George Mason University and Sonic WALL The Phishing






















- Slides: 30

George Mason University and Sonic. WALL The Phishing Ecosystem Analyzing the Dynamics for Maximum Defense Tuesday, April 11 th 2006 – 2: 45 pm

Agenda § Overview of the Phishing Ecosystem § Questions for the panel § § § Scope of the problem What did GMU do Results Phishing education Other email issues § Ask questions as we go § Wrap up & lessons learned 2

Let’s Go Phishing

The Phishing Checklist 4 1. Get an email list 2. Develop the attack 3. Locate sites to send phishing email from 4. Locate sites to host the phishing site 5. Launch the attack 6. Collect the information 7. Transform into cash

A bad day phishin’, beats a good day workin’ § § § 2, 000 emails are sent 5% get to the end user – 100, 000 (APWG) 5% click on the phishing link – 5, 000 (APWG) 2% enter data into the phishing site – 100 (Gartner) $1, 200 from each person who enters data (FTC) Our potential reward: $120, 000 In 2005 David Levi made over $360, 000 from 160 people using an e. Bay Phishing scam 5

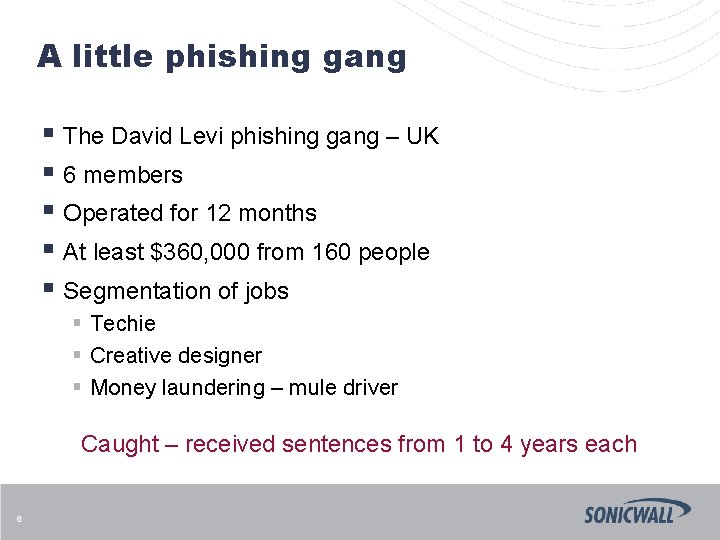
A little phishing gang § The David Levi phishing gang – UK § 6 members § Operated for 12 months § At least $360, 000 from 160 people § Segmentation of jobs § Techie § Creative designer § Money laundering – mule driver Caught – received sentences from 1 to 4 years each 6

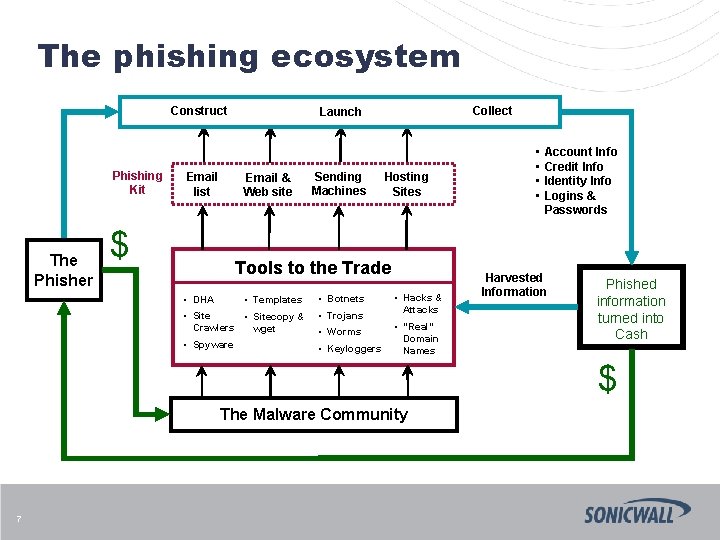
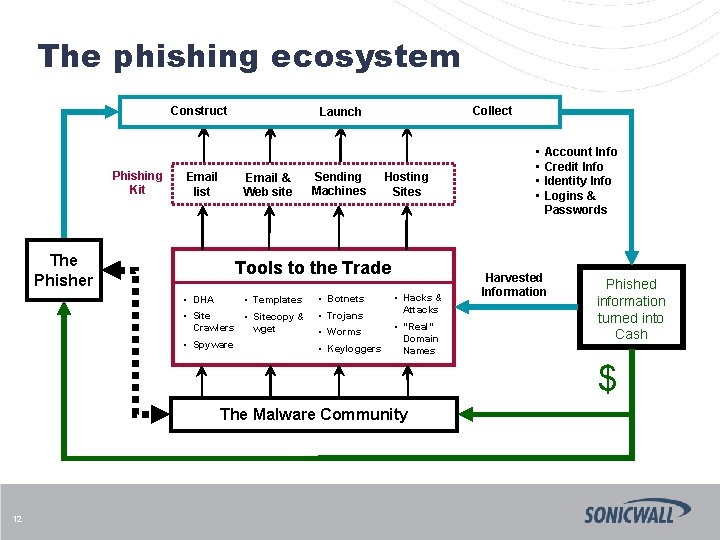
The phishing ecosystem Construct Phishing Kit The Phisher Email list Email & Web site $ Collect Launch Sending Machines Hosting Sites Tools to the Trade • Templates • Botnets • Sitecopy & Crawlers wget • Trojans • Spyware • Keyloggers • DHA • Worms • Hacks & Attacks • “Real” Domain Names • • Account Info Credit Info Identity Info Logins & Passwords Harvested Information Phished information turned into Cash $ The Malware Community 7

