DPS DISSERTATION RETROSPECTIVE Dr James Sicuranza DPS 2019




























- Slides: 47

DPS DISSERTATION RETROSPECTIVE Dr. James Sicuranza DPS 2019 Class - Pace University February 24, 2018

Agenda • • • Overview Dissertation Process Tips DPS/PHD Questions 2

1. 1 Meeting Overview Goal: Why I am here today? Give valuable feedback on the dissertation process. Outcome: • Understanding the makeup of a Dissertation • Explain my Dissertation Process • Share Tips and Tricks • Input on the DPS conversion to Ph. D • Q/A Session DPS - Pace University 3

Dr. James Sicuranza James. Sicuranza@gmail. com • Over 20 years if IT experience with 10 years in Leadership, • Titles: Director, VP, and Program Manager • Current Role: Sr. Program Manager for CSRA and Veterans Affairs guiding their Cloud first strategy Specialties: Building and Architecting Technical Solutions, Infrastructure Delivery, IT Project Management Professional (PMP), Enterprise Email, Directory Services, Vender Management and Negotiations, Risk Management and Data Protection https: //www. linkedin. com/in/james-sicuranza-phd/ DPS - Pace University 4

Dr. James Sicuranza – Dissertation Title James. Sicuranza@gmail. com Usability Case Study: Reduce an Organization’s Usage of Textbased Passwords by Using Built-in Device Hardware for User Authentication Class 2015 DPS - Pace University 5

Dissertation What is a dissertation? • A doctoral dissertation is a lengthy, formal document that argues in defense of a particular thesis. • Two important adjectives used to describe a dissertation are ``original'' and ``substantial. '' The research performed to support a thesis must be both, and the dissertation must show it to be so. In particular, a dissertation highlights original contributions. • There are thousands of websites defining dissertation, templates, formats, videos, help books, and professional writers. • Tip: Review the other DPS Dissertation formats, correlate the pattern you are comfortable with your and copy it Office of Information and Technology 6

Dissertation Template Search Office of Information and Technology 7

Dissertation - Simple Layout This is what I used for my dissertation, very simple: 1. 0 Introduction 2. 0 Literature Review 3. 0 Research Methodology 4. 0 Data Capture and Analysis 5. 0 Research Output and Findings 6. 0 Conclusion and Future Research DPS - Pace University 8

You need an Idea? • This is not a showstopper • Try to find an idea in your area of expertise • You really don’t need an idea, just a unique contribution to the field • The tiny burger on a large bun analogy holds true to the idea • An idea can be something to solve or expose a problem Tip: Look into doing surveys on your area of expertise to gather that unique data as the contribution. Valid surveys can promote new data. DPS - Pace University 9

Find a Problem • Identify a problem that is known but doesn’t have attention or mediation • Any problem in your area of expertise, small or large • Think of anything that could possibly mitigate a problem in your field, or needs investigation • Don’t worried too much on originality as you can find that small unique of data (the burger analogy) • Survey your findings and write a Case study Usability Case Study: Reduce an Organization’s Usage of Text-based Passwords by Using Built-in Device Hardware for User Authentication DPS - Pace University 10

An Idea? TEXTED PASSWORDS! Why are we still using them today? Can I use something else to replace them? Is it technological feasible to replace them? • Despite advances in biometrics and other device authentication technologies, texted passwordbased authentication remains the most commonly used means of authentication in computer systems. • The Media Company has approximately 40, 000 users, on a daily basis, there a substantial number of users need to do a password reset on multiple devices. • This study investigates ways to minimize the use of text passwords. DPS - Pace University 11

Now What? So What? How do I put it together? • Create an experiment • Collect the data (Survey the Users) • Output the results 1. My idea was using Facial Recognition as Built-In technologies make it easier today – So What! This topic has no originality, however? 2. Use the Facial Recognition Software for a selective a group of Users at the workplace as an alternative to text-based password. So What! Some organizations already have Facial as their primary login. Try again! 3. Use the Facial Recognition Software or any alternatives to passwords at the workplace and survey the users in identifying user acceptance of this technology at the workplace? Usability Study, Bingo! DPS - Pace University 12

