Designing and Implementing a Secure Cloud Environment Design











- Slides: 47

Designing and Implementing a Secure Cloud Environment • • • Design Virtual Network for Cloud Deployment Determine Network Access Requirements Secure Networks for Cloud Interaction Manage Cloud Component Security Implement Security Technologies Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 1

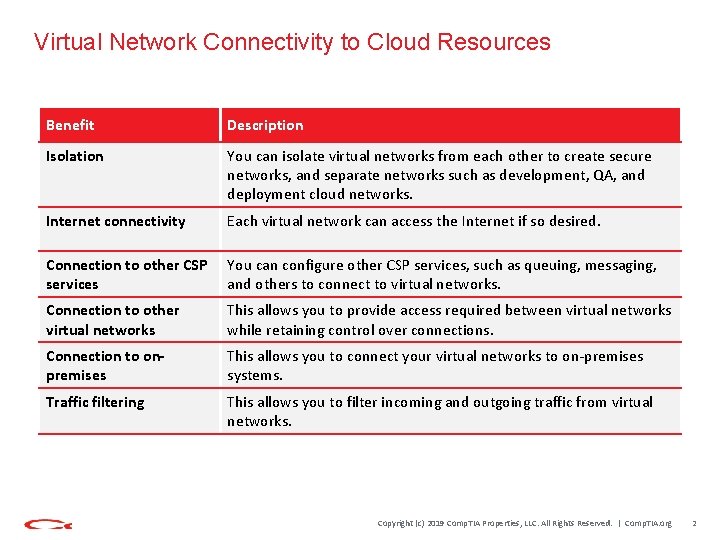
Virtual Network Connectivity to Cloud Resources Benefit Description Isolation You can isolate virtual networks from each other to create secure networks, and separate networks such as development, QA, and deployment cloud networks. Internet connectivity Each virtual network can access the Internet if so desired. Connection to other CSP services You can configure other CSP services, such as queuing, messaging, and others to connect to virtual networks. Connection to other virtual networks This allows you to provide access required between virtual networks while retaining control over connections. Connection to onpremises This allows you to connect your virtual networks to on-premises systems. Traffic filtering This allows you to filter incoming and outgoing traffic from virtual networks. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 2

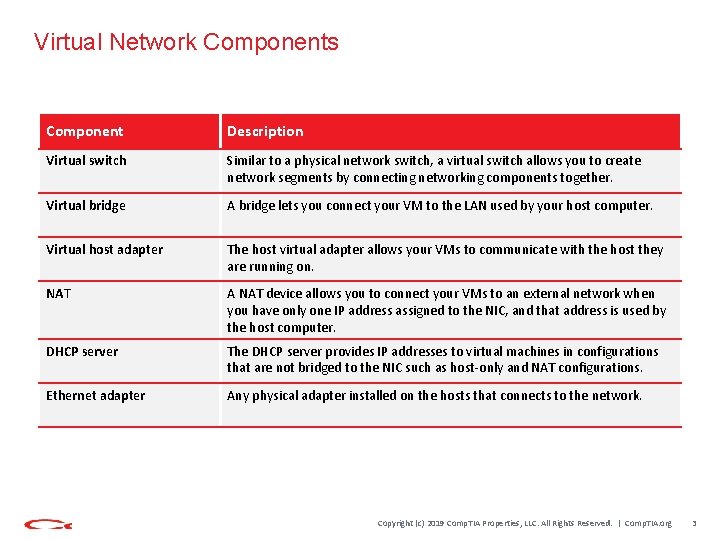
Virtual Network Components Component Description Virtual switch Similar to a physical network switch, a virtual switch allows you to create network segments by connecting networking components together. Virtual bridge A bridge lets you connect your VM to the LAN used by your host computer. Virtual host adapter The host virtual adapter allows your VMs to communicate with the host they are running on. NAT A NAT device allows you to connect your VMs to an external network when you have only one IP address assigned to the NIC, and that address is used by the host computer. DHCP server The DHCP server provides IP addresses to virtual machines in configurations that are not bridged to the NIC such as host-only and NAT configurations. Ethernet adapter Any physical adapter installed on the hosts that connects to the network. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 3

SDN The following key technologies enable SDN: • Functional separation of traffic based on software-defined configuration. • Network virtualization through configuration of routes, protocols, and other networking properties. • Automation through programmability, allowing adaptive routing based on network topology. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 4

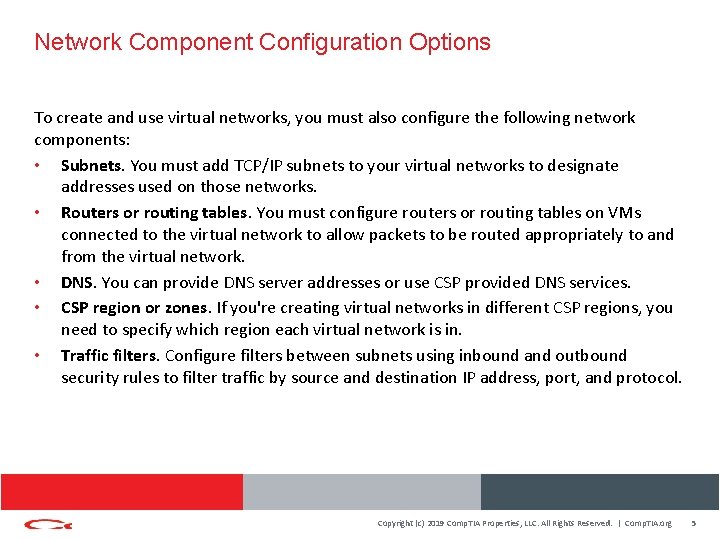
Network Component Configuration Options To create and use virtual networks, you must also configure the following network components: • Subnets. You must add TCP/IP subnets to your virtual networks to designate addresses used on those networks. • Routers or routing tables. You must configure routers or routing tables on VMs connected to the virtual network to allow packets to be routed appropriately to and from the virtual network. • DNS. You can provide DNS server addresses or use CSP provided DNS services. • CSP region or zones. If you're creating virtual networks in different CSP regions, you need to specify which region each virtual network is in. • Traffic filters. Configure filters between subnets using inbound and outbound security rules to filter traffic by source and destination IP address, port, and protocol. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 5

