Chair Professor ChinChen Chang n National Tsing Hua

![Proposed Scheme [1/8] The Core of our method… Turtle Shell Based Matrix 22 Proposed Scheme [1/8] The Core of our method… Turtle Shell Based Matrix 22](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-22.jpg)
![Proposed Scheme [2/8] 2( 3( 2 4 3 1 2 7 ( 5 ( Proposed Scheme [2/8] 2( 3( 2 4 3 1 2 7 ( 5 (](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-23.jpg)
![Proposed Scheme [3/8] … 255 9 8 7 Pixel b 6 5 4 3 Proposed Scheme [3/8] … 255 9 8 7 Pixel b 6 5 4 3](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-24.jpg)
![Proposed Scheme [4/8] 6 7 0 1 2 3 4 5 6 7 4 Proposed Scheme [4/8] 6 7 0 1 2 3 4 5 6 7 4](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-25.jpg)
![Proposed Scheme [5/8] 6 7 0 1 2 3 4 5 6 7 4 Proposed Scheme [5/8] 6 7 0 1 2 3 4 5 6 7 4](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-26.jpg)
![Proposed Scheme [6/8] 3 6 4 4 5 0 1 7 71 80 55 Proposed Scheme [6/8] 3 6 4 4 5 0 1 7 71 80 55](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-27.jpg)
![Proposed Scheme [7/8] 4 4 4 5 7 71 80 55 2 12 30 Proposed Scheme [7/8] 4 4 4 5 7 71 80 55 2 12 30](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-28.jpg)
![Proposed Scheme [8/8] 4 4 3 6 4 5 2 2 6 7 0 Proposed Scheme [8/8] 4 4 3 6 4 5 2 2 6 7 0](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-29.jpg)
![Experimental Results [1/3] 30 Experimental Results [1/3] 30](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-30.jpg)
![Experimental Results [2/3] Table I. Comparisons of PSNRs and ECs of the proposed scheme Experimental Results [2/3] Table I. Comparisons of PSNRs and ECs of the proposed scheme](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-31.jpg)
![Experimental Results [3/3] Table II. Comparisons of PSNRs between the proposed scheme and various Experimental Results [3/3] Table II. Comparisons of PSNRs between the proposed scheme and various](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-32.jpg)
![Conclusions & Future Directions [1/2] ■ Conclusions 1. Simple embedding & extracting 2. Goal: Conclusions & Future Directions [1/2] ■ Conclusions 1. Simple embedding & extracting 2. Goal:](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-33.jpg)
![Conclusions & Future Directions [2/2] ■ Future directions 1. Reversability 2. Applications-Authentication & Watermarking Conclusions & Future Directions [2/2] ■ Future directions 1. Reversability 2. Applications-Authentication & Watermarking](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-34.jpg)

- Slides: 35

基於龜殼魔術矩陣的隱寫技術及 其衍生的研究問題 Chair Professor Chin-Chen Chang (張真誠) n National Tsing Hua University n National Chung Cheng University n Feng Chia University http: //msn. iecs. fcu. edu. tw/~ccc

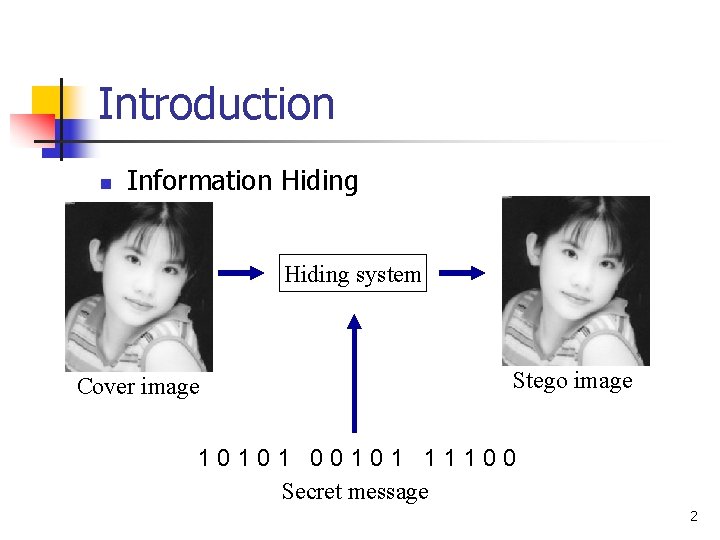
Introduction n Information Hiding system Cover image Stego image 10101 00101 11100 Secret message 2

Introduction (Cont. ) n Cover Carriers n n Image Video Sound Text 3

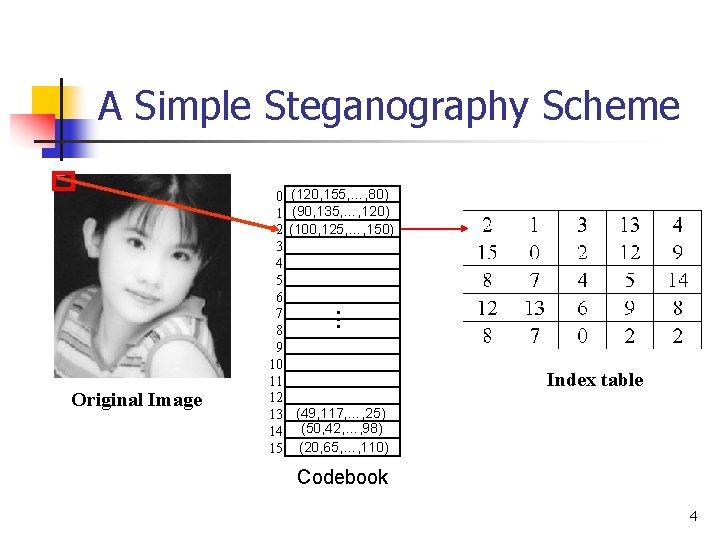
A Simple Steganography Scheme (120, 155, …, 80) (90, 135, …, 120) (100, 125, …, 150) … Original Image 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Index table (49, 117, …, 25) (50, 42, …, 98) (20, 65, …, 110) Codebook 4

