CS 854 Hot Topics in Computer and Communications








![Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r](https://slidetodoc.com/presentation_image_h2/09cc2f75d198f231823935a8ad2789da/image-14.jpg)






- Slides: 33

CS 854 – Hot Topics in Computer and Communications Security Fall 2006 Introduction to Cryptography and Security 1

Slides r based on v Kurose & Ross, Computer networking, Chapter 8 v Stallings, Cryptography and Network Security 2

Overview r Network security r Symmetric-key encryption r Public-key encryption r Message integrity and authentication r Entity authentication r Key distribution r Computer security 3

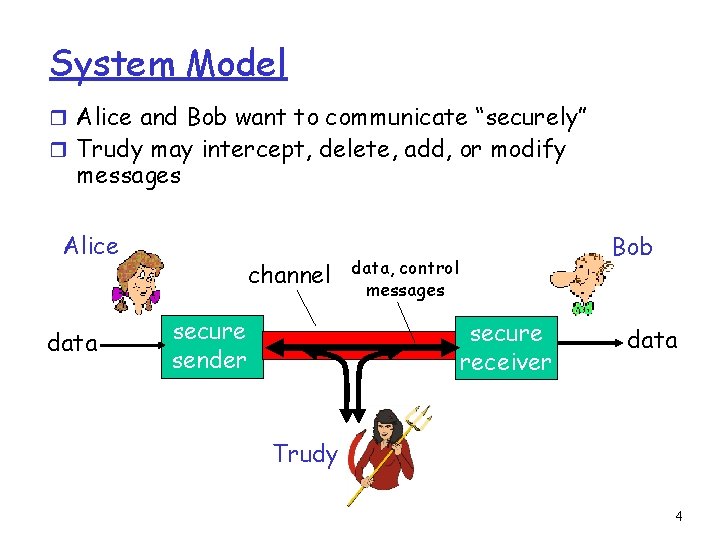
System Model r Alice and Bob want to communicate “securely” r Trudy may intercept, delete, add, or modify messages Alice data channel secure sender Bob data, control messages secure receiver data Trudy 4

Aside: Alice & Bob r Alice wants to send a message to Bob r Eve, the eavesdropper (passive) r Mallory, the malicious attacker (active) r Trudy, the intruder (same as Mallory) 5

What is secure communication? Confidentiality: only Alice and Bob should see message contents Authentication: Alice and Bob can confirm identity of each other Message Integrity: Alice and Bob can ensure message not altered without detection Nonrepudiation: receiver can prove to third party that sender in fact sent message Traffic Analysis: Alice and Bob hide that they are communicating No Denial of Service: Alice and Bob can communicate 6

Threat Model Q: What can a “bad guy” do? A: a lot! v v v eavesdrop: passively intercept messages actively insert, modify, or delete messages into connection impersonation: can fake (spoof) source address in network packet (or any field in packet) hijacking: “take over” ongoing connection by removing sender or receiver, inserting himself in place denial of service: prevent service from being used by others (e. g. , by overloading resources) but (typically) not drop a nuclear bomb on Alice and Bob 7

Overview r Network security r Symmetric-key encryption r Public-key encryption r Message integrity and authentication r Entity authentication r Key distribution r Computer security 8

