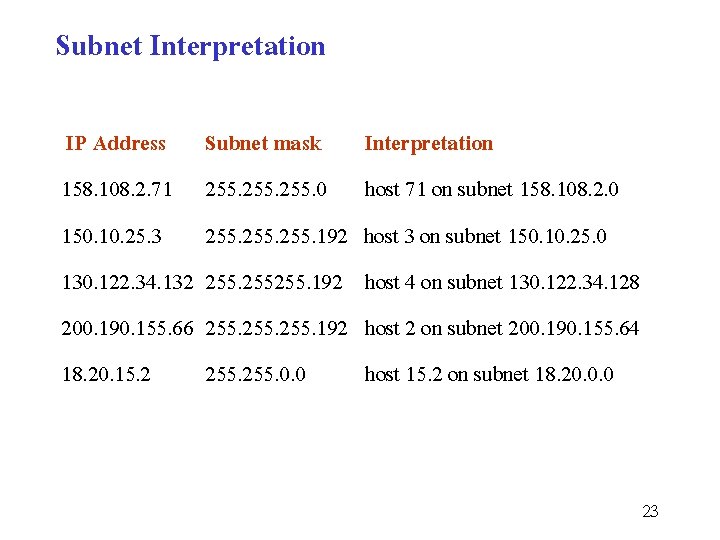
Subnet Interpretation IP Address 158. 108. 2. 71 150. 10. 25. 3 130. 122. 34. 132 200. 190. 155. 66 18. 20. 15. 2 Subnet mask 255. 0 255. 192 255. 0. 0 Interpretation host 71 on subnet 158. 108. 2. 0 host 3 on subnet 150. 10. 25. 0 host 4 on subnet 130. 122. 34. 128 host 2 on subnet 200. 190. 155. 64 host 15. 2 on subnet 18. 20. 0. 0 23

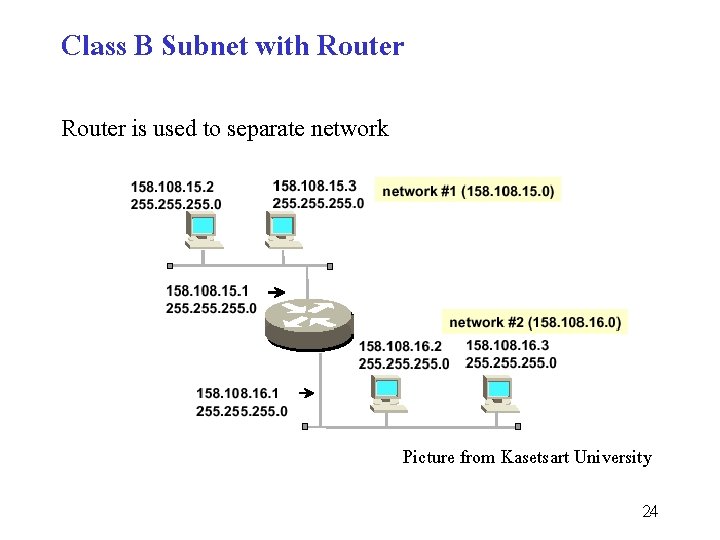
Class B Subnet with Router is used to separate network Picture from Kasetsart University 24

Subnet Routing Traffic is route to a host by looking “bit wise AND” results if dest IP addr & subnet mask = = my IP addr & subnet mask send packet on local network { dest IP addr is on the same subnet{ else send packet to router {dest IP address is on difference subnet{ 25

Type of Subnet • Static subnet: all subnets in the subnetted network use the same subnet mask – pros: simply to implement, easy to maintain – cons: wasted address space (consider a network of 4 hosts with 255. 0 wastes 250 IPs) • Variable Length Subnet : the subnets may use difference subnet masks – pros: utilize address space – cons: required well managment 26

Variable Length Subnet Mask • General idea of VLSM – A small subnet with only a few hosts needs a subnet mask that accommodate only few hosts – A subnet with many hosts need a subnet mask to accomdate the large number of hosts • Network Manager’s responsibility to design and appropriate VLSM 27

VLSM Sample Case Picture from Kasetsart university 28

CIDR Classless Inter-Domain Routing 29

Address Allocation Problem • Exhaustion of the class B network address space • The lack of a network class of size which is appropriate for mid-sizes organization – class C, with a max of 254 hosts, too small – While class B, with a max of 65534 hosts, too large • Allocate block of class C instead and downside is more routes entry in routing table 30

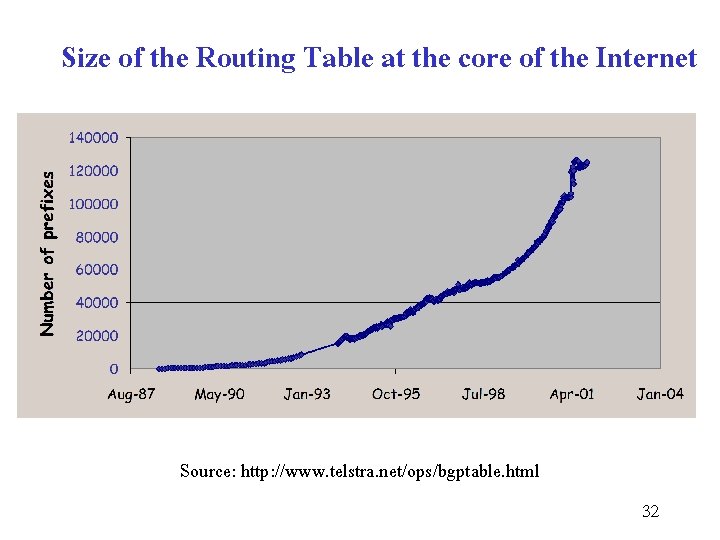
Routing Table Problems • Issue multiple block class C addresses (instead single class B address) solves a running out of class B address • Introduces problems of routing table – By default, a routing table contains an entry for every network – How large a routing table should be for all class C networks? • Growth of routing table in the internet routers beyond the ability of current software and hardware manage 31

