IKEv 2 Configuration Payload Integration http www vpnc









![Host Configuration Attributes • Radius [RFC 2865] defines many attributes. • Attributes extensible via Host Configuration Attributes • Radius [RFC 2865] defines many attributes. • Attributes extensible via](https://slidetodoc.com/presentation_image_h/df637a9d04f59cb38ba935a9d9ec4d51/image-17.jpg)



- Slides: 23

IKEv 2 Configuration Payload Integration http: //www. vpnc. org/temp-draft-lebovitz-ipsec-scalable-ikev 2 cp-00. txt Full presentation - http: //www. employees. org/~ddukes Darren Dukes, ddukes@cisco. com Gregory Lebovitz, gregory@netscreen. com

Agenda • • • IRAC Configuration Problem The Configuration Payload Private Pools DHCP Assigned Addresses RADIUS Assigned Addresses

The IRAC Configuration Problem • IPsec Remote Access Clients (IRACs) need to have a private IP address in order to specify TSi before creating CHILD-SAs. • How do we assign a unique IP address to the client before creating CHILD-SAs?

The Configuration Payload • Allows an IRAC to acquire bootstrapping configuration within IKEv 2 IKE_AUTH exchange • No extension of the IKE_AUTH exchange or new exchange (no “phase 1. 5”) • A generic mechanism to pass minimal bootstrapping parameters for CHILD-SA creation • May be used with any configuration server, such as DHCP, RADIUS, LDAP, etc.

IP Address Bootstrapping • CP(CFG_REQUEST) is sent by an IRAC in IKE_AUTH to request an IP address from an IPsec Remote Access Server (IRAS) • IRAS processes the CP(CFG_REQUEST) and assigns an address to the IRAC from internal or external configuration servers • IRAS sends a CP(CFG_REPLY) to IRAC with minimal IP address configuration so a CHILD-SA can establish.

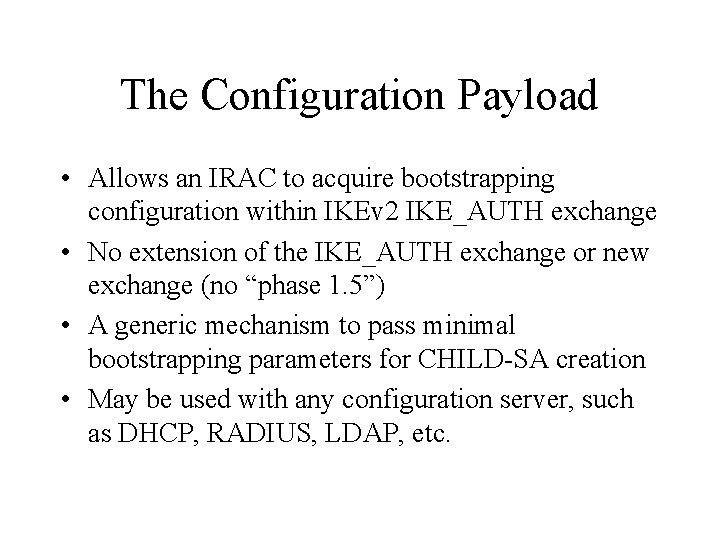
CP and Private Pools IKE Gtwy IRAC (IKE-client) IRAS IKEv 2 Message 1 HDR, SAi 1, KEi, Ni IKEv 2 Message 2 HDR, SAr 1, KEr, Nr, [CERTREQ] IKEv 2 Message 3 HDR, SK {IDi, [CERT, ] [CERTREQ, ] [IDr, ] CP(CFG_REQUEST), SAi 2, TSi, TSr} IKEv 2 Message 4 HDR, SK {IDr, [CERT, ] AUTH, CP(CFG_REPLY), SAr 2, TSi, TSr } CFG_REPLY: Internal_IP 4_ADDR Internal_IP 4_NETMASK Internal_IP 4_DNS Internal_IP 4_NBNS