Previous Work of Steganography on VQ To find the closest pairs 5

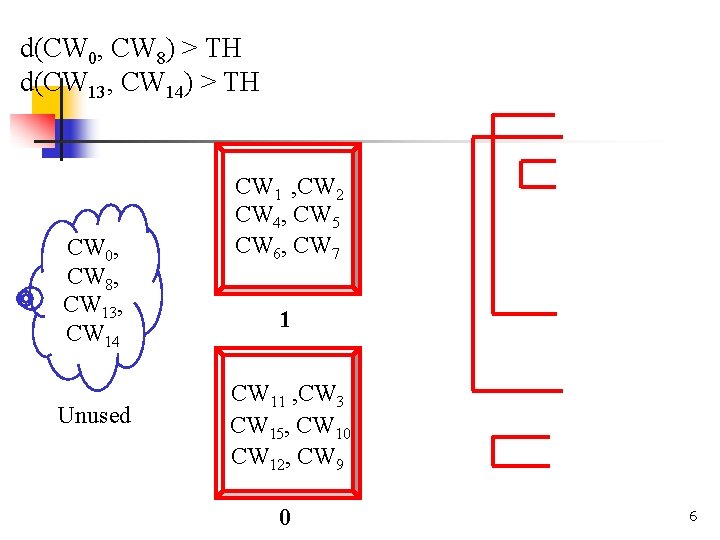
d(CW 0, CW 8) > TH d(CW 13, CW 14) > TH CW 0, CW 8, CW 13, CW 14 Unused CW 1 , CW 2 CW 4, CW 5 CW 6, CW 7 1 CW 11 , CW 3 CW 15, CW 10 CW 12, CW 9 0 6

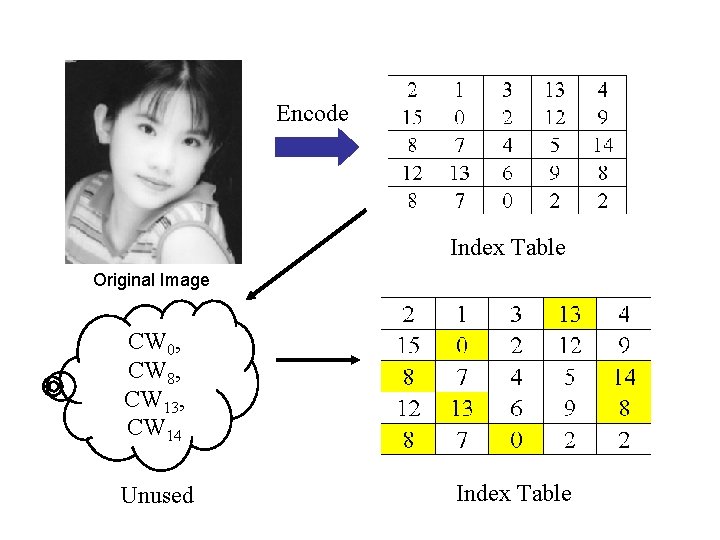
Encode Index Table Original Image CW 0, CW 8, CW 13, CW 14 Unused Index Table

