Designing Secure Sensor Networks Paper Authors Elaine Shi




















- Slides: 36

Designing Secure Sensor Networks Paper Authors: Elaine Shi and Adrian Perrig, Carnegie Mellon University Presenter: Matt Egyhazy November 1, 2005 10/31/2005 1

Presentation Overview ► Introduction, Context, and Definitions ► Threat and Trust Model ► Security Requirements ► Attacks and Countermeasures ► Future Research Directions ► Critique and Conclusion 10/31/2005 2

Introduction: Paper ► Paper § § § is a Survey of the State-of-the-Art Offers complete overview of Sensor Network security Refers to more specific documents for details Some concepts already covered by Prof. Chen ► Concepts covered will be briefly reviewed ► Concepts not covered will be emphasized ► Authentication, Secrecy, Availability, Integrity ► Insider and Outsider Attacks § Compromised Node § Non-authorized Participant 10/31/2005 3

Introduction: Sensor Networks ► Collection of sensor devices ► Communicate through RF ► Scarce Resources § Power § Memory § Computation ► Uses § Monitor Environments and Report Information 10/31/2005 4

Definitions: Security Terms in Context ► Authentication § Verify identity of originator ► Secrecy § Data privacy ► Availability § System is up and running ► Integrity § Verify that data is not modified § Reject falsely injected data 10/31/2005 5

Context: Security Issues in Sensor Networks ► Not powerful enough for PKI § Must use symmetric algorithms ► RSA Signature ► Diffie-Hellman Key ► AES Encryption ► Physically Insecure § Deployment in insecure environments § Must be inexpensive ► Tamper-proof ► ► Exchange hardware is expensive Wireless Communication Large Scale Node Deployment § Most security protocols ► Designed for ► Do not scale 10/31/2005 two-party use 6

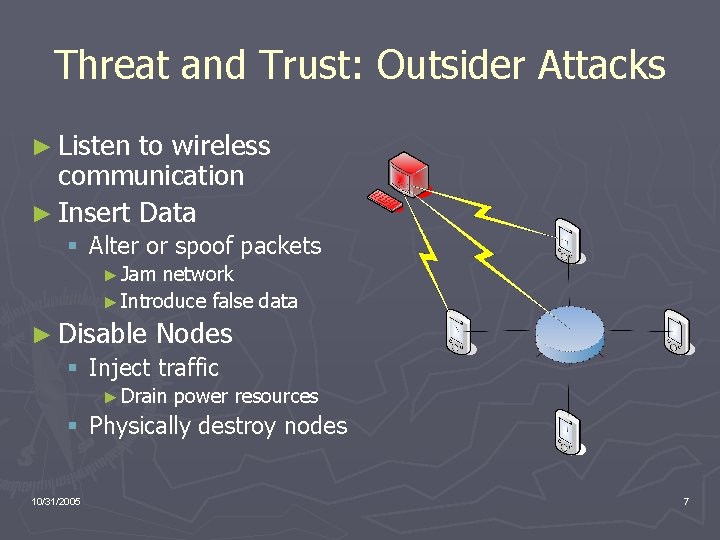
Threat and Trust: Outsider Attacks ► Listen to wireless communication ► Insert Data § Alter or spoof packets ► Jam network ► Introduce false data ► Disable Nodes § Inject traffic ► Drain power resources § Physically destroy nodes 10/31/2005 7

