Forefront Codenname Stirling Ved Christian Stahl Microsoft Enterprise




- Slides: 31

Forefront Codenname ”Stirling” Ved Christian Stahl, Microsoft Enterprise Services

Agenda • Introduktion til Security Management • Introduktion til Fore. Front Codename ”Stirling” • Stirling funktionalitet • Stirling arkitektur

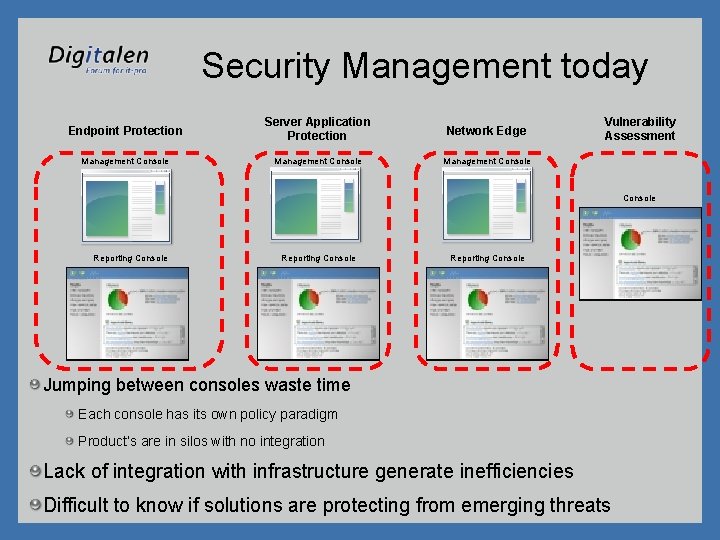
Security Management today Endpoint Protection Server Application Protection Network Edge Management Console Vulnerability Assessment Console Reporting Console Jumping between consoles waste time Each console has its own policy paradigm Product’s are in silos with no integration Lack of integration with infrastructure generate inefficiencies Difficult to know if solutions are protecting from emerging threats

Simplified Management with Stirling • One console for simplified, role-based security management • Define one security policy for your assets across protection technologies • Deploy signatures, policies and software quickly • Integrates with your existing infrastructure: SCOM, SQL, WSUS, AD, NAP, SCCM

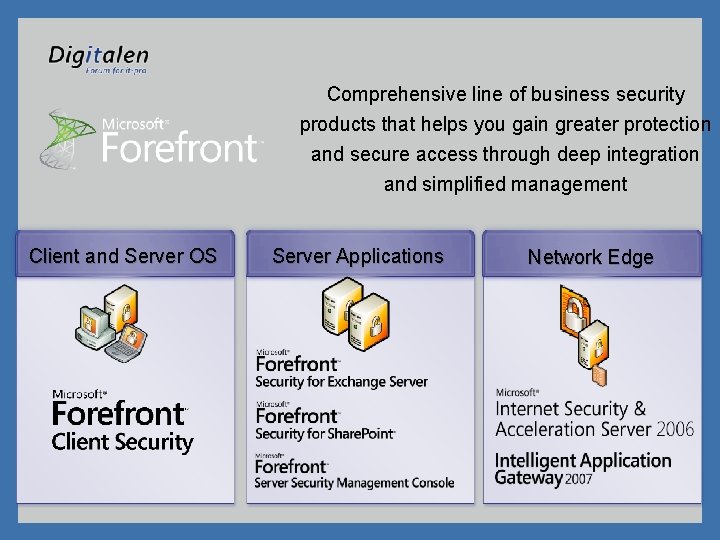
Comprehensive line of business security products that helps you gain greater protection and secure access through deep integration and simplified management Client and Server OS Server Applications Network Edge

Poll Hvor mange anvender: • Fore. Front Client? • ISA Server? • Fore. Front for Exchange eller MOSS?