1. 0 INTRODUCTION

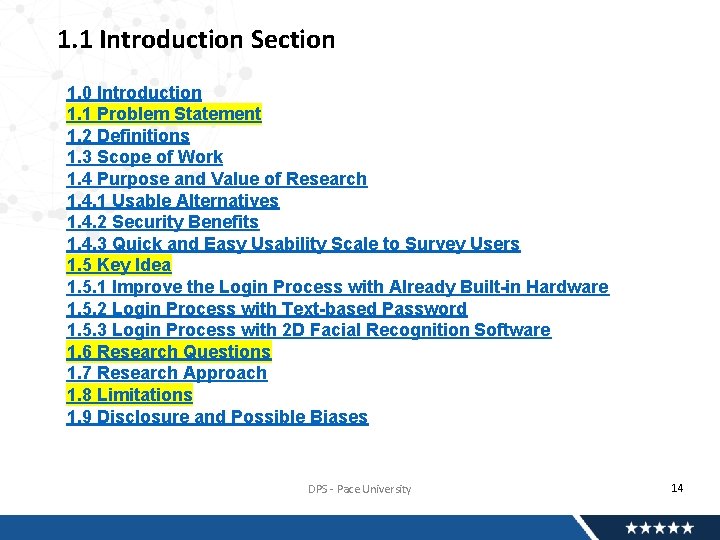
1. 1 Introduction Section 1. 0 Introduction 1. 1 Problem Statement 1. 2 Definitions 1. 3 Scope of Work 1. 4 Purpose and Value of Research 1. 4. 1 Usable Alternatives 1. 4. 2 Security Benefits 1. 4. 3 Quick and Easy Usability Scale to Survey Users 1. 5 Key Idea 1. 5. 1 Improve the Login Process with Already Built-in Hardware 1. 5. 2 Login Process with Text-based Password 1. 5. 3 Login Process with 2 D Facial Recognition Software 1. 6 Research Questions 1. 7 Research Approach 1. 8 Limitations 1. 9 Disclosure and Possible Biases DPS - Pace University 14

1. 2 Research Questions • There are countless examples in how to write your research questions. • Collecting your data first, write your research question second? • Common research questions are What and How questions. 1. What is the user’s acceptance of using facial recognition over text-based passwords in the workplace? 2. What is the frequency a user requires to type in their password at the workplace? 3. What is the amount of time (in hours) a user spends on their workstation at the workplace? 4. How many times (frequency) does a user login per day in the workplace? 5. How does the login totals correlated to the acceptance of Facial Recognition usability? DPS - Pace University 15

2. 0 LITERATURE REVIEW

2. 1 Literature Review • Its overrated, no need to worry • Don’t get overwhelmed as it’s not your data, you are just referencing other peoples work • Use the Electronic Journals and Articles from Commercial Websites • Major trick: use references from an existing article for more relevant information to save time in searching DPS - Pace University 17

2. 2 Literature Review DPS - Pace University 18

2. 3 Literature Review 2. 0 Facial Recognition 2. 1 Biometrics 2. 1. 1 How Does Biometric Recognition Work? 2. 1. 2 Biometric Errors 2. 1. 3 Biometric Recognition – Fingerprints 2. 1. 4 Apple Touch ID 2. 2 Face Recognition 2. 2. 1 Face Recognition Procedure 2. 2. 2 Why Facial Recognition better than Finger Scans? 2. 3 Using Built-in Hardware 2. 4 Current Facial Recognition Adoption 2. 4. 1 Facial Recognition 2 D vs. 3 D DPS - Pace University 19

3. 0 RESEARCH METHODOLOGY

3. 1 What is your method? The Researcher approach utilizes both quantitative and qualitative data collection tools but is rooted in a qualitative (case study) position that recognizes user acceptance of this facial recognition technology at a workplace. • This is the main section to lay out your plan in collecting your data • It will have minor literature in defining the methodology DPS - Pace University 21

3. 2 The main steps 1. Workplace Environment - The context of the location where this study takes place is a Media Company based in New York City, USA. The workstation environments are all desks and office cubicles with business laptops that had a web camera. 2. Authorization - The Researcher reached out in advance to receive permission from the Human Resource and volunteers from the user base. 3. Privacy - To protect all user's privacy in this study all photos for Facial Recognition were stored locally (laptop local hard drive) and not on the corporate server. The facial recognition software managed this private data. 4. Participants - The Researcher chose 15 participants for this study. The size and demographics of the user’s base were sufficed for a usability study. The details are outlined in section 3. 6. 5. Prepare Experiment (Software Installation) - The facial recognition software was by Key Lemon Software [24]. All users in this study installed the software on their own. The Researcher supplied the license keys as Key Lemon kindly lent the keys to test their software in a real working environment. The installation steps are in Appendix C. 6. Run the Experiment (60 days) – All participants used the software approximately 60 days. 7. Primary Data (Usability Survey) - Three SUS Surveys were distributed to each of the 15 participants through email. The survey design is in section 3. 6 and results are in Chapter 4. 8. Secondary Data (Logs) - The data retrieved were Windows Operating System event logs on the subject’s laptop. This was to determine the overall time spent on their workstation and how many times they recorded using the facial recognition software. The details of Log Collection are in Chapter 4. 9. Analysis & Research Questions – The Researcher analyzed the results. 10. Conclusions - To reflect the results of the study and interviews questions related the SUS scores. DPS - Pace University 22