Size of the Routing Table at the core of the Internet Source: http: //www. telstra. net/ops/bgptable. html 32

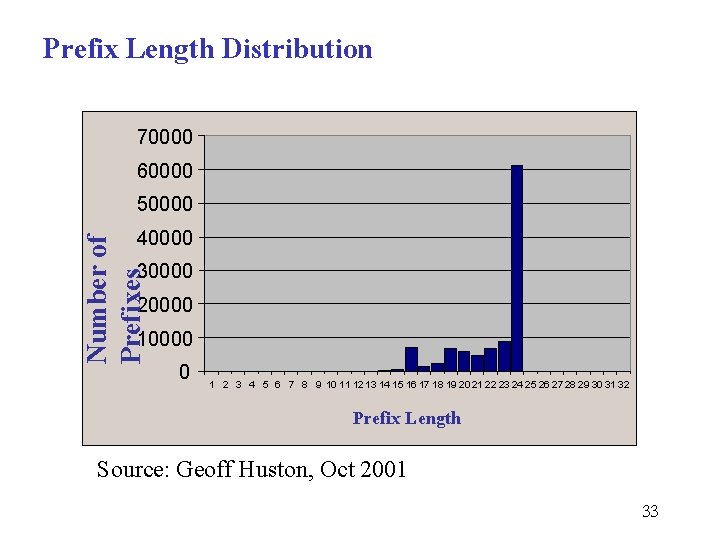
Prefix Length Distribution 70000 60000 50000 Number of Prefixes 40000 30000 20000 10000 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 Prefix Length Source: Geoff Huston, Oct 2001 33

How to solve • Topological allocate IP address assignment • We divide the world into 8 regions (RFC 1466) Multi regional 192. 0. 0. 0 - 193. 255 Europe 194. 0. 0. 0 - 195. 255 Others 196. 0. 0. 0 - 197. 255 North America 198. 0. 0. 0 - 199. 255 Central/South America 200. 0 - 201. 255 Pacific Rim 202. 0. 0. 0 - 203. 255 Others 204. 0. 0. 0 - 205. 255 Others 206. 0. 0. 0 - 207. 255 IANA Reserved 208. 0. 0. 0 - 223. 255 34

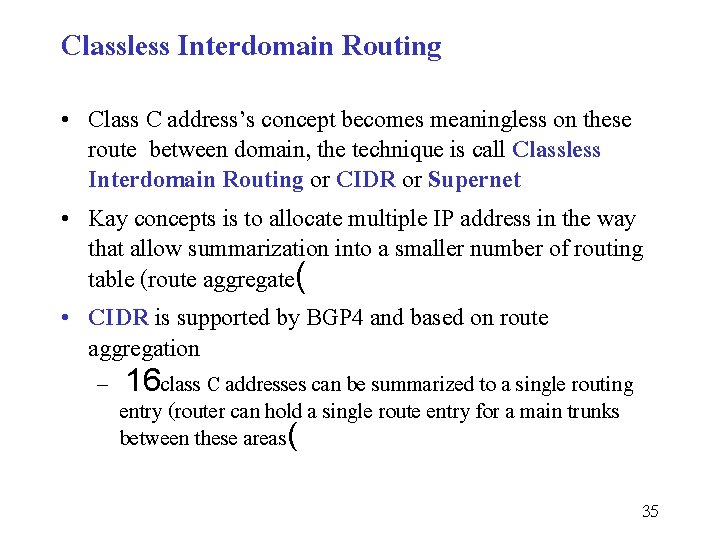
Classless Interdomain Routing • Class C address’s concept becomes meaningless on these route between domain, the technique is call Classless Interdomain Routing or CIDR or Supernet • Kay concepts is to allocate multiple IP address in the way that allow summarization into a smaller number of routing table (route aggregate( • CIDR is supported by BGP 4 and based on route aggregation – 16 class C addresses can be summarized to a single routing entry (router can hold a single route entry for a main trunks between these areas( 35

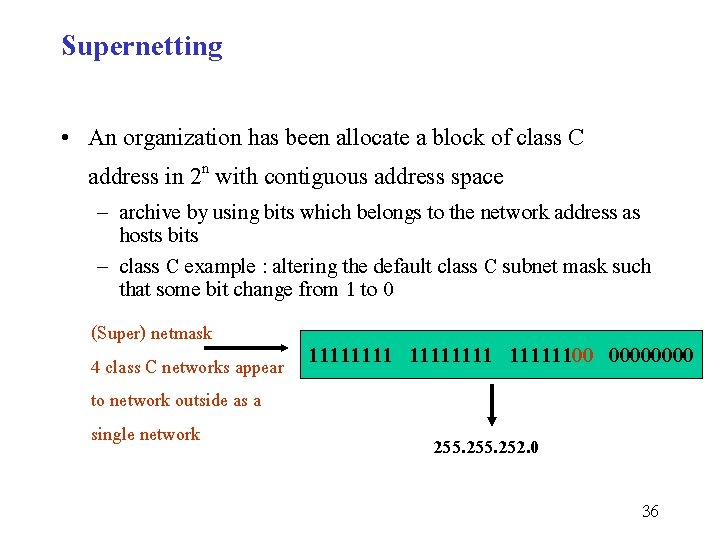
Supernetting • An organization has been allocate a block of class C address in 2 n with contiguous address space – archive by using bits which belongs to the network address as hosts bits – class C example : altering the default class C subnet mask such that some bit change from 1 to 0 (Super) netmask 4 class C networks appear 1111111100 0000 to network outside as a single network 255. 252. 0 36