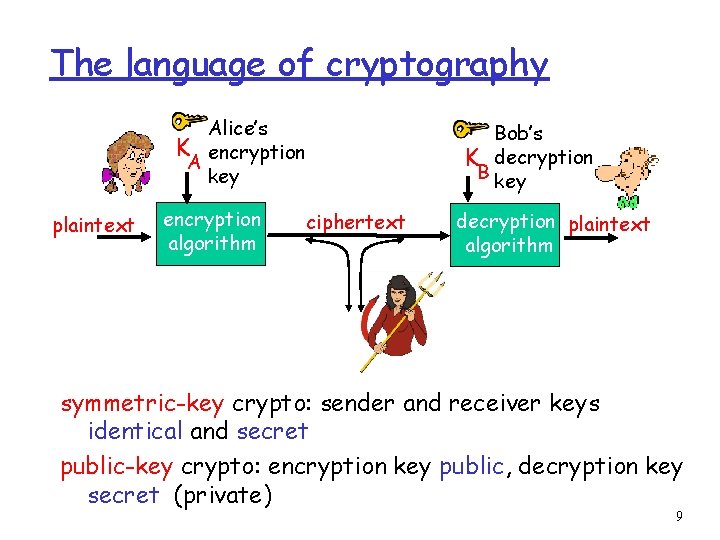
The language of cryptography Alice’s K encryption A key plaintext encryption algorithm Bob’s K decryption B key ciphertext decryption plaintext algorithm symmetric-key crypto: sender and receiver keys identical and secret public-key crypto: encryption key public, decryption key secret (private) 9

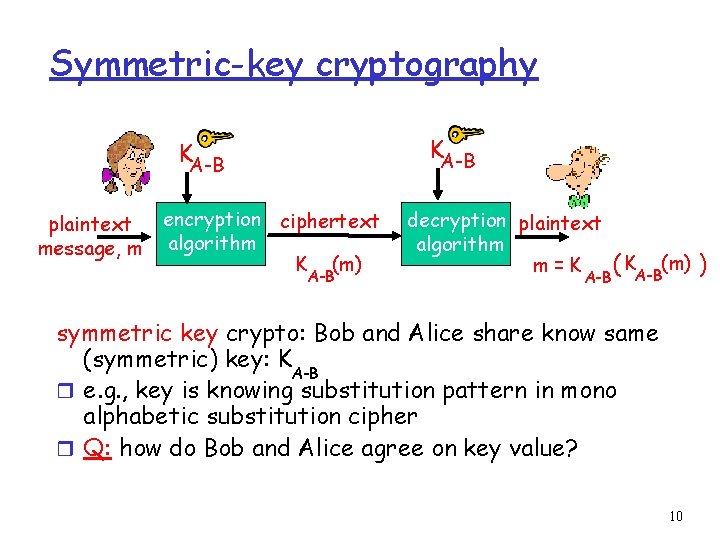
Symmetric-key cryptography KA-B plaintext message, m encryption ciphertext algorithm K (m) A-B decryption plaintext algorithm m=K A-B ( KA-B(m) ) symmetric key crypto: Bob and Alice share know same (symmetric) key: K A-B r e. g. , key is knowing substitution pattern in mono alphabetic substitution cipher r Q: how do Bob and Alice agree on key value? 10

Symmetric key cryptography substitution cipher: substituting one thing for another v monoalphabetic cipher: substitute one letter for another plaintext: abcdefghijklmnopqrstuvwxyz ciphertext: mnbvcxzasdfghjklpoiuytrewq E. g. : Plaintext: bob. i love you. alice ciphertext: nkn. s gktc wky. mgsbc Q: How hard to break this simple cipher? : q brute force (how hard? ) q other? 11

Attacks on encryption schemes Known to attacker (in addition to encryption scheme and ciphertext to be decrypted): r Ciphertext only: nothing else r Known plaintext: plaintext-ciphertext pair(s) r Chosen plaintext: plaintext(s) chosen by attacker and corresponding ciphertext(s) r Chosen ciphertext: ciphertext(s) chosen by attacker and corresponding plaintext(s) 12