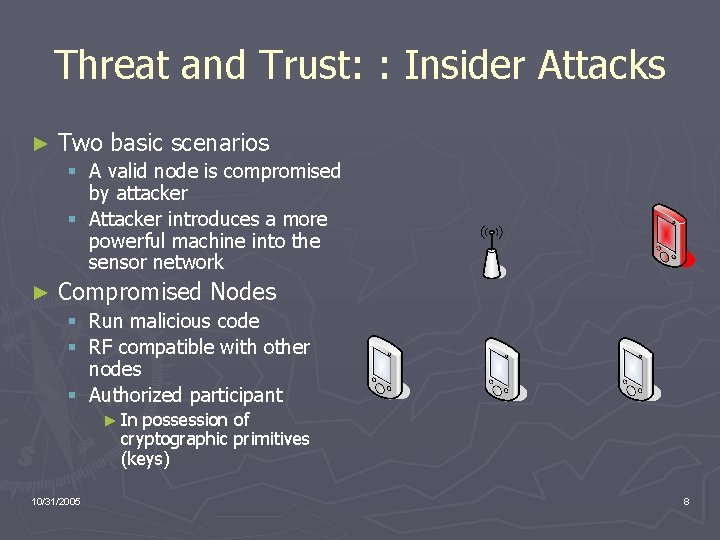
Threat and Trust: : Insider Attacks ► Two basic scenarios § A valid node is compromised by attacker § Attacker introduces a more powerful machine into the sensor network ► Compromised Nodes § Run malicious code § RF compatible with other nodes § Authorized participant ► In possession of cryptographic primitives (keys) 10/31/2005 8

Threat and Trust: Trust Model ► Base Station is Point-of -Trust § Serves as interface between external world and sensor network ► Assumptions § More powerful device ► CPU ► RF ► Memory § Physically secure 10/31/2005 9

Threat and Trust: Trust Model (2) ► Issues with Central Trusted Base Station § Scalability ►D – N/2 keys to setup § Where D is the number of neighbors per node and N is the total number of nodes in the network ►Need to refresh keys on a regular basis or as needed § Higher energy usage ►The nodes closest to the base station use more power § Act as relays for the key exchanges § Single Point of Total Systematic Compromise 10/31/2005 10

Threat and Trust: Trust Model (3) ► Key exchange § Nodes share keys with base station § These keys are used to securely exchange the keys used for node->node communication § We call the secret key node A shares with the base station KA, and similarly KB is the shared key between node B and the base station. If nodes A and B wish to establish a shared secret key KAB, the base station can act as a trusted intermediary to establish that key, for example, by sending a random KAB encrypted with KA to node A and encrypted with KB to node B. 10/31/2005 11

Security Requirements ► Outside Attacks § Robustness ► Encryption ► Release nodes in large quantities ► Adjust routing in real time to overcome changing topology ► Inside Attacks § Graceful Degradation ► Not always possible to detect node compromise and revoke keys ► Use mechanisms to marginalize affect of small number of node breaches 10/31/2005 12

Security Requirements (2) ► Authentication § Prevents outsiders from injecting False Data or stealing secrets § Does not solve compromised node problem ► Secrecy § Encryption used to protect data § ACLs at base station to ensure privacy ►E. g. 10/31/2005 Person Locator 13

Security Requirements (3) ► Availability § Ensure that sensor network is operational until expected end-of-life ► Service Integrity § Secure Data Aggregation ►Detect and reject invalid or false data entries § Time synchronization protocol 10/31/2005 14

Attacks and Countermeasures: Secrecy and Authentication ► Attacks § Eavesdropping ► Listening to node conversation § Packet replay ► Resend recorded node conversations § Modification/Spoofing packets ► Intercept and modify data ► Create completely false data ► Counters § Standard Cryptography 10/31/2005 15

Attacks and Countermeasures: Secrecy and Authentication (2) ► Key Management § Pre-deployed key ► Global § PKI § Complete system compromise ► May be too ► Verification expensive even for initial key setup Do. S § Random key pre-distribution ► Broadcast § u. Tesla Authentication ► Creates Asymmetry § Delayed key disclosure § One-way key chain 10/31/2005 16

Attacks and Countermeasures: Secrecy and Authentication (3) ► Random Key Pre-Distribution § A random pool of keys is selected from the key space. Each sensor node receives a random subset of keys from the key pool before deployment. Any two nodes able to find one common key within their respective subsets can use that key as their shared secret to initiate communication. § Secure paths may not create a connected graph. Range extension is proposed to increase node range. 10/31/2005 17

Attacks and Countermeasures: Availability ► Attacks (Do. S) § Physical Layer ►RF Interference - drains battery § Link Layer ►Collision Attack – induce collisions ►Exhaustion Attack – repeated retransmission ►Unfairness Attack – degrade node performance by hogging channel § Network Layer ►Inject 10/31/2005 malicious packets 18

