Deploying DNSSEC without Losing Your Mind Summer ESNET







- Slides: 31

Deploying DNSSEC without Losing Your Mind Summer ESNET Conference July 2009

DNS Infrastructure Challenges Web 2. 0 Hidden Computing More Devices Performance Demands DNS Security Demands Botnets Malware Cache Poisoning Conventional DNS solutions can’t keep up with today’s performance and security demands 2

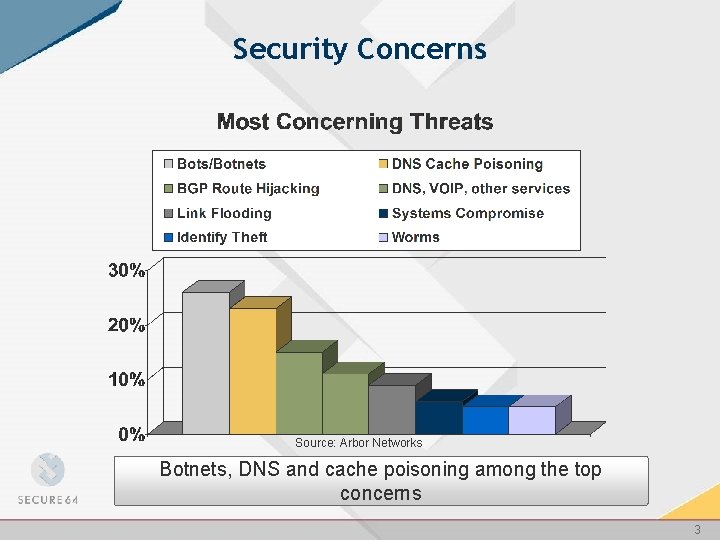
Security Concerns Source: Arbor Networks Botnets, DNS and cache poisoning among the top concerns 3

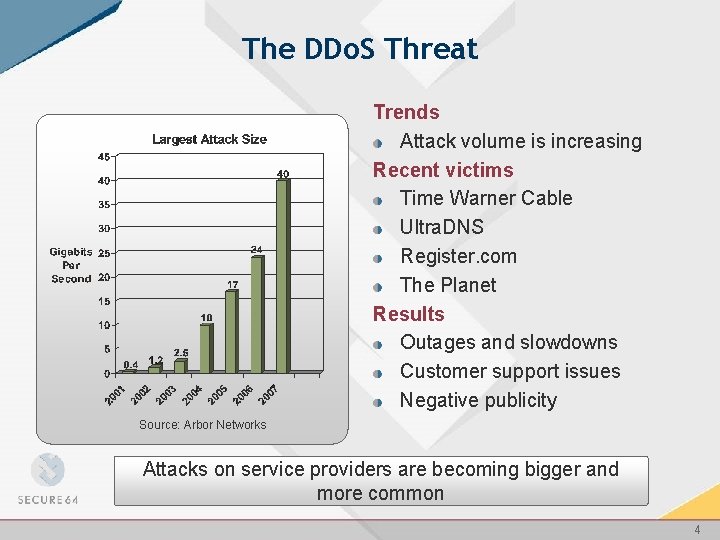
The DDo. S Threat Trends Attack volume is increasing Recent victims Time Warner Cable Ultra. DNS Register. com The Planet Results Outages and slowdowns Customer support issues Negative publicity Source: Arbor Networks Attacks on service providers are becoming bigger and more common 4

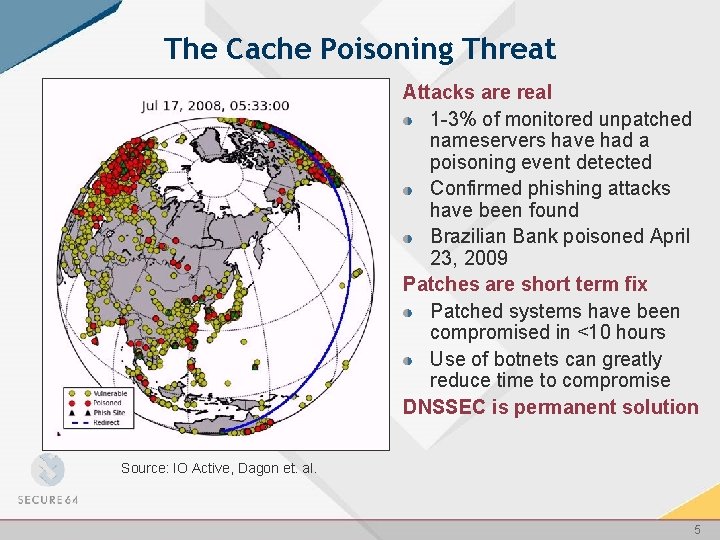
The Cache Poisoning Threat Attacks are real 1 -3% of monitored unpatched nameservers have had a poisoning event detected Confirmed phishing attacks have been found Brazilian Bank poisoned April 23, 2009 Patches are short term fix Patched systems have been compromised in <10 hours Use of botnets can greatly reduce time to compromise DNSSEC is permanent solution Source: IO Active, Dagon et. al. 5

