Computer Security Professor Jennifer Rexford CS 217 1

![Attacking a Web Server • URLs • Input in web forms for(i=0; p[i]; i++) Attacking a Web Server • URLs • Input in web forms for(i=0; p[i]; i++)](https://slidetodoc.com/presentation_image_h2/bca7ff19a6fe0e3dbdafa9583920fa95/image-15.jpg)
![Attacking a Web Browser • HTML keywords • Images for(i=0; p[i]; i++) gif[i]=p[i]; • Attacking a Web Browser • HTML keywords • Images for(i=0; p[i]; i++) gif[i]=p[i]; •](https://slidetodoc.com/presentation_image_h2/bca7ff19a6fe0e3dbdafa9583920fa95/image-16.jpg)
![Attacking everything in sight for(i=0; p[i]; i++) gif[i]=p[i]; Client PC The Internet @ badguy. Attacking everything in sight for(i=0; p[i]; i++) gif[i]=p[i]; Client PC The Internet @ badguy.](https://slidetodoc.com/presentation_image_h2/bca7ff19a6fe0e3dbdafa9583920fa95/image-17.jpg)




- Slides: 32

Computer Security Professor Jennifer Rexford CS 217 1

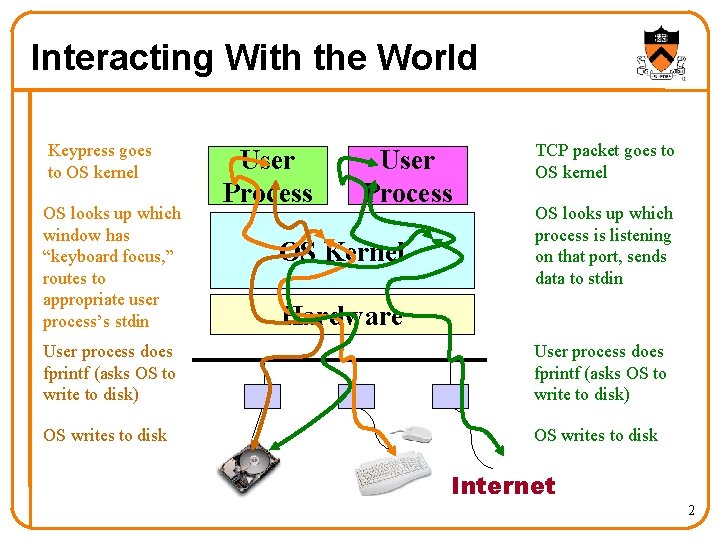
Interacting With the World Keypress goes to OS kernel OS looks up which window has “keyboard focus, ” routes to appropriate user process’s stdin User Process OS Kernel TCP packet goes to OS kernel OS looks up which process is listening on that port, sends data to stdin Hardware User process does fprintf (asks OS to write to disk) OS writes to disk Internet 2

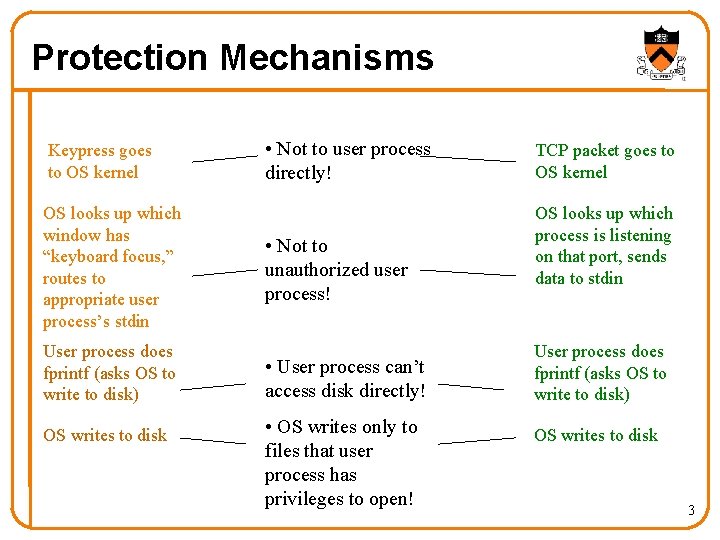
Protection Mechanisms Keypress goes to OS kernel OS looks up which window has “keyboard focus, ” routes to appropriate user process’s stdin User process does fprintf (asks OS to write to disk) OS writes to disk • Not to user process directly! • Not to unauthorized user process! • User process can’t access disk directly! • OS writes only to files that user process has privileges to open! TCP packet goes to OS kernel OS looks up which process is listening on that port, sends data to stdin User process does fprintf (asks OS to write to disk) OS writes to disk 3

User Processes Can’t Directly Access I/O • Input/output instructions are privileged instructions Trying to run them in unprivileged mode triggers trap to OS • Input/output device registers may be memory-mapped Virtual-memory system doesn’t map those pages into user space • Virtual-memory system prevents user process from modifying OS memory Can’t fool OS into performing unauthorized services • Virtual-memory prevents user processes from modifying each others’ memory Can’t fool other processes into writing bad data to its files on disk

How Attackers Defeat Protection • Make the protection mechanism fail By exploiting bugs in protection software • Operate politely through the protection mechanism Manipulating application semantics to obtain services By exploiting bad design of applications • Example: buffer overflow attacks Exploit a program that doesn’t perform bounds checking By presenting large input that runs past the array bounds … and craft that input to be executed as machine code 5