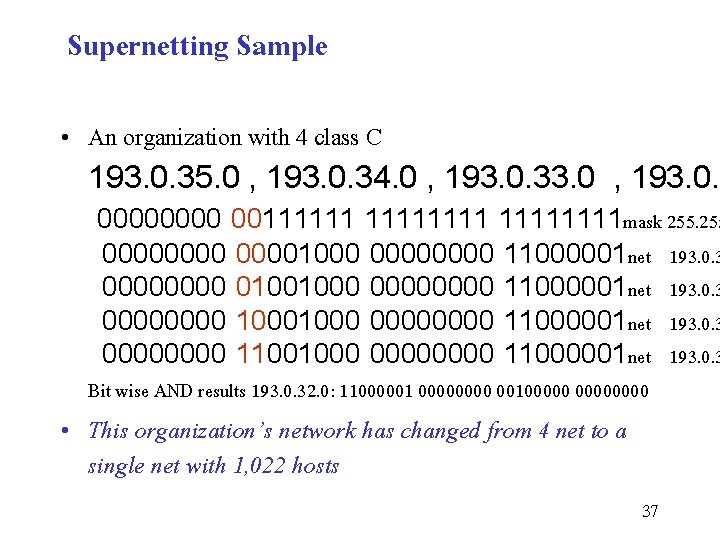
Supernetting Sample • An organization with 4 class C 193. 0. 35. 0 , 193. 0. 34. 0 , 193. 0. 33. 0 , 193. 0. 3 0000 0011111111 mask 255 00001000 0000 11000001 net 193. 0. 3 0000 01001000 0000 11000001 net 193. 0. 3 0000 11001000 0000 11000001 net 193. 0. 3 Bit wise AND results 193. 0. 32. 0: 11000001 0000 00100000 • This organization’s network has changed from 4 net to a single net with 1, 022 hosts 37

The longest Match Supernetting • Europe has 194. 0. 0. 0 - 195. 255 with mask 254. 0. 0. 0 • A case of one organization (195. 0. 16. 0 - 195. 0. 36. 0 mask 255. 254. 0) needs different routing entry • datagrams 195. 0. 20. 1 matches both Europe’s and this organization. How to do? • Routing mechanism selects the longest mask (255. 254. 0 is longer than 254. 0. 0. 0), then route to the organization 38

Summary • Routing decisions are now made based on masking operations of the entries 32 bits address, hence the term “classes” • No existing routes is changed • CIDR slows down the growth of routing tables (current 130 K entries in core routers) • Short term solution to solve routing problem • limitation: not all host/router software allows supernet mask 39

IPv 6 40

IPv 4’s Limitations • • Two driving factors : addressing and routing Addressing : address depletion concerns – Internet exhaust the IPv 4 address space between 2005 and 2011 [RFC 1752]. Routing : routing table explosion – Currently ~120 K entries in core router More factors. . . – Opportunity to optimized on many years of deployment experience – New features needed : multimedia, security, mobile, etc. . 41

Key Issues The new protocol MUST • Support large global internetworks • A clear way to transition IPv 4 based networks 42

What is IPv 6? • IPv 6 is short for "Internet Protocol Version 6. " • IPv 6 is the "next generation" protocol designed by the IETF to replace the current version Internet Protocol, IP Version 4 43

IPV 6 Key Advantages • • 128 bit fix length IP address Real time support Self-configuration of workstations or auto configuration Security features Support mobile workstations Protocol remains the same principle IPv 4 compatibility 44

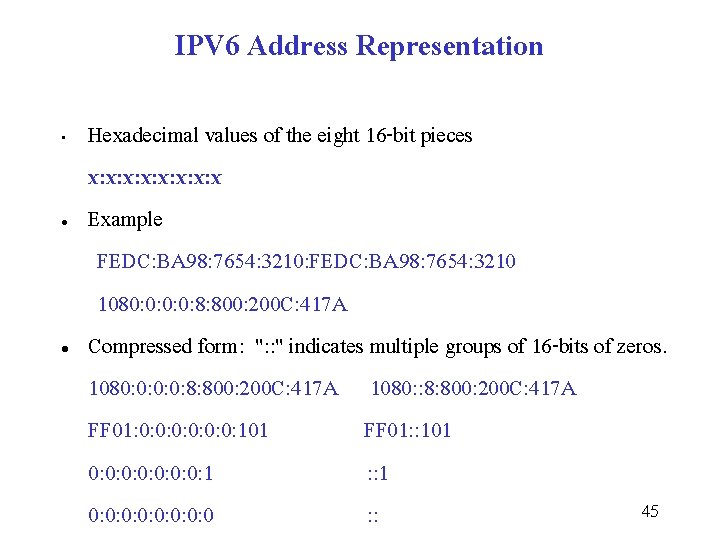
IPV 6 Address Representation • l l Hexadecimal values of the eight 16 -bit pieces x: x: x Example FEDC: BA 98: 7654: 3210: FEDC: BA 98: 7654: 3210 1080: 0: 8: 800: 200 C: 417 A Compressed form: ": : " indicates multiple groups of 16 -bits of zeros. 1080: 0: 8: 800: 200 C: 417 A 1080: : 8: 800: 200 C: 417 A FF 01: 0: 0: 0: 101 FF 01: : 101 0: 0: 1 : : 1 45 0: 0: 0 : :

