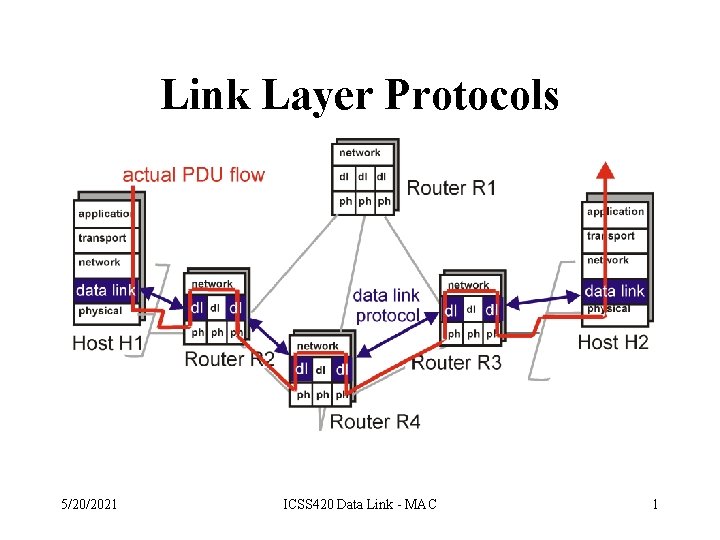
Link Layer Protocols 5202021 ICSS 420 Data Link


























- Slides: 91

Link Layer Protocols 5/20/2021 ICSS 420 Data Link - MAC 1

Link Layer Services • Framing and link access: – encapsulate datagram into frame implement channel access if shared medium, – ‘physical addresses’ are used in frame headers to identify source and destination of frames on broadcast links • Reliable Delivery: – seldom used on fiber optic, co-axial cable and some twisted pairs too due to low bit error rate. – Used on wireless links, where the goal is to reduce errors thus avoiding end-to-end retransmissions 5/20/2021 ICSS 420 Data Link - MAC 2

Link Layer Services (more) • Flow Control: – pacing between senders and receivers • Error Detection: – errors are caused by signal attenuation and noise. – Receiver detects presence of errors: – it signals the sender for retransmission or just drops the corrupted frame • Error Correction: – mechanism for the receiver to locate and correct the error without resorting to retransmission 5/20/2021 ICSS 420 Data Link - MAC 3

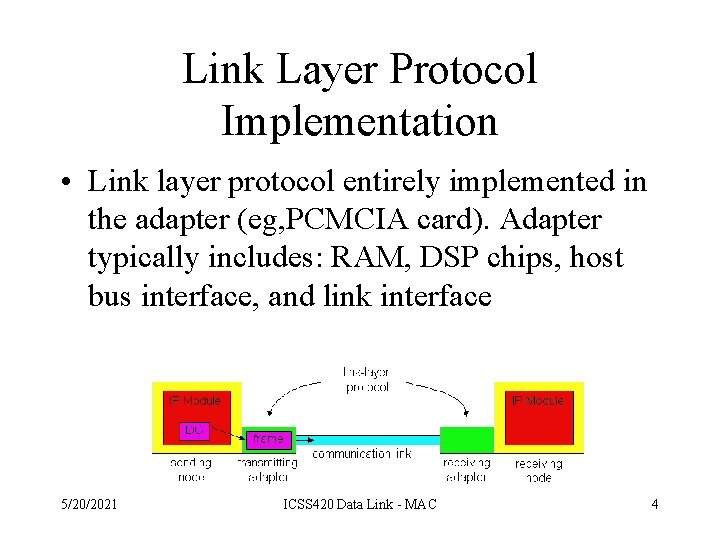
Link Layer Protocol Implementation • Link layer protocol entirely implemented in the adapter (eg, PCMCIA card). Adapter typically includes: RAM, DSP chips, host bus interface, and link interface 5/20/2021 ICSS 420 Data Link - MAC 4

Network Adapters • Network adapters, sometimes called Network Interface Cards (NIC), plug into the data bus on a computer and into a network cable • The NIC performs all of the functions required to communicate on a network • Some computers have a NIC built in 5/20/2021 ICSS 420 Data Link - MAC 5

Selecting a NIC • Before selecting a NIC for your computer, you need to determine three things: – What type of network are you connecting to? – What type of media (cable) are you using? – What type of bus does your computer have? • If you have a choice of bus, you will want to consider the performance of each bus and how will affect the NIC 5/20/2021 ICSS 420 Data Link - MAC 6

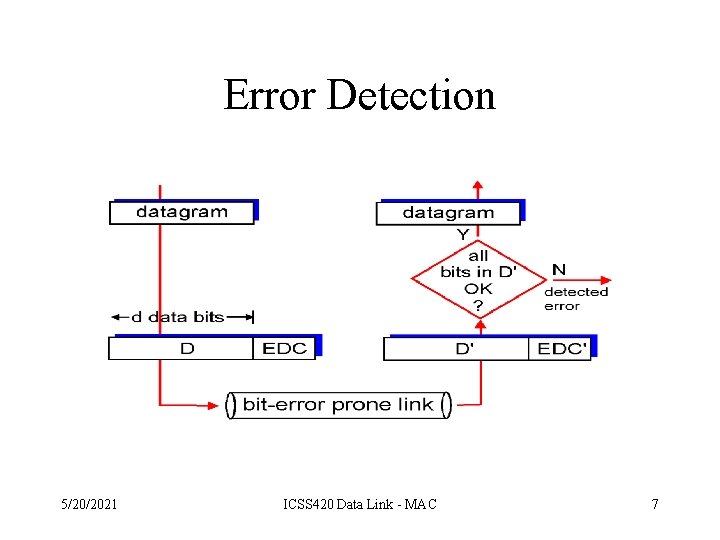
Error Detection 5/20/2021 ICSS 420 Data Link - MAC 7

Errors • Transmission errors are a way of life. • In the digital world an error means that a bit value is flipped. • An error can be isolated to a single bit. • Errors on some media come in bursts – Harder to detect and correct than isolated errors. 5/20/2021 ICSS 420 Data Link - MAC 8

Dealing with Errors • Error detecting codes – provide enough redundant information to enable the receiver to deduce that an error occurred • Error correcting codes – provide enough redundant information to enable the receiver to deduce that an error occurred AND how to fix it • So a message consists of m data bits and r redundant or check bits. 5/20/2021 ICSS 420 Data Link - MAC 9

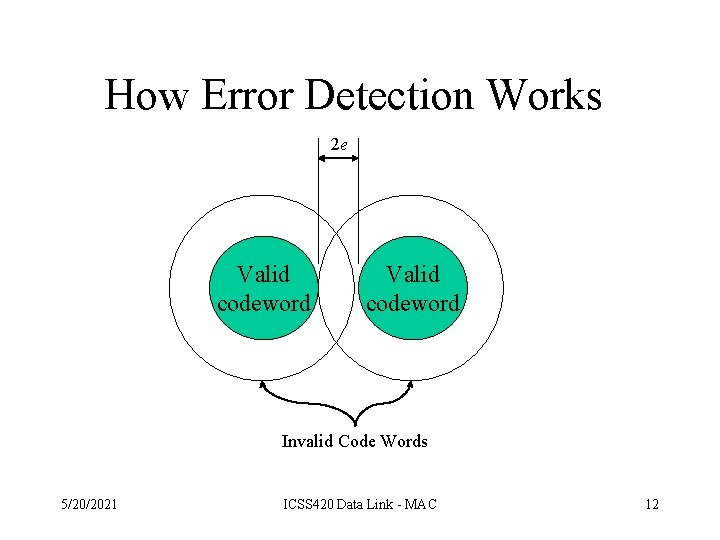
Hamming Distance • Hamming distance: – the number of bit positions in which two codewords differ • Simple to calculate find the XOR • If two codewords are a Hamming distance d apart, it will require d single-bit errors to convert one into the other. • The Hamming distance of a code is the minimum Hamming distance between any two codewords. 5/20/2021 ICSS 420 Data Link - MAC 10

Hamming Distance 2 Code 000 011 101 110 • Note that not all of the 8 different bit patterns are included in the code • Any single error will not convert a valid codeword into another valid codeword. 5/20/2021 ICSS 420 Data Link - MAC 11

How Error Detection Works 2 e Valid codeword Invalid Code Words 5/20/2021 ICSS 420 Data Link - MAC 12

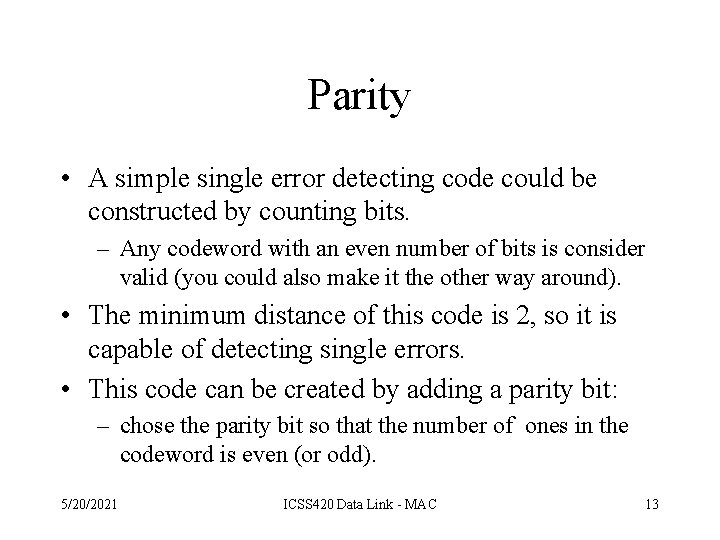
Parity • A simple single error detecting code could be constructed by counting bits. – Any codeword with an even number of bits is consider valid (you could also make it the other way around). • The minimum distance of this code is 2, so it is capable of detecting single errors. • This code can be created by adding a parity bit: – chose the parity bit so that the number of ones in the codeword is even (or odd). 5/20/2021 ICSS 420 Data Link - MAC 13