Guidelines for Designing a Virtual Network for Cloud Deployment • • • Compare virtual network services from cloud providers as they may be the only way you can create virtual networks, or may be more functional and much easier to configure and manage than VM-based virtual networks configured on hosted VMs. If planning to filter traffic to virtual networks, add testing steps to your deployment planning to make sure all necessary traffic is getting through. Work with CSP personnel to help configure virtual networks and network components like routing tables, network virtual appliances, and subnets. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 6

Activity: Designing the Virtual Network for Connecting to Cloud Services • • The Executive Steering Committee wants to ensure that all cloud services have the proper networking in place to address estimated future needs. You will create virtual networks to connect any services or devices that need to communicate with each other. In Azure, you don't currently have other services to connect to but you will create a virtual network to learn the process and have it in place for future services. For Google Cloud, you will create a VPN to allow a connection from your on-premises network to the cloud network. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 7

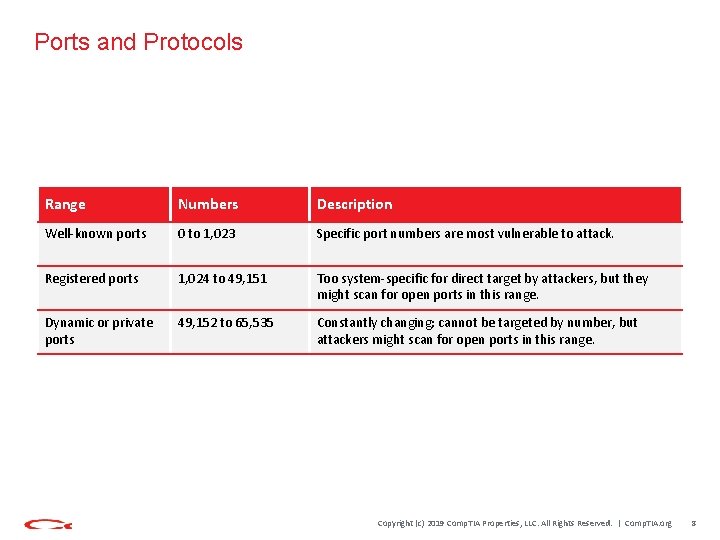
Ports and Protocols Range Numbers Description Well-known ports 0 to 1, 023 Specific port numbers are most vulnerable to attack. Registered ports 1, 024 to 49, 151 Too system-specific for direct target by attackers, but they might scan for open ports in this range. Dynamic or private ports 49, 152 to 65, 535 Constantly changing; cannot be targeted by number, but attackers might scan for open ports in this range. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 8

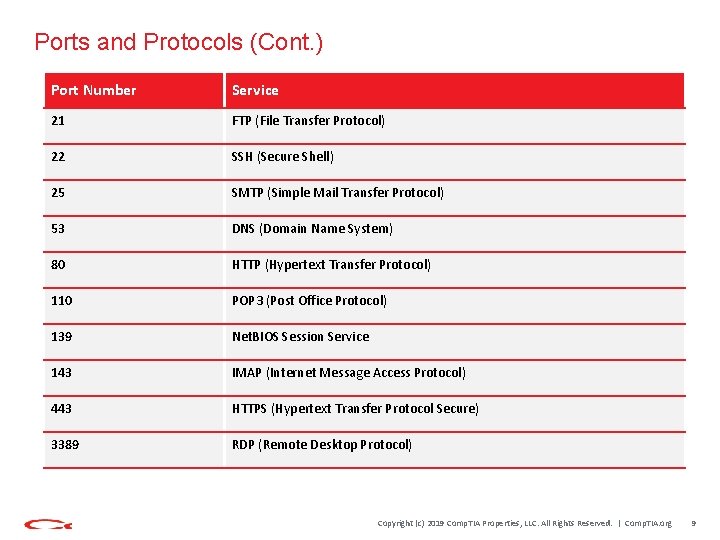
Ports and Protocols (Cont. ) Port Number Service 21 FTP (File Transfer Protocol) 22 SSH (Secure Shell) 25 SMTP (Simple Mail Transfer Protocol) 53 DNS (Domain Name System) 80 HTTP (Hypertext Transfer Protocol) 110 POP 3 (Post Office Protocol) 139 Net. BIOS Session Service 143 IMAP (Internet Message Access Protocol) 443 HTTPS (Hypertext Transfer Protocol Secure) 3389 RDP (Remote Desktop Protocol) Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 9