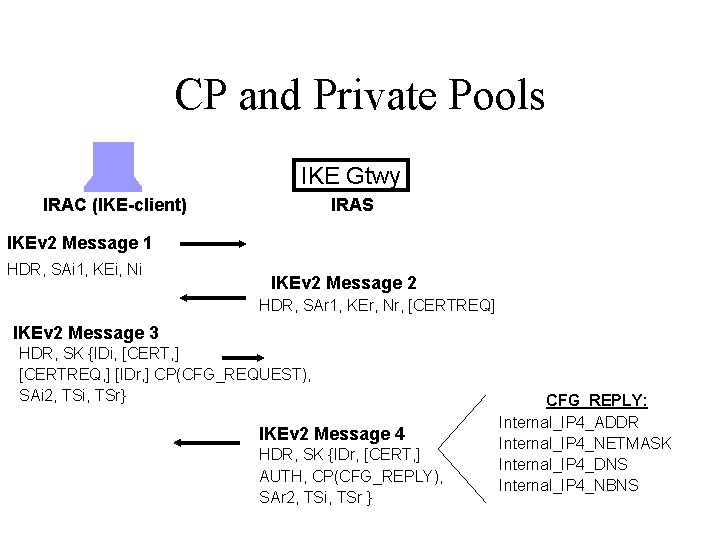
On-IRAS Pools • A private pool of addresses may be configured locally on an IRAS and assigned to requesting IRACs • Works for very small deployments • Won’t scale well for larger deployments.

OFF-IRAS Pools RADIUS Database IRAC (IKE-client) DHCP Server IKE Gateway IRAS proxies the IRAC CP(CFG_REQUEST) for an IP address to an external configuration server Other Configuration Server

Must be able to satisfy CP via DHCP • DHCP is widely deployed for address assignment in LANs • DHCP has many options that may be useful for an IRAC to retrieve

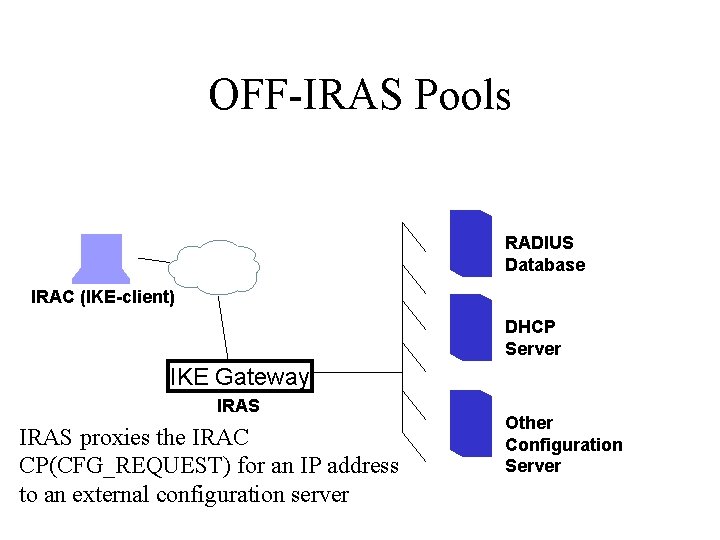
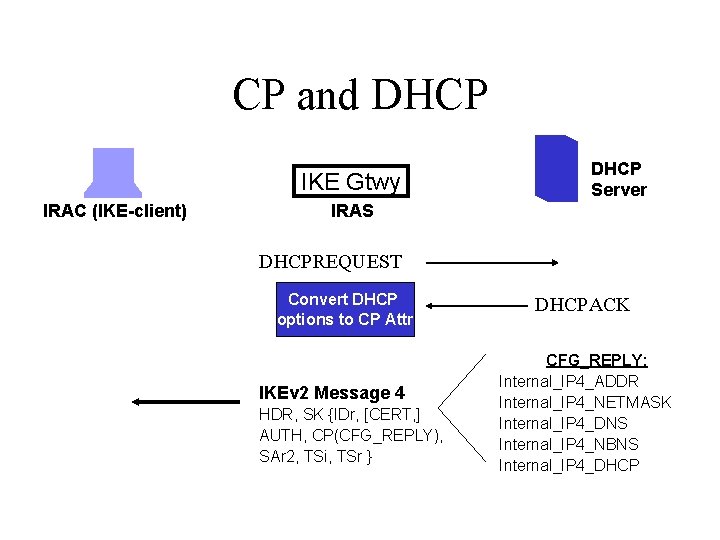
DHCP Assigned Addresses • A DHCP server may be used to assign addresses to the IRAS on behalf of an IRAC • IRAS is responsible for requesting IP addresses on a per-IRAC basis from the DHCP server when it receives a CP(CFG_REQUEST) • IRAS sends the IP address and other minimal configuration to the IRAC via a CP(CFG_REPLY) once an address is retrieved