Attacks and Countermeasures: Availability(2) ► Physical Layer Counters § Frequency Hopping/Spread Spectrum ►Attacker would have to attack wider band ►Might be too sophisticated for low power sensors § Switch to Low Power ►Nodes outlast attacker as he is using more power to Do. S the network than they are while sleeping § Use Alternative Communication ►Optical ►Infrared 10/31/2005 19

Attacks and Countermeasures: Availability(3) ► Link Layer Counters § Collision Attack ► ECC § Repair nodes damaged by collision § Exhaustion Attack ► Rate Limitation § Network can ignore excessive requests without sending expensive radio transmissions § Unfairness Attack ► Small Frames § Individual node can capture the channel only for a short time. § Can increase overhead if nodes usually sends long transmissions § Defeated by quick response by attacker if nodes randomly dealy before responding 10/31/2005 20

Attacks and Countermeasures: Availability(4) ► Network Layer Counters § Authentication ►Allows receiver to detect malicious packets § Message Freshness ►Detect replayed packets ►Nonces § One time use random numbers in message content 10/31/2005 21

Attacks and Countermeasures: Availability (5) ► Sybil Attack § Node illegitimately claims multiple identities § Link Layer - Dominates RF § Routing Layer – Sinkhole ►A sinkhole is created when the Sybil nodes route all their traffic to a sinkhole Sybil node ► Selective Forwarding § Sinkhole can selectively drop valid messages 10/31/2005 22

Attacks and Countermeasures: Availability (6) ► Counters to Sybil § Key Association Technique ►Associate cryptographic keys to the node identity ►Node impersonation can only be accomplished if keys are compromised 10/31/2005 23

Attacks and Countermeasures: Availability (6) ► Routing Attacks § Spread Bogus Routing Information § Hello Flooding ►More powerful adversary sends Hello message to all nodes in the network ►This creates a chain reaction where all the nodes send response back to the adversary. § Not all of these responses can even reach the originator, causing confusion throughout the network 10/31/2005 24

Attacks and Countermeasures: Availability (7) ► Counters to Routing Attacks § Multi-path Routing ►Use multiple paths for each transmission ►This scheme relies on the probability that not all selected paths are controlled by an adversary ►Increases use of network resources 10/31/2005 25

Attacks and Countermeasures: Service Integrity ► Attacks § Focus on forcing the system to accept invalid data § Corrupted sensor/aggregator ► Report invalid results § Sybil ► Impersonated nodes can collude in reporting false data § Do. S ► Prohibit valid nodes from reporting data § False Time Synchronization ► Disseminate 10/31/2005 false synchronization messages 26

Attacks and Countermeasures: Service Integrity (2) ► Counters § Data Aggregation/Reporting ►Secure Information Aggregation Protocol ►aggregate-commit-prove: aggregators help computing aggregation of sensor nodes’ raw data and reply to the home server with the aggregation result together with a commitment to the collection of data; the home server and the aggregators then perform efficient interactive proofs such that the home server will be able to verify the correctness of the results (or detect cheating with high probability). 10/31/2005 27

Attacks and Countermeasures: Service Integrity (3) ► Secure Information Aggregation Protocol § Keys shared between Aggregator and Data sensors ► Provides authenticity § Assuming that nodes cannot be compromised ► Does not protect against corrupt nodes § Aggregator sends hash of sensor values and computed averages to the home server. The home server checks that the committed data is a good representation of the true data values in the sensor network. 2. The home server checks if the aggregator is cheating, in the sense that the aggregation result is not (close to) the correct result aggregated from the committed data values. 1. 10/31/2005 28

Attacks and Countermeasures: Service Integrity (4) ► Time Synchronization Counters § Extremely weak area of sensor network security § All current network designs assume trusted environment 10/31/2005 29

Future Research Directions: Code Attestation ► Verify code running on sensors § Malicious nodes will not have valid code ► Implemented in Hardware § Trusted Computing Group § Next-Generation Secure Computing Base § May add cost to sensor device fabrication ► Implemented in Software § Memory comparison 10/31/2005 30

