Chapter 2 Network Models OSI model and TCPIP









- Slides: 46

Chapter 2: Network Models

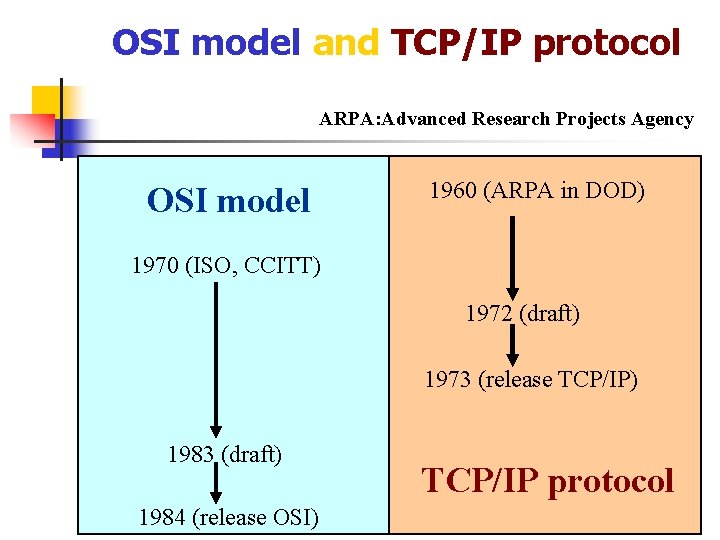
OSI model and TCP/IP protocol ARPA: Advanced Research Projects Agency OSI model 1960 (ARPA in DOD) 1970 (ISO, CCITT) 1972 (draft) 1973 (release TCP/IP) 1983 (draft) 1984 (release OSI) TCP/IP protocol

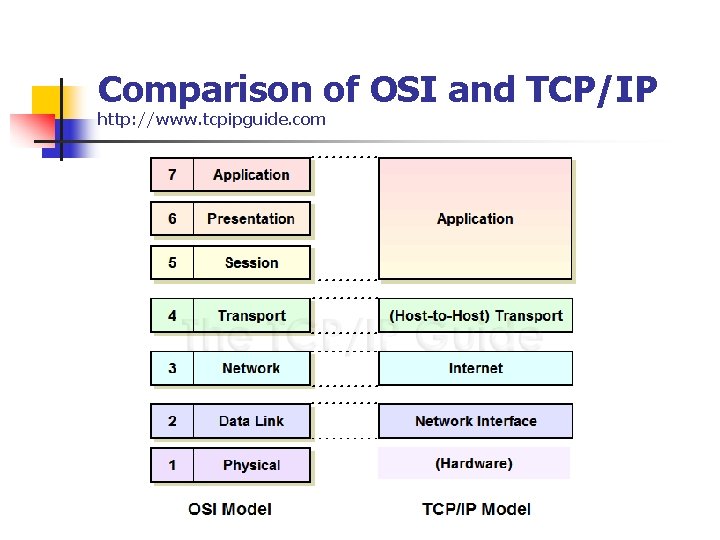
Comparison of OSI and TCP/IP http: //www. tcpipguide. com

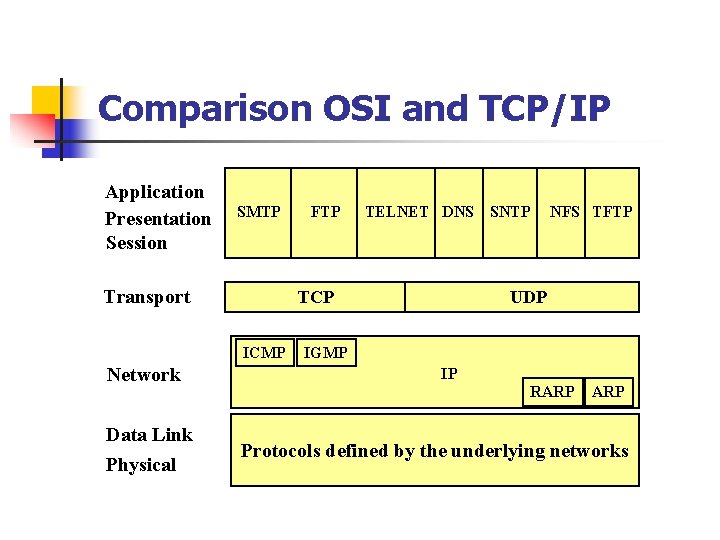
Comparison OSI and TCP/IP Application Presentation Session SMTP Transport Data Link Physical TELNET DNS TCP ICMP Network FTP SNTP NFS TFTP UDP IGMP IP RARP Protocols defined by the underlying networks

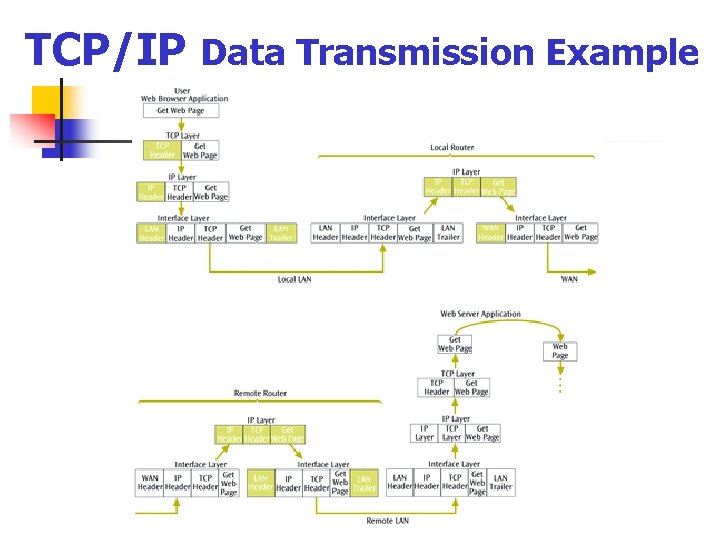
TCP/IP Data Transmission Example

OSI Model n History n 0197 -> ISO (International Standard Organization ( จดตงคณะกรรมการพจารณา architecture ทเปนกลางเพอ กำหนดการเชอมตอระหวาง computer และ อปกรณ - 1984 -> released in ISO 7498 document OSI (Open System Interconnection) -> 7 layers n Objectives n n WCB/Mc. Graw-Hill Compatibility Flexibility

