Implementing Secure Converged Wide Area Networks ISCW Module







- Slides: 26

Implementing Secure Converged Wide Area Networks (ISCW) Module 6: Cisco IOS Threat Defense Features © 2006 Cisco Systems, Inc. All rights reserved.

Module 6: Cisco IOS Threat Defense Features Lesson 6. 4: Introducing Cisco IOS IPS © 2006 Cisco Systems, Inc. All rights reserved.

Objectives § Compare and contrast Intrusion Detection Systems and Intrusion Protection Systems. § Describe the Cisco IPS products and technologies. § Define IDS and IPS types and options. § Compare Network Based and Host Based IPS systems (HIPS and NIPS). © 2006 Cisco Systems, Inc. All rights reserved.

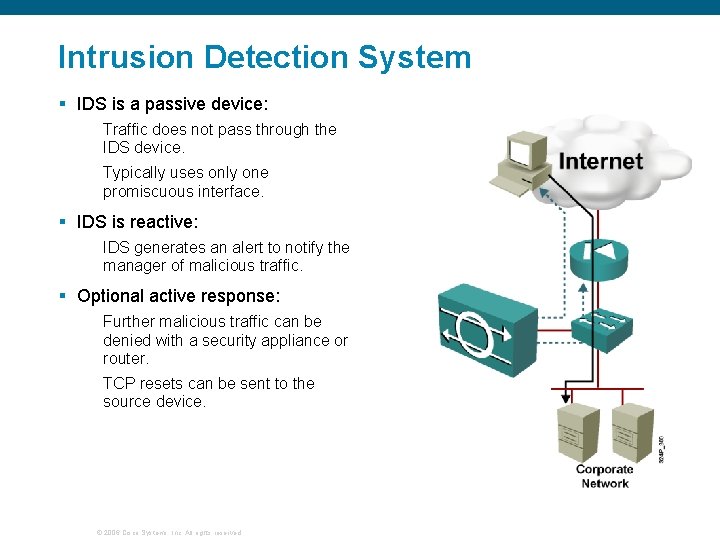
Intrusion Detection System § IDS is a passive device: Traffic does not pass through the IDS device. Typically uses only one promiscuous interface. § IDS is reactive: IDS generates an alert to notify the manager of malicious traffic. § Optional active response: Further malicious traffic can be denied with a security appliance or router. TCP resets can be sent to the source device. © 2006 Cisco Systems, Inc. All rights reserved.

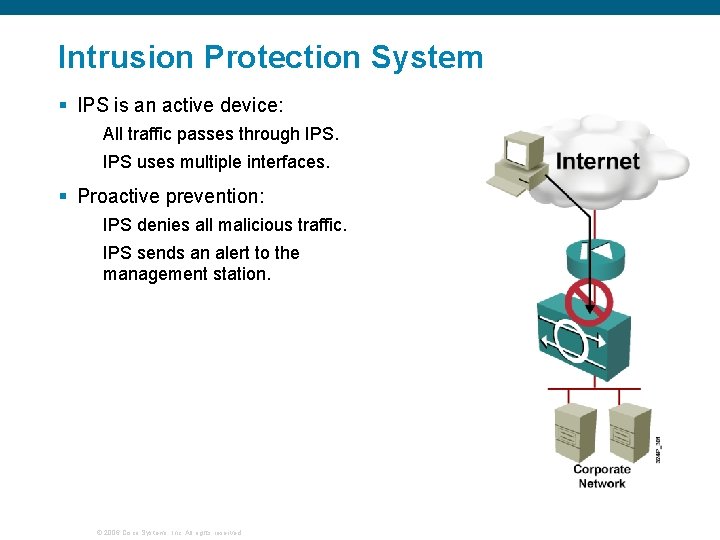
Intrusion Protection System § IPS is an active device: All traffic passes through IPS uses multiple interfaces. § Proactive prevention: IPS denies all malicious traffic. IPS sends an alert to the management station. © 2006 Cisco Systems, Inc. All rights reserved.

Combining IDS and IPS § IPS actively blocks offending traffic: Should not block legitimate data Only stops “known malicious traffic” Requires focused tuning to avoid connectivity disruption § IDS complements IPS: Verifies that IPS is still operational Alerts you about any suspicious data except “known good traffic” Covers the “gray area” of possibly malicious traffic that IPS did not stop © 2006 Cisco Systems, Inc. All rights reserved.