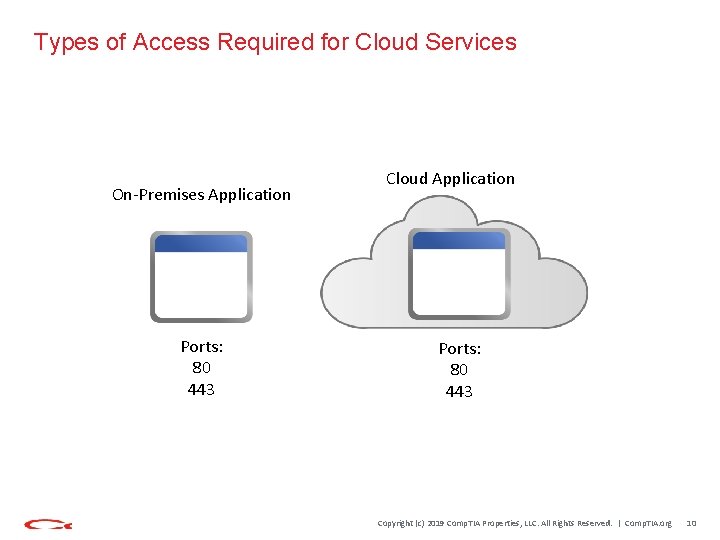
Types of Access Required for Cloud Services On-Premises Application Ports: 80 443 Cloud Application Ports: 80 443 Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 10

Port and Protocol Security When Deploying to Cloud To help you determine which ports and protocols you need to configure access for, and which networks need to pass specific traffic, look for guidance from these sources: • Application and service configuration guides. • CSP security and deployments guides. • Deployment guides from third party sources or consultancies that implement solutions similar to the solutions you're implementing. • Your own documentation, firewall, and routing information. • If you're uncertain what ports and protocols are used by a legacy, on-premises app you'd like to move to the cloud, use tools like a port scanner or protocol analyzer to determine which ports are used. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 11

Guidelines for Determining Network Access Requirements • • Don't assume you know all ports used to access, or used on the back-end of an app or service. Many administrators assume common web ports such as 80 and 443 (HTTP and HTTPS) are used, and may fail to consider ports needed for database access or use by other services. If you're uncertain what ports and protocols are used by a legacy, on-premises app you'd like to move to the cloud, and don't have clear documentation, use tools like a port scanner or protocol analyzer to determine which ports are used. Use CSP and app deployment guides as the basis for designing port and protocol access to services and apps. When creating inbound and outbound rules for network access, be mindful of the direction of traffic flow. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 12

Activity: Securing Ports and Services After Deployment • • • You have been asked to determine if ports for your cloud services are secure while allowing required traffic for their function. You will review what traffic is allowed and denied for both of your cloud platforms and ensure only the required incoming traffic is allowed. Rudison needs to allow access to the cloud data on Azure over HTTP. For your app on Google Cloud, there is a third party API that Rudison uses that is currently locked out. You need to open port 9530 for this API. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 13

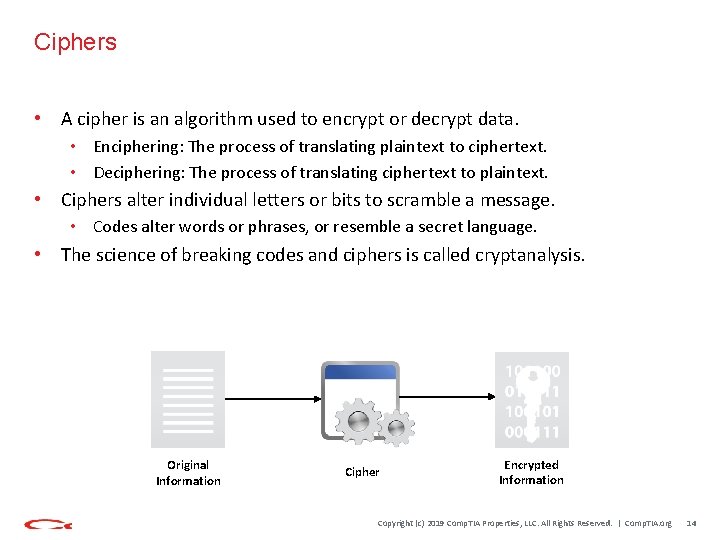
Ciphers • A cipher is an algorithm used to encrypt or decrypt data. • Enciphering: The process of translating plaintext to ciphertext. • Deciphering: The process of translating ciphertext to plaintext. • Ciphers alter individual letters or bits to scramble a message. • Codes alter words or phrases, or resemble a secret language. • The science of breaking codes and ciphers is called cryptanalysis. Original Information Cipher Encrypted Information Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 14

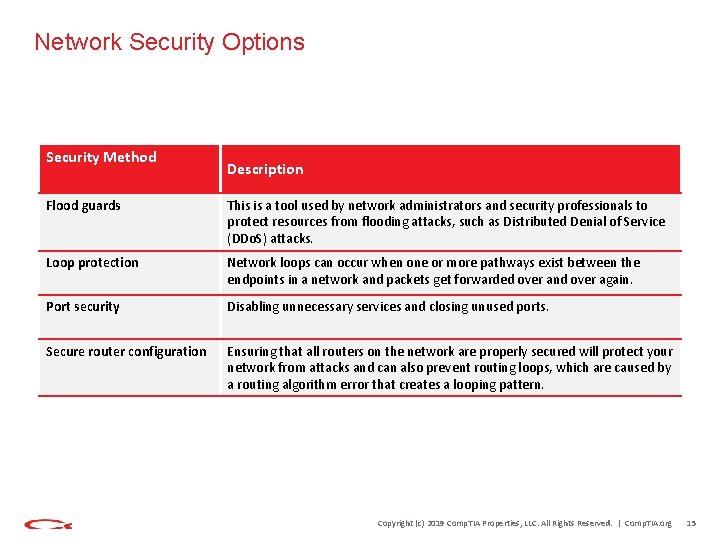
Network Security Options Security Method Description Flood guards This is a tool used by network administrators and security professionals to protect resources from flooding attacks, such as Distributed Denial of Service (DDo. S) attacks. Loop protection Network loops can occur when one or more pathways exist between the endpoints in a network and packets get forwarded over and over again. Port security Disabling unnecessary services and closing unused ports. Secure router configuration Ensuring that all routers on the network are properly secured will protect your network from attacks and can also prevent routing loops, which are caused by a routing algorithm error that creates a looping pattern. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 15