Parity in Action Want to send: 10 Data Link Sends: 110 5/20/2021 Receive: 111 (ERROR) ICSS 420 Data Link - MAC 14

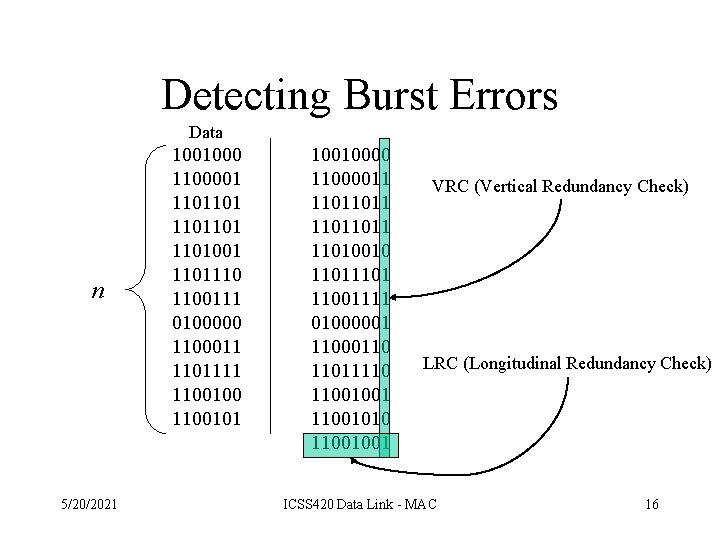
Protecting Blocks • The probability of detecting a burst error on a block using a single parity bit is 50%. • This can be improved by viewing the block as a n by k bit matrix. • A parity bit is then computed for each column. • The check bits are placed in a k-bit row and affixed to the matrix as the last row. • Bursts of length n can be detected. 5/20/2021 ICSS 420 Data Link - MAC 15

Detecting Burst Errors Data n 5/20/2021 1001000 1100001 1101101001 1101110 1100111 0100000 1100011 1101111 1100100 1100101 10010000 11000011 11011011 11010010 1101 11001111 01000001 11000110 11011110 11001001 11001010 11001001 VRC (Vertical Redundancy Check) LRC (Longitudinal Redundancy Check) ICSS 420 Data Link - MAC 16

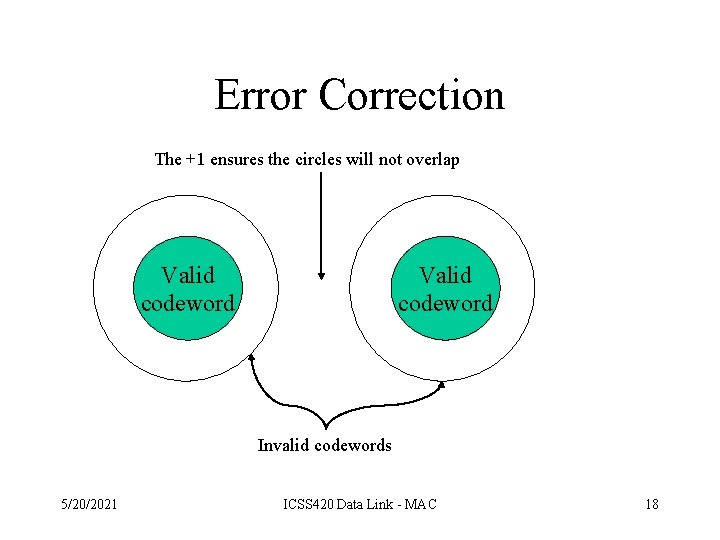
What About Error Correction? • How do we get error correction? – Must increase the minimum distance of the code • The key to error correction is that it must be possible to detect and locate the error. • The minimum distance must be at least 2 e+1 5/20/2021 ICSS 420 Data Link - MAC 17

Error Correction The +1 ensures the circles will not overlap Valid codeword Invalid codewords 5/20/2021 ICSS 420 Data Link - MAC 18

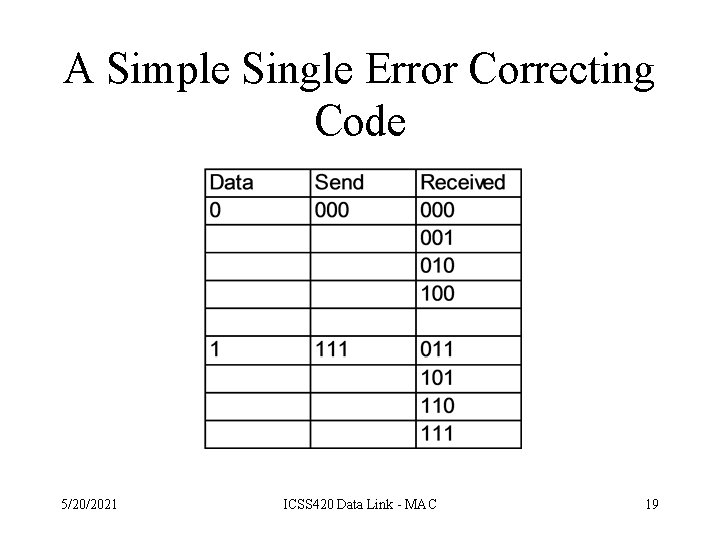
A Simple Single Error Correcting Code 5/20/2021 ICSS 420 Data Link - MAC 19

Hamming Codes • Hamming codes are n-bit codes that can correct single errors. • The basic idea is to split the codeword into two portions – information or message bits (m) – parity bits (k) • The result are codewords that consist of m+k bits 5/20/2021 ICSS 420 Data Link - MAC 20

Choosing m and k • Selecting m is easy, you are usually told what it is. • How do you pick k? • The parity bits are used to generate a k-bit word that identifies where in the codeword the error, if any, occurred. • Consequently, k must satisfy the following: 5/20/2021 ICSS 420 Data Link - MAC 21

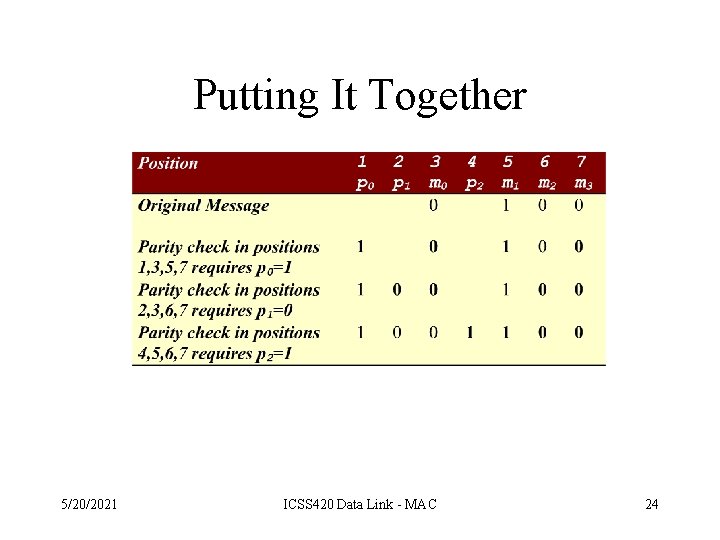
Constructing the Codeword • The codeword consists of m+k bits. • The location of each of the m+k bits is assigned a decimal value, 1 is assigned to the MSB, and m+k to the LSB. • Parity bits go in positions 1, 2, 4, …, 2 k-1 p 0 p 1 m 0 p 2 m 1 m 2 m 3 p 3 m 4. . . mm+k 1 5/20/2021 2 3 4 5 6 7 8 ICSS 420 Data Link - MAC 9 . . . m+k 22

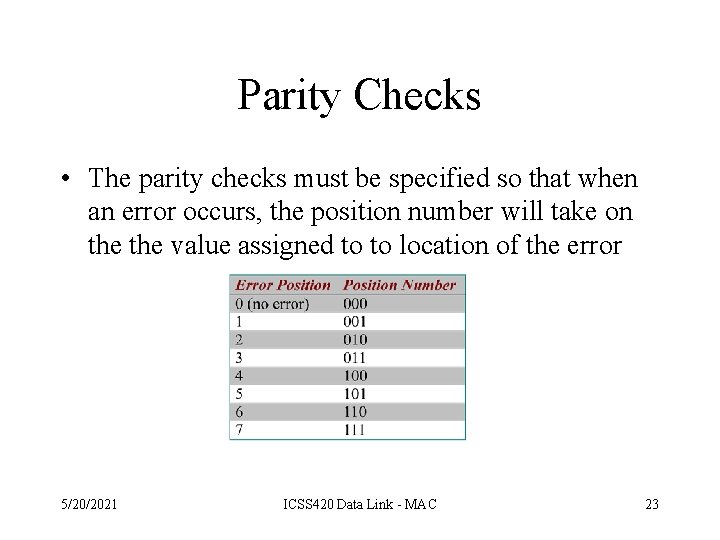
Parity Checks • The parity checks must be specified so that when an error occurs, the position number will take on the value assigned to to location of the error 5/20/2021 ICSS 420 Data Link - MAC 23

