Chapter 1 Introduction Security Violations OSI Security Architecture






![OSI Security Architecture Non-Repudiation SENDER VERIFICATION: A m, [A] B(m, [A]) m A RECEIVER OSI Security Architecture Non-Repudiation SENDER VERIFICATION: A m, [A] B(m, [A]) m A RECEIVER](https://slidetodoc.com/presentation_image_h/a358096cf4f124b05a26057074ede67c/image-13.jpg)





- Slides: 20

Chapter 1 Introduction • Security Violations • OSI Security Architecture • Network Security Model Block Ciphers

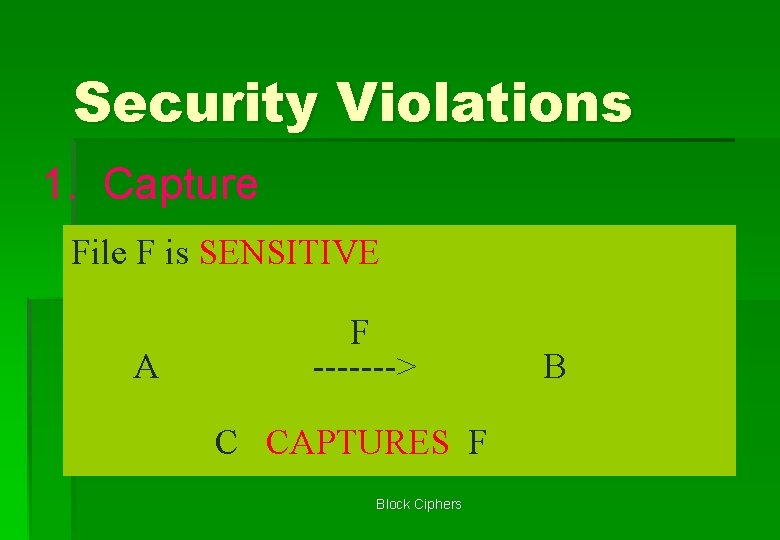
Security Violations 1. Capture File F is SENSITIVE A F -------> C CAPTURES F Block Ciphers B

Security Violations 2. Intercept - Update Authorisation File F is SENSITIVE A sends message to B: ”Update F with names” A(m) m B(F) C INTERCEPTS m and adds name of C A(m) m C(m) m B(F) Block Ciphers

Security Violations 3. Substitute Authorisation File F is SENSITIVE C PRETENDS to be A C sends message to B: ”Update F with name of C” {C}A(m) m Block Ciphers B(F)

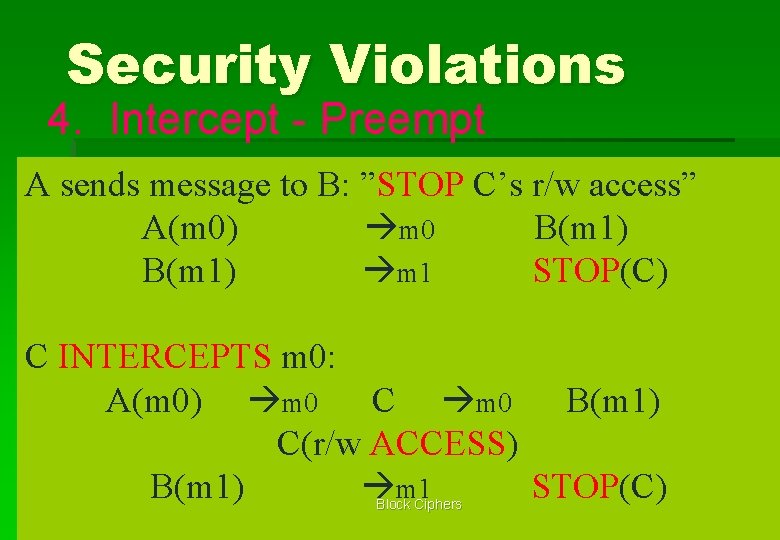
Security Violations 4. Intercept - Preempt A sends message to B: ”STOP C’s r/w access” A(m 0) m 0 B(m 1) m 1 STOP(C) C INTERCEPTS m 0: A(m 0) m 0 C m 0 B(m 1) C(r/w ACCESS) B(m 1) m 1 STOP(C) Block Ciphers

