COMP 1321 Digital Infrastructure Richard Henson University of















- Slides: 48

COMP 1321 Digital Infrastructure Richard Henson University of Worcester October 2017

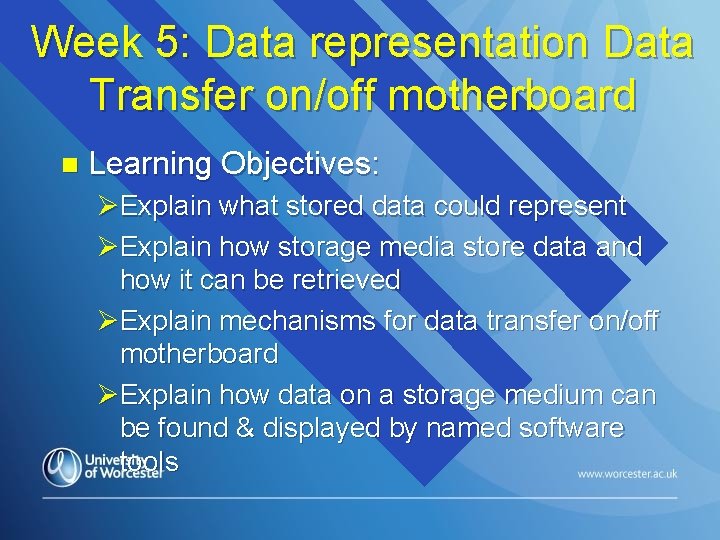
Week 5: Data representation Data Transfer on/off motherboard n Learning Objectives: ØExplain what stored data could represent ØExplain how storage media store data and how it can be retrieved ØExplain mechanisms for data transfer on/off motherboard ØExplain how data on a storage medium can be found & displayed by named software tools

CPU, Memory and Boot-up n BOOT process requires CPU instructions… Øhave to be stored somewhere (in files) Booting up is a matter of loading all these files & their programs n Where to store? n Øneed to be accessed & processed as quickly as possible!

Memory… or Storage? n Lot of confusion… n memory interfaces directly with CPU Øalso called primary storage Øheld on motherboard, controlled by system clock Øfast (dynamic RAM), very fast (static RAM) Øquite fast (ROM)

Primary & Secondary Storage n Secondary storage Øany other form of data storage not directly interfacing with CPU via bus Ø accessible to CPU via i/o calls » e. g. INT 21 (Intel 8086…) Øuses ports to connect electrically with CPU » external e. g. USB, Ethernet » internal e. g. SATA ØSlower than primary storage

Virtual Memory n Use of fast(ish) secondary storage device locations as if they were primary storage locations… Ø hard disk (especially SSD) Ø storage addressed directly by the CPU n Requires programmed mapping between extra primary storage locations & secondary storage locations Ø adv: unlikely that the CPU will run out of “memory” Ø disadv: hard disk performance “falls of a cliff” when virtual memory interfaces with CPU

“Firmware” n Software held on EPROM (erasable, programmable) chip Øcan’t easily be tampered with ØIDEAL for low-level operating system programs, ensures rapid boot-up Øalso embedded applications n Needs updating (like all software)… Øsome flexibility to overwrite

Questions n Is virtual memory primary or secondary storage? n What about firmware?

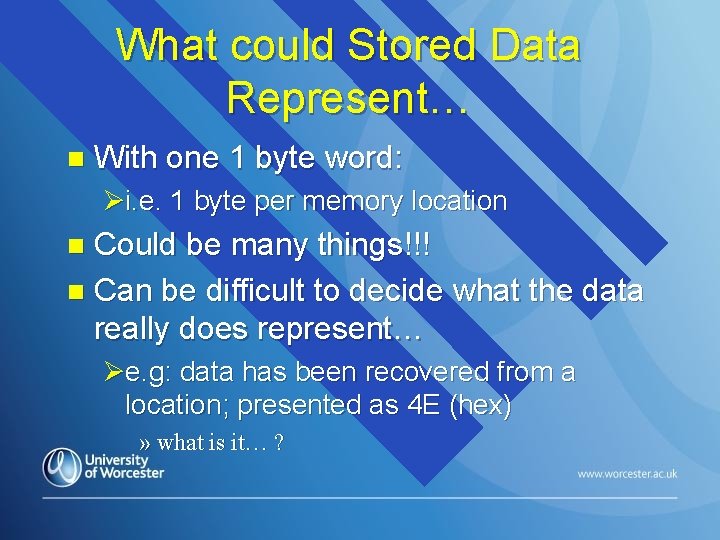
What could Stored Data Represent… n With one 1 byte word: Øi. e. 1 byte per memory location Could be many things!!! n Can be difficult to decide what the data really does represent… n Øe. g: data has been recovered from a location; presented as 4 E (hex) » what is it… ?