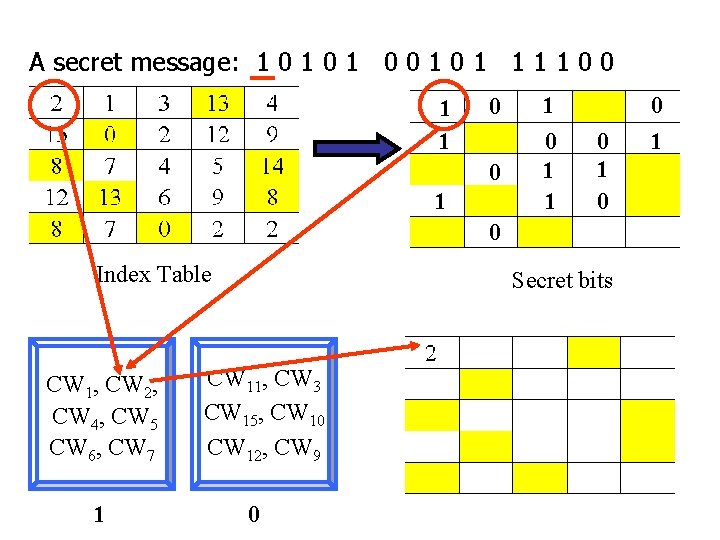
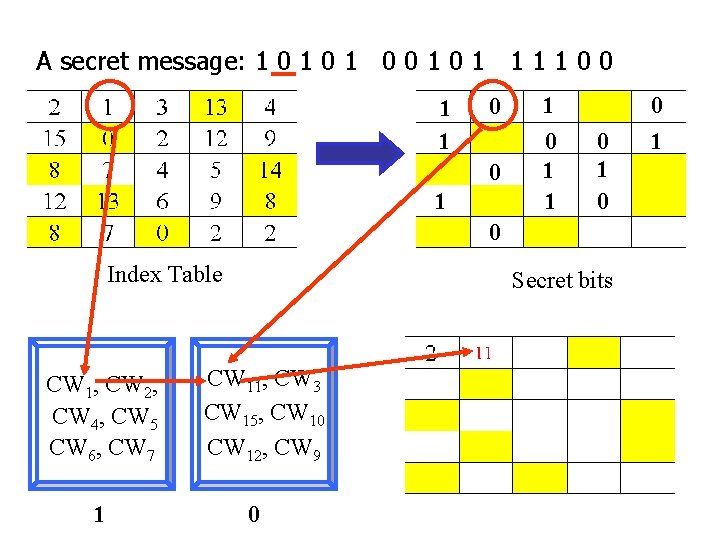
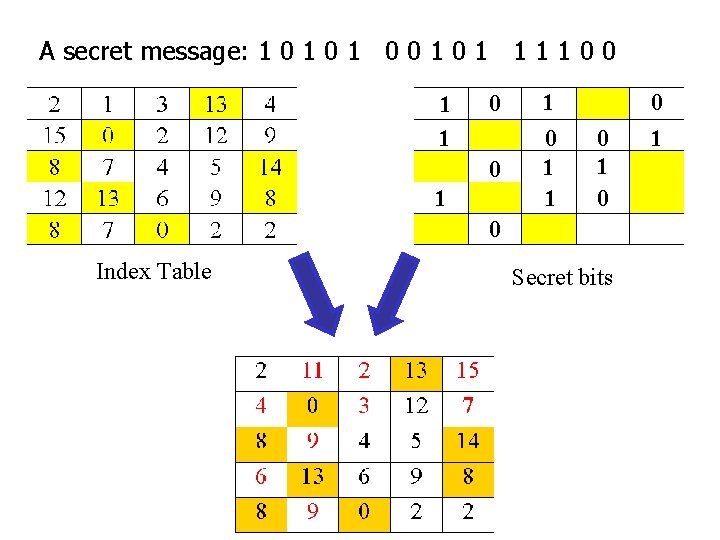
A secret message: 1 0 1 0 0 1 1 1 1 0 0 1 1 0 1 0 0 Index Table CW 1, CW 2, CW 4, CW 5 CW 6, CW 7 1 Secret bits CW 11, CW 3 CW 15, CW 10 CW 12, CW 9 0 0 1

A secret message: 1 0 1 0 0 1 1 1 1 0 0 1 1 0 1 0 0 Index Table CW 1, CW 2, CW 4, CW 5 CW 6, CW 7 1 Secret bits CW 11, CW 3 CW 15, CW 10 CW 12, CW 9 0 0 1

A secret message: 1 0 1 0 0 1 1 1 1 0 0 1 1 0 1 0 0 Index Table Secret bits 0 1

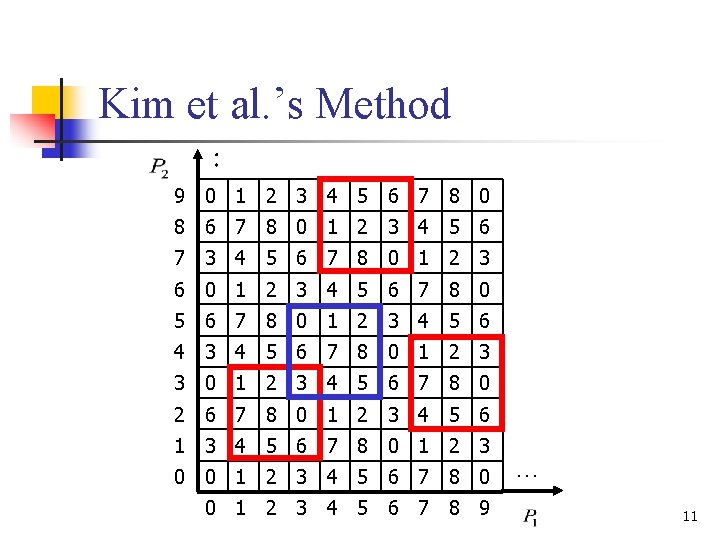
Kim et al. ’s Method : 9 0 1 2 3 4 5 6 7 8 0 8 6 7 8 0 1 2 3 4 5 6 7 8 0 1 2 3 6 0 1 2 3 4 5 6 7 8 0 1 2 3 4 5 6 4 3 4 5 6 7 8 0 1 2 3 3 0 1 2 3 4 5 6 7 8 0 2 6 7 8 0 1 2 3 4 5 6 1 3 4 5 6 7 8 0 1 2 3 0 0 1 2 3 4 5 6 7 8 9 … 11

