PE Format Guo Yu Computer virus Outline PE





![Relocation • Direct Memory Address – call dword ptr [0 x 00401152] – mov Relocation • Direct Memory Address – call dword ptr [0 x 00401152] – mov](https://slidetodoc.com/presentation_image_h2/a82188433970f4c028578a82b7dd93f4/image-13.jpg)




![Per Section Header • Name[8] – “. text” “. data” “. idata” – “. Per Section Header • Name[8] – “. text” “. data” “. idata” – “.](https://slidetodoc.com/presentation_image_h2/a82188433970f4c028578a82b7dd93f4/image-32.jpg)


![Programming DWORD dw. RVAImp. Tbl = p. Opt. Header->Data. Directory[1]. Virtual. Address; DWORD dw. Programming DWORD dw. RVAImp. Tbl = p. Opt. Header->Data. Directory[1]. Virtual. Address; DWORD dw.](https://slidetodoc.com/presentation_image_h2/a82188433970f4c028578a82b7dd93f4/image-50.jpg)











- Slides: 85

PE Format Guo Yu Computer virus

Outline • PE Overview • PE Structure Header • Import Table • Export Table • Base Relocation Table • Resource Table • Virus Techniques Computer virus

PE Overview • PE files are derived from the Common Object File Format (COFF) found on VAX/VMS • Why “Portable” ? – versatility in numerous environments of operating system software architecture. • x 86, MIPS®, Alpha • NT Team (from Digital) Computer virus

PE Overview • EXE, DLL, SYS, CPL • Windows Kernel – ntoskrnl. exe • . NET framework support Computer virus

Why Learn PE Format • PE structures everywhere – EXE, DLL files in hard-disks – Modules in process memory space • Loaded from PE files • PE structures support dynamic loading and dynamic linking – User process memory space – Kernel memory space • Kernel image and various device drivers Computer virus

Utilities • Hex file viewer (tools) – – – Ultra-editor (not free) Win. Hex (not free) HT Editor, http: //hte. sourceforge. net/ BIEW, http: //biew. sourceforge. net/en/biew. html Hiew, http: //www. hiew. ru/ • Static PE files viewer – PE Explorer (not free) – Lord. PE (free) – Stud_PE (free) , http: //www. cgsoftlabs. ro/ • Dynamic PE images viewer – Ollydbg (free), http: //www. ollydbg. de/ – Soft. ICE (not free) Computer virus

Example • hello. exe Computer virus

PE Structure: Overview Computer virus

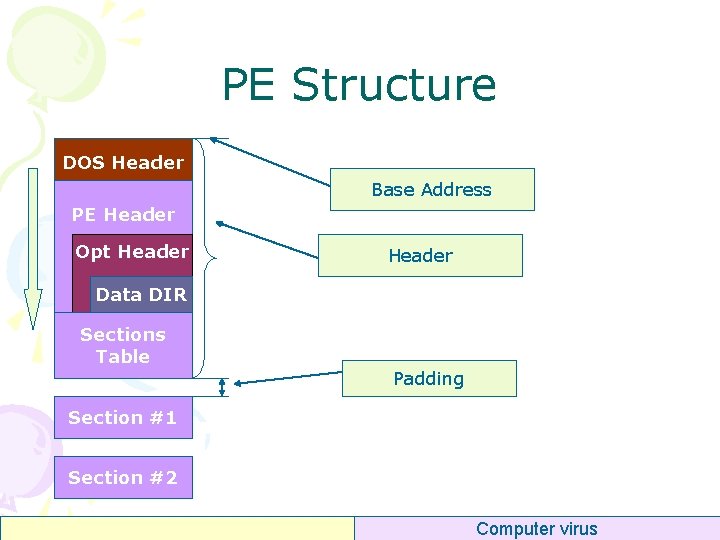
PE Structure DOS Header Base Address PE Header Opt Header Data DIR Sections Table Padding Section #1 Section #2 Computer virus

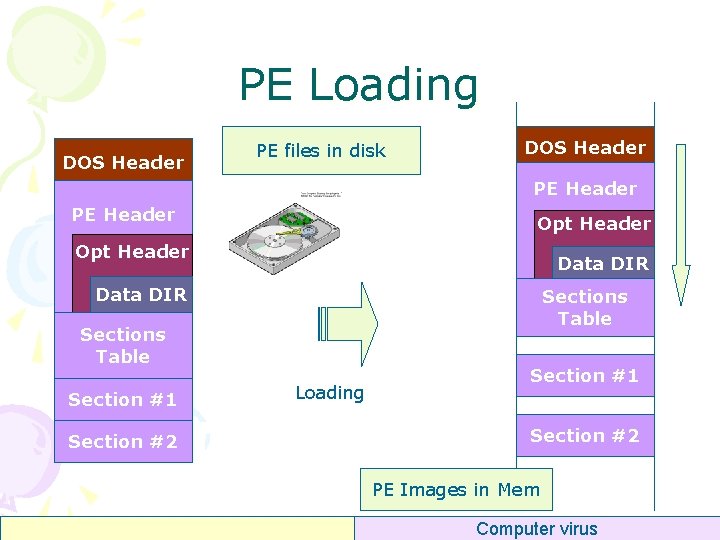
PE Loading DOS Header PE files in disk DOS Header PE Header Opt Header Data DIR Sections Table Section #1 Section #2 Loading Section #1 Section #2 PE Images in Mem Computer virus

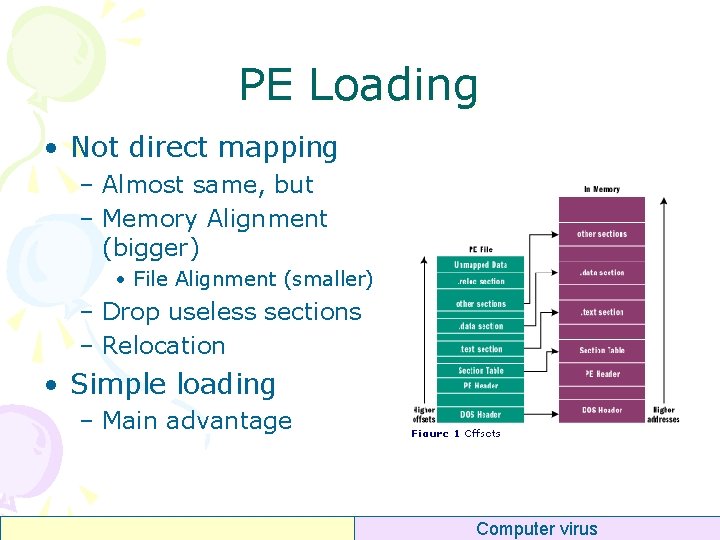
PE Loading • Not direct mapping – Almost same, but – Memory Alignment (bigger) • File Alignment (smaller) – Drop useless sections – Relocation • Simple loading – Main advantage Computer virus

Relocation • Quiz – Why need relocation? Computer virus
![Relocation Direct Memory Address call dword ptr 0 x 00401152 mov Relocation • Direct Memory Address – call dword ptr [0 x 00401152] – mov](https://slidetodoc.com/presentation_image_h2/a82188433970f4c028578a82b7dd93f4/image-13.jpg)
Relocation • Direct Memory Address – call dword ptr [0 x 00401152] – mov eax, dword ptr [00401300] • If the base address of a PE image is not 0 x 00400000 – Then we need relocation actions – Why the base address can be changed ? Computer virus

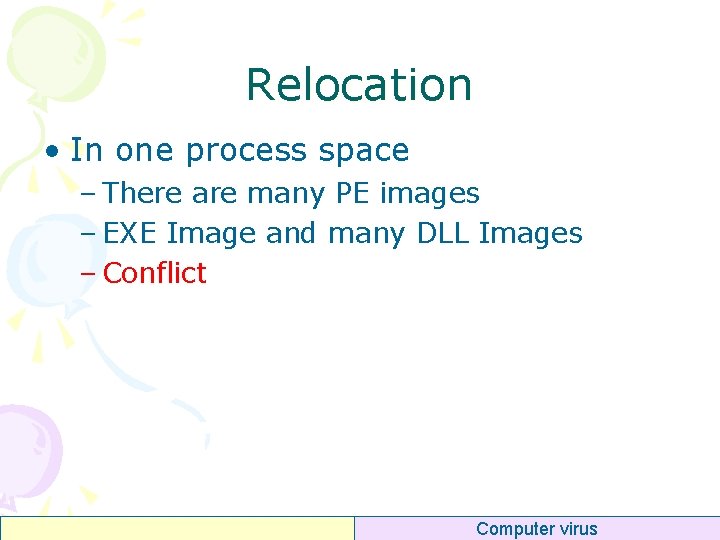
Relocation • In one process space – There are many PE images – EXE Image and many DLL Images – Conflict Computer virus

Relocation • Need the addresses in PE header be relocated ? • No Need Computer virus

RVA • RVA – (Relative Virtual Address) – For PE Structures – Used by PE Loader • Note : RVA points to the address in memory images – Not the offset in disk files • PE Image Address = Base Address + RVA Computer virus

RVA PE file in disk Base Addr DOS Header PE Header Opt Header Data DIR Sections Table RVA Sections Table + Section #1 Section #2 Loading PE Image in Mem Computer virus

Outline • PE Overview • PE Structure Header • Import Table • Export Table • Base Relocation Table • Resource Table • Virus Techniques Computer virus