What could “ 4 E” represent? 0 n 1 0 0 1 1 1 Could be part of a program instruction Øin assembly language Øor source code (as ASCII code) n 0 Program data Øas a number Øas an ASCII character…

More possibilities for “ 4 E” Over to you… n In groups… n Five minutes… n

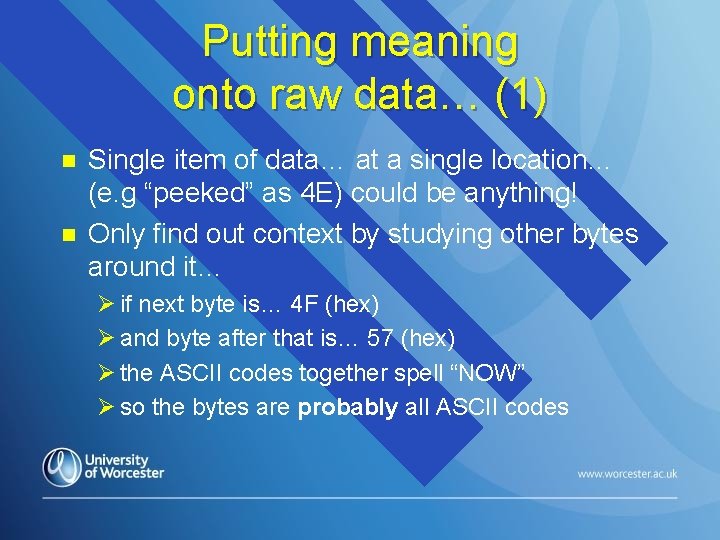
Putting meaning onto raw data… (1) n n Single item of data… at a single location… (e. g “peeked” as 4 E) could be anything! Only find out context by studying other bytes around it… Ø if next byte is… 4 F (hex) Ø and byte after that is… 57 (hex) Ø the ASCII codes together spell “NOW” Ø so the bytes are probably all ASCII codes

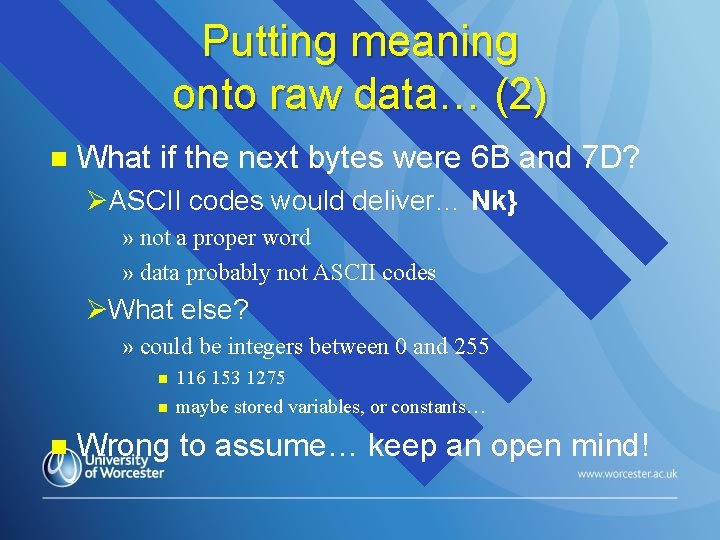
Putting meaning onto raw data… (2) n What if the next bytes were 6 B and 7 D? ØASCII codes would deliver… Nk} » not a proper word » data probably not ASCII codes ØWhat else? » could be integers between 0 and 255 n n n 116 153 1275 maybe stored variables, or constants… Wrong to assume… keep an open mind!

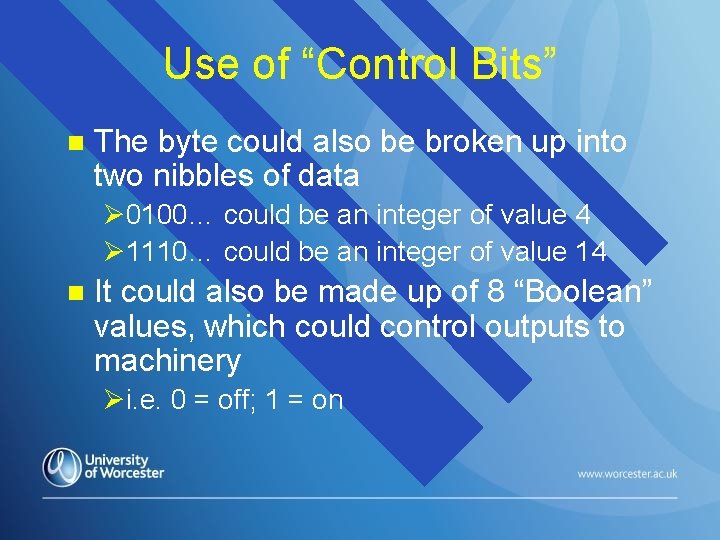
Use of “Control Bits” n The byte could also be broken up into two nibbles of data Ø 0100… could be an integer of value 4 Ø 1110… could be an integer of value 14 n It could also be made up of 8 “Boolean” values, which could control outputs to machinery Øi. e. 0 = off; 1 = on

Looking at Memory locations… (Peeking) n Intel 8086 tool… debug Ø available since early days of DOS n Debug needs –d parameter to peek… Ø shows 128 bytes at a time (& corresp ASCII codes) Ø default memory location is the start of “free” memory » locations may still contain data from previous usage n Specified memory locations can be peeked Ø e. g. –d 0200 for next 128 bytes starting from &0200

“Peeking” and “Poking”… n n & … represents address (as opposed to data) Debug –d can be used to present a whole range of memory Ø e. g. –d 0200 0300 would display every byte between addresses &0200 (hex) and &0300 (hex) n Debug –e can overwrite contents of a specified location (or sequence of locations) with new data Ø called “poking” Ø potentially can crash the computer… (!)

Protection against memory overwrite Operating system protects memory addresses used by “active” processes n Use of debug -e bypasses protection!!! n Øonly protection for computer’s primary memory is to disable the debug program Øbut could in theory still be executed remotely, if administrative access to local computer has been granted… (!)

