Identifying Computer Attacks Tips Tricks and Tools Kai
























- Slides: 31

Identifying Computer Attacks – Tips, Tricks and Tools Kai Axford, CISSP, MCSE-Security Sr. Security Strategist Microsoft Corporation kaiax@microsoft. com http: //blogs. technet. com/kaiaxford

“The server is acting weird. ”

The Demo Disclaimer… Is everyone paying attention now? Remember, SQL Injection is the result of improper form validation…. . and can happen on ANY database server that supports ANSI 99 (incl My. SQL, Oracle, DB 2). No, I will not give you those tools. I don’t care what you do or who you work for…. (besides, if you really DO work for the NSA, you’ve got better tools than this anyway). If you don’t ask, I don’t have to say no.

Agenda The Incident and the 31337 h 4 XØr Identifying the Attack and Proving it Summary & Resources

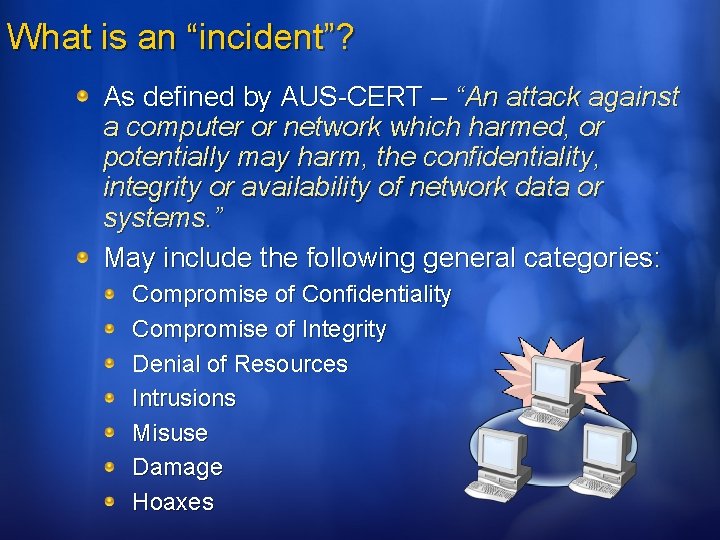
What is an “incident”? As defined by AUS-CERT – “An attack against a computer or network which harmed, or potentially may harm, the confidentiality, integrity or availability of network data or systems. ” May include the following general categories: Compromise of Confidentiality Compromise of Integrity Denial of Resources Intrusions Misuse Damage Hoaxes

The components of an incident Howard, John D. “A Common Language for Computer Security Incidents” 1998. http: //www. cert. org/research/taxonomy_988667. pdf

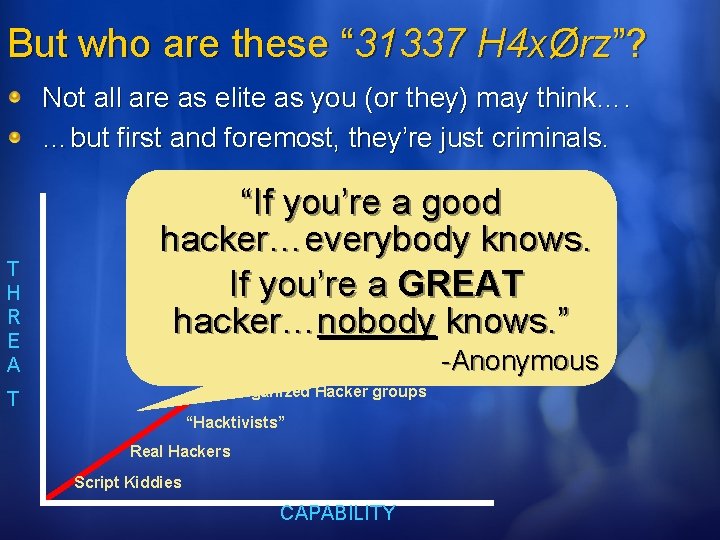
But who are these “ 31337 H 4 xØrz”? Not all are as elite as you (or they) may think…. …but first and foremost, they’re just criminals. T H R E A “If you’re a good. Cyber. War Intelligence hacker…everybody. Foreign knows. Terrorists If you’re a GREAT Organized Crime hacker…nobody knows. ” Competitors (Foreign & Domestic) -Anonymous Organized Hacker groups T “Hacktivists” Real Hackers Script Kiddies CAPABILITY