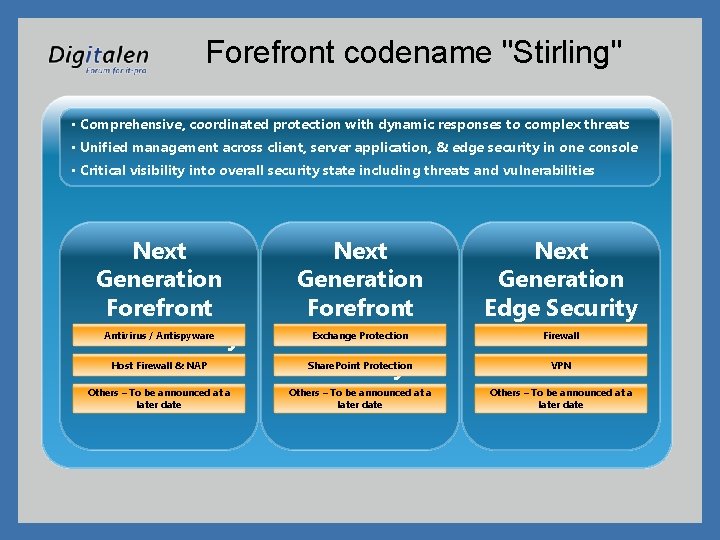
Forefront codename "Stirling" • Comprehensive, coordinated protection with dynamic responses to complex threats • Unified management across client, server application, & edge security in one console • Critical visibility into overall security state including threats and vulnerabilities Next Generation Forefront Antivirus / Antispyware Client Security Host Firewall & NAP Others – To be announced at a later date Next Generation Forefront Exchange Protection Server Share. Point Protection Security Next Generation Edge Security and Firewall Access Others – To be announced at a later date VPN

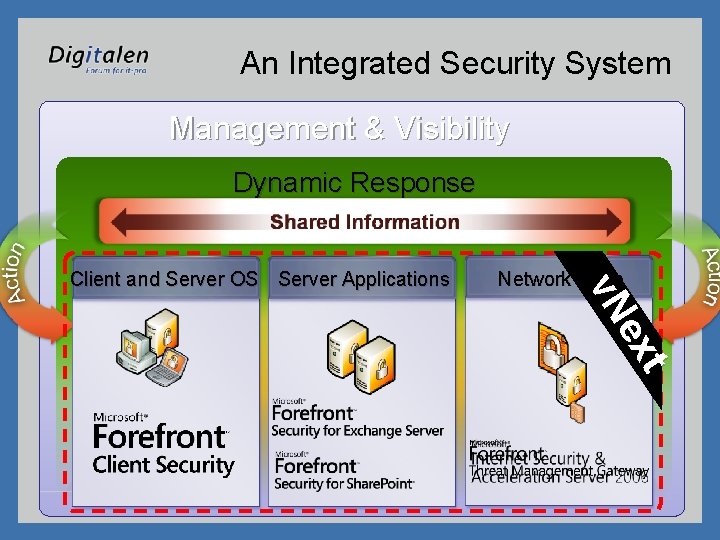
An Integrated Security System Management & Visibility Dynamic Response Network Edge t ex v. N Client and Server OS Server Applications

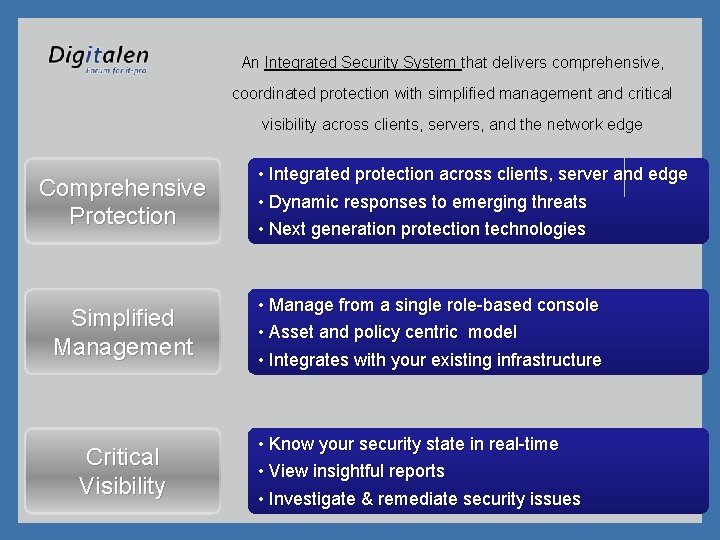
An Integrated Security System that delivers comprehensive, coordinated protection with simplified management and critical visibility across clients, servers, and the network edge Comprehensive Protection Simplified Management Critical Visibility • Integrated protection across clients, server and edge • Dynamic responses to emerging threats • Next generation protection technologies • Manage from a single role-based console • Asset and policy centric model • Integrates with your existing infrastructure • Know your security state in real-time • View insightful reports • Investigate & remediate security issues