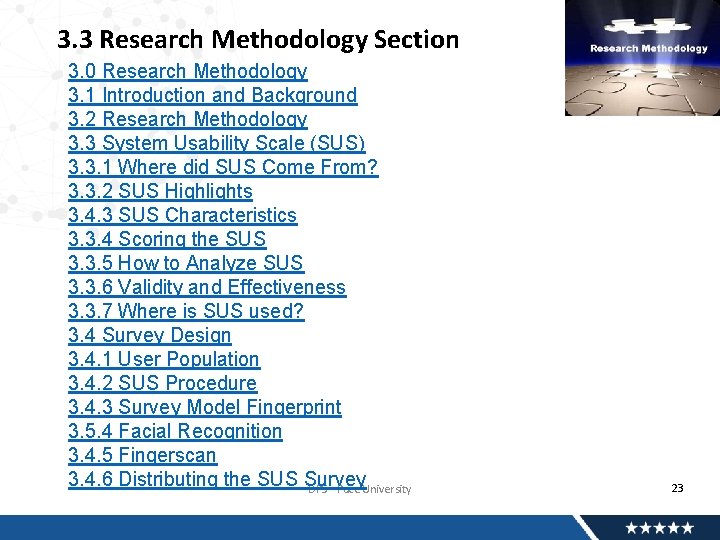
3. 3 Research Methodology Section 3. 0 Research Methodology 3. 1 Introduction and Background 3. 2 Research Methodology 3. 3 System Usability Scale (SUS) 3. 3. 1 Where did SUS Come From? 3. 3. 2 SUS Highlights 3. 4. 3 SUS Characteristics 3. 3. 4 Scoring the SUS 3. 3. 5 How to Analyze SUS 3. 3. 6 Validity and Effectiveness 3. 3. 7 Where is SUS used? 3. 4 Survey Design 3. 4. 1 User Population 3. 4. 2 SUS Procedure 3. 4. 3 Survey Model Fingerprint 3. 5. 4 Facial Recognition 3. 4. 5 Fingerscan 3. 4. 6 Distributing the SUS Survey DPS - Pace University 23

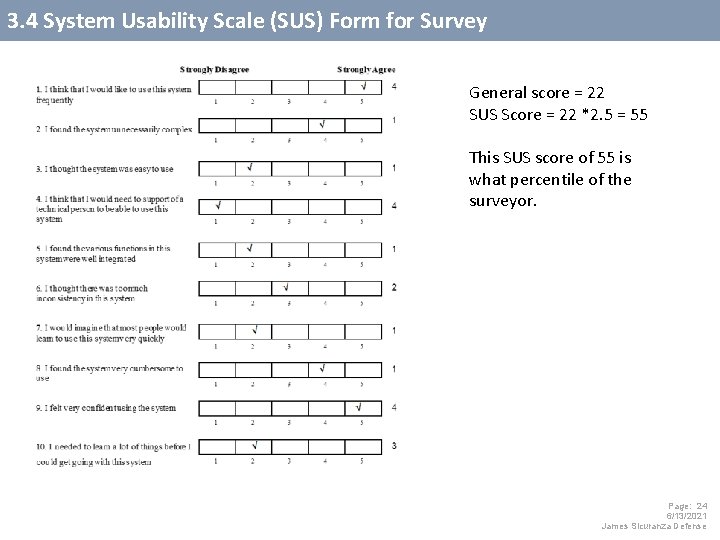
3. 4 System Usability Scale (SUS) Form for Survey General score = 22 SUS Score = 22 *2. 5 = 55 This SUS score of 55 is what percentile of the surveyor. Page: 24 6/13/2021 James Sicuranza Defense

4. 0 DATA CAPTURE

4. 1 Capture you data • Identify the Process to capture the data • Ensure the data capture process can be replicated as a how to book • Identify the data in raw form, and save the results for Findings section This is the section lays out the data, shows results of the data, with minor interpretation of the data. The Research Output & Findings section will further interpret the data to answer your Research questions. DPS - Pace University 26

4. 2 Capture you data 4. 0 Data Capture 4. 1 Experiment plan and Perquisites 4. 1. 1 Workplace Environment 4. 1. 2 Authorization & Privacy 4. 1. 3 Identify Participants 4. 1. 4 Prepare the User’s Laptop 4. 1. 5 Collect Primary Data and Secondary Data 4. 2 Log Capture Process - Session Time & Login Count 4. 2. 1 Export the log files 4. 2. 2 Secondary Data (User 1 Example) 4. 3 Secondary Dataset 1: Log Analysis of Session Time (12 Users) 4. 4 Secondary Dataset 2: Log Analysis Login Count (12 Users) 4. 5 Primary Data 1: SUS Texted-Based Password (Survey 1 - All Users) 4. 6 Primary Data 2: SUS Facial Recognition (Survey 2 - All Users) 4. 7 Primary Data 3: SUS Fingerscan (Survey 3 - All Users) 4. 8 Compile all SUS Scores 4. 9 Total Comparisons DPS - Pace University 27