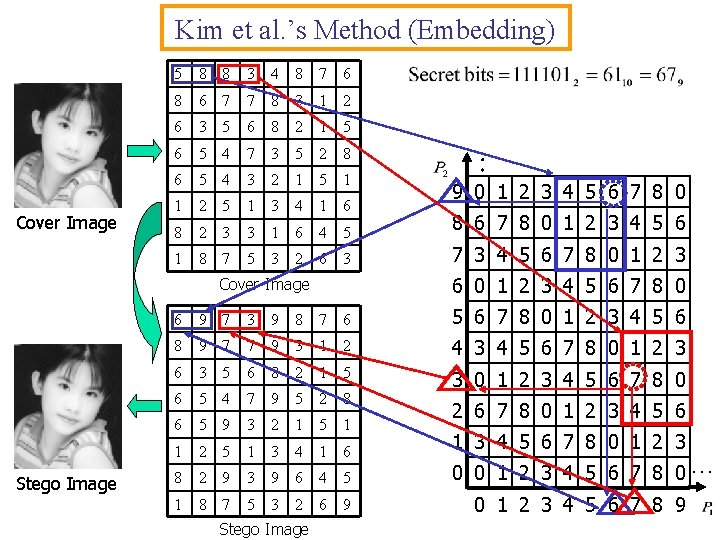
Kim et al. ’s Method (Embedding) Cover Image 5 8 8 3 4 8 7 6 8 6 7 7 8 3 1 2 6 3 5 6 8 2 1 5 6 5 4 7 3 5 2 8 6 5 4 3 2 1 5 1 1 2 5 1 3 4 1 6 8 2 3 3 1 6 4 5 8 6 7 8 0 1 2 3 4 5 6 1 8 7 5 3 2 6 3 7 3 4 5 6 7 8 0 1 2 3 9 0 1 2 3 4 5 6 7 8 0 6 0 1 2 3 4 5 6 7 8 0 Cover Image Stego Image : 6 9 7 3 9 8 7 6 5 6 7 8 0 1 2 3 4 5 6 8 9 7 7 9 3 1 2 4 3 4 5 6 7 8 0 1 2 3 6 3 5 6 8 2 1 5 6 5 4 7 9 5 2 8 3 0 1 2 3 4 5 6 7 8 0 6 5 9 3 2 1 5 1 1 2 5 1 3 4 1 6 8 2 9 3 9 6 4 5 1 8 7 5 3 2 6 9 Stego Image 2 6 7 8 0 1 2 3 4 5 6 1 3 4 5 6 7 8 0 1 2 3 0 0 1 2 3 4 5 6 7 8 0… 0 1 2 3 4 5 6 7 8 9

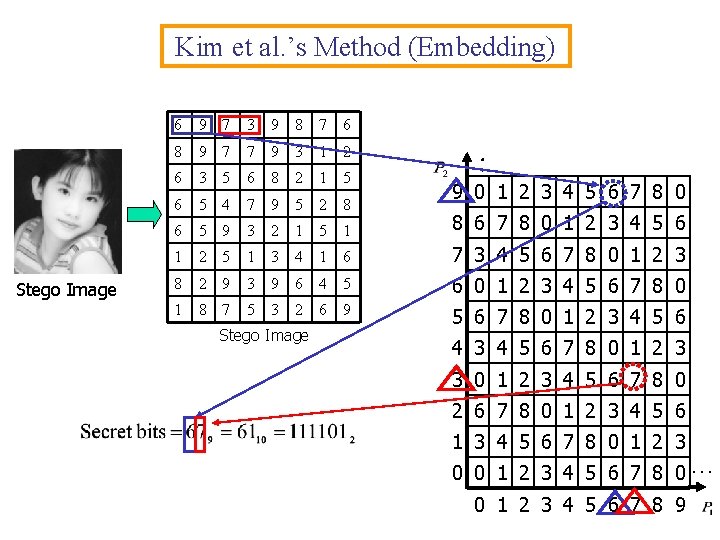
Kim et al. ’s Method (Embedding) Stego Image 6 9 7 3 9 8 7 6 8 9 7 7 9 3 1 2 6 3 5 6 8 2 1 5 6 5 4 7 9 5 2 8 6 5 9 3 2 1 5 1 8 6 7 8 0 1 2 3 4 5 6 1 2 5 1 3 4 1 6 7 3 4 5 6 7 8 0 1 2 3 8 2 9 3 9 6 4 5 6 0 1 2 3 4 5 6 7 8 0 1 8 7 5 3 2 6 9 5 6 7 8 0 1 2 3 4 5 6 Stego Image : 9 0 1 2 3 4 5 6 7 8 0 4 3 4 5 6 7 8 0 1 2 3 3 0 1 2 3 4 5 6 7 8 0 2 6 7 8 0 1 2 3 4 5 6 1 3 4 5 6 7 8 0 1 2 3 0 0 1 2 3 4 5 6 7 8 0… 0 1 2 3 4 5 6 7 8 9

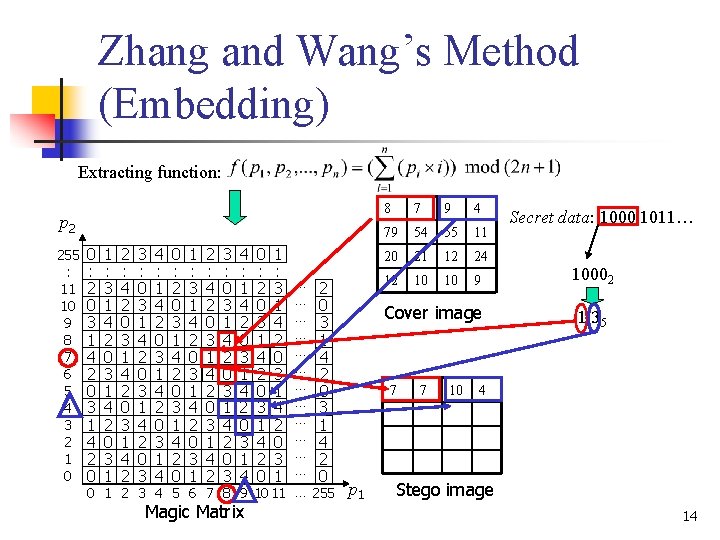
Zhang and Wang’s Method (Embedding) Extracting function: p 2 255 : 11 10 9 8 7 6 5 4 3 2 1 0 0 : 2 0 3 1 4 2 0 1 : 3 1 4 2 0 3 1 2 : 4 2 0 3 1 4 2 3 : 0 3 1 4 2 0 3 4 : 1 4 2 0 3 1 4 0 : 2 0 3 1 4 2 0 1 : 3 1 4 2 0 3 1 … … … 2 0 3 1 4 2 0 0 1 2 3 4 5 6 7 8 9 10 11 … 255 Magic Matrix 8 7 9 4 79 54 55 11 20 21 12 24 12 10 10 9 Cover image 7 p 1 7 10 Secret data: 1000 1011… 10002 1 35 4 Stego image 14