Dos Header “MZ” DOS PE Header Opt Header struct { WORD e_magic; . . . DWORD e_lfanew; } DOS Header Dos Stub Data DIR Sections Table Section #1 Section #2 00000048 00000050 00000058 00000060 00000068 00000070 . . 69 61 74 20 6 D . . 73 6 D 20 69 6 F . . 20 20 62 6 E 64 . . 70 63 65 20 65 CD 72 61 20 44. . 21 6 F 6 E 72 4 F. . 54 67 6 E 75 53. . 68 72 6 F 6 E 20. . Th is progr am canno t be run in DOS mode Computer virus

DOS Stub • Modify DOS Stub code – Link /stub: dosfile. exe hello. obj Computer virus

_IMAGE_DOS_HEADER typedef struct _IMAGE_DOS_HEADER { // WORD e_magic; // WORD e_cblp; // WORD e_crlc; // WORD e_cparhdr; // WORD e_minalloc; // WORD e_maxalloc; // WORD e_ss; // WORD e_sp; // WORD e_csum; // WORD e_ip; // WORD e_cs; // WORD e_lfarlc; // WORD e_ovno; // WORD e_res[4]; // WORD e_oemid; // WORD e_oeminfo; // WORD e_res 2[10]; // LONG e_lfanew; // } IMAGE_DOS_HEADER, *PIMAGE_DOS_HEADER; DOS. EXE header Magic number Bytes on last page of file Pages in file Relocations Size of header in paragraphs Minimum extra paragraphs needed Defined in Win. NT. h Maximum extra paragraphs needed Initial (relative) SS value Initial SP value Checksum Initial IP value Initial (relative) CS value File address of relocation table Overlay number Reserved words OEM identifier (for e_oeminfo) OEM information; e_oemid specific Reserved words File address of new exe header Computer virus

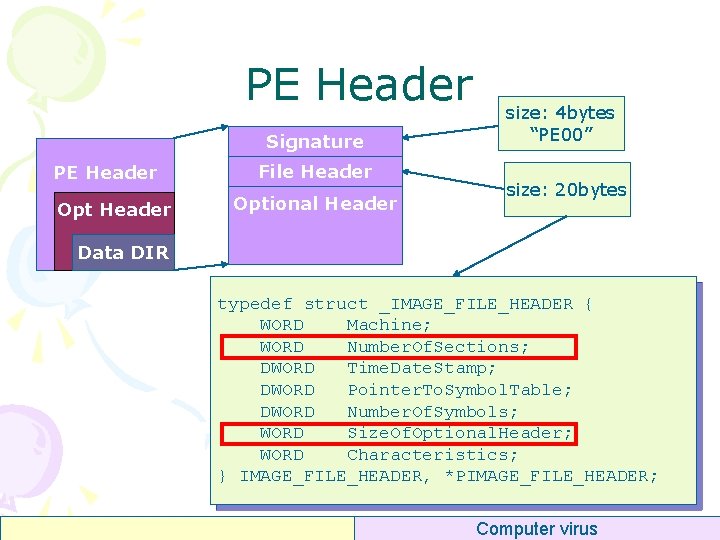
PE Header Signature PE Header Opt Header File Header Optional Header size: 4 bytes “PE 00” size: 20 bytes Data DIR typedef struct _IMAGE_FILE_HEADER { WORD Machine; WORD Number. Of. Sections; DWORD Time. Date. Stamp; DWORD Pointer. To. Symbol. Table; DWORD Number. Of. Symbols; WORD Size. Of. Optional. Header; WORD Characteristics; } IMAGE_FILE_HEADER, *PIMAGE_FILE_HEADER; Computer virus

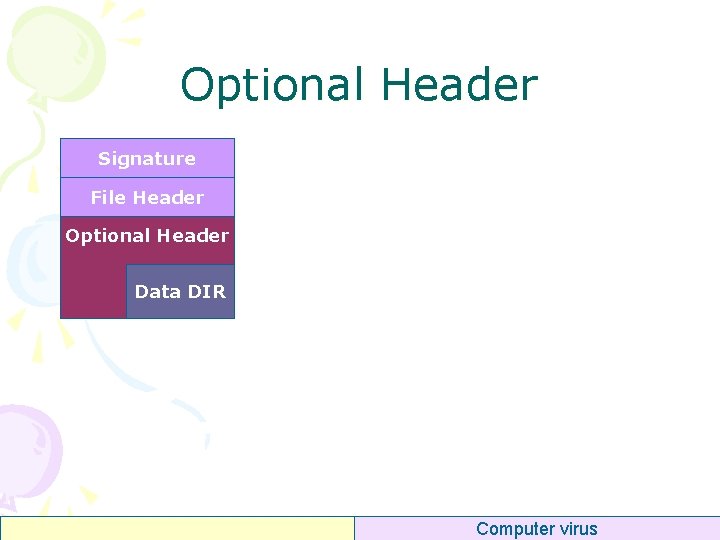
Optional Header Signature File Header Optional Header Data DIR Computer virus

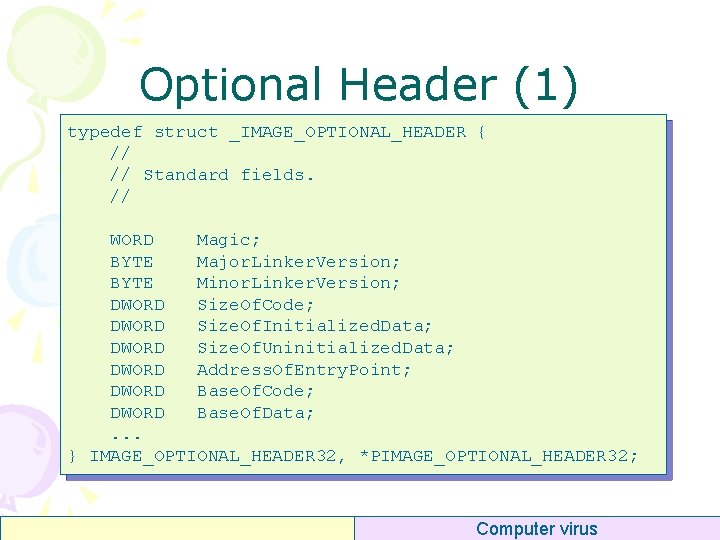
Optional Header (1) typedef struct _IMAGE_OPTIONAL_HEADER { // // Standard fields. // WORD Magic; BYTE Major. Linker. Version; BYTE Minor. Linker. Version; DWORD Size. Of. Code; DWORD Size. Of. Initialized. Data; DWORD Size. Of. Uninitialized. Data; DWORD Address. Of. Entry. Point; DWORD Base. Of. Code; DWORD Base. Of. Data; . . . } IMAGE_OPTIONAL_HEADER 32, *PIMAGE_OPTIONAL_HEADER 32; Computer virus

typedef struct _IMAGE_OPTIONAL_HEADER { // NT additional fields. DWORD Image. Base; DWORD Section. Alignment; DWORD File. Alignment; . . . DWORD Win 32 Version. Value; DWORD Size. Of. Image; DWORD Size. Of. Headers; DWORD Check. Sum; WORD Subsystem; WORD Dll. Characteristics; DWORD Size. Of. Stack. Reserve; DWORD Size. Of. Stack. Commit; 16 DWORD Size. Of. Heap. Reserve; DWORD Size. Of. Heap. Commit; DWORD Loader. Flags; DWORD Number. Of. Rva. And. Sizes; IMAGE_DATA_DIRECTORY Data. Directory[IMAGE_NUMBEROF_DIRECTORY_ENTRIES]; } IMAGE_OPTIONAL_HEADER 32, *PIMAGE_OPTIONAL_HEADER 32; Optional Header (2) Computer virus

Optional Header (3) • Address. Of. Entry. Point – Execution Entry (Note : RVA) • Image. Base • Alignment (Padding) – Section. Alignment (Bigger) – File. Alignment (Smaller) • Subsystem – “D: > link /subsystem: windows hello. obj” – Console, windows, posix, native, … Computer virus

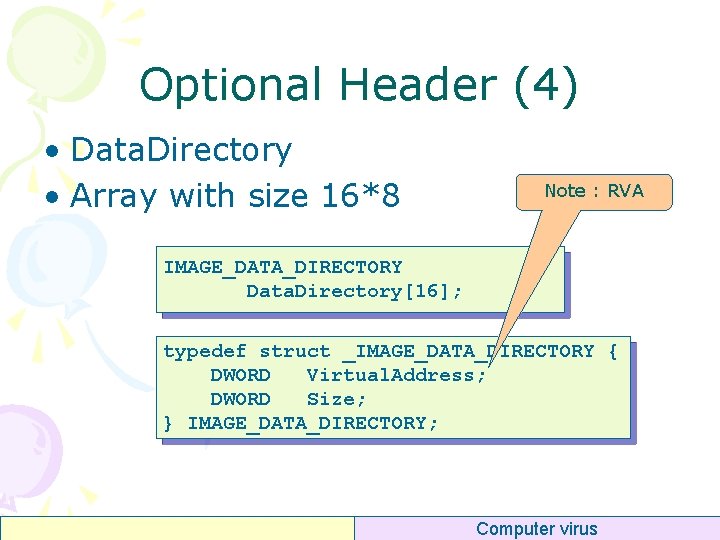
Optional Header (4) • Data. Directory • Array with size 16*8 Note : RVA IMAGE_DATA_DIRECTORY Data. Directory[16]; typedef struct _IMAGE_DATA_DIRECTORY { DWORD Virtual. Address; DWORD Size; } IMAGE_DATA_DIRECTORY; Computer virus

