UNITIII SENSOR AND MESH NETWORKS Sensor Networks Role




















- Slides: 57

UNIT-III SENSOR AND MESH NETWORKS Sensor Networks – Role in Pervasive Computing – In Network Processing and Data Dissemination – Sensor Databases – Data Management in Wireless Mobile Environments –Wireless Mesh Networks – Architecture – Mesh Routers – Mesh Clients – Routing – Cross Layer Approach – Security Aspects of Various Layers in WMN – Applications of Sensor and Mesh networks IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 1

SENSOR NETWORK • • • Large networks of simple sensors Usually deployed randomly Very prone to failures Use broadcast paradigms to communicate with other sensors Collect information and send it to base station Must focus on power conservation, instead of Qo. S. Energy=distance 2 • Static: once deployed do not change. • Dynamic: could move by themselves or by an external agent. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 2

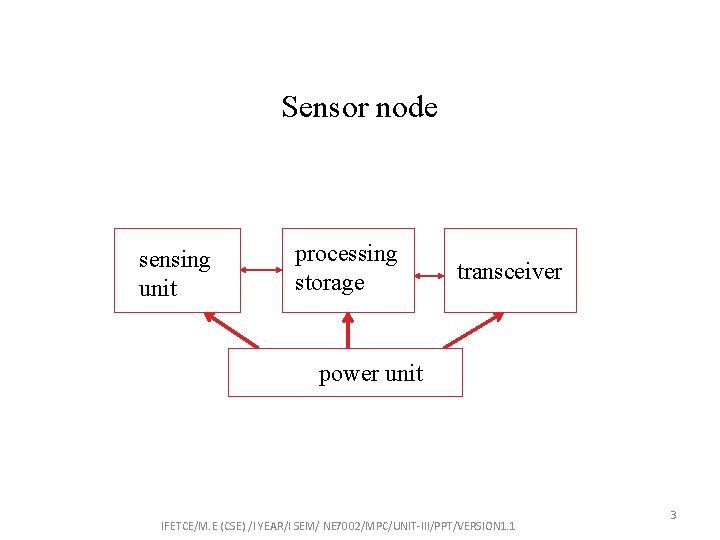
Sensor node sensing unit processing storage transceiver power unit IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 3

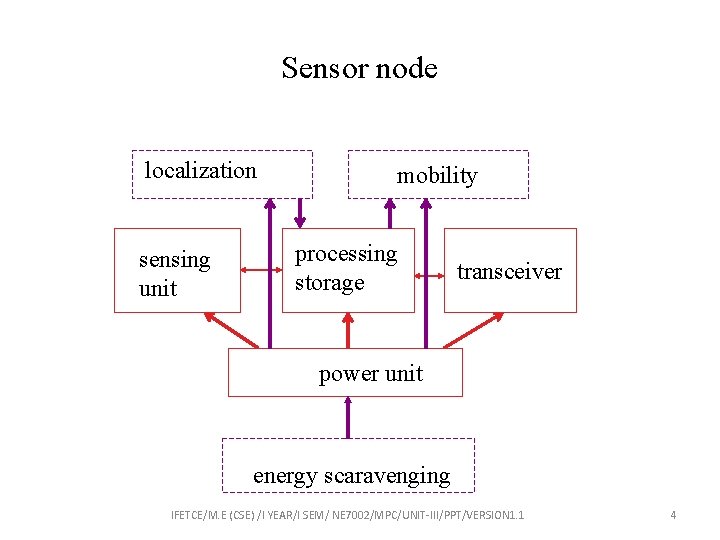
Sensor node localization sensing unit mobility processing storage transceiver power unit energy scaravenging IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 4

Sensor characteristics • • • consume low power autonomous operate in high volumetric densities adaptive to environment cheap IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 5