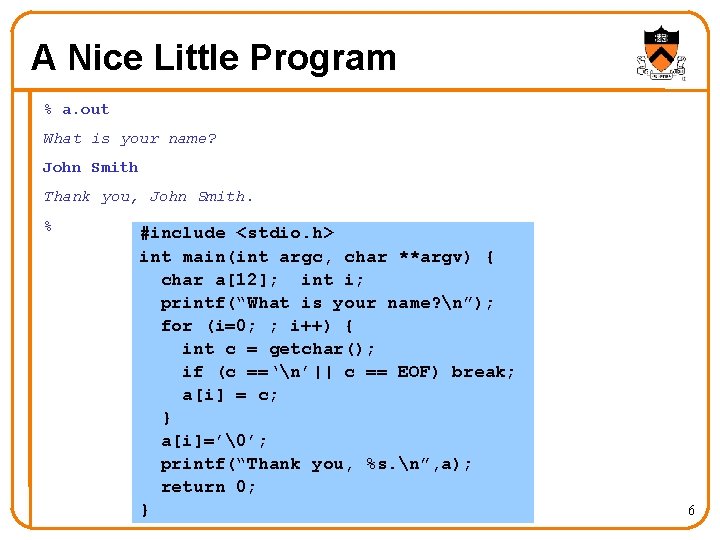
A Nice Little Program % a. out What is your name? John Smith Thank you, John Smith. % #include <stdio. h> int main(int argc, char **argv) { char a[12]; int i; printf(“What is your name? n”); for (i=0; ; i++) { int c = getchar(); if (c ==‘n’|| c == EOF) break; a[i] = c; } a[i]=’�’; printf(“Thank you, %s. n”, a); return 0; } 6

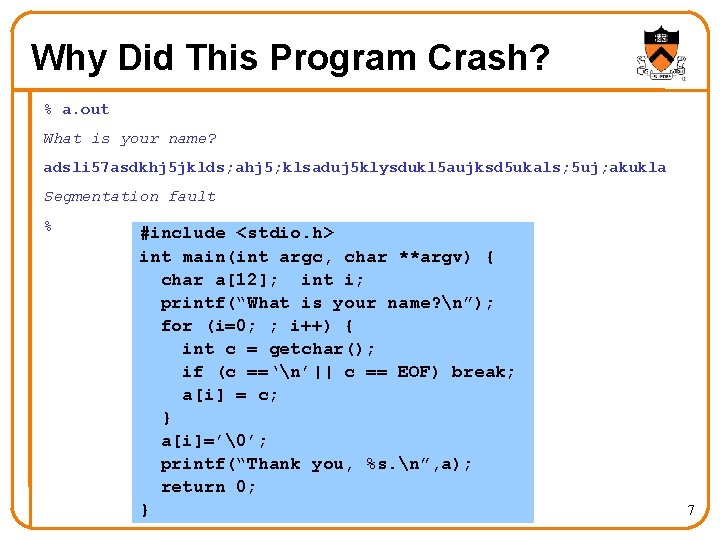
Why Did This Program Crash? % a. out What is your name? adsli 57 asdkhj 5 jklds; ahj 5; klsaduj 5 klysdukl 5 aujksd 5 ukals; 5 uj; akukla Segmentation fault % #include <stdio. h> int main(int argc, char **argv) { char a[12]; int i; printf(“What is your name? n”); for (i=0; ; i++) { int c = getchar(); if (c ==‘n’|| c == EOF) break; a[i] = c; } a[i]=’�’; printf(“Thank you, %s. n”, a); return 0; } 7

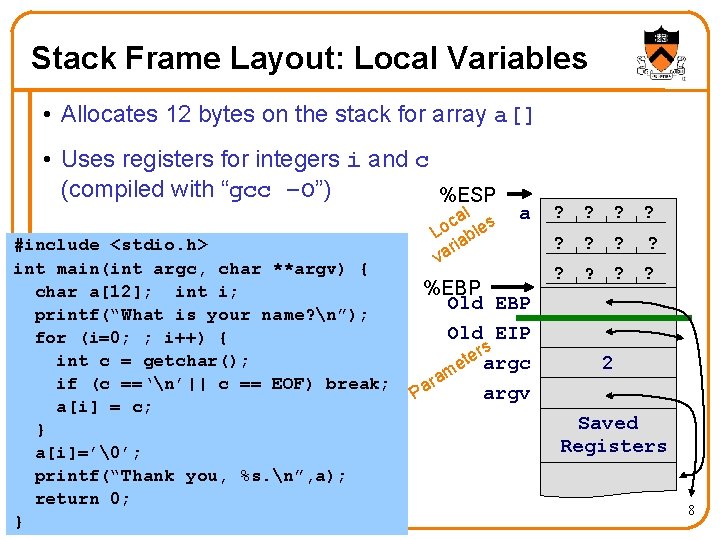
Stack Frame Layout: Local Variables • Allocates 12 bytes on the stack for array a[] • Uses registers for integers i and c (compiled with “gcc –O”) %ESP #include <stdio. h> int main(int argc, char **argv) { char a[12]; int i; printf(“What is your name? n”); for (i=0; ; i++) { int c = getchar(); if (c ==‘n’|| c == EOF) break; a[i] = c; } a[i]=’�’; printf(“Thank you, %s. n”, a); return 0; } al s c Lo able ri va a %EBP Old EIP rs e t e argc m ra argv Pa ? ? ? 2 Saved Registers 8