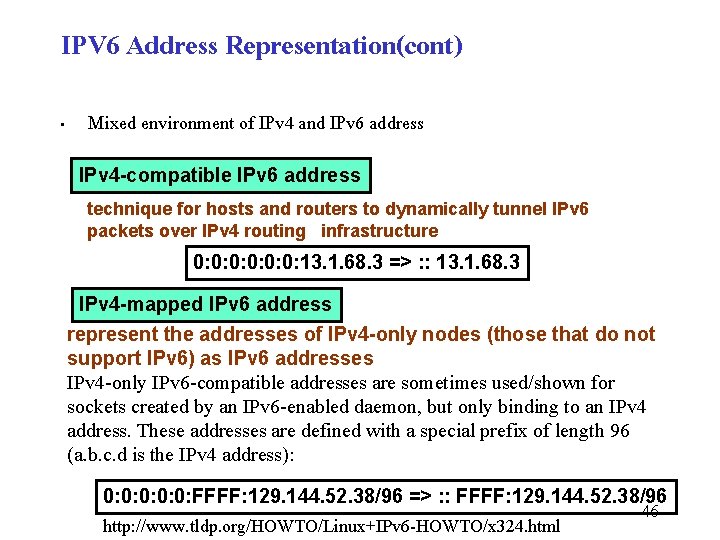
IPV 6 Address Representation(cont) • Mixed environment of IPv 4 and IPv 6 address IPv 4 -compatible IPv 6 address technique for hosts and routers to dynamically tunnel IPv 6 packets over IPv 4 routing infrastructure 0: 0: 0: 13. 1. 68. 3 => : : 13. 1. 68. 3 IPv 4 -mapped IPv 6 address represent the addresses of IPv 4 -only nodes (those that do not support IPv 6) as IPv 6 addresses IPv 4 -only IPv 6 -compatible addresses are sometimes used/shown for sockets created by an IPv 6 -enabled daemon, but only binding to an IPv 4 address. These addresses are defined with a special prefix of length 96 (a. b. c. d is the IPv 4 address): 0: 0: 0: FFFF: 129. 144. 52. 38/96 => : : FFFF: 129. 144. 52. 38/96 http: //www. tldp. org/HOWTO/Linux+IPv 6 -HOWTO/x 324. html 46

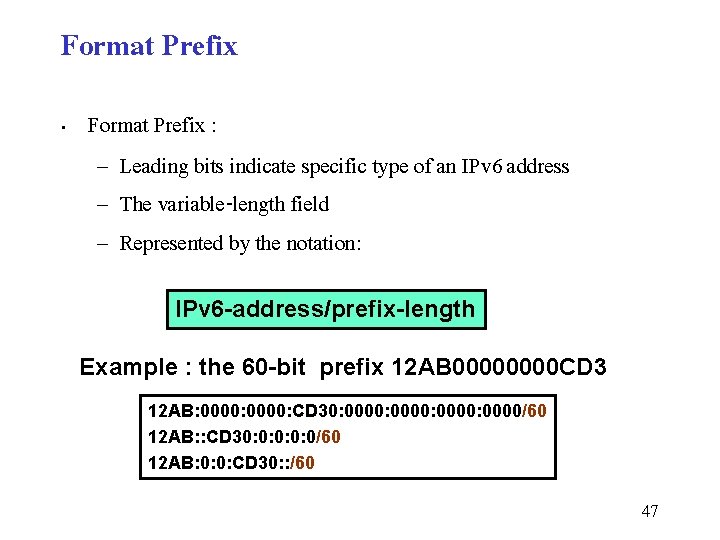
Format Prefix • Format Prefix : – Leading bits indicate specific type of an IPv 6 address – The variable-length field – Represented by the notation: IPv 6 -address/prefix-length Example : the 60 -bit prefix 12 AB 0000 CD 3 12 AB: 0000: CD 30: 0000: 0000/60 12 AB: : CD 30: 0: 0/60 12 AB: 0: 0: CD 30: : /60 47

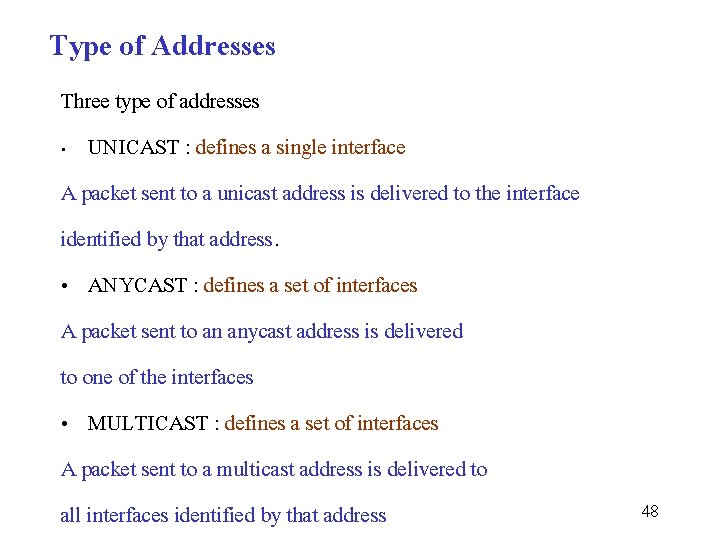
Type of Addresses Three type of addresses • UNICAST : defines a single interface A packet sent to a unicast address is delivered to the interface identified by that address. • ANYCAST : defines a set of interfaces A packet sent to an anycast address is delivered to one of the interfaces • MULTICAST : defines a set of interfaces A packet sent to a multicast address is delivered to all interfaces identified by that address 48

Address Types • Unspecified address, 0: 0: 0 or : : • Loopback address, 0: 0: 1 of : : 1 • Global address, 2000: : /3 and E 000: : /3 currently only 2000: : /3 is being assigned • Link local address, FE 80: : /64 • Site local address, FEC 0: : /10 49