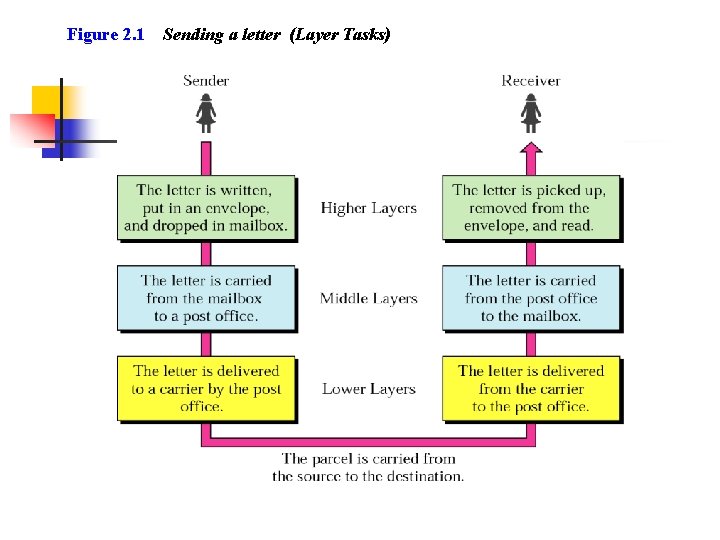
Figure 2. 1 Sending a letter (Layer Tasks)

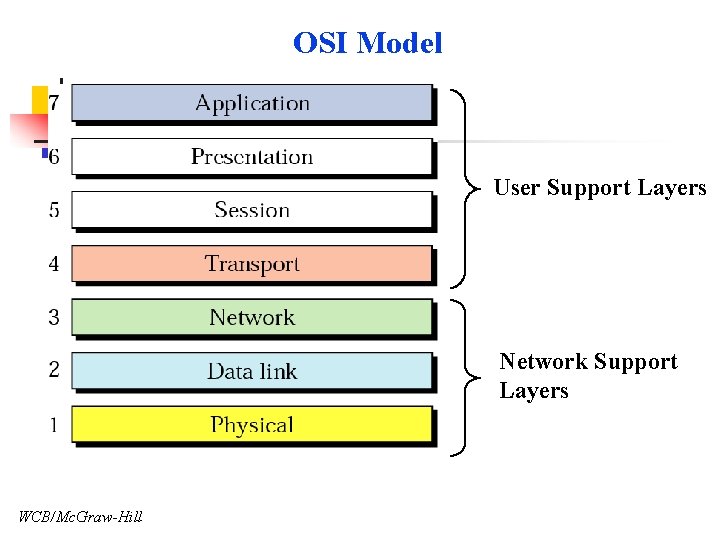
OSI Model User Support Layers Network Support Layers WCB/Mc. Graw-Hill

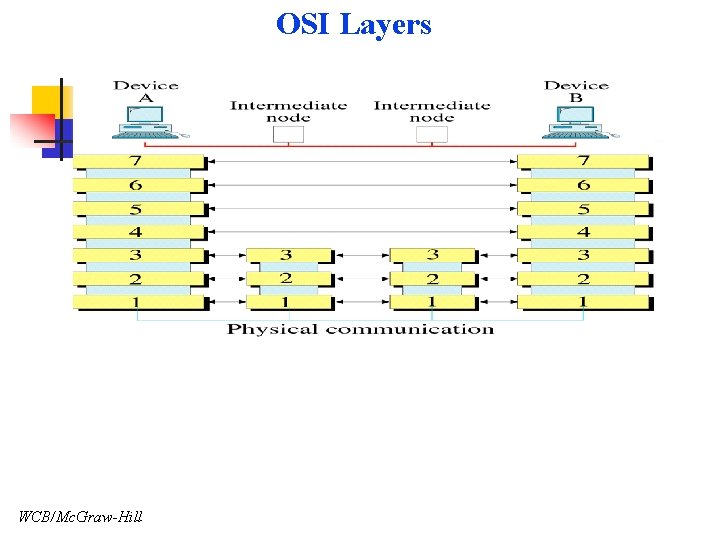
OSI Layers WCB/Mc. Graw-Hill

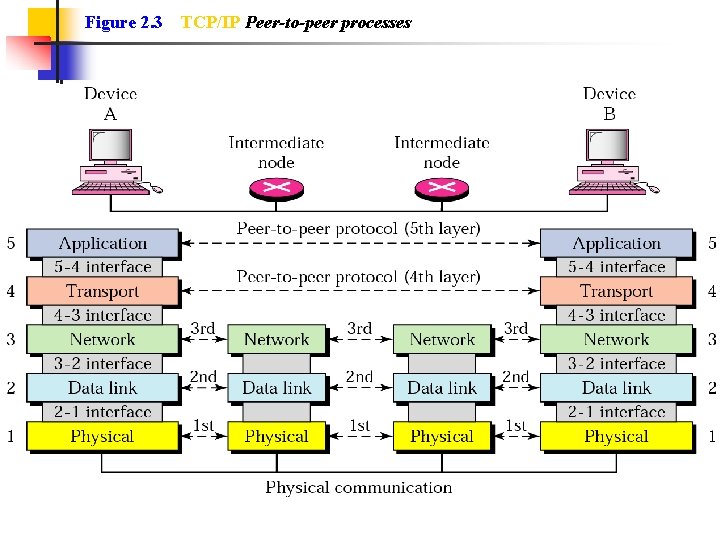
Figure 2. 3 TCP/IP Peer-to-peer processes

