EEC 693793 Special Topics in Electrical Engineering Secure





























- Slides: 38

EEC 693/793 Special Topics in Electrical Engineering Secure and Dependable Computing Lecture 3 Wenbing Zhao Department of Electrical and Computer Engineering Cleveland State University wenbing@ieee. org Spring 2007 EEC 693: Secure & Dependable Computing

2 Outline • • Types of threats Meaning of computer security Vulnerabilities in computer systems Threats in computer networks Spring 2007 EEC 693: Secure & Dependable Computing 2

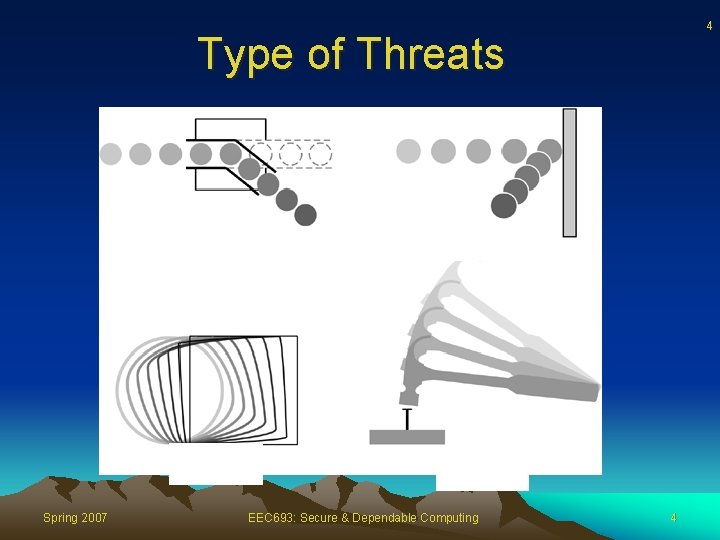
3 Type of Threats • An interception means that some unauthorized party has gained access to an asset • In an interruption, an asset of the system becomes lost, unavailable, or unusable • If an unauthorized party not only accesses but tampers with an asset, the threat is a modification • An unauthorized party might create a fabrication of counterfeit objects on a computing system Spring 2007 EEC 693: Secure & Dependable Computing 3

4 Type of Threats Spring 2007 EEC 693: Secure & Dependable Computing 4

5 Interception • An interception means that some unauthorized party has gained access to an asset – Example: illicit copying of program or data files, or wiretapping to obtain data in a network – Unlike a loss, which may be discovered fairly quickly, a silent interceptor may leave no traces by which the interception can be readily detected Spring 2007 EEC 693: Secure & Dependable Computing 5

6 Interruption • In an interruption, an asset of the system becomes lost, unavailable, or unusable – Example: malicious destruction of a hardware device – Example: erasure of a program or data file – Example: (distributed) denial of service attacks Spring 2007 EEC 693: Secure & Dependable Computing 6

7 Modification • If an unauthorized party not only accesses but tampers with an asset, the threat is a modification – Example: someone might change the values in a database, alter a program so that it performs an additional computation – Example: modify message being transmitted over the network – Some cases of modification can be detected with simple measures, but other, more subtle, changes may be almost impossible to detect Spring 2007 EEC 693: Secure & Dependable Computing 7

8 Fabrication • An unauthorized party might create a fabrication of counterfeit objects on a computing system – Example: the intruder may insert spurious transactions to a network communication system or add records to an existing database – Sometimes these additions can be detected as forgeries, but if skillfully done, they are virtually indistinguishable from the real thing Spring 2007 EEC 693: Secure & Dependable Computing 8

9 Threats: Methods, Opportunity, and Motive • A malicious attacker must have three things: – Method: the skills, knowledge, tools, and other things with which to launch an attack – Opportunity: the time and access to accomplish the attack – Motive: a reason to want to perform this attack against this system Spring 2007 EEC 693: Secure & Dependable Computing 9

