IOR Scottish Chapter The Use Test in Practice












- Slides: 30

IOR Scottish Chapter: The Use Test in Practice Friday 26 th October 2012 NOTICE: Proprietary and Confidential This material is proprietary to Chase Cooper. It contains trade secrets and confidential information which is solely the property of Chase Cooper. The material is solely for the Client’s internal use. This materials shall not be used, reproduced, copied, disclosed, transmitted, in whole or in part, without the express consent of Chase cooper. Copyright 2012 Chase Cooper Limited. All rights reserved

Agenda Use Test: What is it – in terms of operational risk? How are you using your data? What do the regulators say? What data have we got already? How can we use it in the business? Combining the data for the RC and the Board 2

Use test: What is it? Showing that the operational risk management framework is used in the management of the firm As well as Governance, o Is the data used by the business? o Is the business involved in the generation of the data? For example, how is operational risk appetite reported to and discussed by the business? It is NOT ‘doing the process for the regulators’ 3

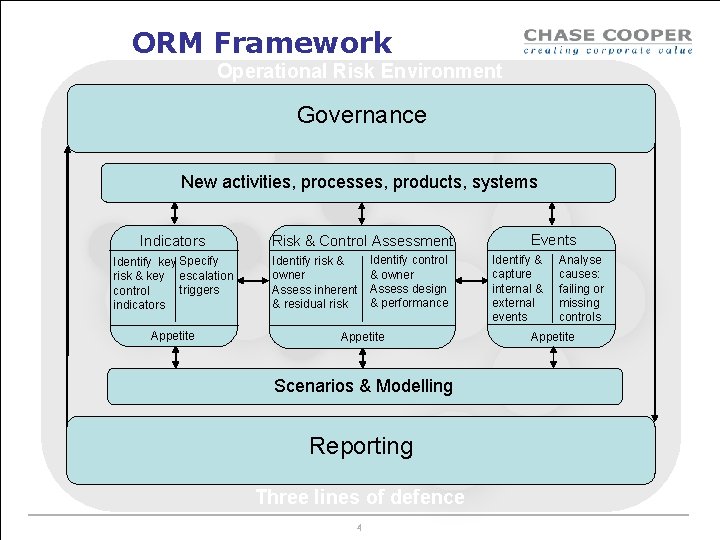
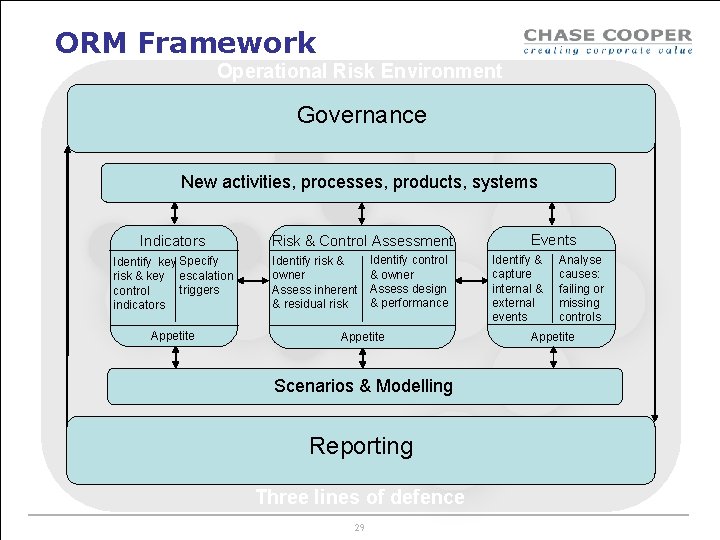
ORM Framework Operational Risk Environment Governance New activities, processes, products, systems Indicators Identify key Specify risk & key escalation triggers control indicators Appetite Risk & Control Assessment Identify risk & owner Assess inherent & residual risk Identify control & owner Assess design & performance Appetite Scenarios & Modelling Reporting Three lines of defence 4 Events Identify & capture internal & external events Analyse causes: failing or missing controls Appetite

Reporting: BCBS commentary Regular reports from both business units and internal audit Breaches of risk appetite Recent significant internal events and losses Relevant external events Top level (objectives) review Compliance with controls Identification and treatment of non-compliance Authorisation at appropriate level, if no treatment 5