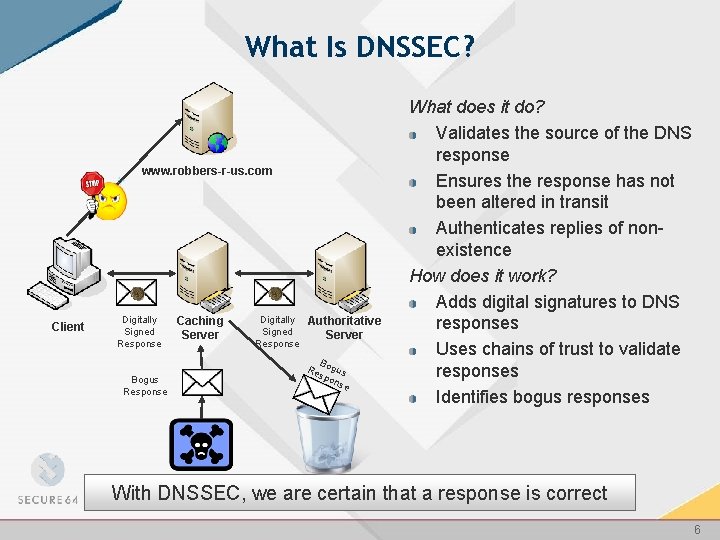
What Is DNSSEC? www. robbers-r-us. com Client Digitally Signed Response Bogus Response Caching Server Digitally Signed Response Authoritative Server B Re ogus spo nse What does it do? Validates the source of the DNS response Ensures the response has not been altered in transit Authenticates replies of nonexistence How does it work? Adds digital signatures to DNS responses Uses chains of trust to validate responses Identifies bogus responses With DNSSEC, we are certain that a response is correct 6

Why You Must Act Now Because you have to … OMB mandate M-08 -23 requires all agencies to sign all external zones (low, medium and high impact) by December 2009 Publication of NIST SP 800 -53 rev 3 specifies deployment of DNSSEC with internal zones (low, medium and high impact) FISMA requires compliance 1 year from 800 -53 publication date, which is June 2010 Because you should … Real attacks have escalated. The Kaminsky exploit alone has captured the attention of the entire planet. Your user base is at risk right now with any web, email, or other Internet transaction http: //www. whitehouse. gov/omb/memoranda/fy 2008/m 08 -23. pdf 7

DNSSEC Deployment Challenges Complexity Education, development, QA required Security General purpose OS cannot protect keys Crypto cards are complicated Offline keys labor intensive Failover How to handle a hardware or network failure? Scalability Signing speed for large or numerous zones Offline key management Dynamic Updates to DNS zone data Auditability What zones are signed? What keys are about to expire? Early adopters invest 4 -6+ man-months to deploy, ½ full time person to maintain 8