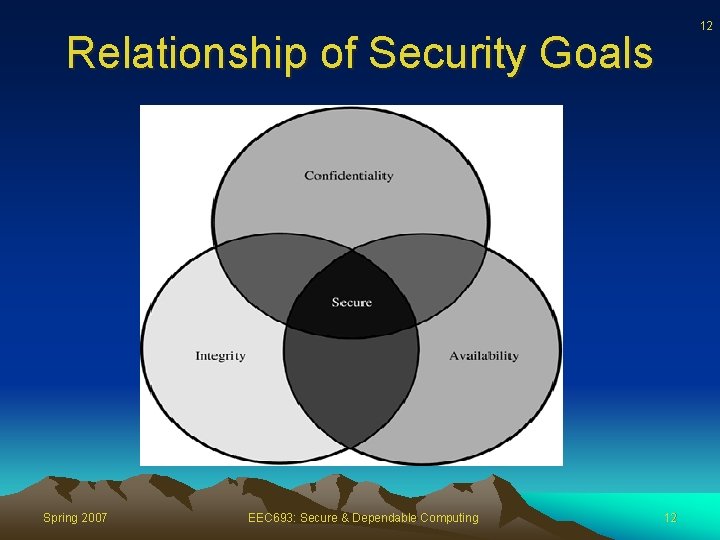
The Meaning of Computer Security • The purpose of computer security is to devise ways to prevent the weaknesses from being exploited • What we mean when we say that a system is secure: – Confidentiality: computer-related assets are accessed only by authorized parties. Confidentiality is sometimes called secrecy or privacy – Integrity: assets can be modified only by authorized parties or only in authorized ways – Availability: assets are accessible to authorized parties at appropriate times Spring 2007 EEC 693: Secure & Dependable Computing 10 10

11 Relationship of Security Goals • A secure system must meet all three requirements • The challenge is how to find the right balance among the goals, which often conflict – For example, it is easy to preserve a particular object's confidentiality in a secure system simply by preventing everyone from reading that object – However, this system is not secure, because it does not meet the requirement of availability for proper access – => There must be a balance between confidentiality and availability Spring 2007 EEC 693: Secure & Dependable Computing 11

12 Relationship of Security Goals Spring 2007 EEC 693: Secure & Dependable Computing 12

13 Confidentiality • It is not trivial to ensure confidentiality. For example, – Who determines which people or systems are authorized to access the current system? – By "accessing" data, do we mean that an authorized party can access a single bit? pieces of data out of context? – Can someone who is authorized disclose those data to other parties? • Confidentiality is the security property we understand best because its meaning is narrower than the other two • We also understand confidentiality well because we can relate computing examples to those of preserving confidentiality in the real world Spring 2007 EEC 693: Secure & Dependable Computing 13

14 Integrity • It is much harder to ensure integrity. One reason is that integrity means different things in different context • For example, if we say that we have preserved the integrity of an item, we may mean that the item is: – – – – – precise accurate unmodified only in acceptable ways modified only by authorized people modified only by authorized processes consistent internally consistent meaningful and usable Spring 2007 EEC 693: Secure & Dependable Computing 14

15 Integrity • Aspects of integrity: computerized data are the same as those in source documents; they have not been exposed to accidental or malicious alteration or destruction • Aspects of integrity: authorized actions, separation and protection of resources, and error detection and correction • Integrity can be enforced in much the same way as can confidentiality: by rigorous control of who or what can access which resources in what ways Spring 2007 EEC 693: Secure & Dependable Computing 15

16 Availability • Availability applies both to data and to services (i. e. , to information and to information processing), and it is similarly complex • We say a data item, service, or system is available if – There is a timely response to our request – There is a fair allocation of resources, so that some requesters are not favored over others – The service or system involved are fault tolerant - hardware or software faults lead to graceful cessation of service or to workarounds rather than to crashes and abrupt loss of information – The service or system can be used easily and in the way it was intended to be used – …. Spring 2007 EEC 693: Secure & Dependable Computing 16

17 Availability • The security community is just beginning to understand what availability implies and how to ensure it • A small, centralized control of access is fundamental to preserving confidentiality and integrity, but it is not clear that a single access control point can enforce availability • Much of computer security's past success has focused on confidentiality and integrity; full implementation of availability is security's next great challenge Spring 2007 EEC 693: Secure & Dependable Computing 17