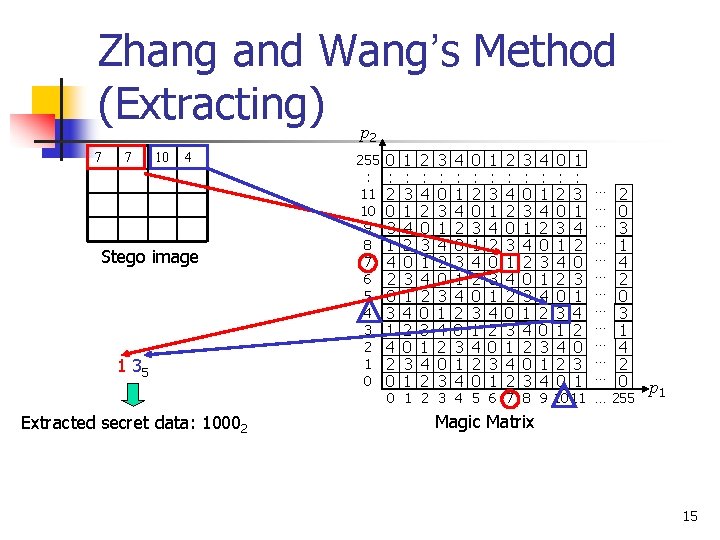
Zhang and Wang’s Method (Extracting) p 2 7 7 10 4 Stego image 1 35 255 : 11 10 9 8 7 6 5 4 3 2 1 0 0 : 2 0 3 1 4 2 0 1 : 3 1 4 2 0 3 1 2 : 4 2 0 3 1 4 2 3 : 0 3 1 4 2 0 3 4 : 1 4 2 0 3 1 4 0 : 2 0 3 1 4 2 0 1 : 3 1 4 2 0 3 1 … … … 2 0 3 1 4 2 0 0 1 2 3 4 5 6 7 8 9 10 11 … 255 Extracted secret data: 10002 p 1 Magic Matrix 15

Sudoku n A logic-based number placement puzzle 16

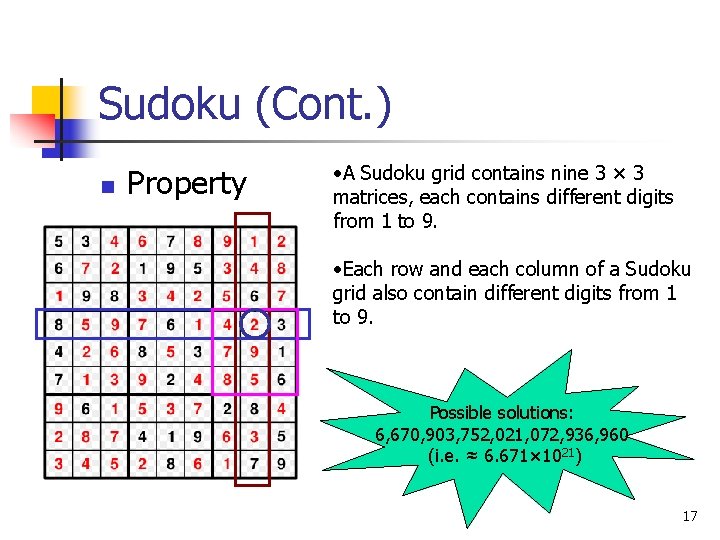
Sudoku (Cont. ) n Property • A Sudoku grid contains nine 3 × 3 matrices, each contains different digits from 1 to 9. • Each row and each column of a Sudoku grid also contain different digits from 1 to 9. Possible solutions: 6, 670, 903, 752, 021, 072, 936, 960 (i. e. ≈ 6. 671× 1021) 17

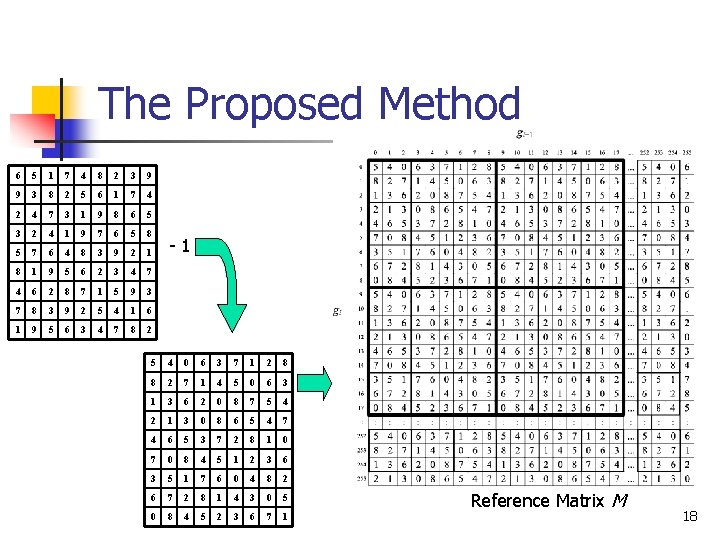
The Proposed Method 6 5 1 7 4 8 2 3 9 9 3 8 2 5 6 1 7 4 2 4 7 3 1 9 8 6 5 3 2 4 1 9 7 6 5 8 5 7 6 4 8 3 9 2 1 8 1 9 5 6 2 3 4 7 4 6 2 8 7 1 5 9 3 7 8 3 9 2 5 4 1 6 1 9 5 6 3 4 7 8 2 -1 5 4 0 6 3 7 1 2 8 8 2 7 1 4 5 0 6 3 1 3 6 2 0 8 7 5 4 2 1 3 0 8 6 5 4 7 4 6 5 3 7 2 8 1 0 7 0 8 4 5 1 2 3 6 3 5 1 7 6 0 4 8 2 6 7 2 8 1 4 3 0 5 0 8 4 5 2 3 6 7 1 Reference Matrix M 18