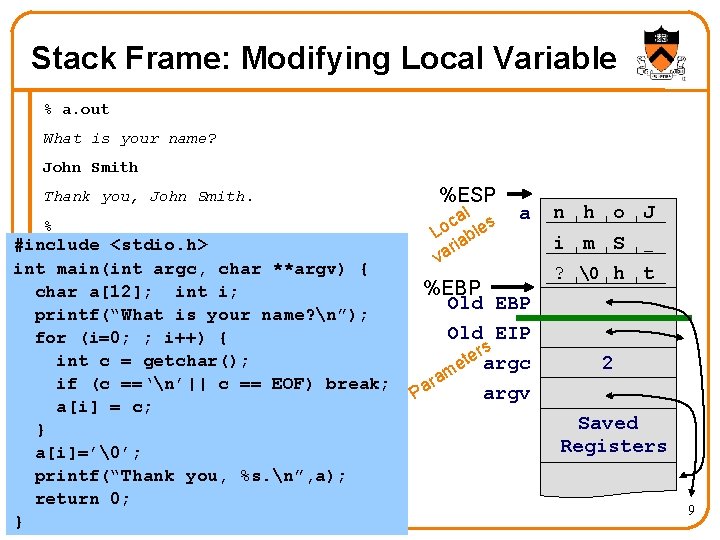
Stack Frame: Modifying Local Variable % a. out What is your name? John Smith Thank you, John Smith. % #include <stdio. h> int main(int argc, char **argv) { char a[12]; int i; printf(“What is your name? n”); for (i=0; ; i++) { int c = getchar(); if (c ==‘n’|| c == EOF) break; a[i] = c; } a[i]=’�’; printf(“Thank you, %s. n”, a); return 0; } %ESP al s c Lo able ri va a %EBP Old EIP rs e t e argc m ra argv Pa n h o J i m S _ ? � h t 2 Saved Registers 9

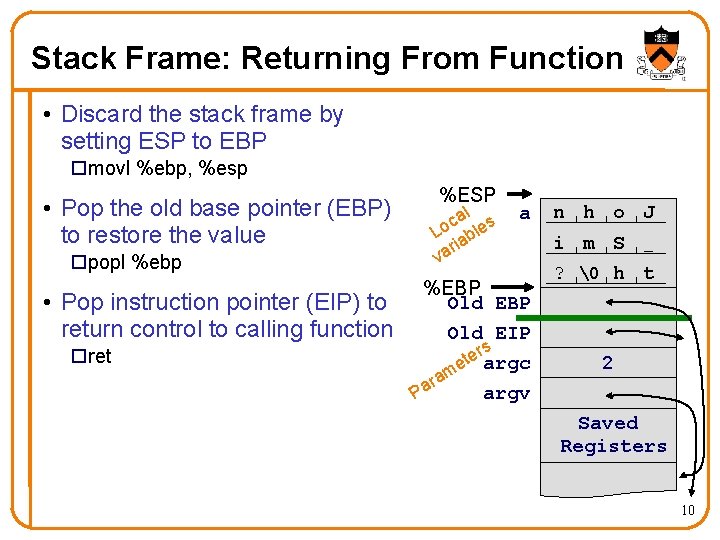
Stack Frame: Returning From Function • Discard the stack frame by setting ESP to EBP movl %ebp, %esp • Pop the old base pointer (EBP) to restore the value popl %ebp • Pop instruction pointer (EIP) to return control to calling function ret %ESP al s c Lo able ri va a %EBP Old EIP rs e t e argc m ra argv Pa n h o J i m S _ ? � h t 2 Saved Registers 10

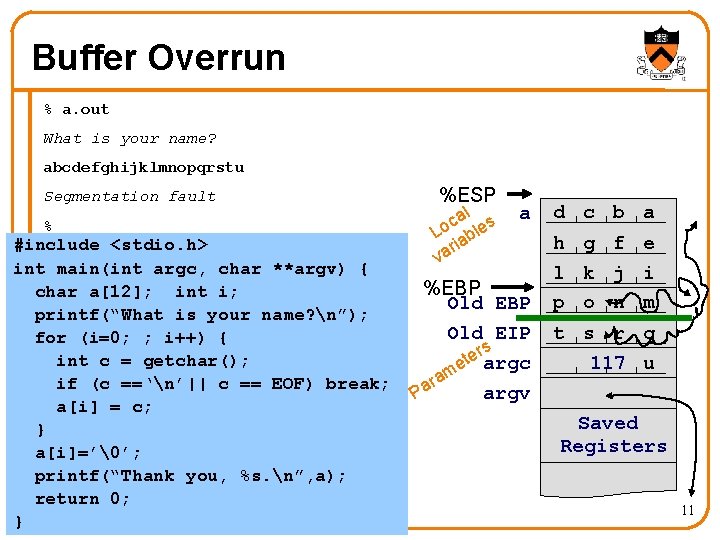
Buffer Overrun % a. out What is your name? abcdefghijklmnopqrstu Segmentation fault % #include <stdio. h> int main(int argc, char **argv) { char a[12]; int i; printf(“What is your name? n”); for (i=0; ; i++) { int c = getchar(); if (c ==‘n’|| c == EOF) break; a[i] = c; } a[i]=’�’; printf(“Thank you, %s. n”, a); return 0; } %ESP al s c Lo able ri va a %EBP Old EIP rs e t e argc m ra argv Pa d c b a h g f e l k j i p o n m t s r q 117 u Saved Registers 11