Cisco IOS IPS Products and Technologies § Cisco IOS IPS uses a blend of Cisco IDS and IPS products: Cisco IDS Series appliances Cisco Catalyst Series IDS services modules Cisco network module hardware IDS appliances § Cisco IOS IPS uses a blend of technologies: Profile-based intrusion detection Signature-based intrusion detection Protocol analysis-based intrusion detection © 2006 Cisco Systems, Inc. All rights reserved.

IPS vs. Firewall § A firewall permits and blocks traffic by port/protocol rules. § However, an attacker can use legitimate ports to send illegitimate traffic. § An IPS looks at the contents of the packets and/or can correlate over time to determine if an attack is happening. § An IPS works in tandem with a firewall to make sure that the traffic the firewall permitted is actual legitimate traffic. © 2006 Cisco Systems, Inc. All rights reserved.

Difference between Firewalls and IPS § Firewalls will do statefull packet filtering whereas IPS will detect and stop traffic anomalies, based on signatures and rules using deep packet inspection § But firewalls also use deep packet inspection the what is different between both firewall and IPS's packet inspection ? ? § The difference is anomaly detection. It is true that deep packet inspection can identify the illegitimate traffic, but this is only per-packet. If an infected machine starts scanning other hosts for example, via ICMP or TCP SYN scans or likewise, the IPS can pick this up but the firewall does not. © 2006 Cisco Systems, Inc. All rights reserved.

IPS Capabilities § The scanning detection is only one example. § Another one is a host that starts sending large number of packets with no return traffic when that behaviour was never detected from that host before. § The IPS learns "normal" behaviour of a network and then can identify changes going forward. § A firewall with DPI would not have this capability. © 2006 Cisco Systems, Inc. All rights reserved.

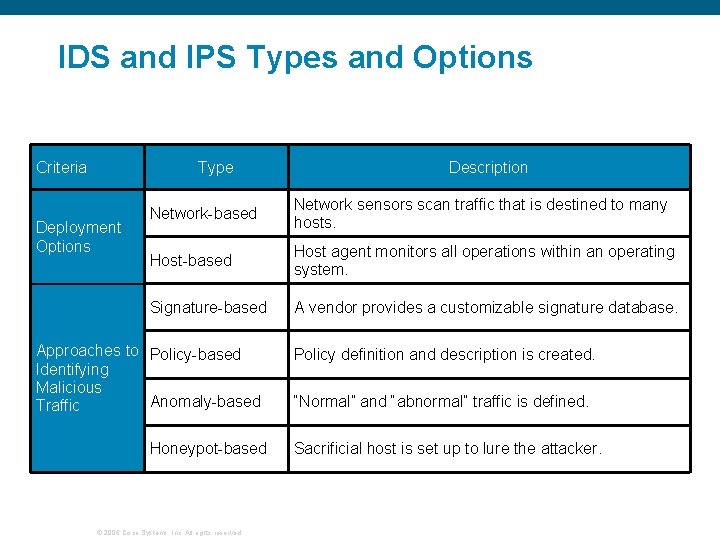
IDS and IPS Types and Options Criteria Type Deployment Options Description Network-based Network sensors scan traffic that is destined to many hosts. Host-based Host agent monitors all operations within an operating system. Signature-based A vendor provides a customizable signature database. Approaches to Policy-based Identifying Malicious Anomaly-based Traffic Honeypot-based © 2006 Cisco Systems, Inc. All rights reserved. Policy definition and description is created. “Normal” and “abnormal” traffic is defined. Sacrificial host is set up to lure the attacker.

Network-Based and Host-Based IPS § NIPS: Sensor appliances are connected to network segments to monitor many hosts. § HIPS: Centrally managed software agents are installed on each host. CSAs defend the protected hosts and report to the central management console. HIPS provides individual host detection and protection. HIPS does not require special hardware. © 2006 Cisco Systems, Inc. All rights reserved.

Comparing HIPS and NIPS § Application-level encryption protection § Policy enhancement (resource control) § Web application protection § Buffer overflow § Network attack and reconnaissance prevention § Do. S prevention © 2006 Cisco Systems, Inc. All rights reserved.

NIPS Features § Sensors are network appliances that you tune for intrusion detection analysis: The operating system is “hardened. ” The hardware is dedicated to intrusion detection analysis. § Sensors are connected to network segments. A single sensor can monitor many hosts. § Growing networks are easily protected: New hosts and devices can be added without adding sensors. New sensors can be easily added to new networks. © 2006 Cisco Systems, Inc. All rights reserved.

