COMP 1321 Digital Infrastructures Richard Henson University of













![Utilizing Google etc. (“passive”) Google: Advanced Search options: n Uses [site: ] [intitle: ] Utilizing Google etc. (“passive”) Google: Advanced Search options: n Uses [site: ] [intitle: ]](https://slidetodoc.com/presentation_image_h/97ebc885edc5bf70cb2479c72a5581b2/image-17.jpg)




- Slides: 25

COMP 1321 Digital Infrastructures Richard Henson University of Worcester April 2016

Week 21: Web Communications - Securing Web Pages n Objectives: ØExplain the principles of hacking ethically ØAccess and exploit a “test” client site ØExplain “Footprinting” and reconnaissance from a penetration testers perspective Ø“Passively” scan networks from the outside

Ethical Hacking Principles n Hacking is a criminal offence in the UK Øcovered through The Computer Misuse Act (1990) Øtightened by further legislation (2006) n It can only be done ”legally” by a trained (or trainee) professional Øa computing student would be considered in this context under the law

Ethical Hacking principles n Even if it is legal… Ødoesn’t mean it is ethical! n Professionals only hack without owner’s permission if there is reason to believe a law is being broken Øif not… they must ask permission Øotherwise definitely unethical (and possibly illegal)

Ethical Hacking Principles n What is “hacking”? Øbreaching a computer system without permission n How is it done? Øusing software tools to get through the security of the system Øalso called penetration testing (again… if done with permission…)

Penetration Testers Toolkit n n n Many penetration testing tools available Also a body of knowledge that shows how to use them… Together, provide the expertise to penetration test a client’s site Ø but this should only be undertaken with the client’s permission…

Preparing to use a Toolkit n Ethical Hacking Professionals need to be familiar with both Windows Server, and Linux n To fully engage with principles of penetration testing, install the following as virtual machines on your own computer: Ø Windows 2008 Server Ø Linux, with Backtrack (as VM) … Ø Remember: this should only be used ethically! n Instead, you may wish to just take an overview (plenty of excellent youtube videos)

Reminder of Virtualisation… n The use of software to allow hardware to run multiple operating system images at the same time Ø Possible to run Windows OS under Mac OS Ø run multiple versions of Windows OS on the same PC n Enables the creation of a “virtual” (rather than actual) version of any software environment on the desktop, e. g. Operating Systems, a server, a storage device or networks, an application

What and Why of “Footprinting” n Definition: Ø “Gathering information about a “target” system” n Could be passive (non-penetrative) or active Ø Find out as much information about the digital and physical evidence of the target’s existence as possible » need to use multiple sources… » may (e. g. “black hat” hacking) need to be done secretly

Useful Info to Gather about a network n n n n Domain Names User/Group names System Names IP addresses Employee Details/Company Directory Network protocols used & VPN start/finish Company documents Intrusion detection system used

Rationale for “passive” Footprinting n The ethical hacker can gather a lot of information from publicly available sources Øorganisation needs to know what is “out there” n Methodology: Østart by finding the URL (search engine) » e. g. www. worc. ac. uk Øfrom main website, find other external-facing names » e. g. staffweb. worc. ac. uk

Website Connections & History n History: use www. archive. org: ØThe Wayback Machine Connections: use robtex. com n Business Intelligence: n Øsites that reveal company details Øe. g. www. companieshouse. co. uk

More Company Information… n “Whois” & Check. DNS. com: Ølookups of IP/DNS combinations Ødetails of who owns a domain name Ødetails of DNS Zones & subdomains n Job hunters websites: Øe. g. www. reed. co. uk Øwww. jobsite. co. uk Øwww. totaljobs. com n IT technicians “blog entries”

People Information Company information will reveal names n Use names in n Øsearch engines ØFacebook ØLinked. In n Google Earth reveals: Øcompany location(s)