CP and DHCP IKE Gtwy IRAC (IKE-client) DHCP Server IRAS IKEv 2 Message 1 HDR, SAi 1, KEi, Ni IKEv 2 Message 2 HDR, SAr 1, KEr, Nr, [CERTREQ] IKEv 2 Message 3 Request address HDR, SK {IDi, [CERT, ] from DHCP [CERTREQ, ] [IDr, ] CP(CFG_REQUEST), Server SAi 2, TSi, TSr} DHCPDISCOVER DHCPOFFER

CP and DHCP IKE Gtwy IRAC (IKE-client) DHCP Server IRAS DHCPREQUEST Convert DHCP options to CP Attr IKEv 2 Message 4 HDR, SK {IDr, [CERT, ] AUTH, CP(CFG_REPLY), SAr 2, TSi, TSr } DHCPACK CFG_REPLY: Internal_IP 4_ADDR Internal_IP 4_NETMASK Internal_IP 4_DNS Internal_IP 4_NBNS Internal_IP 4_DHCP

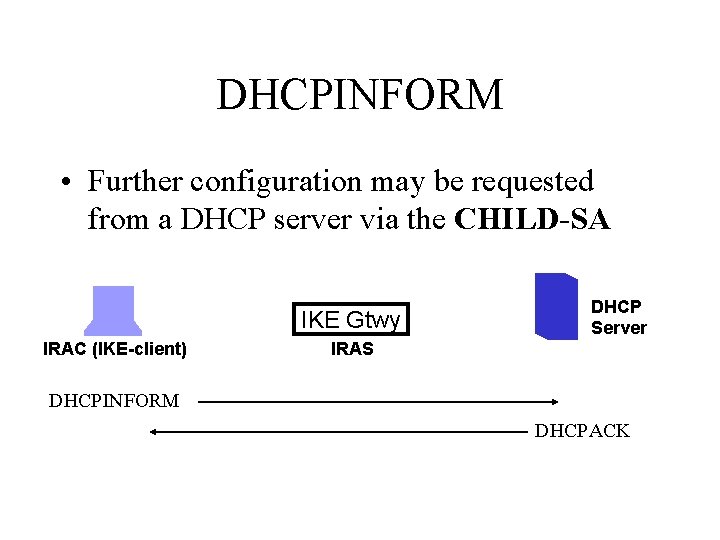
DHCPINFORM • Further configuration may be requested from a DHCP server via the CHILD-SA IKE Gtwy IRAC (IKE-client) DHCP Server IRAS DHCPINFORM DHCPACK

