CS 4470 Computer Networking Protocols 4 Data Link


















- Slides: 38

CS 4470 Computer Networking Protocols 4. Data Link Layer 2 Huiping Guo Department of Computer Science California State University, Los Angeles

Outline r LANs m Topologies m Ethernet m Extended LANs 4. LAN 2 CS 4470_F 17 4 -2

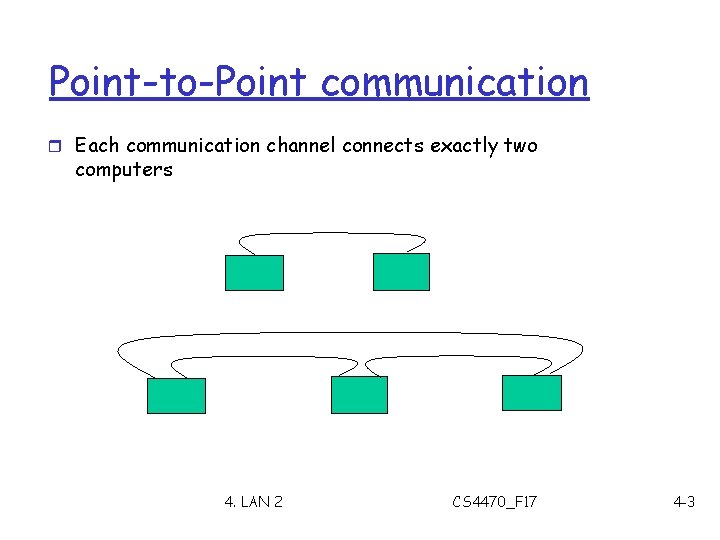
Point-to-Point communication r Each communication channel connects exactly two computers 4. LAN 2 CS 4470_F 17 4 -3

Point-to-Point communication (cont. ) r Disadvantages: m The number of connections grows quickly as the size of the network increases m The number of connections needed for N computers is proportional to N 2 • Direct connections required = (N 2 -N)/2 m The expense is especially high 4. LAN 2 CS 4470_F 17 4 -4

Shared communication channels r Local Area Networks m Devised as alternatives to expensive, dedicated point-topoint connections. r Rely on the shared medium m A set of computers attach to a cable m The computers take turns sending data r Sharing reduces cost! 4. LAN 2 CS 4470_F 17 4 -5

Comparison r Networks based on the shared medium m Used for LOCAL communication. r Point-to-point connections m Used for long-distance networks m Why not shared medium? 4. LAN 2 CS 4470_F 17 4 -6

Shared medium not suitable for long distance networks r Computers attached to a shared network must coordinate use of the network r Coordination requires communication, introduces longer delays r Shared networks with long delays are inefficient m they spend more time coordinating the use of the shared medium and less time sending data 4. LAN 2 CS 4470_F 17 4 -7

LAN: A definition r LAN --- Local Area Network r A LAN is computer network in which devices (computers, printers) are connect to a shared medium (wire or cable) to exchange data or share resources within a small geographic area m m An office, the floor of a building, a building itself, or a small campus Not always clear where a “local area” ends and a “wide area” begins 4. LAN 2 CS 4470_F 17 4 -8

LANs are popular r LANs are the most popular form of computer network r They are relatively cheap r They are typically fast r Deployed today in not just workplace and offices, but also in the home 4. LAN 2 CS 4470_F 17 4 -9

Features r Limited to short distance r Rely on shared media r Topologies r Many LAN technologies exist m Determined by the link layer protocol 4. LAN 2 CS 4470_F 17 4 -10

Network Topology r Specify general “shape” of a network r Often applied to LAN r LAN Topologies m Bus m Star m Tree 4. LAN 2 CS 4470_F 17 4 -11

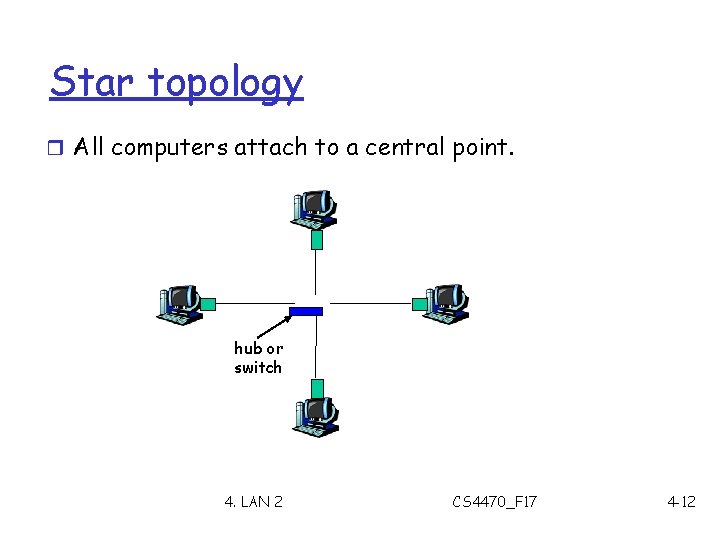
Star topology r All computers attach to a central point. hub or switch 4. LAN 2 CS 4470_F 17 4 -12