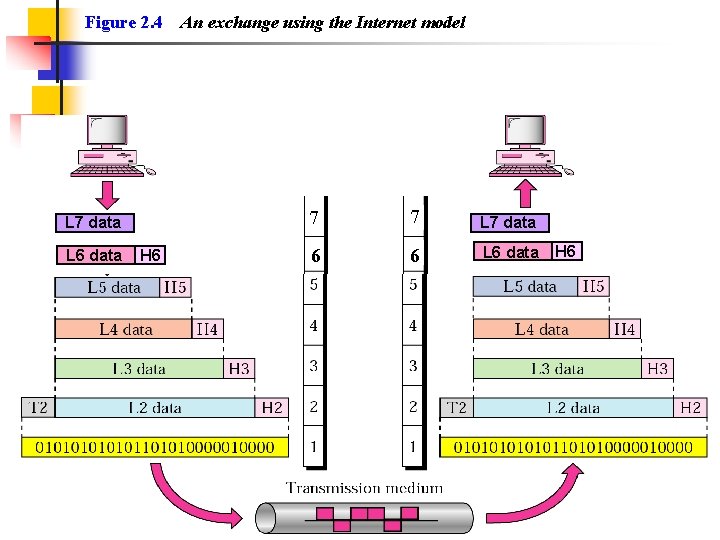
Figure 2. 4 L 7 data L 6 data H 6 An exchange using the Internet model 7 7 L 7 data 6 6 L 6 data H 6

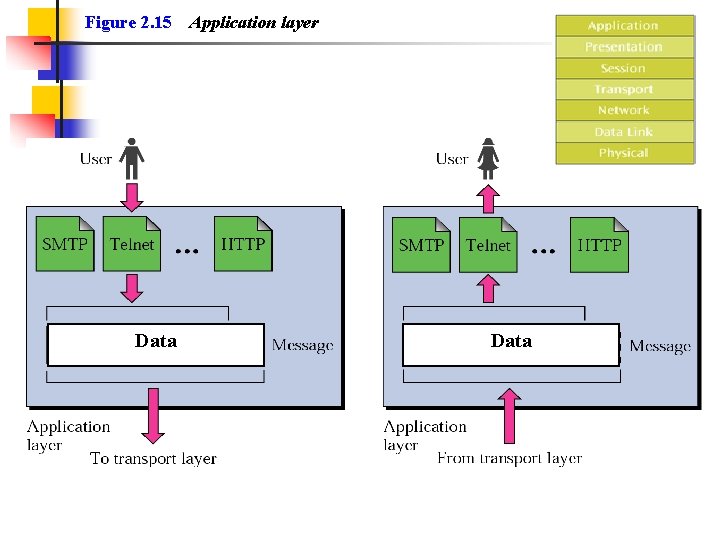
Figure 2. 15 Data Application layer Data

Application Layer n Responsibility n n n User interface (Software application) No header or trailer Services n n Network Virtual Terminal File transfer, access, and management (FTAM) Mail service Accessing WWW

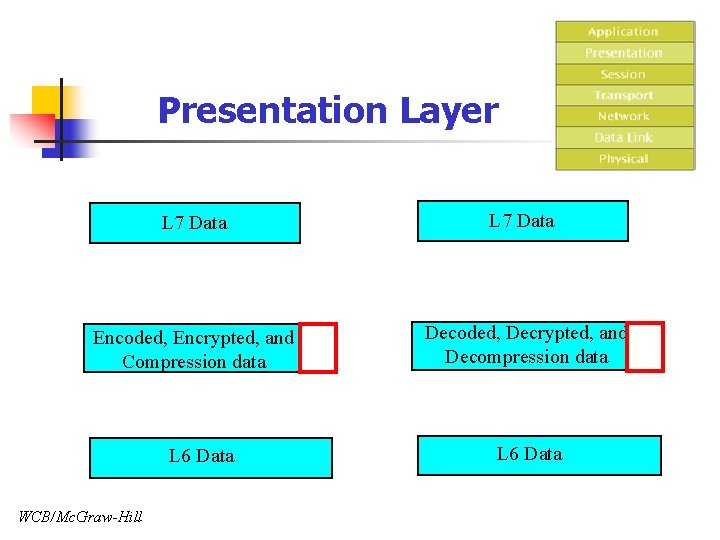
Presentation Layer L 7 Data Encoded, Encrypted, and Compression data Decoded, Decrypted, and Decompression data L 6 Data WCB/Mc. Graw-Hill L 6 Data

Presentation Layer n Responsibility n n Manage syntax and semantics of different data format between any two systems Services n Translation of data format n n Encryption (privacy & security) n n Ex. ASCII -> non ASCII system For sensitive information: Compression n Ex. Zip, Gif, JPEG login-password, credit card, bank account, personal information

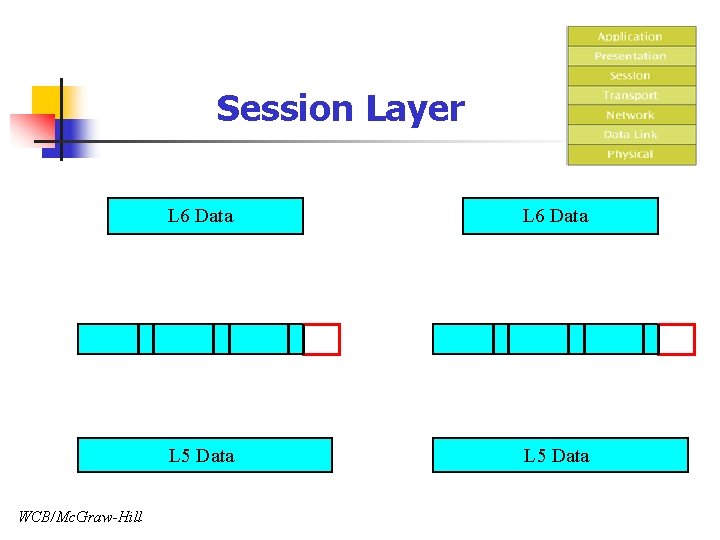
Session Layer WCB/Mc. Graw-Hill L 6 Data L 5 Data

Session Layer n Responsibility n n Establish, manage, and terminate session Services n Dialog control n n Traffic control & direction control Message synchronization n Adding checkpoints (synchronization points) in the message stream