Reporting: FSA (additionally) Results of identification, measurement and monitoring Actions taken to control risks Exposure thresholds and actual exposures Effectiveness of tools Board of Directors to receive information identifying, measuring, managing and controlling risks of regulatory concern fair treatment of customers protection of consumers confidence in financial system reduction in financial crime 6

The Use Test (ORIAG paper) “The effective management of OR depends on consistent and timely reporting of exposures” “…imperative that business line managers can make the connection between the overall view and what they need to achieve on the ground” “OR MIS plays the key role in linking senior management and staff level incentives to deliver the OR strategy” 7

What RCA data have we got already? Risks Likelihood Impact Risk owners Controls Design Performance Control owners 8

VOTE Do you have this data? 1: Yes 2: No 9

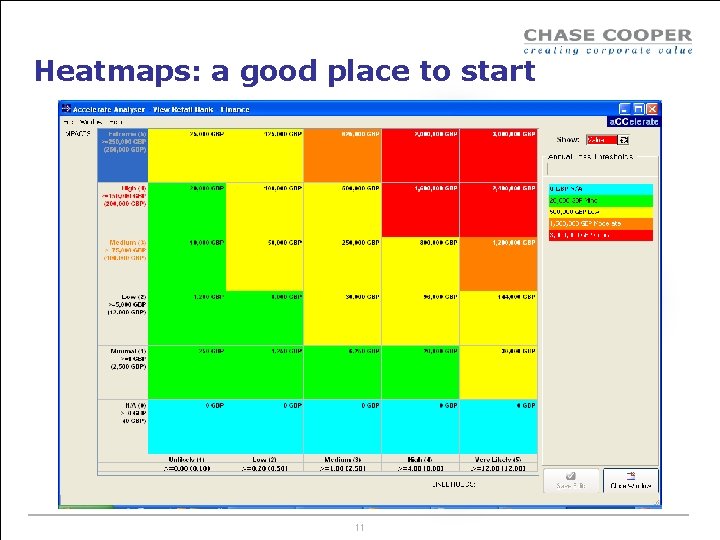
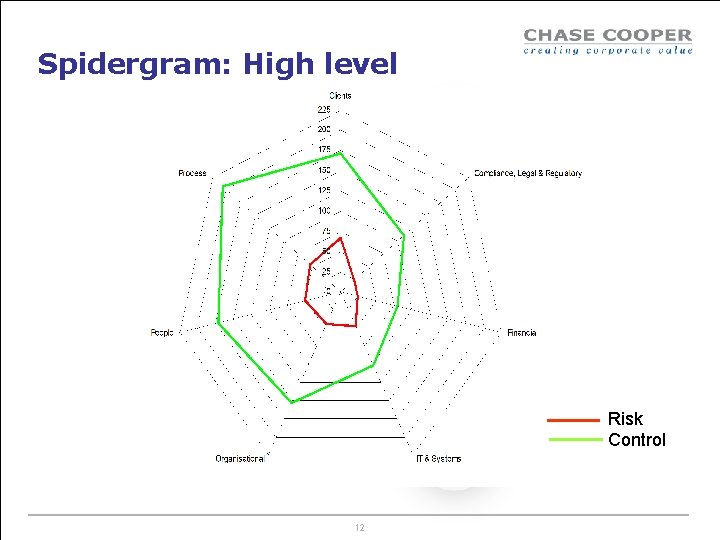
Using the data that we’ve got Heatmaps Spidergrams Min-Max spidergrams 10

Heatmaps: a good place to start 11

Spidergram: High level Risk Control 12

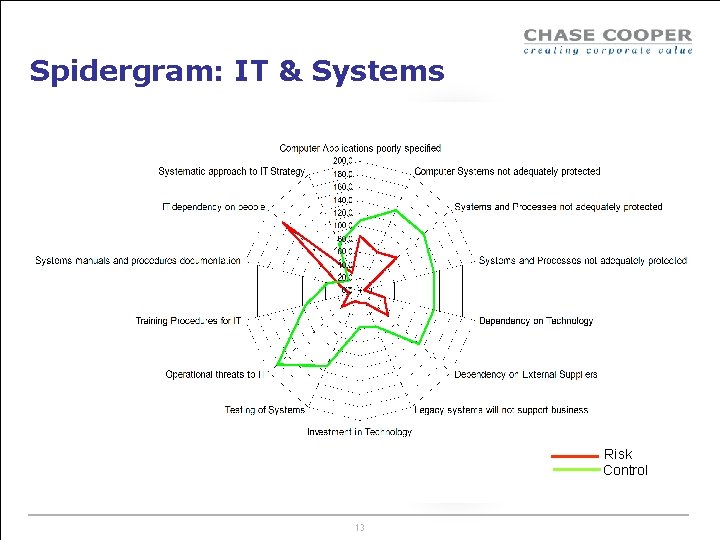
Spidergram: IT & Systems Risk Control 13

