Gerard Verweij Partner Information Security The Security audit

























- Slides: 32

Gerard Verweij Partner Information Security

The Security audit • Security requirements, issues and challenges • Security Framework • Policies and Standards • Tips

A Framework for understanding Information Security Lets start with a definition of Information Security Information security includes the people, processes and technology necessary to ensure the confidentiality, integrity and availability of an organizations Information resources in whatever form those resources exist

Security requirements, issues and challenges

Current key Questions to Ask • • How vulnerable / exposed is your organization to security threats and interruptions? How would you know that you were exposed or under attack? What is your organization's ability to respond to security incidents? (i. e. , denial of service, cyber-crime) Are you getting value for your security dollar spent? Are there any cost or efficiency opportunities? How well is security integrated into new business and technology initiatives? Are you taking your business to the Internet? Have you thought through the security ramifications? How well does your current security infrastructure (i. e. , organization, process, policy, technology) match your future business strategy and business needs/requirements? How do you compare to your peers? Your industry?

Defining the Business Problem “The key question is not whether to deploy internet technology – companies have no choice if they want to stay competitive – but how to deploy it. ” Strategy and the Internet Harvard Business Review March ’ 01 The medium and longer-term outlook for security remains strong: Michael Porter - Companies will increasingly employ the Internet as a means for competitive advantage - Companies are finding that chronic under-investment in security is hampering the implementation of their Internet initiatives

Security. . . the Threat Customers Suppliers Vendors Employees Opportunity

How do you manage the user’s identity and credentials across the enterprise application landscape?

e-Business Security Challenges • Protect corporate network resources against internal and external threats • Provide worldwide connectivity for mobile and remote employees and customers • Use the Internet to lower wide area data communication costs • Provide business partners with selective network access through a secure extranet • Guarantee secure network’s performance, reliability and availability • Define and enforce user-level security policies across the network • Immediately detect and respond to attacks and suspicious activity against the network • Securely and efficiently manage the network’s IP address infrastructure • Implement and open security solution that allows integration with other applications • Manage the total cost of ownership across the secure network

The Five Worst Security Mistakes End Users Make: 1) Opening unsolicited email attachments without verifying their source and checking their content first. 2) Failing to install security patches, especially MS Office, IE and Netscape. 3) Installing screen savers or games without safety guarantees. 4) Not making and testing backups. 5) Connecting a modem to a phone line while the same computer is connected to a LAN.

The Ten Worst Mistakes Information Technology People Make: Connecting systems to the Internet before hardening them. (removing unnecessary devices and patching necessary ones). 2) Connecting test systems to the Internet with default accounts and passwords. 3) Failing to update systems when security vulnerabilities are found and patches or upgrades are available. 4) Using telnet and other unencrypted protocols for managing systems, routers, firewalls and PKI (Public Key Infrastructure). 5) Giving users passwords over the phone, or changing passwords in response to telephone or personal request when the requester is not authenticated. 6) Failing to maintain and test backups. 7) Running unnecessary services, especially ftpd, telnetd, finger, rpc, mail, rservices (some of these are Unix specific). 8) Implementing firewalls with rules that allow malicious or dangerous traffic incoming or outgoing. 9) Failing to implement or update virus detection software. 10)Failing to educate users on that to look for and what to do when they see a potential security problem. 1)

The Seven Worst Security Mistakes Senior Executives Make: 1) Assigning untrained people to maintain security and providing neither the training nor the time to make it possible to learn and do the job. 2) Failing to understand the relationship of information security to the business problem - they understand physical security but do not see the consequences of poor information security. 3) Failing to deal with the operational aspects of security: making a few fixes and then not allowing the follow through necessary to ensure that problems stay fixed. 4) Relying primarily on a firewall. 5) Failing to realize how much money their information and organizational reputations are worth. 6) Authorizing reactive, short term fixes so problems re-emerge rapidly. 7) Pretending the problem will go away if they ignore it.

Enterprise Security Architecture • Lack of a comprehensive security framework leads to dysfunctional, disconnected, and/or ineffective security organizations. • Inconsistently applied policies and standards across domains (inter- and extra-enterprise) can open an organization up to security vulnerabilities. • Need for a centralized security content management system and intuitive user interface to content. • Limited ability to enforce security policies, procedures, and standards. • Lack of awareness of good security hygiene.