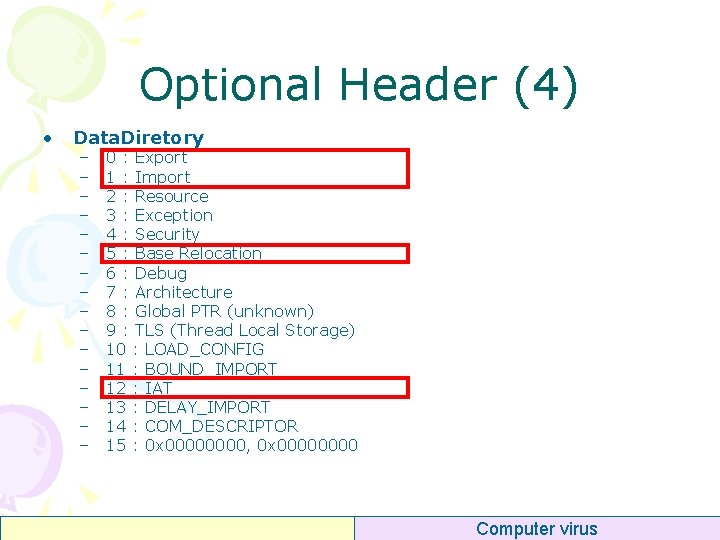
Optional Header (4) • Data. Diretory – – – – 0 : Export 1 : Import 2 : Resource 3 : Exception 4 : Security 5 : Base Relocation 6 : Debug 7 : Architecture 8 : Global PTR (unknown) 9 : TLS (Thread Local Storage) 10 : LOAD_CONFIG 11 : BOUND_IMPORT 12 : IAT 13 : DELAY_IMPORT 14 : COM_DESCRIPTOR 15 : 0 x 0000, 0 x 0000 Computer virus

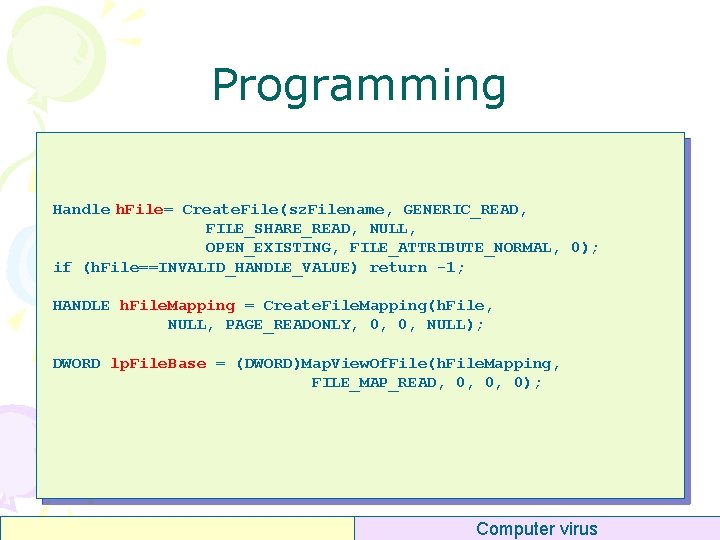
Programming Handle h. File= Create. File(sz. Filename, GENERIC_READ, FILE_SHARE_READ, NULL, OPEN_EXISTING, FILE_ATTRIBUTE_NORMAL, 0); if (h. File==INVALID_HANDLE_VALUE) return -1; HANDLE h. File. Mapping = Create. File. Mapping(h. File, NULL, PAGE_READONLY, 0, 0, NULL); DWORD lp. File. Base = (DWORD)Map. View. Of. File(h. File. Mapping, FILE_MAP_READ, 0, 0, 0); Computer virus

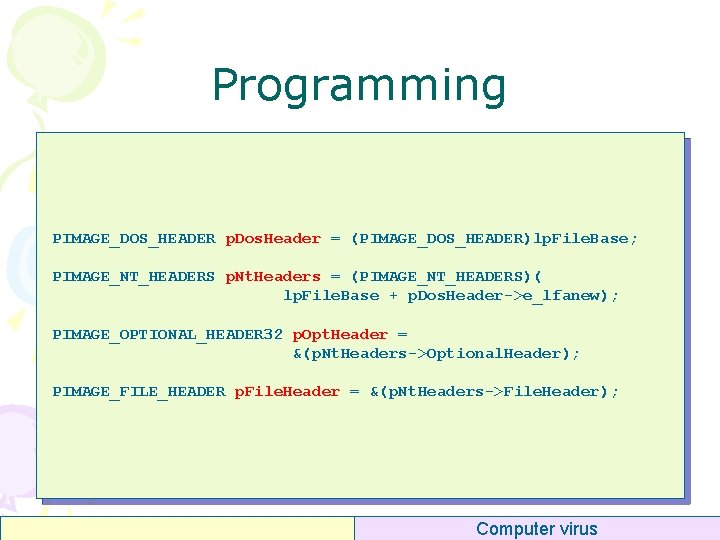
Programming PIMAGE_DOS_HEADER p. Dos. Header = (PIMAGE_DOS_HEADER)lp. File. Base; PIMAGE_NT_HEADERS p. Nt. Headers = (PIMAGE_NT_HEADERS)( lp. File. Base + p. Dos. Header->e_lfanew); PIMAGE_OPTIONAL_HEADER 32 p. Opt. Header = &(p. Nt. Headers->Optional. Header); PIMAGE_FILE_HEADER p. File. Header = &(p. Nt. Headers->File. Header); Computer virus

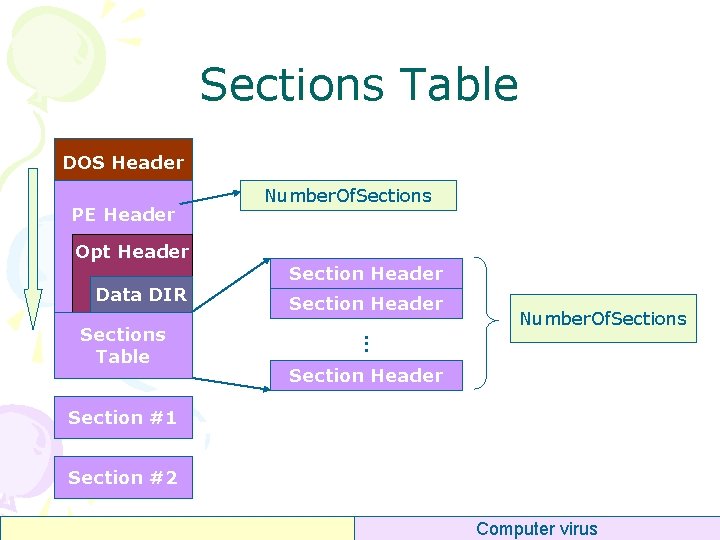
Sections Table DOS Header PE Header Opt Header Data DIR Section Header Number. Of. Sections . . . Sections Table Number. Of. Sections Section Header Section #1 Section #2 Computer virus
![Per Section Header Name8 text data idata Per Section Header • Name[8] – “. text” “. data” “. idata” – “.](https://slidetodoc.com/presentation_image_h2/a82188433970f4c028578a82b7dd93f4/image-32.jpg)
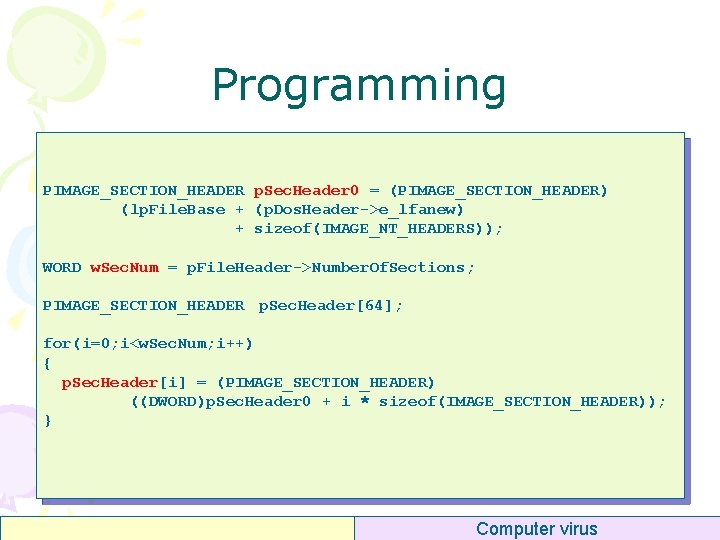
Per Section Header • Name[8] – “. text” “. data” “. idata” – “. reloc” “. rsrc” “. rdata” • Virtual. Address (RVA) – Addr of section • Size. Of. Raw. Data – Size of section in PE file • Pointer. To. Raw. Data – Offset of section in PE file • Characteristics – – Cached? Paged? Shared? Executable? Readable? Writable? Discardable? typedef struct _IMAGE_SECTION_HEADER { BYTE Name[8]; union { DWORD Physical. Address; DWORD Virtual. Size; } Misc; DWORD Virtual. Address; DWORD Size. Of. Raw. Data; DWORD Pointer. To. Relocations; DWORD Pointer. To. Linenumbers; WORD Number. Of. Relocations; WORD Number. Of. Linenumbers; DWORD Characteristics; } IMAGE_SECTION_HEADER; Computer virus