Block and Stream Ciphers r Block cipher: v operates on fix-sixed blocks at a time • today’s ciphers: 128 bits reversible v plaintext and ciphertext have same size v common key sizes: 128 or 256 bit v Kerckhofs’ principle: structure of cipher is publicly known v r Stream cipher: v operates on single bit (byte) at a time 13
![Symmetric key crypto DES Data Encryption Standard r US encryption standard NIST 1993 r Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r](https://slidetodoc.com/presentation_image_h2/09cc2f75d198f231823935a8ad2789da/image-14.jpg)
Symmetric key crypto: DES: Data Encryption Standard r US encryption standard [NIST 1993] r 56 -bit symmetric key, 64 -bit plaintext input r How secure is DES? DES Challenge: 56 -bit-key-encrypted phrase (“Strong cryptography makes the world a safer place”) decrypted (brute force) in 4 months (1997) v no known “backdoor” decryption approach r making DES more secure: v use three keys sequentially (3 DES) on each block v slow v 14

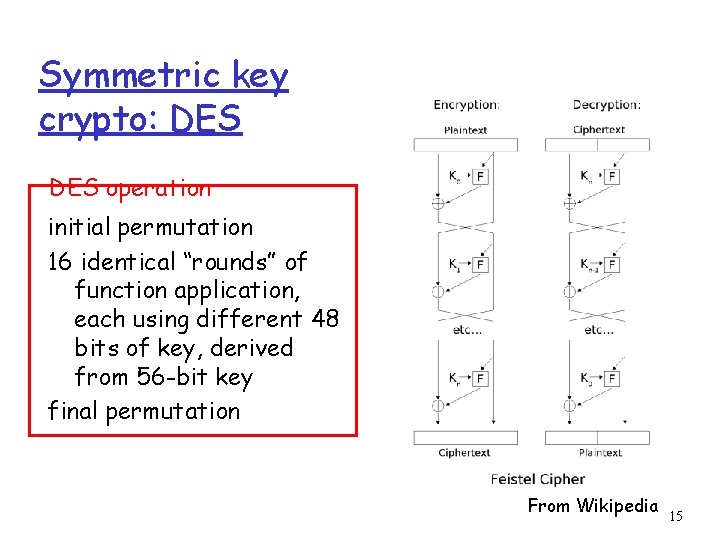
Symmetric key crypto: DES operation initial permutation 16 identical “rounds” of function application, each using different 48 bits of key, derived from 56 -bit key final permutation From Wikipedia 15

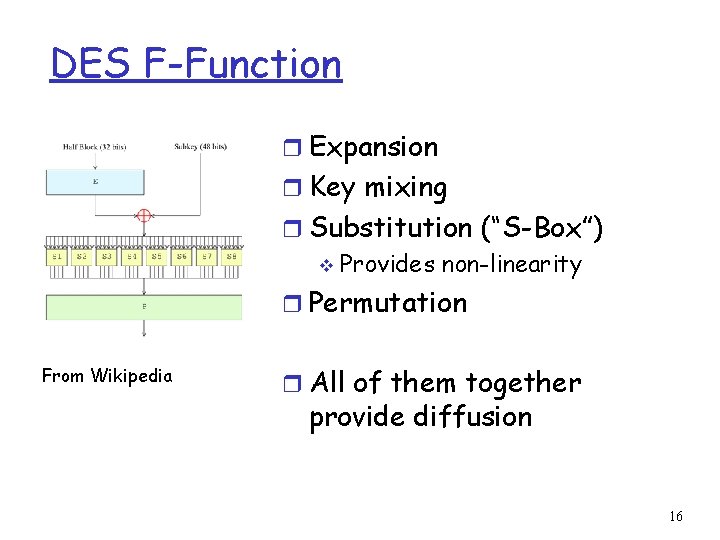
DES F-Function r Expansion r Key mixing r Substitution (“S-Box”) v Provides non-linearity r Permutation From Wikipedia r All of them together provide diffusion 16