The money laundering “Mule” § “Make Money at Home” § Recruits receive funds in their accounts § Transfer funds from their account via Western Union wire transfers to a 2 nd (phishers) account § Paid 10% of the sum of each money transfer § One or two transfers each week - $3, 000 to $5, 000 each § “Nations Welfare Foundation” § § 8 Looking for a “Financial Operations Manager” Transfer money for young cancer patients in USSR Real looking web site complete with pictures Paid 7% - can make $500 to $2, 000 per week

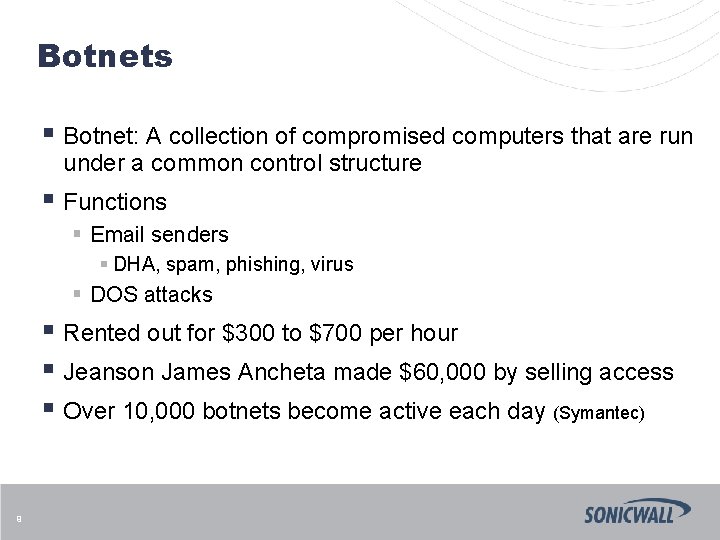
Botnets § Botnet: A collection of compromised computers that are run under a common control structure § Functions § Email senders § DHA, spam, phishing, virus § DOS attacks § Rented out for $300 to $700 per hour § Jeanson James Ancheta made $60, 000 by selling access § Over 10, 000 botnets become active each day (Symantec) 9

