FACILITY SAFETY Creating a Safe and Secure Environment



























- Slides: 30

FACILITY SAFETY: Creating a Safe and Secure Environment in the Community Health Center Presented by Steve Wilder, BA, CHSP, STS Sorensen, Wilder & Associates Bourbonnais, Illinois

The Complete Security Program (P 2 T 2®) PEOPLE PROGRAMS TRAINING TECHNOLOGY

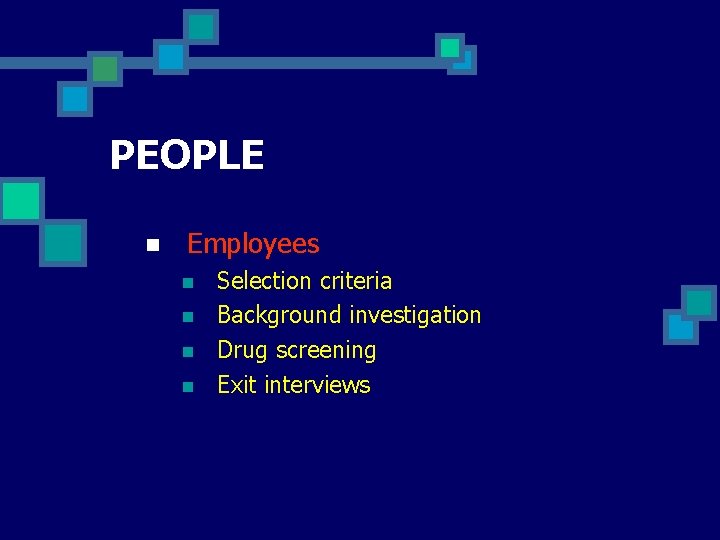
PEOPLE n Employees n n Selection criteria Background investigation Drug screening Exit interviews

PEOPLE n Visitors n n Backgrounds Supervision Criminal history Legitimacy of visit

PROGRAMS n Focuses on developing and implementing the right security programs n n Policy and Procedure Development n Is there a policy and procedure plan accessible to all employees? Staffing and Organization n How do you determine the number of security staff? n Do you have a minimum staffing plan for each shift? n What is the organization of the department?

PROGRAMS (cont’d) Emergency Preparedness Do you have a procedure workplace violence? Do you have a procedure Do you have a procedure in place in the event of a bomb threat? in place in the event of domestic or in in in place place in the event of a civil disturbance? in the event of a fire? in the event of a hostage situation? for inclement weather? for a hazardous materials incident? in the event of terrorist activity?

TRAINING n Focuses on security knowledge of staff n Physical protection of people and property n n n Security staff Non-security staff Training on personal safety and protection Security awareness training Proprietary vs. contractual security services n Performance based contracts

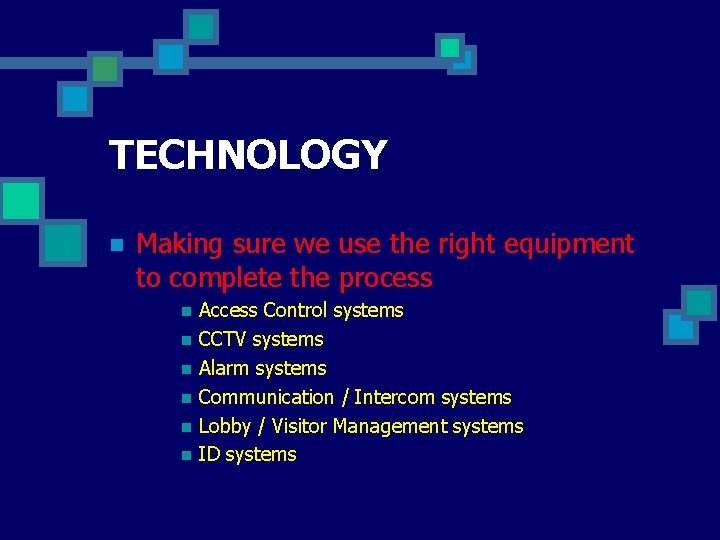
TECHNOLOGY n Making sure we use the right equipment to complete the process n n n Access Control systems CCTV systems Alarm systems Communication / Intercom systems Lobby / Visitor Management systems ID systems