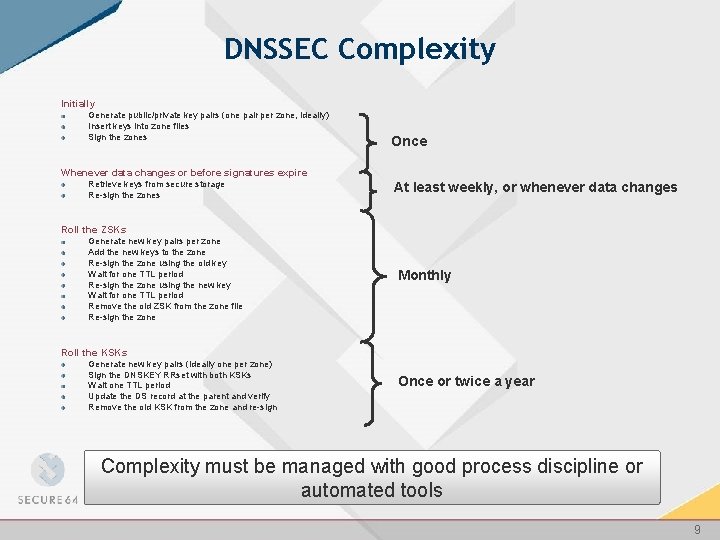
DNSSEC Complexity Initially Generate public/private key pairs (one pair per zone, ideally) Insert keys into zone files Sign the zones Once Whenever data changes or before signatures expire Retrieve keys from secure storage Re-sign the zones At least weekly, or whenever data changes Roll the ZSKs Generate new key pairs per zone Add the new keys to the zone Re-sign the zone using the old key Wait for one TTL period Re-sign the zone using the new key Wait for one TTL period Remove the old ZSK from the zone file Re-sign the zone Monthly Roll the KSKs Generate new key pairs (ideally one per zone) Sign the DNSKEY RRset with both KSKs Wait one TTL period Update the DS record at the parent and verify Remove the old KSK from the zone and re-sign Once or twice a year Complexity must be managed with good process discipline or automated tools 9

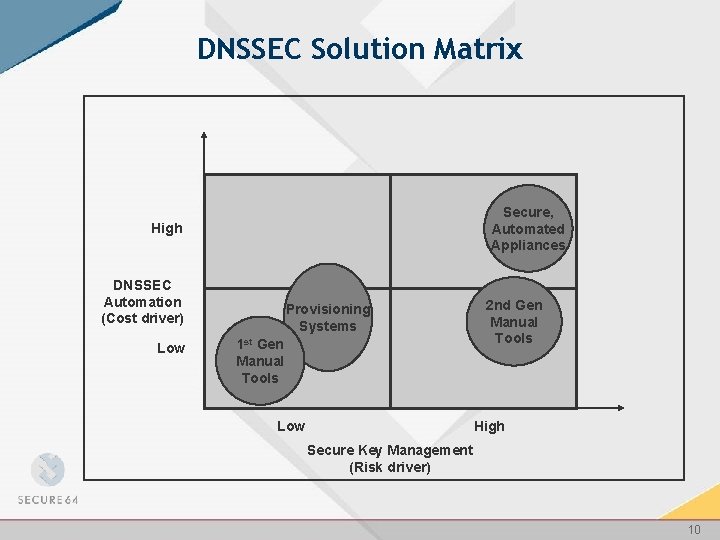
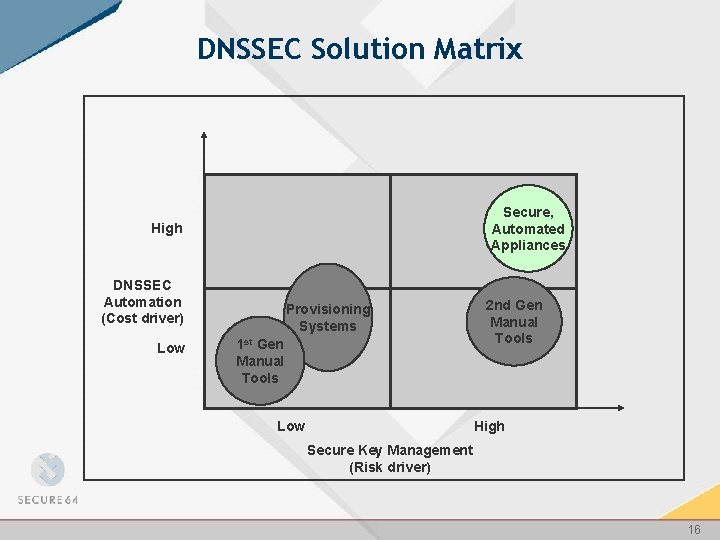
DNSSEC Solution Matrix Secure, Automated Appliances High DNSSEC Automation (Cost driver) Low Provisioning Systems 1 st Gen Manual Tools Low 2 nd Gen Manual Tools High Secure Key Management (Risk driver) 10