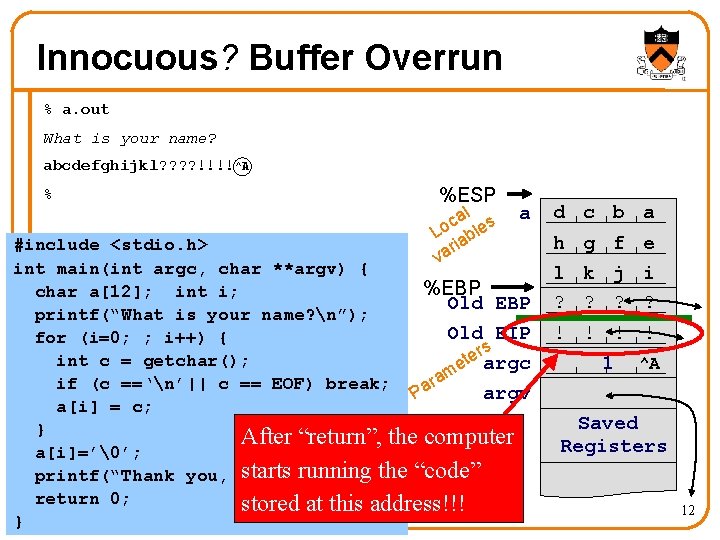
Innocuous? Buffer Overrun % a. out What is your name? abcdefghijkl? ? !!!!^A % %ESP a d c b a #include <stdio. h> int main(int argc, char **argv) { %EBP char a[12]; int i; Old EBP printf(“What is your name? n”); Old EIP for (i=0; ; i++) { rs e t int c = getchar(); e argc m ra if (c ==‘n’|| c == EOF) break; argv Pa a[i] = c; } After “return”, the computer a[i]=’�’; starts running the “code” printf(“Thank you, %s. n”, a); return 0; stored at this address!!! } h g f e l k j i ? ? al s c Lo able ri va ! ! 1 ^A Saved Registers 12

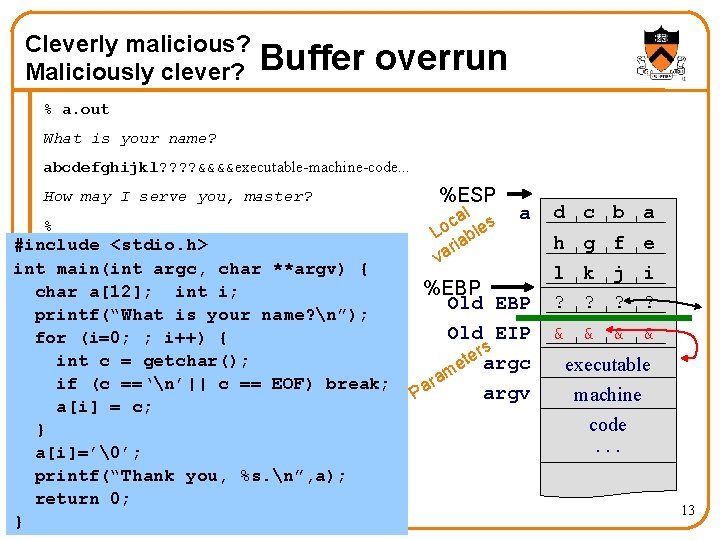
Cleverly malicious? Maliciously clever? Buffer overrun % a. out What is your name? abcdefghijkl? ? &&&&executable-machine-code. . . How may I serve you, master? % #include <stdio. h> int main(int argc, char **argv) { char a[12]; int i; printf(“What is your name? n”); for (i=0; ; i++) { int c = getchar(); if (c ==‘n’|| c == EOF) break; a[i] = c; } a[i]=’�’; printf(“Thank you, %s. n”, a); return 0; } %ESP al s c Lo able ri va a %EBP Old EIP rs e t e argc m ra argv Pa d c b a h g f e l k j i ? ? & & executable machine code. . . 13

Buffer-Overrun Vulnerabilities Keypress goes to OS kernel OS looks up which window has “keyboard focus, ” routes to appropriate user process’s stdin E-mail client Web Browser OS Kernel TCP packet goes to OS kernel OS looks up which process is listening on that port, sends data to stdin Hardware User process does fprintf (asks OS to write to disk) OS writes to disk Internet 14
![Attacking a Web Server URLs Input in web forms fori0 pi i Attacking a Web Server • URLs • Input in web forms for(i=0; p[i]; i++)](https://slidetodoc.com/presentation_image_h2/bca7ff19a6fe0e3dbdafa9583920fa95/image-15.jpg)
Attacking a Web Server • URLs • Input in web forms for(i=0; p[i]; i++) url[i]=p[i]; • Crypto keys for SSL • etc. Client PC Web Server 15
![Attacking a Web Browser HTML keywords Images fori0 pi i gifipi Attacking a Web Browser • HTML keywords • Images for(i=0; p[i]; i++) gif[i]=p[i]; •](https://slidetodoc.com/presentation_image_h2/bca7ff19a6fe0e3dbdafa9583920fa95/image-16.jpg)
Attacking a Web Browser • HTML keywords • Images for(i=0; p[i]; i++) gif[i]=p[i]; • Image names • URLs • etc. Client PC Web Server @ badguy. com www. badguy. com Earn $$$ Thousands working at home! 16
![Attacking everything in sight fori0 pi i gifipi Client PC The Internet badguy Attacking everything in sight for(i=0; p[i]; i++) gif[i]=p[i]; Client PC The Internet @ badguy.](https://slidetodoc.com/presentation_image_h2/bca7ff19a6fe0e3dbdafa9583920fa95/image-17.jpg)
Attacking everything in sight for(i=0; p[i]; i++) gif[i]=p[i]; Client PC The Internet @ badguy. com • E-mail client • PDF viewer • Operating-system kernel • TCP/IP stack • Any application that ever sees input directly from the outside 17