Programming PIMAGE_SECTION_HEADER p. Sec. Header 0 = (PIMAGE_SECTION_HEADER) (lp. File. Base + (p. Dos. Header->e_lfanew) + sizeof(IMAGE_NT_HEADERS)); WORD w. Sec. Num = p. File. Header->Number. Of. Sections; PIMAGE_SECTION_HEADER p. Sec. Header[64]; for(i=0; i<w. Sec. Num; i++) { p. Sec. Header[i] = (PIMAGE_SECTION_HEADER) ((DWORD)p. Sec. Header 0 + i * sizeof(IMAGE_SECTION_HEADER)); } Computer virus

Outline • PE Overview • PE Structure Header • Import Table • Export Table • Base Relocation Table • Resource Table • Virus Techniques Computer virus

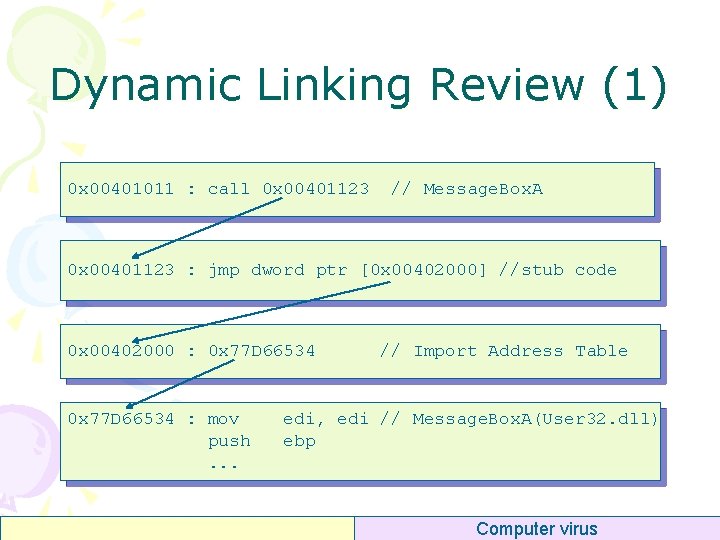
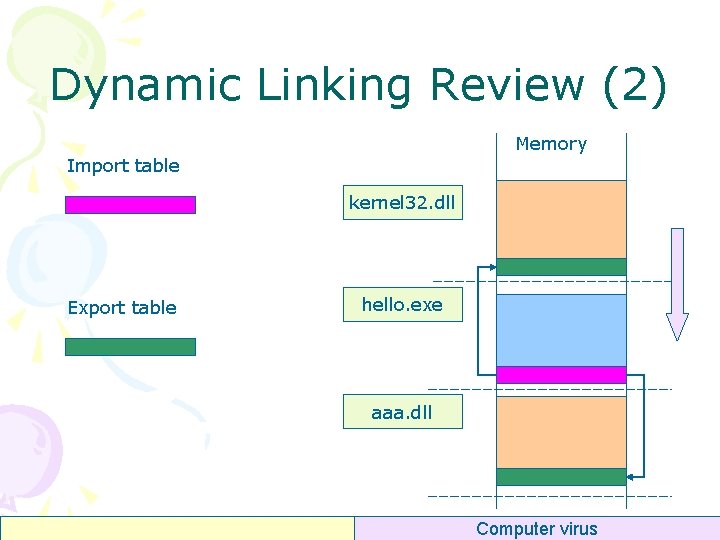
Dynamic Linking Review (1) 0 x 00401011 : call 0 x 00401123 // Message. Box. A 0 x 00401123 : jmp dword ptr [0 x 00402000] //stub code 0 x 00402000 : 0 x 77 D 66534 : mov push. . . // Import Address Table edi, edi // Message. Box. A(User 32. dll) ebp Computer virus

Dynamic Linking Review (2) Memory Import table kernel 32. dll Export table hello. exe aaa. dll Memory Computer virus

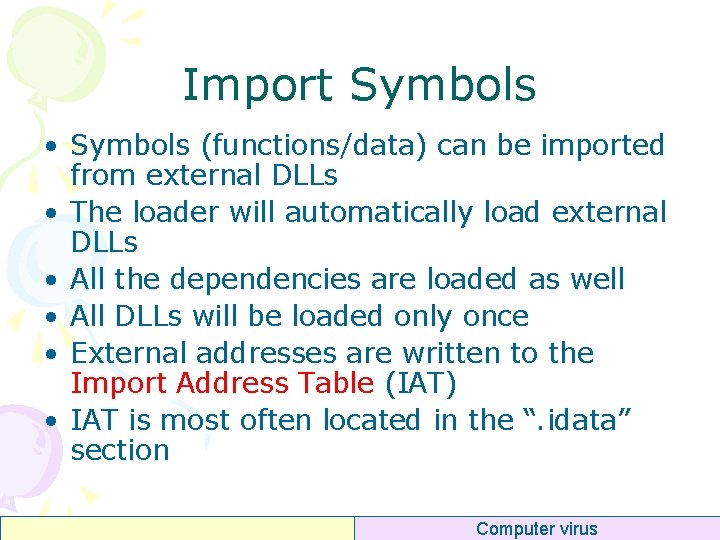
Import Symbols • Symbols (functions/data) can be imported from external DLLs • The loader will automatically load external DLLs • All the dependencies are loaded as well • All DLLs will be loaded only once • External addresses are written to the Import Address Table (IAT) • IAT is most often located in the “. idata” section Computer virus

DLL Dependency Tree Computer virus

Tool • Dependency Walker (free) – A free utility that scans any 32 -bit or 64 -bit Windows module (exe, dll, ocx, sys, etc. ) and builds a hierarchical tree diagram of all dependent modules. – http: //www. dependencywalker. com/ Computer virus

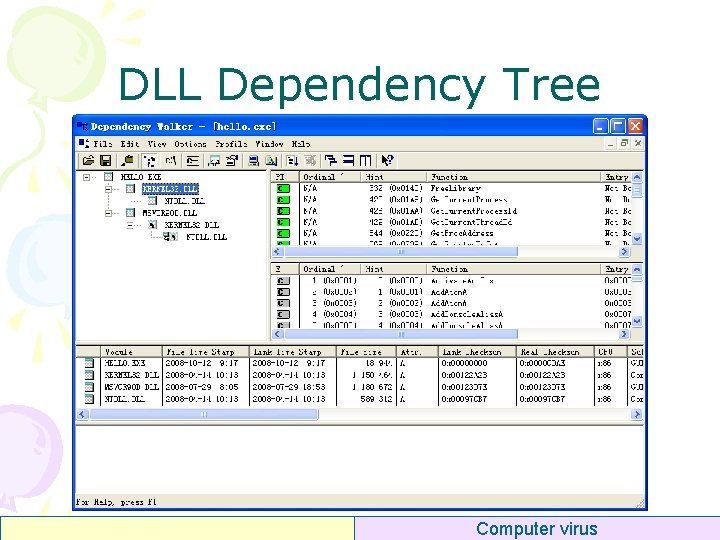
Dynamic Linking • Write target function addresses into IAT in PE structure Import Address Table Message. Box. A … … … • Where to find IAT ? Computer virus

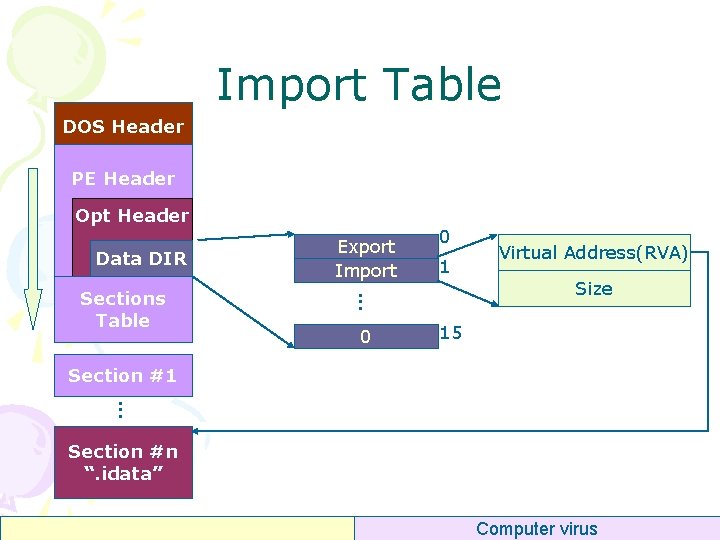
Import Table DOS Header PE Header Opt Header Data DIR 0 1 . . . Sections Table Export Import 0 Virtual Address(RVA) Size 15 Section #1. . . Section #n “. idata” Computer virus

Import Table • Quiz – Where to find import table in PE file? – Note : RVA is memory address, not PE file offset Computer virus

Import Table • Quiz – Where to find import table in PE file? – Note : RVA is memory address, not PE file offset • Answer – 1, – 2, – 3, – 4, get RVA of some section, RVAsec get Offsetsec of this section RVAoffset=RVAIAT- RVAsec Offset. IAT=Offsetsec+RVAoffset Computer virus