VOTE Do you use: 1: Heatmaps only 2: Spidergrams only 3: Heatmaps and spidergrams 4: Neither 14

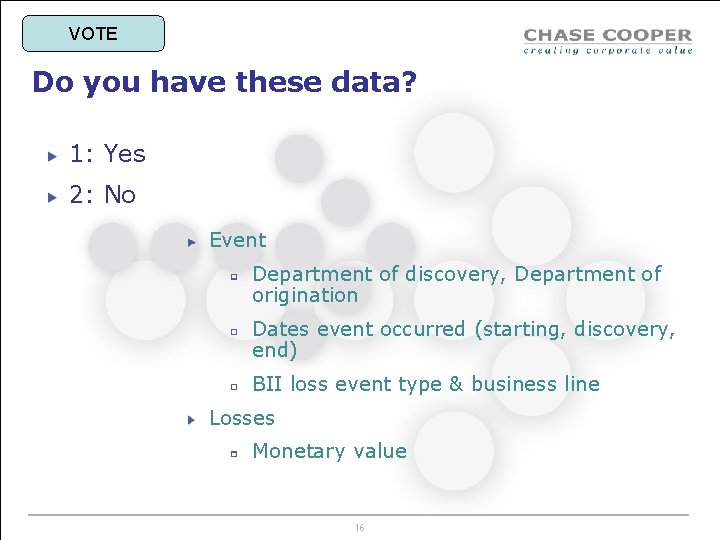
What Event data have we got already? Event Department of discovery, Department of origination Dates event occurred (starting, discovery, end) BII loss event type & business line Losses Monetary value 15

VOTE Do you have these data? 1: Yes 2: No Event Department of discovery, Department of origination Dates event occurred (starting, discovery, end) BII loss event type & business line Losses Monetary value 16

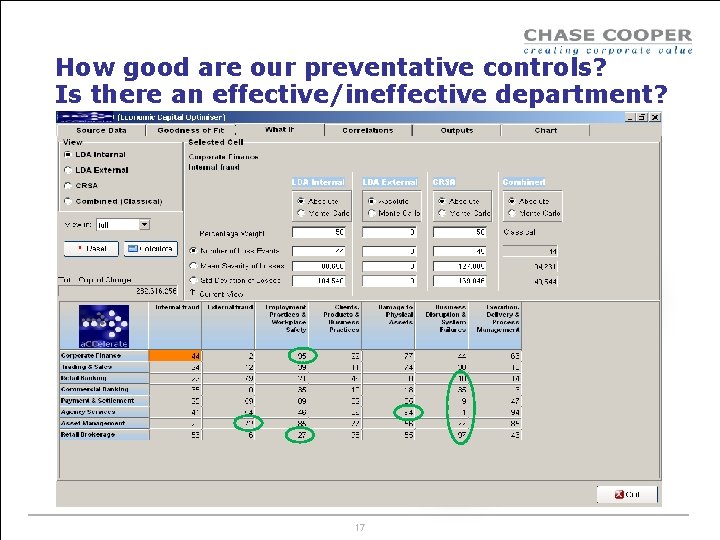
How good are our preventative controls? Is there an effective/ineffective department? 17