Putting It Together 5/20/2021 ICSS 420 Data Link - MAC 24

Example Send the message 0010 using a hamming code Step 1: Find k. Here k=3 Step 2: Determine where things go Step 3: Figure out the parity bits p 1 will cover 1, 3, 5, 7, 9, 11, … p 2 will cover 2, 3, 6, 7, 10, 11, … p 3 will cover 4, 5, 6, 7, 12, 13, 14, 15, . . . 5/20/2021 ICSS 420 Data Link - MAC 25

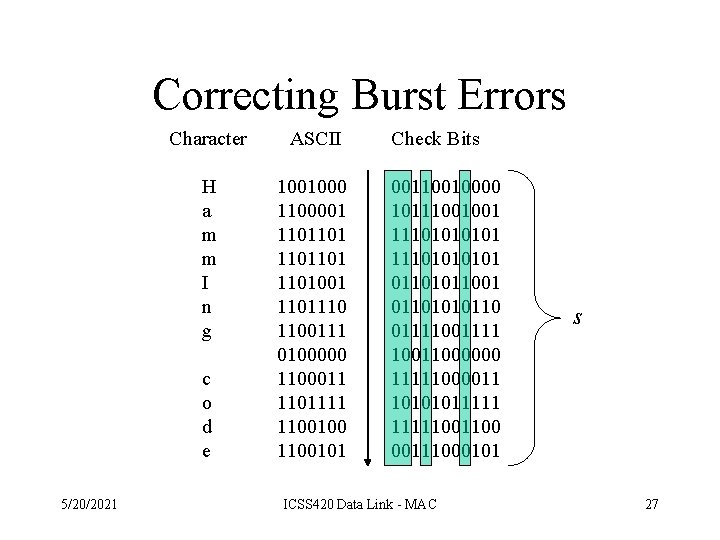
Correcting Burst Errors • Hamming codes can be used to correct burst errors • A sequence of s consecutive codewords are arranged as a matrix, one codeword per row. • Transmit data one column (s bits) at a time. • The matrix is reconstructed by the receiver one column at a time. • If a burst error of size s occurs, only a single column will be affected. 5/20/2021 ICSS 420 Data Link - MAC 26

Correcting Burst Errors Character ASCII H a m m I n g 1001000 1100001 1101101001 1101110 1100111 0100000 1100011 1101111 1100100 1100101 c o d e 5/20/2021 Check Bits 00110010000 10111001001 11101010101 01101011001 01101010110 01111001111 10011000000 11111000011 1010101111100 00111000101 ICSS 420 Data Link - MAC s 27

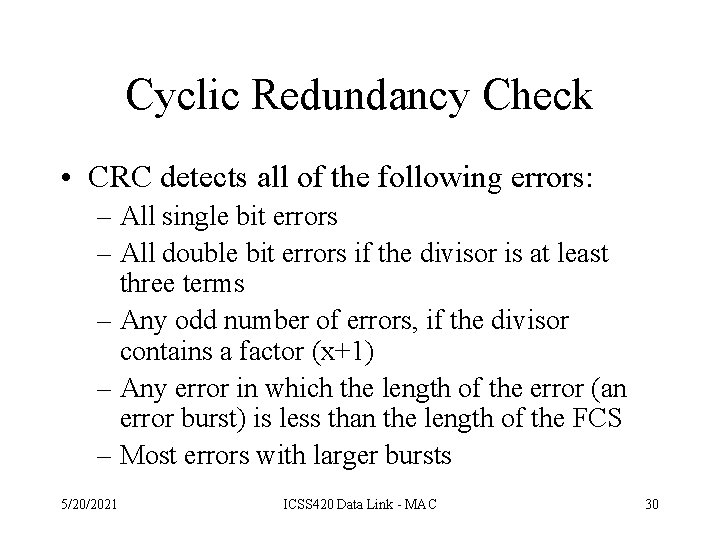
Correcting vs. Detecting • Most often error detection followed by retransmission is more efficient. • Consider a channel with an error rate is 10 -6 per bit (one error per million bits sent) – Block size 1000 == 10 check bits ( k == 10 ) – For parity one check bit will suffice • Overhead for sending 1 MB – Hamming == 10, 000 bits – Parity == 2001 bits (since 1 block will be retransmitted) 5/20/2021 ICSS 420 Data Link - MAC 28

Cyclic Redundancy Check • The transmitter generates a bit pattern called a Frame Check Sequence (FCS), based on the contents of the frame. • The combined contents of the frame and the FCS are exactly divisible by some predetermined polynomial. • If the contents of the frame are damaged during transmission, the receiver’s division will yield a non-zero remainder. 5/20/2021 ICSS 420 Data Link - MAC 29

Cyclic Redundancy Check • CRC detects all of the following errors: – All single bit errors – All double bit errors if the divisor is at least three terms – Any odd number of errors, if the divisor contains a factor (x+1) – Any error in which the length of the error (an error burst) is less than the length of the FCS – Most errors with larger bursts 5/20/2021 ICSS 420 Data Link - MAC 30

Polynomials • CRC is based upon treating bit strings as representations of polynomials with coefficients of 0 and 1 only. – 11001 == x 5+ x 4+ x 0 • A k-bit frame is regarded as the coefficient list for a polynomial with k terms, ranging from xk-1 to x 0 5/20/2021 ICSS 420 Data Link - MAC 31

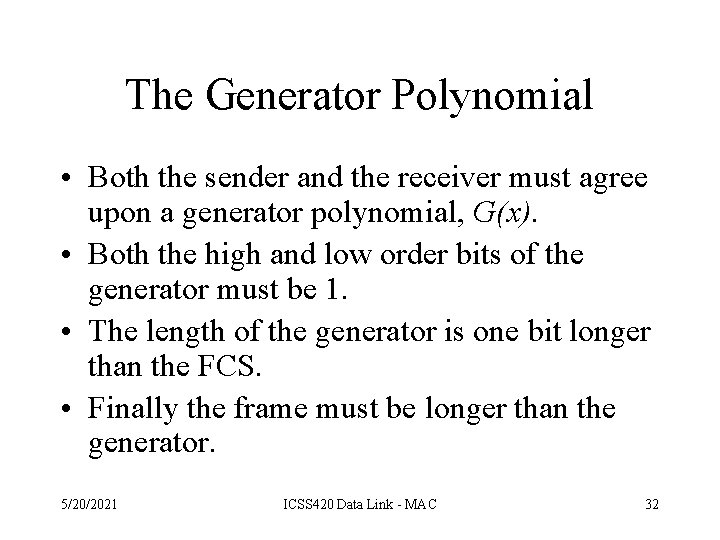
The Generator Polynomial • Both the sender and the receiver must agree upon a generator polynomial, G(x). • Both the high and low order bits of the generator must be 1. • The length of the generator is one bit longer than the FCS. • Finally the frame must be longer than the generator. 5/20/2021 ICSS 420 Data Link - MAC 32

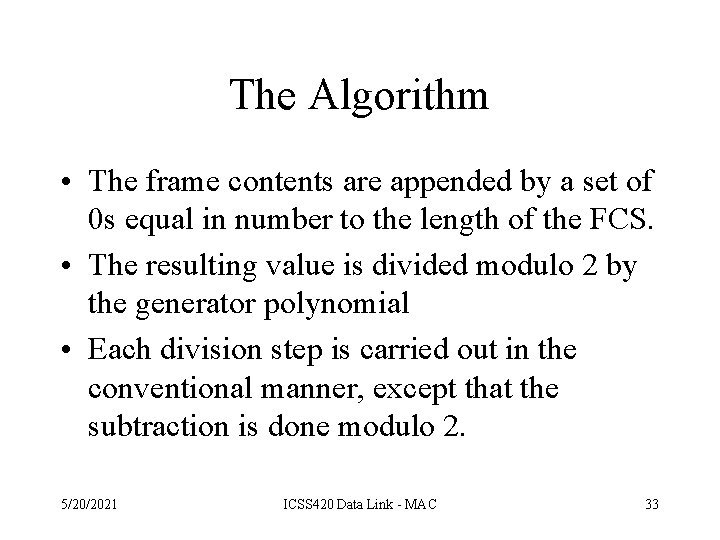
The Algorithm • The frame contents are appended by a set of 0 s equal in number to the length of the FCS. • The resulting value is divided modulo 2 by the generator polynomial • Each division step is carried out in the conventional manner, except that the subtraction is done modulo 2. 5/20/2021 ICSS 420 Data Link - MAC 33