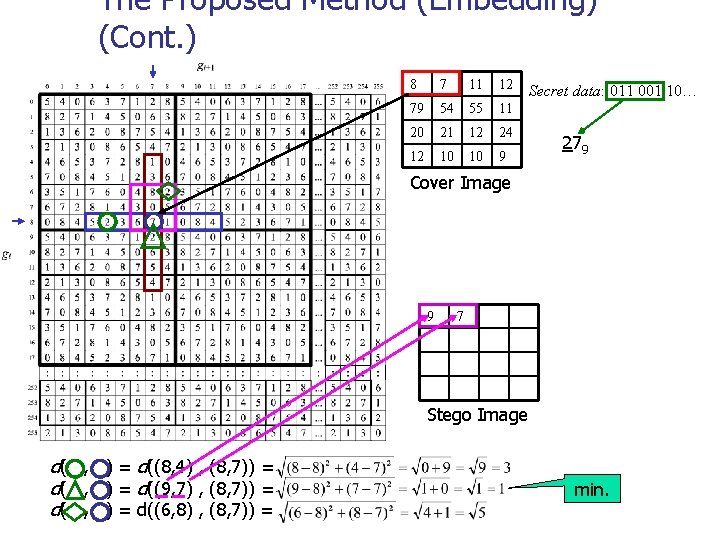
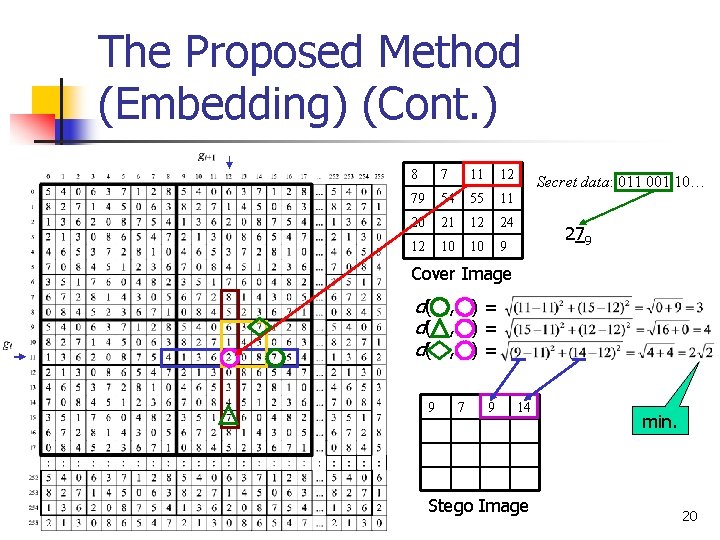
The Proposed Method (Embedding) (Cont. ) 8 7 11 12 79 54 55 11 20 21 12 24 12 10 10 9 Secret data: 011 001 10… 279 Cover Image 9 7 Stego Image d( , ) = d((8, 4) , (8, 7)) = d( , ) = d((9, 7) , (8, 7)) = d( , ) = d((6, 8) , (8, 7)) = min.

The Proposed Method (Embedding) (Cont. ) 8 7 11 12 79 54 55 11 20 21 12 24 12 10 10 9 Secret data: 011 001 10… 279 Cover Image d( , ) = 9 7 9 14 Stego Image min. 20