Do-It-Yourself Method BIND programs DNSSEC-Keygen & DNSSEC-Signzone Visit www. nlnetlabs. nl LDNS library Ø Ø Examples include a zone-walker (follows NSEC records) and DNSSEC validation tools to check signatures, etc. Also contain programs to manually sign zones and generate keys (alternative to BIND tools) DRILL (an interesting version of DIG) Visit www. dnssec-tools. org Tools and programs from SPARTA labs created with DHS funding assistance to validate, error-check, sign zones, rollkeys Key signer and roller Donuts (LINT-like error checking tool) Validation tools to check signatures, etc. 11

Manual DNSSEC Deployment Steps Generate keys and Insert them into zone files Sign and publish the zones generate NSECs generate RRSIGs Do process over and over again when data changes or when keys need to be replaced OK for small deployments, but begs for automation 12

What could go wrong…will go w. Rorn. G Wrong keys Expired Keys Stolen Keys Lose the Recipe Solution doesn’t scale 13

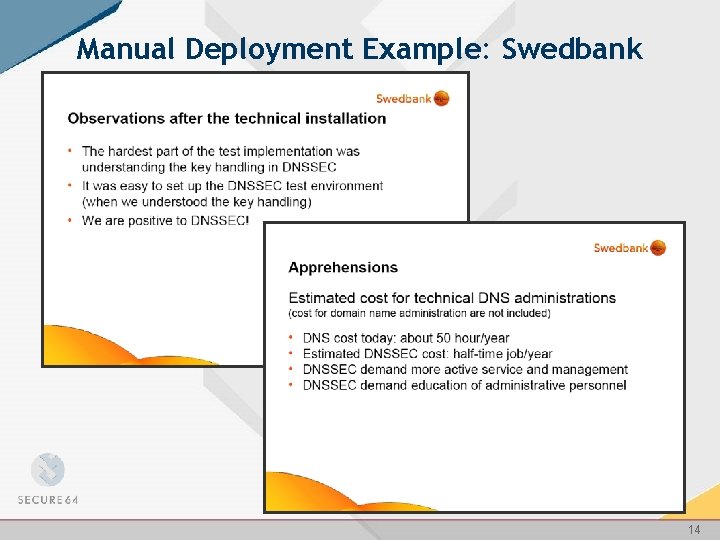
Manual Deployment Example: Swedbank 14

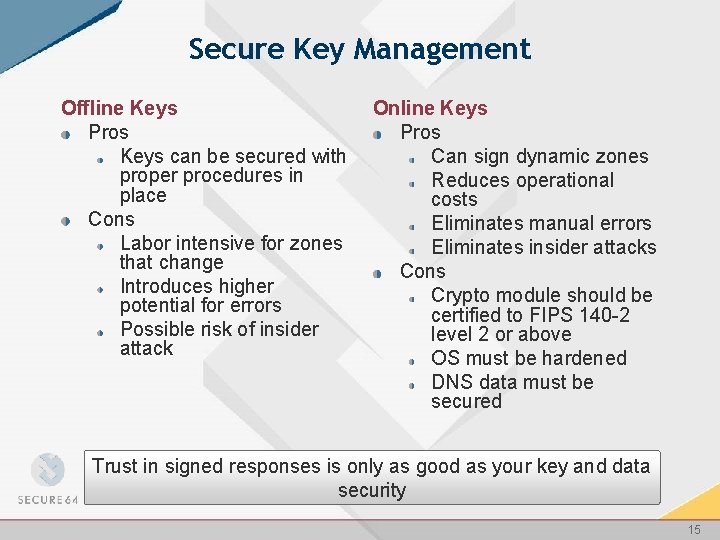
Secure Key Management Offline Keys Pros Keys can be secured with proper procedures in place Cons Labor intensive for zones that change Introduces higher potential for errors Possible risk of insider attack Online Keys Pros Can sign dynamic zones Reduces operational costs Eliminates manual errors Eliminates insider attacks Cons Crypto module should be certified to FIPS 140 -2 level 2 or above OS must be hardened DNS data must be secured Trust in signed responses is only as good as your key and data security 15