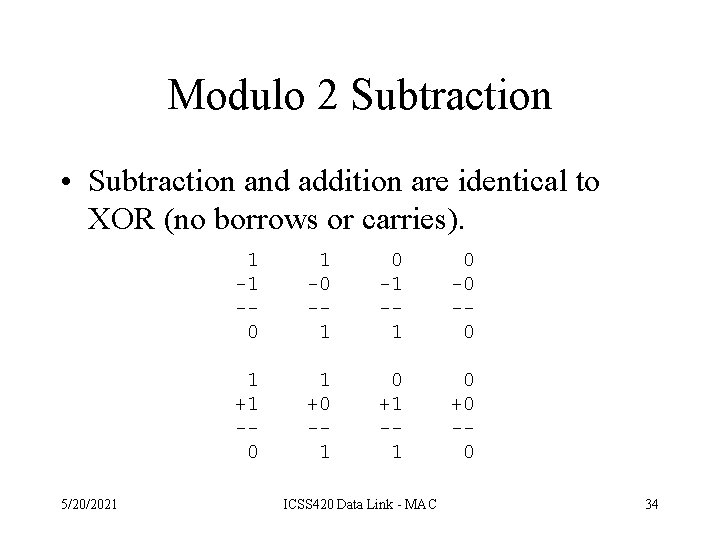
Modulo 2 Subtraction • Subtraction and addition are identical to XOR (no borrows or carries). 5/20/2021 1 -1 -0 -1 -1 0 -0 -0 1 +1 -0 1 +0 -1 0 +1 -1 0 +0 -0 ICSS 420 Data Link - MAC 34

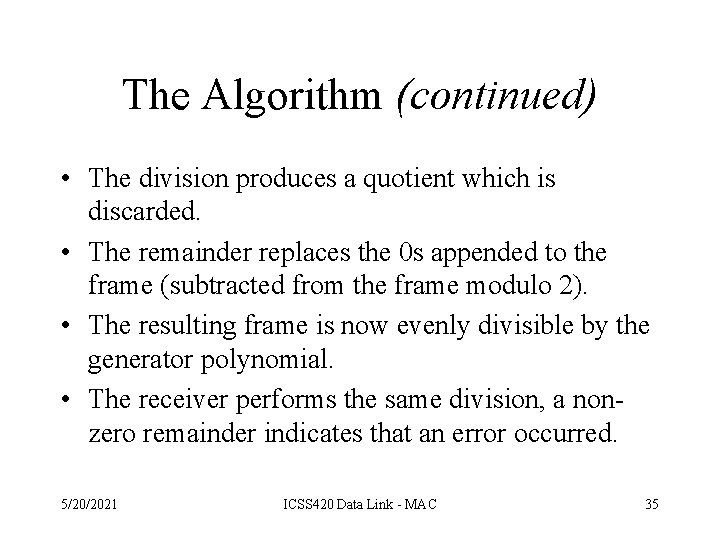
The Algorithm (continued) • The division produces a quotient which is discarded. • The remainder replaces the 0 s appended to the frame (subtracted from the frame modulo 2). • The resulting frame is now evenly divisible by the generator polynomial. • The receiver performs the same division, a nonzero remainder indicates that an error occurred. 5/20/2021 ICSS 420 Data Link - MAC 35

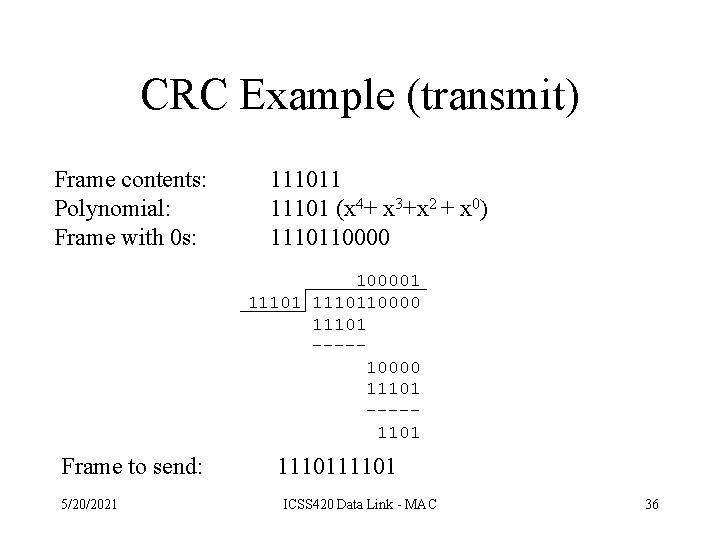
CRC Example (transmit) Frame contents: Polynomial: Frame with 0 s: 111011 11101 (x 4+ x 3+x 2 + x 0) 11101100001 1110110000 11101 ----1101 Frame to send: 5/20/2021 11101 ICSS 420 Data Link - MAC 36

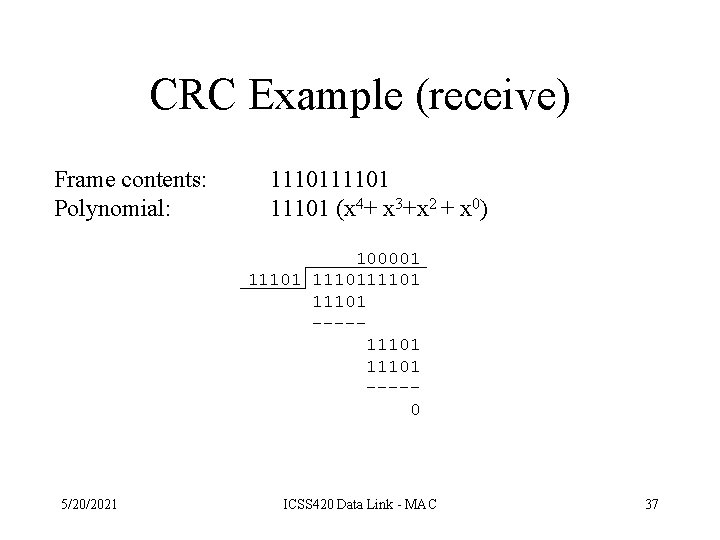
CRC Example (receive) Frame contents: Polynomial: 11101 (x 4+ x 3+x 2 + x 0) 100001 1110111101 ----0 5/20/2021 ICSS 420 Data Link - MAC 37

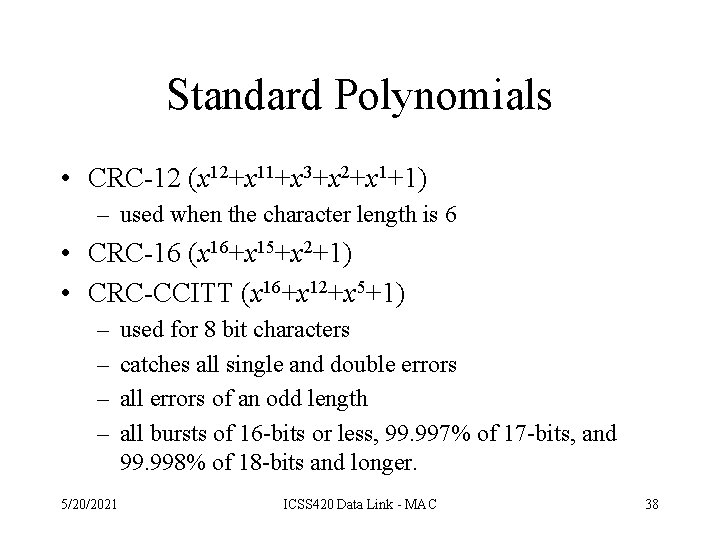
Standard Polynomials • CRC-12 (x 12+x 11+x 3+x 2+x 1+1) – used when the character length is 6 • CRC-16 (x 16+x 15+x 2+1) • CRC-CCITT (x 16+x 12+x 5+1) – – 5/20/2021 used for 8 bit characters catches all single and double errors all errors of an odd length all bursts of 16 -bits or less, 99. 997% of 17 -bits, and 99. 998% of 18 -bits and longer. ICSS 420 Data Link - MAC 38

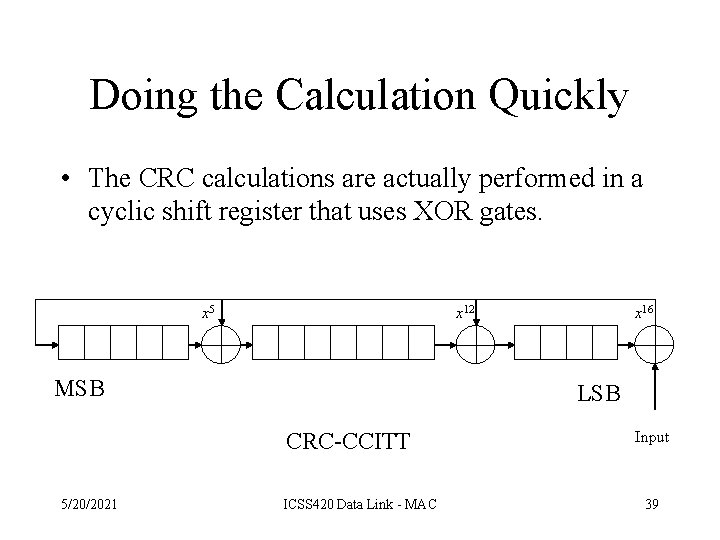
Doing the Calculation Quickly • The CRC calculations are actually performed in a cyclic shift register that uses XOR gates. x 5 x 12 MSB LSB CRC-CCITT 5/20/2021 x 16 ICSS 420 Data Link - MAC Input 39