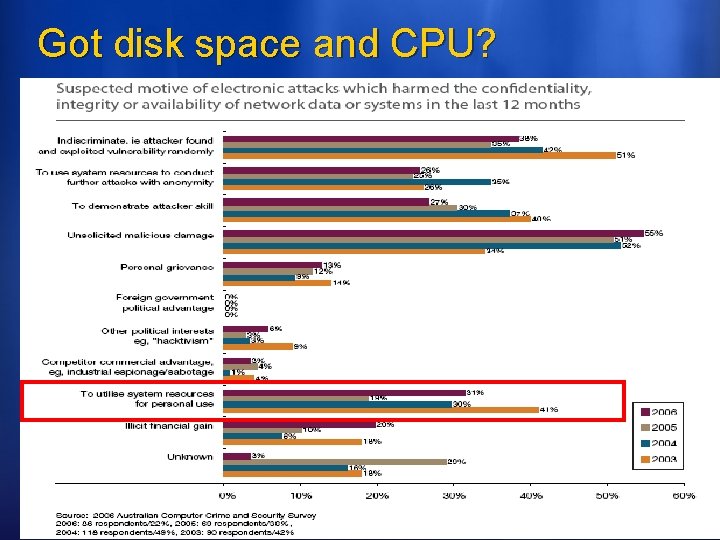
Got disk space and CPU?

Attack of the 10, 000 Bots A Bot. Net of 10, 000 machines can: 4. 5 million SYN packets /second 930, 000 HTTP-GET requests /second 1. 8 GBPS Uplink 4. 5 GBPS Downlink (. . and you thought he only helped Luke)

It’s getting worse…

So what is “Incident Handling”? Incident Handling - Actions taken to protect and restore the normal operating condition of computers and the information stored in them when an adverse event occurs. Incentives for efficient incident handling: Economic Protecting Proprietary / Classified / Sensitive Information Operational / Business Continuity Public Relations Legal / Regulatory Compliance Safety

Did something occur? How do you know? Determine what the problem is and to assess its magnitude Major sources of information Log files and syslog output Wrapper tools (e. g. , TCP wrapper) Firewall logs (personal and network) Intrusion detection systems (IDS) and prevention systems (IPS) Analyze all anomalies Gather proof!

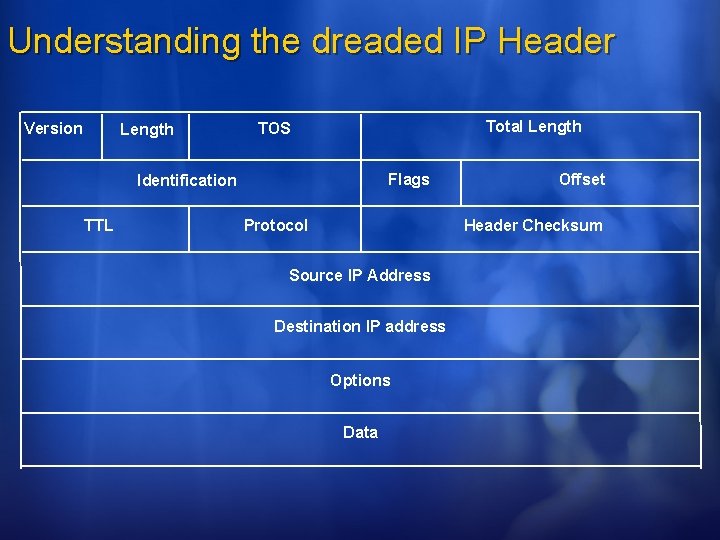
Understanding the dreaded IP Header Version Length Total Length TOS Flags Identification TTL Protocol Offset Header Checksum Source IP Address Destination IP address Options Data

What should I be looking for? Are any IP Header fields suspect? Is the Source IP address suspect? Is odd fragmentation occurring? Does the size of the packet raise concerns? Are any TCP header fields suspect? Is the destination port a valid service? Does the traffic follow RFC standards? What are the timestamps of the traffic? Mandia, Kevin and Chris Prosise. “Incident Response: Fighting Computer Crime”. 2001. Osborne/Mc. Graw Hill.