DNSSEC Solution Matrix Secure, Automated Appliances High DNSSEC Automation (Cost driver) Low Provisioning Systems 1 st Gen Manual Tools Low 2 nd Gen Manual Tools High Secure Key Management (Risk driver) 16

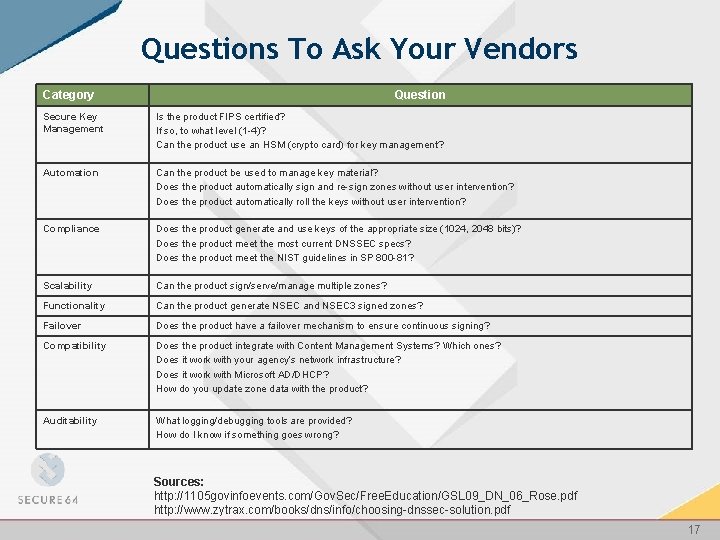
Questions To Ask Your Vendors Category Question Secure Key Management Is the product FIPS certified? If so, to what level (1 -4)? Can the product use an HSM (crypto card) for key management? Automation Can the product be used to manage key material? Does the product automatically sign and re-sign zones without user intervention? Does the product automatically roll the keys without user intervention? Compliance Does the product generate and use keys of the appropriate size (1024, 2048 bits)? Does the product meet the most current DNSSEC specs? Does the product meet the NIST guidelines in SP 800 -81? Scalability Can the product sign/serve/manage multiple zones? Functionality Can the product generate NSEC and NSEC 3 signed zones? Failover Does the product have a failover mechanism to ensure continuous signing? Compatibility Does the product integrate with Content Management Systems? Which ones? Does it work with your agency’s network infrastructure? Does it work with Microsoft AD/DHCP? How do you update zone data with the product? Auditability What logging/debugging tools are provided? How do I know if something goes wrong? Sources: http: //1105 govinfoevents. com/Gov. Sec/Free. Education/GSL 09_DN_06_Rose. pdf http: //www. zytrax. com/books/dns/info/choosing-dnssec-solution. pdf 17

Secure 64 Software Corporation Privately funded, Colorado-based corporation, founded in 2002 Focused on making the DNS trustworthy and secure Secure 64 products: ‘DNS Authority’ & ‘DNS Signer’ Partially funded by the US Department of Homeland Security 18

Automation: the Secure 64 DNS Signer Simple Deployment Automated key management, rollover, signing, re-signing Secure Key Repository Malware-immune OS FIPS 140 -2 compliant (pending) Scalable High performance signing algorithms Incremental zone signing Secure 64 DNS Signer makes it easy to deploy DNSSEC correctly and securely 19