Security Monitoring and Management is Challenging • Requires skilled security experts • Technology infrastructure to support them • Significant resources researching and tracking latest threats and vulnerabilities • There is a rise in web server and virus attacks • Must be done 24 x 7 x 365

Security Monitoring and Management is expensive 8 -5 24 x 7 “Personnel cost alone for setting up a starter monitoring operation with problem resolution will run at least $60, 000 per month” – Forrester Research

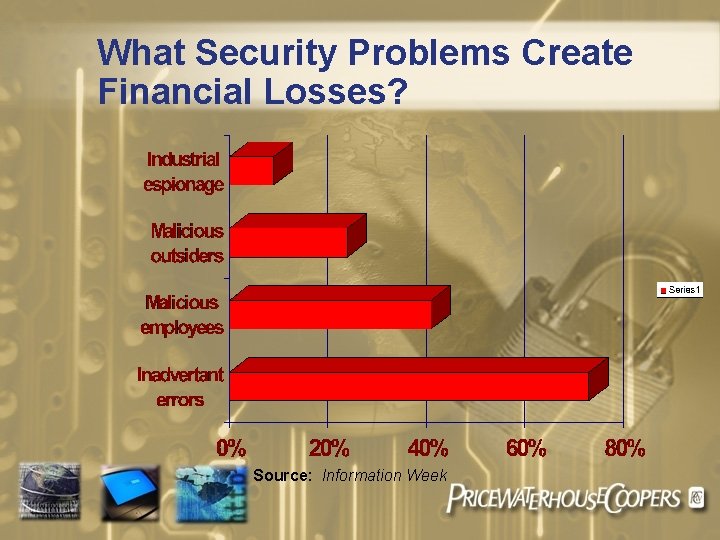
What Security Problems Create Financial Losses? Source: Information Week

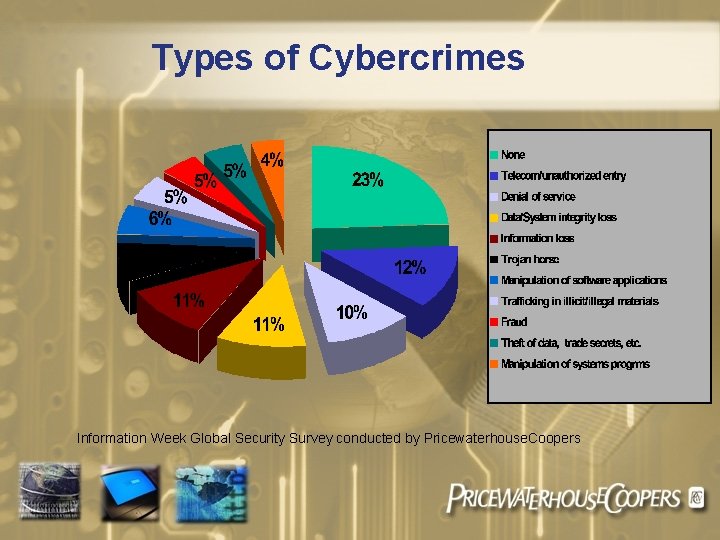
Types of Cybercrimes Information Week Global Security Survey conducted by Pricewaterhouse. Coopers

And It’s Probably Worse Than We Think. . . • Do. D Controlled Study – Machines Attacked: – Machine Penetrated: – Attacks Detected: – Attacks Reported: 18 38, 000 24, 700 (65%) 988 (4%) 267 (27%)

So what does this all mean? • There are new security challenges almost every day • Security has shifted from keeping people out to letting people in • It’s becoming more and more challenging to provide adequate security • It’s becoming more and more challenging to perform adequate security audits • Security audits are needed to determine where major concerns are, what the specific issues are, and how risks can be mitigated

Security Framework

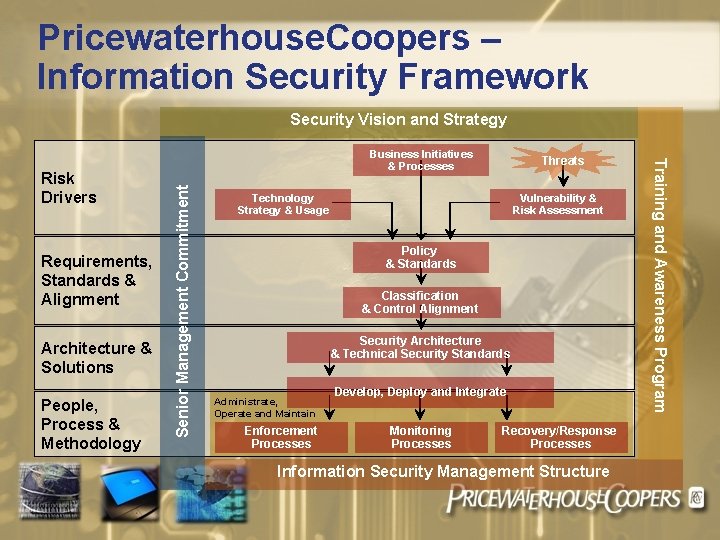
Pricewaterhouse. Coopers – Information Security Framework Security Vision and Strategy Architecture & Solutions People, Process & Methodology Senior Management Commitment Requirements, Standards & Alignment Threats Technology Strategy & Usage Vulnerability & Risk Assessment Policy & Standards Classification & Control Alignment Security Architecture & Technical Security Standards Administrate, Operate and Maintain Enforcement Processes Develop, Deploy and Integrate Monitoring Processes Recovery/Response Processes Information Security Management Structure Training and Awareness Program Risk Drivers Business Initiatives & Processes