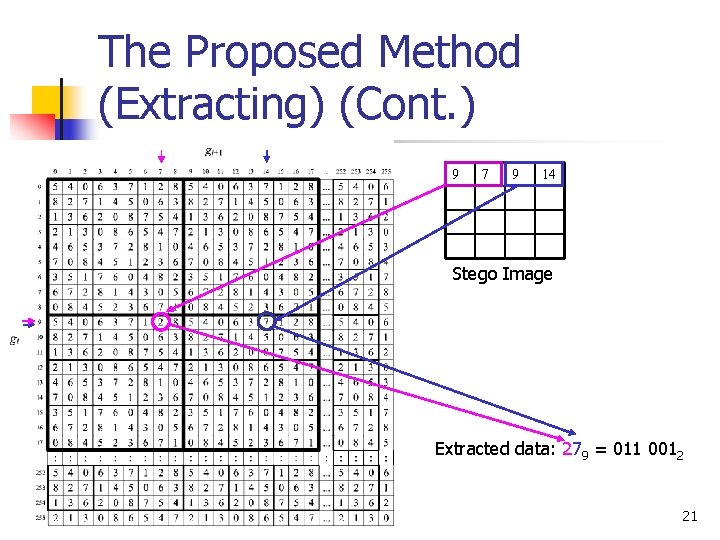
The Proposed Method (Extracting) (Cont. ) 9 7 9 14 Stego Image Extracted data: 279 = 011 0012 21
![Proposed Scheme 18 The Core of our method Turtle Shell Based Matrix 22 Proposed Scheme [1/8] The Core of our method… Turtle Shell Based Matrix 22](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-22.jpg)
Proposed Scheme [1/8] The Core of our method… Turtle Shell Based Matrix 22
![Proposed Scheme 28 2 3 2 4 3 1 2 7 5 Proposed Scheme [2/8] 2( 3( 2 4 3 1 2 7 ( 5 (](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-23.jpg)
Proposed Scheme [2/8] 2( 3( 2 4 3 1 2 7 ( 5 ( 2 ( 0 0 1 2 3 4 5 6 7 0 1 2 3 4 5 6 2( 23
![Proposed Scheme 38 255 9 8 7 Pixel b 6 5 4 3 Proposed Scheme [3/8] … 255 9 8 7 Pixel b 6 5 4 3](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-24.jpg)
Proposed Scheme [3/8] … 255 9 8 7 Pixel b 6 5 4 3 2 1 0 2( 3( 2( 6 7 0 1 2 3 4 5 6 7 0 1 2 3 4 5 6 7 0 4 5 1 2 3 4 5 3 6 7 0 1 2 3 7 0 3 4 5 6 7 0 5 6 7 ( 5 ( 2 ( 0 0 2 6 2 4 3 1 2 7 1 2 3 4 5 6 7 0 1 2 3 4 5 6 Pixel a 7 8 9 … 255 24
![Proposed Scheme 48 6 7 0 1 2 3 4 5 6 7 4 Proposed Scheme [4/8] 6 7 0 1 2 3 4 5 6 7 4](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-25.jpg)
Proposed Scheme [4/8] 6 7 0 1 2 3 4 5 6 7 4 3 44 8 4 5 6 7 0 1 2 3 4 5 9 7 1 2 3 4 5 6 7 0 5 4 5 6 7 0 1 2 3 4 5 4 2 3 4 5 6 7 0 1 2 3 3 7 0 1 2 3 4 5 6 7 0 2 5 6 7 0 1 2 3 4 5 6 7 0 1 0 0 1 2 3 4 5 6 Pixel a Pixel b 9 3 5 4 4 7 71 80 55 21 64 73 28 83 23 202 57 11 0 1 2 12 30 95 91 9 76 42 19 3 7 55 234 39 27 40 18 0 42 215 89 255 107 59 16 11 6 99 200 64 185 97 21 23 243 2 3 25 101 235 79 57 33 198 211 7 0 1 7 8 9 110 000 111 6 2 0 7 25
![Proposed Scheme 58 6 7 0 1 2 3 4 5 6 7 4 Proposed Scheme [5/8] 6 7 0 1 2 3 4 5 6 7 4](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-26.jpg)
Proposed Scheme [5/8] 6 7 0 1 2 3 4 5 6 7 4 4 3 5 6 4 4 0 1 8 4 5 6 7 0 1 2 3 4 5 9 7 71 80 55 2 12 30 7 1 2 3 4 5 6 7 0 1 2 21 64 73 28 95 91 9 76 6 7 0 1 2 3 4 5 6 7 0 83 23 202 42 19 3 7 55 5 4 5 6 7 0 1 2 3 4 5 57 11 234 39 27 40 18 0 4 2 3 4 5 6 7 0 1 2 3 3 7 0 1 2 3 4 5 6 7 0 42 215 89 255 107 59 16 11 99 200 64 185 97 21 23 243 25 101 235 79 57 33 198 211 Pixel b 9 2 5 6 7 0 1 2 3 4 5 6 7 0 1 2 3 0 0 1 2 3 4 5 6 7 0 1 2 3 4 5 6 Pixel a 7 8 9 110 000 111 6 2 0 7 26
![Proposed Scheme 68 3 6 4 4 5 0 1 7 71 80 55 Proposed Scheme [6/8] 3 6 4 4 5 0 1 7 71 80 55](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-27.jpg)
Proposed Scheme [6/8] 3 6 4 4 5 0 1 7 71 80 55 2 12 30 21 64 73 28 95 91 9 76 83 23 202 42 19 3 7 55 57 11 234 39 27 40 18 0 42 215 89 255 107 59 16 11 99 200 64 185 97 21 23 243 25 101 235 79 57 33 198 211 4 4 6 7 0 1 2 3 4 5 6 7 8 4 5 6 7 0 1 2 3 4 5 9 7 1 2 3 4 5 6 7 0 5 4 5 6 7 0 1 2 3 4 5 4 2 3 4 5 6 7 0 1 2 3 3 7 0 1 2 3 4 5 6 7 0 Pixel b 9 2 5 6 7 0 1 2 3 4 5 6 7 0 1 2 3 0 0 1 2 3 4 5 6 7 0 1 2 3 4 5 6 Pixel a 7 8 9 110 000 111 6 2 0 7 27
![Proposed Scheme 78 4 4 4 5 7 71 80 55 2 12 30 Proposed Scheme [7/8] 4 4 4 5 7 71 80 55 2 12 30](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-28.jpg)
Proposed Scheme [7/8] 4 4 4 5 7 71 80 55 2 12 30 21 64 73 28 95 91 9 76 83 23 202 42 19 3 7 55 57 11 234 39 27 40 18 0 42 215 89 255 107 59 16 11 99 200 64 185 97 21 23 243 25 101 235 79 57 33 198 211 7 0 1 2 3 4 5 6 7 8 4 5 6 7 0 1 2 3 4 5 9 7 1 2 3 4 5 6 7 0 5 4 5 6 7 0 1 2 3 4 5 4 2 3 4 5 6 7 0 1 2 3 3 7 0 1 2 3 4 5 6 7 0 Pixel b 6 2 5 6 7 0 1 2 3 4 5 6 7 0 1 2 3 0 0 1 2 3 4 5 6 7 0 1 2 3 4 5 6 Pixel a 7 8 9 0 2 2 1 3 6 9 110 000 111 6 2 0 7 28
![Proposed Scheme 88 4 4 3 6 4 5 2 2 6 7 0 Proposed Scheme [8/8] 4 4 3 6 4 5 2 2 6 7 0](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-29.jpg)
Proposed Scheme [8/8] 4 4 3 6 4 5 2 2 6 7 0 1 2 3 4 5 6 7 8 4 5 6 7 0 1 2 3 4 5 9 7 71 80 55 2 12 30 7 1 2 3 4 5 6 7 0 1 2 21 64 73 28 95 91 9 76 6 7 0 1 2 3 4 5 6 7 0 83 23 202 42 19 3 7 55 5 4 5 6 7 0 1 2 3 4 5 57 11 234 39 27 40 18 0 4 2 3 4 5 6 7 0 1 2 3 3 7 0 1 2 3 4 5 6 7 0 42 215 89 255 107 59 16 11 99 200 64 185 97 21 23 243 25 101 235 79 57 33 198 211 Pixel b 9 2 5 6 7 0 1 2 3 4 5 6 7 0 1 2 3 0 0 1 2 3 4 5 6 7 0 1 2 3 4 5 6 Pixel a 7 8 9 110 000 111 6 2 0 7 29
![Experimental Results 13 30 Experimental Results [1/3] 30](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-30.jpg)
Experimental Results [1/3] 30
![Experimental Results 23 Table I Comparisons of PSNRs and ECs of the proposed scheme Experimental Results [2/3] Table I. Comparisons of PSNRs and ECs of the proposed scheme](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-31.jpg)
Experimental Results [2/3] Table I. Comparisons of PSNRs and ECs of the proposed scheme and reference-tablebased schemes Schemes Images Lena Airplane Boat Elaine House Peppers Baboon Man Average EMD [9] PSNR 52. 12 52. 11 52. 11 EC 1 1 1 1 1 EMD-2 [12] PSNR 50. 86 50. 79 50. 64 50. 67 50. 71 50. 78 50. 69 50. 82 50. 75 EC 1. 37 1. 37 Proposed PSNR 49. 42 49. 39 49. 40 49. 41 49. 40 49. 39 49. 42 49. 40 EC 1. 5 1. 5 PIXEL PAIR 3 4 SECRET 110 31
![Experimental Results 33 Table II Comparisons of PSNRs between the proposed scheme and various Experimental Results [3/3] Table II. Comparisons of PSNRs between the proposed scheme and various](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-32.jpg)
Experimental Results [3/3] Table II. Comparisons of PSNRs between the proposed scheme and various reference-tablebased schemes Schemes 1 bpp 1. 5 bpp EMD [9] 52. 11 n/a 52. 39 n/a 48. 99 44. 89 50. 68 48. 67 51. 08 47. 83 52. 39 49. 40 EMD-2 [12] Sudoku-S [10] Sudoku. SR [11] HP-PVD [13] Proposed 32
![Conclusions Future Directions 12 Conclusions 1 Simple embedding extracting 2 Goal Conclusions & Future Directions [1/2] ■ Conclusions 1. Simple embedding & extracting 2. Goal:](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-33.jpg)
Conclusions & Future Directions [1/2] ■ Conclusions 1. Simple embedding & extracting 2. Goal: Design Philosophy: Embedding Capacity Image Quality 33
![Conclusions Future Directions 22 Future directions 1 Reversability 2 ApplicationsAuthentication Watermarking Conclusions & Future Directions [2/2] ■ Future directions 1. Reversability 2. Applications-Authentication & Watermarking](https://slidetodoc.com/presentation_image_h2/ed39de64085eda7a9ae5824fbc4c0b07/image-34.jpg)
Conclusions & Future Directions [2/2] ■ Future directions 1. Reversability 2. Applications-Authentication & Watermarking 3. Optimal Substitution Table Problem (Dynamic Programming, Genetic Algorithm, PSO etc. ) 4. Vector Quantization (VQ) 5. Side Match VQ 6. Generalization: Small Turtle → Big Turtle 7. Formula Derivation f(p 1, p 2)=k 8. Performance Evaluation 9. Steganalysis 34