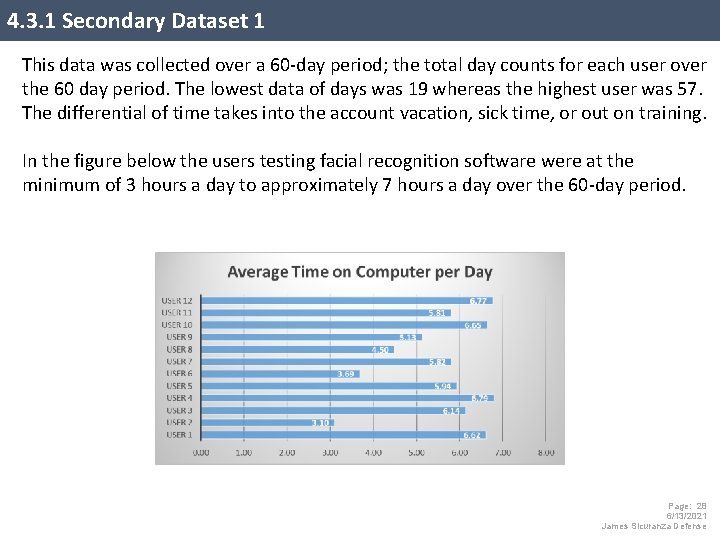
4. 3. 1 Secondary Dataset 1 This data was collected over a 60 -day period; the total day counts for each user over the 60 day period. The lowest data of days was 19 whereas the highest user was 57. The differential of time takes into the account vacation, sick time, or out on training. In the figure below the users testing facial recognition software were at the minimum of 3 hours a day to approximately 7 hours a day over the 60 -day period. Page: 28 6/13/2021 James Sicuranza Defense

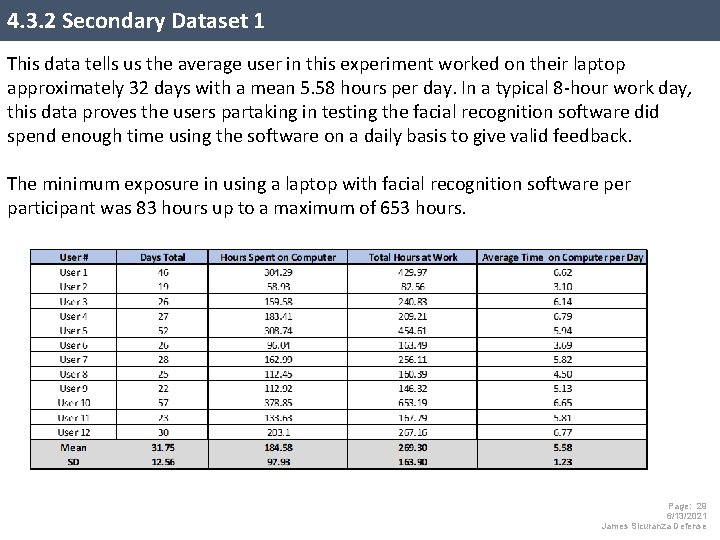
4. 3. 2 Secondary Dataset 1 This data tells us the average user in this experiment worked on their laptop approximately 32 days with a mean 5. 58 hours per day. In a typical 8 -hour work day, this data proves the users partaking in testing the facial recognition software did spend enough time using the software on a daily basis to give valid feedback. The minimum exposure in using a laptop with facial recognition software per participant was 83 hours up to a maximum of 653 hours. Page: 29 6/13/2021 James Sicuranza Defense

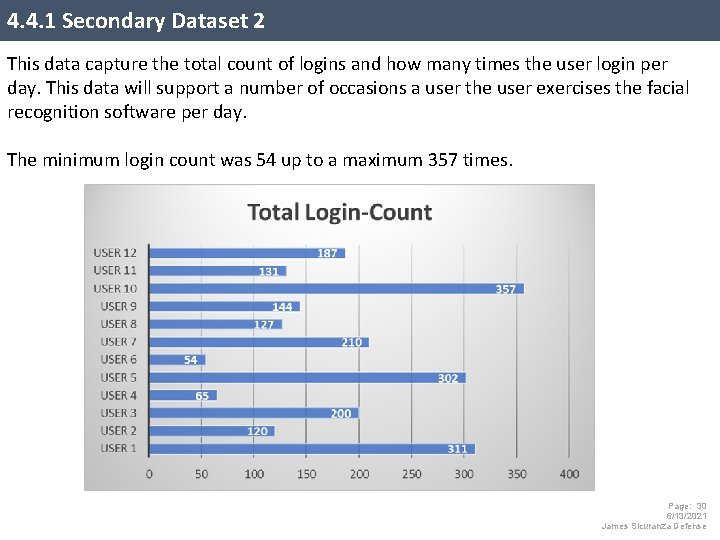
4. 4. 1 Secondary Dataset 2 This data capture the total count of logins and how many times the user login per day. This data will support a number of occasions a user the user exercises the facial recognition software per day. The minimum login count was 54 up to a maximum 357 times. Page: 30 6/13/2021 James Sicuranza Defense