How does data get between devices? n Data usually needs to go in both directions… DEVICE A DEVICE B

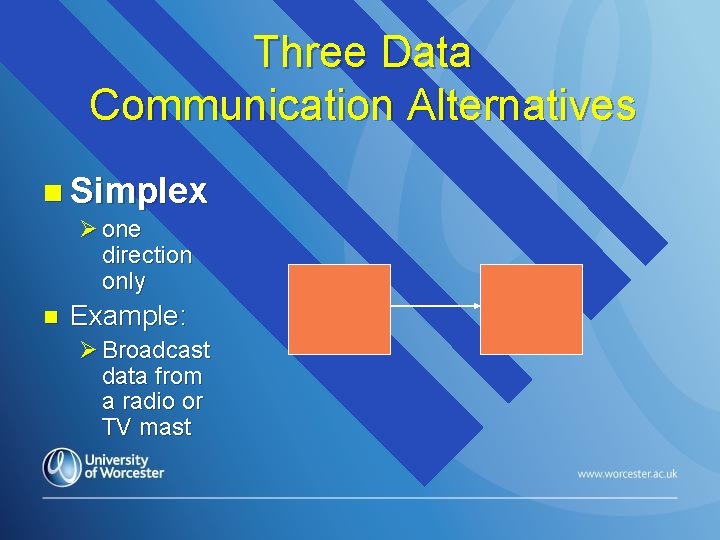
Three Data Communication Alternatives n Simplex Ø one direction only n Example: Ø Broadcast data from a radio or TV mast

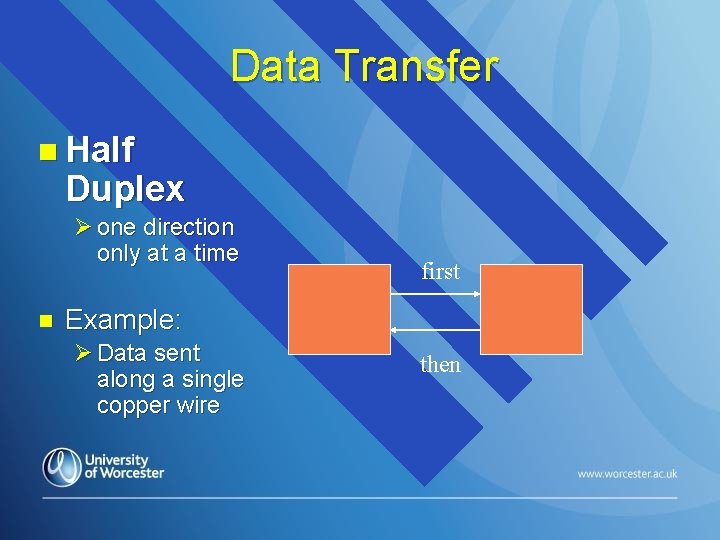
Data Transfer n Half Duplex Ø one direction only at a time n first Example: Ø Data sent along a single copper wire then

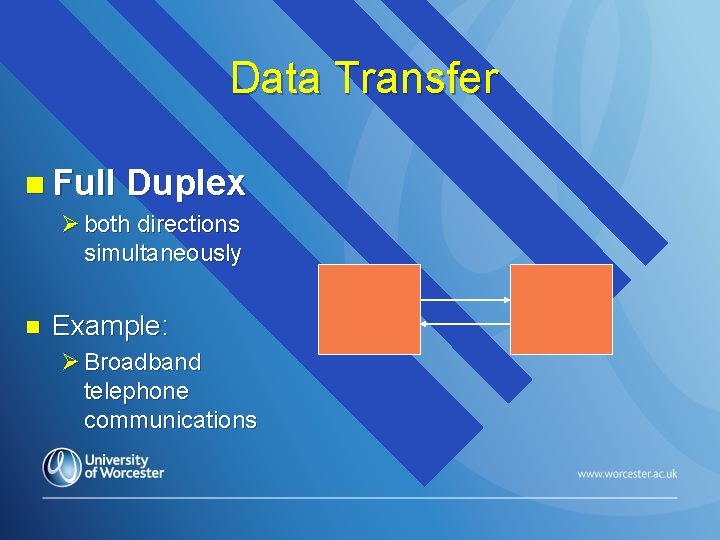
Data Transfer n Full Duplex Ø both directions simultaneously n Example: Ø Broadband telephone communications

i/o connections with the motherboard n Normally connect digital i/o devices to the motherboard via: ØDirect connections through “ports” ØClick in expansion or “daughter” cards with their own ports

i/o Buses used with older expansion Cards n ISA = Industry Standard Association Ø early (1981 -1984) communications standard Ø speed: up to 16 MB s-1 Ø 8 or 16 -bit parallel connections n PCI = Peripheral Component Interconnect Ø later (1990 -1993) communications standard Ø speed: up to 133 MB s-1 Ø 32 -bit parallel connection Ø ‘Plug and play’ – no set-up software needed, (depending on the operating system used…)