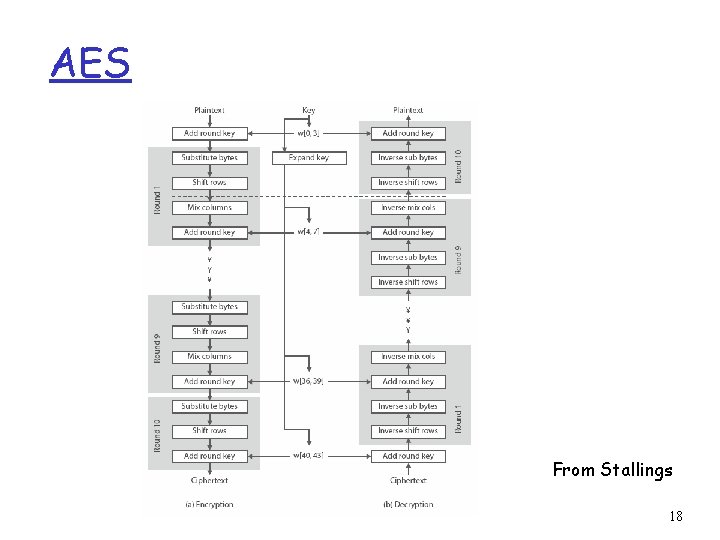
AES: Advanced Encryption Standard r new (Nov. 2001) symmetric-key NIST standard, replacing DES r processes data in 128 -bit blocks r iterative, rather than Feistel cipher v v v operates on entire data block in every round decryption different from encryption efficient implementation r 128, 192, or 256 bit keys r brute force decryption (try each key) taking 1 sec on DES takes 149 trillion years for 128 -bit AES 17

AES From Stallings 18

Block Cipher Modes r Block cipher modes enable processing of messages with arbitrary length r Electronic Codebook Mode (ECB) r Don’t use ECB From Wikipedia 19

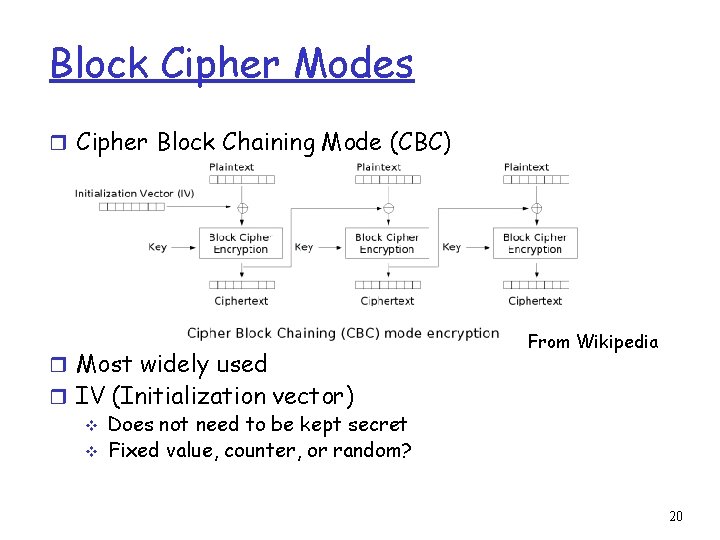
Block Cipher Modes r Cipher Block Chaining Mode (CBC) r Most widely used From Wikipedia r IV (Initialization vector) v Does not need to be kept secret v Fixed value, counter, or random? 20

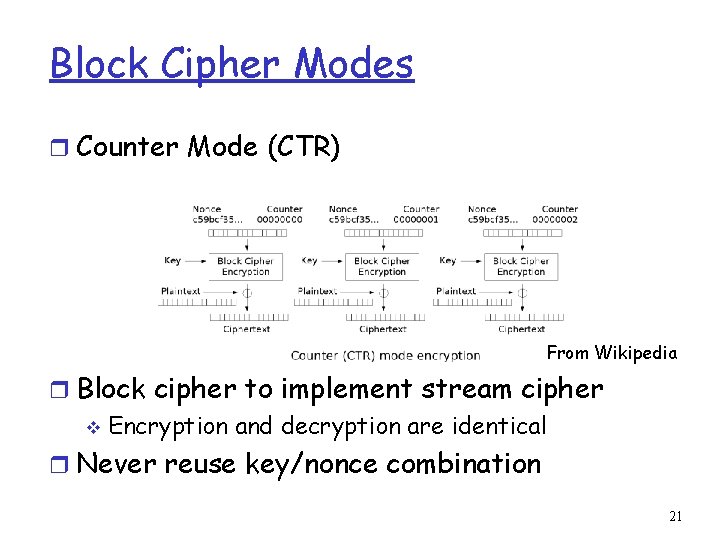
Block Cipher Modes r Counter Mode (CTR) From Wikipedia r Block cipher to implement stream cipher v Encryption and decryption are identical r Never reuse key/nonce combination 21