Event logs: Some Logon/Logoff Event IDs 528 - Successful Logon 529 - Logon Failure: Unknown user name or bad password 530 - Logon Failure: Account logon time restriction violation 531 - Logon Failure: Account currently disabled 532 - Logon Failure: The specified user account has expired 533 - Logon Failure: User not allowed to logon at this computer 534 - Logon Failure: User not granted requested logon type at this machine 535 - Logon Failure: The specified account’s password has expired 539 - Logon Failure: Account locked out 540 - Successful Network Logon (Win 2000, XP, 2003 Only)

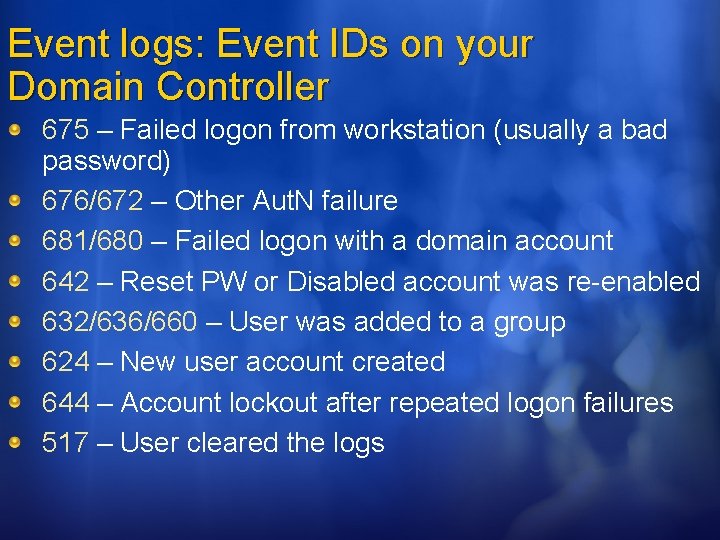
Event logs: Event IDs on your Domain Controller 675 – Failed logon from workstation (usually a bad password) 676/672 – Other Aut. N failure 681/680 – Failed logon with a domain account 642 – Reset PW or Disabled account was re-enabled 632/636/660 – User was added to a group 624 – New user account created 644 – Account lockout after repeated logon failures 517 – User cleared the logs

“Are you sure they did it? ” Electronic Discovery

Kai’s Tools and Tips…(see a common trend? ) Process Explorer – Free tool that provides detailed process info. Task manager on steroids Auto. Runs – Free util that checks all the startup folders and reg keys Wire Shark (formerly Ethereal)– Free OSS network sniffer. Very pretty. md 5 sum – Free file integrity verifier. Get a hash from a “known good” file. Event. Comb. MT – Free event ID parser. Part of the …. . there are TONS more free tools!

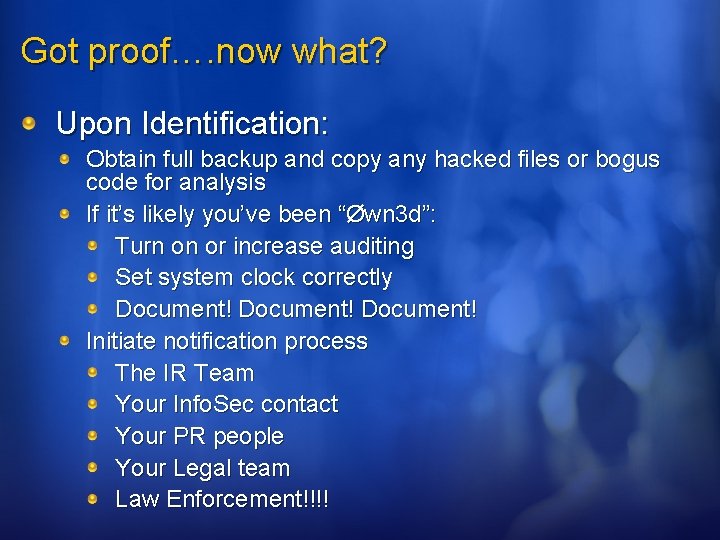
Got proof…. now what? Upon Identification: Obtain full backup and copy any hacked files or bogus code for analysis If it’s likely you’ve been “Øwn 3 d”: Turn on or increase auditing Set system clock correctly Document! Initiate notification process The IR Team Your Info. Sec contact Your PR people Your Legal team Law Enforcement!!!!

Digital Forensics First and foremost: Kai is not a lawyer. Always consult your local law enforcement agency and legal department first! Digital forensics is SERIOUS BUSINESS You can easily shoot yourself in the foot by doing it incorrectly Get some in-depth training …this is not in-depth training!!! (Nor is it legal advice. Be smart. The job you save may be your own. ) I just want to spend a few minutes showing you some common forensic tools and how they can help.

