Financial Fraud and the Internet Det Missy Coyne


























- Slides: 30

Financial Fraud and the Internet Det. Missy Coyne Baltimore County Police Department

Goals • To define Social Networking and it’s dangers • To be able to identify fraud related crimes and scams that occur on the Internet • To discuss Identity Theft and credit card fraud • To understand the difference between a “breach” and a “skim” • To discuss safe practices while using the Internet

Definition Cybercrime is criminal activity done using computers and the Internet. This includes anything from downloading illegal music files to stealing millions of dollars from online bank accounts. Cybercrime also includes nonmonetary offenses, such as creating and distributing viruses on other computers or posting confidential business information on the Internet. Definition obtained from www. techterms. com

How do people access the Internet? • • Internet Service Provider (ISP) Cell phone Tablets Gaming System – Playstation 3 – Xbox 360 – Wii

What do we get from the Internet? • • • Social networking sites Email On line chatting On line gaming Access to Financial Institutions Access to Retail websites

What is a “social network site”? • Social Network Sites are defined as “web-based services that allow individuals to (1) construct a public or semiprivate profile within a bounded system, (2) articulate a list of other users with whom they share a connection, and (3) view and traverse their list of connections and those made by others within the system. The nature and nomenclature of these connections may vary from site to site”. 2007 Journal of Computer-Mediated Communication, 13(1), article 11.

• • Examples of Social Networking Sites (SNS) Myspace. com Facebook Match. com Plenty of Fish – Free Site • Christian Mingle

Facebook • Harvard ONLY SNS in early 2004 • Started supporting other colleges but they had to have university email addresses associated to those institutions • 2005, opened up to high school students, professionals inside corporate networks, and eventually, everyone.

Dangers of SNS’s • • • Cyber stalking Cyber bullying/ threats Disclosure of private information ID Theft Take over or create pages

Dating Web Site Dangers • After communicating for a period of time, the individual indicates they have a friend in another country that needs assistance and convinces the subject to send money to the person in the other country. • Similar scenario but ask the individual to send packages to them because they can’t receive the packages where they are.

Cyber Stalking • Cyberstalking is the use of the Internet to “Stalk” someone. • "Stalking is a form of mental assault, in which the perpetrator repeatedly, unwantedly, and disruptively breaks into the life-world of the victim, with whom he has no relationship (or no longer has), with motives that are directly or indirectly traceable to the affective sphere. Moreover, the separated acts that make up the intrusion cannot by themselves cause the mental abuse, but do taken together (cumulative effect). Wikipedia

Cyber bullying • Cyberbullying is being cruel to others by sending or posting harmful material or engaging in other forms of social aggression using the Internet or other digital technologies. – Center for Safe and Responsible Internet Use

Lack of Laws for Adult based crimes

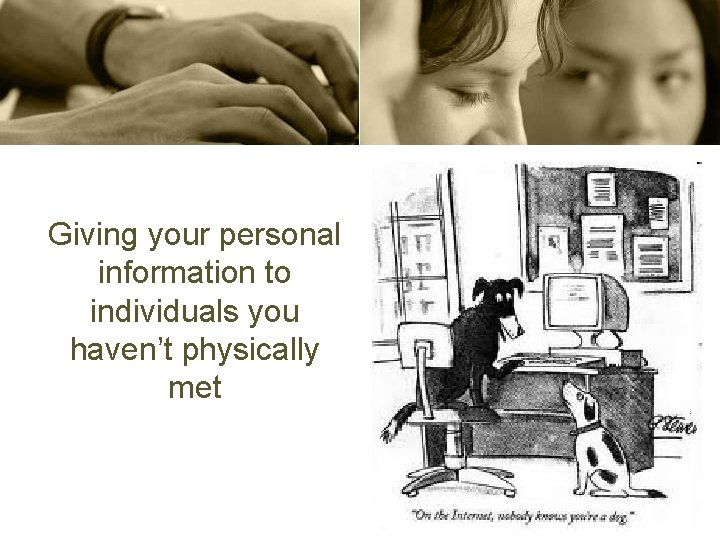
Giving your personal information to individuals you haven’t physically met