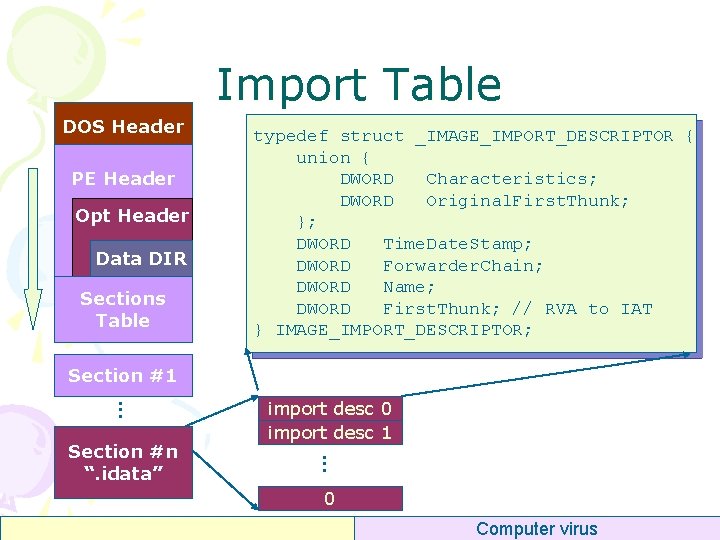
Import Table DOS Header PE Header Opt Header Data DIR Sections Table typedef struct _IMAGE_IMPORT_DESCRIPTOR { union { DWORD Characteristics; DWORD Original. First. Thunk; }; DWORD Time. Date. Stamp; DWORD Forwarder. Chain; DWORD Name; DWORD First. Thunk; // RVA to IAT } IMAGE_IMPORT_DESCRIPTOR; Section #1. . . Section #n “. idata” import desc 0 import desc 1 0 Computer virus

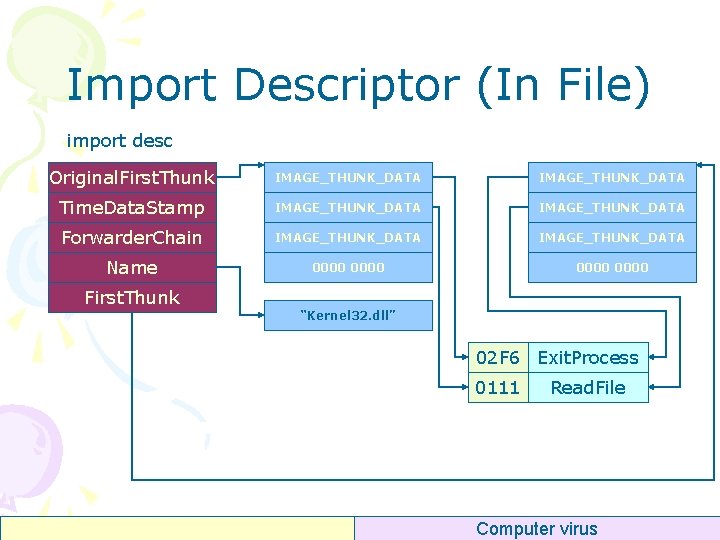
Import Descriptor (In File) import desc Original. First. Thunk IMAGE_THUNK_DATA Time. Data. Stamp IMAGE_THUNK_DATA Forwarder. Chain IMAGE_THUNK_DATA Name 0000 First. Thunk “Kernel 32. dll” 02 F 6 Exit. Process 0111 Read. File Computer virus

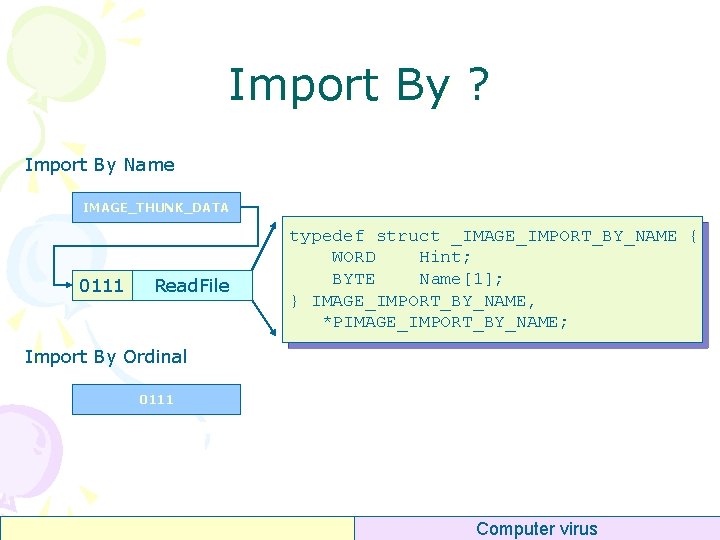
Import By ? Import By Name IMAGE_THUNK_DATA 0111 Read. File typedef struct _IMAGE_IMPORT_BY_NAME { WORD Hint; BYTE Name[1]; } IMAGE_IMPORT_BY_NAME, *PIMAGE_IMPORT_BY_NAME; Import By Ordinal 0111 Computer virus

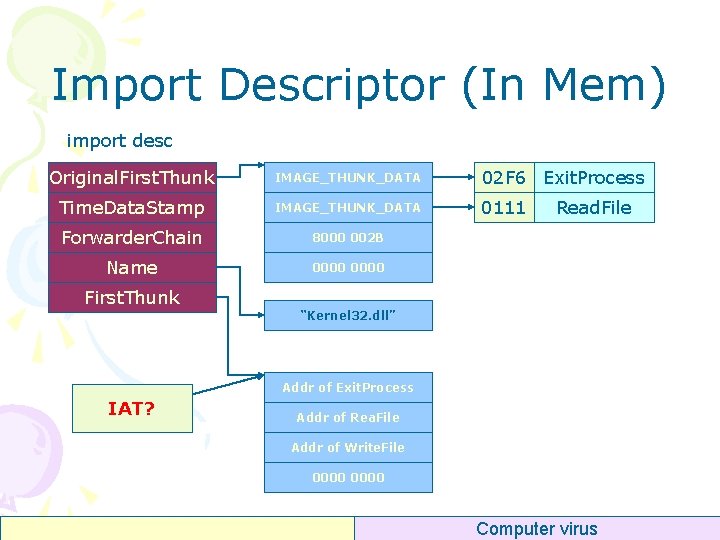
Import Descriptor (In Mem) import desc Original. First. Thunk IMAGE_THUNK_DATA 02 F 6 Exit. Process Time. Data. Stamp IMAGE_THUNK_DATA 0111 Forwarder. Chain 8000 002 B Name 0000 First. Thunk Read. File “Kernel 32. dll” Addr of Exit. Process IAT? Addr of Rea. File Addr of Write. File 0000 Computer virus

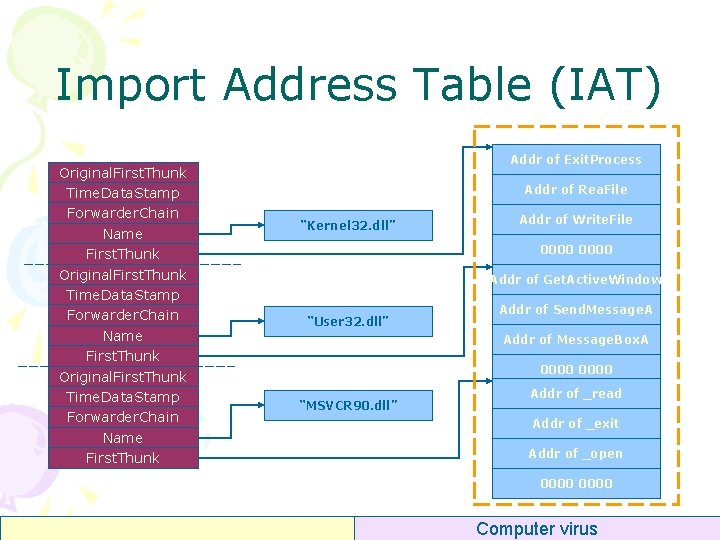
Import Address Table (IAT) Original. First. Thunk Time. Data. Stamp Forwarder. Chain Name First. Thunk Addr of Exit. Process Addr of Rea. File “Kernel 32. dll” Addr of Write. File 0000 Addr of Get. Active. Window “User 32. dll” Addr of Send. Message. A Addr of Message. Box. A 0000 “MSVCR 90. dll” Addr of _read Addr of _exit Addr of _open 0000 Computer virus

