COMP 3123 Internet Security Richard Henson University of



































- Slides: 42

COMP 3123 Internet Security Richard Henson University of Worcester October 2011

Week 4 Access Controls: Network Directories & the PKI n Objectives: Ø Explain the components of a network directory service Ø Explain how the use of security policies can help prevent network internal security breaches Ø Analyse Windows active directory and compare it with an x 500 standard service Ø Prepare a Windows active directory tree with two contiguously named domain controllers

“Network Directories” n Directories not to be confused with “folders”… Ø generally a data store that changes only infrequently… » e. g. a telephone directory Ø to avoid confusion, computer-based directories also called “repositories” n Lots of different “network databases” have evolved on the web Ø not a good idea! Ø often contain approx. the same info. . . Ø Problem: one updated, all should be » but unlikely in practice unless a managed solution

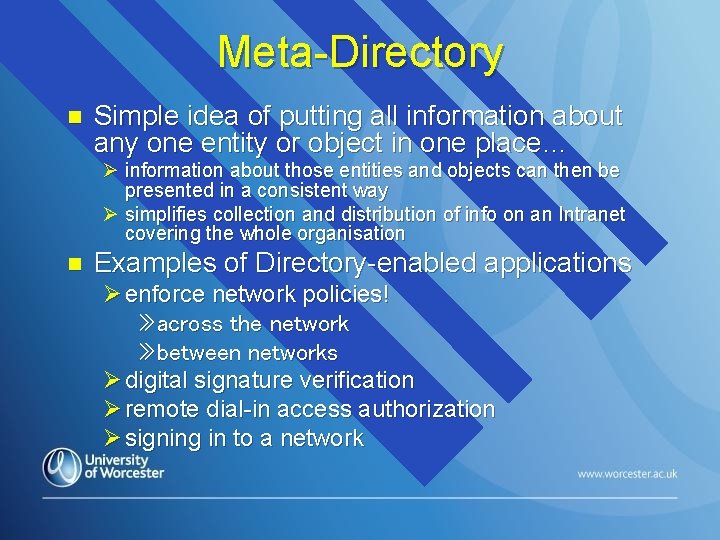
Meta-Directory n Simple idea of putting all information about any one entity or object in one place… Ø information about those entities and objects can then be presented in a consistent way Ø simplifies collection and distribution of info on an Intranet covering the whole organisation n Examples of Directory-enabled applications Ø enforce network policies! » across the network » between networks Ø digital signature verification Ø remote dial-in access authorization Ø signing in to a network

Network Directories & the PKI Needs to avoid multiple-directories problem… n Solution: n Ø use the meta directory approach Ø provide digital certificate information on the web as a “directory service” Ø use LDAP applications to directly access that info

Distributed Directory n Another way of keeping entity information consistent if it does need to appear in multiple locations Ø entry may appear in multiple directories » e. g. one for each email system (if more than one) » e. g. one for gaining access to the network by logging on n n Paper-based equivalent – series of telephone directories each covering a clearly define area Ø collectively cover a wide geographical region Ø serve a variety of purposes Ø all part of the same system for communication Regular directory synchronisation essential for maintaining consistency of information

Development of Internet Directories and IESG n IESG (Internet Engineering Steering Group) provides technical management of IETF activities Ø As approp, translate RFC proposals into RFC standards n Procedure: Ø draft RFC submitted Ø if accepted: IESG elevates it to RFC “draft” status Ø RFC then given consideration as a standard… Ø draft RFC eventually may become a true Internet standard n Example of successful evolution: x 500 -> LDAP

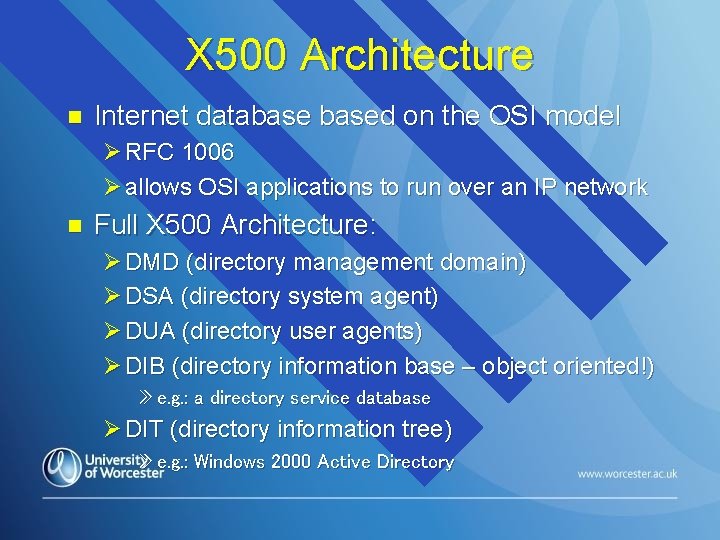
X 500 Architecture n Internet databased on the OSI model Ø RFC 1006 Ø allows OSI applications to run over an IP network n Full X 500 Architecture: Ø DMD (directory management domain) Ø DSA (directory system agent) Ø DUA (directory user agents) Ø DIB (directory information base – object oriented!) » e. g. : a directory service database Ø DIT (directory information tree) » e. g. : Windows 2000 Active Directory