4. 4. 2 Secondary Dataset 2 Page: 31 6/13/2021 James Sicuranza Defense

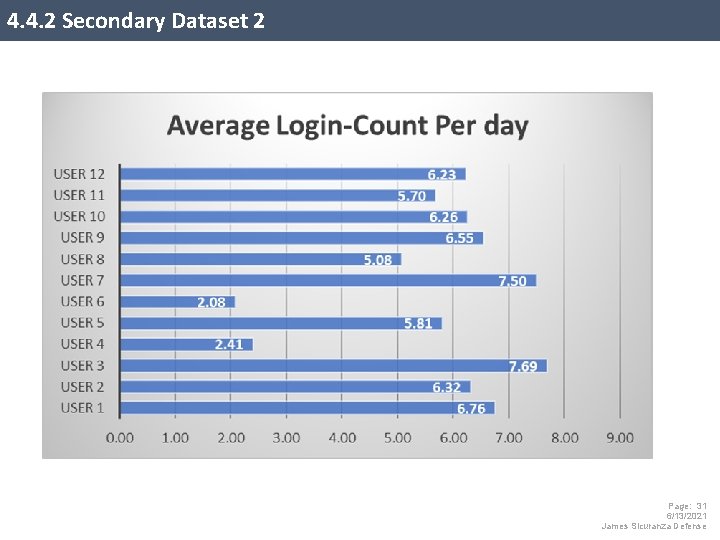
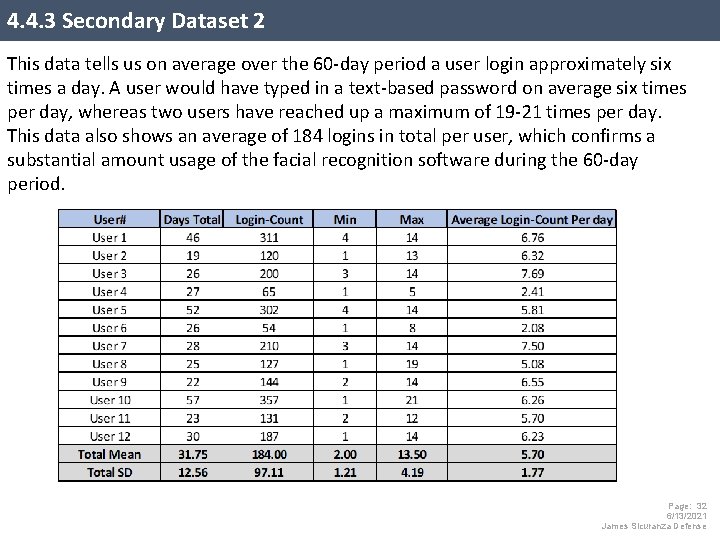
4. 4. 3 Secondary Dataset 2 This data tells us on average over the 60 -day period a user login approximately six times a day. A user would have typed in a text-based password on average six times per day, whereas two users have reached up a maximum of 19 -21 times per day. This data also shows an average of 184 logins in total per user, which confirms a substantial amount usage of the facial recognition software during the 60 -day period. Page: 32 6/13/2021 James Sicuranza Defense

4. 5. 1 Primary Data 1: SUS Text-Base Password (Survey 1) Page: 33 6/13/2021 James Sicuranza Defense