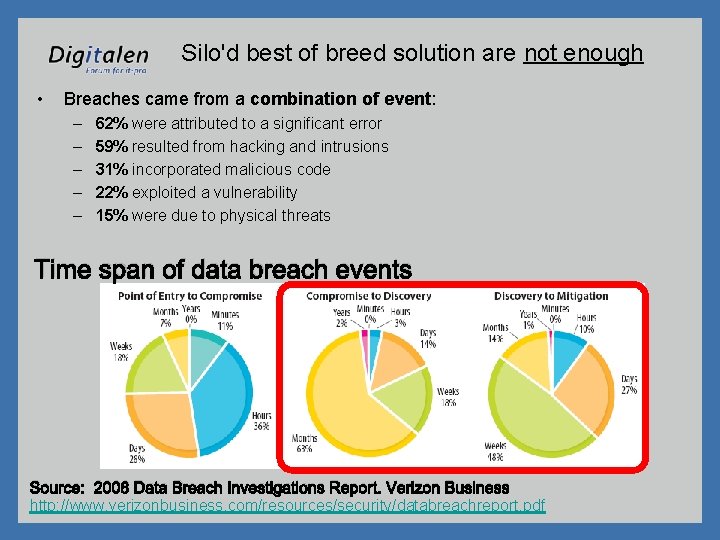
Silo'd best of breed solution are not enough • Breaches came from a combination of event: – – – 62% were attributed to a significant error 59% resulted from hacking and intrusions 31% incorporated malicious code 22% exploited a vulnerability 15% were due to physical threats Time span of data breach events Source: 2008 Data Breach Investigations Report. Verizon Business http: //www. verizonbusiness. com/resources/security/databreachreport. pdf

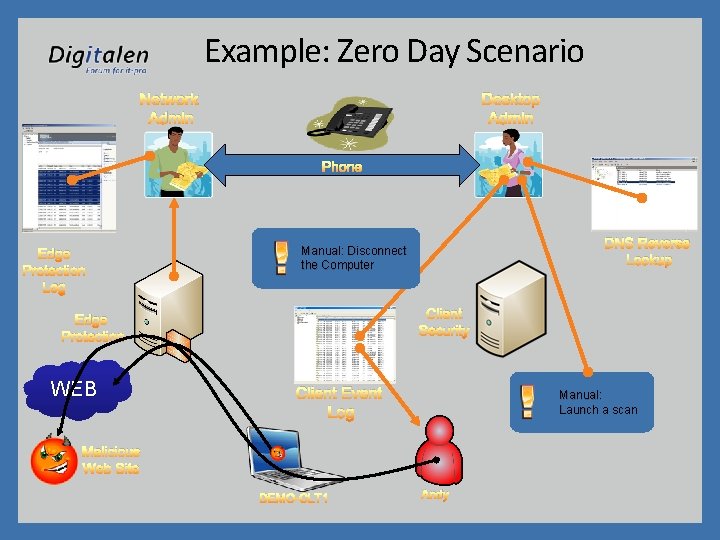
Example: Zero Day Scenario Network Admin Desktop Admin Phone Edge Protection Log Client Security Edge Protection WEB DNS Reverse Lookup Manual: Disconnect the Computer Client Event Log Manual: Launch a scan Malicious Web Site DEMO-CLT 1 Andy

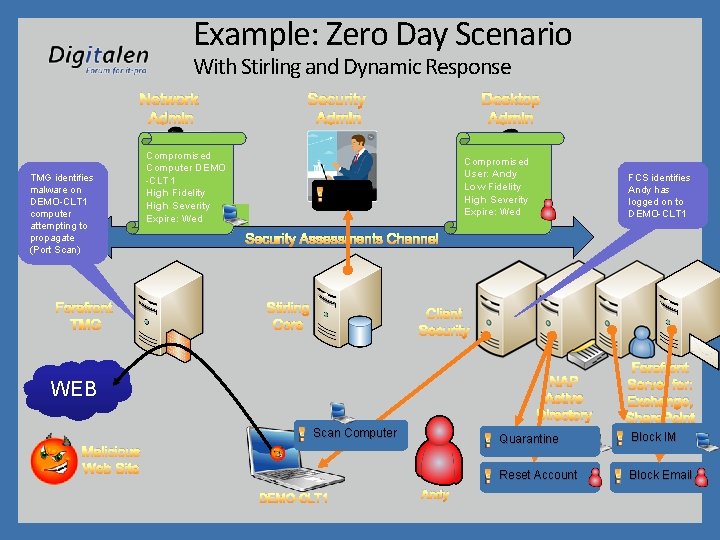
Example: Zero Day Scenario With Stirling and Dynamic Response Network Admin TMG identifies malware on DEMO-CLT 1 computer attempting to propagate (Port Scan) Forefront TMG Security Admin Compromised Computer DEMO -CLT 1 High Fidelity High Severity Expire: Wed Desktop Admin Compromised User: Andy Low Fidelity High Severity Expire: Wed Alert FCS identifies Andy has logged on to DEMO-CLT 1 Security Assessments Channel Stirling Core Client Security Quarantine Forefront Server for: Exchange, Share. Point OCS Block IM Reset Account Block Email NAP Active Directory WEB Scan Computer Malicious Web Site DEMO-CLT 1 Andy