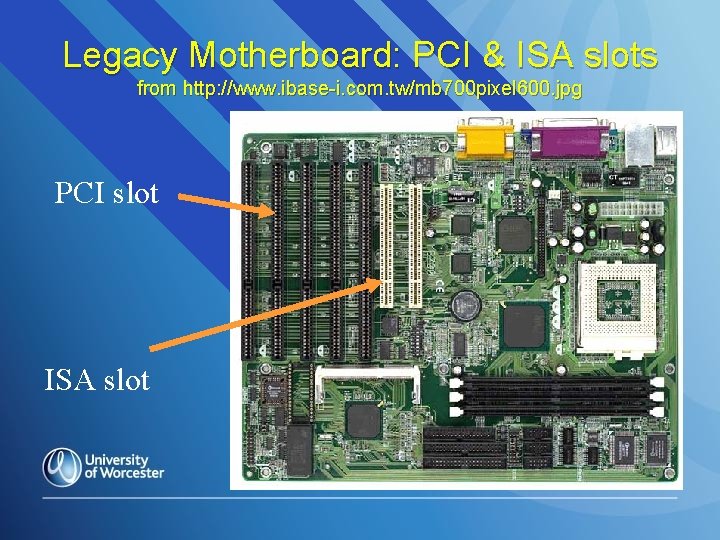
Legacy Motherboard: PCI & ISA slots from http: //www. ibase-i. com. tw/mb 700 pixel 600. jpg PCI slot ISA slot

Peripheral Connectors on the Motherboard n On-board IDE slot (now legacy) Øup to TWO hard disk or DVD-ROM Ø 40 -pin “ribbon” cable n On-board SCSI slot (server board) Øconnects a much larger number of devices

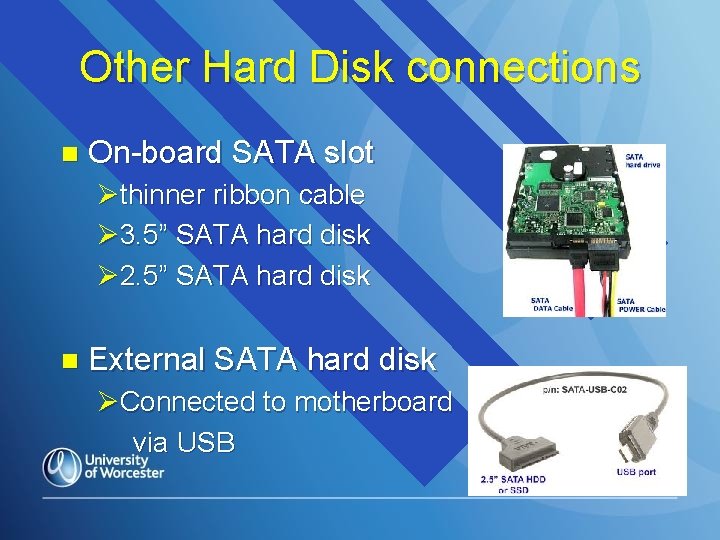
Other Hard Disk connections n On-board SATA slot Øthinner ribbon cable Ø 3. 5” SATA hard disk Ø 2. 5” SATA hard disk n External SATA hard disk ØConnected to motherboard via USB

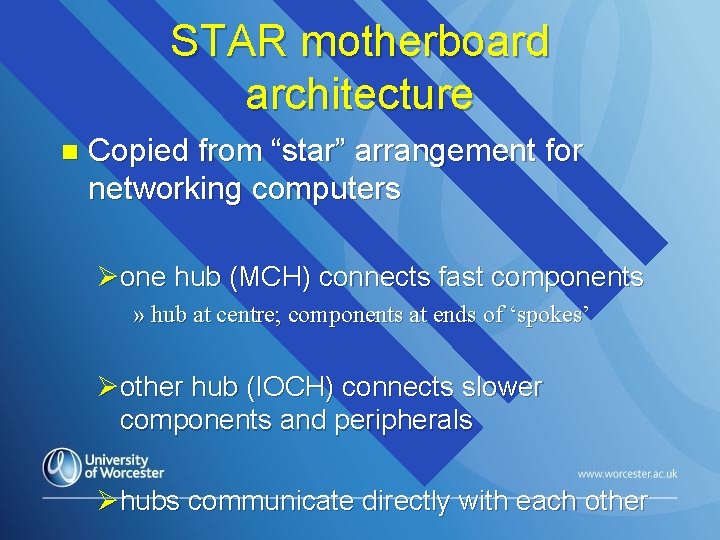
STAR motherboard architecture n Copied from “star” arrangement for networking computers Øone hub (MCH) connects fast components » hub at centre; components at ends of ‘spokes’ Øother hub (IOCH) connects slower components and peripherals Øhubs communicate directly with each other

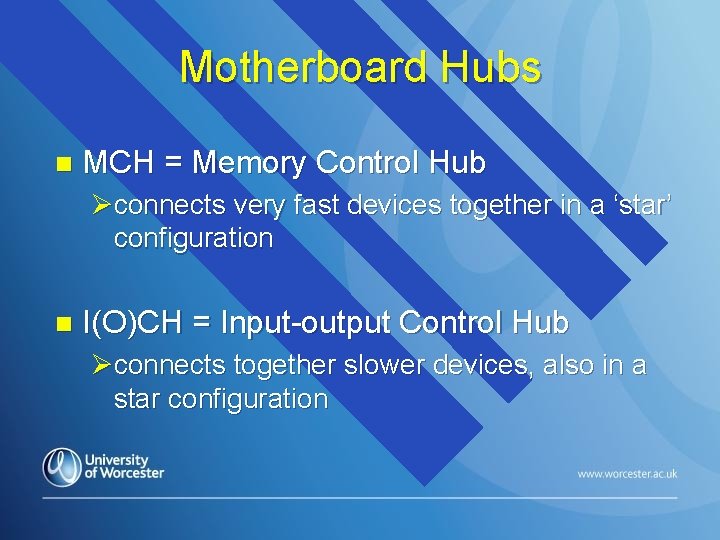
Motherboard Hubs n MCH = Memory Control Hub Øconnects very fast devices together in a ‘star’ configuration n I(O)CH = Input-output Control Hub Øconnects together slower devices, also in a star configuration