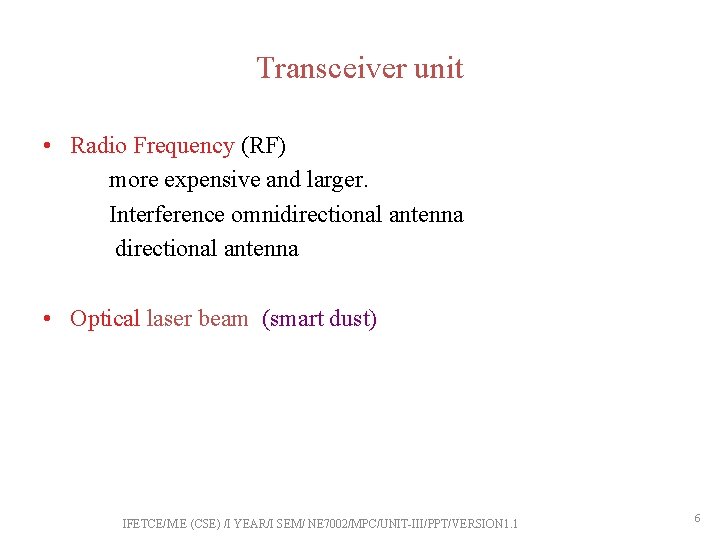
Transceiver unit • Radio Frequency (RF) more expensive and larger. Interference omnidirectional antenna directional antenna • Optical laser beam (smart dust) IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 6

Transceiver unit • Radio Frequency (RF) more expensive and larger. Interference omnidirectional antenna directional antenna • Optical laser beam (smart dust) IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 7

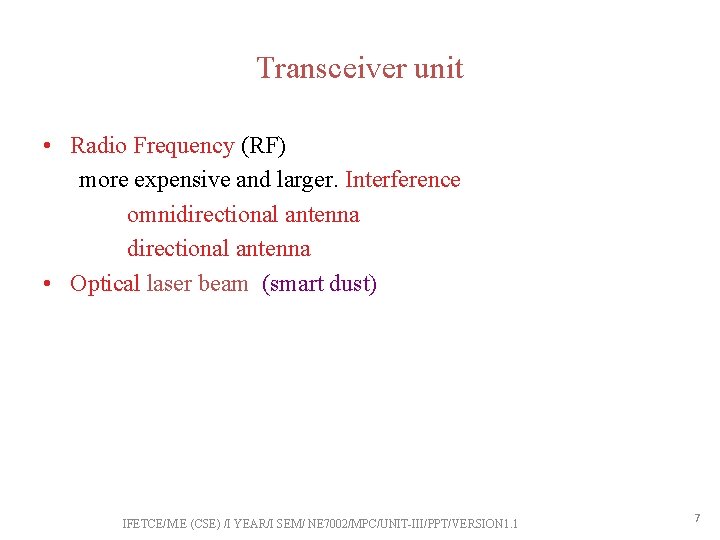
Transceiver unit • Radio Frequency (RF) more expensive and larger. Interference omnidirectional antenna • Optical laser beam (smart dust) need line of sight for communication no interference IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 8

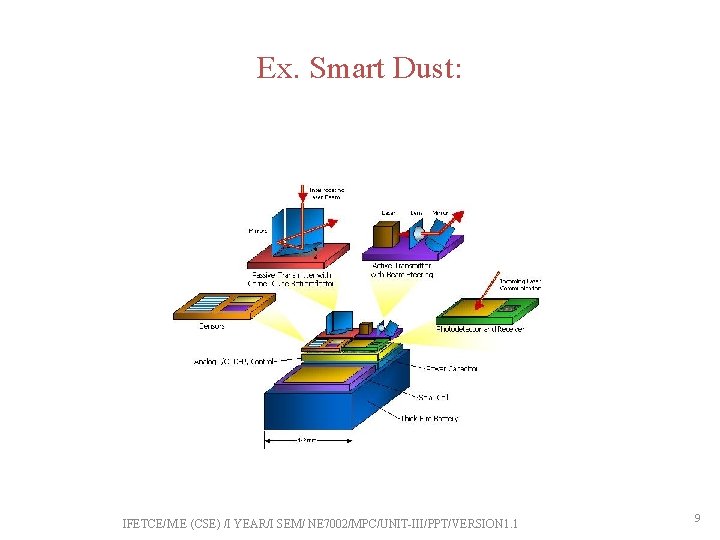
Ex. Smart Dust: IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 9

ROLE IN PERVASIVE COMPUTING Motivation: • Future ‘pervasive applications’ need to adapt the variations of context of execution, change of locations, change of devices, change of hardware resources of devices, and so on • Recent research efforts focused on designing new mobile middleware systems capable of supporting mobility • Apart from mobility, pervasive middleware will need to operate under above-mentioned conditions of a radical change • Few contemporary researches have indeed focused on some of these requirement • A qualitative difference between intended requirements and practical achievements still remains there IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 10