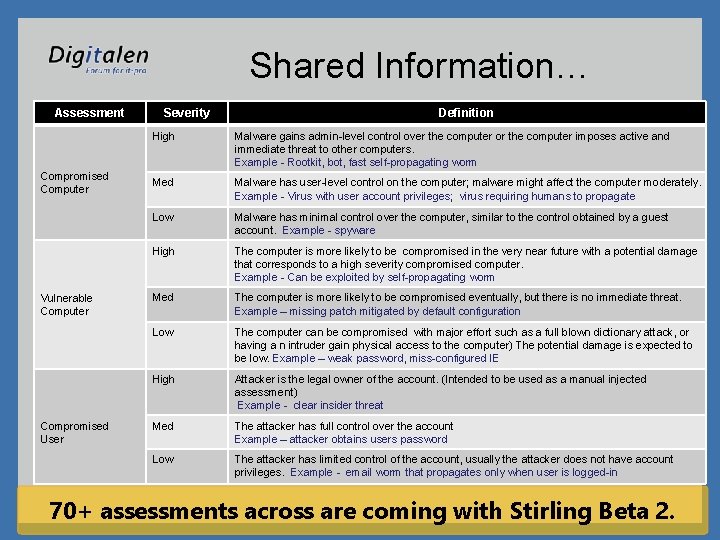
Shared Information… Assessment Compromised Computer Vulnerable Computer Compromised User Severity Definition High Malware gains admin-level control over the computer or the computer imposes active and immediate threat to other computers. Example - Rootkit, bot, fast self-propagating worm Med Malware has user-level control on the computer; malware might affect the computer moderately. Example - Virus with user account privileges; virus requiring humans to propagate Low Malware has minimal control over the computer, similar to the control obtained by a guest account. Example - spyware High The computer is more likely to be compromised in the very near future with a potential damage that corresponds to a high severity compromised computer. Example - Can be exploited by self-propagating worm Med The computer is more likely to be compromised eventually, but there is no immediate threat. Example – missing patch mitigated by default configuration Low The computer can be compromised with major effort such as a full blown dictionary attack, or having a n intruder gain physical access to the computer) The potential damage is expected to be low. Example – weak password, miss-configured IE High Attacker is the legal owner of the account. (Intended to be used as a manual injected assessment) Example - clear insider threat Med The attacker has full control over the account Example – attacker obtains users password Low The attacker has limited control of the account, usually the attacker does not have account privileges. Example - email worm that propagates only when user is logged-in 70+ assessments across are coming with Stirling Beta 2.

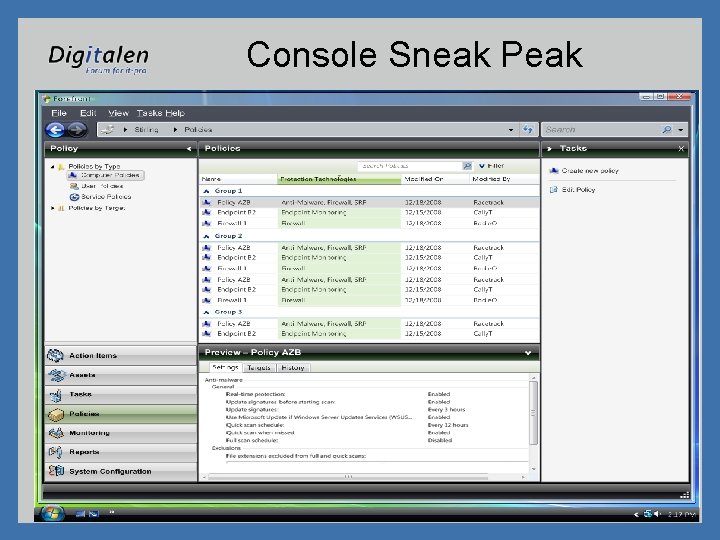
Console Sneak Peak

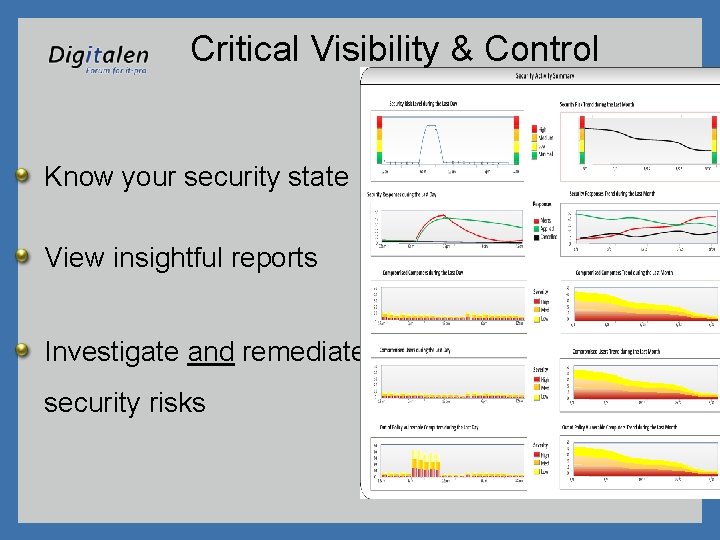
Critical Visibility & Control Know your security state View insightful reports Investigate and remediate security risks