X 500 Protocols n n n DAP (Directory Access protocol) DSP (Directory System protocol) DISP (Directory Information Shadowing Protocol) DOP (Directory operational binding management protocol) Collectively, these protocols give X 500 a wide range of functionality, but the structure is cumbersome…

Simplifying X 500 - LDAP n n Known as Lightweight Directory Access Protocol Thanks to University of Michigan Researchers, early 1990 s Ø gave up on the complexities of X. 500 Ø came up with a scheme that: » retained the X. 500 directory structure » gave it a streamlined access protocol based on standard TCP/IP instead of ISO Ø Other improvements: » pared-down referral mechanism » more flexible security model » no fixed replication protocol

Microsoft and x 500 n n In 1996, Microsoft launched version 4 of its mailserver software, Exchange Designed also to provide the infrastructure to enable DAP clients to access Microsoft Exchange directory service information… Ø client served as an X. 500 DAP client to DAP-compliant directories » e. g. U. S. Government Defense Messaging System (DMS) n Also designed to manage table entries efficiently using a new obj oriented database engine called ESE (Extensible Storage engine)

Microsoft and LDAP n Microsoft wanted to use X 500 in its directory service planned for next version of NT Ø Like Michigan Uni, found X 500 cumbersome, and adapted LDAP n Supporting the Open Directory Services Interface (ODSI), Microsoft helped build a PKI service provider (Verisign) that supports the LDAP protocol Ø allowed developers to build applications that register with, access, and manage multiple directory services with a single set of well-defined interfaces Ø Microsoft Exchange Server 4 supported LDAP Ø Internet Explorer supported LDAP from v 4 onwards

LDAP, ESE, and Active directory n Windows 2000 “active directory” service was a successful commercial roll out of an X 500 compliant directory service Ø used LDAP… Ø also used (uses) ESE to manage data tables Ø and DNS to integrate with www locations n Next version of Microsoft Exchange also used the ESE/LDAP/DNS combination…

Directory Services and “Active Directory” n Active Directory has just one data store, known as the directory Ø Stored as NTFS. DIT » where does “. dit” originate from? Ø distributed across ALL domain controllers (dcs) Ø links to objects on/controlled by each dc Ø changes automatically replicated to all dcs Ø Contains details of: » stored objects » shared resources » network user and computer accounts

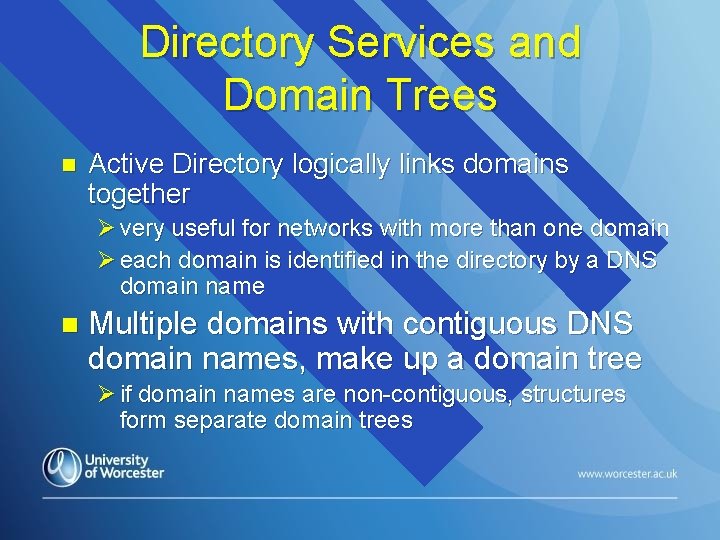
Directory Services and Domain Trees n Active Directory logically links domains together Ø very useful for networks with more than one domain Ø each domain is identified in the directory by a DNS domain name n Multiple domains with contiguous DNS domain names, make up a domain tree Ø if domain names are non-contiguous, structures form separate domain trees

“Trust Relationships” between (legacy) NT Domains n Account authentication between domains was first established in the Windows NT architecture Ø Allowed users and computers can be authenticated between any domains n Problem: Windows NT trust relationships were isolated and individual

Active Directory Trust Relationships n Automatically created between adjacent domains (parent and child domains) in the tree Øusers and computers can be authenticated between ANY domains in the domain tree n So how does this all work securely in practice, across an entire enterprise? ?