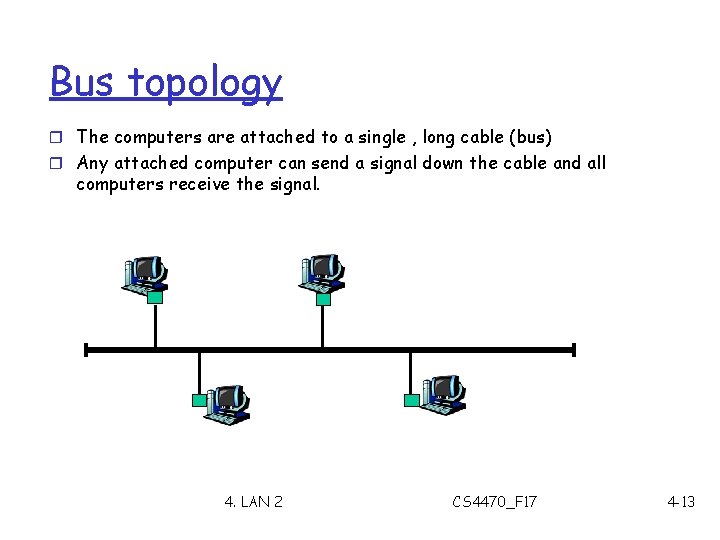
Bus topology r The computers are attached to a single , long cable (bus) r Any attached computer can send a signal down the cable and all computers receive the signal. 4. LAN 2 CS 4470_F 17 4 -13

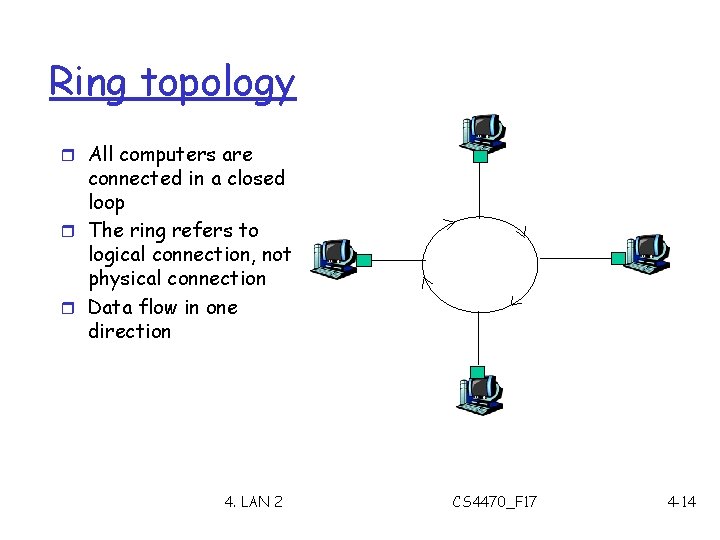
Ring topology r All computers are connected in a closed loop r The ring refers to logical connection, not physical connection r Data flow in one direction 4. LAN 2 CS 4470_F 17 4 -14

Choice of Topology r Reliability r Expandability r Performance r Needs considering in context of: m Medium m Wiring layout m Access control 4. LAN 2 CS 4470_F 17 4 -15