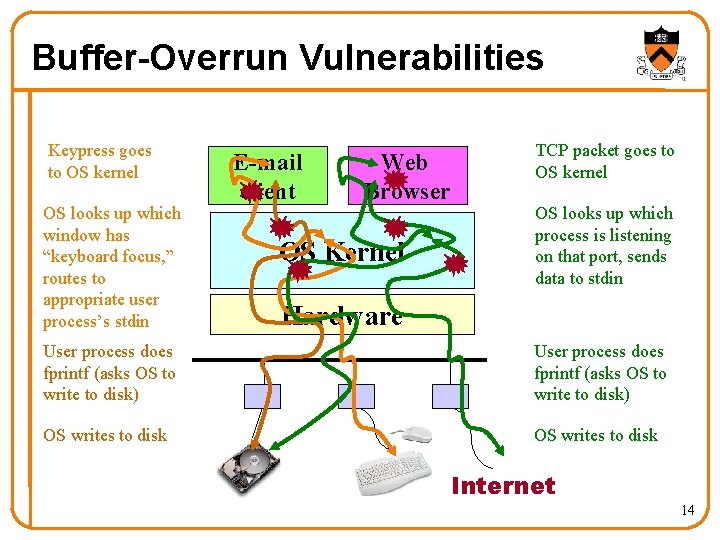
Your Programming Assignment % a. out What is your name? John Smith Thank you, John Smith. I recommend that you get a grade of D on this assignment % char grade = 'D'; int main(void) { printf("What is your name? n"); read. String(Name); if (strcmp(Name, "Andrew Appel")==0) grade='B'; printf("Thank you, %s. n I recommend that you get a grade of %c on this assignment. n", Name, grade); exit(0); } 18

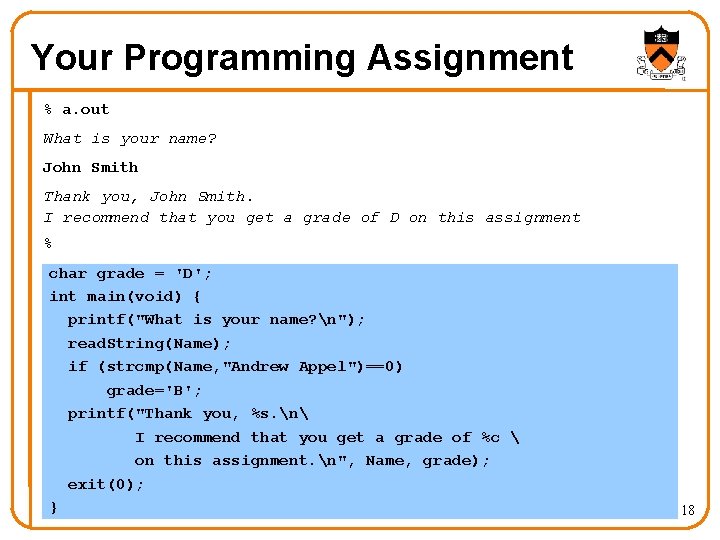
Three Ways to Change the Grade • Smashing the stack in read. String() Change Old. EIP point to the “grade=‘B’” code Write entirely new machine code, and have Old. EIP point to it Write machine code to change grade and jump back to main() char grade = 'D'; int main(void) { printf("What is your name? n"); read. String(Name); if (strcmp(Name, "Andrew Appel")==0) grade='B'; printf("Thank you, %s. n I recommend that you get a grade of %c on this assignment. n", Name, grade); exit(0); }

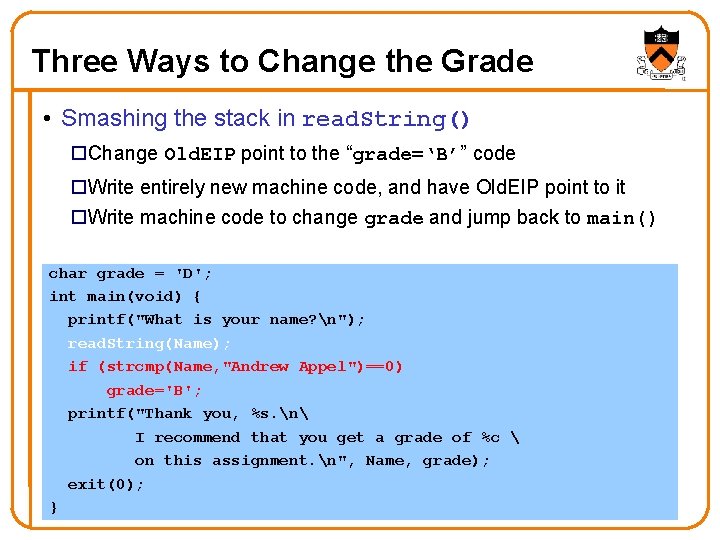
OK, That’s a B. . . % a. out What is your name? John Smith�. ? ? @*&%} Thank you, John Smith. I recommend. . . a grade of B. . . % %ESP buf al s c Lo able ri va char grade = 'D'; %EBP int main(void) { Old EBP printf("What is your name? n"); Old EIP read. String(Name); rs e t e if (strcmp(Name, "Andrew Appel")==0) m ra grade='B'; Pa printf("Thank you, %s. n I recommend. . . grade of %c . . . nment. n", Name, grade); exit(0); } n h o J i m S. � h t 7 ? k ? A ? ? } % * @ Saved Registers 20