Warning • All the analysis that has been done on CRC techniques assume the frames contain random bits. • Real data, however, is not all that random. • As a consequence, under some circumstances, undetected errors are much more common than had been previously thought. 5/20/2021 ICSS 420 Data Link - MAC 40

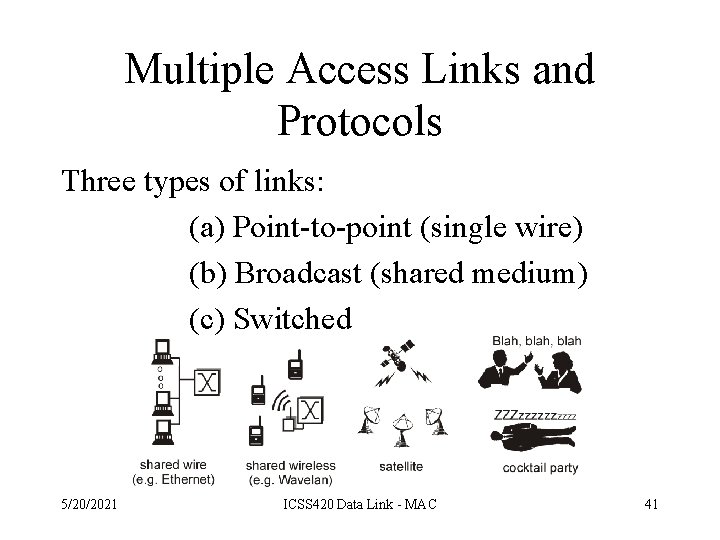
Multiple Access Links and Protocols Three types of links: (a) Point-to-point (single wire) (b) Broadcast (shared medium) (c) Switched 5/20/2021 ICSS 420 Data Link - MAC 41

Multiple Access Control (MAC) Protocols • MAC protocol: coordinates transmissions from different stations in order to minimize/avoid collisions – Channel Partitioning MAC protocols – Random Access MAC protocols – “Taking turns” MAC protocols • Goal: efficient, fair, simple, decentralized 5/20/2021 ICSS 420 Data Link - MAC 42

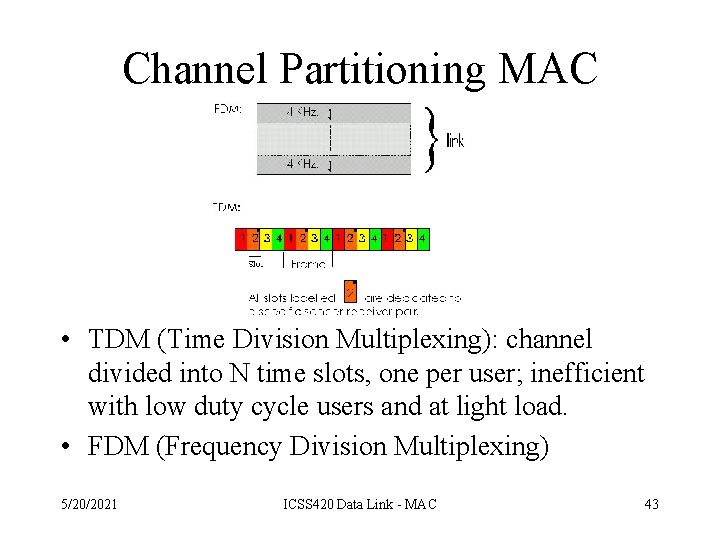
Channel Partitioning MAC protocols • TDM (Time Division Multiplexing): channel divided into N time slots, one per user; inefficient with low duty cycle users and at light load. • FDM (Frequency Division Multiplexing) 5/20/2021 ICSS 420 Data Link - MAC 43

Cocktail Party Analogy • TDM – Everyone stands in the middle of the room, taking turns talking • FDM – People group into widely separated clumps, each clumping holding a conversation at the same time, but still independent of the others. 5/20/2021 ICSS 420 Data Link - MAC 44

Code Division Multiple Access • CDMA – Used widely in wireless technologies – Allows each station to transmit using the same frequency • Cocktail party example – Everyone is talking at the same time, but in different languages 5/20/2021 ICSS 420 Data Link - MAC 45

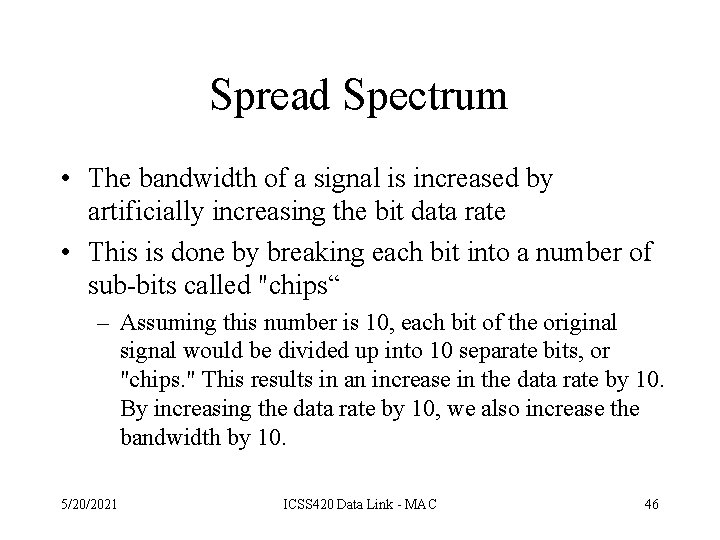
Spread Spectrum • The bandwidth of a signal is increased by artificially increasing the bit data rate • This is done by breaking each bit into a number of sub-bits called "chips“ – Assuming this number is 10, each bit of the original signal would be divided up into 10 separate bits, or "chips. " This results in an increase in the data rate by 10. By increasing the data rate by 10, we also increase the bandwidth by 10. 5/20/2021 ICSS 420 Data Link - MAC 46

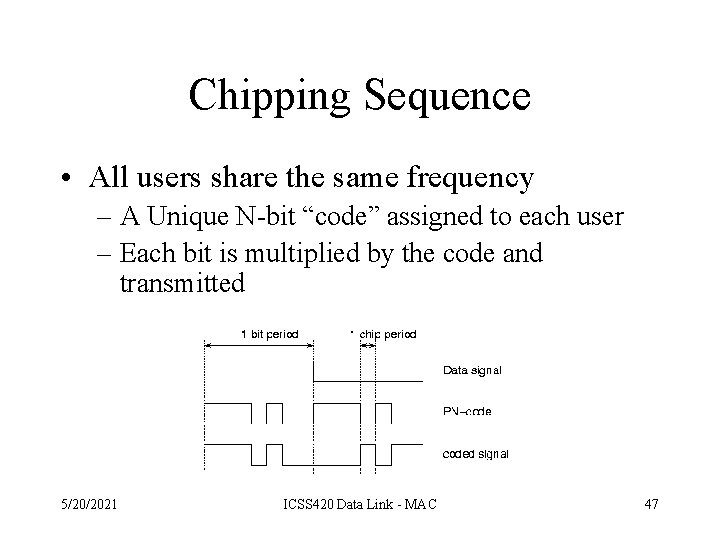
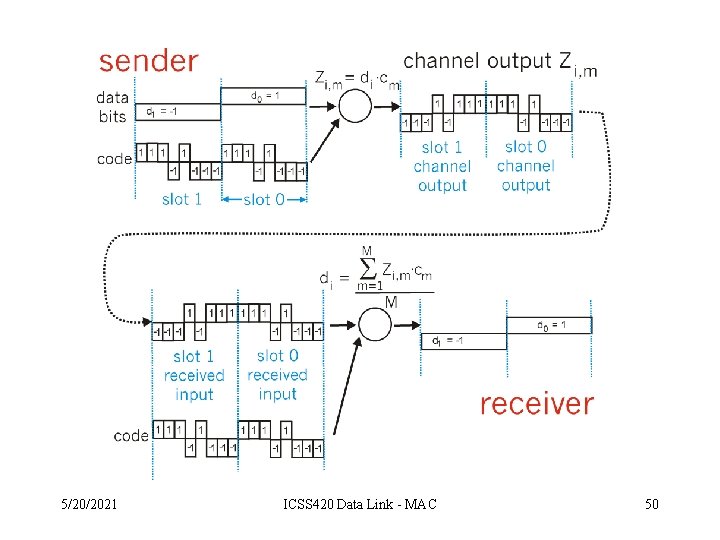
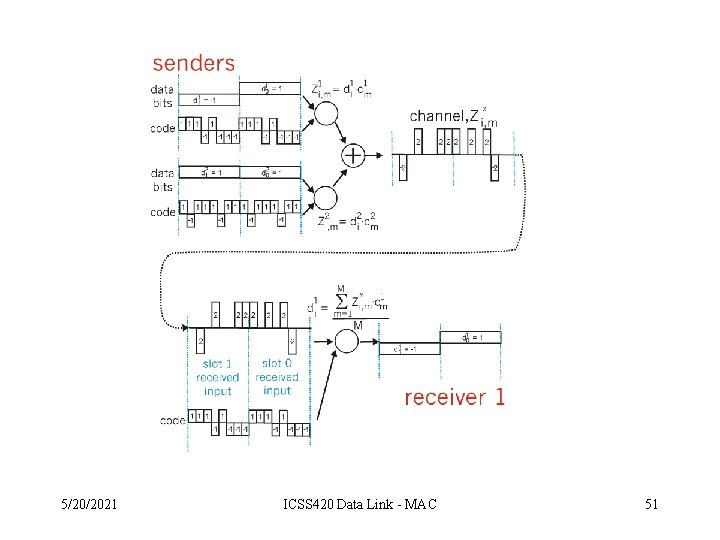
Chipping Sequence • All users share the same frequency – A Unique N-bit “code” assigned to each user – Each bit is multiplied by the code and transmitted 5/20/2021 ICSS 420 Data Link - MAC 47