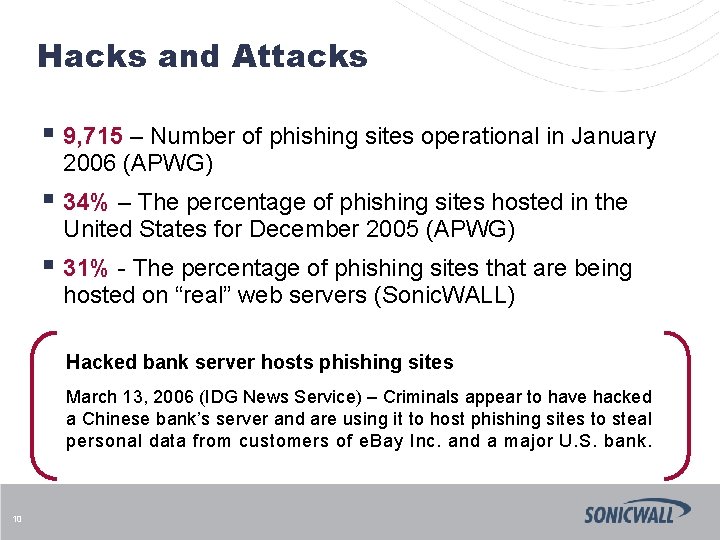
Hacks and Attacks § 9, 715 – Number of phishing sites operational in January 2006 (APWG) § 34% – The percentage of phishing sites hosted in the United States for December 2005 (APWG) § 31% - The percentage of phishing sites that are being hosted on “real” web servers (Sonic. WALL) Hacked bank server hosts phishing sites March 13, 2006 (IDG News Service) – Criminals appear to have hacked a Chinese bank’s server and are using it to host phishing sites to steal personal data from customers of e. Bay Inc. and a major U. S. bank. 10

Scaling a phishing gang § The Campina Grande - Brazil § 65 members § Operated for at least 3 months § 200 accounts in six banks § $4. 7 million stolen from bank accounts Feb 2006 – 41 members caught, 24 more still on the run 11

The phishing ecosystem Construct Phishing Kit Email list Email & Web site The Phisher Collect Launch Sending Machines Hosting Sites Tools to the Trade • Templates • Botnets • Sitecopy & Crawlers wget • Trojans • Spyware • Keyloggers • DHA • Worms • Hacks & Attacks • “Real” Domain Names • • Account Info Credit Info Identity Info Logins & Passwords Harvested Information Phished information turned into Cash $ The Malware Community 12

Roles of the Education in Phishing 13 § Victim § Receive and respond to phishing attack § Bad for victim / Bad for you § Labor § Mules § Coders § Phisher § Organized cooperative environment § Participant § Hosting phishing sites § Sending email – Botnets

GMU Slides

Email and Academia: The Challenge § Email supports communications, academic projects and business administration, but also makes you vulnerable § Diverse user needs § Limited resources and need to reduce operating costs 15

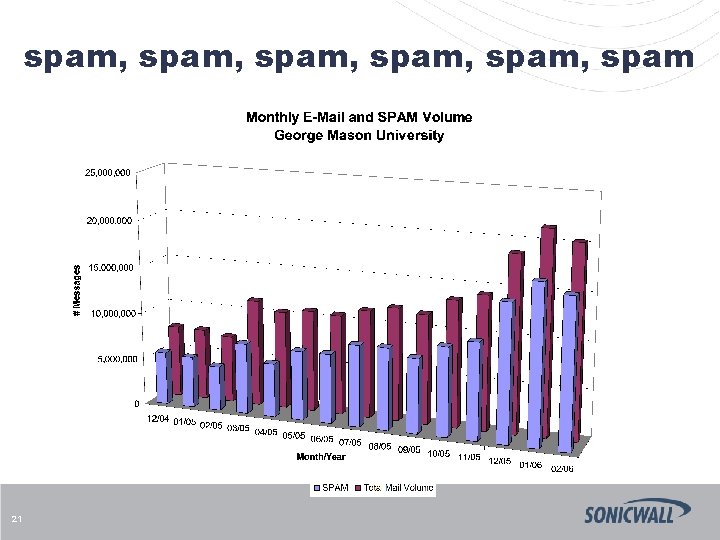
Email At George Mason University § 30, 000 active email accounts § 400, 000 inbound messages/day (82% junk) § Decentralized, ineffective protection for spam § No protection from phishing § Six AV appliances § Costly maintenance 16

Determine The Requirements § User Town Hall Meetings § Quarantine is required § Ability to opt-out § Systems Management § No new staff – minimize daily tasks § Solaris-based § Management reporting 17

Evaluation Requirements § Effective - we receive only the emails we want to receive § Easy to manage – something that doesn’t require additional IT time (actually, less time than what we’re spending is better) § Easy for end users – little to no training required, also something they can self-manage 18

The Process… § Product analysis, review requirements § Vendor questionnaire § Review responses § Invitation to technology day § § § 19 Each vendor given 50 minutes Present same info in specified order Must include pricing and references Q&A Vendors cannot see other vendor presentations

Evaluation § All vendors that satisfied all requirements invited § Solutions placed in production mail flow for 15 days 20

spam, spam, spam 21

Wrap-up

Wrap-up § Overview of the Phishing Ecosystem § Phish School § § § 23 Scope of the problem What did GMU do Results Phishing education Other email issues