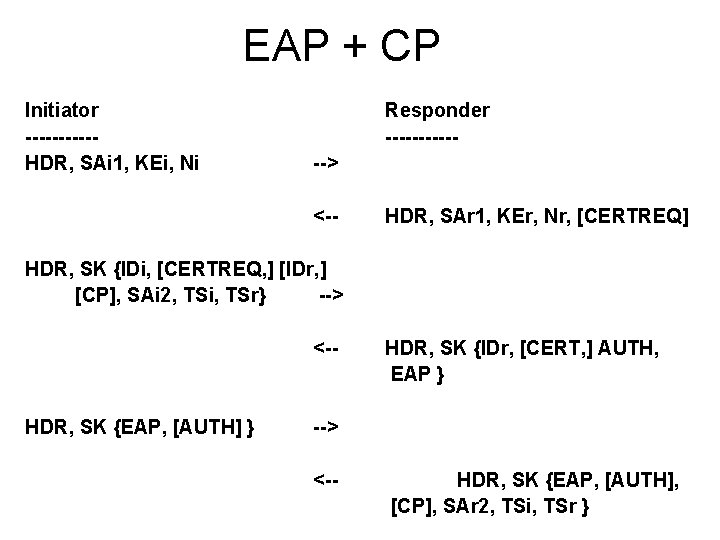
EAP + CP Initiator -----HDR, SAi 1, KEi, Ni Responder ------> <-- HDR, SAr 1, KEr, Nr, [CERTREQ] HDR, SK {IDi, [CERTREQ, ] [IDr, ] [CP], SAi 2, TSi, TSr} --> <-- HDR, SK {EAP, [AUTH] } HDR, SK {IDr, [CERT, ] AUTH, EAP } --> <-- HDR, SK {EAP, [AUTH], [CP], SAr 2, TSi, TSr }

MUST be able to satisfy CP via RADIUS • Mature as a client configuration mechanism • Widely implemented • Predominant client configuration mechanism in use by ISPs and large enterprises today

CP w/ RADIUS needs EAP • RADIUS is very user/pass centric. Needs them to perform db lookup. RFC 2865: – SHOULD send User-Name – MUST send Password (User or CHAP) • User entry in db contains list of requirements, and optional attributes. • RADIUS attributes map to CP attributes
![Host Configuration Attributes Radius RFC 2865 defines many attributes Attributes extensible via Host Configuration Attributes • Radius [RFC 2865] defines many attributes. • Attributes extensible via](https://slidetodoc.com/presentation_image_h/df637a9d04f59cb38ba935a9d9ec4d51/image-17.jpg)
Host Configuration Attributes • Radius [RFC 2865] defines many attributes. • Attributes extensible via Vendor Specific Attributes (VSAs) • Attributes relative to CP: Pre-Defined - IP address - Netmask - Session Timeout VSA - Prim/Secondary DNS - Prim/Secondary WINS * List not exhaustive

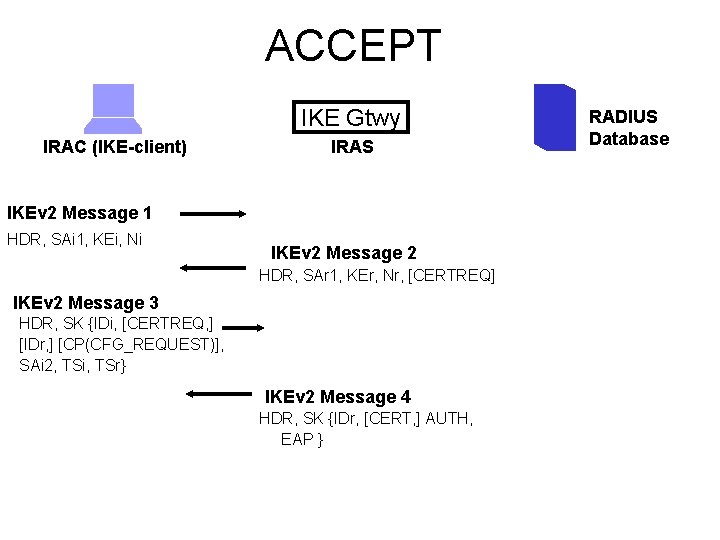
Example: ACCEPT • Accept shown next • Reject is easy • Challenge is mutation of Accept, but pretty close. (see the document for details).