Characteristics • Pervasive middleware is characterized by following: • Context awareness and service discovery – learn the environment so that the interactions between services and devices are made proper to get a desired service • Smartness and adaptation – construct, manipulate and display environments, resources and contents for any services • Heterogeneity and integration – handle different applications on different devices connected to different network environments, and integrate a number of parameters such as Qo. S, service reliability, invisibility etc. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 11

• Programming interface – address issues related to service adaptation and integration • Disconnectivity – protect services and applications from transient failures when users or devices go out of the range of wireless connectivity • Security – minimize threats to privacy, in spite of being pervasive IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 12

Design Components • Three prime design components of a pervasive middleware • Proactive Knowledge on Environment – discover proactively network bandwidth, nature of communication, types of devices and their functionalities – Pervasive middleware will facilitate a transparent communication model to applications to interact flexibly with different devices in different network environments IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 13

• Building Applications on Context-awareness – develop systems, which determine user tasks in different contexts, such as profile history, preferences, societal behavior and environmental conditions – An application is usually synthesized to suit tasks, associated with components and services • Appropriate Programming Interface – express different activities, preferences of users, and different characteristics of physical and functional computing components – the semantic modeling in pervasive middleware should provide a uniform and common way to express contextawareness for users’ various activities in their applications IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 14

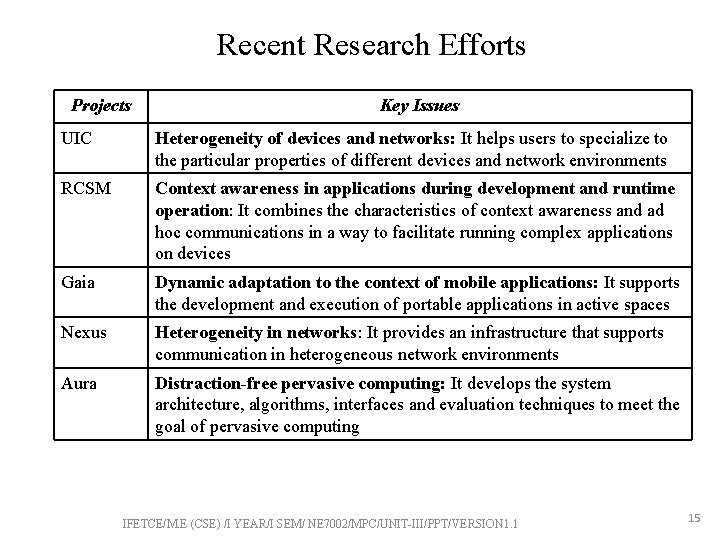
Recent Research Efforts Projects Key Issues UIC Heterogeneity of devices and networks: It helps users to specialize to the particular properties of different devices and network environments RCSM Context awareness in applications during development and runtime operation: It combines the characteristics of context awareness and ad hoc communications in a way to facilitate running complex applications on devices Gaia Dynamic adaptation to the context of mobile applications: It supports the development and execution of portable applications in active spaces Nexus Heterogeneity in networks: It provides an infrastructure that supports communication in heterogeneous network environments Aura Distraction-free pervasive computing: It develops the system architecture, algorithms, interfaces and evaluation techniques to meet the goal of pervasive computing IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 15

Challenges • Some of immediate challenges faced by the researchers are charted below: • Service discovery – Research challenge would be to make use of a task (needs) to discover services in an entire pervasive computing environment that would be able to give services to users based on Qo. S-aware specifications – Example: L 2 imbo has developed a middleware to support Qo. S in mobile applications. However, currently these needs are taken into account locally only IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 16

• Context awareness – Research challenge will be that N classes of applications will have to adopt M numbers devices (N-to-M) instead of doing a single new application to a group of devices (1 -to. M) – Context (or extension) with respect to an application is to bind and re-bind a number of pervasive devices to facilitate the continuity of applications running on – Example: In projects-RCSM, Lime, Tspaces- task components interact with services by sharing a tuple space or an event service or data-oriented services IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 17

• Adaptation – Different adaptation schemes need different system configurations that vary over time to accommodate dynamic requirements of users – Research challenge arises because adaptation must often take place without human intervention or ‘minimum’ human intervention to achieve calm computing – Possible extensions of existing mobile middleware to include transformation and adaptation for content and human interface in terms of context in applications IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 18