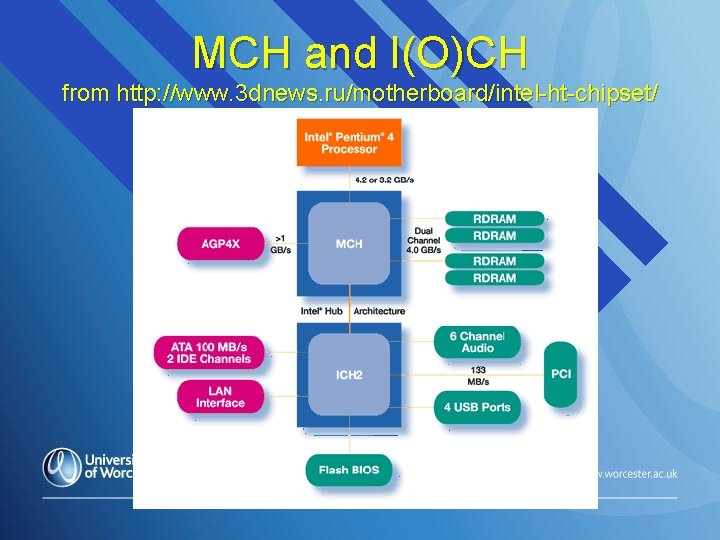
MCH and I(O)CH from http: //www. 3 dnews. ru/motherboard/intel-ht-chipset/

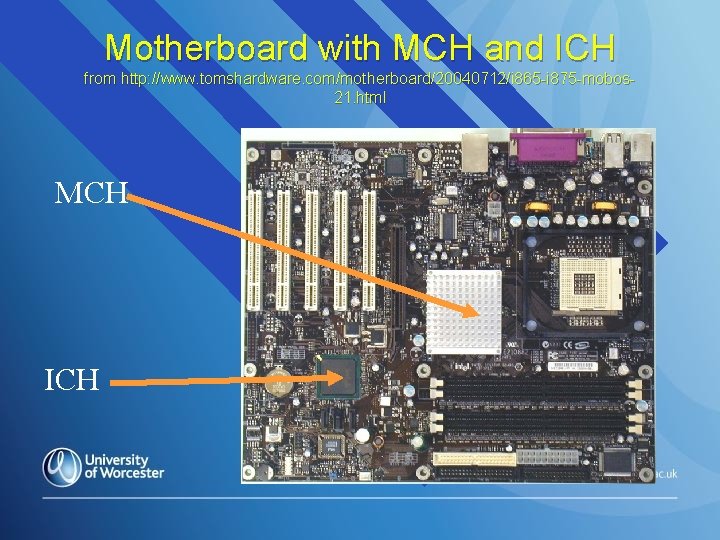
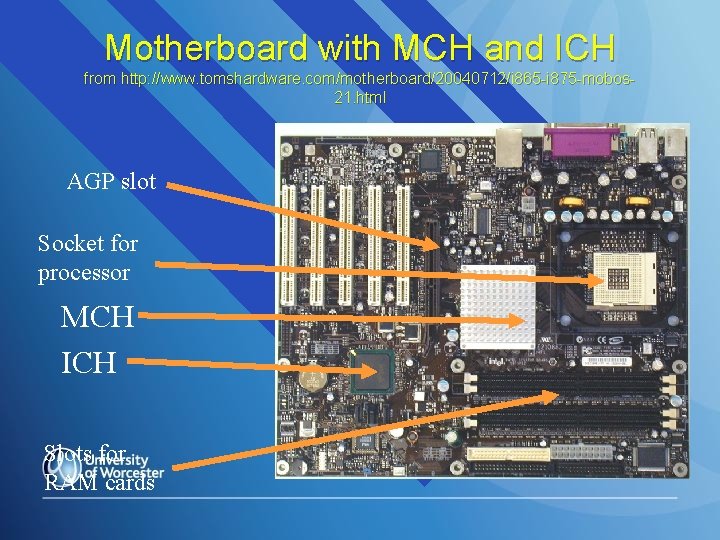
Motherboard with MCH and ICH from http: //www. tomshardware. com/motherboard/20040712/i 865 -i 875 -mobos 21. html MCH ICH

Why arrange motherboard components like this? n Longer wires… Ømore time to send messages (good) Ødegradation of message at high speed (bad) n Therefore… Øimportant for fast components to be close together Øslower components can be further apart

Motherboard with MCH and ICH from http: //www. tomshardware. com/motherboard/20040712/i 865 -i 875 -mobos 21. html AGP slot Socket for processor MCH ICH Slots for RAM cards