Security Violations 5. Denial C sends message to B C(m) m B Later, B QUERIES C about message B m, ? C C DENIES sending message C(m, ? ) NO Block Ciphers B

OSI Security Architecture (X. 800 – Security for Open Systems Interconnection) • International Standard • 5 Categories • 14 Services Block Ciphers

OSI Security Architecture Categories(services) • Authentication (peer-entity, data-origin) • Access Control • Data Confidentiality (connection, connectionless, selective-field, traffic-flow) • Data Integrity (connection[recovery, no-recovery, selective-field], connectionless[no-recovery, selective-field]) • Non. Repudiation (origin, destination) Block Ciphers

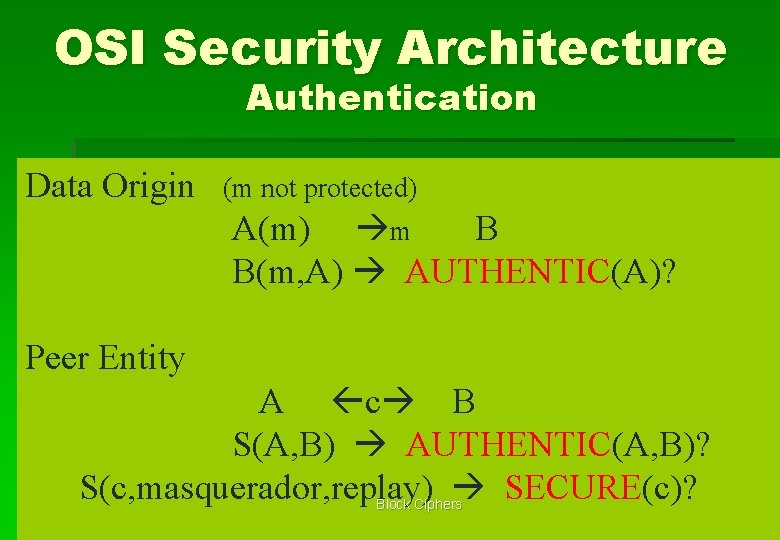
OSI Security Architecture Authentication Data Origin (m not protected) A(m) m B B(m, A) AUTHENTIC(A)? Peer Entity A c B S(A, B) AUTHENTIC(A, B)? S(c, masquerador, replay) SECURE(c)? Block Ciphers

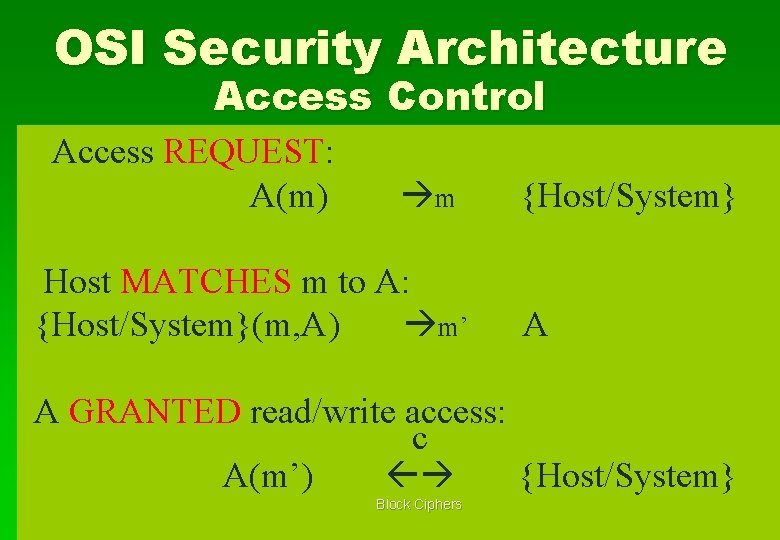
OSI Security Architecture Access Control Access REQUEST: A(m) m Host MATCHES m to A: {Host/System}(m, A) m’ {Host/System} A A GRANTED read/write access: c A(m’) {Host/System} Block Ciphers