Physical Network Information (“active” footprinting or phishing) n External “probing” Øshould be detectable by a good defence system… (could be embarrassing!) n e. g. Traceroute: ØUses ICMP protocol “echo” » no TCP or UDP port Øreveals names/IP addresses of intelligent hardware: » e. g. Routers, Gateways, DMZs

Email Footprinting n Using the email system to find the organisation’s email names structure Ø“passive” monitor emails sent » IP source address » structure of name Ø“active” email sending programs : » test whether email addresses actually exist » test restrictions on attachments
![Utilizing Google etc passive Google Advanced Search options n Uses site intitle Utilizing Google etc. (“passive”) Google: Advanced Search options: n Uses [site: ] [intitle: ]](https://slidetodoc.com/presentation_image_h/97ebc885edc5bf70cb2479c72a5581b2/image-17.jpg)
Utilizing Google etc. (“passive”) Google: Advanced Search options: n Uses [site: ] [intitle: ] [allintitle: ] [inurl: ] n ØIn each case a search string should follow Øe. g. “password” n Maltego Øgraphical representations of data

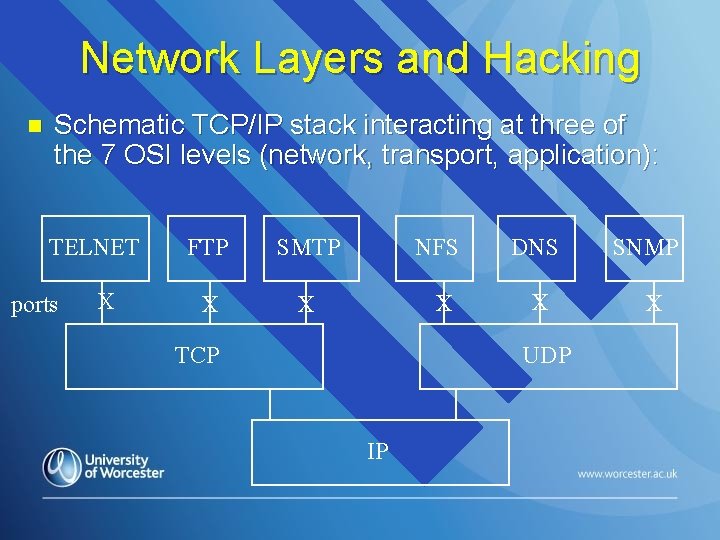
Network Layers and Hacking n Schematic TCP/IP stack interacting at three of the 7 OSI levels (network, transport, application): TELNET ports X FTP SMTP NFS DNS X X TCP UDP IP SNMP X

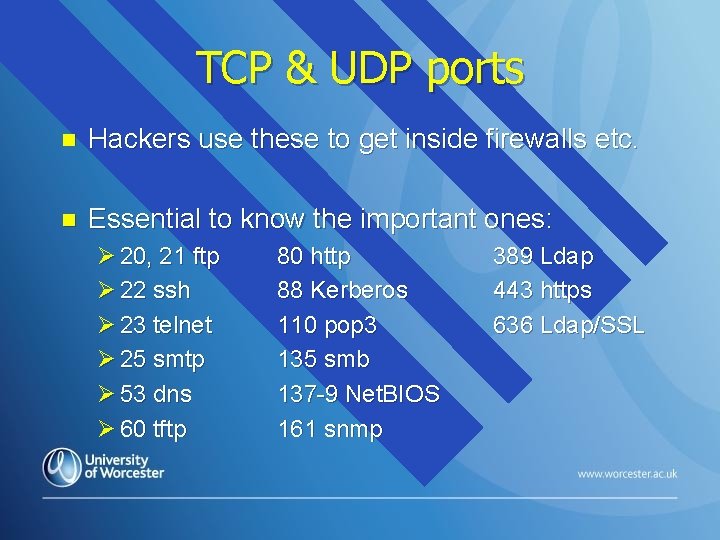
TCP & UDP ports n Hackers use these to get inside firewalls etc. n Essential to know the important ones: Ø 20, 21 ftp Ø 22 ssh Ø 23 telnet Ø 25 smtp Ø 53 dns Ø 60 tftp 80 http 88 Kerberos 110 pop 3 135 smb 137 -9 Net. BIOS 161 snmp 389 Ldap 443 https 636 Ldap/SSL