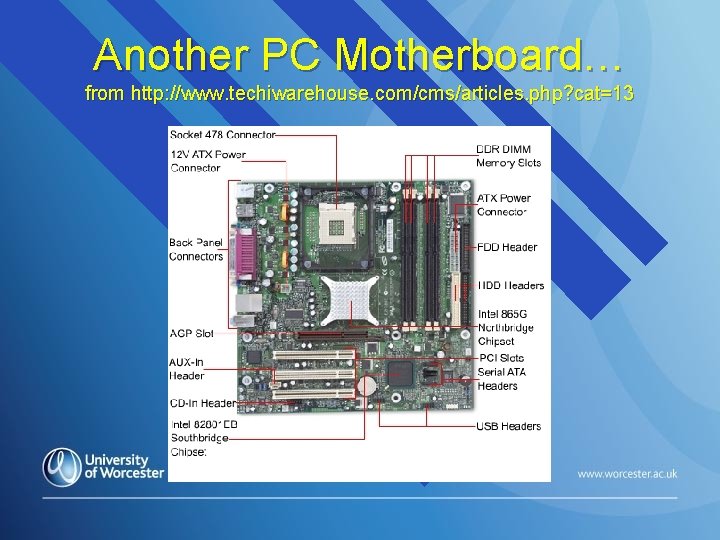
Another PC Motherboard… from http: //www. techiwarehouse. com/cms/articles. php? cat=13

Finding data on Secondary Storage (1) n “file” ~ conventional name for a package of bytes of data ØPrimary storage : controlled directly by CPU instructions ØSecondary storage: controlled by hard disk controller programs & file system manager

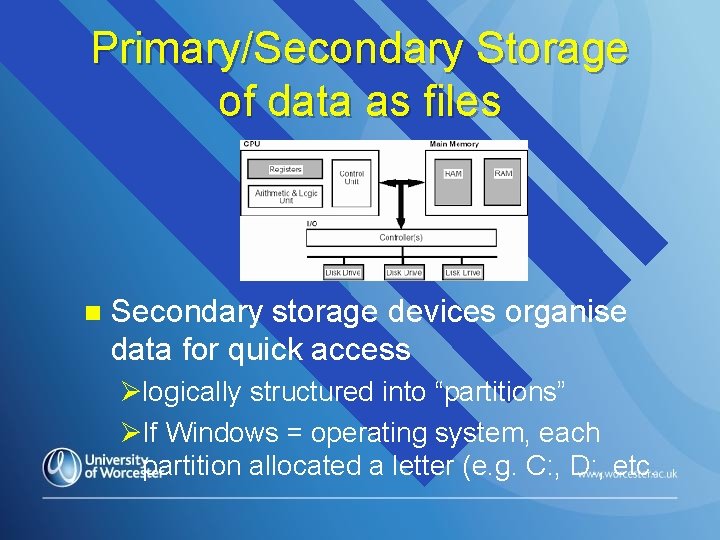
Primary/Secondary Storage of data as files n Secondary storage devices organise data for quick access Ølogically structured into “partitions” ØIf Windows = operating system, each partition allocated a letter (e. g. C: , D: , etc.

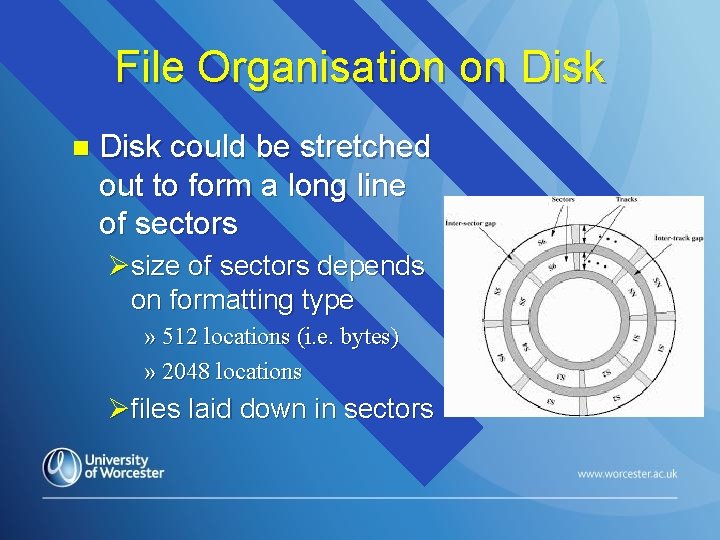
File Organisation on Disk could be stretched out to form a long line of sectors Øsize of sectors depends on formatting type » 512 locations (i. e. bytes) » 2048 locations Øfiles laid down in sectors

Finding data on Secondary Storage n Essential for each partition to create a table or catalogue for starting address of files that are written to it Ø otherwise the file becomes very difficult to retrieve… n Method depends on filing system chosen when partition formatted… Ø As well as formatting each filing system structures the media to receive data in its own unique way…

“Boot Sector” Important for hard disk boot up n Process of loading operating system from on secondary storage starts from… n Øprovides configuration information for effective communication with CPU Øif damaged, boot up halted! » should have a backup… needs to be copied to boot sector to overwrite corrupted data

Partitions Created by special program n Areas of hard disk managed by a file system n Ødifferent partitions can use different file systems Øsingle boot partition containing boot sector » can point to different operating systems » Selectable via screen menu

Booting up: loading an Operating System… n Needs to be loaded into RAM Øsome operating systems load everything from ROM Øothers use a combination… » some loaded first from ROM » rest from hard disk or other source n Hard disk needs a bootable partition to load rest of operating system into RAM