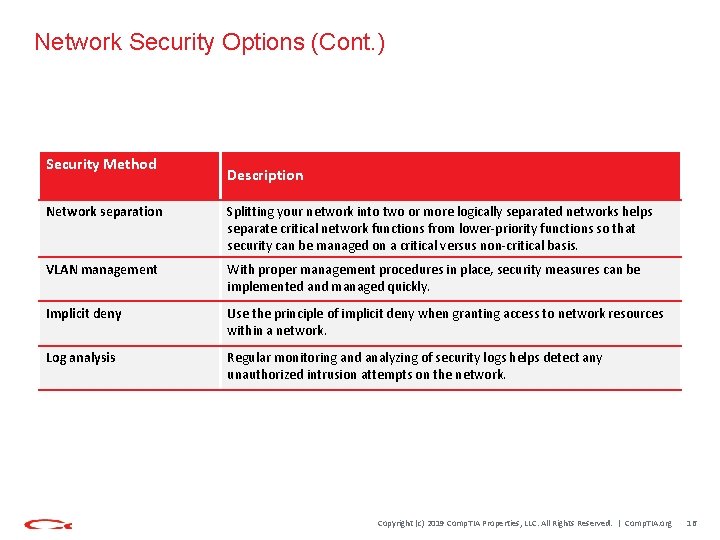
Network Security Options (Cont. ) Security Method Description Network separation Splitting your network into two or more logically separated networks helps separate critical network functions from lower-priority functions so that security can be managed on a critical versus non-critical basis. VLAN management With proper management procedures in place, security measures can be implemented and managed quickly. Implicit deny Use the principle of implicit deny when granting access to network resources within a network. Log analysis Regular monitoring and analyzing of security logs helps detect any unauthorized intrusion attempts on the network. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 16

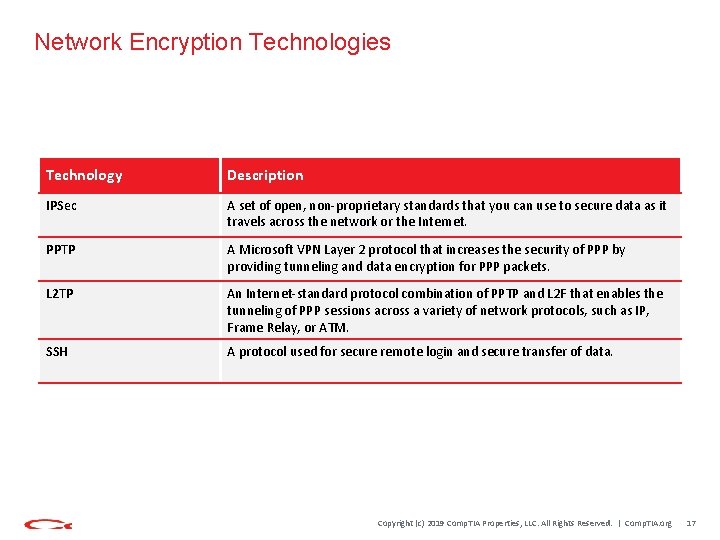
Network Encryption Technologies Technology Description IPSec A set of open, non-proprietary standards that you can use to secure data as it travels across the network or the Internet. PPTP A Microsoft VPN Layer 2 protocol that increases the security of PPP by providing tunneling and data encryption for PPP packets. L 2 TP An Internet-standard protocol combination of PPTP and L 2 F that enables the tunneling of PPP sessions across a variety of network protocols, such as IP, Frame Relay, or ATM. SSH A protocol used for secure remote login and secure transfer of data. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 17

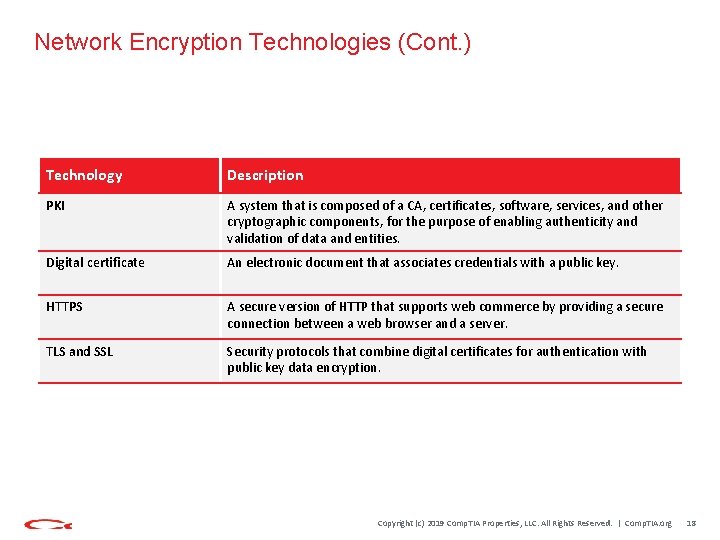
Network Encryption Technologies (Cont. ) Technology Description PKI A system that is composed of a CA, certificates, software, services, and other cryptographic components, for the purpose of enabling authenticity and validation of data and entities. Digital certificate An electronic document that associates credentials with a public key. HTTPS A secure version of HTTP that supports web commerce by providing a secure connection between a web browser and a server. TLS and SSL Security protocols that combine digital certificates for authentication with public key data encryption. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 18