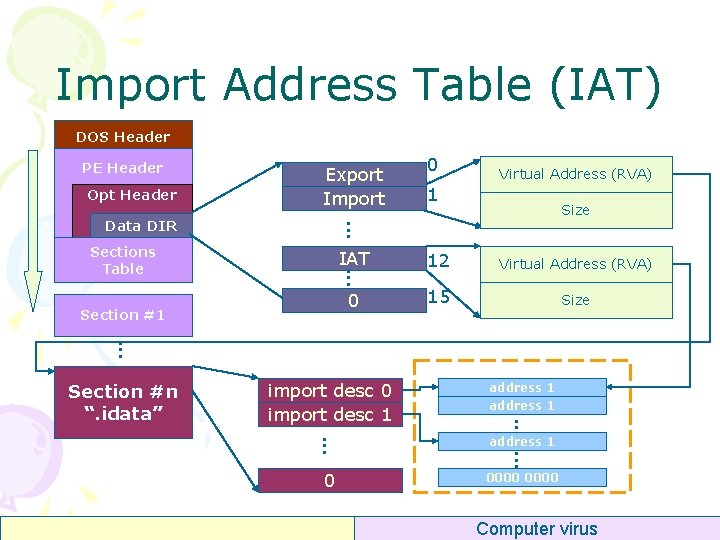
Import Address Table (IAT) DOS Header PE Header Opt Header Export Import Virtual Address (RVA) 1 Size . . . Data DIR 0 IAT 12 Virtual Address (RVA) 0 15 Size . . . Sections Table Section #1 . . . address 1 0 0000 . . . . import desc 0 import desc 1. . . Section #n “. idata” Computer virus
![Programming DWORD dw RVAImp Tbl p Opt HeaderData Directory1 Virtual Address DWORD dw Programming DWORD dw. RVAImp. Tbl = p. Opt. Header->Data. Directory[1]. Virtual. Address; DWORD dw.](https://slidetodoc.com/presentation_image_h2/a82188433970f4c028578a82b7dd93f4/image-50.jpg)
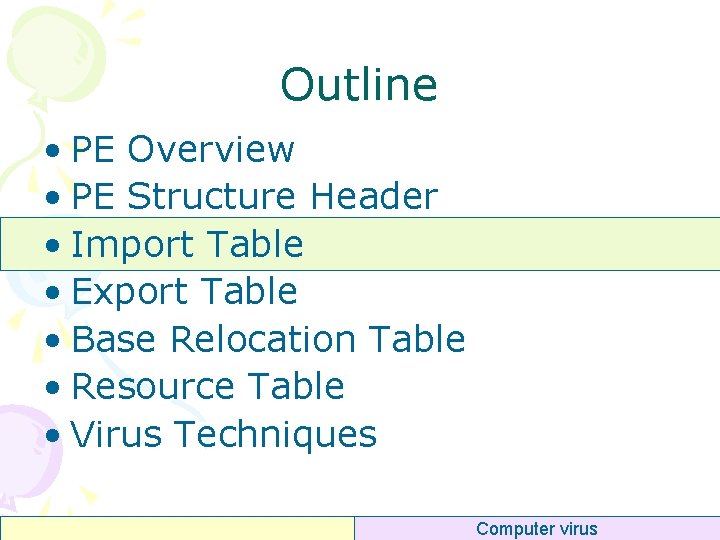
Programming DWORD dw. RVAImp. Tbl = p. Opt. Header->Data. Directory[1]. Virtual. Address; DWORD dw. Size. Of. Imp. Tbl = p. Opt. Header->Data. Directory[1]. Size; DWORD p. Imp. Tbl = lp. File. Base + RVA 2 Offset(dw. RVAImp. Tbl); PIMAGE_IMPORT_DESCRIPTOR p = (PIMAGE_IMPORT_DESCRIPTOR)p. Imp. Tbl; for (i=0; (p – p. Imp. Tbl) < dw. Size. Of. Imp. Tbl; i++, p++) { p. Imp. Desc[i] = p; if (p. Imp. Desc[i]->Name == NULL) break; } DWORD dw. Num. Of. Imp. Desc = i; Computer virus

Outline • PE Overview • PE Structure Header • Import Table • Export Table • Base Relocation Table • Resource Table • Virus Techniques Computer virus

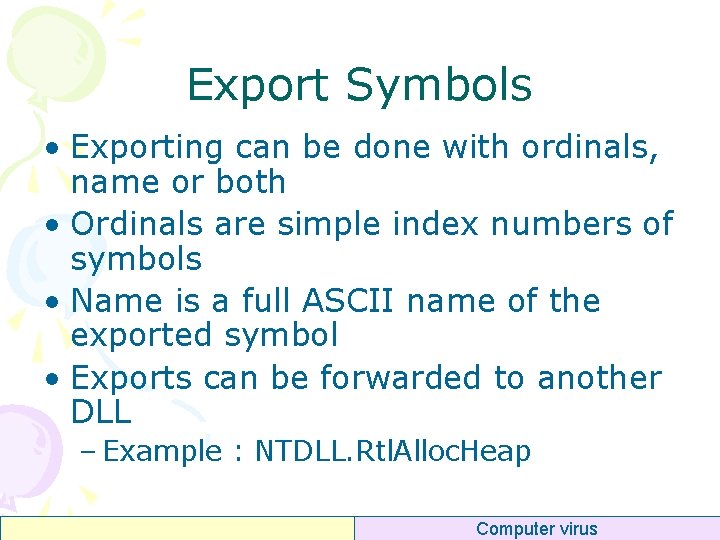
Export Symbols • Exporting can be done with ordinals, name or both • Ordinals are simple index numbers of symbols • Name is a full ASCII name of the exported symbol • Exports can be forwarded to another DLL – Example : NTDLL. Rtl. Alloc. Heap Computer virus

Export Table • Usually, EXE files have no export table • Most DLLs files have export table – Except DLLs only for resources container Computer virus

Export Table DOS Header PE Header Opt Header Data DIR 0 1 . . . Sections Table Export Import 0 Virtual Address(RVA) Size 15 Section #1. . . Section #n “. edata” Computer virus

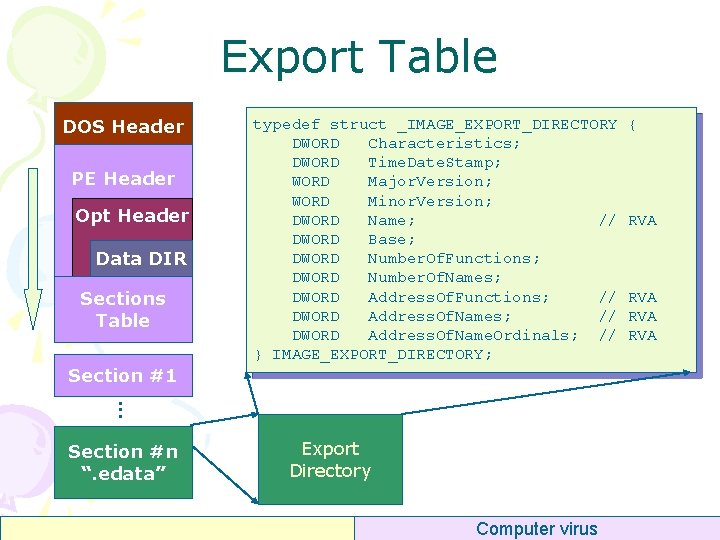
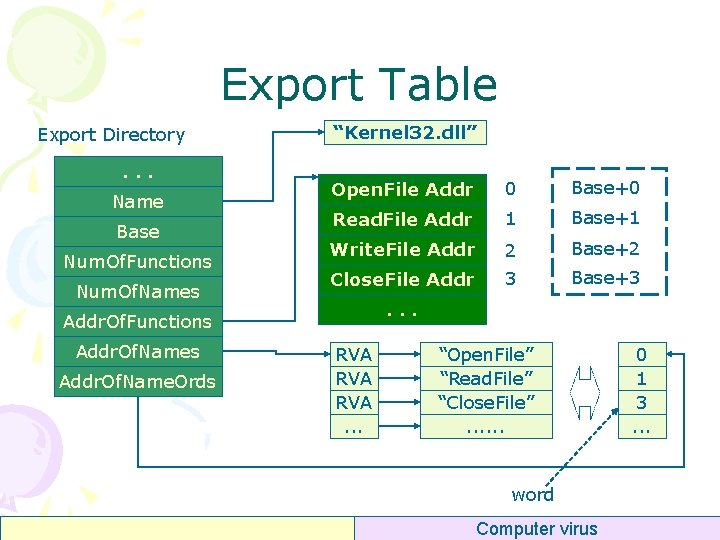
Export Table DOS Header PE Header Opt Header Data DIR Sections Table Section #1 typedef struct _IMAGE_EXPORT_DIRECTORY DWORD Characteristics; DWORD Time. Date. Stamp; WORD Major. Version; WORD Minor. Version; DWORD Name; // DWORD Base; DWORD Number. Of. Functions; DWORD Number. Of. Names; DWORD Address. Of. Functions; // DWORD Address. Of. Name. Ordinals; // } IMAGE_EXPORT_DIRECTORY; . . . Export Directory. . . Section #n “. edata” Computer virus { RVA RVA

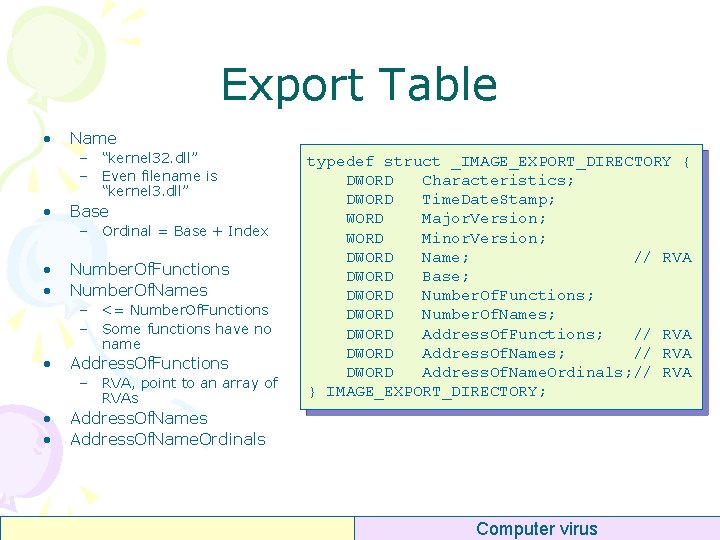
Export Table • Name – “kernel 32. dll” – Even filename is “kernel 3. dll” • Base – Ordinal = Base + Index • • Number. Of. Functions Number. Of. Names – <= Number. Of. Functions – Some functions have no name • Address. Of. Functions – RVA, point to an array of RVAs • • typedef struct _IMAGE_EXPORT_DIRECTORY { DWORD Characteristics; DWORD Time. Date. Stamp; WORD Major. Version; WORD Minor. Version; DWORD Name; // RVA DWORD Base; DWORD Number. Of. Functions; DWORD Number. Of. Names; DWORD Address. Of. Functions; // RVA DWORD Address. Of. Name. Ordinals; // RVA } IMAGE_EXPORT_DIRECTORY; Address. Of. Names Address. Of. Name. Ordinals Computer virus

Export Table Export Directory. . . Name Base Num. Of. Functions Num. Of. Names “Kernel 32. dll” Open. File Addr 0 Base+0 Read. File Addr 1 Base+1 Write. File Addr 2 Base+2 Close. File Addr 3 Base+3 . . . Addr. Of. Functions Addr. Of. Name. Ords RVA RVA. . . “Open. File” “Read. File” “Close. File”. . . word Computer virus 0 1 3. . .