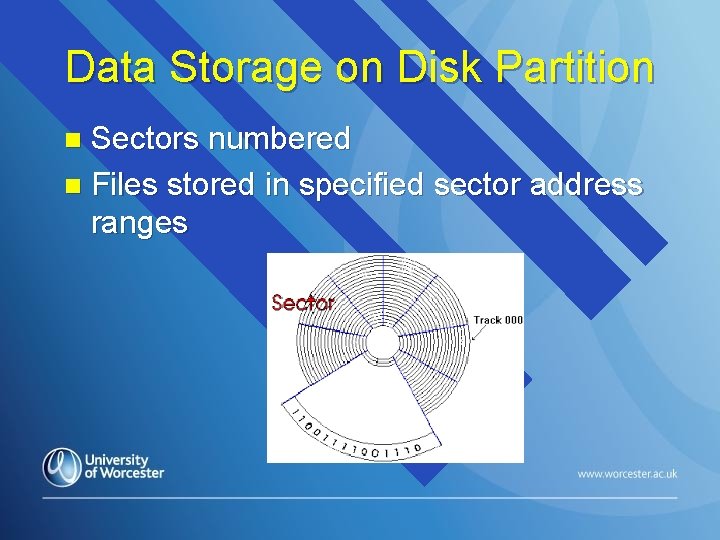
Data Storage on Disk Partition Sectors numbered n Files stored in specified sector address ranges n

Disk Catalogues n Organise files into directories/folders ØTop folder (C: ) = root ØRest of folders link hierarchically n Catalogue logically allocates each file to a folder for ease of retrieval

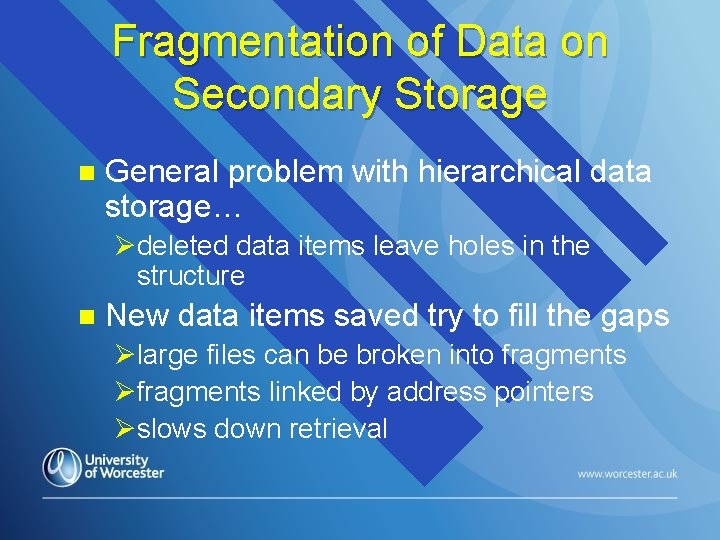
Fragmentation of Data on Secondary Storage n General problem with hierarchical data storage… Ødeleted data items leave holes in the structure n New data items saved try to fill the gaps Ølarge files can be broken into fragments Øfragments linked by address pointers Øslows down retrieval

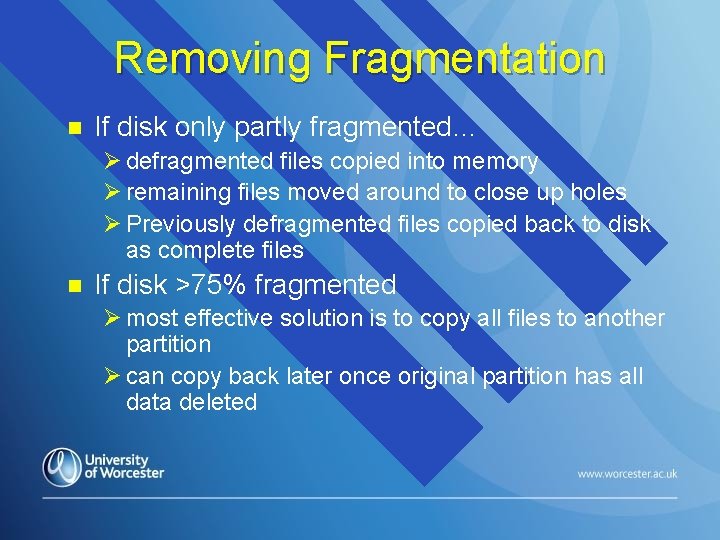
Removing Fragmentation n If disk only partly fragmented… Ø defragmented files copied into memory Ø remaining files moved around to close up holes Ø Previously defragmented files copied back to disk as complete files n If disk >75% fragmented Ø most effective solution is to copy all files to another partition Ø can copy back later once original partition has all data deleted

Is it true that deleted files aren’t really deleted? n n Absolutely! Two things happen when a file is deleted: Ø the first data item stored in the file (first character of filename) is changed to “? ” Ø the catalogue entry ceases to recognise & display the filename » starting address shows “? ” Character » file system is programmed to ignore ? at such a location n Rest of the data is untouched… Ø easily demonstrated through use of a Hex editor program: can show file contents “before” and “after”