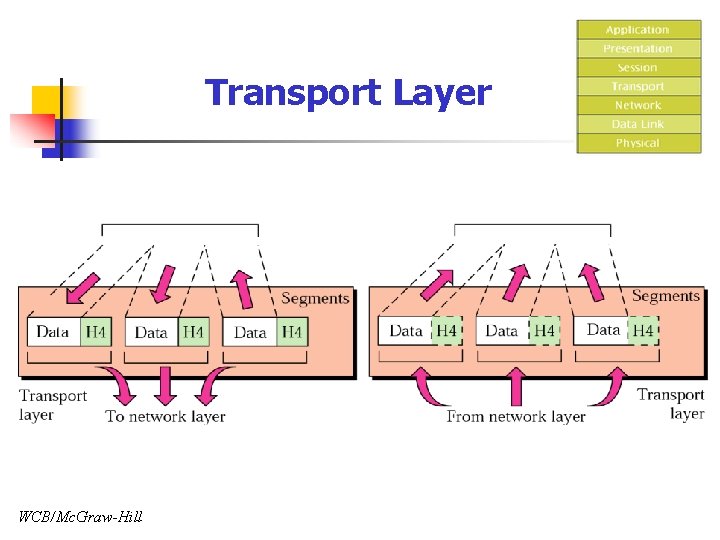
Transport Layer WCB/Mc. Graw-Hill

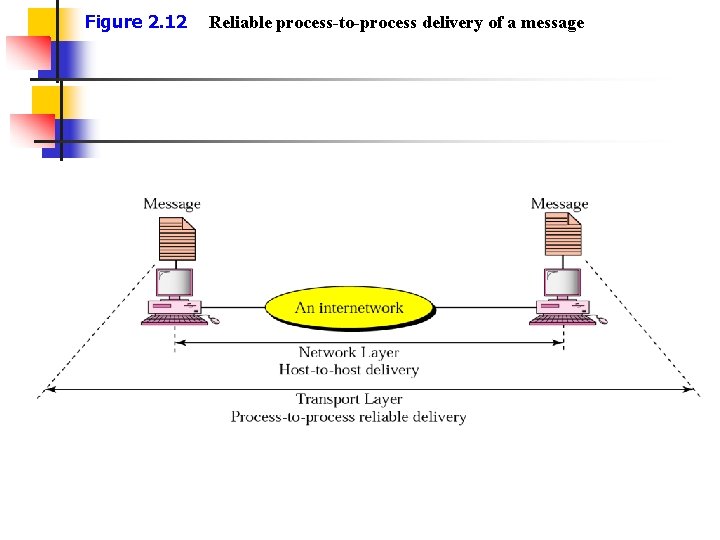
Figure 2. 12 Reliable process-to-process delivery of a message

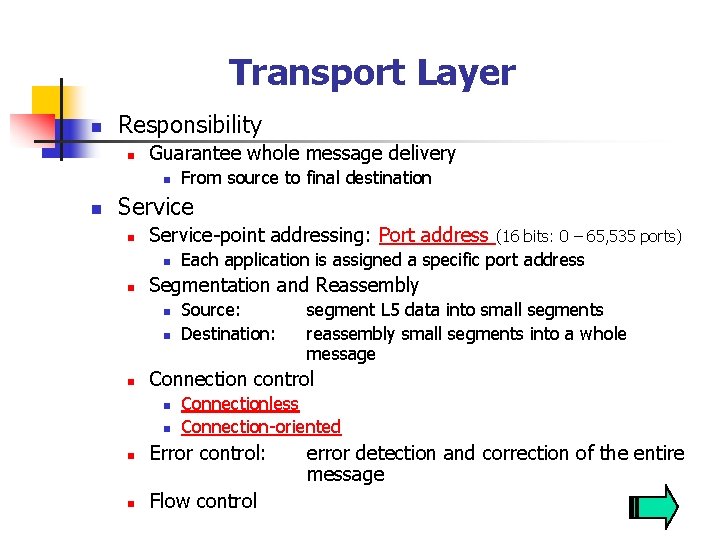
Transport Layer n Responsibility n Guarantee whole message delivery n n From source to final destination Service-point addressing: Port address n n Each application is assigned a specific port address Segmentation and Reassembly n n n (16 bits: 0 – 65, 535 ports) Source: Destination: segment L 5 data into small segments reassembly small segments into a whole message Connection control n n Connectionless Connection-oriented n Error control: n Flow control error detection and correction of the entire message

Port Address n n Handy way for computers and users to keep track of which port belongs to what program Ports are numbered from 0 to 65, 535 n n The Internet Assigned Numbers Authority (IANA) decided to reserve the first 1024 port numbers (i. e. , 0 to 1023) for requesting entities. Ports 1024 - 49, 151: registered port numbers Ports 49, 152 - 65, 535: dynamic or private port numbers General ways to use port number for source and destination n n Well-known port numbers -> usually for destination port Ramdomly generate -> for source port http: //www. winnetmag. com/Windows. Scripting/Article. ID/40313/Windows. Scripting_40313. html

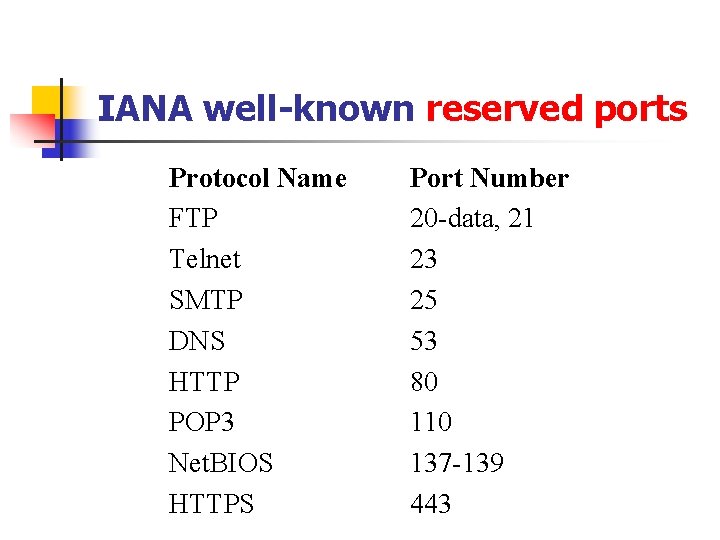
IANA well-known reserved ports Protocol Name FTP Telnet SMTP DNS HTTP POP 3 Net. BIOS HTTPS Port Number 20 -data, 21 23 25 53 80 110 137 -139 443