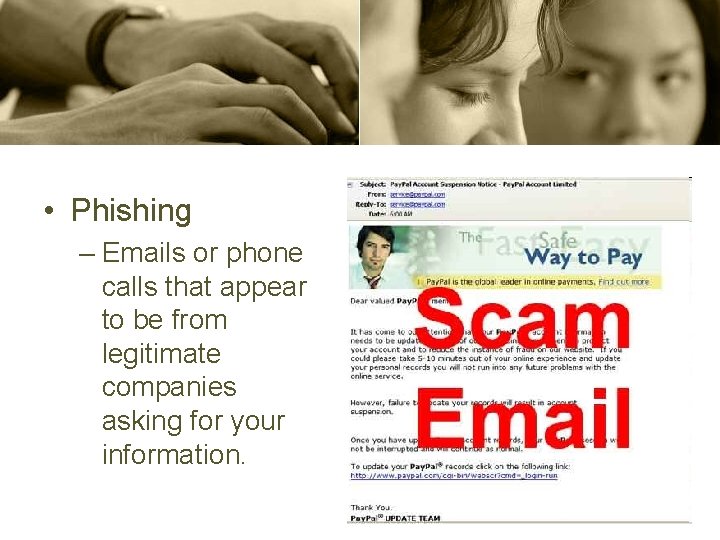
Fraud Related Computer Crimes • Phishing

• Phishing – Emails or phone calls that appear to be from legitimate companies asking for your information.

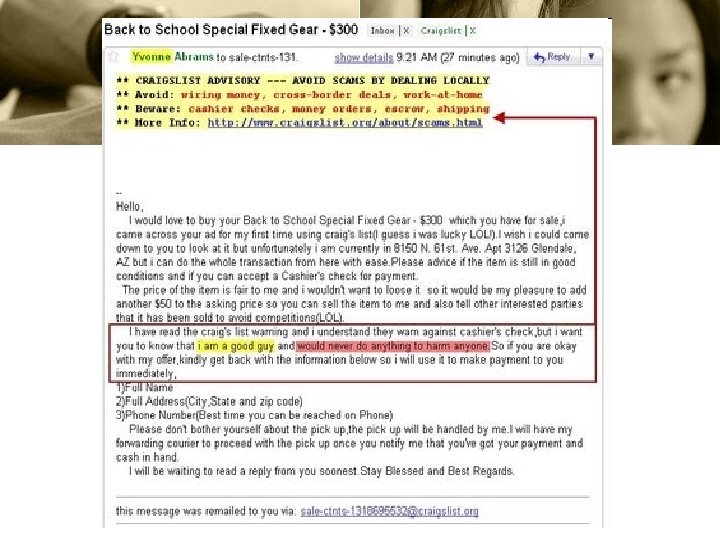
Fraud Related Scams • Jobs – Reshipping • Craigs List – Room mates – Items – Vacation rentals • Other Fraud Scams

RESHIPPING SCAM • Victims are usually contacted by instant message (IM) or online personal ads • Suspects are from African Country (Nigeria or Ghana). They start “chatting” and a personal relationship develops • Eventually they will ask victim to do favors such as accept deliveries and reship them to other countries


FOREIGN LOTTERY SCAMS It’s illegal to play foreign lotteries in the United States A Federal Statute prohibits mailing lottery tickets, advertisements or payments to purchase tickets in a foreign lottery

Publishers Clearing House They do NOT call you on the PHONE

Fraud Related Computer Crimes • Identity Theft and Credit Card Fraud – Take over account fraud • Wire Fraud – Use of Credit card numbers

Identity Theft • Begins when criminals obtain personal identifiers of individuals with good credit by: – Recruiting individuals who have access to other people’s personal information in the course of their employment – Collusive Employees – Stealing documents from businesses that contain personal information - Medical records, loan applications, etc.