IN NETWORK PROCESSING AND DATA DISSEMINATION Conventional Methods • Direct communication with the base station – Sensor nodes communicate with the base station directly. – Energy consuming. • Multi-hop Scheme – Transmit through some other intermediate nodes. – Energy consuming. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 19

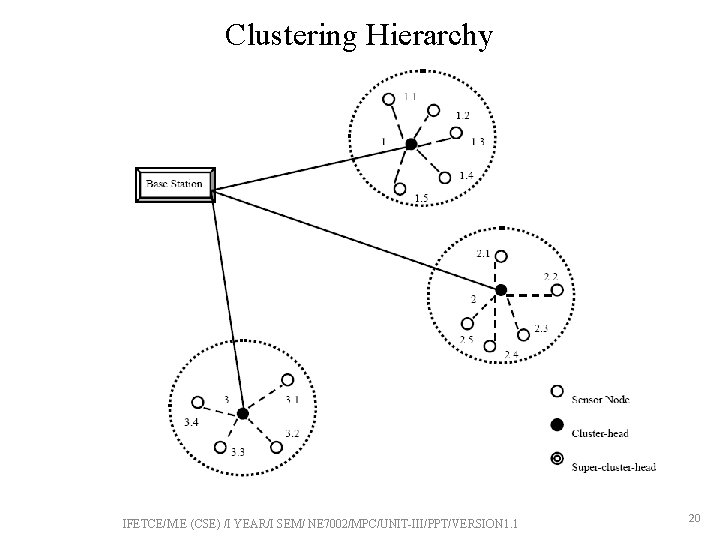
Clustering Hierarchy IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 20

Low Energy Adaptive Clustering Hierarchy (LEACH) • Designed for sensor networks where an end-user wants to remotely monitor the environment. Where the data from the individual nodes must be sent to a central base station, often located far from the sensor network. • Desirable properties for protocols on these networks: – Use 100’s – 1000’s of nodes – Maximize system lifetime – Maximize network coverage – Use uniform, battery operated nodes • The use of distributed cluster formation and local processing to reduce global communication along with randomized rotation of the cluster-heads allows LEACH to achieve the desired properties while being energy-efficient. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 21

SENSOR DATABASES Why Databases and Sensors? • All applications depend on data processing • Declarative query language over sensors attractive – Application specific solutions difficult to built and deploy • Want “to combine and aggregate data streaming from motes. ” – Sounds like a database… IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 22

New Problems In Sensor Databases • Sensors unreliable – Come on and offline, variable bandwidth • Sensors push data • Sensors stream data • Sensors have limited memory, power, bandwidth – Communication very expensive • Sensors have processors • Sensors very numerous IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 23

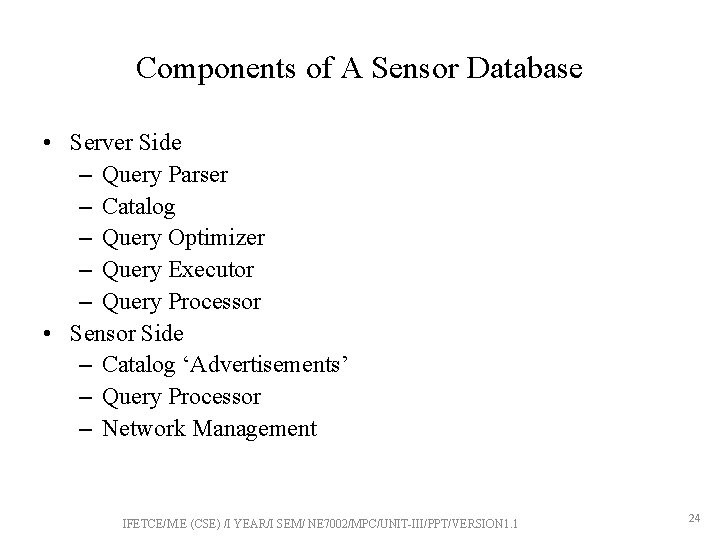
Components of A Sensor Database • Server Side – Query Parser – Catalog – Query Optimizer – Query Executor – Query Processor • Sensor Side – Catalog ‘Advertisements’ – Query Processor – Network Management IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 24

DATA MANAGEMENT IN WIRELESS MOBILE ENVIRONMENTS Why Mobile Data Management? • Wireless Connectivity and use of PDA’s, handheld computing devices on the rise • Workforces will carry extracts of corporate databases with them to have continuous connectivity • Need central database repositories to serve these work groups and keep them fairly upto-date and consistent IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 25