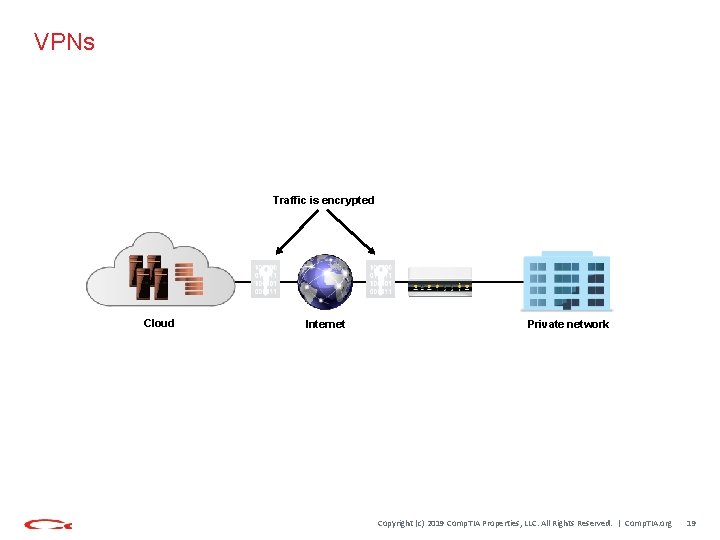
VPNs Traffic is encrypted Cloud Internet Private network Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 19

Network Segmentation and Security Some common network segmentation implementations related to cloud deployments include the following: • De-Militarized Zone (DMZ) • Virtual Extensible LAN (VXLan) • Segmentation • Micro-Segmentation Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 20

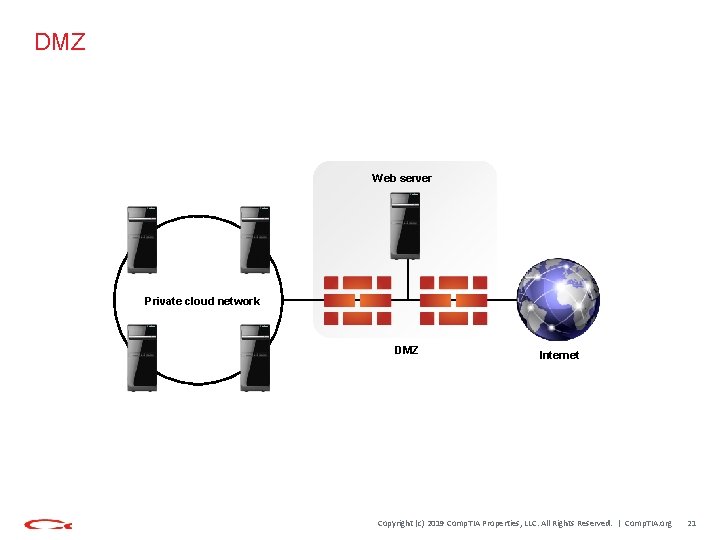
DMZ Web server Private cloud network DMZ Internet Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 21

VXLAN • • VLAN specifications only allow for 4, 096 network IDs to be assigned at any given time, which might not be enough addresses for a large cloud computing environment. The goal of VXLAN is to extend the VLAN address space to support 16 million IDs. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 22

Segmentation Options The first type of segmentation allows isolation of different types of network traffic. The following three types of network traffic should be segmented: • Management traffic. Most enterprise virtualization platforms provide a special virtual network connection for management traffic, such as VMWare's service console traffic that is used to connect hypervisor platforms to management tools such as VWWare v. Center. • Operations traffic. This traffic is associated with dynamic memory migration and storage operations. • Virtual machine production traffic. This is the traffic to and from VMs generated by the services and apps running on those VMs and the requests and responses from the client. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 23

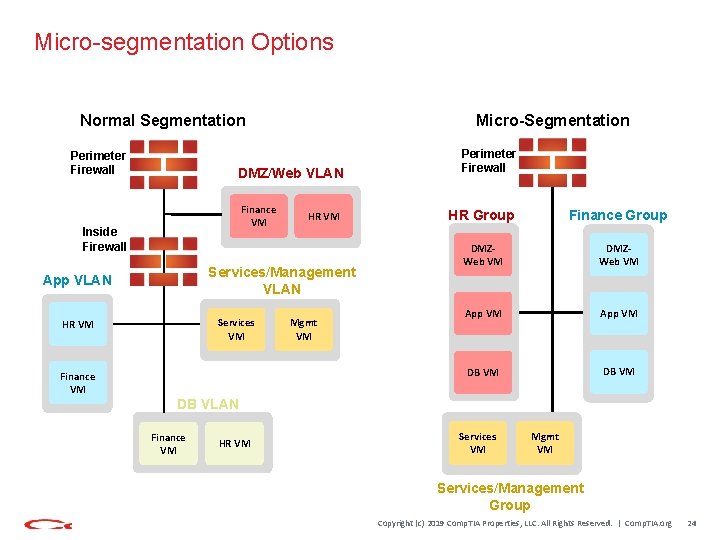
Micro-segmentation Options Normal Segmentation Perimeter Firewall Micro-Segmentation DMZ/Web VLAN Finance VM Inside Firewall HR VM Services/Management VLAN App VLAN Services VM HR VM Finance VM Mgmt VM Perimeter Firewall HR Group Finance Group DMZWeb VM App VM DB VLAN Finance VM HR VM Services VM Mgmt VM Services/Management Group Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 24

Guidelines for Securing Deployments with Segmentation • • • Use virtual DMZs to isolate publicly accessible cloud resources from those that aren't. Provide some form of network security and encryption to protect data in transit from corporate data sources, corporate cloud sources, and corporate users. Consider micro-segmentation to provide granular security for your in-cloud deployment for persistent protection. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 25