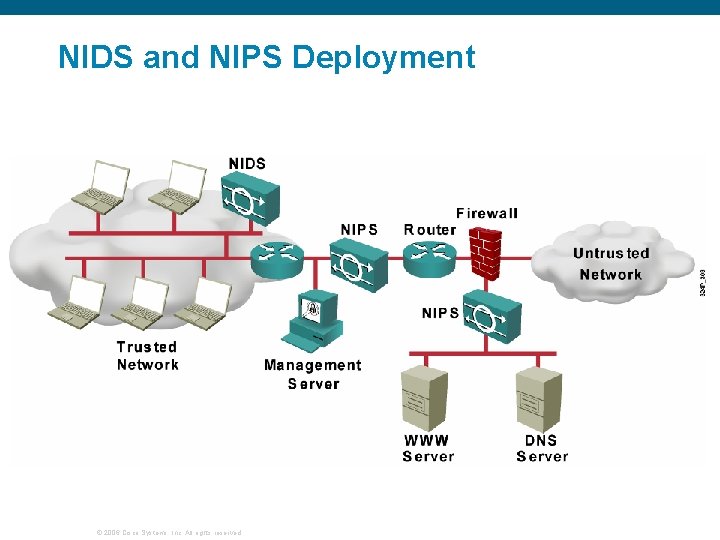
NIDS and NIPS Deployment © 2006 Cisco Systems, Inc. All rights reserved.

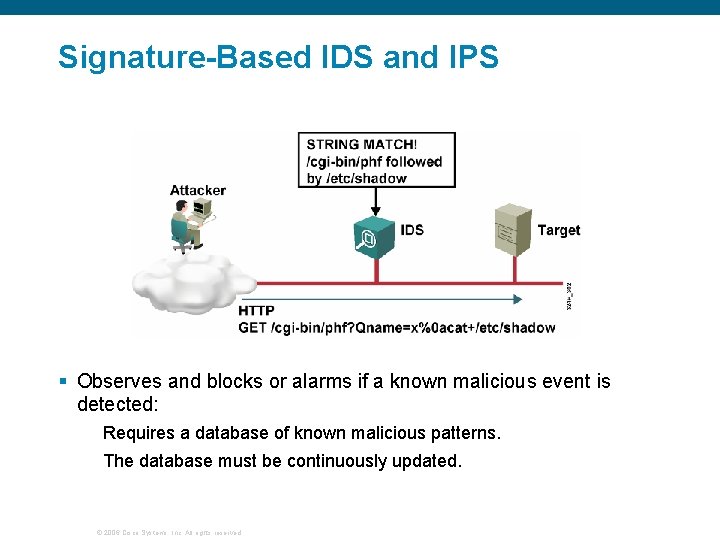
Signature-Based IDS and IPS § Observes and blocks or alarms if a known malicious event is detected: Requires a database of known malicious patterns. The database must be continuously updated. © 2006 Cisco Systems, Inc. All rights reserved.

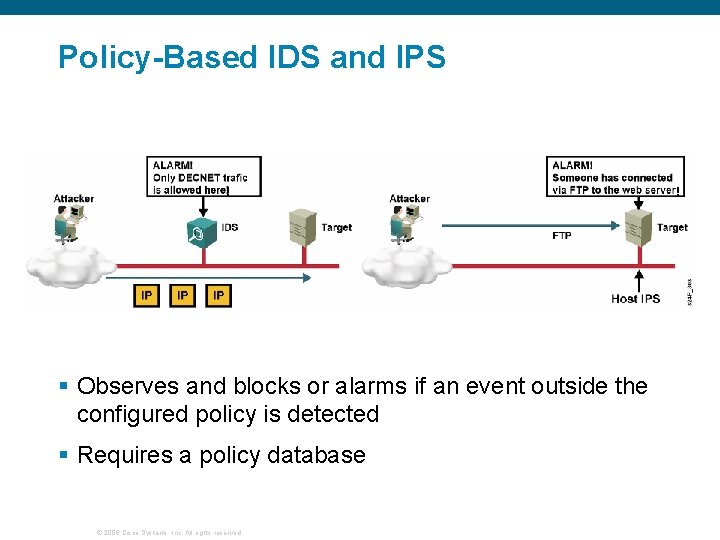
Policy-Based IDS and IPS ! § Observes and blocks or alarms if an event outside the configured policy is detected § Requires a policy database © 2006 Cisco Systems, Inc. All rights reserved. !