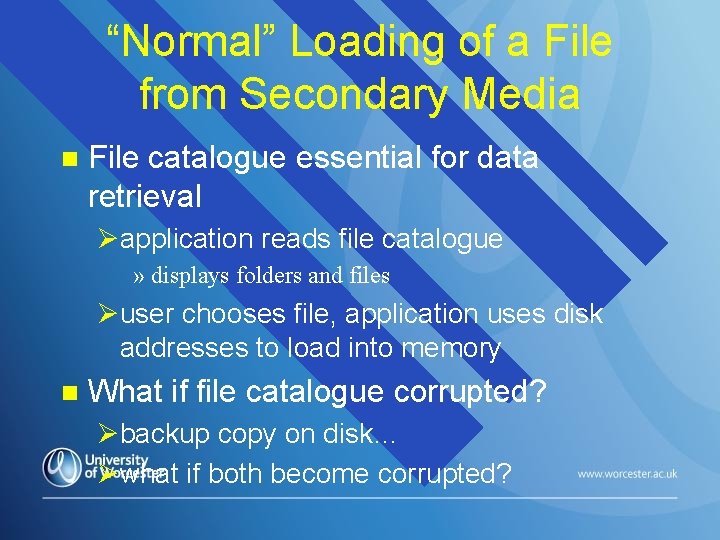
“Normal” Loading of a File from Secondary Media n File catalogue essential for data retrieval Øapplication reads file catalogue » displays folders and files Øuser chooses file, application uses disk addresses to load into memory n What if file catalogue corrupted? Øbackup copy on disk… Øwhat if both become corrupted?

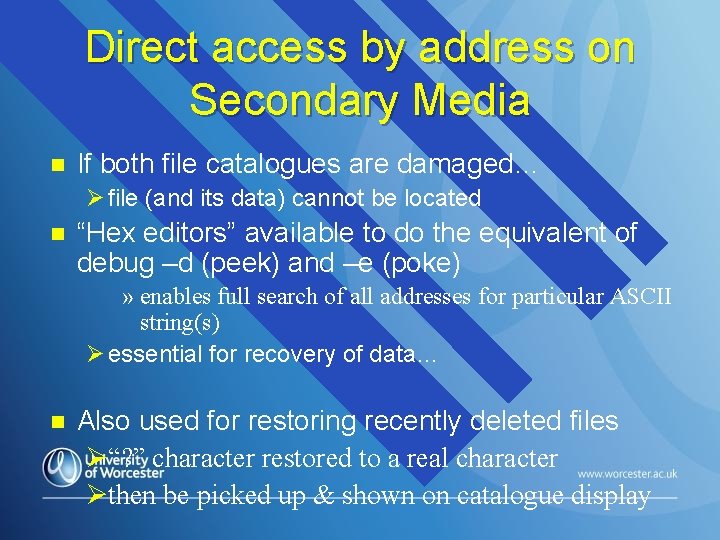
Direct access by address on Secondary Media n If both file catalogues are damaged… Ø file (and its data) cannot be located n “Hex editors” available to do the equivalent of debug –d (peek) and –e (poke) » enables full search of all addresses for particular ASCII string(s) Ø essential for recovery of data… n Also used for restoring recently deleted files Ø“? ” character restored to a real character Øthen be picked up & shown on catalogue display

Win. Hex n Probably the most popular tool to examine hard disks Øreadout quite similar to debug –e Ødata presented byte-by-byte according to catalogue address Ørange of options for extracting, overwriting data, and (like debug) writing consecutive raw data items to a file
 Henson trust manitoba
Henson trust manitoba Phoebe henson
Phoebe henson Art. 1321 cc
Art. 1321 cc Risoluzione
Risoluzione Cse 1321
Cse 1321 Ksu cse 1321 lab final
Ksu cse 1321 lab final Cse 1321
Cse 1321 Enseñanza de la parábola del sembrador
Enseñanza de la parábola del sembrador Dante alighieri 1265
Dante alighieri 1265 Cse 1321
Cse 1321 Looking for richard
Looking for richard Infrastructure digital audit
Infrastructure digital audit 5 layers of e business infrastructure
5 layers of e business infrastructure Digital infrastructure challenges
Digital infrastructure challenges E-commerce infrastructure
E-commerce infrastructure Richard anderson york university
Richard anderson york university Richard davidson andrews university
Richard davidson andrews university Maksud warga negara
Maksud warga negara Digital markets and digital goods
Digital markets and digital goods Digital data digital signals
Digital data digital signals Digital data digital signals
Digital data digital signals E-commerce: digital markets, digital goods
E-commerce: digital markets, digital goods Digital data to digital signal encoding
Digital data to digital signal encoding Luxembourg digital innovation hub
Luxembourg digital innovation hub Unique features of digital markets
Unique features of digital markets Gondar university digital library
Gondar university digital library Kurukshetra university digital site
Kurukshetra university digital site 詹景裕
詹景裕 Plexus ranks
Plexus ranks Comp tox
Comp tox Ap computer science recursion
Ap computer science recursion Comp 3007
Comp 3007 Hotel competitive set
Hotel competitive set Hotel comp set benchmarking
Hotel comp set benchmarking Dairy comp 305
Dairy comp 305 1991105
1991105 Should engineering
Should engineering Im comp plan
Im comp plan Comp 4620
Comp 4620 Excel comp planning
Excel comp planning Eecs 110
Eecs 110 Comp 410 unc
Comp 410 unc Comp sci 1102
Comp sci 1102 Comp 6321 machine learning concordia
Comp 6321 machine learning concordia Comp 585
Comp 585 Comp 553
Comp 553 Comp 512
Comp 512 Comp 512
Comp 512 Design and analysis of algorithms
Design and analysis of algorithms