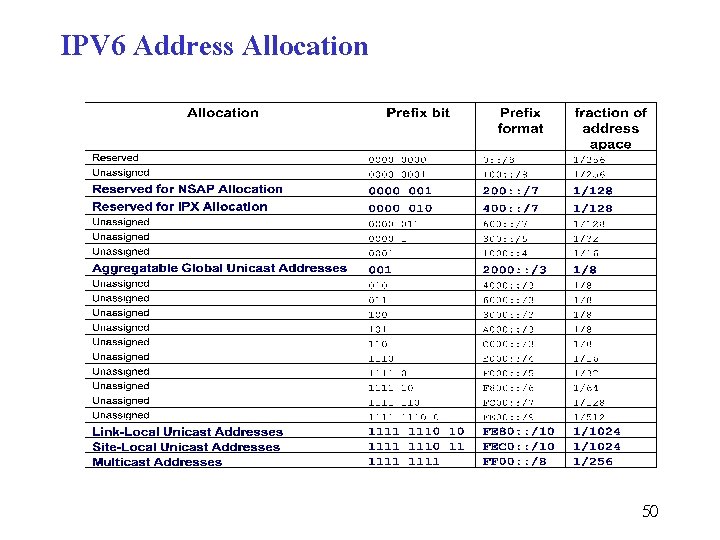
IPV 6 Address Allocation 50

Address Registries Address registries for IPv 6 are the same one as for IPv 4, ARIN, RIPE and APNIC. • Only large network providers will ever obtain addresses directly from the registries, such as UNINET : one such provider in Thailand • If a /35 prefix is allocates, the registry internally will reserve a /32. • The basic unit of assignment to any organization is a /48 prefix 51

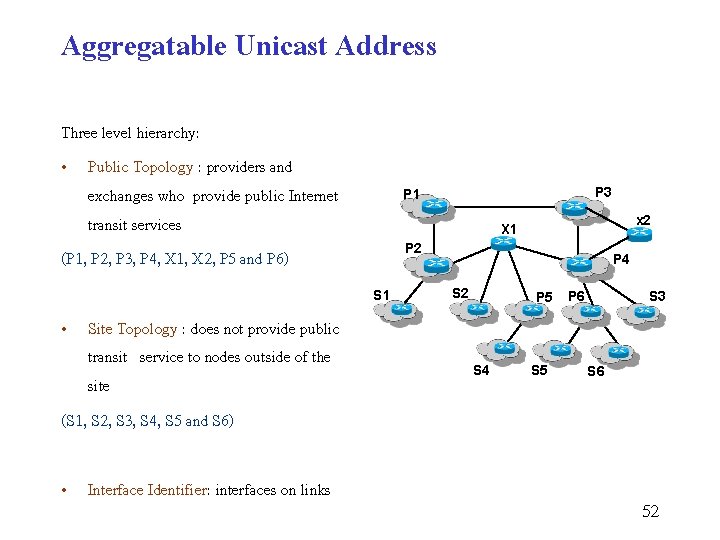
Aggregatable Unicast Address Three level hierarchy: • Public Topology : providers and exchanges who provide public Internet transit services (P 1, P 2, P 3, P 4, X 1, X 2, P 5 and P 6) • Interface Identifier: interfaces on links x 2 X 1 P 2 S 1 • Site Topology : does not provide public transit service to nodes outside of the site (S 1, S 2, S 3, S 4, S 5 and S 6) P 3 P 1 P 4 S 2 P 5 S 4 S 5 P 6 S 3 S 6 52

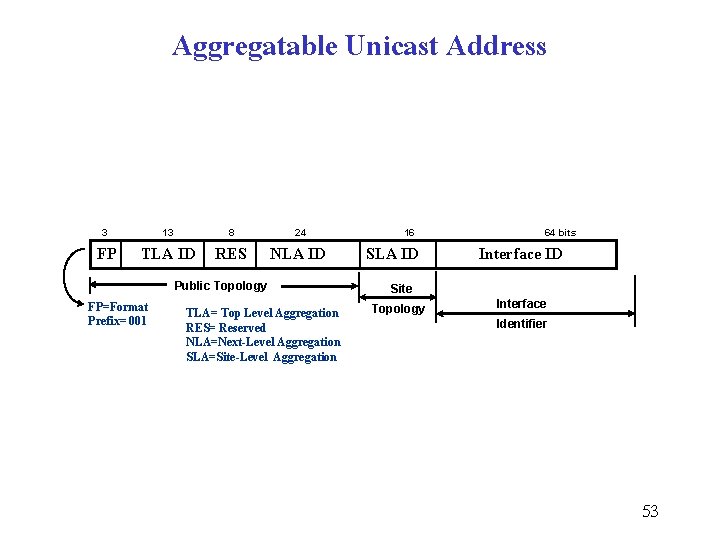
Aggregatable Unicast Address 3 13 8 24 FP TLA ID RES NLA ID Public Topology FP=Format Prefix= 001 TLA= Top Level Aggregation RES= Reserved NLA=Next-Level Aggregation SLA=Site-Level Aggregation 16 SLA ID 64 bits Interface ID Site Topology Interface Identifier 53