Questions ? Thank you! 35
 Tsing tsing prison
Tsing tsing prison Anna lowenhaupt tsing
Anna lowenhaupt tsing Promotion from associate professor to professor
Promotion from associate professor to professor Hua
Hua Logo smjk yu hua kajang
Logo smjk yu hua kajang Sophie ming
Sophie ming Mont hua
Mont hua Tom hua
Tom hua Spectral decomposition
Spectral decomposition Tom hua
Tom hua Law of multiplicity of evidence in identification
Law of multiplicity of evidence in identification Chung hua middle school no.4
Chung hua middle school no.4 Hua
Hua Kien a
Kien a It is a large hanging barrel drum. *
It is a large hanging barrel drum. * Chin-chung tsai
Chin-chung tsai Chớ mang ách chung với kẻ chẳng tin
Chớ mang ách chung với kẻ chẳng tin Hee chang trading co ltd
Hee chang trading co ltd Chang wah technology
Chang wah technology Youngho chang
Youngho chang Fay chang
Fay chang Remco chang
Remco chang Post classical vietnam
Post classical vietnam Chẳng nhìn thấy ve đâu
Chẳng nhìn thấy ve đâu Angel xuan chang
Angel xuan chang Chang
Chang Pien fu clothing
Pien fu clothing Wilke chang
Wilke chang Alberto chang
Alberto chang Darrick chang
Darrick chang Jichuan chang
Jichuan chang Chia hui chang
Chia hui chang Chang g lai
Chang g lai Chang pui chung memorial school
Chang pui chung memorial school Mitchell chang ucla
Mitchell chang ucla Khởi nghĩa chàng lía nổ ra ở đâu
Khởi nghĩa chàng lía nổ ra ở đâu

























