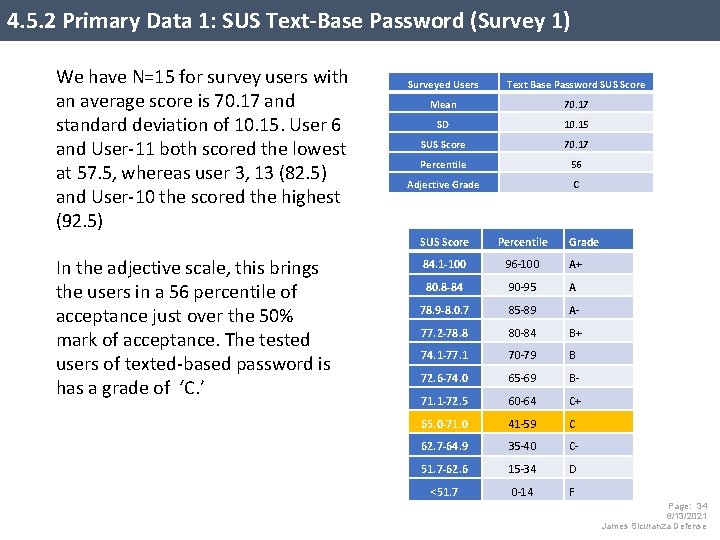
4. 5. 2 Primary Data 1: SUS Text-Base Password (Survey 1) We have N=15 for survey users with an average score is 70. 17 and standard deviation of 10. 15. User 6 and User-11 both scored the lowest at 57. 5, whereas user 3, 13 (82. 5) and User-10 the scored the highest (92. 5) In the adjective scale, this brings the users in a 56 percentile of acceptance just over the 50% mark of acceptance. The tested users of texted-based password is has a grade of ‘C. ’ Surveyed Users Text Base Password SUS Score Mean 70. 17 SD 10. 15 SUS Score 70. 17 Percentile 56 Adjective Grade C SUS Score Percentile Grade 84. 1 -100 96 -100 A+ 80. 8 -84 90 -95 A 78. 9 -8. 0. 7 85 -89 A- 77. 2 -78. 8 80 -84 B+ 74. 1 -77. 1 70 -79 B 72. 6 -74. 0 65 -69 B- 71. 1 -72. 5 60 -64 C+ 65. 0 -71. 0 41 -59 C 62. 7 -64. 9 35 -40 C- 51. 7 -62. 6 15 -34 D <51. 7 0 -14 F Page: 34 6/13/2021 James Sicuranza Defense

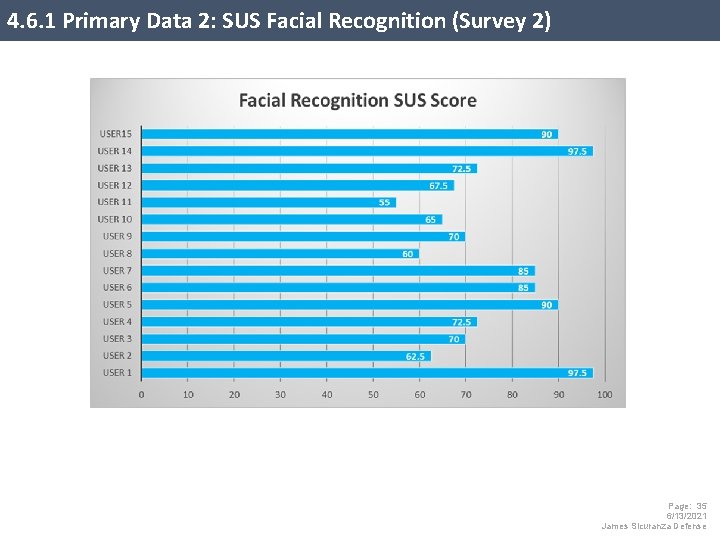
4. 6. 1 Primary Data 2: SUS Facial Recognition (Survey 2) Page: 35 6/13/2021 James Sicuranza Defense

4. 6. 2 Primary Data 2: SUS Facial Recognition (Survey 2) The SUS score is 76. In the adjective scale, this brings the users in a 76 percentile of well over the 50% mark of acceptance. The tested users scored a “B” just 1. 1 points away from a “B+. ” The background in this study calculates in the pain points described in section 1. 1 where the users must change their passwords every 90 days here for this survey results, the “B. ” Survey User Facial SUS Score Mean 76. 00 SD 13. 75 SUS Score 76 Percentile 77 Adjective Grade B Page: 36 6/13/2021 James Sicuranza Defense