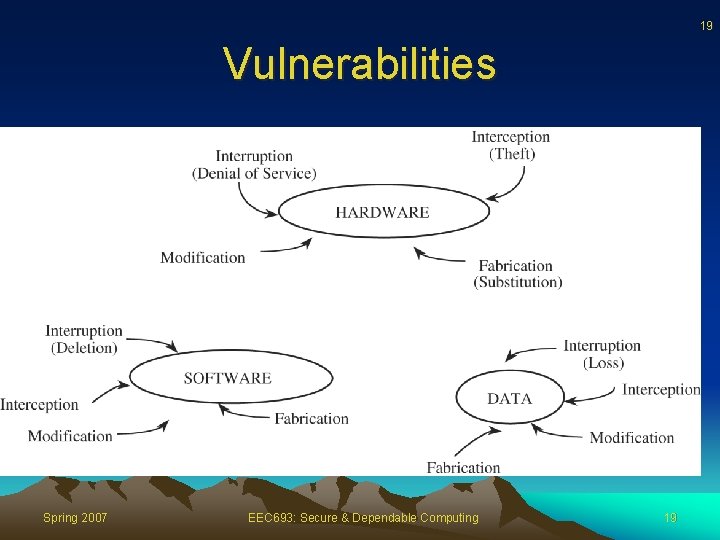
18 Vulnerabilities • When we prepare to specify, design, code, or test a secure system, we try to imagine the vulnerabilities that would prevent us from reaching one or more of our three security goals • The three assets (hardware, software and data) and the connections among them are all potential security weak points Spring 2007 EEC 693: Secure & Dependable Computing 18

19 Vulnerabilities Spring 2007 EEC 693: Secure & Dependable Computing 19

20 Software Vulnerabilities • Software is surprisingly easy to delete and to copy • Software is vulnerable to modifications that either cause it to fail or cause it to perform an unintended task Spring 2007 EEC 693: Secure & Dependable Computing 20

21 Software Vulnerabilities • Logic bomb: a program that has been maliciously modified to fail when certain conditions are met or when a certain date or time is reached • Trojan horse: a program that overtly does one thing while covertly doing another • Virus: a specific type of Trojan horse that can be used to spread its "infection" from one computer to another • Trapdoor: a program that has a secret entry point • Information leaks in a program: code that makes information accessible to unauthorized people or programs Spring 2007 EEC 693: Secure & Dependable Computing 21

22 Data Vulnerabilities • Data items have greater public value than hardware and software, because more people know how to use or interpret data • By themselves, out of context, pieces of data have essentially no intrinsic value • On the other hand, data items in context do relate to cost, perhaps measurable by the cost to reconstruct or redevelop damaged or lost data Spring 2007 EEC 693: Secure & Dependable Computing 22

23 Data Vulnerabilities • Confidential data leaked to a competitor may narrow a competitive edge • Data incorrectly modified can cost human lives • Inadequate security may lead to financial liability if certain personal data are made public Spring 2007 EEC 693: Secure & Dependable Computing 23

24 Data Vulnerabilities • The value of data over time is far less predictable or consistent • Initially, data may be valued highly. However, some data items are of interest for only a short period of time, after which their value declines precipitously Spring 2007 EEC 693: Secure & Dependable Computing 24

25 Principle of Adequate Protection • Principle of Adequate Protection: – Computer items must be protected only until they lose their value – They must be protected to a degree consistent with their value Spring 2007 EEC 693: Secure & Dependable Computing 25