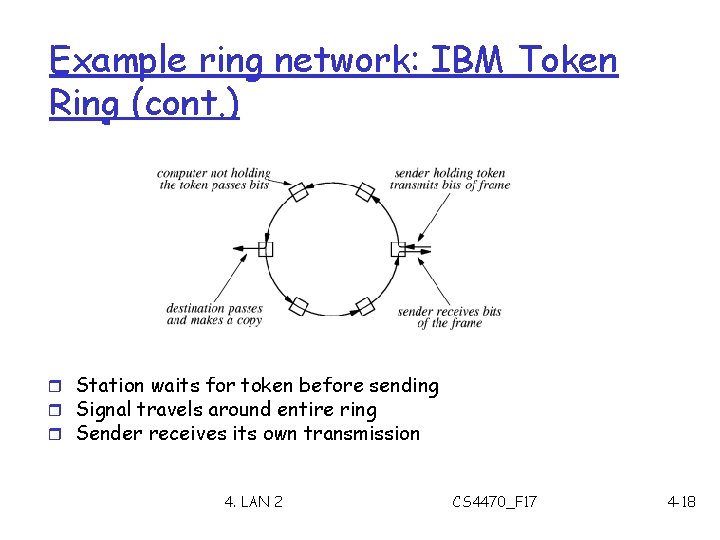
Example ring network: IBM Token Ring r Access the shared medium -- ring m Use token passing m token passing ring networks r Media access control m A computer must wait for permission before it can send data m Once it obtains permission, the sending computer has complete control of the network m The data pass from the sender to the next computer, then to the next computer and so on until the data pass completely around the ring and arrive back at the sender 4. LAN 2 CS 4470_F 17 4 -16

Example ring network: IBM Token Ring (cont. ) r Token m A special reserved bit pattern which gives a computer permission to send data m The token passes around the ring m How to make sure data doesn’t contain the token? r A computer cannot hold a token forever! m Receive a token m Remove it from the ring m Send a frame m Release the token 4. LAN 2 CS 4470_F 17 4 -17

Example ring network: IBM Token Ring (cont. ) r Station waits for token before sending r Signal travels around entire ring r Sender receives its own transmission 4. LAN 2 CS 4470_F 17 4 -18

Pros and Cons r Advantages m Easy detection of • Broking ring • Hardware failures • Interference r Disadvantages m Each computer attached to a ring must pass bits of a frame to the next computer m Failure of a single machine or link can disable the entire network m Point-to-Point wiring: difficult to add/remove a satation 4. LAN 2 CS 4470_F 17 4 -19

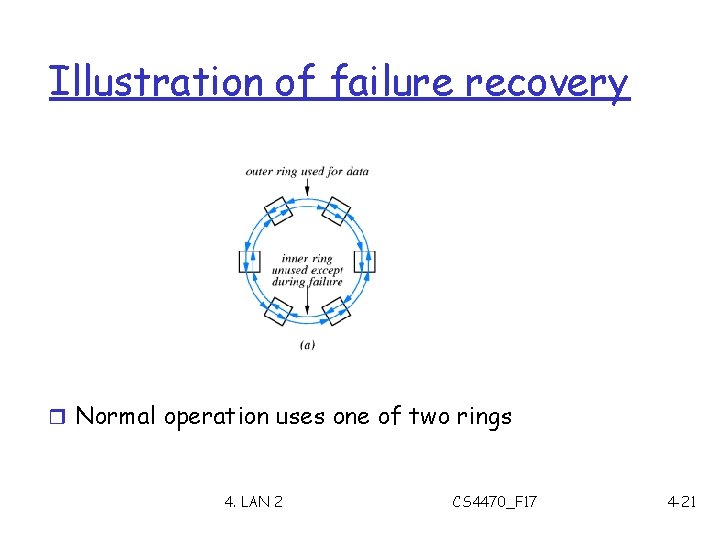
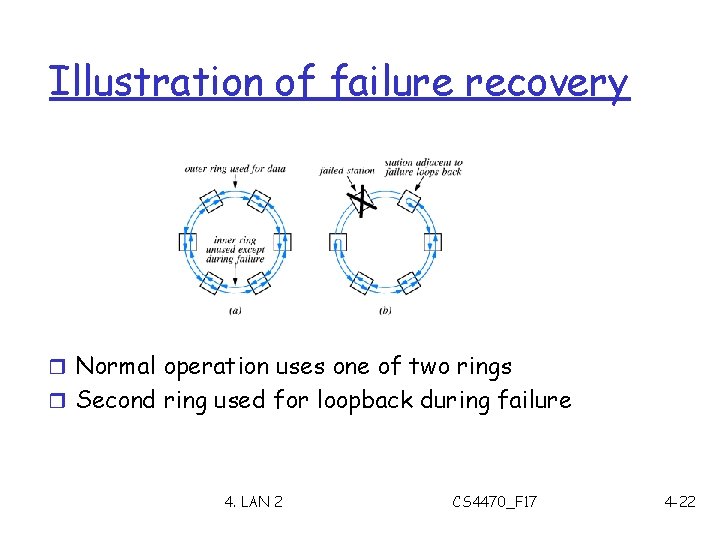
Failure recovery in ring networks r Automatic failure recovery r Introduced by FDDI r Uses two rings r Terminology m Dual-attached m Counter rotating m Self healing 4. LAN 2 CS 4470_F 17 4 -20