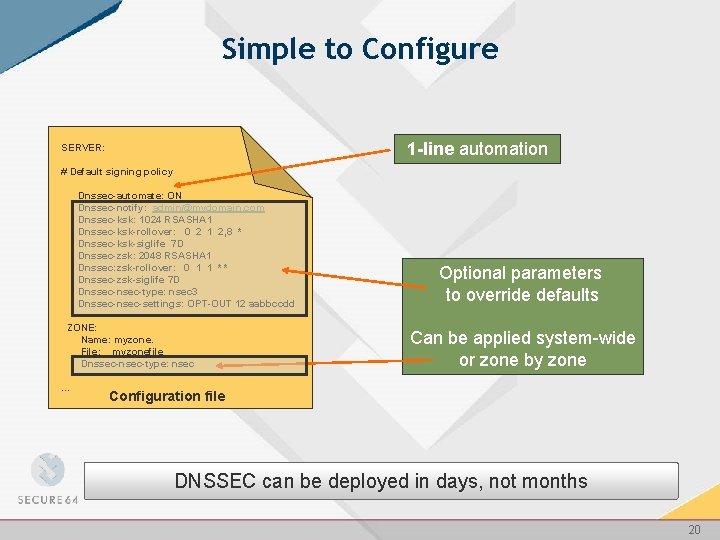
Simple to Configure 1 -line automation SERVER: # Default signing policy Dnssec-automate: ON Dnssec-notify: admin@mydomain. com Dnssec-ksk: 1024 RSASHA 1 Dnssec-ksk-rollover: 0 2 1 2, 8 * Dnssec-ksk-siglife 7 D Dnssec-zsk: 2048 RSASHA 1 Dnssec: zsk-rollover: 0 1 1 * * Dnssec-zsk-siglife 7 D Dnssec-nsec-type: nsec 3 Dnssec-nsec-settings: OPT-OUT 12 aabbccdd ZONE: Name: myzone. File: myzonefile Dnssec-nsec-type: nsec … Optional parameters to override defaults Can be applied system-wide or zone by zone Configuration file DNSSEC can be deployed in days, not months 20

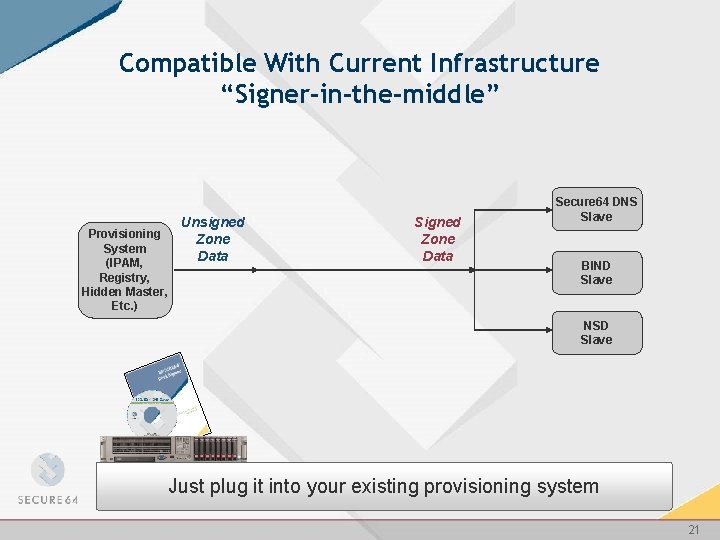
Compatible With Current Infrastructure “Signer-in-the-middle” Provisioning System (IPAM, Registry, Hidden Master, Etc. ) Unsigned Zone Data Secure 64 DNS Slave BIND Slave NSD Slave Secure 64 Just DNS Signer plug it into your existing provisioning system 21

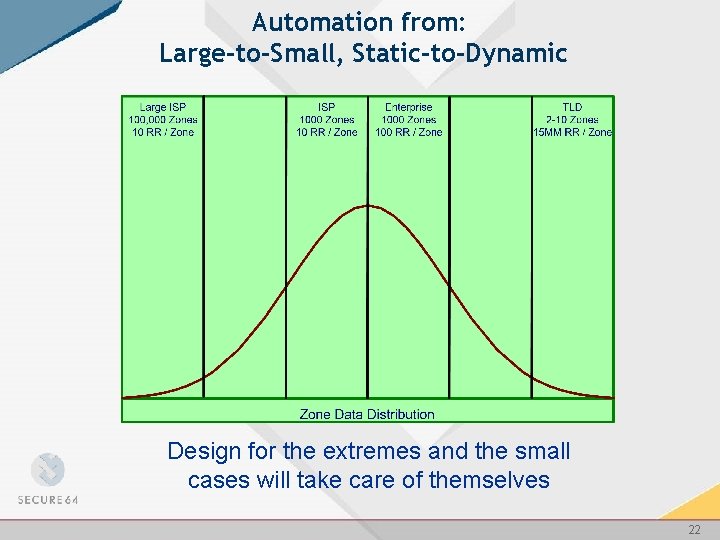
Automation from: Large-to-Small, Static-to-Dynamic Design for the extremes and the small cases will take care of themselves 22