Access to Network Resources and Security Controls n The set of security mechanisms used to define what a user can access after logging on to a secured environment Ø enforce “authorisation” Ø “identification” and “authentication” may also be associated with logging on n Effect includes: Ø access to systems & resources Ø interactions users can perform

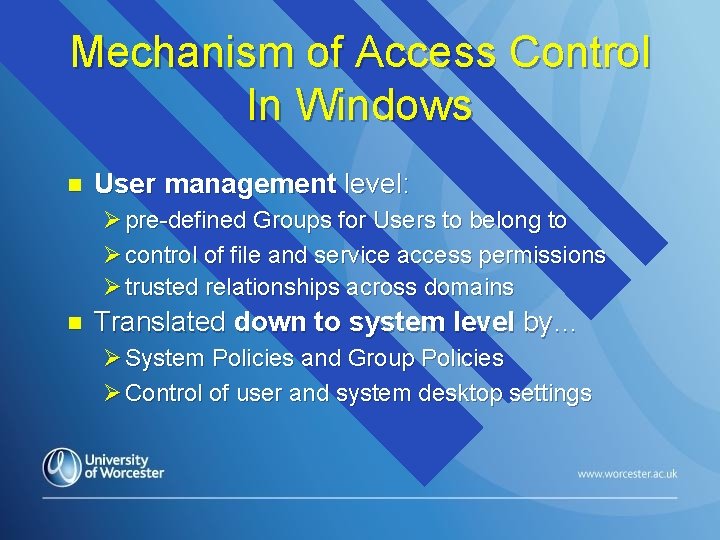
Mechanism of Access Control In Windows n User management level: Ø pre-defined Groups for Users to belong to Ø control of file and service access permissions Ø trusted relationships across domains n Translated down to system level by… Ø System Policies and Group Policies Ø Control of user and system desktop settings

Control of End User and System Settings n In Windows, ultimately, controls user access through the local Windows registry Ø first made available to simplify configuration in Windows 95 » effectively replaced CONFIG. SYS, AUTOEXEC. BAT, SYSTEM. INI and WIN. INI by a single structure Ø all settings saved into a hierarchical data file called SYSTEM. DAT n Principles later extended to networks…

The local registry and Windows networks n n Like Windows 95, Windows NT v 4 allowed system and user settings to be configured locally by registry overwrite files However, it also made it possible for files within a network to overwrite the local registry as well… Øfacility available on any Windows client machine that used a Windows registry

What is The Registry? n Five basic subtrees: Ø HKEY_LOCAL_MACHINE : local computer info. Does not change no matter which user is logged on Ø HKEY_USERS : default user settings Ø HKEY_CURRENT_USER : current user settings Ø HKEY_CLASSES_ROOT : software config data Ø HKEY_CURRENT_CONFIG : “active” hardware profile n Each subtree contains one or more subkeys

Editing Registry Settings n n Generally…. DON’T!!! Contents of the registry should not be changed in any way unless you really know what you are doing!!! Special tools available e. g. REGEDT 32 for those with experience: Ø used to edit local registry settings on Windows NT systems Ø Bearing in mind, however, that registry settings can also be overwritten in memory by data downloaded across the network…

System Policy File n n n Consists of a collection of registry settings Can apply different system settings to a computer, depending on the user or group logging on Can overwrite: Ø local machine registry settings Ø current user registry settings n Should therefore only be used by those who know what they are doing!!!

System Policy File n NTCONFIG. POL Ø provides a list of desktop settings, and therefore can be used to control aspects of appearance of the desktop Ø held on Domain Controllers Ø read during logon procedure n Different NTCONFIG. POL files can be applied to: Ø groups Ø users Ø computers

What is a Security Policy? n n A set of rules and procedures that state the access rights and privileges of a particular user/group of users Should also: Ø confirm the identity of the people that are attempting to access the network Ø prevent imposters from accessing, stealing, or damaging system resources

Implementation of Security Policy n Intention: Øcreate a computing environment that provides users with all of the information and resources they need to be successful Øprotect the information and resources on the network from damage and unauthorized access