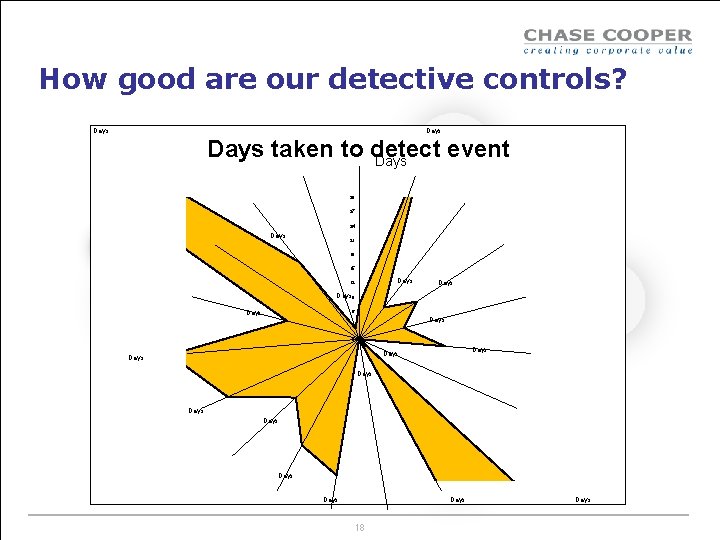
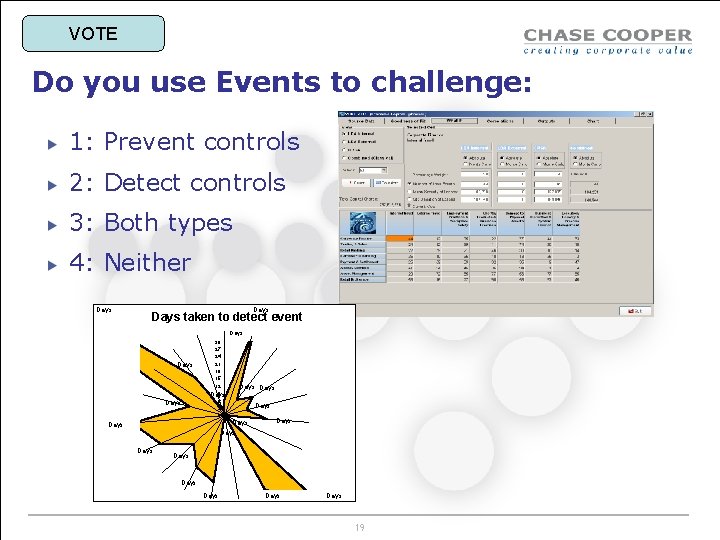
How good are our detective controls? Days taken to detect event Days 30 27 24 Days 21 18 15 Days 12 Days 9 6 Days 3 0 Days Days Days 18 Days

VOTE Do you use Events to challenge: 1: Prevent controls 2: Detect controls 3: Both types 4: Neither Days taken to detect event Days 30 27 24 21 18 15 12 9 Days 6 3 0 Days Days Days Days 19

What KRI data have we got already? Thresholds (green, yellow, red) Values Areas data is drawn from Period of data (e. g. monthly) Linked risks, controls, actions, events Event data which can be used as indicator data 20

VOTE Do you have these data? 1: Yes 2: No Thresholds (green, yellow, red) Values Areas data is drawn from Period of data (e. g. monthly) 21

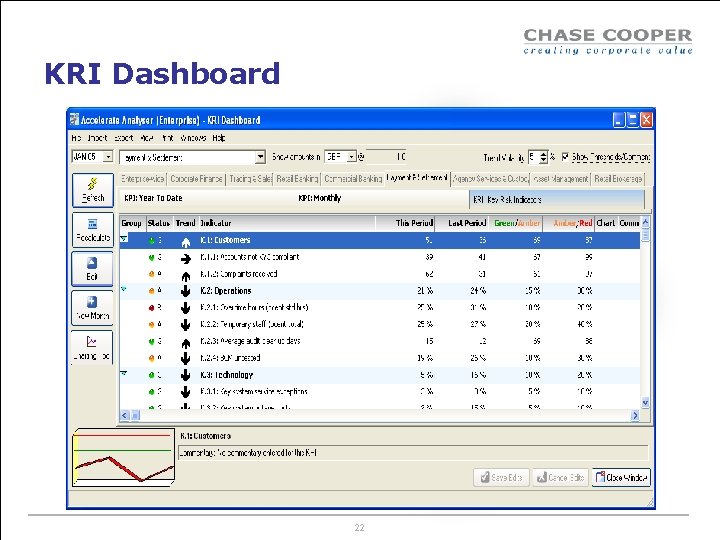
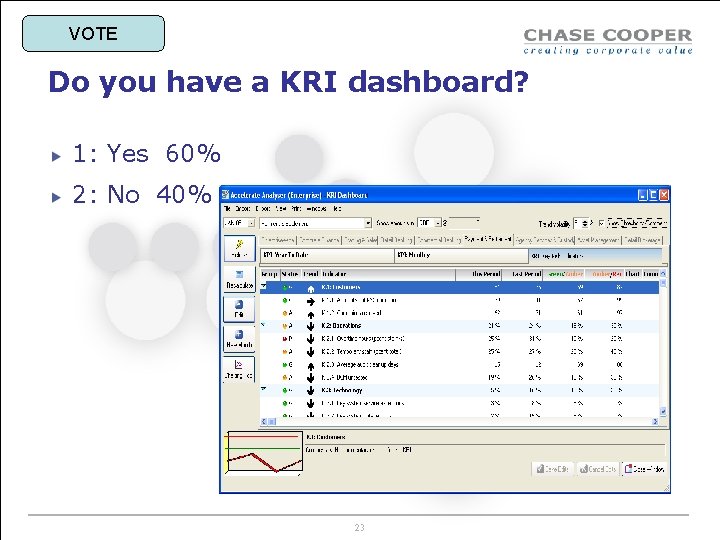
KRI Dashboard 22