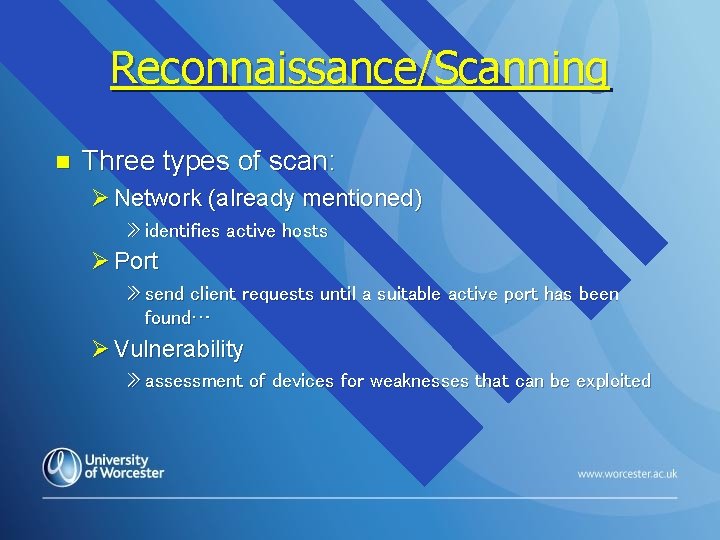
Reconnaissance/Scanning n Three types of scan: Ø Network (already mentioned) » identifies active hosts Ø Port » send client requests until a suitable active port has been found… Ø Vulnerability » assessment of devices for weaknesses that can be exploited

A “Scanning” Methodology for Ethical Hackers… Check for Live Systems n Check for open ports n “Banner Grabbing” n Øe. g. bad html request Scan for vulnerabilities n Draw Network diagram(s) n Prepare proxies… n

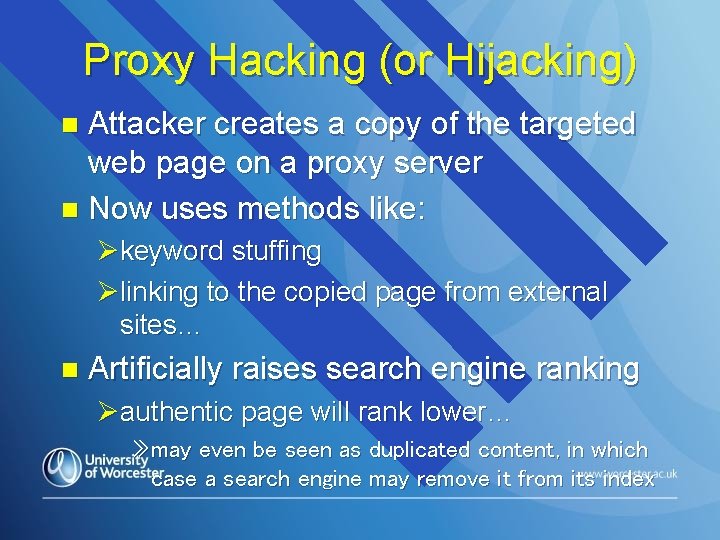
Proxy Hacking (or Hijacking) Attacker creates a copy of the targeted web page on a proxy server n Now uses methods like: n Økeyword stuffing Ølinking to the copied page from external sites… n Artificially raises search engine ranking Øauthentic page will rank lower… » may even be seen as duplicated content, in which case a search engine may remove it from its index

Lots more “tricks” ethically available!

Now you try it! Download software tools first… n Try out the tools on an informal basis without infringing “ethical hacking” rules n Gather evidence documenting your activities n Øafter Campbell Murray’s presentation (27 th April) n Present evidence for assignment 2, guidance 4/11 th May…

Thanks for Listening