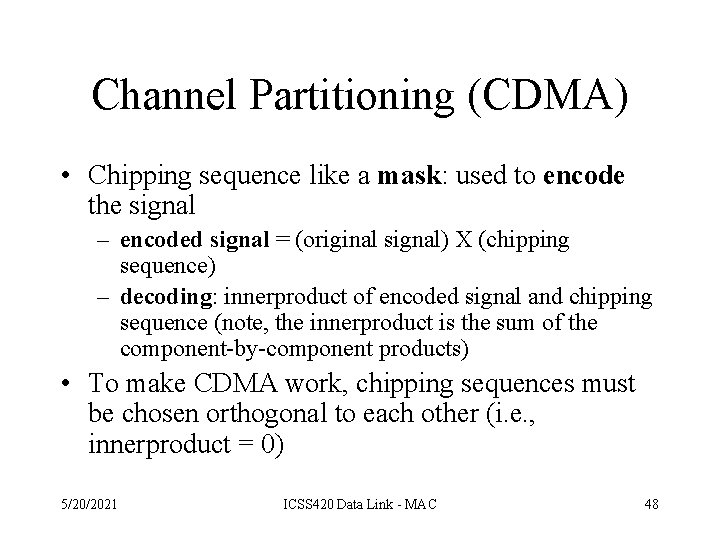
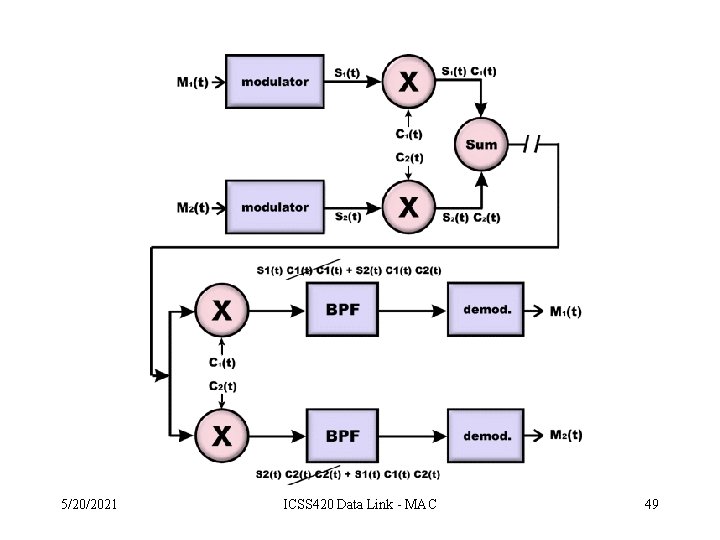
Channel Partitioning (CDMA) • Chipping sequence like a mask: used to encode the signal – encoded signal = (original signal) X (chipping sequence) – decoding: innerproduct of encoded signal and chipping sequence (note, the innerproduct is the sum of the component-by-component products) • To make CDMA work, chipping sequences must be chosen orthogonal to each other (i. e. , innerproduct = 0) 5/20/2021 ICSS 420 Data Link - MAC 48

5/20/2021 ICSS 420 Data Link - MAC 49

5/20/2021 ICSS 420 Data Link - MAC 50

5/20/2021 ICSS 420 Data Link - MAC 51

CDMA (cont’d) CDMA Properties: • protects users from interference and jamming (used in WW II) • protects users from radio multipath fading • allows multiple users to “coexist” and transmit simultaneously with minimal interference (if codes are “orthogonal”) 5/20/2021 ICSS 420 Data Link - MAC 52

Random Access protocols • A node transmits at random at full channel data rate R. • If two or more nodes “collide”, they retransmit • The random access MAC protocol specifies how to detect collisions and how to recover from them • Examples of random access MAC protocols: – SLOTTED ALOHA – CSMA and CSMA/CD 5/20/2021 ICSS 420 Data Link - MAC 53

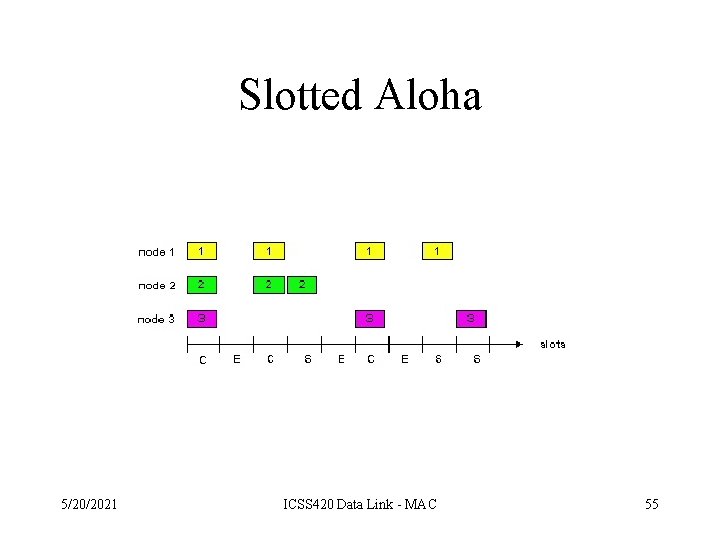
Slotted Aloha • Time is divided into equal size slots (= full packet size) • a newly arriving station transmits a the beginning of the next slot • if collision occurs the source retransmits the packet at each slot with probability P • S-ALOHA is channel utilization efficient; it is fully decentralized. 5/20/2021 ICSS 420 Data Link - MAC 54

Slotted Aloha 5/20/2021 ICSS 420 Data Link - MAC 55

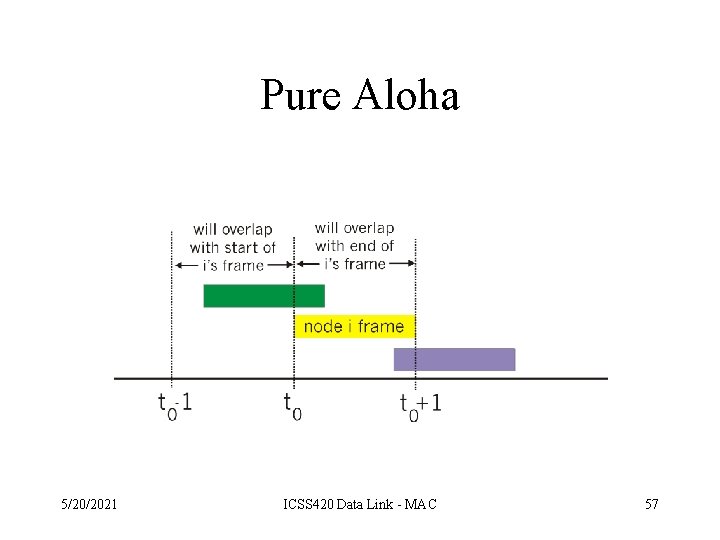
Pure (unslotted) ALOHA • Slotted ALOHA requires slot synchronization • A simpler version, pure ALOHA, does not require slots • A node transmits without waiting for the beginning of a slot • Collision probability increases (packet can collide with other packets which are transmitted within a window twice as large as in S-Aloha) • Throughput is reduced by one half 5/20/2021 ICSS 420 Data Link - MAC 56

Pure Aloha 5/20/2021 ICSS 420 Data Link - MAC 57

Carrier Sense Multiple Access • CSMA: listen before transmit. If channel is sensed busy, defer transmission – Persistent CSMA: retry immediately when channel becomes idle (this may cause instability) – Non persistent CSMA: retry after random interval • Collisions may still exist, since two stations may sense the channel idle at the same time • In case of collision, the entire packet transmission time is wasted 5/20/2021 ICSS 420 Data Link - MAC 58

“Taking Turns” MAC protocols • So far we have seen that channel partitioning MAC protocols (TDM, FDM and CDMA) can share the channel fairly; but a single station cannot use it all • Random access MAC protocols allow a single user full channel rate; but cannot share the channel fairly (in fact, capture is often observed) • Also there are “taking turns” protocols. . . 5/20/2021 ICSS 420 Data Link - MAC 59

“Taking Turns” MAC protocols • Taking Turns MAC protocols achieve both fairness and full rate, at the expense of some extra control overhead – Polling: a Master station on a LAN in turn “invites” the slave stations to transmit their packets. Problems: Request to Send/Clear to Send overhead, latency, single point of failure (Master) – Token passing: the control token is passed from one node to the next sequentially. Can alleviate the latency and improve fault tolerance Still, elaborate procedures to recover from lost token, etc. 5/20/2021 ICSS 420 Data Link - MAC 60