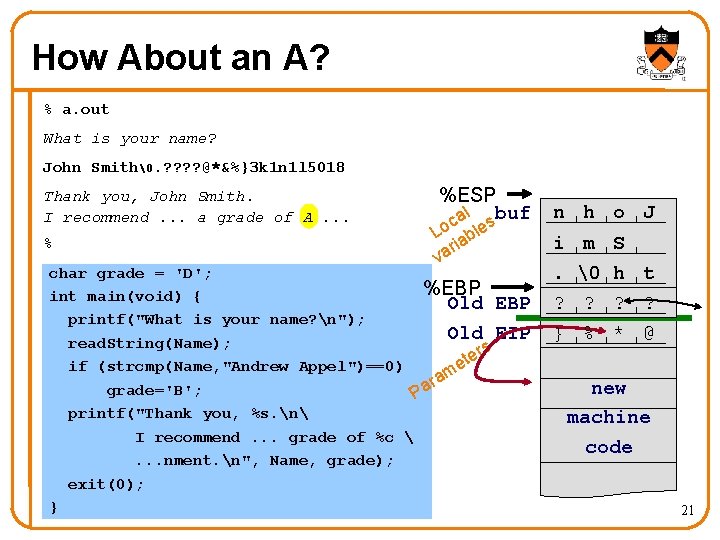
How About an A? % a. out What is your name? John Smith�. ? ? @*&%}3 k 1 n 1 l 5018 Thank you, John Smith. I recommend. . . a grade of A. . . % %ESP l buf ca s Lo able ri va char grade = 'D'; %EBP int main(void) { Old EBP printf("What is your name? n"); Old EIP read. String(Name); rs e t e if (strcmp(Name, "Andrew Appel")==0) m ra grade='B'; Pa printf("Thank you, %s. n I recommend. . . grade of %c . . . nment. n", Name, grade); exit(0); } n h o J i m S. � h t 7 ? k ? A ? ? } % * @ n 1 k 3 new machine code 21

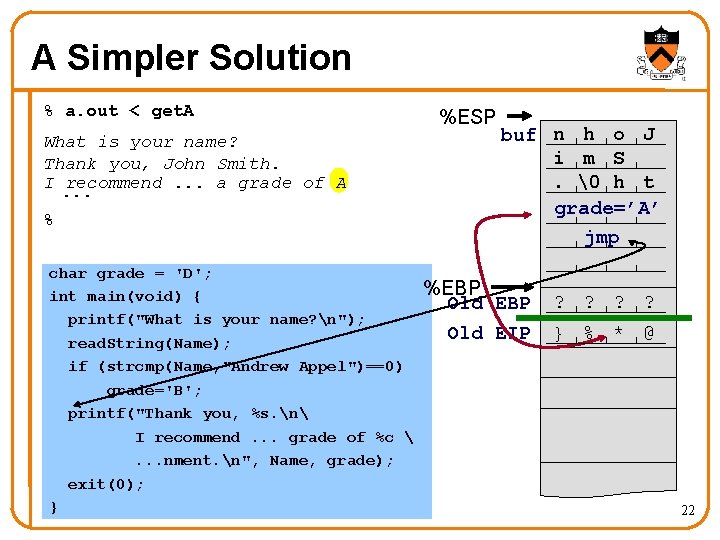
A Simpler Solution % a. out < get. A What is your name? Thank you, John Smith. I. . . recommend. . . a grade of A % char grade = 'D'; int main(void) { printf("What is your name? n"); read. String(Name); if (strcmp(Name, "Andrew Appel")==0) grade='B'; printf("Thank you, %s. n I recommend. . . grade of %c . . . nment. n", Name, grade); exit(0); } %ESP buf n h o J i m S. � h t grade=’A’ jmp %EBP Old EIP ? ? } % * @ 22