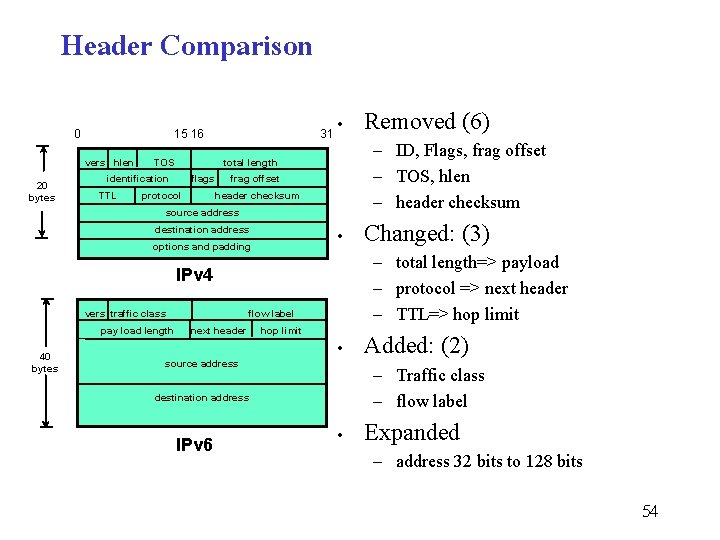
Header Comparison 0 15 16 vers hlen 20 bytes TOS • flags protocol frag offset header checksum source address destination address • options and padding pay load length 40 bytes flow label next header hop limit • source address Added: (2) – Traffic class – flow label destination address IPv 6 Changed: (3) – total length=> payload – protocol => next header – TTL=> hop limit IPv 4 vers traffic class Removed (6) – ID, Flags, frag offset – TOS, hlen – header checksum total length identification TTL 31 • Expanded – address 32 bits to 128 bits 54

IPv 6 Node Configuration • Ethernet address is an IEEE EUI-48 • Node address is an IEEE EUI-64 • EUI-48 can be converted into an EUI-64 by inserting the bits FF FE between the 3 rd and 4 th octets EUI-48 EUI-64 00: 06: 5 B: DA: 45: AD = 00: 06: 5 B: FF: FE: DA: 45: AD 55

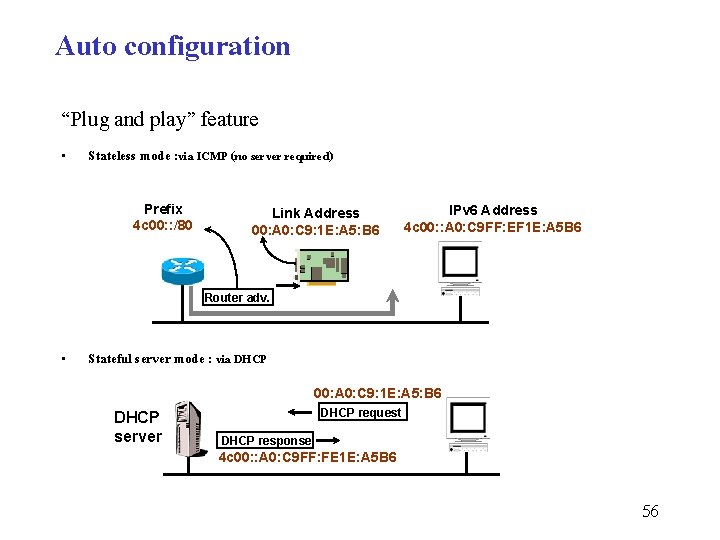
Auto configuration “Plug and play” feature • Stateless mode : via ICMP (no server required) Prefix 4 c 00: : /80 Link Address 00: A 0: C 9: 1 E: A 5: B 6 IPv 6 Address 4 c 00: : A 0: C 9 FF: EF 1 E: A 5 B 6 Router adv. • Stateful server mode : via DHCP 00: A 0: C 9: 1 E: A 5: B 6 DHCP server DHCP request DHCP response 4 c 00: : A 0: C 9 FF: FE 1 E: A 5 B 6 56

Security • • Authentication/Confidential Authentication: – MD 5 based • Confidential : – payload encryption – Cipher Block Chaining mode of the Data Encryption Standard (DESCBC) 57
![Support Protocols ICMPv 6 RFC 1885 DHCPv 6 DNS extensions to support Support Protocols • • ICMPv 6 [RFC 1885] DHCPv 6 DNS extensions to support](https://slidetodoc.com/presentation_image_h2/b64136b03d6cba1cf05b18028214e088/image-58.jpg)
Support Protocols • • ICMPv 6 [RFC 1885] DHCPv 6 DNS extensions to support IPv 6 [RFC 1886] Routing Protocols – – – RIPv 6 [RFC 2080] OSPFv 6 IDRP IS-IS Cisco EIGRP 58

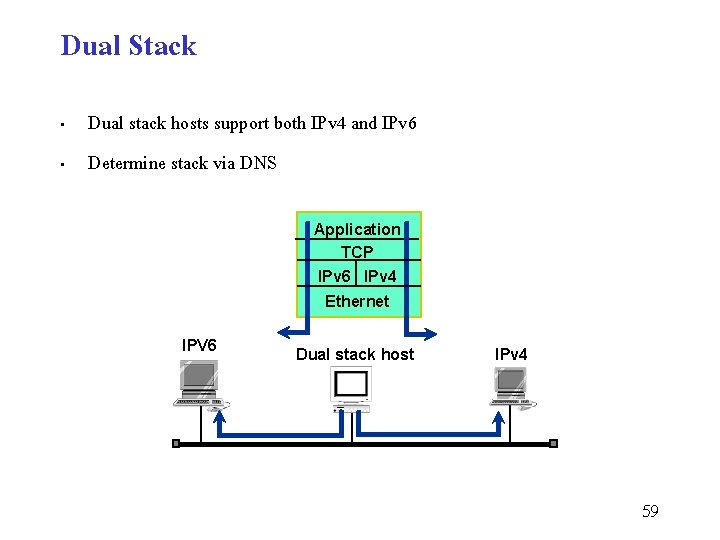
Dual Stack • • Dual stack hosts support both IPv 4 and IPv 6 Determine stack via DNS Application TCP IPv 6 IPv 4 Ethernet IPV 6 Dual stack host IPv 4 59