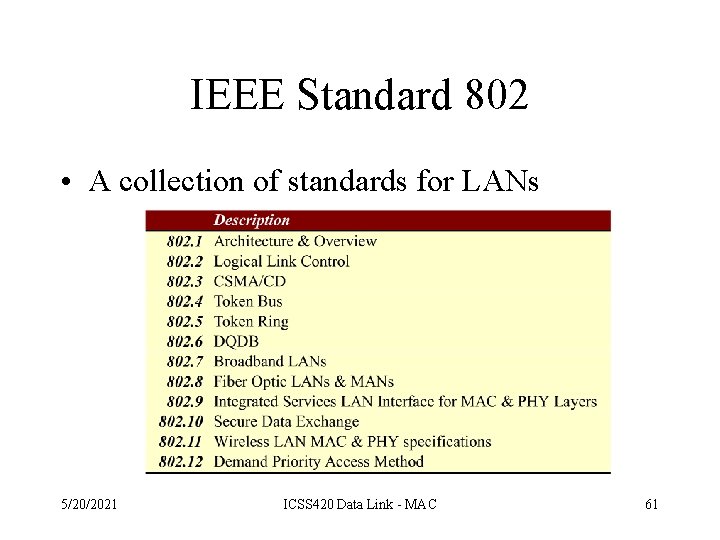
IEEE Standard 802 • A collection of standards for LANs 5/20/2021 ICSS 420 Data Link - MAC 61

802. 3 - CSMA/CD • The 802. 3 standard encompasses both the MAC layer and the physical layer. • This standard is for a 1 -persistent CSMA/CD LAN. • Xerox developed a CSMA/CD system to connect personal workstations. This system was called Ethernet. • Ethernet is often used to refer to all CSMA/CD protocols. 5/20/2021 ICSS 420 Data Link - MAC 62

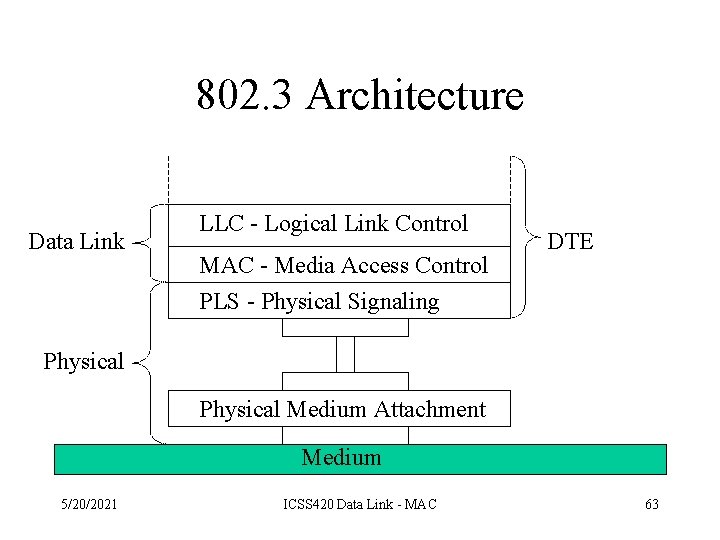
802. 3 Architecture Data Link LLC - Logical Link Control MAC - Media Access Control PLS - Physical Signaling DTE Physical Medium Attachment Medium 5/20/2021 ICSS 420 Data Link - MAC 63

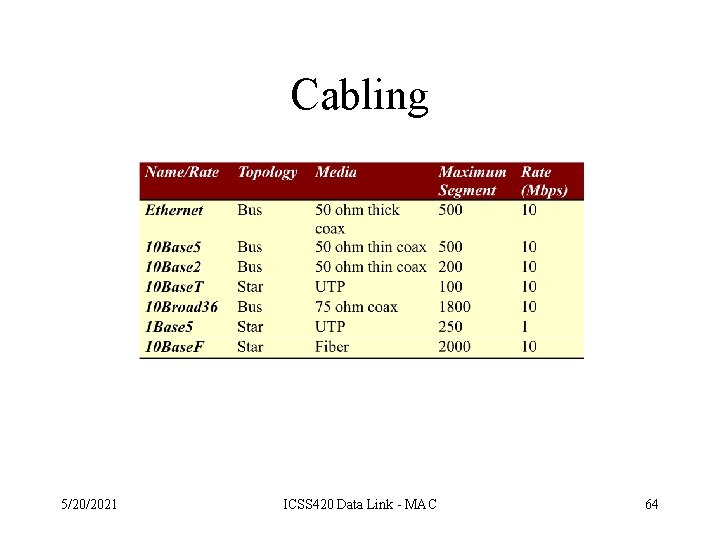
Cabling 5/20/2021 ICSS 420 Data Link - MAC 64

802. 3 Addresses • Every machine on a 802. 3 network is assigned a unique physical address – the address is typically defined in hardware and cannot be changed • This address is often referred to as a MAC address. • MAC addresses can vary in size – 48 bits is a common length for a MAC address 5/20/2021 ICSS 420 Data Link - MAC 65

Performance • As more and more stations are added to an 802. 3 LAN, the traffic will go up, and eventually the LAN will saturate. • What do you do? – Faster LAN? – Segment your LAN 5/20/2021 ICSS 420 Data Link - MAC 66

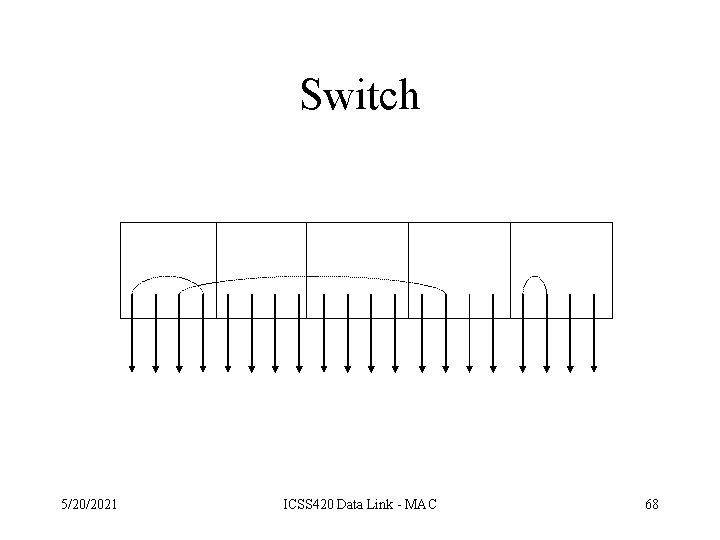
Switched 802. 3 LANs • The main component of this system is a box containing a high-speed backplane and room for plug in adapter cards. • A station does what it always does. • When the switch sees the packet – if destined for a machine on the same card send it to the appropriate station – else ship it using the high-speed backplane to the card that handles that station 5/20/2021 ICSS 420 Data Link - MAC 67

Switch 5/20/2021 ICSS 420 Data Link - MAC 68

Collisions • How are collisions handled? – One possibility is to wire each card so that it forms a local on-card LAN. • Only one transmission per card is possible, but all the cards can transmit in parallel. – Buffer each input port, so incoming frames are stored in RAM as they arrive. • Collisions do not occur. 5/20/2021 ICSS 420 Data Link - MAC 69

Topology Issues • The original Ethernet specification was for a bus topology – only one channel – if the cable breaks the whole network is down • Today most organizations install 10 Base. T – star topology – machines connect to hubs 5/20/2021 ICSS 420 Data Link - MAC 70

Concerns About 802. 3 • During the development of the 802 standard, people doing networking on factory floors had serious reservations about it. • Due to the probabilistic MAC protocol, a station may have to wait arbitrarily long to send a frame. • In a real time system time, timing is critical. • A simple solution is to form a ring, in which stations take turns sending frames. No frame will have to wait more than n. T seconds. 5/20/2021 ICSS 420 Data Link - MAC 71

802. 4 Token Bus • Physically, the token bus is a linear or tree-shaped cable onto which stations are attached. • Logically, the stations are arranged in a ring. • Each station has an address and knows the address of the machine to its “left” and “right”. • When the ring starts, the highest numbered machine sends. • Permission to send is then sent around the ring. 5/20/2021 ICSS 420 Data Link - MAC 72

Tokens • A control frame known as a token regulates the right of access. • The token frame contains a destination address. • The station receiving the token is granted control of the medium for up to some maximum time. • The token must be passed when: – The station has no (more) data to send – The station’s time expires 5/20/2021 ICSS 420 Data Link - MAC 73

FDDI • FDDI was developed to support high-capacity LANs (operates at 100 Mbps). • Is typically used as a backbone to connect copper LANs. • Uses multimode optical fibers and LEDs (as opposed to laser). • The cabling consists of two fiber rings, one transmitting clockwise and the other counterclockwise. 5/20/2021 ICSS 420 Data Link - MAC 74