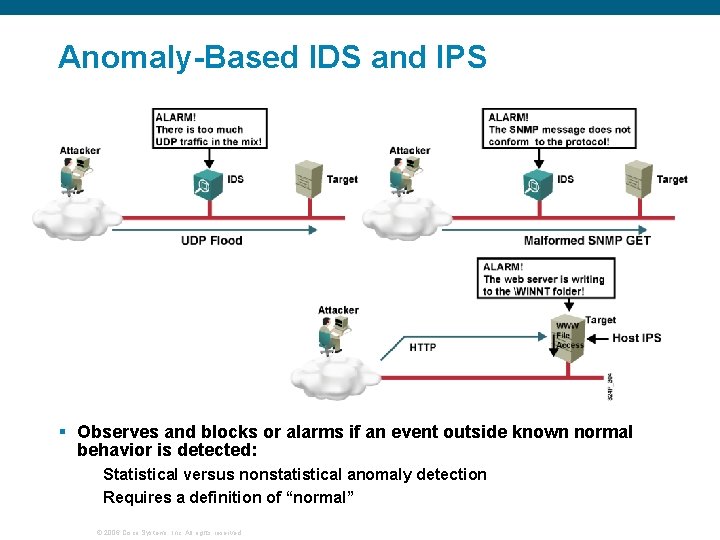
Anomaly-Based IDS and IPS § Observes and blocks or alarms if an event outside known normal behavior is detected: Statistical versus nonstatistical anomaly detection Requires a definition of “normal” © 2006 Cisco Systems, Inc. All rights reserved.

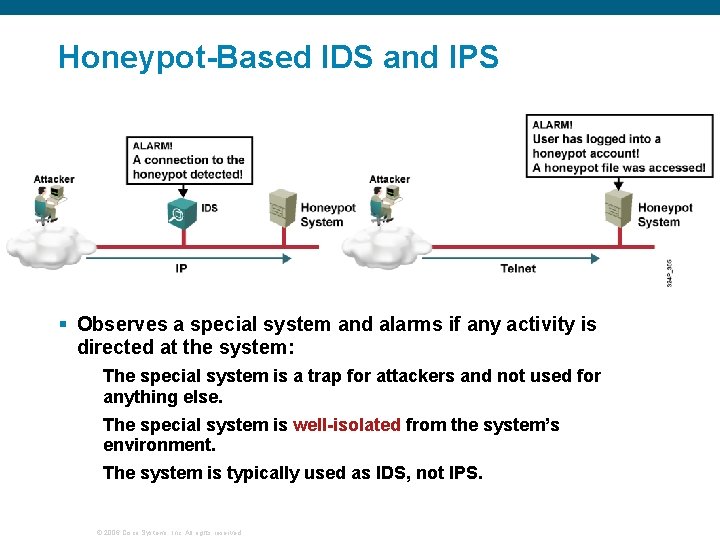
Honeypot-Based IDS and IPS § Observes a special system and alarms if any activity is directed at the system: The special system is a trap for attackers and not used for anything else. The special system is well-isolated from the system’s environment. The system is typically used as IDS, not IPS. © 2006 Cisco Systems, Inc. All rights reserved.

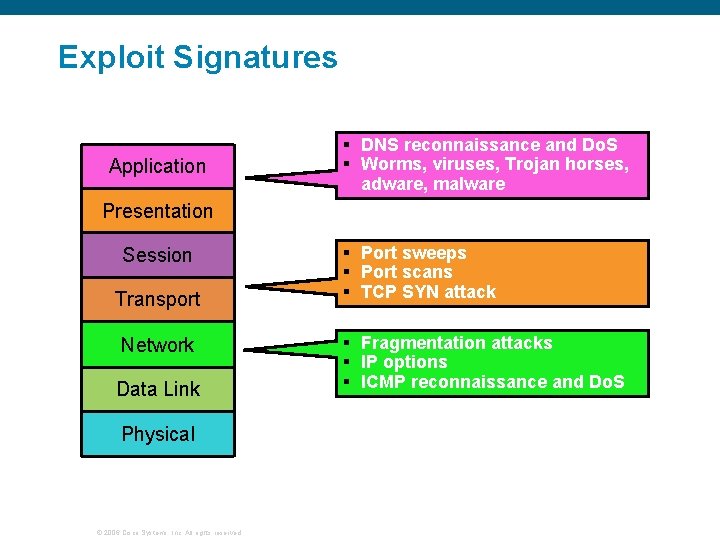
Signature Categories § Four types of signatures: Exploit signatures match specific known attacks. Connection signatures match particular protocol traffic. String signatures match string sequences in data. Do. S signatures match Do. S attempts. § Signature selection is based on: Type of network protocol Operating system Service Attack type § Number of available signatures: About 1500 for IPS sensors, 1200 for IOS IPS © 2006 Cisco Systems, Inc. All rights reserved.