Sample port numbers for popular applications Application MSN Messenger IRC ICQ Port Number 1863, 6666 -6670, 7000 4000 -4001 ICQ AOL Instant Messenger PCAnywhere Real. Audio Napster Half-Life game 4000 -4001 5190, 6040 5631 -5632 7070, 6970 -7170 7777, 8875, 8888 27, 018

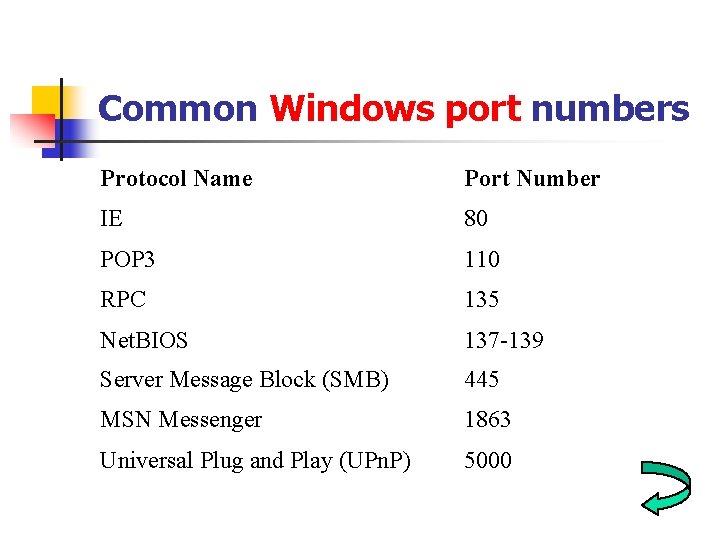
Common Windows port numbers Protocol Name Port Number IE 80 POP 3 110 RPC 135 Net. BIOS 137 -139 Server Message Block (SMB) 445 MSN Messenger 1863 Universal Plug and Play (UPn. P) 5000

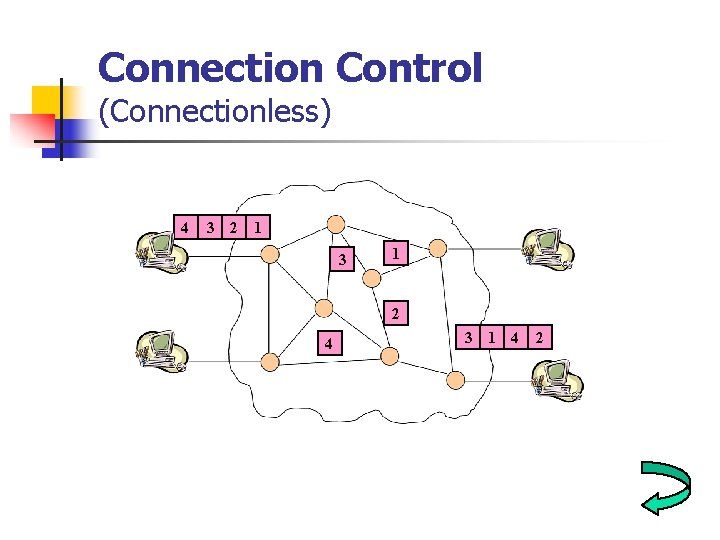
Connection Control (Connectionless) 4 3 2 1 3 1 2 4 3 1 4 2

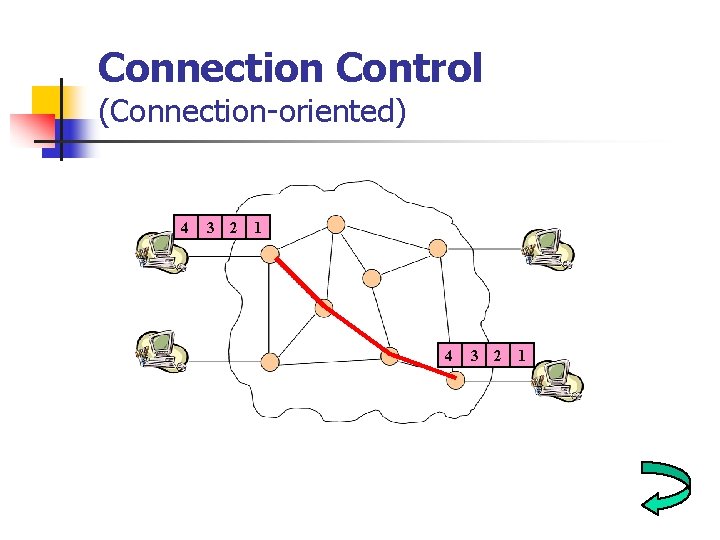
Connection Control (Connection-oriented) 4 3 2 1