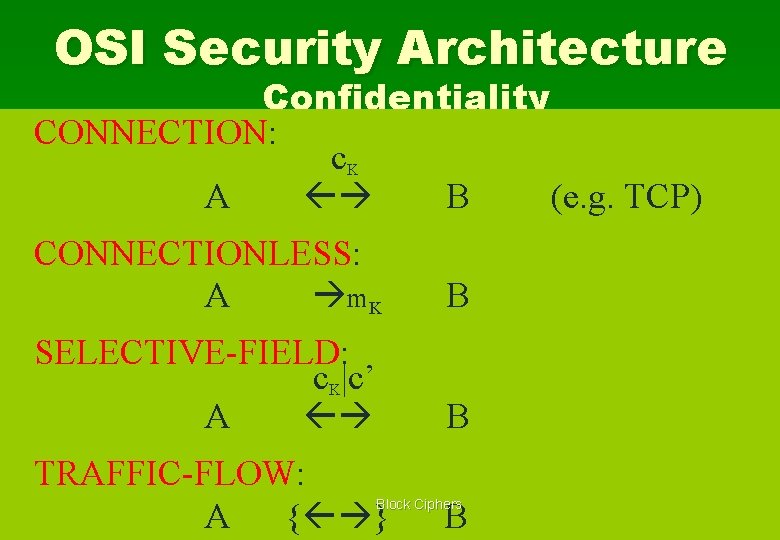
OSI Security Architecture Confidentiality CONNECTION: c. K A B (e. g. TCP) CONNECTIONLESS: A m K B SELECTIVE-FIELD: c. K|c’ A B TRAFFIC-FLOW: A { } B Block Ciphers

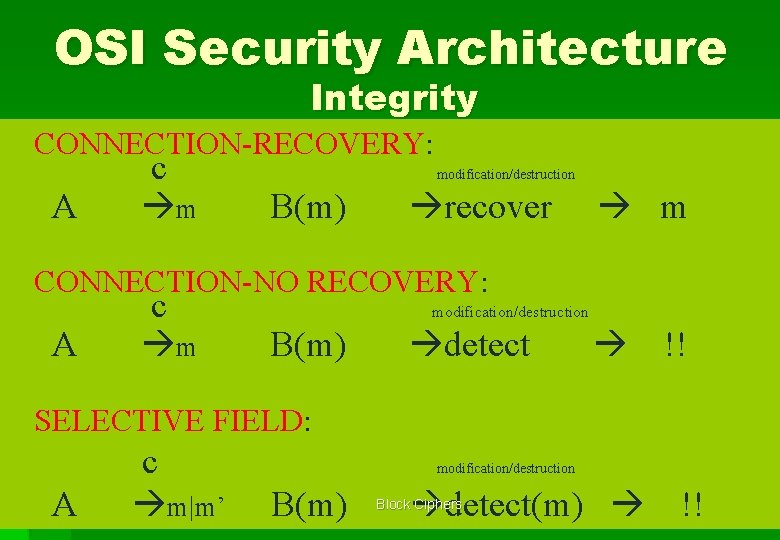
OSI Security Architecture Integrity CONNECTION-RECOVERY: A c m modification/destruction B(m) recover m CONNECTION-NO RECOVERY: A c m modification/destruction B(m) detect !! SELECTIVE FIELD: A c m|m’ modification/destruction B(m) detect(m) Block Ciphers !!
![OSI Security Architecture NonRepudiation SENDER VERIFICATION A m A Bm A m A RECEIVER OSI Security Architecture Non-Repudiation SENDER VERIFICATION: A m, [A] B(m, [A]) m A RECEIVER](https://slidetodoc.com/presentation_image_h/a358096cf4f124b05a26057074ede67c/image-13.jpg)
OSI Security Architecture Non-Repudiation SENDER VERIFICATION: A m, [A] B(m, [A]) m A RECEIVER VERIFICATION: A m B B [m], [B] A([m], [B]) m B Block Ciphers