Encase – Guidance Software, Inc. http: //www. guidancesoftware. com Very popular in private corporations En. Script Macro Language allows for creation of powerful scripts and filters to automate tasks Safely preview a disk before acquisition Picture gallery shows thumbnails of all images Virtually boot disk image using VMWare to allow first-hand view of the system

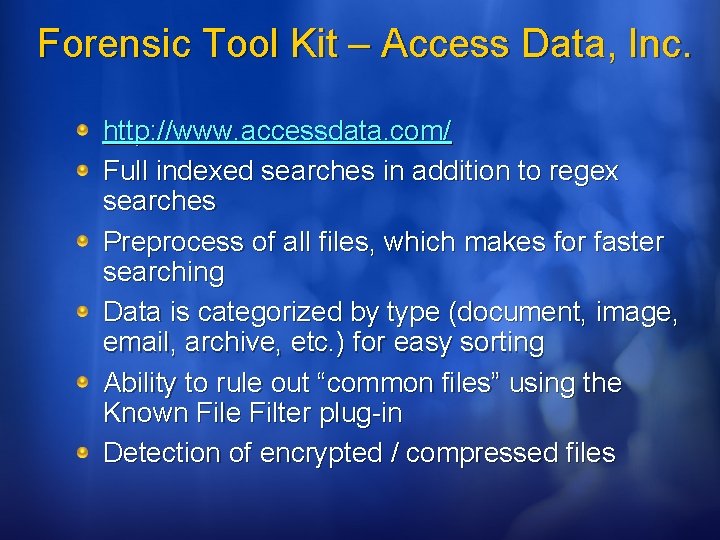
Forensic Tool Kit – Access Data, Inc. http: //www. accessdata. com/ Full indexed searches in addition to regex searches Preprocess of all files, which makes for faster searching Data is categorized by type (document, image, email, archive, etc. ) for easy sorting Ability to rule out “common files” using the Known File Filter plug-in Detection of encrypted / compressed files

Open Source Forensics Tools The Sleuth Kit (TSK) and Autopsy Written by Brian Carrier (www. sleuthkit. org) TSK is command line; Autopsy provides GUI for TSK. Runs on *nix platforms. Client server architecture allows multiple examiners to use one central server Allows basic recovery of deleted data and searching Lots of manual control to the investigator, but is light on the automation Helix – e-Fense Customized Knoppix disk that is forensically safe Includes improved versions of ‘dd’ Terminal windows log everything for good documentation Includes Sleuthkit, Autopsy, chkrootkit, and others Includes tools that can be used on a live Windows machine, including precompiled binaries and live acquisition tools

“I have you now…. ” – D. Vader Digital Forensics

Acquiring Data should always be done carefully… Always preserve originals and ONLY work on copies! Utilize HW write blockers to ensure MAC times are not altered Your legal team and law enforcement will thank you!

Have a forensics jumpkit! Critical for the success of the investigation

Other stuff Some incidents may occur on a SAN or large servers with special complications Cannot go offline OR They have so much storage that it cannot be successfully imaged (or have RAID, so an image will be technically infeasible) The best option is still to perform some sort of backup, at least of the suspicious files and logs, then analyze them off-line A tape backup will not include all the information such as slack space data, but it may be the only alternative

Additional Microsoft Resources • NEW! Fundamental Computer Investigation Guide For Windows http: //www. microsoft. com/technet/security/guidance/disasterre covery/computer_investigation • Windows Security Logging and Other Esoterica http: //blogs. msdn. com/ericfitz/ • The Security Monitoring and Attack Detection Planning Guide http: //www. microsoft. com/technet/security/topics/auditingandm onitoring/securitymonitoring/default. mspx • Microsoft Windows Security Resource Kit v 2. 0. ISBN: 0735621748

My Digital Forensics Reading List File System Forensic Analysis. Brian Carrier ISBN: 0 -321 -26817 -2 Digital Evidence and Computer Crime. Eoghan Casey. ISBN: 012162885 X Incident Response: Investigating Computer Crime. Kevin Mandia & Chris Prosise ISBN: 007222696 X Hacking Exposed: Computer Forensics. Chris Davis, Aaron Phillip ISBN: 0072256753

Questions and Answers

© 2006 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.