VOTE Do you have a KRI dashboard? 1: Yes 60% 2: No 40% 23

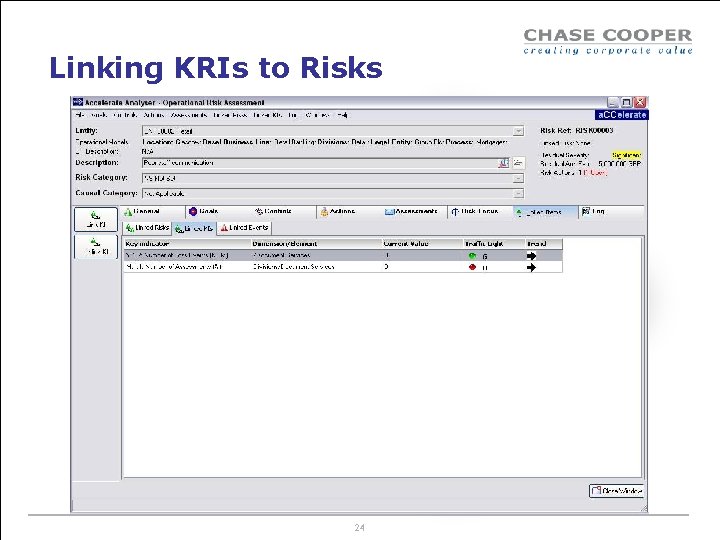
Linking KRIs to Risks 24

VOTE Have you linked KRIs to risks? 1: Yes 2: No Thresholds (green, yellow, red) Values Areas data is drawn from Period of data (e. g. monthly) Linked risks, controls, actions, events Event data which can be used as indicator data 25

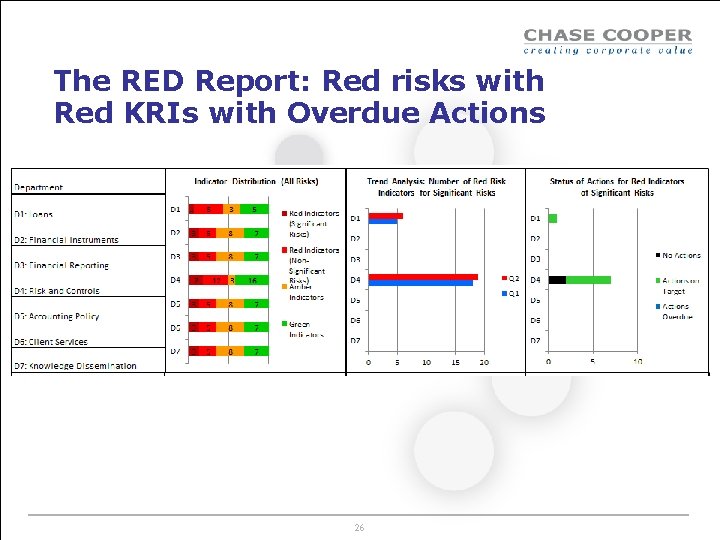
The RED Report: Red risks with Red KRIs with Overdue Actions 26