Challenges for Large-Scale Deployments 1. 2. 3. 4. 5. Key Generation for huge numbers of keys Bulk Signing and Re-signing can take lots of time --- and you don’t have enough time Small Changes to Large Zones Disaster Planning: Automatic & Secure Backup of Metadata Chain-of-Trust Coordination 23

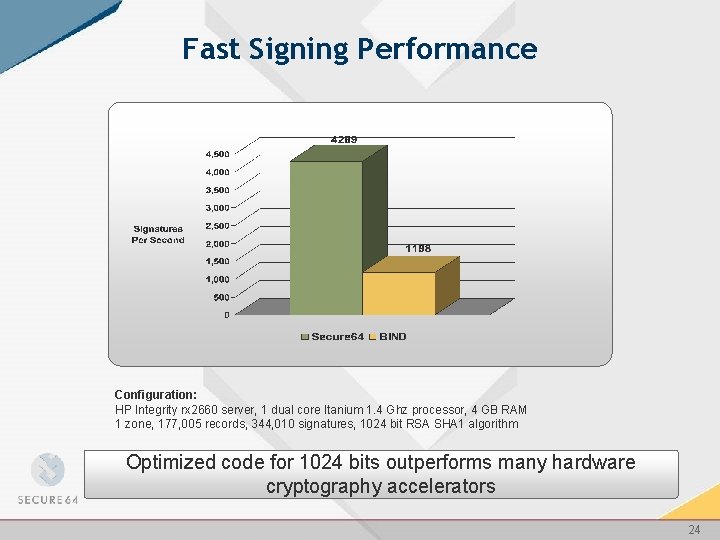
Fast Signing Performance Configuration: HP Integrity rx 2660 server, 1 dual core Itanium 1. 4 Ghz processor, 4 GB RAM 1 zone, 177, 005 records, 344, 010 signatures, 1024 bit RSA SHA 1 algorithm Optimized code for 1024 bits outperforms many hardware cryptography accelerators 24

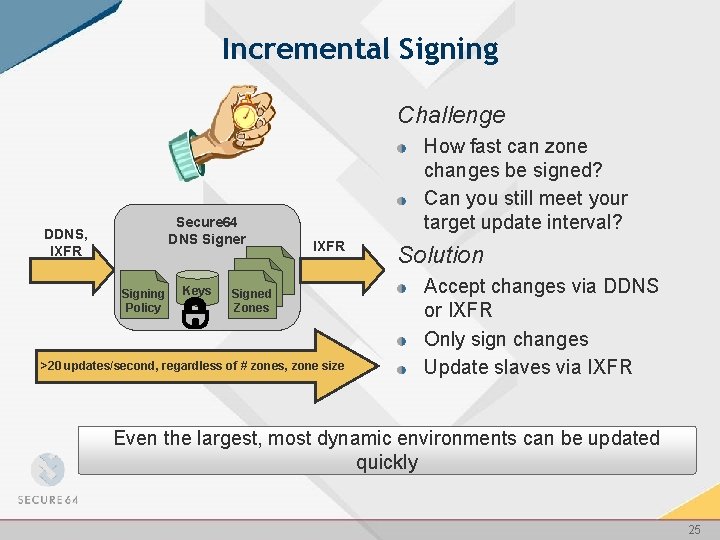
Incremental Signing Challenge Secure 64 DNS Signer DDNS, IXFR Signing Policy Keys How fast can zone changes be signed? Can you still meet your target update interval? IXFR Signed Zones >20 updates/second, regardless of # zones, zone size Solution Accept changes via DDNS or IXFR Only sign changes Update slaves via IXFR Even the largest, most dynamic environments can be updated quickly 25