ACCEPT IKE Gtwy IRAC (IKE-client) IRAS IKEv 2 Message 1 HDR, SAi 1, KEi, Ni IKEv 2 Message 2 HDR, SAr 1, KEr, Nr, [CERTREQ] IKEv 2 Message 3 HDR, SK {IDi, [CERTREQ, ] [IDr, ] [CP(CFG_REQUEST)], SAi 2, TSi, TSr} IKEv 2 Message 4 HDR, SK {IDr, [CERT, ] AUTH, EAP } RADIUS Database

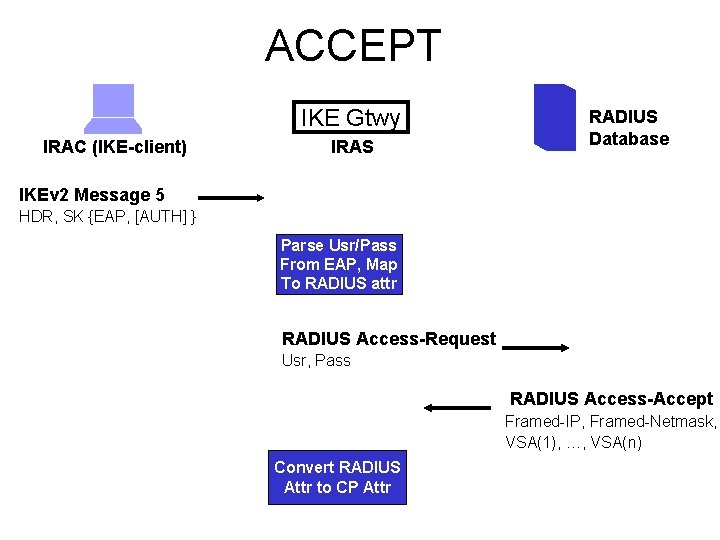
ACCEPT IKE Gtwy IRAC (IKE-client) IRAS RADIUS Database IKEv 2 Message 5 HDR, SK {EAP, [AUTH] } Parse Usr/Pass From EAP, Map To RADIUS attr RADIUS Access-Request Usr, Pass RADIUS Access-Accept Framed-IP, Framed-Netmask, VSA(1), …, VSA(n) Convert RADIUS Attr to CP Attr

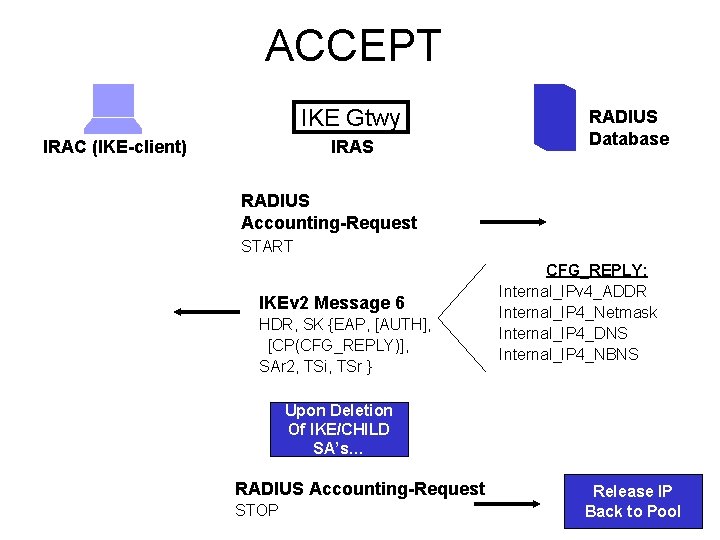
ACCEPT IKE Gtwy IRAC (IKE-client) IRAS RADIUS Database RADIUS Accounting-Request START IKEv 2 Message 6 HDR, SK {EAP, [AUTH], [CP(CFG_REPLY)], SAr 2, TSi, TSr } CFG_REPLY: Internal_IPv 4_ADDR Internal_IP 4_Netmask Internal_IP 4_DNS Internal_IP 4_NBNS Upon Deletion Of IKE/CHILD SA’s… RADIUS Accounting-Request STOP Release IP Back to Pool

Advancement • Become WG document? • If so, how to proceed?

Volunteers? ? • Section for LDAP • Section for DHCPv 6.