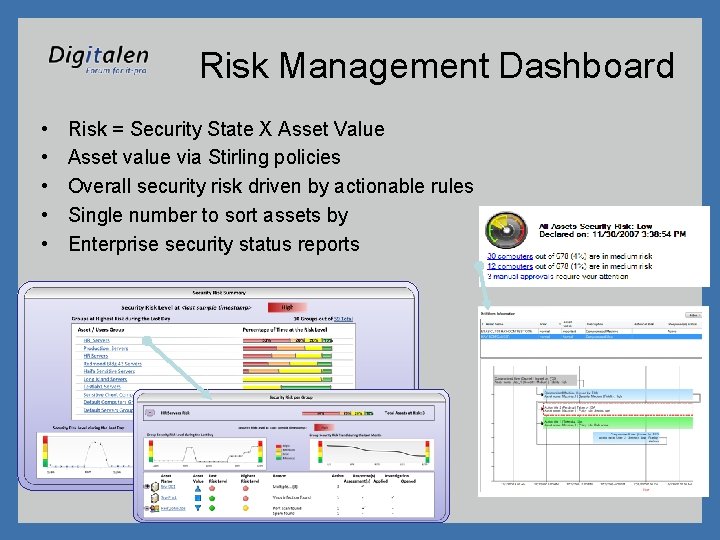
Risk Management Dashboard • • • Risk = Security State X Asset Value Asset value via Stirling policies Overall security risk driven by actionable rules Single number to sort assets by Enterprise security status reports

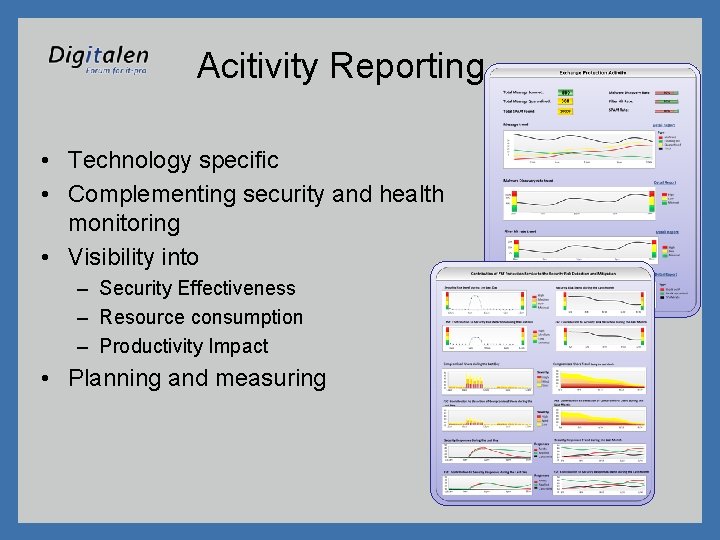
Acitivity Reporting • Technology specific • Complementing security and health monitoring • Visibility into – Security Effectiveness – Resource consumption – Productivity Impact • Planning and measuring

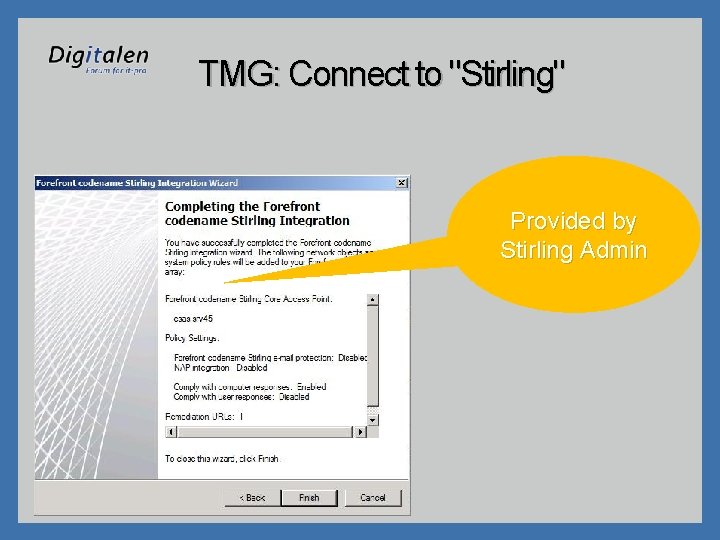
TMG: Connect to "Stirling" Provided by Stirling Admin