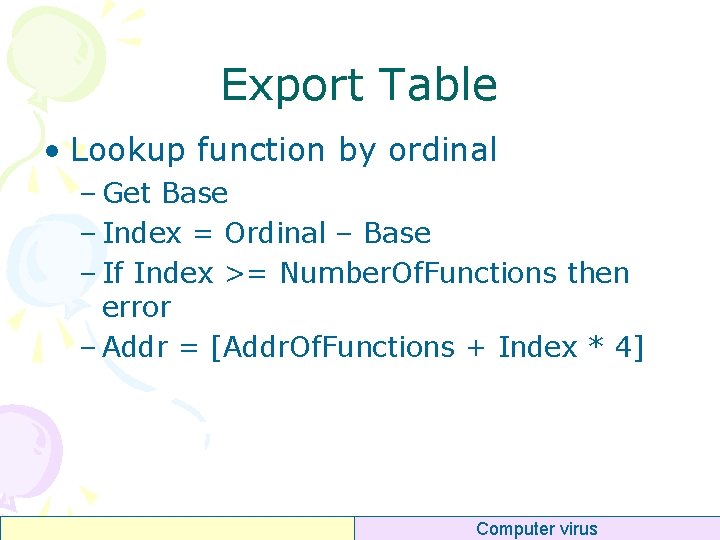
Export Table • Lookup function by ordinal – Get Base – Index = Ordinal – Base – If Index >= Number. Of. Functions then error – Addr = [Addr. Of. Functions + Index * 4] Computer virus

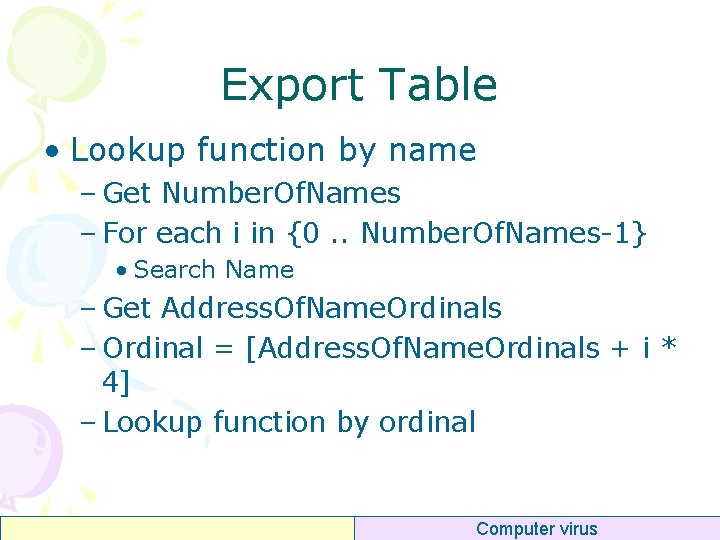
Export Table • Lookup function by name – Get Number. Of. Names – For each i in {0. . Number. Of. Names-1} • Search Name – Get Address. Of. Name. Ordinals – Ordinal = [Address. Of. Name. Ordinals + i * 4] – Lookup function by ordinal Computer virus

Programming mov mov mov add edi, eax, edx, pex, ecx, ebx, 0 x. XXXXYYYY [edi + 0 x 3 c] [edi + eax + edi edx [edx + 0 x 18] [edx + 0 x 20] edi // edi = Base. Addr, eax = p. NTHeader 0 x 78] // edx = Export Table (RVA) // ecx = Number. Of. Names // // ebx = Address. Of. Names _search: dec ecx mov esi, [ebx + ecx*4] add esi, edi mov eax, 0 x 50746547 // "Pte. G" cmp [esi], eax jne _search mov eax, 0 x 41636 f 72 //"Acor" cmp [esi+4], eax jne search // to be continued … Computer virus

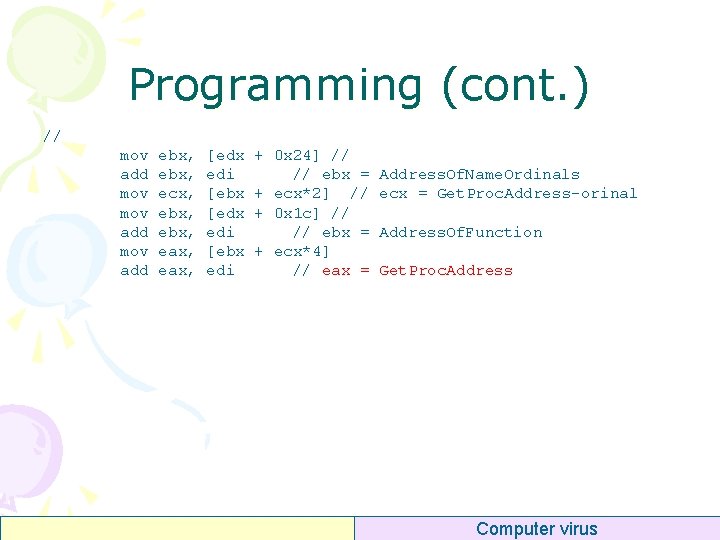
Programming (cont. ) // mov add ebx, ecx, ebx, eax, [edx edi [ebx edi + 0 x 24] // // ebx = + ecx*2] // + 0 x 1 c] // // ebx = + ecx*4] // eax = Address. Of. Name. Ordinals ecx = Get. Proc. Address-orinal Address. Of. Function Get. Proc. Address Computer virus

Outline • PE Overview • PE Structure Header • Import Table • Export Table • Base Relocation Table • Resource Table • Virus Techniques Computer virus

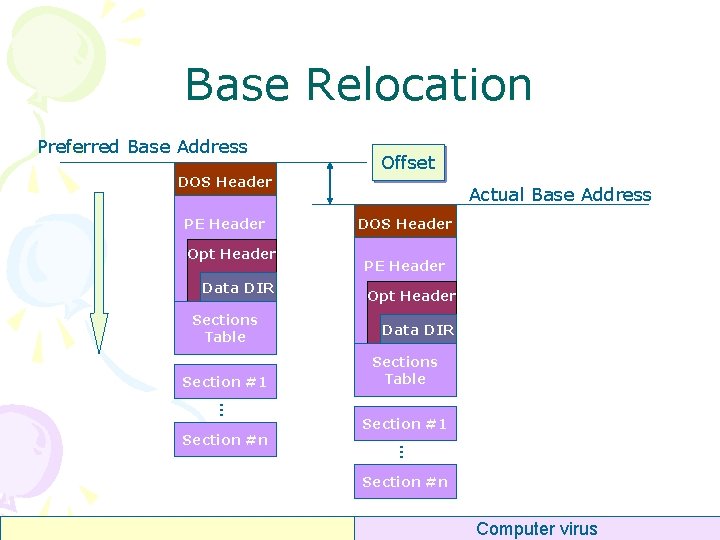
Base Relocation Preferred Base Address DOS Header PE Header Opt Header Data DIR Sections Table Section #1. . . Actual Base Address DOS Header PE Header Opt Header Data DIR Sections Table Section #1. . . Section #n Offset Section #n Computer virus

Base Relocation • Sometimes a DLL can not be loaded to its preferred address (Image. Base) • When rebasing, the loader has to adjust all hardcoded address • Relocations are done in 4 KB blocks – Page size on x 86 • Each relocation entry gives a type and points to a location • The offsets are adjusted according to the difference Computer virus

Base Relocation • Who need be relocated ? – Code with hardcoded address – Data with hardcoded address • How to know who ? – Compiler – “. reloc” section • Generated by compilers Computer virus

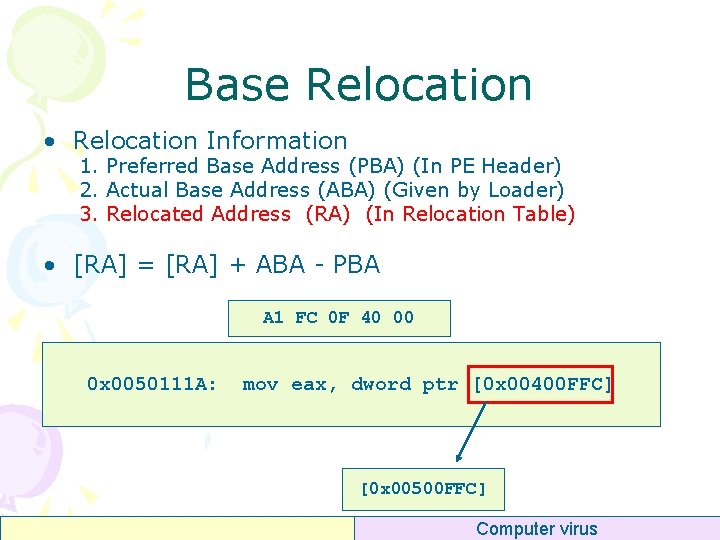
Base Relocation • Base Address – 0 x 00500000 A 1 FC 0 F 40 00 0 x 0050111 A: mov eax, dword ptr [0 x 00400 FFC] [0 x 00500 FFC] Computer virus