Mobile Data Applications • Sales Force Automation - especially in pharmaceutical industry, consumer goods, parts • Financial Consulting and Planning • Insurance and Claim Processing - Auto, General, and Life Insurance • Real Estate/Property Management Maintenance and Building Contracting • Mobile E-commerce IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 26

Mobility – Impact on DBMS • • • Handling/representing fast-changing data Scale Data Shipping v/s Query shipping Transaction Management Replica management Integrity constraint enforcement Recovery Location Management Security User interfaces IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 27

DBMS Industry Scenario • Most RDBMS vendors support the mobile scenario - but no design and optimization aids • Specialized Environments for mobile applications: Sybase Remote Server Synchrologic i. MOBILE Microsoft SQL server - mobile application support Oracle Lite Xtnd-Connect-Server (Extended Technologies) Scoutware (Riverbed Technologies) IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 28

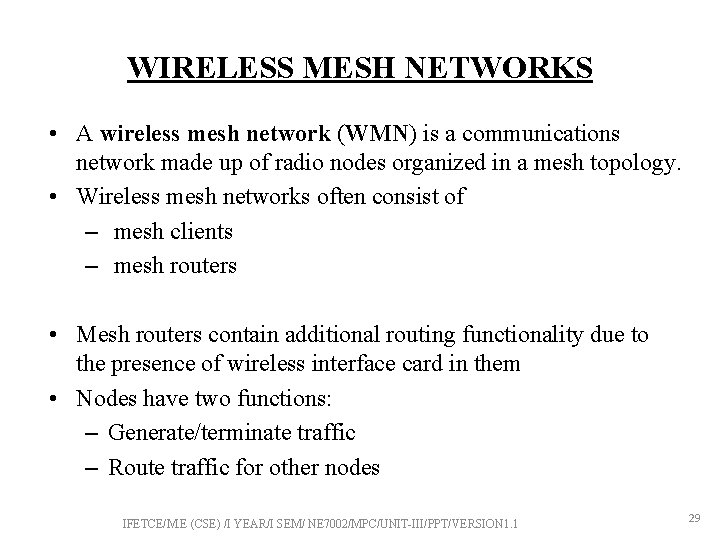
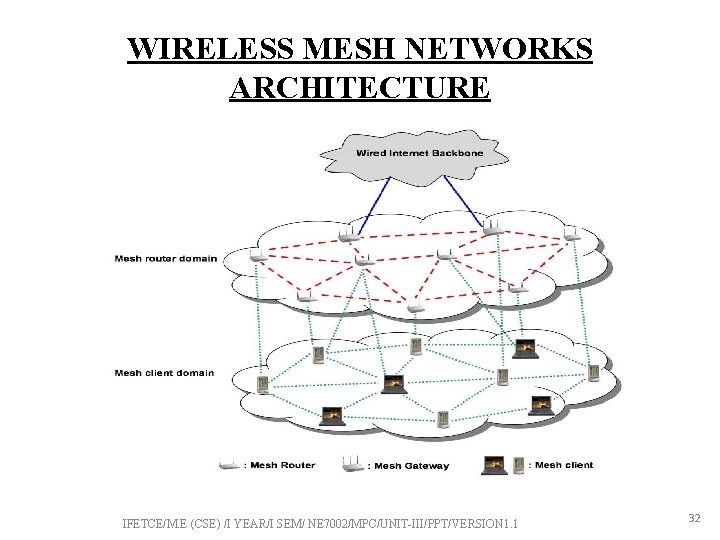
WIRELESS MESH NETWORKS • A wireless mesh network (WMN) is a communications network made up of radio nodes organized in a mesh topology. • Wireless mesh networks often consist of – mesh clients – mesh routers • Mesh routers contain additional routing functionality due to the presence of wireless interface card in them • Nodes have two functions: – Generate/terminate traffic – Route traffic for other nodes IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 29

Characteristics of Wireless mesh networks • Multihop Wireless network. • Support for adhoc networking and capability of self forming, self healing and self organization. • Mobility dependence on the type of mesh node. • Multiple types of network access. • Dependence of power consumption constraints on the type of mesh nodes IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 30

Why WMN? • Multi-hop wireless network • Support for ad-hoc networking, and capability of selfforming, self healing and self organization. • Multiple types of network access • Mobility dependence on the type of mesh nodes • Compatibility and interpretability with existing wireless technologies • Compatibility and inter operability with existing wireless networks • Dedicated routing and configuration • Mobility IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 31