Future Research Directions: Misbehavior Detection and Revocation ► Utilize voting § Node A votes against B if B is found to be misbehaving § If enough bad votes against B, B’s usage of the network is revoked § However, malicious nodes can slander good nodes by casting votes against them § One work-around is to limit number of votes and store them with the key-ring ► At startup, each node pair exchanges the activation votes to allow its neighbors to vote against it 10/31/2005 31

Future Research Directions: Secure Routing ► Existing Routing Protocols Assume Trusted Environment § Directed Diffusion § Geographic Routing ► Proposed Secure Protocols for Ad-Hoc Wireless are Too Heavy § Also, traffic patterns of sensor network do not align with Ad-Hoc Wireless network 10/31/2005 32

Future Research Directions: Secure Localization ► Properties § Sensor can determine its geographic location § Malicious sensors cannot claim false position ► Solves Several Attacks § Wormhole can be detected if route goes “out of its way” to wormhole node § Sybil can be detected by its close geographic location of impersonated nodes 10/31/2005 33

Future Research Directions: Efficient Cryptographic Primitives ► Traditional security solutions are too expensive in sensor networks ► Symmetric algorithms are not flexible enough ► Cure-all would be more efficient asymmetric algorithms for use in key establishment and digital signatures 10/31/2005 34

Conclusion and Critique ► Conclusion § Sensor networks are not ready for secure deployment § More research and better implementations are needed ► Critique § Light overview of entire field of security in sensor networks § Extra reading of cited documents is required to fully understand mentioned concepts § Overall, well written and authoritative introduction into the field 10/31/2005 35

References ► ► ► A. Wood and J. Stankovic, “Denial of Service in Sensor Networks, ” IEEE Comp. , Oct. 2002, pp. 54– 62. Laurent Eschenauer and Virgil D. Gligor. A key management scheme for distributed sensor networks. In Proceedings of the 9 th ACM Conference on Computer and Communication Security, pages 41– 47, November 2002. H. Chan, A. Perrig, and D. Song, “Random Key Pre-distribution Schemes for Sensor Networks, ” IEEE Symp. Security and Privacy, May 2003. C. Karlof and D. Wagner, “Secure Routing in Wireless Sensor Networks: Attacks and Countermeasures, ” Proc. 1 st IEEE Int’l. , Wksp. Sensor Network Protocols and Applications, May 2003. B. Przydatek, D. Song, and A. Perrig, “SIA: Secure Information Aggregation in Sensor Networks, ” Proc. 1 st ACM Int’l. Conf. Embedded Networked Sensor Sys. , Nov. 2003, pp. 255– 65. 10/31/2005 36
 Elaine shi
Elaine shi Design a secure network
Design a secure network Bluetooth based smart sensor networks
Bluetooth based smart sensor networks Bluetooth based smart sensor networks
Bluetooth based smart sensor networks Habitat monitoring sensor
Habitat monitoring sensor Single node architecture in wireless sensor networks
Single node architecture in wireless sensor networks Habitat monitoring sensor
Habitat monitoring sensor Designing and managing value networks
Designing and managing value networks Designing and managing value networks
Designing and managing value networks Designing global supply chain networks
Designing global supply chain networks Value network in marketing
Value network in marketing How to cite apa when multiple authors
How to cite apa when multiple authors Virtual circuit vs datagram networks
Virtual circuit vs datagram networks Backbone networks in computer networks
Backbone networks in computer networks Qin shi huang mercury
Qin shi huang mercury Zhu shi
Zhu shi Shi yun lim
Shi yun lim Hiragana shi
Hiragana shi S3xt trade
S3xt trade Helped overthrow the qin dynasty
Helped overthrow the qin dynasty Jieming shi
Jieming shi Shi vs tsu
Shi vs tsu Shi order tracking
Shi order tracking Ao lei shi
Ao lei shi Ni hao wo jiao
Ni hao wo jiao August shi
August shi Shi
Shi Dr margaret shi
Dr margaret shi A shi ra la do nai
A shi ra la do nai Qin map
Qin map Lim yun
Lim yun Qingkai shi
Qingkai shi Chi wanfan
Chi wanfan Qin dynasty quotes
Qin dynasty quotes Bouriscot
Bouriscot Exército de terracota
Exército de terracota Model order reduction
Model order reduction