Activity: Creating a Secure Network Design with Segmentation • • • Rudison has another app they would like to add to the cloud. It has a front end for the user interface and a database that would be on the back end. You have been asked to create a segmented network that has a subnet for resources that are accessed publicly and another subnet for resources that are strictly private. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 26

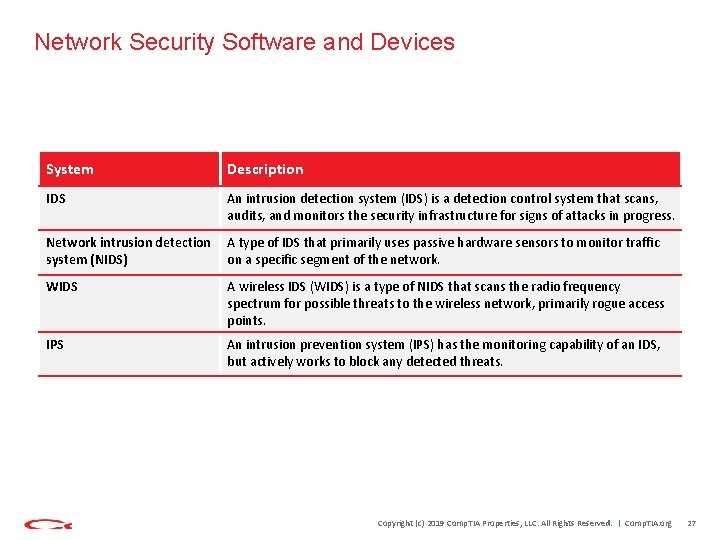
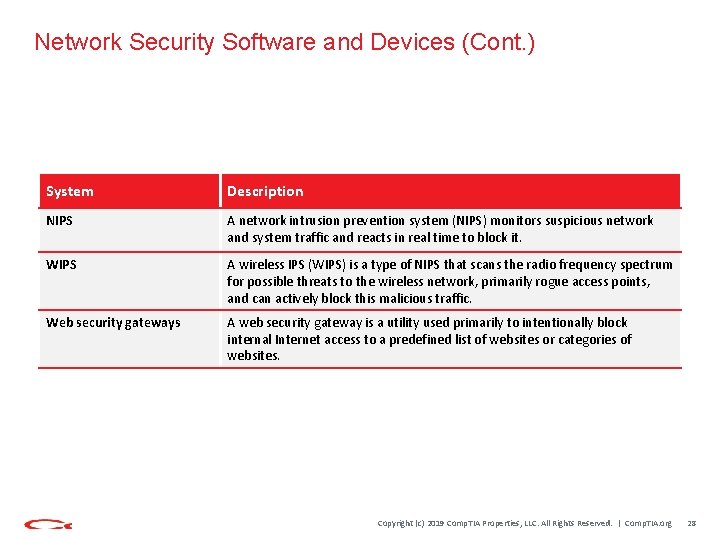
Network Security Software and Devices System Description IDS An intrusion detection system (IDS) is a detection control system that scans, audits, and monitors the security infrastructure for signs of attacks in progress. Network intrusion detection system (NIDS) A type of IDS that primarily uses passive hardware sensors to monitor traffic on a specific segment of the network. WIDS A wireless IDS (WIDS) is a type of NIDS that scans the radio frequency spectrum for possible threats to the wireless network, primarily rogue access points. IPS An intrusion prevention system (IPS) has the monitoring capability of an IDS, but actively works to block any detected threats. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 27

Network Security Software and Devices (Cont. ) System Description NIPS A network intrusion prevention system (NIPS) monitors suspicious network and system traffic and reacts in real time to block it. WIPS A wireless IPS (WIPS) is a type of NIPS that scans the radio frequency spectrum for possible threats to the wireless network, primarily rogue access points, and can actively block this malicious traffic. Web security gateways A web security gateway is a utility used primarily to intentionally block internal Internet access to a predefined list of websites or categories of websites. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 28

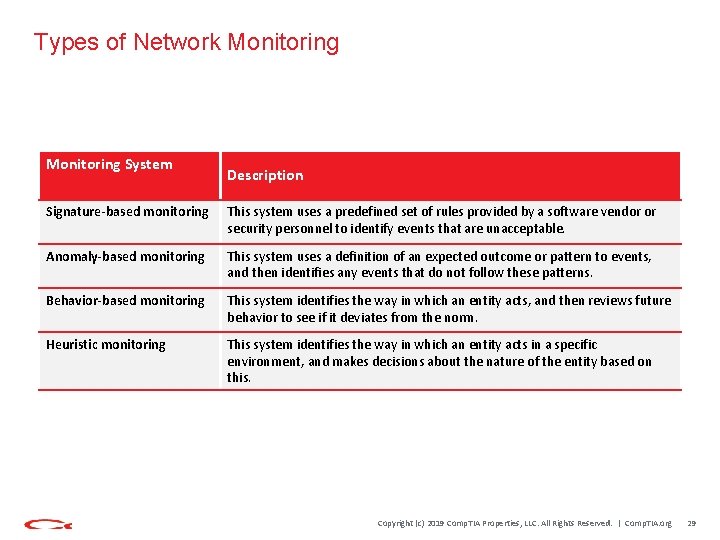
Types of Network Monitoring System Description Signature-based monitoring This system uses a predefined set of rules provided by a software vendor or security personnel to identify events that are unacceptable. Anomaly-based monitoring This system uses a definition of an expected outcome or pattern to events, and then identifies any events that do not follow these patterns. Behavior-based monitoring This system identifies the way in which an entity acts, and then reviews future behavior to see if it deviates from the norm. Heuristic monitoring This system identifies the way in which an entity acts in a specific environment, and makes decisions about the nature of the entity based on this. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 29