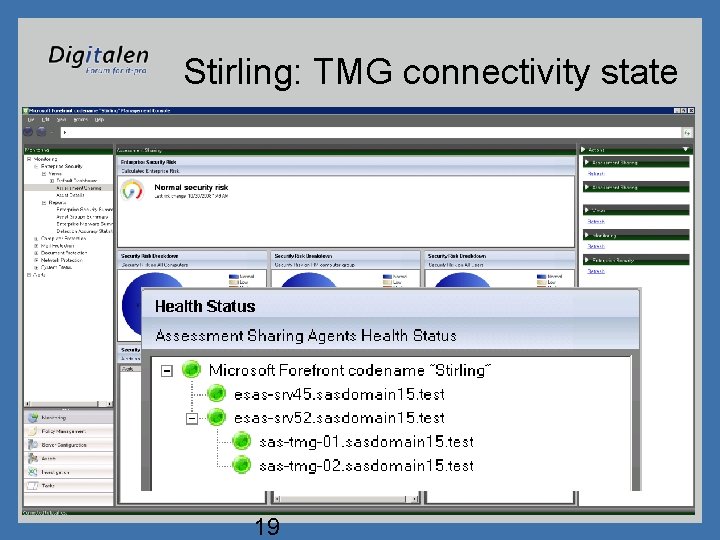
Stirling: TMG connectivity state 19

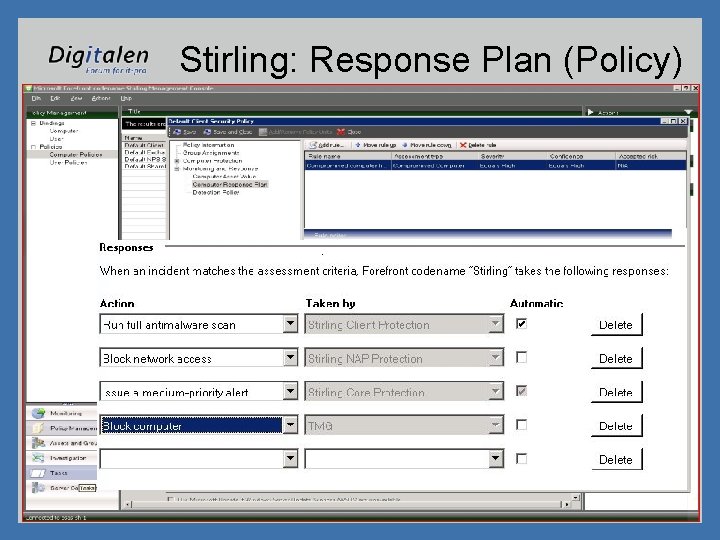
Stirling: Response Plan (Policy)

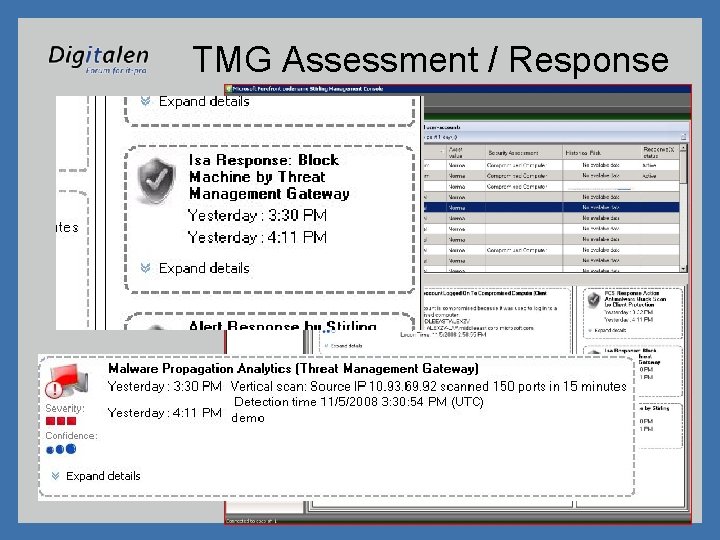
TMG Assessment / Response

TMG: Response Implementation

Poll Hvor mange anvender: • SCOM? • WSUS?