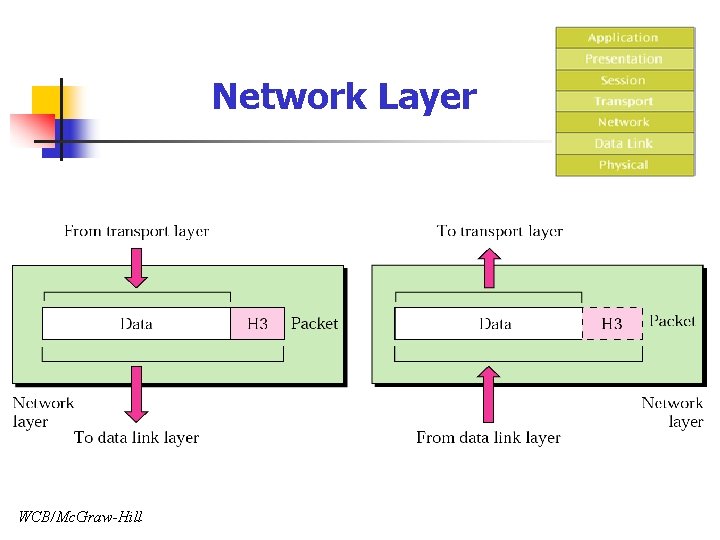
Network Layer WCB/Mc. Graw-Hill

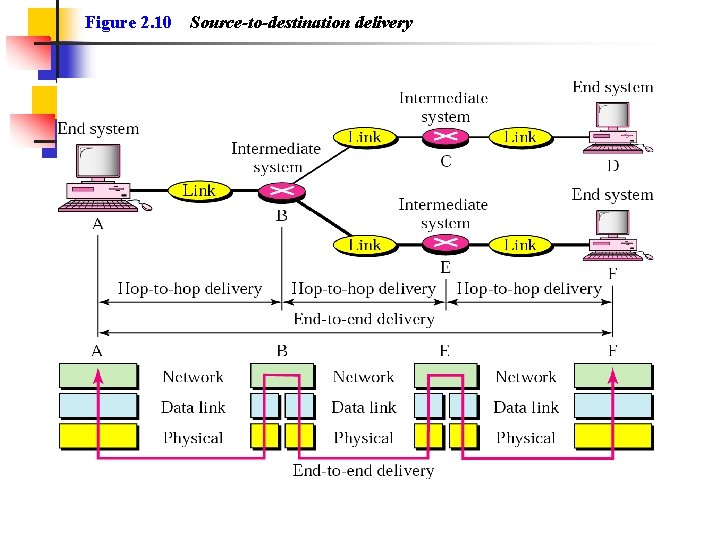
Figure 2. 10 Source-to-destination delivery

Network Layer n Responsibility n n Guarantee packet delivery Service n n Logical (Network) address (header): IP address Routing packets through internetworking device n Router || Gateway

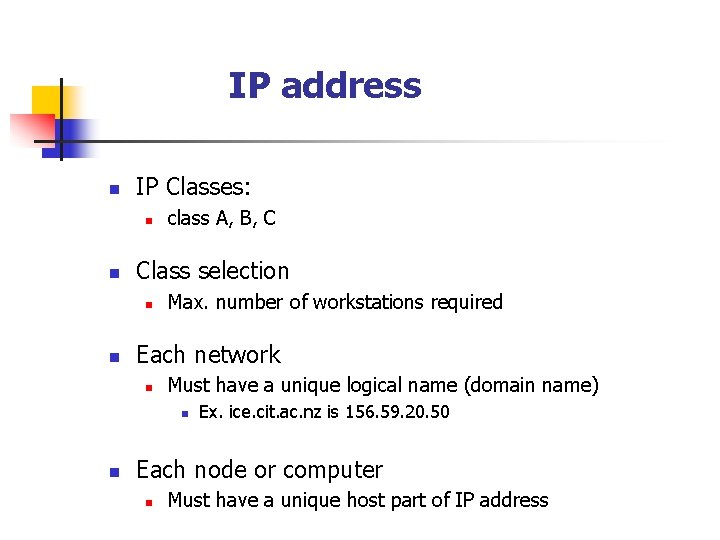
IP address n IP Classes: n n Class selection n n class A, B, C Max. number of workstations required Each network n Must have a unique logical name (domain name) n n Ex. ice. cit. ac. nz is 156. 59. 20. 50 Each node or computer n Must have a unique host part of IP address

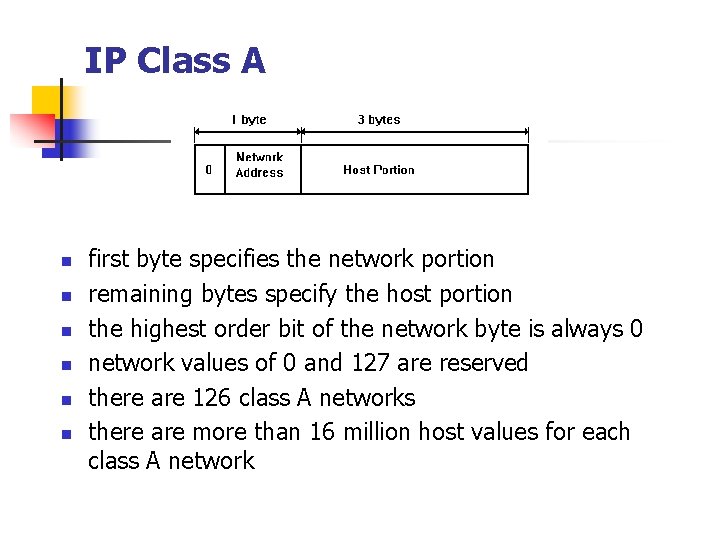
IP Class A n n n first byte specifies the network portion remaining bytes specify the host portion the highest order bit of the network byte is always 0 network values of 0 and 127 are reserved there are 126 class A networks there are more than 16 million host values for each class A network

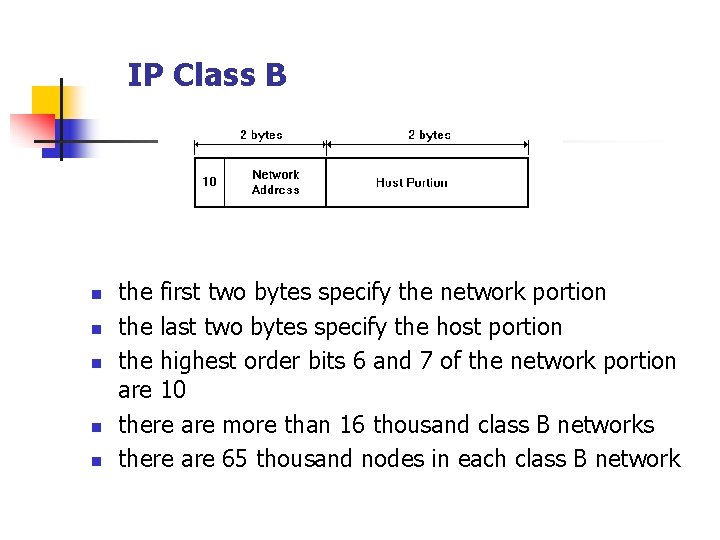
IP Class B n n n the first two bytes specify the network portion the last two bytes specify the host portion the highest order bits 6 and 7 of the network portion are 10 there are more than 16 thousand class B networks there are 65 thousand nodes in each class B network