WIRELESS MESH NETWORKS ARCHITECTURE IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 32

Types of WMN • Infrastructure/ Backbone WMN • Client WMN • Hybrid WMN IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 33

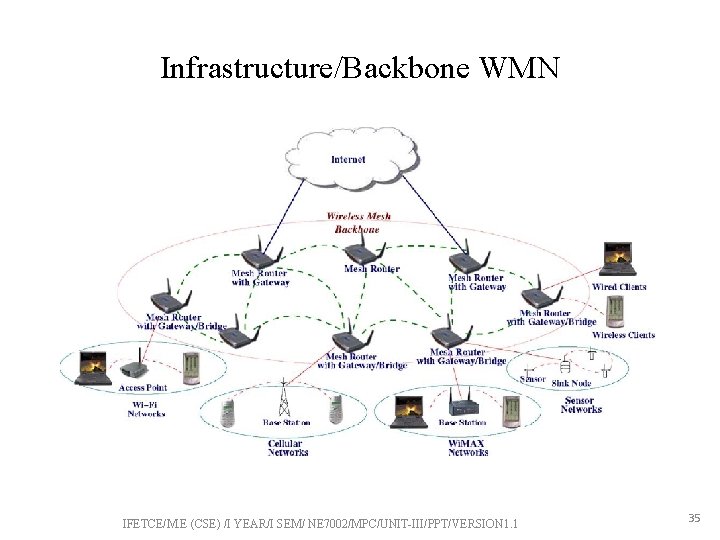
Infrastructure/Backbone WMN • Mesh routers form an mesh infrastructure among themselves. • Provides backbone for clients and enables integration of WMNs with existing wireless networks and Internet through gateway/bridge functionalities. • Clients connect to mesh router with wireless link or Ethernet IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 34

Infrastructure/Backbone WMN IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 35

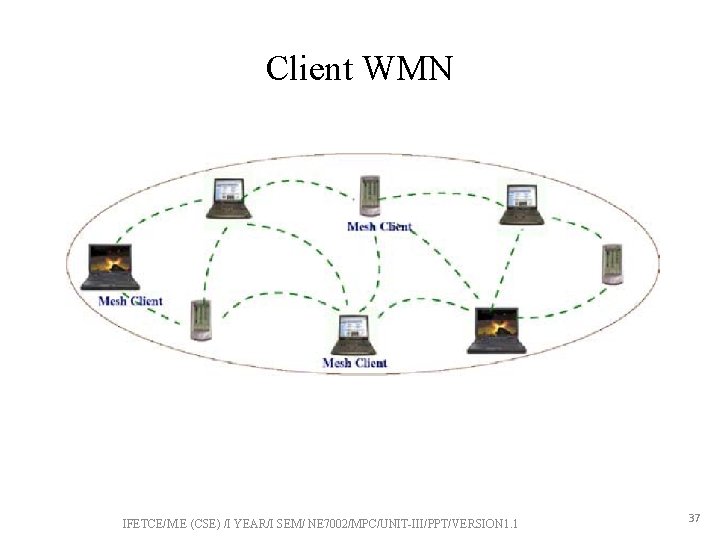
Client WMN • Client nodes constitute peer-to-peer network, and perform routing and configuration functionalities as well as provide end -user applications to customers, ”mesh routers are not required” • Multi-hop routing. • Client nodes have to perform additional functions such as routing and self-configuration. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 36

Client WMN IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 37

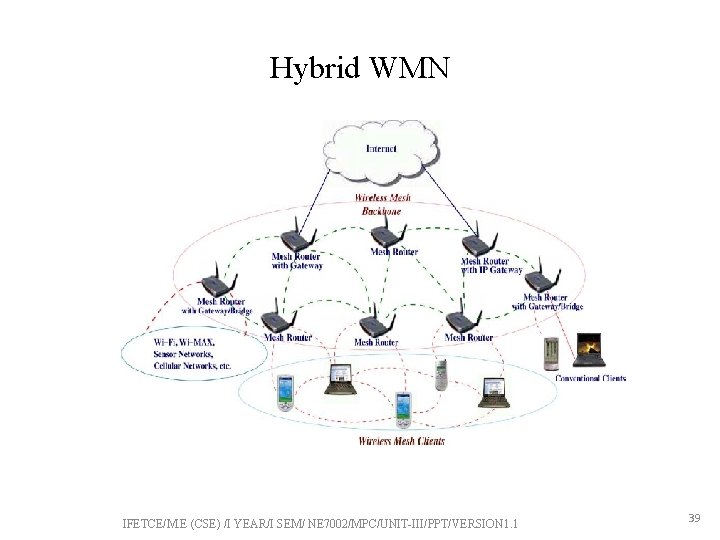
Hybrid WMN • A combination of infrastructure and client meshing. • Infrastructure provides connectivity to other networks such as the Internet, Wi-Fi, Wi. MAX, cellular, and sensor networks; • Mesh clients can access the network through mesh routers as well as directly meshing with other mesh clients. • The routing capabilities of clients provide better connectivity and coverage IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 38