Illustration of failure recovery r Normal operation uses one of two rings 4. LAN 2 CS 4470_F 17 4 -21

Illustration of failure recovery r Normal operation uses one of two rings r Second ring used for loopback during failure 4. LAN 2 CS 4470_F 17 4 -22

Outline r LANs m Topologies m Ethernet m Extended LANs 4. LAN 2 CS 4470_F 17 4 -23

Ethernet r Ethernet uses bus topologies r “dominant” wired LAN technology: r First widely used LAN technology r Simpler, cheaper than token ring, FDDI and ATM r Kept up with speed race: 10 Mbps – 10 Gbps 4. LAN 2 CS 4470_F 17 4 -24

Shared medium in a LAN r Shared medium used for all transmissions r Only one station transmits at any time r Stations “take turns” using medium r Media Access Control (MAC) policy ensures fairness 4. LAN 2 CS 4470_F 17 4 -25

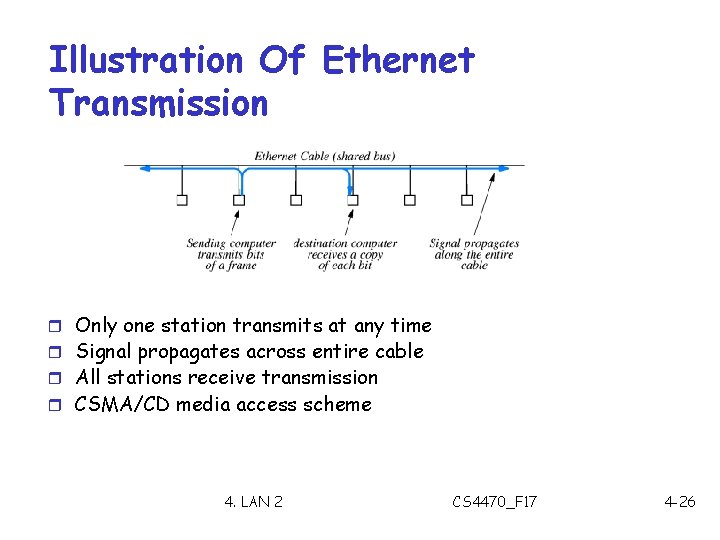
Illustration Of Ethernet Transmission r Only one station transmits at any time r Signal propagates across entire cable r All stations receive transmission r CSMA/CD media access scheme 4. LAN 2 CS 4470_F 17 4 -26

CSMA/CD Paradigm r Multiple Access (MA) m Multiple computers attach to shared media m Each uses same access algorithm r Carrier Sense (CS) m Wait until medium idle m Begin to transmit frame r CSMA plus Collision Detection (CD) m Listen to medium during transmission m Detect whether another station’s signal interferes 4. LAN 2 CS 4470_F 17 4 -27

Transmitter algorithm r When a station has a frame to send and the line is idle, it transmits the frame immediately m m There is no negotiation with other adaptors The frame size is up to 1, 500 bytes which means that the station can occupy the line for only a fixed length of time r When an adaptor has a frame to send and the line is busy, it waits for the line to go idle and then transmits immediately m m The Ethernet is said to be 1 -persistent protocol because a station with a frame to send transmits with prob. 1 whenever a busy line goes idle In general, a p-persistent algorithm transmits with prob. P after a line becomes idle 4. LAN 2 CS 4470_F 17 4 -28

Transmitter algorithm r Collisions m Two stations find the line idle and transmit at the same time m While a station on one end starts to transmit a frame, the other station on the opposite end doesn’t sense the line busy and transmits r While a station is transmitting, it keeps listing to the line m m If there is a collision, the station stops transmission and sends a jam signal Back off from the interference and try again 4. LAN 2 CS 4470_F 17 4 -29

Backoff after collision r Exponential backoff m after the mth collision, chooses a K at random from {0, 1, 2, …, 2 m-1} m waits K·512 bit times r Bit time: m 1 microsec for 10 Mbps Ethernet ; m For K=1023, wait time is about 50 msec 4. LAN 2 CS 4470_F 17 4 -30

Backoff after collision (cont. ) r Goal m adapt retransmission attempts to estimated current load m heavy load: random wait will be longer r first collision m choose K from {0, 1}; delay is K· 512 bit transmission times r after second collision m choose K from {0, 1, 2, 3}… r after ten collisions, choose K from {0, 1, 2, 3, 4, …, 1023} 4. LAN 2 CS 4470_F 17 4 -31