Overview r Network security r Symmetric-key encryption r Public-key encryption r Message integrity and authentication r Entity authentication r Key distribution r Computer security 22

Public-Key Cryptography symmetric-key crypto r requires sender, receiver know shared secret key r Q: how to agree on key in first place (particularly if never “met”)? public-key cryptography r radically different approach [Diffie. Hellman 76, RSA 78] r sender, receiver do not share secret key r public encryption key known to all r private decryption key known only to receiver 23

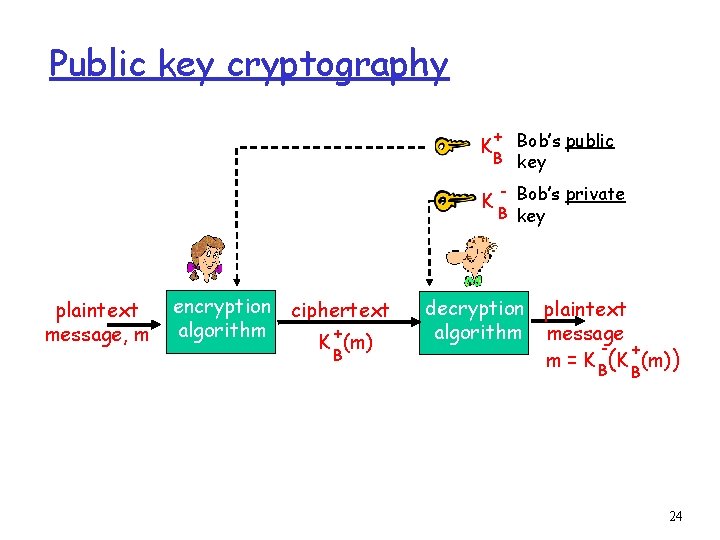
Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B 24

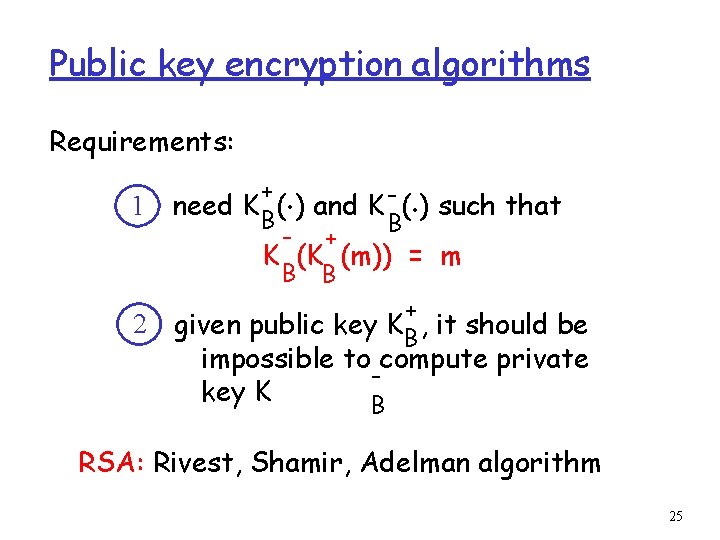
Public key encryption algorithms Requirements: 1 2 . . + need K B( ) and K - ( ) such that B - + K (K (m)) = m B B + given public key KB , it should be impossible to compute private key K B RSA: Rivest, Shamir, Adelman algorithm 25