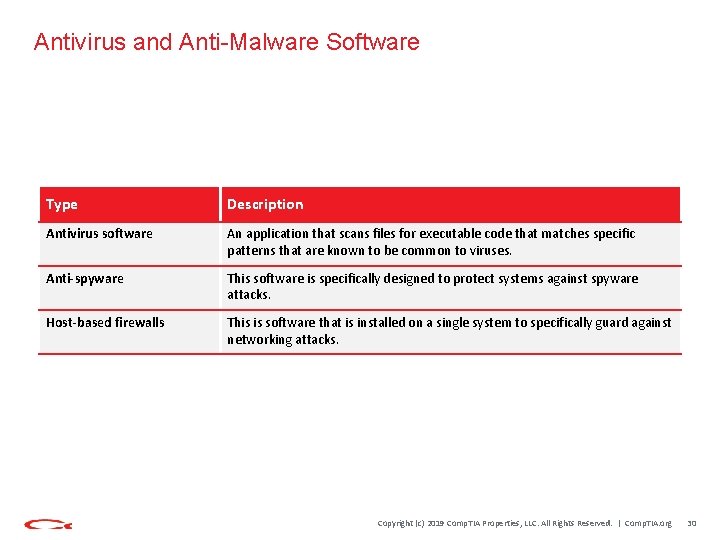
Antivirus and Anti-Malware Software Type Description Antivirus software An application that scans files for executable code that matches specific patterns that are known to be common to viruses. Anti-spyware This software is specifically designed to protect systems against spyware attacks. Host-based firewalls This is software that is installed on a single system to specifically guard against networking attacks. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 30

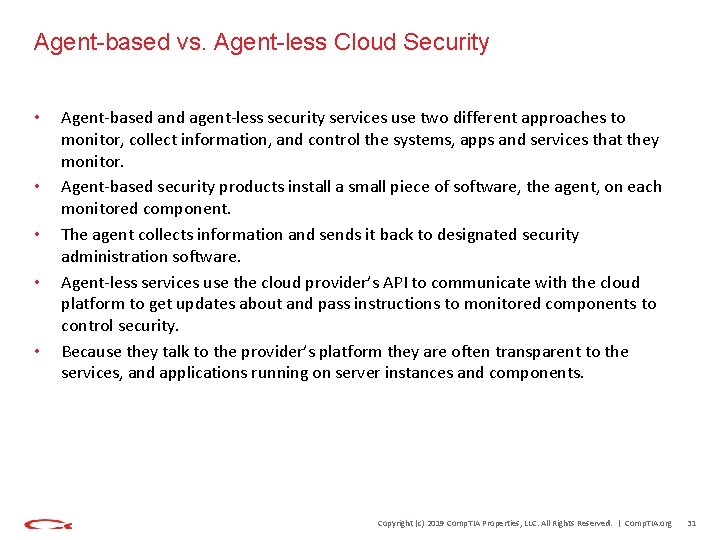
Agent-based vs. Agent-less Cloud Security • • • Agent-based and agent-less security services use two different approaches to monitor, collect information, and control the systems, apps and services that they monitor. Agent-based security products install a small piece of software, the agent, on each monitored component. The agent collects information and sends it back to designated security administration software. Agent-less services use the cloud provider’s API to communicate with the cloud platform to get updates about and pass instructions to monitored components to control security. Because they talk to the provider’s platform they are often transparent to the services, and applications running on server instances and components. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 31

Pros and Cons of Agent-based vs. Agent-less Cloud Security Some experts endorse agent-based monitoring for several reasons, including: • Agents can connect more deeply into components to gather more data, and perform more complex configuration. • Agents don't require a lot of network bandwidth. • Agents can be custom designed for systems and components to collect specific data or perform specific configuration tasks, where agent-less systems tend to collect the same high-level data about all the systems and components they monitor. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 32

Pros and Cons of Agent-based vs. Agent-less Cloud Security (Cont. ) Some experts endorse agentless-based monitoring for several reasons, including: • Overhead of installation and maintenance since agents must be installed on every cloud instance, and maintained so that they stay up-to-date. • Some cloud environments don't allow agent installation on many or all of their services. • Many agent-based solutions may not be aware of some cloud-native services such as CSP-provided load-balancing or databases, so you may not be able to model these services in security policies, forcing the use of overly permissive configurations. • Third parties that offer security management across multiple cloud providers use the APIs of each provider, essentially leveraging agent-less security management that provides visibility and control in a multi-cloud environment. • There is a very small processor utilization “tax” using agents. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 33

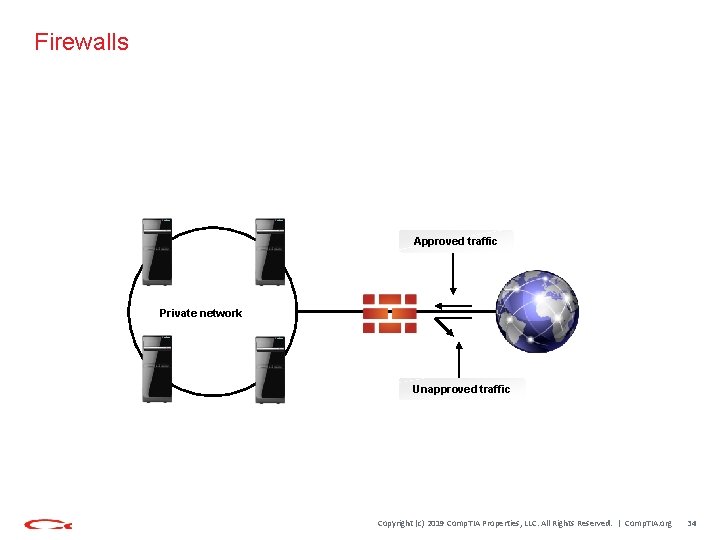
Firewalls Approved traffic Private network Unapproved traffic Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 34