Addressing: Identifying A Destination r A pair of computers communicate across a LAN r All other computer in the LAN receive and process each copy of the message r How to avoid this? 4. LAN 2 CS 4470_F 17 4 -32

Addressing: Identifying A Destination (cont. ) r Allow sender to specify destination m Each station assigned unique 48 -bit address: MAC address m Address assigned when network interface card (NIC) manufactured m Each frame contains address of intended recipient 4. LAN 2 CS 4470_F 17 4 -33

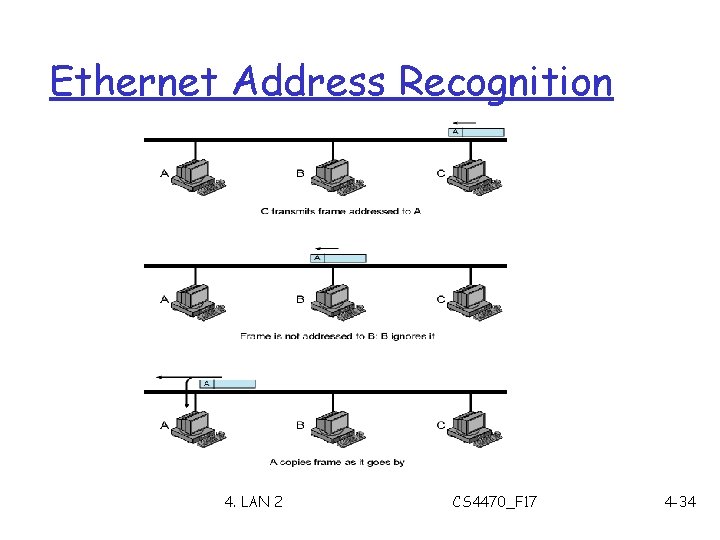
Ethernet Address Recognition 4. LAN 2 CS 4470_F 17 4 -34

Broadcast On Ethernet r All 1 s address specifies broadcast r Sender m Places broadcast address in frame m Transmits one copy on shared network m All stations receive copy r Receiver always accepts frame that contains m Station’s address m The broadcast address 4. LAN 2 CS 4470_F 17 4 -35

Frame header and frame format r Each LAN defines the exact frame format used with the technology r General format: m m Frame header+DATA All frames with the same LAN technology have the same header size 4. LAN 2 CS 4470_F 17 4 -36

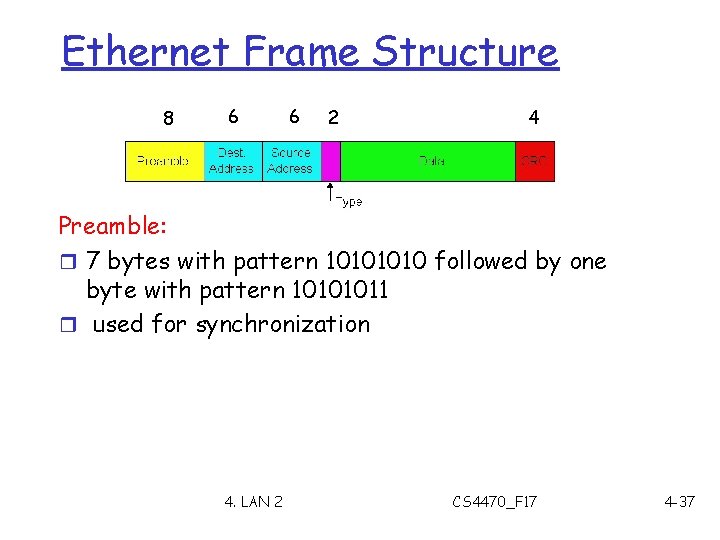
Ethernet Frame Structure 8 6 6 2 4 Preamble: r 7 bytes with pattern 1010 followed by one byte with pattern 10101011 r used for synchronization 4. LAN 2 CS 4470_F 17 4 -37

Ethernet Frame Structure (more) r Addresses: 6 bytes m m if adapter receives frame with matching destination address, or with broadcast address it passes data in frame to net-layer protocol otherwise, adapter discards frame r Type: indicates the higher layer protocol (mostly IP but others may be supported such as Novell IPX and Apple. Talk) r CRC: checked at receiver, if error is detected, the frame is simply dropped 4. LAN 2 CS 4470_F 17 4 -38