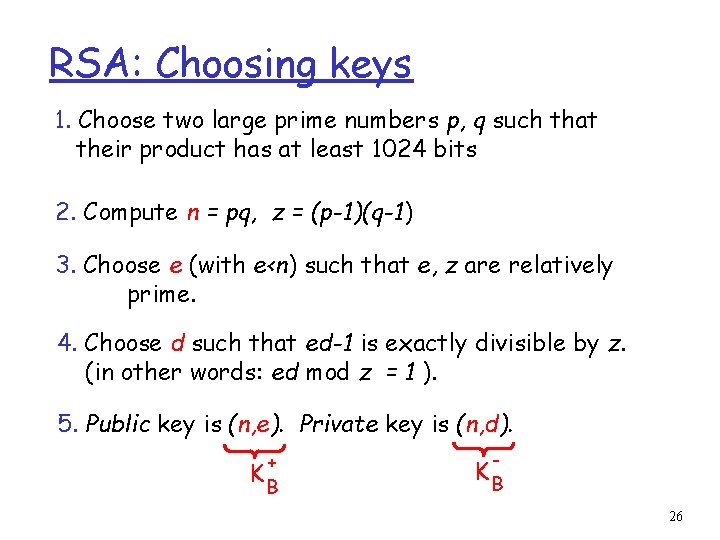
RSA: Choosing keys 1. Choose two large prime numbers p, q such that their product has at least 1024 bits 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e<n) such that e, z are relatively prime. 4. Choose d such that ed-1 is exactly divisible by z. (in other words: ed mod z = 1 ). 5. Public key is (n, e). Private key is (n, d). + KB - KB 26

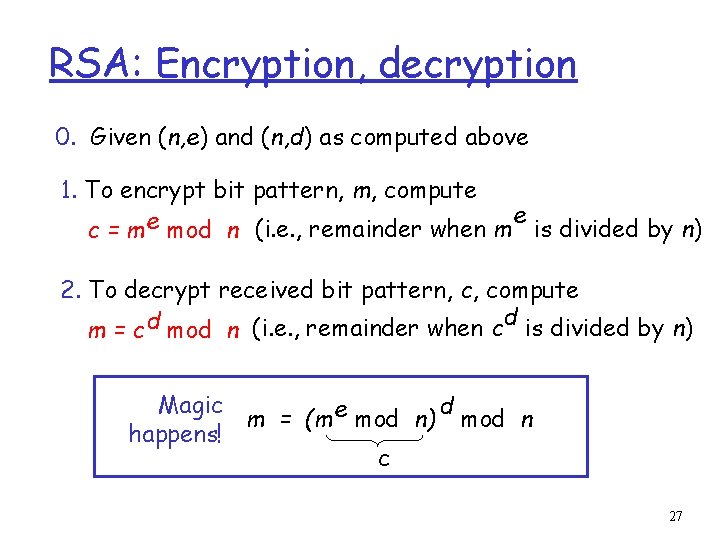
RSA: Encryption, decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt bit pattern, m, compute e e c = m mod n (i. e. , remainder when m is divided by n) 2. To decrypt received bit pattern, c, compute d m = c d mod n (i. e. , remainder when c is divided by n) Magic d m = (m e mod n) mod n happens! c 27