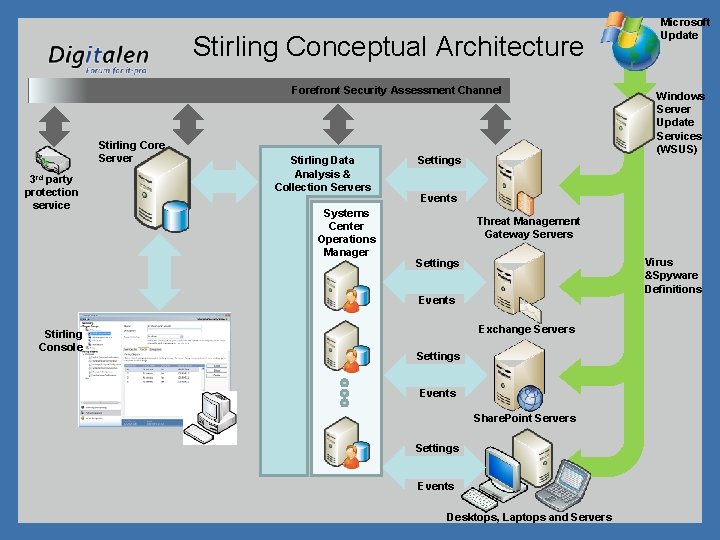
Stirling Conceptual Architecture Forefront Security Assessment Channel Stirling Core Server 3 rd party protection service Stirling Data Analysis & Collection Servers Systems Center Operations Manager Settings Windows Server Update Services (WSUS) Events Threat Management Gateway Servers Virus &Spyware Definitions Settings Events Stirling Console Microsoft Update Exchange Servers Settings Events Share. Point Servers Settings Events Desktops, Laptops and Servers

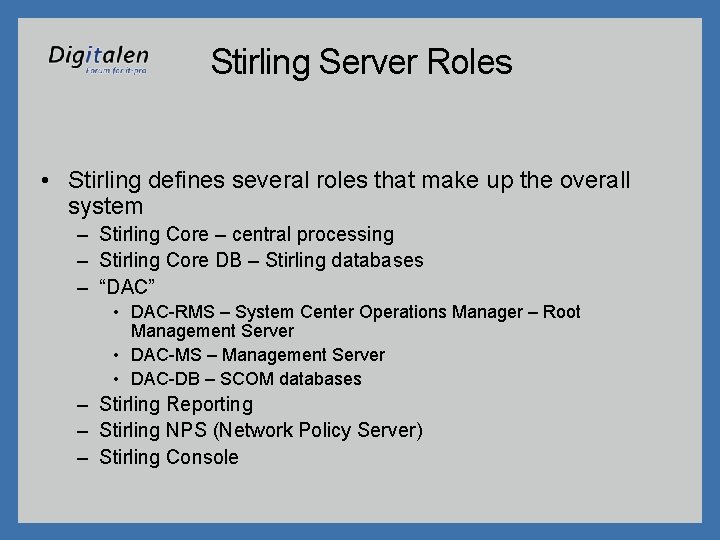
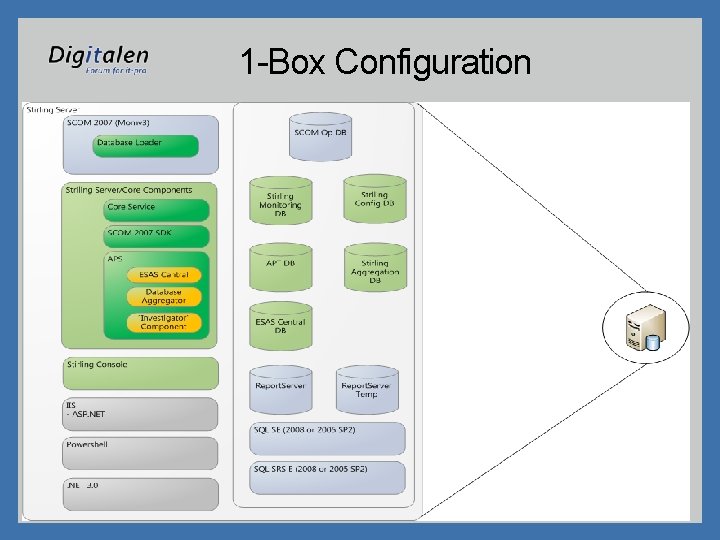
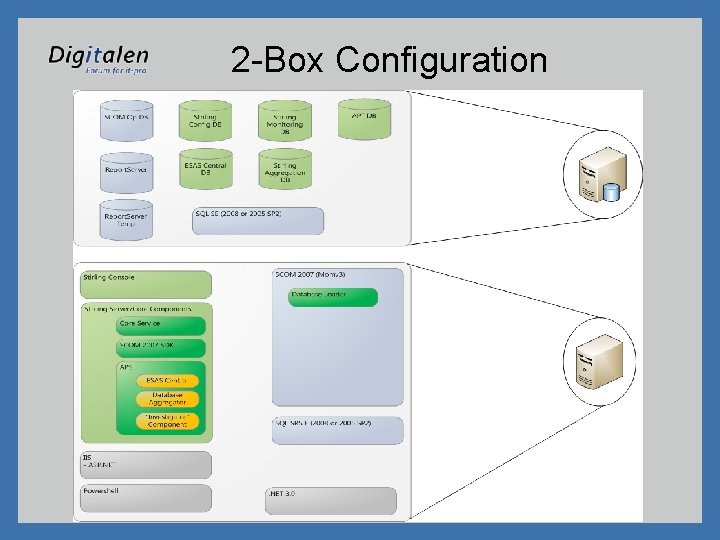
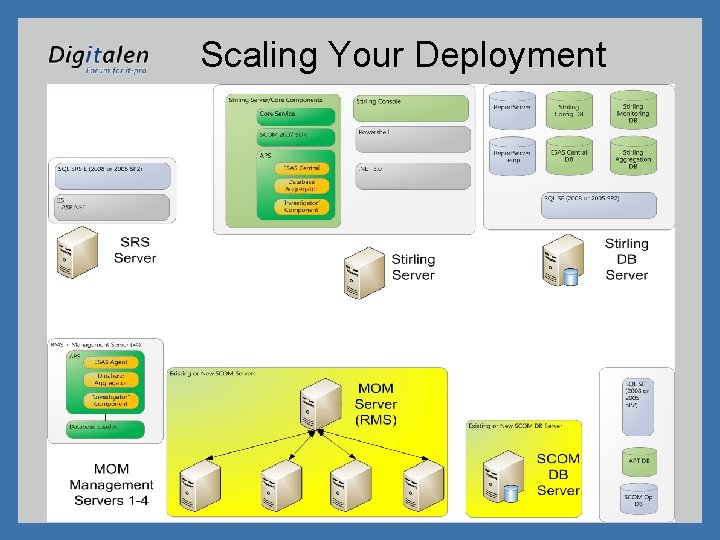
Stirling Server Roles • Stirling defines several roles that make up the overall system – Stirling Core – central processing – Stirling Core DB – Stirling databases – “DAC” • DAC-RMS – System Center Operations Manager – Root Management Server • DAC-MS – Management Server • DAC-DB – SCOM databases – Stirling Reporting – Stirling NPS (Network Policy Server) – Stirling Console