Group Policy in Windows 2000 (and subsequent) Networks n Group Policy settings Ø define access to local and network resources from the user's desktop environment: Ø e. g. Start menu options » provide access to programs/resources that user needs to use n Group Policy Objects Ø used with authenticated users to enhance flexibility and scalability of security beyond “domains”, and “NT trusted domains” Ø trust achieved through: » Active directory – establishment of “trees” » Kerberos authentication

Implementation of Group Policy Objects n Group Policy objects are EXTREMELY POWERFUL… Ø contain all specified settings to give a group of users their desktop with agreed security levels applied Ø template editing tool available as a “snap-in” with Windows 2000 Ø creates a specific desktop configuration for a particular group of users n The GPO is in turn associated with selected Active Directory objects: Ø Sites Ø Domains Ø organizational units

Combined Power of Group Policies and Active Directory n n Enables written user/group policies to be easily implemented in software Enables policies to be applied across whole domains: Ø beyond in trusted contiguous domains in the domain tree Ø or even across any non-contiguous domains in the same forest n Because Active directory is x 500 compliant, all the principles of directory services apply

Authentication Factors n n Classified as type 1, type 2, or type 3: Type 1: Knowledge based (what user knows) Ø information provided based on unique knowledge of the individual being authenticated n Type 2: Token based (what user has/does) Ø information comes from a token generated by a particular system Ø token is tied in some way to the user logging on Ø generally not considered a good idea on its own because someone else could have stolen/copied it n Type 3: Characteristic based (what user is) Ø biometric data from the person logging in

One time Passwords (OTP) n Can only be used once… Ø If user gets it wrong, becomes invalid… » locked out » has to contact administrator to reset n Implemented as a type 2 factor Ø password characters randomly generated n If used properly… Ø very secure indeed Ø problem: degree of randomness…

Single Sign On (SSO) n Logon once… Ø authenticated for all servers in that environment n More a convenience matter than a security issue Ø only one set of authentication factors needed Ø single username/authentication factor database covering all servers n SOME very secure environments have dropped SSO in favour of separate logon for each server Ø arguable whether this is necessary but avoids the “all eggs in one basket” argument

Password Administration n Three aspects: Ø Selection » should be a company IS policy that includes choice of password » generally no. of characters is a good match with strength – the higher the better Ø Management » selection & expiration period must comply with policy Ø Control » policy should be enforced by the network itself » usually achieved through use of “group policies”

Access Control Techniques n Discretionary (DAC) Ø access to files/resources controlled by administrator Ø Achieved through ACLs (Access Control Lists) » consist of ACEs (Access Control Entries) Ø the granting of access can be audited n Mandatory (MAC) Ø access dependent on rules/classifications Ø classification dependent on security clearance levels Ø hierarchical or compartmentalised, or hybrids

Remote Logon and Kerberos Authentication n KDC can maintain a secure database of authorised users, passwords & domain names maintained throughout an active directory domain tree using Kerberos V 5 security protocol Ø uses strong encryption Ø freely available from its inventor, MIT n Active Directory + Kerberos = Very Powerful combination Ø can even be used to authenticate across mobile & wireless networks

Components of “Enterprise wide” Login with kerberos authentication n n Active Directory tree logical connects and “trusts” servers throughout the enterprise Servers in their turn control access to users within domains Group(s) selected during the user authentication process Group Policy Objects invoked which rewrite registry settings and control client desktops

How much security should be applied to domain users? n n General rule: don’t give a user more rights than they actually need Think carefully… Ø identify security privileges appropriate to different types of user Ø create a group based on each type of user n Allocate each new user to an appropriate group Ø automatically will have appropriate access rights…

Users, Groups, Security, and NTFS partitions n n Any file or folder on an NTFS partition will have file permissions imposed Typical permissions: Ø No Access Ø Read only Ø Read and Execute Ø Write Ø Modify Ø Ownership/Full Control n Much wider range of permissions available

Point for debate: is “read only” access dangerous? n If information held on server, and accessed by dumb terminals… Ø secure enough! Ø this was the case in the days of centralised networks with no distributed processing n With client-server networking, read only means “the user can take a copy” Ø is this dangerous, from an organisational security point of view?

What if the network goes wrong? Accountability n The broad security concept of being able to hold a human to account for their actions using … Ø a strong authentication environment so one user cannot masquerade as another Ø strict imposition of “least privilege” Ø regular monitoring of the network environment Ø rigorous inspection of audit logs

What if the network goes wrong? Auditing n n n Essential component of security monitoring A network can generate lots of data on a wide variety of network functions and results they return this is readily customisable to focus on, for example, the behaviour of particular users or resources Ø data normally saved as timestamped. log files Ø audit files help to ensure accountability for user behaviour