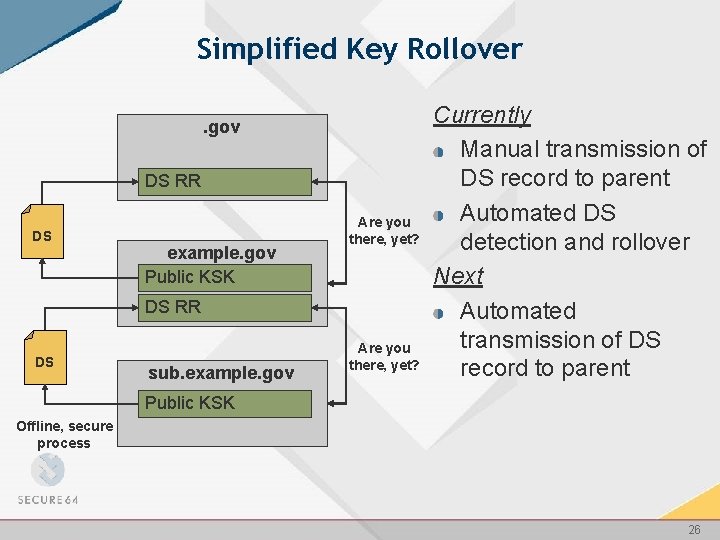
Simplified Key Rollover. gov DS RR DS example. gov Public KSK Are you there, yet? DS RR DS sub. example. gov Are you there, yet? Currently Manual transmission of DS record to parent Automated DS detection and rollover Next Automated transmission of DS record to parent Public KSK Offline, secure process 26

Disaster Recovery DNSSEC Meta. Data: Signing Keys – private & public Serial # tracking key rollover state Chain-of-trust info Automated backup of encrypted metadata to standard storage devices Secure backup with TPM prevents INSIDER attacks 27

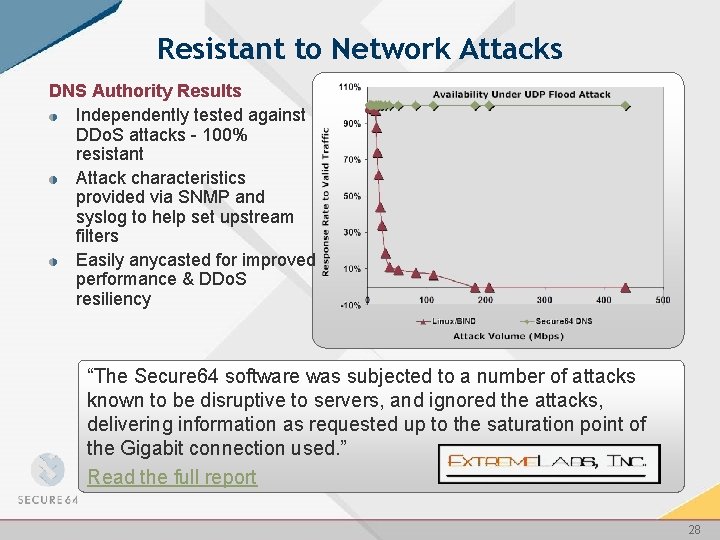
Resistant to Network Attacks DNS Authority Results Independently tested against DDo. S attacks - 100% resistant Attack characteristics provided via SNMP and syslog to help set upstream filters Easily anycasted for improved performance & DDo. S resiliency “The Secure 64 software was subjected to a number of attacks known to be disruptive to servers, and ignored the attacks, delivering information as requested up to the saturation point of the Gigabit connection used. ” Read the full report 28

Benefits Summary For management Quicker implementation Reduced cost versus For staff Simple. Less to learn Timely. Deploy in days, not months Correct. Eliminates errors that can take you offline Secure. Protects the signing keys For users: Internet is safer to access Secure 64 DNS Signer makes it easy to deploy DNSSEC correctly and securely 29

Secure 64: The DNSSEC Leader Agencies trained with NIST: US Department of Commerce National Telecommunication Information Administration Economic and Statistics Administration Bureau of Statistics Bureau of Economic Analysis International Trade Administration US Patent and Trademark Office National Oceanic and Atmospheric Administration US Department of Health and Human Services National Institute of Health Federal Aviation Administration US Department of Housing and Urban Development US Antarctic Program US Department of Energy US Department of Agriculture US Department of the Interior National Park Service US Agency of International Development US Department of State US Nuclear Regulatory Commission US Department of Treasury Court Services and Offender Supervision Agency Federal Maritime Commission US Government Accountability Office US Department of Labor 30

Thank You! For More Information Secure 64 web site: www. secure 64. com Sign up to access to an online signing engine to try it out with your own data Contact Adam. Tice@Secure 64. com for Copies of this presentation Schedule a demo of our automated DNSSEC solution DNSSEC whitepapers, newsletters, case studies Invitation to hands on training workshops (NIST, HP) 31