1 -Box Configuration

2 -Box Configuration

Scaling Your Deployment

Stirling Common Questions • Q: Can I use my existing SCOM infrastructure for Stirling? • A: Yes, but unless it’s already managing all your desktops too, you’ll have to add more servers to scale it out • Q: Can I use. . – Clusters? – Virtualization? • A: Yes

Stirling Common Questions • Q: How many clients can each SCOM server support? • A: Performance testing is well underway , but I’ll cover some of our scale goals coming up
 Microsoft forefront security for exchange server
Microsoft forefront security for exchange server Sperried
Sperried Microsoft forefront protection 2010 for exchange server
Microsoft forefront protection 2010 for exchange server Ms forefront client security
Ms forefront client security Forefront screeners
Forefront screeners Microsoft identity manager end of life
Microsoft identity manager end of life Francesco giorgini
Francesco giorgini Gfi max mail protection
Gfi max mail protection Forefront security solutions
Forefront security solutions Meselson and stahl experiment quizlet
Meselson and stahl experiment quizlet Meselson–stahl experiment
Meselson–stahl experiment Jean-paul stahl
Jean-paul stahl Meiosis fases
Meiosis fases Stahl index
Stahl index Meselson and stahl's experiment
Meselson and stahl's experiment Achim stahl
Achim stahl En que fase se da el crecimiento de la celula
En que fase se da el crecimiento de la celula First generation antipsychotics
First generation antipsychotics Facs
Facs Croset cervico alveolar deschis dental
Croset cervico alveolar deschis dental Herdfrischverfahren
Herdfrischverfahren Solarhaus
Solarhaus Brinkibon v stahag stahl
Brinkibon v stahag stahl Stahl
Stahl Benedicta stahl sodré
Benedicta stahl sodré Stahl electronics
Stahl electronics Bimetallthermometer aufbau
Bimetallthermometer aufbau Jorge stahl jr
Jorge stahl jr Scott stahl make a wish
Scott stahl make a wish Gerry stahl
Gerry stahl Stirling lloyd waterproofing
Stirling lloyd waterproofing James stirling cambridge
James stirling cambridge