Types of Access Device Fraud • Skimming – Theft of account numbers and track data • Counterfeit Credit Cards • Altered Credit Cards (re-embossing) • White Plastic • Lost/Stolen/Non-Received Issued (NRI) • Misuse of Account Numbers

Skimming “The replication of electronically transmitted full track data to allow or enable valid authorization to occur. ”

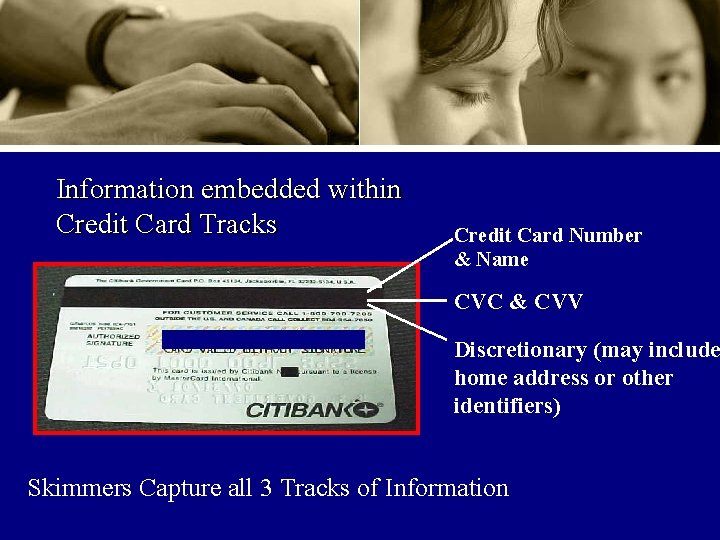
What areembedded they within stealing? Information Credit Card Tracks Credit Card Number & Name CVC & CVV Discretionary (may include home address or other identifiers) Skimmers Capture all 3 Tracks of Information

Breaches Intentional vs. Unintentional Sam’s Club vs Target Breaches vs skimming Location of transactions

Internet Fraud Prevention • Don’t answer or open emails from unknown sources • Don’t provide your personal information to someone you don’t know • If it sounds too good to be true…it is • Look for secure websites…. https: // when conducting on line purchases • Check your financial statements regularly

Internet Fraud Prevention • Use Anti virus and firewall protection to protect your system • Don’t download software from unknown sites • Use secure passwords for websites – Letters and numbers (characters if permitted) – Change often and don’t duplicate

Questions?
 How do fraud symptoms help in detecting fraud
How do fraud symptoms help in detecting fraud Coyne first aid
Coyne first aid Ann coyne suffolk university
Ann coyne suffolk university David coyne ndis
David coyne ndis Media measurement solutions
Media measurement solutions Det beskrivende kulturbegreb
Det beskrivende kulturbegreb Vem leder bönen i mosken
Vem leder bönen i mosken What is the theme of the story katie clean and messy missy
What is the theme of the story katie clean and messy missy Missy diwater the former platform
Missy diwater the former platform Missy diwater the former platform diver
Missy diwater the former platform diver Dna replication vs pcr
Dna replication vs pcr Centripetal force period
Centripetal force period Missy ward
Missy ward Symboliska perspektivet
Symboliska perspektivet Missy petty
Missy petty Missy ward
Missy ward E commerce security and fraud issues and protections
E commerce security and fraud issues and protections Financial methods of motivation definition
Financial methods of motivation definition Internet or internet
Internet or internet Verifyny
Verifyny Fraud and abuse module
Fraud and abuse module E commerce security and fraud protection
E commerce security and fraud protection E-commerce security and fraud protection
E-commerce security and fraud protection Computer fraud and abuse techniques
Computer fraud and abuse techniques Sas 78/coso
Sas 78/coso Anti bribery and corruption analytics
Anti bribery and corruption analytics Principles of cash management
Principles of cash management Ethics and internal controls in accounting
Ethics and internal controls in accounting Fraud waste and abuse training answers
Fraud waste and abuse training answers Fraud waste and abuse training answers
Fraud waste and abuse training answers Computer fraud and security
Computer fraud and security