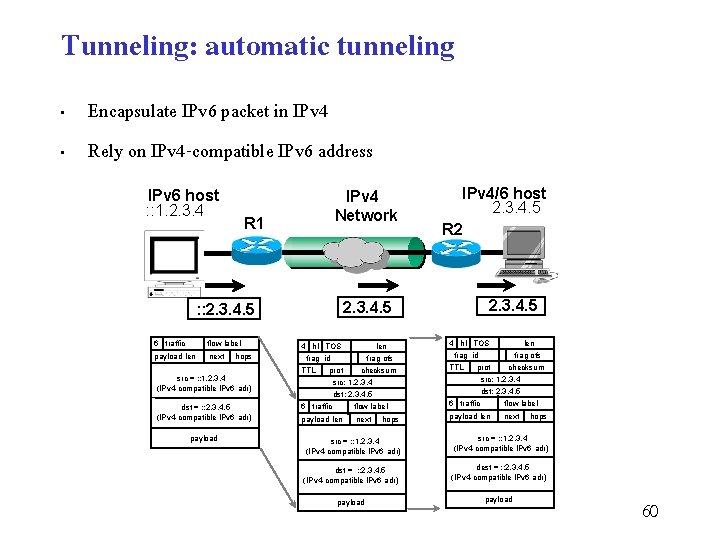
Tunneling: automatic tunneling • • Encapsulate IPv 6 packet in IPv 4 Rely on IPv 4 -compatible IPv 6 address IPv 6 host : : 1. 2. 3. 4 IPv 4 Network R 1 flow label payload len next hops src = : : 1. 2. 3. 4 (IPv 4 -compatible IPv 6 adr) dst = : : 2. 3. 4. 5 (IPv 4 -compatible IPv 6 adr) payload 2. 3. 4. 5 : : 2. 3. 4. 5 6 traffic IPv 4/6 host 2. 3. 4. 5 R 2 4 hl TOS frag id len frag ofs 4 hl TOS frag id prot checksum src: 1. 2. 3. 4 dst: 2. 3. 4. 5 6 traffic flow label TTL payload len TTL next hops len frag ofs prot checksum src: 1. 2. 3. 4 dst: 2. 3. 4. 5 6 traffic flow label next hops src = : : 1. 2. 3. 4 (IPv 4 -compatible IPv 6 adr) dst = : : 2. 3. 4. 5 (IPv 4 -compatible IPv 6 adr) dest = : : 2. 3. 4. 5 (IPv 4 -compatible IPv 6 adr) payload 60

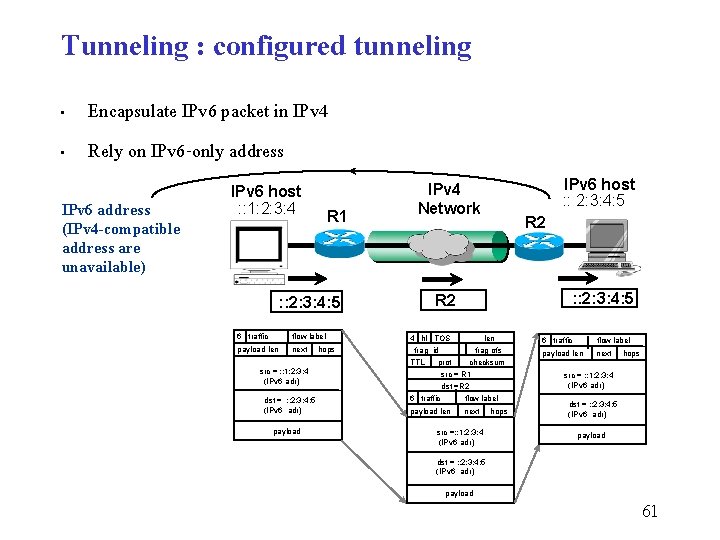
Tunneling : configured tunneling • • Encapsulate IPv 6 packet in IPv 4 Rely on IPv 6 -only address IPv 6 address (IPv 4 -compatible address are unavailable) IPv 6 host : : 1: 2: 3: 4 R 1 flow label payload len next hops R 2 : : 2: 3: 4: 5 6 traffic IPv 6 host : : 2: 3: 4: 5 IPv 4 Network 4 hl TOS frag id len frag ofs TTL src = : : 1: 2: 3: 4 (IPv 6 adr) dst = : : 2: 3: 4: 5 (IPv 6 adr) payload prot checksum src = R 1 dst =R 2 6 traffic flow label payload len next src =: : 1: 2: 3: 4 (IPv 6 adr) hops 6 traffic flow label payload len next hops src = : : 1: 2: 3: 4 (IPv 6 adr) dst = : : 2: 3: 4: 5 (IPv 6 adr) payload 61