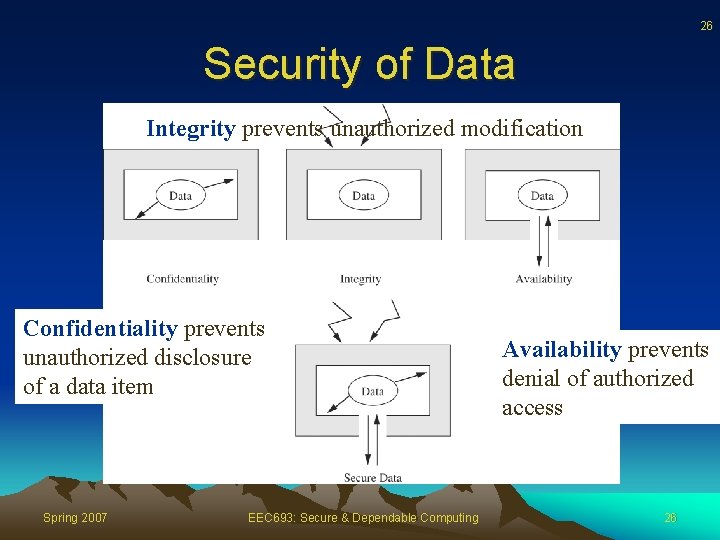
26 Security of Data Integrity prevents unauthorized modification Confidentiality prevents unauthorized disclosure of a data item Spring 2007 EEC 693: Secure & Dependable Computing Availability prevents denial of authorized access 26

27 Threats in Networks • Networks are specialized collections of hardware, software, and data – Each network node is itself a computing system – It experiences all normal security problems • A network must also confront communication problems that involve the interaction of system components and outside resources Spring 2007 EEC 693: Secure & Dependable Computing 27

28 Threats in Networks • The challenges to achieve network security are rooted in – A network's lack of physical proximity – Use of insecure, shared media, and – The inability of a network to identify remote users positively Spring 2007 EEC 693: Secure & Dependable Computing 28

29 What Makes a Network Vulnerable • Anonymity. An attacker can mount an attack from thousands of miles away and never come into direct contact with the system, its administrators, or users • Many points of attack—both targets and origins. An attack can come from any host to any host, so that a large network offers many points of vulnerability Spring 2007 EEC 693: Secure & Dependable Computing 29

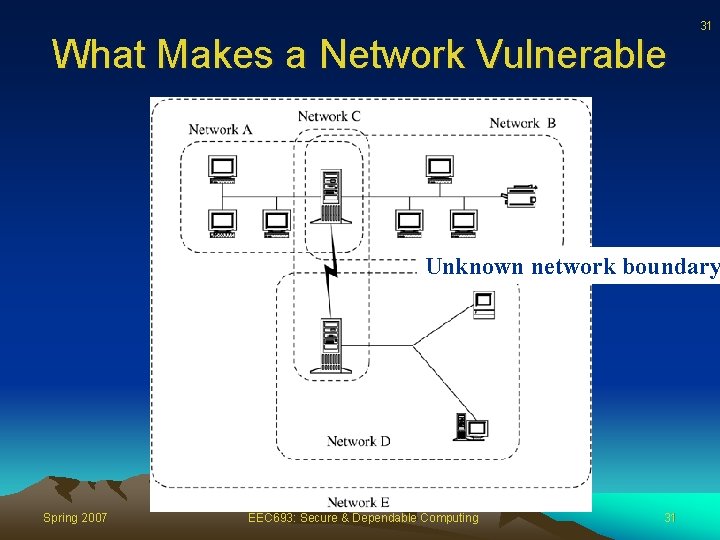
30 What Makes a Network Vulnerable • Sharing. Because networks enable resource and workload sharing, more users have the potential to access networked systems than on single computers • Complexity of system. A network combines two or more possibly dissimilar operating systems. • Unknown network boundary. A network's expandability also implies uncertainty about the network boundary Spring 2007 EEC 693: Secure & Dependable Computing 30

What Makes a Network Vulnerable 31 Unknown network boundary Spring 2007 EEC 693: Secure & Dependable Computing 31