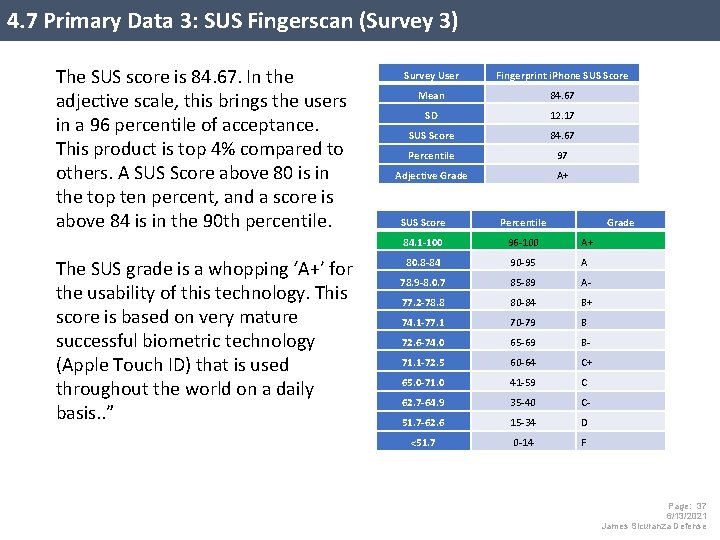
4. 7 Primary Data 3: SUS Fingerscan (Survey 3) The SUS score is 84. 67. In the adjective scale, this brings the users in a 96 percentile of acceptance. This product is top 4% compared to others. A SUS Score above 80 is in the top ten percent, and a score is above 84 is in the 90 th percentile. The SUS grade is a whopping ‘A+’ for the usability of this technology. This score is based on very mature successful biometric technology (Apple Touch ID) that is used throughout the world on a daily basis. . ” Survey User Fingerprint i. Phone SUS Score Mean 84. 67 SD 12. 17 SUS Score 84. 67 Percentile 97 Adjective Grade A+ SUS Score Percentile Grade 84. 1 -100 96 -100 A+ 80. 8 -84 90 -95 A 78. 9 -8. 0. 7 85 -89 A- 77. 2 -78. 8 80 -84 B+ 74. 1 -77. 1 70 -79 B 72. 6 -74. 0 65 -69 B- 71. 1 -72. 5 60 -64 C+ 65. 0 -71. 0 41 -59 C 62. 7 -64. 9 35 -40 C- 51. 7 -62. 6 15 -34 D <51. 7 0 -14 F Page: 37 6/13/2021 James Sicuranza Defense

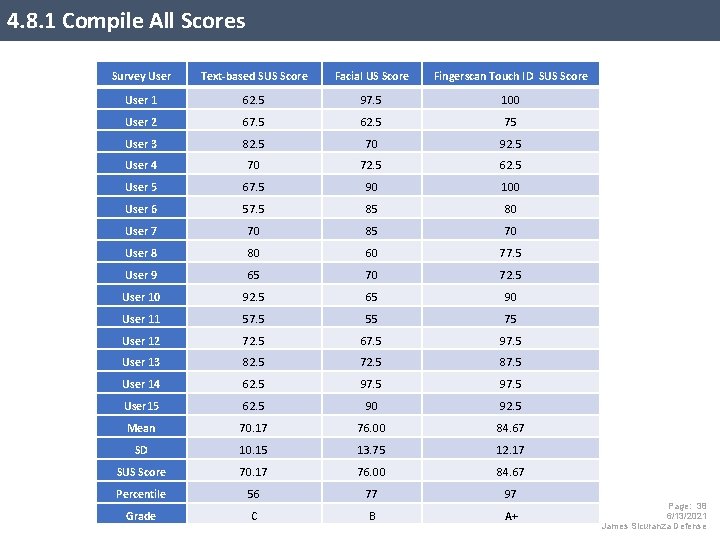
4. 8. 1 Compile All Scores Survey User Text-based SUS Score Facial US Score Fingerscan Touch ID SUS Score User 1 62. 5 97. 5 100 User 2 67. 5 62. 5 75 User 3 82. 5 70 92. 5 User 4 70 72. 5 62. 5 User 5 67. 5 90 100 User 6 57. 5 85 80 User 7 70 85 70 User 8 80 60 77. 5 User 9 65 70 72. 5 User 10 92. 5 65 90 User 11 57. 5 55 75 User 12 72. 5 67. 5 97. 5 User 13 82. 5 72. 5 87. 5 User 14 62. 5 97. 5 User 15 62. 5 90 92. 5 Mean 70. 17 76. 00 84. 67 SD 10. 15 13. 75 12. 17 SUS Score 70. 17 76. 00 84. 67 Percentile 56 77 97 Grade C B A+ Page: 38 6/13/2021 James Sicuranza Defense

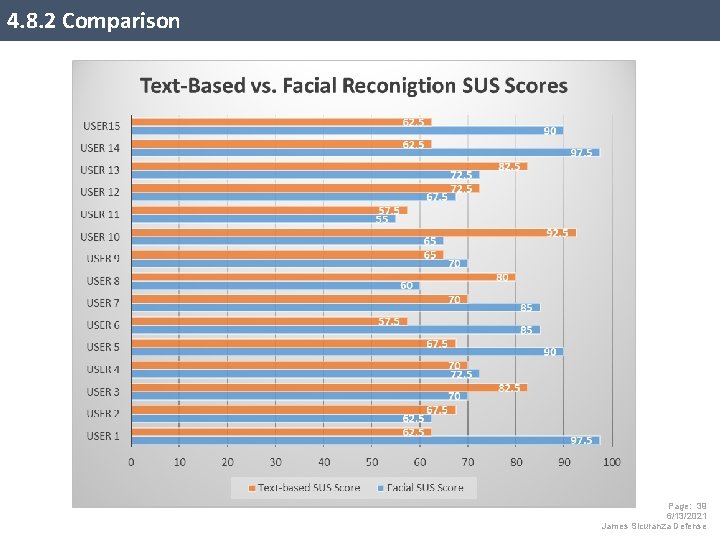
4. 8. 2 Comparison Page: 39 6/13/2021 James Sicuranza Defense