SLA Security Considerations Security SLAs and provisions often address three common areas of risk: • Ownership. Agreements need to address who owns digital assets, including data, especially who maintains custody and control of data, and how data will be controlled. • Availability of services. These provisions include details about monitoring and response times. • Baseline Services. These are often regulatory, or common practice guarantees, such as performing intrusion detection monitoring or firewalling cloud network access as part of security due diligence. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 35

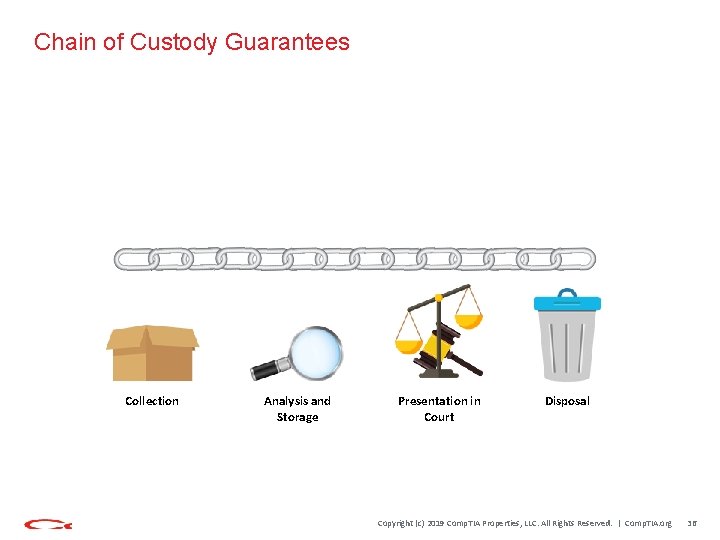
Chain of Custody Guarantees Collection Analysis and Storage Presentation in Court Disposal Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 36

Patches and Maintenance for Network Security You can do the following to help facilitate patching and maintenance in your organization: • Take a detailed inventory and keep it up to date. • Standardize systems as much as possible. • Make a list and map of security software and devices in place. • Put in place a reliable system for collecting vulnerability alerts. • When alerts come out, compare them to inventory to quickly identify systems that may be impacted. • Assess the risk based on the alert, the degree to which the solution is mission critical, security apparatus already in place, and so forth. • Create a priority system for quickly deploying patches to affected systems. • Update all affected documentation. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 37

Managed Cloud Services Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 38

Guidelines for Securing Networks for Cloud Interaction • • • Work with CSPs during on-boarding to learn their security and response processes and to learn their recommendations for their clients. Since CSP resources, staff, and response procedures will effectively become part of your security and response process, review and update your security and response processes to incorporate CSP notifications, responsibilities, escalations, and timelines. Consider the tradeoffs in agent versus agent-less security options and evaluate the benefits of software for those solutions. Consider agent-less security management for cloud environments or agent-based solutions that are specifically designed for cloud environments. Review CSP SLAs per recommendations in this topic. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 39

Activity: Securing Networks for Cloud Interaction • • So far you have implemented some security features to help make the Rudison cloud environment more secure. There may be some issues you have missed or are unaware of. You want to verify the security of your cloud environment. You will use the Azure Security Center to see what security issues may exist and how to address them. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 40

Impact of Security Tools on Systems and Services The need for security is not lost on business and organizations. Still, the impact of this need is far reaching and includes: • The need for security software of all types to manage, monitor, and secure systems. • The need to hire skilled security staff. • The need to obtain continuing education of skilled security staff. • The need to invest in automation and Dev. Ops practices to automate patching and other security processes. • The need to invest in software, training, or consulting to federate identity management to allow single sign-on and tight access controls across diverse multicloud and hybrid cloud environments. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 41

Microsoft Azure Security Features Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 42

Google Cloud Platform Security Features Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 43

Guidelines for Implementing Security Technologies • • Consider the impact use of security technologies will have on use of systems and apps. While the CSP will manage patching for the host OS, you are responsible for patching and verifying the security configuration of the VMs and containers you use. Consider ways to use automation and orchestration to automate updates so that patching and security update roll-outs can be done quickly and efficiently. Review any security tools provided by your CSP to see what capabilities they provide that you can leverage to secure, manage, and monitor your network. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 44

Activity: Implementing Security Technologies • • • The Executive Steering Committee wants you to ensure that the cloud services have sufficient security for accessing the services. For access to your data in Azure, you implement multi-factor authentication. For Google Cloud, you will create your own server-side encryption keys that can be used to encrypt or decrypt data when users connect to the cloud. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 45

Activity: Implementing Orchestration • Rudison wants you to orchestrate the provisioning of user accounts. • • New accounts should have the appropriate access based on the user's role to both Google Cloud and Azure. The new account should also exist in the on-premises network. Users should be able to connect to each network or service with a minimum number of steps on the users’ part. Rudison is finishing development on a new application. • • • With the release date coming up, there is a big push to finish development on time. This has added a high load to the test environment and new VM instances are being added to increase performance. You need to orchestrate the provisioning of the new VM instances to reduce the amount of time and effort it takes to get the developers and testers the performance they need. Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 46

Reflective Questions 1. What types of virtual or physical network layouts does your organization use to secure communications and isolate mission critical apps and services? 2. What types of network monitoring are in use in your organization, and which have you interacted with the most? Copyright (c) 2019 Comp. TIA Properties, LLC. All Rights Reserved. | Comp. TIA. org 47