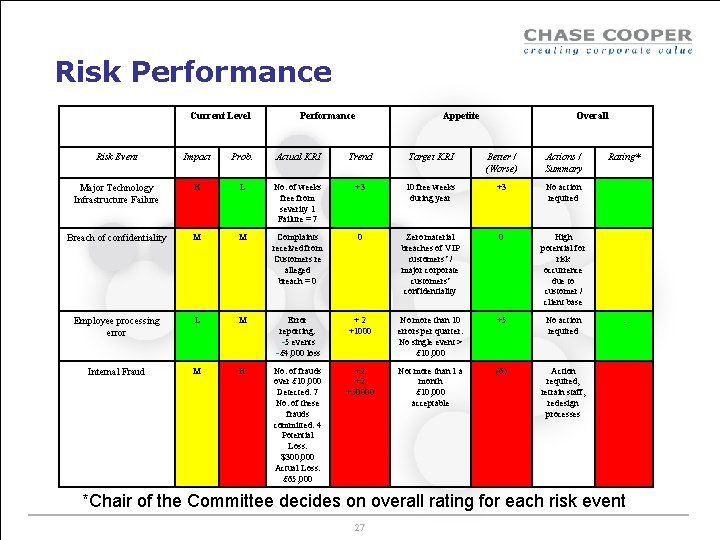
Risk Performance Current Level Performance Appetite Overall Risk Event Impact Prob. Actual KRI Trend Target KRI Better / (Worse) Actions / Summary Major Technology Infrastructure Failure H L No. of weeks free from severity 1 Failure = 7 +3 10 free weeks during year +3 No action required Breach of confidentiality M M Complaints received from Customers re alleged breach = 0 0 Zero material breaches of VIP customers’ / major corporate customers’ confidentiality 0 High potential for risk occurrence due to customer / client base Employee processing error L M Error reporting: -5 events -£ 4, 000 loss +2 +1000 No more than 10 errors per quarter. No single event > £ 10, 000 +5 No action required Internal Fraud M H No. of frauds over £ 10, 000 Detected: 7 No. of these frauds committed: 4 Potential Loss: $300, 000 Actual Loss: £ 65, 000 +2 +2 +50000 Not more than 1 a month £ 10, 000 acceptable (6) Action required, retrain staff, redesign processes Rating* . *Chair of the Committee decides on overall rating for each risk event 27

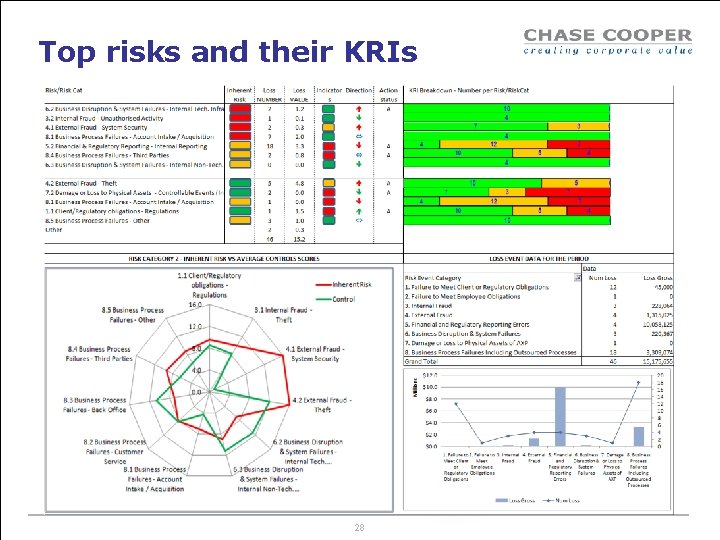
Top risks and their KRIs 28

ORM Framework Operational Risk Environment Governance New activities, processes, products, systems Indicators Identify key Specify risk & key escalation triggers control indicators Appetite Risk & Control Assessment Identify risk & owner Assess inherent & residual risk Identify control & owner Assess design & performance Appetite Scenarios & Modelling Reporting Three lines of defence 29 Events Identify & capture internal & external events Analyse causes: failing or missing controls Appetite

Contact details Tony Blunden Head of Consulting, Chase Cooper Hon Professor, Glasgow Caledonian University Tel: +44 (0) 207 377 2269 Fax: +44 (0) 207 426 0882 Mob: +44 (0) 770 325 7480 E-mail: tony. blunden@chasecooper. com www. chasecooper. com 30