Hybrid WMN IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 39

Protocol Design • • • Physical Layer Mac Layer Network Layer Transport Layer Application Layer IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 40

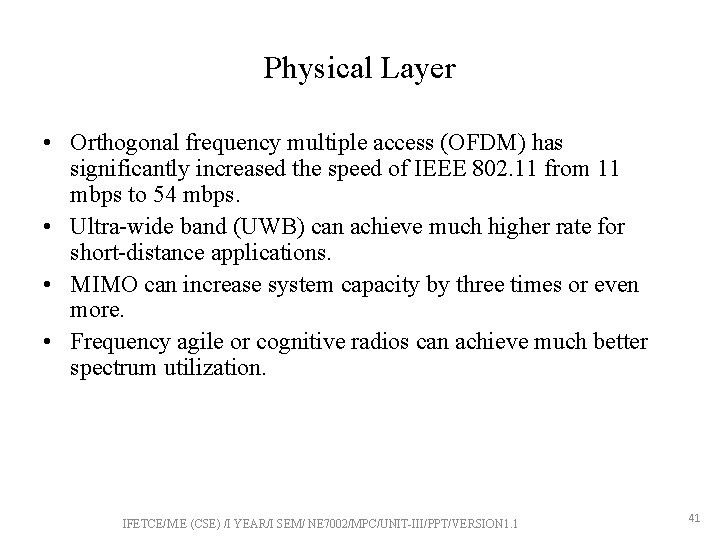
Physical Layer • Orthogonal frequency multiple access (OFDM) has significantly increased the speed of IEEE 802. 11 from 11 mbps to 54 mbps. • Ultra-wide band (UWB) can achieve much higher rate for short-distance applications. • MIMO can increase system capacity by three times or even more. • Frequency agile or cognitive radios can achieve much better spectrum utilization. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 41

MAC Layer Differences between WMNs MACs and Wireless Networks MACs • MACs for WMNs are concerned with more than one hop communication • MAC must be distributed and collaborative, and must work for multipoint-to-multipoint communication. • Network self-organization is needed for better collaboration between neighboring nodes and nodes in multi-hop distances. • Mobility affects the performance of MAC. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 42

Routing Layer Features of routing protocol for WMNs: • Multiple Performance Metrics – Hop-count is not an effective routing metric. – Other performance metrics, e. g. , link quality and round trip time (RTT), must be considered. • Scalability – Routing setup in large network is time consuming. – Node states on the path may change. – Scalability of routing protocol is critical in WMNs. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 43

Routing Layer • Robustness – WMNs must be robust to link failures or congestion. – Routing protocols need to be fault tolerant with link failures and can achieve load balancing. • Adaptive Support of Both Mesh Routers and Mesh Clients – Mesh routers : minimal mobility, no constraint of power consumption, routing is simpler – Mesh clients : mobility, power efficiency, routing is complicated – Need to design a routing protocol that can adaptively support both mesh routers and mesh clients. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 44

Transport layer: research issues • Cross-layer Solution to Network Asymmetry – Routing protocol can select an optimal path for both data and ACK packets. – MAC layer and error control may need to treat TCP data and ACK packets differently. • Adaptive TCP – WMNs will be integrated with the Internet and various wireless networks such as IEEE 802. 11, 802. 16, 802. 15, etc. – Same TCP is not effective for all networks. – Applying different TCPs in different networks is a complicated and costly approach, and cannot achieve satisfactory performance. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 45