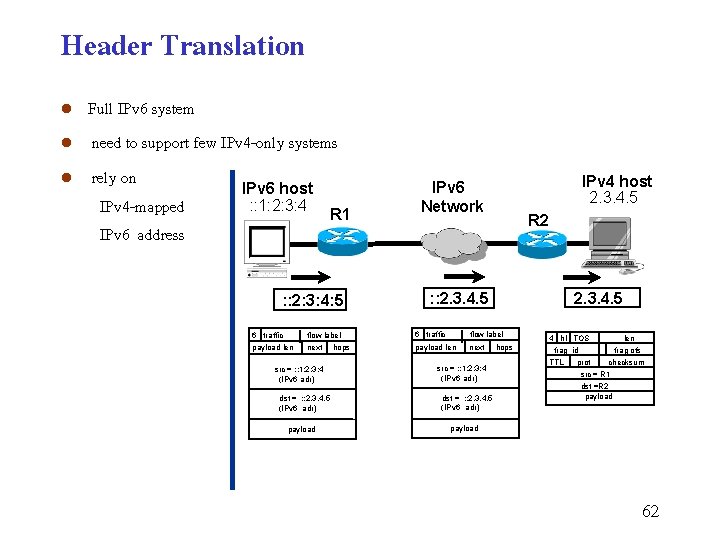
Header Translation l l l Full IPv 6 system need to support few IPv 4 -only systems rely on IPv 6 host : : 1: 2: 3: 4 IPv 4 -mapped R 1 IPv 6 address : : 2: 3: 4: 5 IPv 4 host 2. 3. 4. 5 IPv 6 Network R 2 2. 3. 4. 5 : : 2. 3. 4. 5 6 traffic flow label payload len next src = : : 1: 2: 3: 4 (IPv 6 adr) dst = : : 2. 3. 4. 5 (IPv 6 adr) payload hops src = : : 1: 2: 3: 4 (IPv 6 adr) dst = : : 2. 3. 4. 5 (IPv 6 adr) hops 4 hl TOS frag id TTL len frag ofs prot checksum src = R 1 dst =R 2 payload 62

Migration Steps 1. Upgrade DNS servers to handle IPv 6 Address 2. Introduce dual stack systems that support IPv 4 and IPv 6 3. Rely on tunnels to connect IPv 6 networks separated by IPv 4 networks 4. Remove support for IPv 4 5. Rely on header translation for IPv 4 -only systems 63

Conclusion • • IPv 6 will provide for future Internet growth and enhancement IPv 6 : – solve the Internet scaling problem – support large hierarchical address – provide a flexible transition mechanism – interoperate with IPv 4 – provide a platform for new Internet functionality 64
 Three address code
Three address code Physical address vs logical address
Physical address vs logical address Three address code
Three address code Contoh soal set instruksi 3 alamat
Contoh soal set instruksi 3 alamat Three address statement for boolean expression
Three address statement for boolean expression Three address code
Three address code Unit 7
Unit 7 Three address code for boolean expression
Three address code for boolean expression Three address code
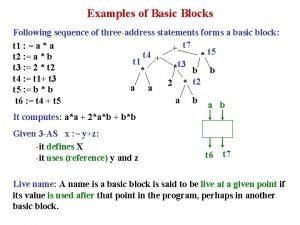
Three address code Basic block example
Basic block example Molecular level vs cellular level
Molecular level vs cellular level Isis level 1 vs level 2
Isis level 1 vs level 2 Dr shaffi
Dr shaffi Isis level 1 vs level 2
Isis level 1 vs level 2 What is the interpretation of a 96 confidence level
What is the interpretation of a 96 confidence level Confidence level and significance level
Confidence level and significance level Level 0 dfd
Level 0 dfd Level security
Level security Examples of level three questions
Examples of level three questions Thread-level parallelism
Thread-level parallelism Low-level thinking in high-level shading languages
Low-level thinking in high-level shading languages Grade 4 pfp
Grade 4 pfp Socratic seminar roles
Socratic seminar roles Level 3 questions examples
Level 3 questions examples Costa level 2 and 3 questions examples
Costa level 2 and 3 questions examples Level 3 questions
Level 3 questions Jim clawson
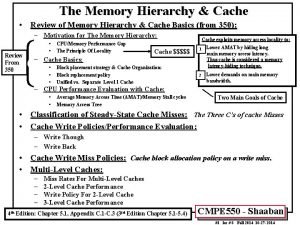
Jim clawson Three level cache organization
Three level cache organization 3 levels of biodiversity
3 levels of biodiversity Three level model of pollution management
Three level model of pollution management 3 hobbits
3 hobbits Othello act three scene three
Othello act three scene three In three minutes write
In three minutes write The purpose of traffic signs are
The purpose of traffic signs are The three colonial sections-one society or three
The three colonial sections-one society or three Glorck
Glorck Windows server 2008 ip address management
Windows server 2008 ip address management Writing a letter parts
Writing a letter parts Explain how dishes on a menu address environmental issues.
Explain how dishes on a menu address environmental issues. How to write address in informal letter
How to write address in informal letter Process virtual address space
Process virtual address space Virtual address space
Virtual address space Process virtual address space
Process virtual address space Mary give me tony's address before she left
Mary give me tony's address before she left Last line of a letter
Last line of a letter Literary allusion lead
Literary allusion lead Royal surrey hospital buses
Royal surrey hospital buses Ad in microprocessor
Ad in microprocessor Katrina flood map by address
Katrina flood map by address Osi model layers
Osi model layers Assonance in jfk inaugural address
Assonance in jfk inaugural address Assessing grammar effectively
Assessing grammar effectively Subnet 172
Subnet 172 Subnetting kelas c /28
Subnetting kelas c /28 Mac address format
Mac address format How to write address on letter
How to write address on letter Nslsc mailing address
Nslsc mailing address School telephone number
School telephone number Import address table
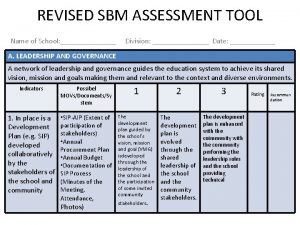
Import address table Sbm assessment tool 2020 excel
Sbm assessment tool 2020 excel Actions to address risks and opportunities
Actions to address risks and opportunities Windows virtual address space
Windows virtual address space Anecdotes persuasive techniques
Anecdotes persuasive techniques Image_thunk_data
Image_thunk_data What is a cosmic address
What is a cosmic address