Framework Cornerstones Ø Security Vision and Strategy Ø Ø Senior Management Commitment Ø Ø Commitment in principle and in practice Support through policy, directives and resource allocation Determination of risk tolerance Training and Awareness Program Ø Ø Ø Mission statement, guiding principles and philosophy Strategy for addressing information protection Security Committee as an authoritative decision and communication vehicle Communication covers all levels of an organization and aspects of information security Continuous, pervasive and an integral part of training curriculum Security Management Structure Ø Ø Centralized and decentralized resource deployment Cross functional roles and responsibilities

The Framework and security audits • State of Security; perform an overall gap analysis – Where are my major concerns? – How do I compare to standards, best practices and peers? – Do I get value for money? • Perform detailed security audits for certain areas in the Security Framework

Policies and standards

Policy provides the cornerstone of your information security program

Information Security Policy • Policies – Management instructions on how an organization is to be run – A collection of related standards – Mandatory conditions that the organization requires • Standards – Independent thoughts or ideas relating to security – Make specific reference of technologies and methodologies – Different from Controls • Technical Controls – Technology specific control requirements that provide platform specific instructions to policy and standards compliance – Focused at the technology level, Win 2 K, Solaris, MVS, etc

What Policy Framework Should you Use? • There are many examples of Policies and Standards that can be deployed within an organization • While there are similarities in many of the components of these standards there are important differences as well. • Examples of Information Technology Control Standards: – Carnegie Mellon’s Capability Maturity ModelÒ – ISO 17799 Security Standard adopted from British Standard 7799 – SSE’s Capability Maturity ModelÒ for system security – ISACA’s COBIT • Standards can be substituted or supplemented by best practices

Tips

Take a top down approach • Perform an objective comprehensive assessment of the current “State of Security” • Get an understanding of how effectively security has linked in to business and technology initiatives • Get an understanding of where the major risks and concerns are, and what the issues and root causes are • Zoom in on the areas of concern

Develop a state of the art and objective standards framework • Choose the appropriate framework: – ISO – Cobit – CMM – Best practices • Tailor the standards framework to specific needs

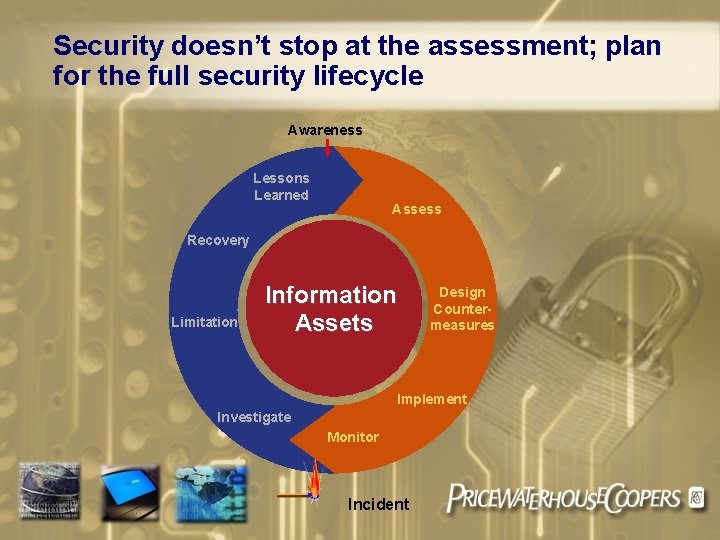
Security doesn’t stop at the assessment; plan for the full security lifecycle Awareness Lessons Learned Assess Recovery Limitation Information Assets Design Countermeasures Implement Investigate Monitor Incident

Ensure all ingredients for an effective and efficient audit are in place • • Trained security auditors Subject Matter Experts Methodologies A Framework Standards and best practices Tools A follow up plan