Application layer Applications supported by WMNs: • Internet Access – Advantages of WMNs: low cost, higher speed, and easy installation. • Distributed Information Storage and Sharing – Data sharing between nodes within WMNs – Query/retrieve information located in distributed database servers. • Information Exchange across Multiple Wireless Networks. – Cellular phone talks Wi-Fi phone through WMNs, – Wi-Fi user monitors the status of wireless sensor networks. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 46

When WMN? • • Broadband home networking Community and neighborhood networking Enterprise networking Wireless mesh networks Transportation systems Building automation Health and medical systems Security surveillance systems IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 47

MESH ROUTER • Routers are used to direct data traffic from one place, or node, to another. Each router has a specific set of locations from which it can accept data, and a specific set of locations to which it can send data • A mesh, or multi-hop network, is a highly decentralized way of organizing nodes that does not require predetermined paths between them. Such networks are made possible by mesh routers, which adjust, in real time, the locations with which they can communicate. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 48

MESH CLIENTS • The mesh clients are often laptops, cell phones and other wireless devices. • Necessary routing capability • No bridging, single wireless interface -- hardware platform &software much simpler • High variety of devices, e. g. laptop/desktop PC, pocket PC, PDA, IP phone etc. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 49

ROUTING • The design of the routing protocols for WMNs is still an area of research although there are many routing protocols that are available for ad hoc networks. • However, an optimal routing protocol for WMNs must possess features like: – multiple performance metrics – scalability – robustness and – efficient routing with mesh infrastructure. • The routing protocols for ad hoc networks is equipped with some of these features, but non of them possesses all of the above. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 50

• Multi Radio Routing – In a multi-radio link quality source routing (MR-LQSR) a new performance metric , weighted cumulative expected transmission time (WCETT) , is incorporated. – Both link quality metric and the minimum hop count are accounted for in WCETT which provides a good tradeoff between delay and throughput. • Multi-Path Routing: – Better load balancing and providing high fault tolerance are the two main objectives of using multi-path routing. – Multiple paths are selected between source and the destination – This provides better fault tolerance as when a link is broken another path can be chosen. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 51

– This enhances efficiency since without waiting to set up a new routing path, the end-to-end delay, throughput, and fault tolerance can be improved. – Complexity is the major hurdle of multi-path routing. • Geographical routing - This kind of routing scheme forwards packets only by using the position information of the nodes in the vicinity and in the destination node unlike the topology based schemes. - This suggests that there is less impact on the geographic routing due to a topology change than the other routing protocols. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 52

CROSS-LAYER APPROACH • Cross-layer optimization is an escape from the pure waterfall -like concept of the OSI communications model with virtually strict boundaries between layers. • The cross layer approach transports feedback dynamically via the layer boundaries to enable the compensation for e. g. overload, latency or other mismatch of requirements and resources by any control input to another layer but that layer directly affected by the detected deficiency. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 53

SECURITY ASPECTS OF VARIOUS LAYERS IN WMN • various possible attacks on different layers of the communication protocol stack for WMNs and their corresponding defense mechanisms. • First, it identifies the security vulnerabilities in the physical, link, network, transport, application layers. • Furthermore, various possible attacks on the key management protocols, user authentication and access control protocols, and user privacy preservation protocols are presented. • Security schemes for WMNs are still not ready. Due to the distributed nature of WMN, there is no centralized authority that can be fully trusted and can distribute a public key. • Capacity, scalability, and Qo. S are considered as the major weakness of current WMN technology. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 54

APPLICATIONS OF SENSOR NETWORK • • • Area monitoring Health care monitoring Environmental/Earth monitoring Air quality monitoring Air pollution monitoring Forest fire detection Landslide detection Water quality monitoring Natural disaster prevention Industrial monitoring IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 55

APPLICATIONS OF MESH NETWORK • U. S. military forces are now using wireless mesh networking to connect their computers, mainly ruggedized laptops, in field operations. • Electric meters now being deployed on residences transfer their readings from one to another and eventually to the central office for billing without the need for human meter readers or the need to connect the meters with cables. • The laptops in the One Laptop per Child program use wireless mesh networking to enable students to exchange files and get on the Internet even though they lack wired or cell phone or other physical connections in their area. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 56

• Unique Mesh Dynamics Technology Benefits for Mining Applications • A miner location and tracking system based on Wi-Fi • Remote Real Time Video Monitoring of Long wall Shearers. IFETCE/M. E (CSE) /I YEAR/I SEM/ NE 7002/MPC/UNIT-III/PPT/VERSION 1. 1 57