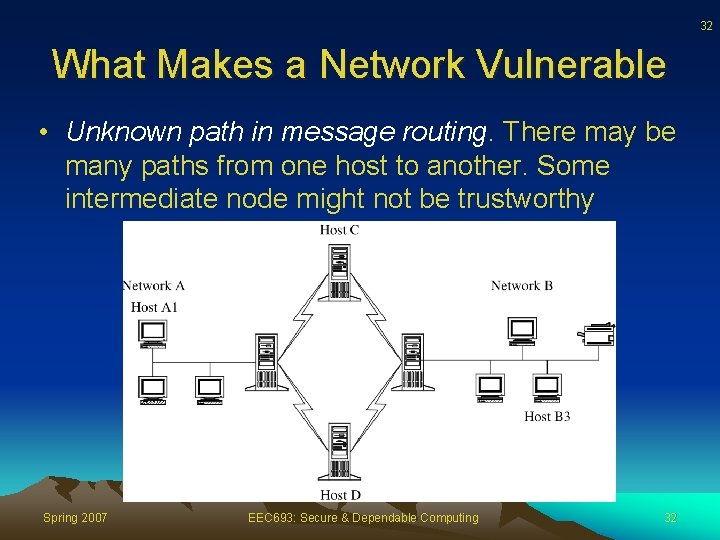
32 What Makes a Network Vulnerable • Unknown path in message routing. There may be many paths from one host to another. Some intermediate node might not be trustworthy Spring 2007 EEC 693: Secure & Dependable Computing 32

33 Methods of Defense • Harm occurs when a threat is realized against a vulnerability • To protect against harm, we can neutralize threat, close the vulnerability, or both • The possibility for harm to occur is called risk Spring 2007 EEC 693: Secure & Dependable Computing 33

34 Methods of Defense • We can deal with harm in several ways. We can seek to – Prevent it, by blocking the attack or closing the vulnerability – Deter it, by making the attack harder, but not impossible – Deflect it, by making another target more attractive (or this one less so) – Detect it, either as it happens or some time after the fact – Recover from its effects Spring 2007 EEC 693: Secure & Dependable Computing 34

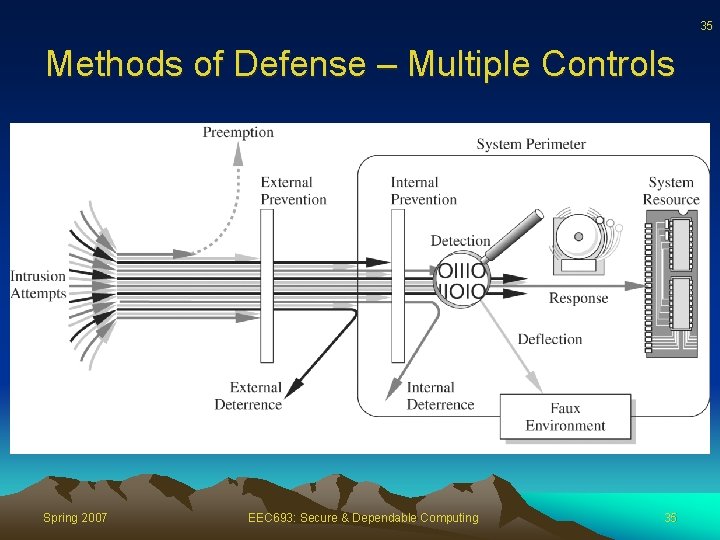
35 Methods of Defense – Multiple Controls Spring 2007 EEC 693: Secure & Dependable Computing 35

36 Countermeasures / Controls • Encryption – Scrambling process • Software controls • Hardware controls – hardware or smart card implementations of encryption • Policies and Procedures – Example: change password periodically • Physical Controls – Example: Locks on doors, guards at entry points Spring 2007 EEC 693: Secure & Dependable Computing 36

37 Software Controls • Internal program controls: parts of the program that enforce security restrictions, such as access limitations • Operating system and network system controls: limitations enforced by the operating system or network to protect each user from all other users • Independent control programs: application programs, such as password checkers, intrusion detection utilities, or virus scanners, that protect against certain types of vulnerabilities • Development controls: quality standards under which a program is designed, coded, tested, and maintained, to prevent software faults from becoming exploitable vulnerabilities Spring 2007 EEC 693: Secure & Dependable Computing 37

38 Principle of Effectiveness • Principle of Effectiveness: Controls must be used—and used properly—to be effective. They must be efficient, easy to use, and appropriate Spring 2007 EEC 693: Secure & Dependable Computing 38