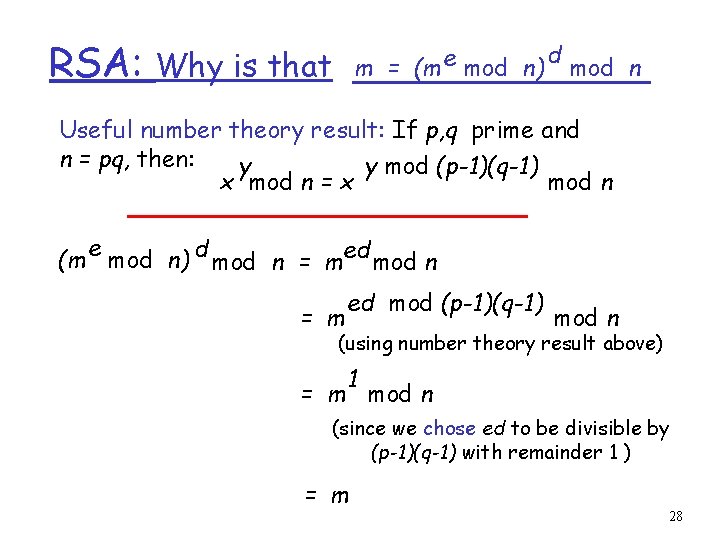
RSA: m = (m e mod n) Why is that d mod n Useful number theory result: If p, q prime and n = pq, then: y y mod (p-1)(q-1) x mod n = x mod n e (m mod n) d mod n = med mod n = m ed mod (p-1)(q-1) mod n (using number theory result above) 1 = m mod n (since we chose ed to be divisible by (p-1)(q-1) with remainder 1 ) = m 28

RSA: Security r relies on the assumption that there are no algorithms for quickly factoring n into p and q v would allow attacker to compute z=(p-1)(q-1) and d using ed mod z = 1 r but we don’t know whethere exist such fast algorithms… 29

RSA: Issues r RSA exponentiation is slow v at least 100 times slower than DES v use hybrid scheme, e. g. , • AES for encrypting actual data • RSA for encrypting corresponding AES session key r RSA can be vulnerable, e. g. , v small d or e v deterministic v timing attacks v do not use your own implementation of RSA 30

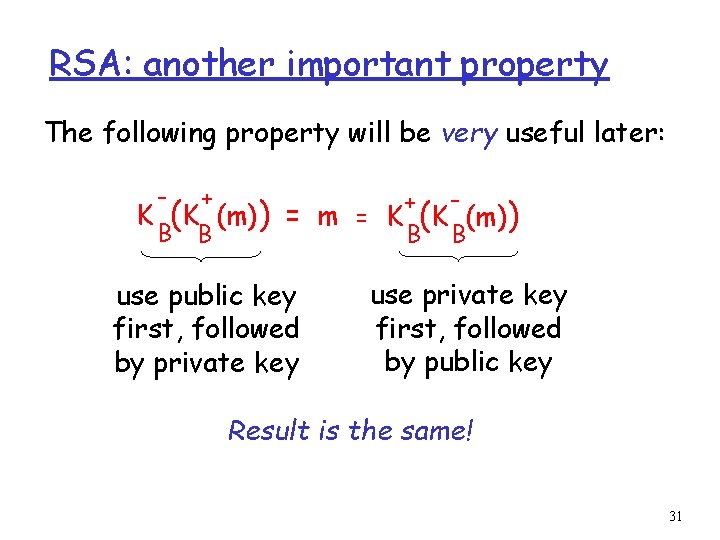
RSA: another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! 31

El Gamal r Prime p, random g (< p) r Private key: d Public key: e = gd mod p r Encryption: message m, random r c = (gr, mer) (mod p) r Decryption: c = (c 1, c 2) c 2/(c 1 d) = mer/gdr = mgdr/gdr = m r assumes that computing discrete logarithms is hard r probabilistic scheme (ciphertext > plaintext) 32

Diffie-Hellman Key Exchange r first published public-key algorithm r Alice and Bob establish joint secret even though r r r Eve is reading all the exchanged messages! assumption: public prime q, integer n Alice: Choose secret XA, compute and give YA to Bob: Choose secret XB, compute and give YB to Alice Joint secret: Also relies on discrete logarithms problem Susceptible to man-in-the-middle attack 33