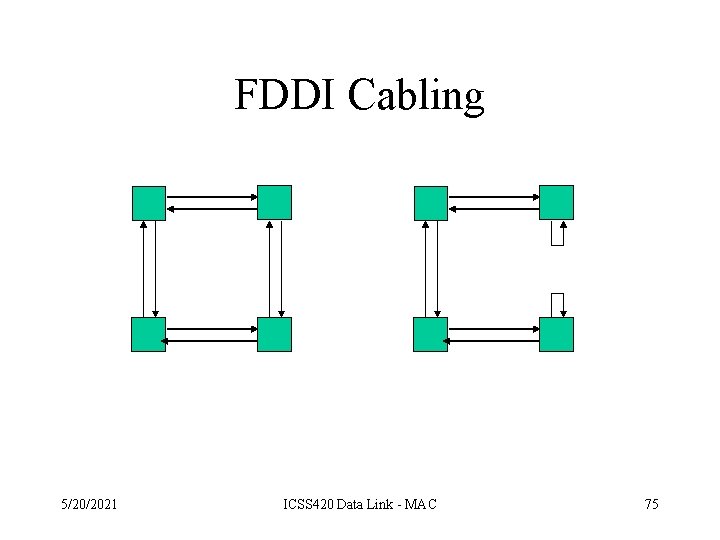
FDDI Cabling 5/20/2021 ICSS 420 Data Link - MAC 75

Hubs • Hubs provide a single connection between each workstation and the hub • The connection is typically made over twisted pair cabling • Hubs typically have a fixed number of ports. Common sizes are 8 and 16 port hubs. • Hubs can be daisy chained (up to a limit) to provide more ports for connections 5/20/2021 ICSS 420 Data Link - MAC 76

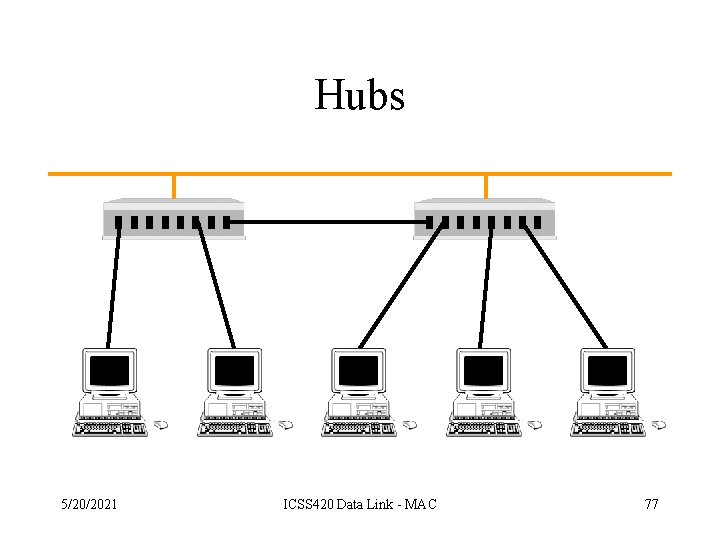
Hubs 5/20/2021 ICSS 420 Data Link - MAC 77

Working with Hubs • There is a limit to the number of hubs that can be connected together to extend a network (a typical maximum is 4) • When possible, connect each hub directly to the backbone or a server • Label the connections on the hub • The more hubs data passes through, the slower the connection 5/20/2021 ICSS 420 Data Link - MAC 78

Passive Hubs • A passive hub simply combines the signals of network segments • The passive hub absorbs some of the signal and reduces in half the maximum cabling distance permitted • Passive hubs pass received signals onto to all the computers connected to the hub 5/20/2021 ICSS 420 Data Link - MAC 79

Active Hubs • Active hubs have electronic components that regenerate or amplify signals • Distances supported by active hubs are greater than those of passive hubs • The main drawback is that they amplify noise as well as the signal • Because active hubs function as repeaters, they are sometimes called multiport repeaters 5/20/2021 ICSS 420 Data Link - MAC 80

Intelligent Hubs • In addition to signal regeneration, intelligent hubs perform some network management and intelligent path selection • A switching hub chooses only the port of the device where the signal needs to go, rather than sending the signal along all paths • Many switching hubs can choose which alternative path will be the quickest and send the signal that way 5/20/2021 ICSS 420 Data Link - MAC 81

Making LANs Bigger • Usually it does not take too long until an organization needs to expand a LAN. • This can be done in a number of ways – physically make the cable longer – use repeaters – use bridges • The primary difference between a repeater and a bridge is the OSI level that they operate at. 5/20/2021 ICSS 420 Data Link - MAC 82

Repeaters • All transmission media attenuate (weaken) the signals that travel through them • Attenuation is one of the things that limit the distance any medium can carry data • Adding a device that amplifies the signal can allow it to travel further, increasing the size of the network • Devices that amplify signals are called repeaters 5/20/2021 ICSS 420 Data Link - MAC 83

Repeaters • A repeater is an electronic device that receives an electronic signal from a cable and sends it out on another cable segment. • Repeaters are simple devices because they do not need to understand what they receive. Signals are simply retransmitted. • A repeater is used when the physical length of the cable has reached its maximum. 5/20/2021 ICSS 420 Data Link - MAC 84

Repeaters • Repeaters fall into two categories – amplifiers simply amplify the entire incoming signal (which includes noise) – signal regenerating repeaters create an exact duplicate of incoming data by identifying the signal amidst the noise, reconstructs it, and retransmits only the signal • Since repeaters simply deal with the actual signals on a network, they operate at the physical layer of the OSI model 5/20/2021 ICSS 420 Data Link - MAC 85

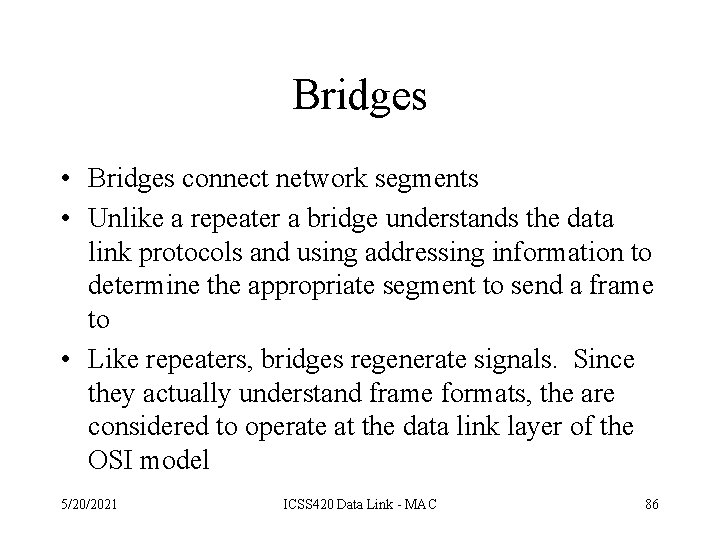
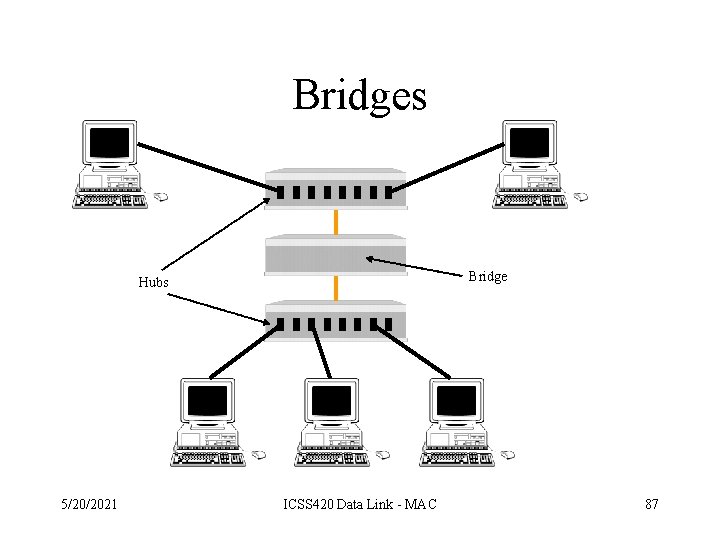
Bridges • Bridges connect network segments • Unlike a repeater a bridge understands the data link protocols and using addressing information to determine the appropriate segment to send a frame to • Like repeaters, bridges regenerate signals. Since they actually understand frame formats, the are considered to operate at the data link layer of the OSI model 5/20/2021 ICSS 420 Data Link - MAC 86

Bridges Bridge Hubs 5/20/2021 ICSS 420 Data Link - MAC 87

Bridges • How a bridge handles traffic – receives all signals from segments A and B – the bridge filters all packets from segment A addressed to segment A (and likewise for segment B) – signals from A to B are retransmitted to segment B – signals form B to A are retransmitted to segment A • Through address filtering, bridges can divide busy networks into segments and reduce traffic 5/20/2021 ICSS 420 Data Link - MAC 88

Problems that Bridges Deal With • Each LAN uses a different frame format – any copying between different LANs requires reformatting • All LANs do not necessarily run at the same rate. • All three 802 LANs have a different maximum frame length. – Frames that are too large to be forwarded must be discarded. • Many problems going from 802. x to 802. y 5/20/2021 ICSS 420 Data Link - MAC 89

Routers • Routers are devices that connect two or more networks • They consist of hardware and software – the hardware can be a network server, a PC, or a special black box – The software components consist of an operating system and routing software • Routers operate at the network layer of the OSI reference model 5/20/2021 ICSS 420 Data Link - MAC 90

Routing 5/20/2021 ICSS 420 Data Link - MAC 91