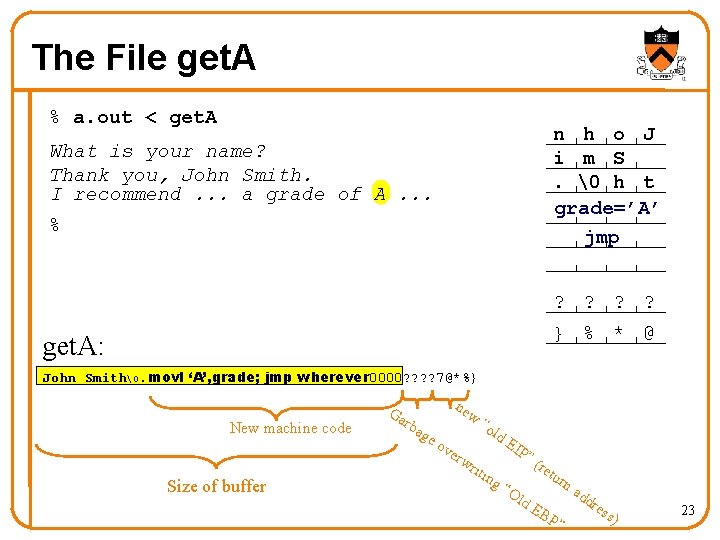
The File get. A % a. out < get. A n h o J i m S. � h t grade=’A’ jmp What is your name? Thank you, John Smith. I recommend. . . a grade of A. . . % ? ? } % * @ get. A: John Smith�. movl ‘A’, grade; jmp wherever 0000? ? 7@*%} New machine code Size of buffer Ga ne w rba ge o “o ve rw riti ld ng EI P” (re tur na “O ld E BP ” dd res s) 23

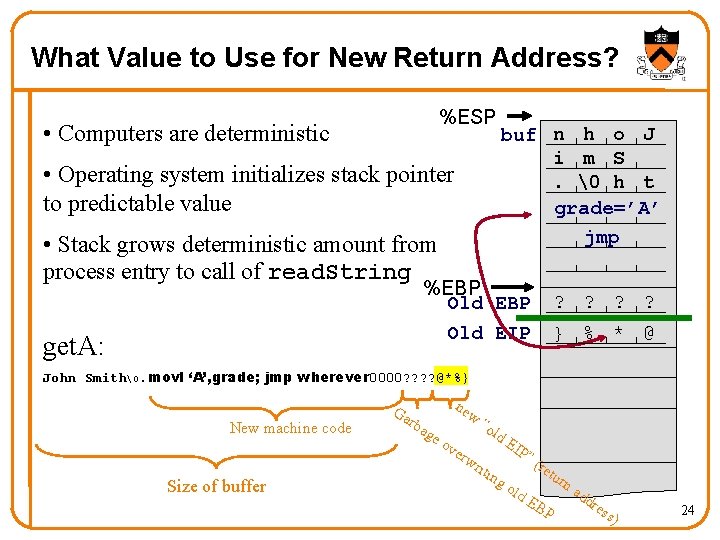
What Value to Use for New Return Address? %ESP • Computers are deterministic • Operating system initializes stack pointer to predictable value • Stack grows deterministic amount from process entry to call of read. String buf n h o J i m S. � h t grade=’A’ jmp %EBP Old EIP get. A: ? ? } % * @ John Smith�. movl ‘A’, grade; jmp wherever 0000? ? @*%} New machine code Size of buffer Ga rba ge ne w “o ld EI ov P” erw (re riti tur ng na old dd EB res P s) 24

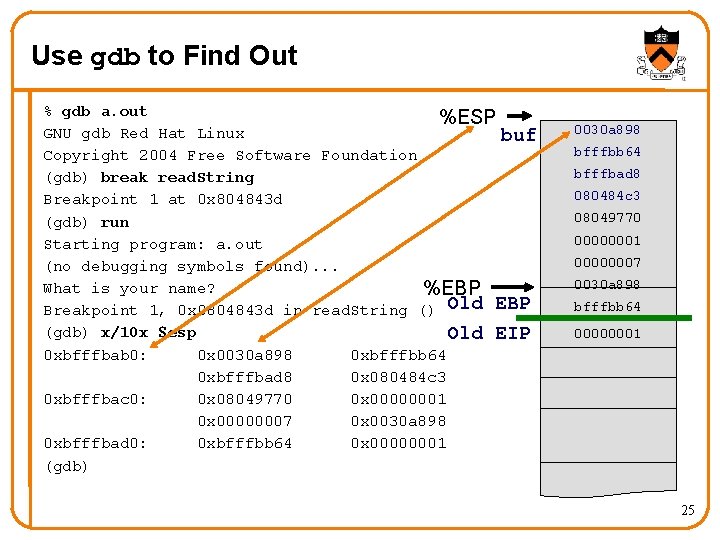
Use gdb to Find Out % gdb a. out %ESP GNU gdb Red Hat Linux buf Copyright 2004 Free Software Foundation (gdb) break read. String Breakpoint 1 at 0 x 804843 d (gdb) run Starting program: a. out (no debugging symbols found). . . What is your name? %EBP Breakpoint 1, 0 x 0804843 d in read. String () Old EBP (gdb) x/10 x $esp Old EIP 0 xbfffbab 0: 0 x 0030 a 898 0 xbfffbb 64 0 xbfffbad 8 0 x 080484 c 3 0 xbfffbac 0: 0 x 08049770 0 x 00000001 0 x 00000007 0 x 0030 a 898 0 xbfffbad 0: 0 xbfffbb 64 0 x 00000001 (gdb) 0030 a 898 bfffbb 64 bfffbad 8 080484 c 3 08049770 00000001 00000007 0030 a 898 bfffbb 64 00000001 25

Defenses Against This Attack • Best: program in languages that make array-out-of-bounds impossible (Java, C#, ML, . . ) • Good: use discipline in C programming always to check bounds of array subscripts • Better than nothing: Operating system randomizes initial stack pointer How to attack it: John Smith�. . . nop; . . . ; nop; do_bad_things; exit(0) Can jump anywhere in here, so don’t have to know exact value of stack pointer 26