Exploit Signatures Application § DNS reconnaissance and Do. S § Worms, viruses, Trojan horses, adware, malware Presentation Session Transport Network Data Link Physical © 2006 Cisco Systems, Inc. All rights reserved. § Port sweeps § Port scans § TCP SYN attack § Fragmentation attacks § IP options § ICMP reconnaissance and Do. S

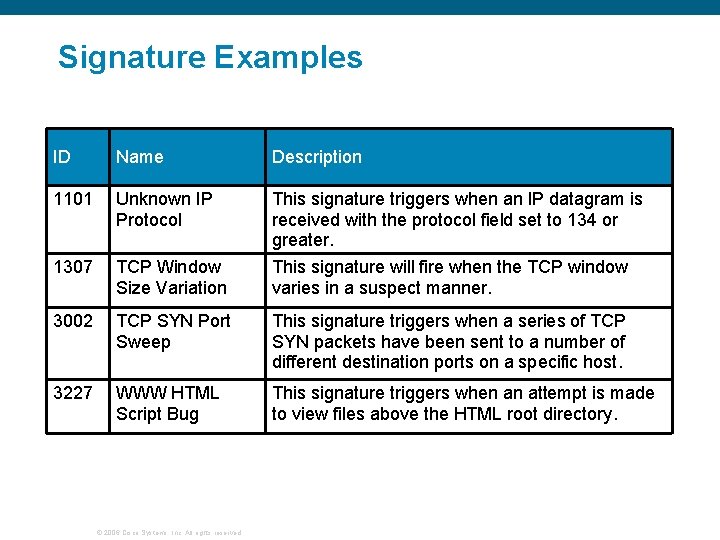
Signature Examples ID Name Description 1101 Unknown IP Protocol 1307 TCP Window Size Variation This signature triggers when an IP datagram is received with the protocol field set to 134 or greater. This signature will fire when the TCP window varies in a suspect manner. 3002 TCP SYN Port Sweep This signature triggers when a series of TCP SYN packets have been sent to a number of different destination ports on a specific host. 3227 WWW HTML Script Bug This signature triggers when an attempt is made to view files above the HTML root directory. © 2006 Cisco Systems, Inc. All rights reserved.

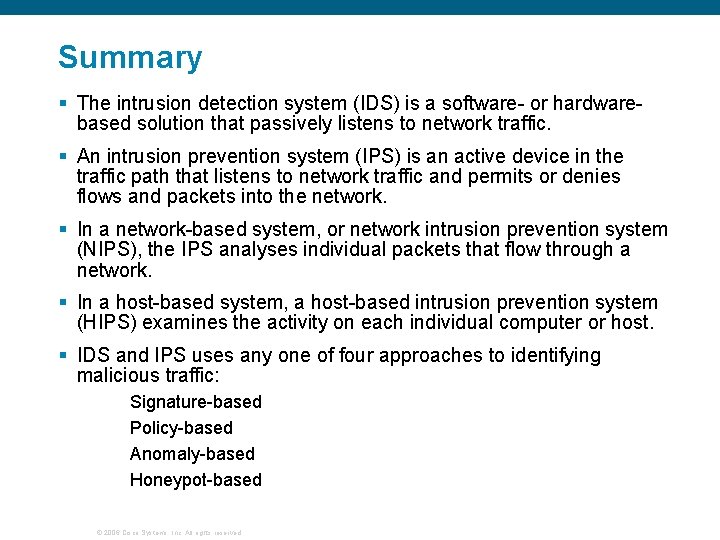
Summary § The intrusion detection system (IDS) is a software- or hardwarebased solution that passively listens to network traffic. § An intrusion prevention system (IPS) is an active device in the traffic path that listens to network traffic and permits or denies flows and packets into the network. § In a network-based system, or network intrusion prevention system (NIPS), the IPS analyses individual packets that flow through a network. § In a host-based system, a host-based intrusion prevention system (HIPS) examines the activity on each individual computer or host. § IDS and IPS uses any one of four approaches to identifying malicious traffic: Signature-based Policy-based Anomaly-based Honeypot-based © 2006 Cisco Systems, Inc. All rights reserved.

Q and A © 2006 Cisco Systems, Inc. All rights reserved.

Resources § Cisco Intrusion Prevention System http: //cisco. com/en/US/partner/products/sw/secursw/ps 2113/ind ex. html § Cisco Intrusion Prevention System Support http: //cisco. com/en/US/partner/products/sw/secursw/ps 2113/tsd _products_support_series_home. html © 2006 Cisco Systems, Inc. All rights reserved.

© 2006 Cisco Systems, Inc. All rights reserved.