Base Relocation • Relocation Information 1. Preferred Base Address (PBA) (In PE Header) 2. Actual Base Address (ABA) (Given by Loader) 3. Relocated Address (RA) (In Relocation Table) • [RA] = [RA] + ABA - PBA A 1 FC 0 F 40 00 0 x 0050111 A: mov eax, dword ptr [0 x 00400 FFC] [0 x 00500 FFC] Computer virus

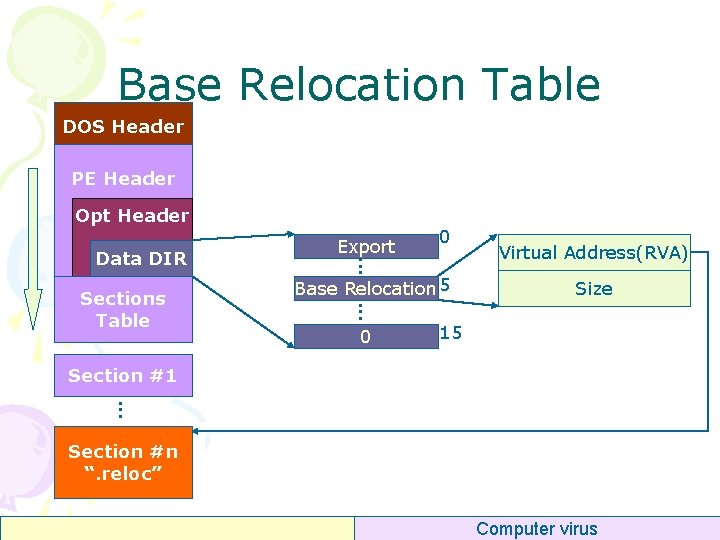
Base Relocation Table DOS Header PE Header Opt Header Sections Table 0 . . . Data DIR Export Base Relocation 5 0 Virtual Address(RVA) Size 15 Section #1. . . Section #n “. reloc” Computer virus

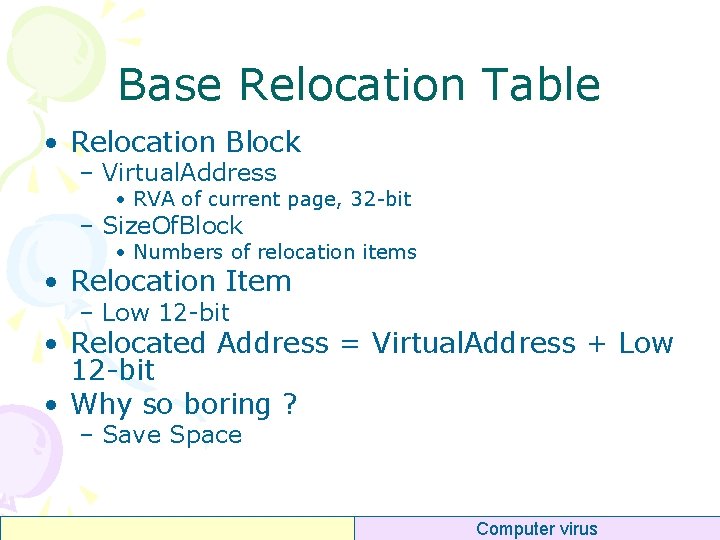
Base Relocation Table DOS Header PE Header typedef struct _IMAGE_BASE_RELOCATION { DWORD Virtual. Address; DWORD Size. Of. Block; } IMAGE_BASE_RELOCATION; Opt Header Data DIR Sections Table Base Relocation Block Low Addr Base Relocation Block. . Section #n “. reloc” Low Addr. . Section #1 Low Addr 0000 low 12 -bit 0 1 2 3 4 5 6 7 ABSOLUTE HIGH LOW HIGHADJ MIPS_JMPADDR SECTION REL 32 Computer virus

Base Relocation Table • Relocation Block – Virtual. Address • RVA of current page, 32 -bit – Size. Of. Block • Numbers of relocation items • Relocation Item – Low 12 -bit • Relocated Address = Virtual. Address + Low 12 -bit • Why so boring ? – Save Space Computer virus

That’s why • Program entry address is always like 0 x 00401000, not 0 x 00400000 – The second page after Base-Address • Reason: – Relocation. Block. Virtual. Address cannot be 0 – And, Relocation. Block. Virtual. Address is page aligned Computer virus

Outline • PE Overview • PE Structure Header • Import Table • Export Table • Base Relocation Table • Resource Table • Virus Techniques Computer virus

Resources • Resources in PE are similar to an archive • Resources files can be organized into directory tree • The data structure is quite complex but there are tools to handle it • Most common resources: – Icons – Version Information – GUI resources Computer virus

Resources Tools • e. Xe. Scope (free) – http: //hp. vector. co. jp/authors/VA 003525/Eindex. htm • Resource Hacker (free) – http: //www. angusj. com/resourcehacker/ • Res. Scope (not free) – http: //www. restools. net/index. htm • PE Explorer (not free) Computer virus

Outline • PE Overview • PE Structure Header • Import Table • Export Table • Base Relocation Table • Resource Table • Virus Techniques Introduction Computer virus

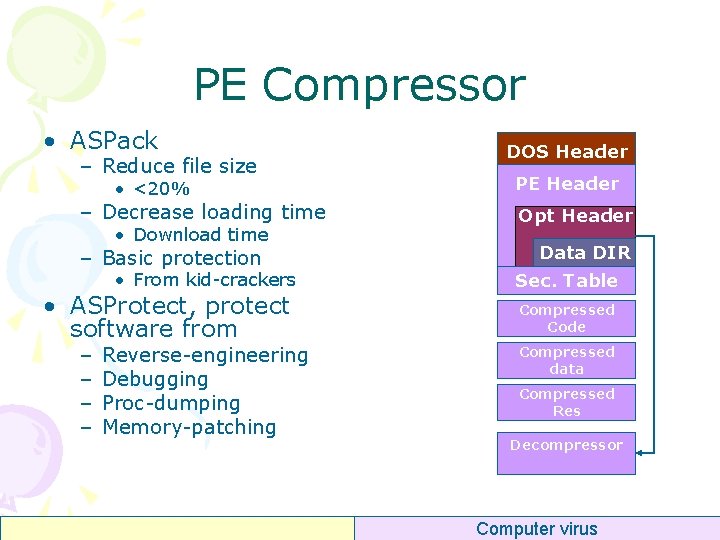
PE Compressor • ASPack – Reduce file size • <20% – Decrease loading time • Download time – Basic protection • From kid-crackers • ASProtect, protect software from – – Reverse-engineering Debugging Proc-dumping Memory-patching DOS Header PE Header Opt Header Data DIR Sec. Table Compressed Code Compressed data Compressed Res Decompressor Computer virus

IAT Hook • Hook Read. File function • Code Open. File Addr address 1 address 2 Write. File Addr . . . . Read. File Addr address 4 Close. File Addr 0000 . . . Virus Code Computer virus

Get API Entry • What should virus code do if it want to use system DLLs? – Analyze the import table of the host file • If import table has no some DLL ? – Use Get. Module. Handle to get this DLL Base. Address, and use Get. Proc. Address function, if the DLL have been loaded already • If the DLL is not in memory ? – Use Load. Library to load this DLL dynamically • The point is, – Load. Library is also an API function Computer virus

Get API Entry (cont. ) • The problem is – How to get Load. Library function • We can get Get. Proc. Address firstly – Find the Base-Address of “Kernel 32. dll” – Analyze PE structures of Kernel 32. dll – Peek into its export table – Find Get. Proc. Address function • Wait, It’s not easy to find Base. Address of “Kernel 32. dll” ? Computer virus

Get API Entry (cont. ) • How to find Base-Address of “Kernel 32. dll” ? Computer virus

Code Injection • Virus can inject itself into a PE files, known as “infection” – Put virus in padding space of some sections – Or add Additional sections – Modify Address. Of. Entry. Point (point to virus code) Computer virus

DLL Detour • Modify DLL code at run-time • Detours: Binary Interception of Win 32 Functions – Galen C. Hunt (Microsoft Research Operating Systems Group) – http: //research. microsoft. com/~galenh/ Publications/Hunt. Usenix. Nt 99. pdf Computer virus

Supply Readings • Matt Pietrek: An In-Depth Look into PE • Microsoft Portable Executable and Common Object File Format Specification Computer virus

Exercise • Write a PE file parser – Read analyze the header of EXE PE files (e. g. hello. exe, any valid EXE file will be ok) • • • Dos Header (Requisite) PE File Header, Optinal Header (Requisite) Sections Table (Requisite) Import Table (Optional) Export Table (Optional) – Output the results • In friendly format • To console, or window, or msgbox, even debugger • Deadline – 2008 -11 -14 (20: 00) Computer virus

Any Question ? Computer virus