4. 8. 2 Total Comparison This table represents all five datasets captured with full comparisons. This data can point out any correlation between login counts and the user acceptance scores. One of the research questions is, does the high count in logins relates to users accepting a password alternative? Page: 40 6/13/2021 James Sicuranza Defense

5. 0 RESEARCH OUTPUT AND FINDINGS

5. 1 Show off your data • This section simply outlines the results of the data • Remember the Research questions, use the data with graphs and charts to answer those questions • User the results to drive home the Key Findings • The results will be your unique contribution, the small burger in the big sandwich DPS - Pace University 42

5. 1 Show off your data 5. 0 Research Output and Findings 5. 1 Background 5. 2 Key Findings (Research Questions) 5. 2. 1 Research Questions 6. 0 Conclusion 6. 1 Relevance of the Results 6. 2 Future Research DPS - Pace University 43

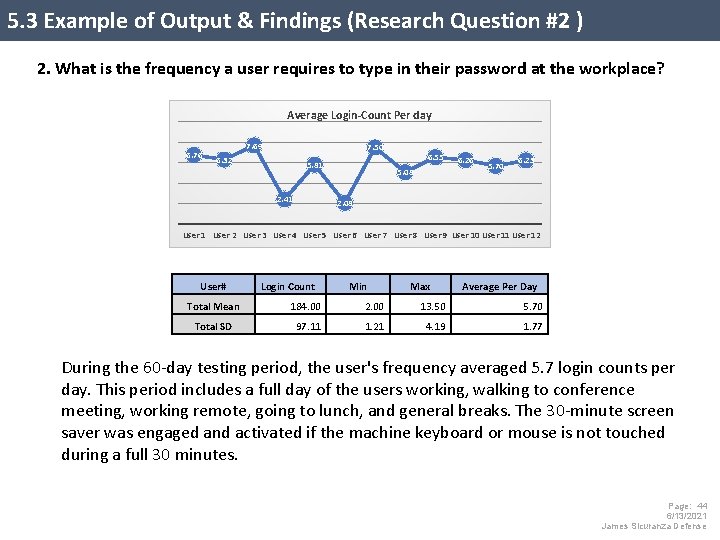
5. 3 Example of Output & Findings (Research Question #2 ) 2. What is the frequency a user requires to type in their password at the workplace? Average Login-Count Per day 6. 76 7. 69 7. 50 6. 32 5. 81 2. 41 6. 55 5. 08 6. 26 5. 70 6. 23 2. 08 User 1 User 2 User 3 User 4 User 5 User 6 User 7 User 8 User 9 User 10 User 11 User 12 User# Login Count Min Max Average Per Day Total Mean 184. 00 2. 00 13. 50 5. 70 Total SD 97. 11 1. 21 4. 19 1. 77 During the 60 -day testing period, the user's frequency averaged 5. 7 login counts per day. This period includes a full day of the users working, walking to conference meeting, working remote, going to lunch, and general breaks. The 30 -minute screen saver was engaged and activated if the machine keyboard or mouse is not touched during a full 30 minutes. Page: 44 6/13/2021 James Sicuranza Defense

Tips 1. During the timeframe 7 -11 PM, stop watching TV. 2. Make a Project Plan, more of a Work Breakdown structure into 5 -6 sections. Be Agile - review each section with your Advisor 3. Do something every night, even little effort adds up 4. If possible, still meet with your team and make a bet who is first or who is last, motivation is key! 5. Try to make it to 140 pages, your data collection in tables can take up to 10 -20 pages in the Appendix 6. References: Have two documents one is your manuscript and the other dedicated to references to make it easier for editing 7. THE DEFNENSE: do not worry too much just have a shorter version of the Dissertation in a professional deck format 8. POST DEFENSE: there will be feedback, modify your dissertation quickly, don’t wait! Department of Veterans Affairs 45

DPS or Ph. D • Pace is AACSB Certified: Association to Advance Collegiate School of Business • A Doctorate from an AACSB School is impressive • DPS dissertation meets the Ph. D requirements • Explaining a DPS can be challenging or overlook • Many online schools will have Ph. D programs but not AACSB accreditation • There is process to covert the DPS to Ph. D, however no target date • Since there is consideration to convert, I use the Ph. D suffix for my resume to make things easier. DPS - Pace University 46

QUESTIONS? 47