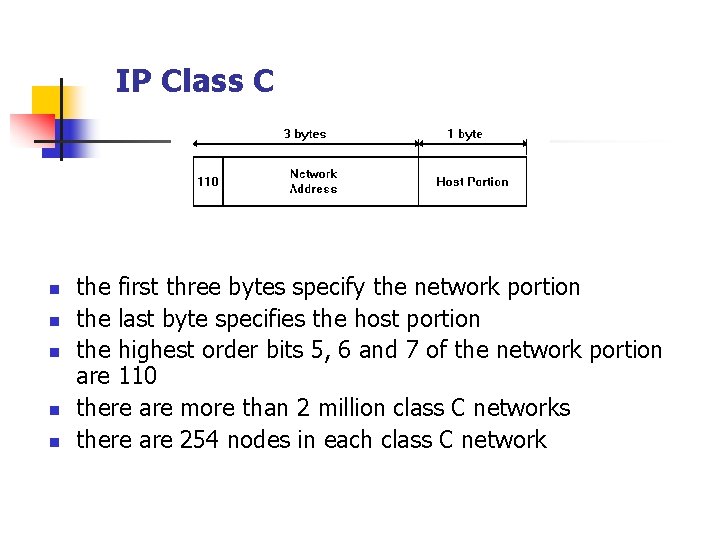
IP Class C n n n the first three bytes specify the network portion the last byte specifies the host portion the highest order bits 5, 6 and 7 of the network portion are 110 there are more than 2 million class C networks there are 254 nodes in each class C network

Reserved IP Addresses n n n Network Addresses : The host portion is set to all zero's (129. 47. 0. 0) Broadcast Address : The host portion is set to all one's (129. 47. 255) Loopback Addresses : 127. 0. 0. 0 and 127. 0. 0. 1



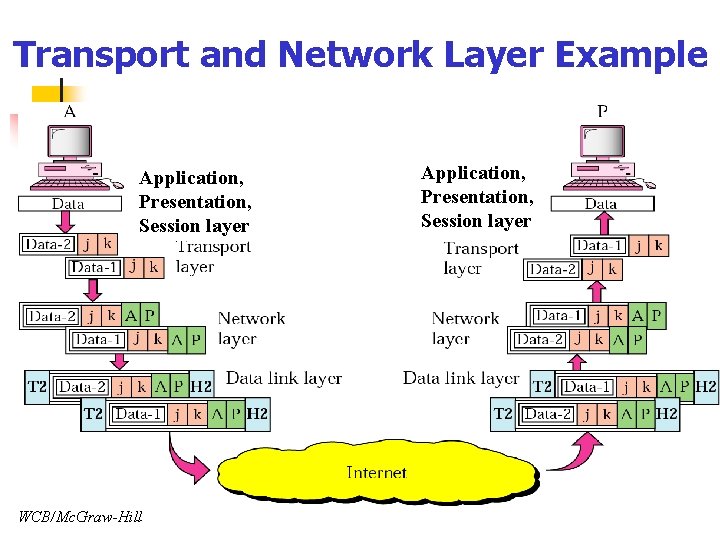
Transport and Network Layer Example Application, Presentation, Session layer WCB/Mc. Graw-Hill Application, Presentation, Session layer

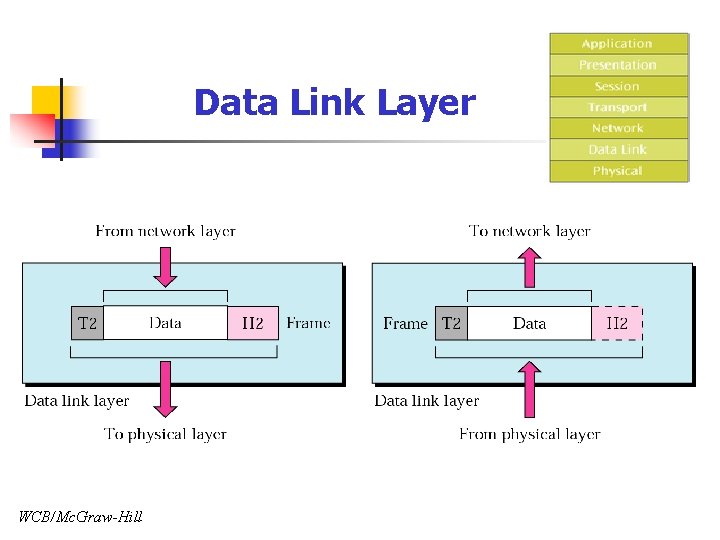
Data Link Layer WCB/Mc. Graw-Hill

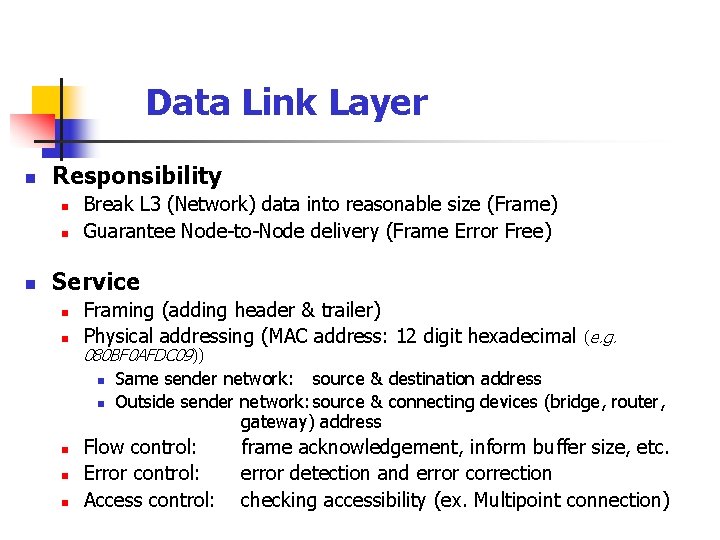
Data Link Layer n Responsibility n n n Break L 3 (Network) data into reasonable size (Frame) Guarantee Node-to-Node delivery (Frame Error Free) Service n n Framing (adding header & trailer) Physical addressing (MAC address: 12 digit hexadecimal (e. g. 080 BF 0 AFDC 09)) n n n Same sender network: source & destination address Outside sender network: source & connecting devices (bridge, router, gateway) address Flow control: Error control: Access control: frame acknowledgement, inform buffer size, etc. error detection and error correction checking accessibility (ex. Multipoint connection)