OSI Security Architecture Availability • Upon request • Denial of Service • Attack Countermeasures: Authentication Encryption Physical Response Block Ciphers

SECURITY MECHANISMS (X. 800) - specific • Encipherment – unintelligible • Signature – data tag to ensure a) Source b) Integrity c) anti-forgery • Access Control • Data Integrity • Authentication • Traffic Padding – prevent traffic analysis • Routing Control – adapt upon partial failure • Notarization – trusted third party Block Ciphers

SECURITY MECHANISMS (X. 800) - pervasive • Trusted Functionality • Security Label • Event Detection • Audit Trail • Recovery Block Ciphers

ATTACKS • PASSIVE: System unaltered, – hard to detect, easier to prevent • ACTIVE: System altered, – easier to detect, hard to prevent Block Ciphers

ATTACKS • PASSIVE: eavesdropping, message release, • ACTIVE: replay, modification, monitoring, traffic analysis masquerade(impersonation), denial of service(supression, overload) Block Ciphers

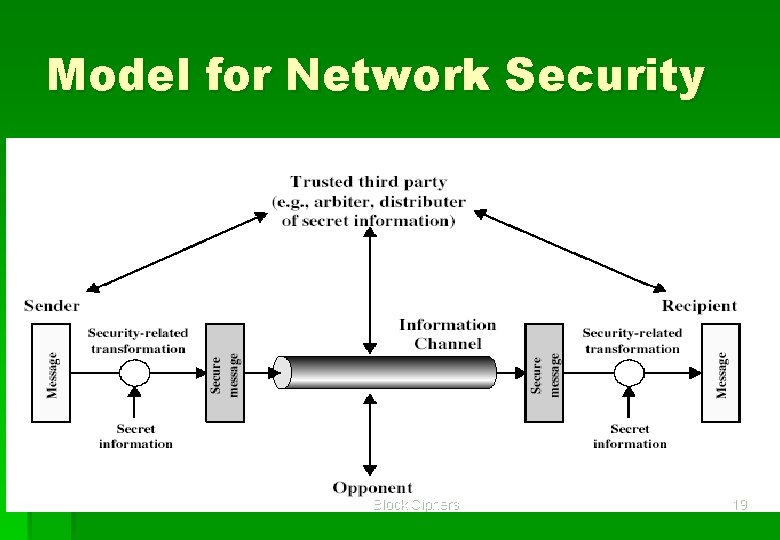
Model for Network Security Block Ciphers 19

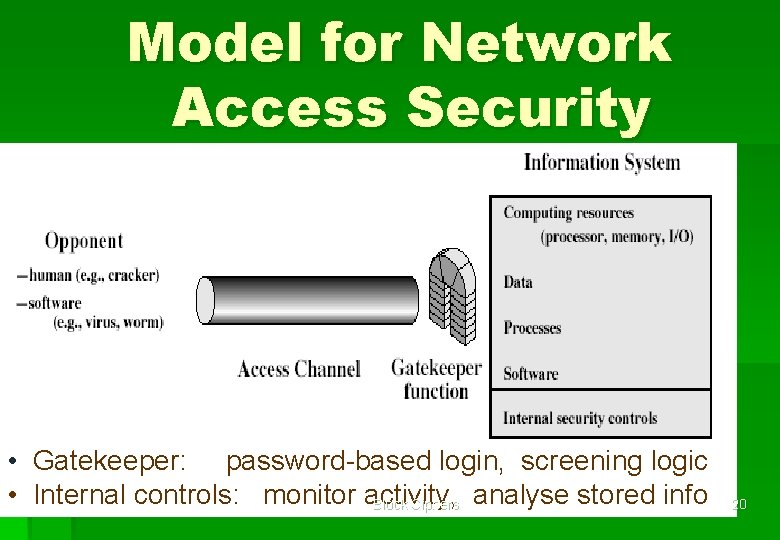
Model for Network Access Security • Gatekeeper: password-based login, screening logic • Internal controls: monitor activity, Block Ciphers analyse stored info 20