Defenses Against This Attack • Best: program in languages that make array-out-of-bounds impossible (Java, C#, ML, . . ) • Good: use discipline in C programming always to check bounds of array subscripts • Better than nothing: Operating system randomizes initial stack pointer How to attack it: John Smith�. . . nop; . . . ; nop; do_bad_things; exit(0) For this assignment, you don’t need such a fancy attack. The hello. c program copies the buffer to the global bss data space (into the Name array) so you can just jump there, don’t have to know the stack height. 27

Defenses Against This Attack • Best: program in languages that make array-out-of-bounds impossible (Java, C#, ML, . . ) • Good: use discipline in C programming always to check bounds of array subscripts • Better than nothing: Operating system randomizes initial stack pointer • Better than nothing: Prohibit execution of machine code from the stack and data segments • Problem 1: backward compatibility • Problem 2: need VM hardware with “exec/noexec” bit on a page by page basis; x 86/Pentium family lacks this • Amazing hack solution: use obsolete “segment registers” 28 left over from 80286.

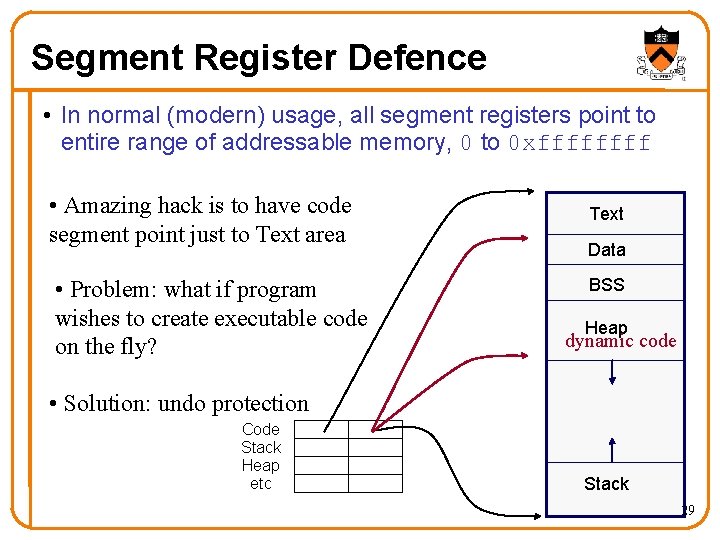
Segment Register Defence • In normal (modern) usage, all segment registers point to entire range of addressable memory, 0 to 0 xffff • Amazing hack is to have code segment point just to Text area • Problem: what if program wishes to create executable code on the fly? Text Data BSS Heap dynamic code • Solution: undo protection Code Stack Heap etc Stack 29

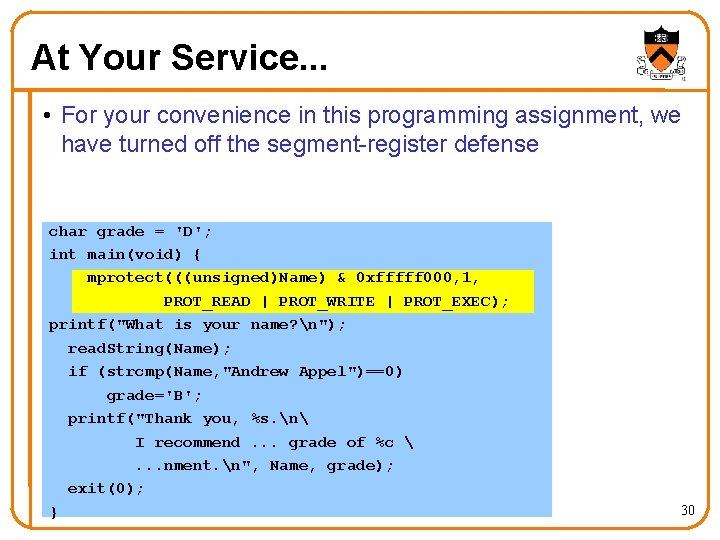
At Your Service. . . • For your convenience in this programming assignment, we have turned off the segment-register defense char grade = 'D'; int main(void) { mprotect(((unsigned)Name) & 0 xfffff 000, 1, PROT_READ | PROT_WRITE | PROT_EXEC); printf("What is your name? n"); read. String(Name); if (strcmp(Name, "Andrew Appel")==0) grade='B'; printf("Thank you, %s. n I recommend. . . grade of %c . . . nment. n", Name, grade); exit(0); } 30

How to Get Started • Use gdb to map out where things are Stack frame of “read. String” Stack frame of “main” underneath it Global data area containing “grade” and “Name” Machine code for “main” Take notes of all these things, by address. • Write a little assembly-language program Set the “grade” variable to ‘A’; jump to wherever Assemble it, maybe even link it into a copy of hello. c, and examine what it looks like using gdb • Prepare your attack data Write a C program to print out the data string Useful functions: printf, putchar, putw 31

Start Early • Use gdb to map out where things are Stack frame of “read. String” Stack frame of “main” underneath it Global data area containing “grade” and “Name” Machine code for “main” Take notes of all these things, by address. If possible, get this part done by the time your Weds/Thurs precept meets this week. Bring your notes with you to precept. We recommend you work in pairs on this assignment. 32