Key Elements to Successful Security Program: n n n A Comprehensive Vulnerability Assessment A Written Security Plan Implementation Exercises and Evaluations Ongoing Updates and Revisions

Part I The Security Vulnerability Assessment (SVA)

The SVA n n n Conducted annually, at minimum Conducted by a competent healthcare security professional Assesses risks inherent to the community health center environment

Purpose of an SVA n Identification of Credible Threats n n Identification of Critical Assets n n Who and what should the community health center be protecting Identification and Consequences n n From what and whom should the community health center be protecting itself against Likely consequences of identified vulnerabilities Provision of Sound and Viable Security Recommendations n Systematic improvements and or upgrades in P 2 T 2®

Elements of the SVA A security vulnerability assessment includes a comprehensive review in key areas: n n Human Resources Employee Identification Systems / Practices Student Identification Visitor / Vendor Identification

Elements of the Assessment A security vulnerability assessment includes a comprehensive review in 12 key areas : • Access Control • CCTV / Monitoring Systems • Duress Alarm Systems • Parking Control • Exterior Lighting • Interior Lighting • • • Training Structural Safeguards Cash Handling Staff Interviews Written Security Management Programs • Physical Plant and Grounds

Elements of the Assessment A security vulnerability assessment also includes a comprehensive review of: n n n Exterior Lighting Interior Lighting Structural Safeguards

Part II The Written Security Plan

Define the Purpose n The purpose of the written plan should be to: n n n First, protect the staff, clients and visitors Second, protect property Third, provide services

Objectives of the Plan n n n Assign responsibility for the plan Provide orientation to all new employees, clients, and families Develop a system for reporting security incidents and emergencies Establish security performance standards Determine areas that are particularly vulnerable Evaluate the plan effectiveness annually

Assigning Responsibility n n n Who is responsible for implementing security? What are his/her qualifications? Who does s/he report to? What gets reported? How often? What follow up action is needed?

Even if this is a good depiction of your security guard, this does NOT represent a good site security plan…. . .

Providing Orientation to Staff n n n Overview of the security plan and purpose The mission of the community health center How to minimize security risks What emergency procedures to take during an incident How to report security incidents n n Emergency Codes Emergency Numbers What should be reported Key security services: n Escorts

Reporting System n Establish a system to: n n Collect pertinent security information Evaluate the information n n Every incident Aggregate data Establish goals to reduce or eliminate security hazards Monitor the ongoing effectiveness of goals Provide annual evaluation of security plan effectiveness

Performance Standards n Standards should be developed to: n n n Test staff knowledge, skill and participation in security program Monitor security inspection activities Evaluate security incident reporting

Vulnerable Areas n Conduct annual security assessment to determine: n n n Potential for harm to staff, clients, families, and visitors Potential for theft or damage to assets Frequency of security incidents

Annual Assessment of Security n n Evaluate the effectiveness of the security plan Determine goals for the next year Develop measurable performance standards List performance indicators

Part III Implementing the Security Plan

Develop Your Team n Form a multi-disciplinary task force to: Create a purpose statement n Design the elements of your security plan n Conduct and review the security assessment (Careful consideration should be given for the use of an outside security consultant for the 1 st assessment) n

Using The Threat Assessment n Upon completion of the assessment, categorize the vulnerabilities: n n n High Risk / High Cost to Correct High Risk / Low Cost to Correct Low Risk / High Cost to Correct Low Risk / Low Cost to Correct Report high risk, high cost recommendations to safety committee and Board of Directors / Senior Management for consideration and support

Quality Process Additionally: n n Develop and implement a quality process to reduce or eliminate security incidents Determine indicators based on past history, assessment data, etc. Measure and report your results regularly Evaluate the effectiveness at least annually

Questions & Thoughts… Steven S. Wilder Sorensen, Wilder & Associates Bourbonnais, IL swilder@swa 4 safety. com 800 -568 -2931