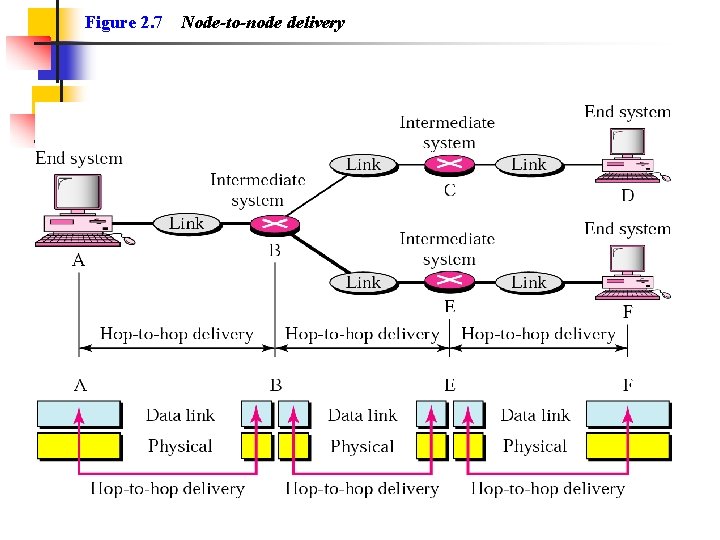
Figure 2. 7 Node-to-node delivery

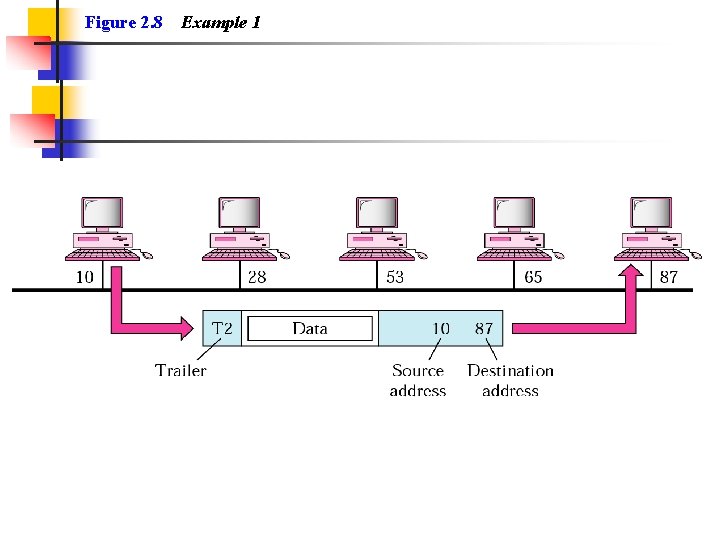
Example 1 In Figure 2. 8 a node with physical address 10 sends a frame to a node with physical address 87. The two nodes are connected by a link. At the data link level this frame contains physical addresses in the header. These are the only addresses needed. The rest of the header contains other information needed at this level. The trailer usually contains extra bits needed for error detection

Figure 2. 8 Example 1

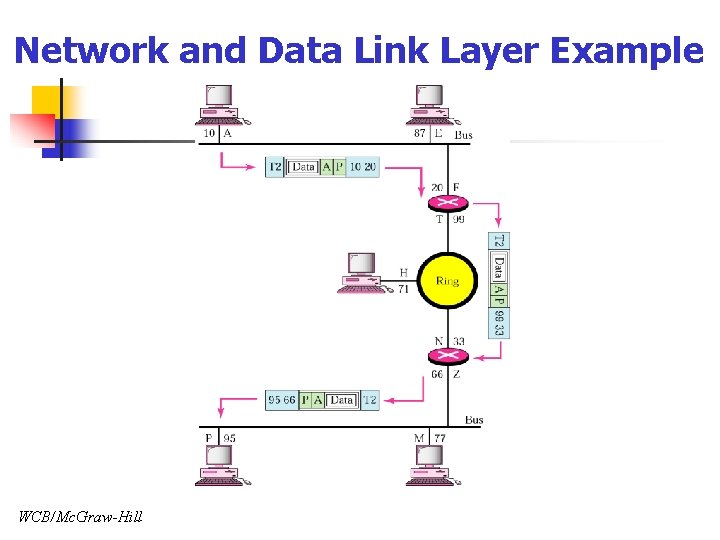
Network and Data Link Layer Example WCB/Mc. Graw-Hill

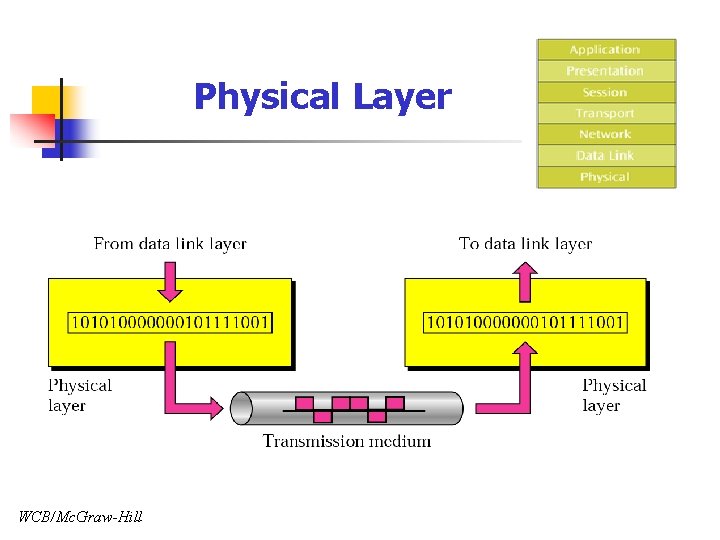
Physical Layer WCB/Mc. Graw-Hill

Physical Layer n Responsibility n n Sending and receiving bitstream through physical medium Service n n n Physical characteristics of interface and medium Representation of bits (encoding or modulation) Data rate Bit synchronization Line configuration & Topology Transmission mode (Simplex, Half-duplex, Full-duplex)

Summary of Layer Functions WCB/Mc. Graw-Hill