Thank you Andrew Klein aklein@sonicwall. com www. sonicwall. com

The Four Parts of the Solution

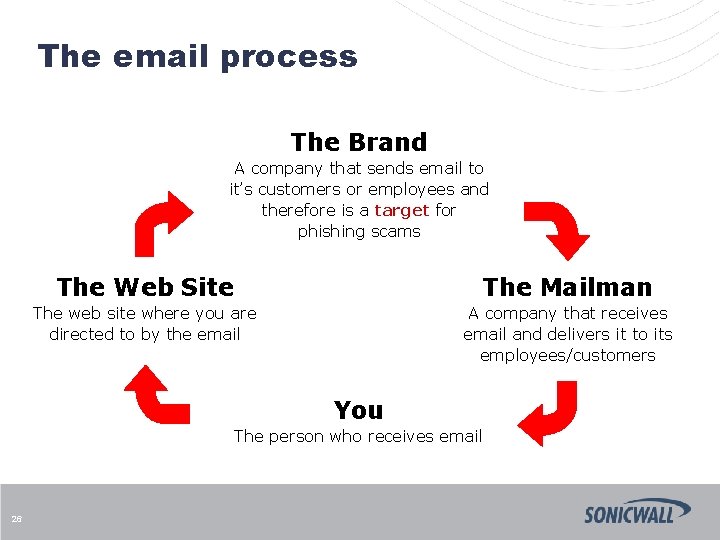
The email process The Brand A company that sends email to it’s customers or employees and therefore is a target for phishing scams The Web Site The Mailman The web site where you are directed to by the email A company that receives email and delivers it to its employees/customers You The person who receives email 26

The brand § § Cut-and-Paste links, minimize links Use personal information where possible § Dear John J. Smith § Account ending in 1234 § Your zip code is 94304 § § Provide non-email ways to verify Use standard company domain names Identify your partners Set and follow standard communication practices § Internally and externally 27

The mailman § Preemptive § Protect your email address § Phishing is more than spam – think Virus § Technology § Multi-faceted solution – No silver bullet § Sender authentication and reputation, content, contact point divergence, URL exploits, real-time phish lists, etc. § World-wide community collaboration § Change is part of the business § Psychology § Educate your customers/employees – their Phishing. IQ § Email is still Good! Really it is! 28

The web site § Company and personal sites § § § Monitor your site Know your content Practice good passwords Keep logs, report phishing to authorities Hosting services § Monitor new customers § Take phishing seriously § Unless they are e. Bay, assume they are not e. Bay! § Domain name registration services § Be diligent about domain registrations § Actively work to shut down phishing sites 29

You § Know your senders § Is this someone I do business with? § Is this something I was told I’d receive? § Look for other ways to respond § Be aware § § § 30 Look for clues – improve your Phishing. IQ Don’t be afraid to ask Protect your system Know how your system is updated Check your records
 Health informatics george mason
Health informatics george mason George mason university off campus housing
George mason university off campus housing Gmu registration dates
Gmu registration dates George mason university english language institute
George mason university english language institute George mason university orientation
George mason university orientation Shirley ardell mason walter mason
Shirley ardell mason walter mason Mason high motivation
Mason high motivation Was george mason an anti federalist
Was george mason an anti federalist George mason anti federalist
George mason anti federalist Gmu health informatics
Gmu health informatics Knowyourmeme
Knowyourmeme Phishing
Phishing Howsecureismypassword phishing
Howsecureismypassword phishing Phishing austin texas
Phishing austin texas Mobifish
Mobifish Phishing
Phishing Phishing cia triad
Phishing cia triad Types of phishing attacks
Types of phishing attacks Csirt playbook
Csirt playbook Halloween phishing
Halloween phishing Anti phishing phil
Anti phishing phil Spear phishing attack kali linux
Spear phishing attack kali linux Email phishing
Email phishing Phishing
Phishing Phishing is a form of
Phishing is a form of Ics phishing sms
Ics phishing sms George washington vs king george iii
George washington vs king george iii George washington and thomas jefferson venn diagram
George washington and thomas jefferson venn diagram Sound wall instead of word wall
Sound wall instead of word wall Chris brown wall to wall
Chris brown wall to wall T junction brick wall
T junction brick wall