Chair Professor ChinChen Chang National Tsing Hua University













- Slides: 27

視覺密碼與數位簽章 Chair Professor Chin-Chen Chang (張真誠) National Tsing Hua University (清華大學) n National Chung Cheng University (中正大學) n Feng Chia University (逢甲大學) http: //msn. iecs. fcu. edu. tw/~ccc n 1

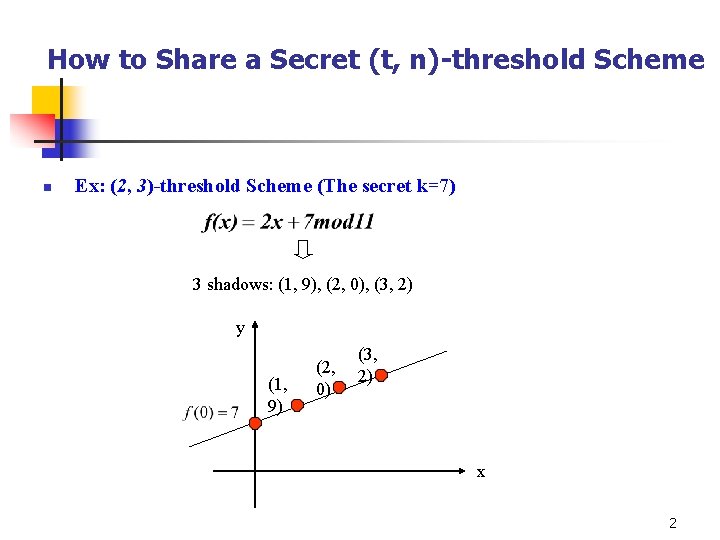
How to Share a Secret (t, n)-threshold Scheme n Ex: (2, 3)-threshold Scheme (The secret k=7) 3 shadows: (1, 9), (2, 0), (3, 2) y (1, 9) (2, 0) (3, 2) x 2

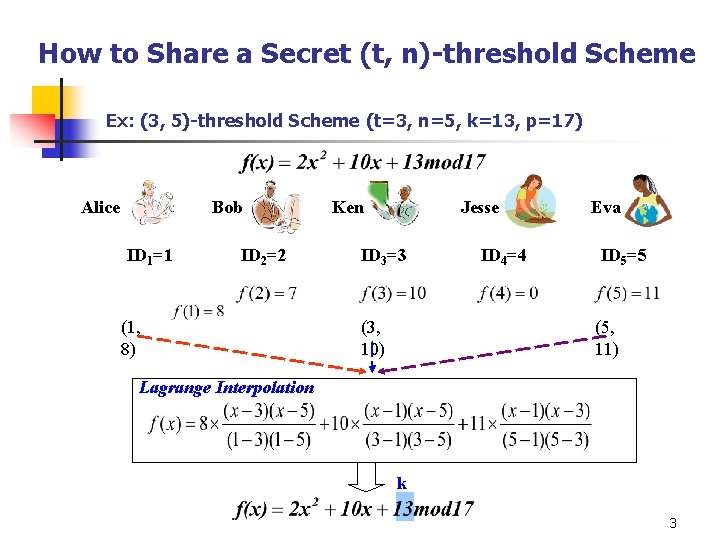
How to Share a Secret (t, n)-threshold Scheme Ex: (3, 5)-threshold Scheme (t=3, n=5, k=13, p=17) Bob Alice ID 1=1 ID 2=2 (1, 8) Ken Jesse ID 3=3 (3, 10) ID 4=4 Eva ID 5=5 (5, 11) Lagrange Interpolation k 3

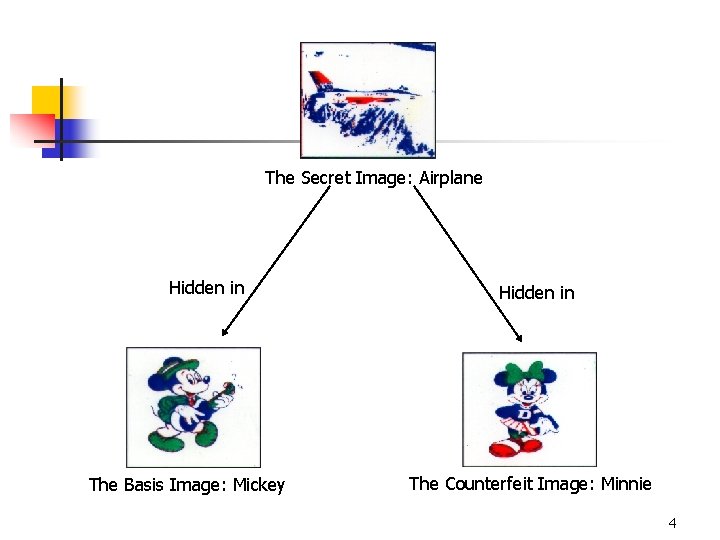
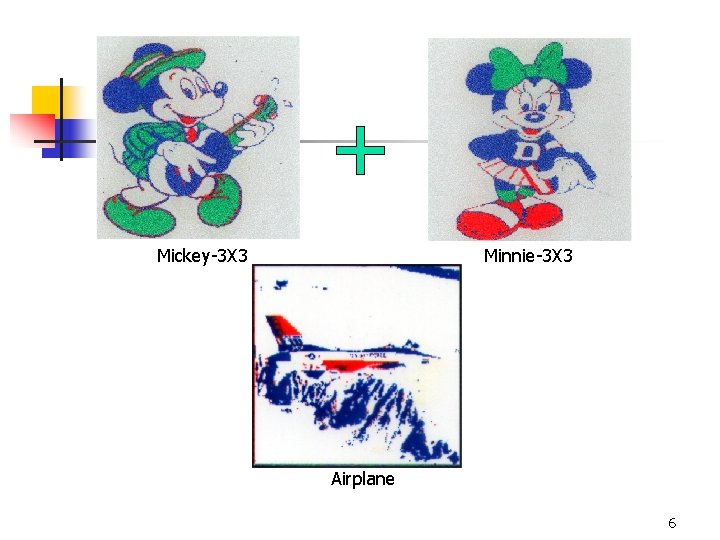
The Secret Image: Airplane Hidden in The Basis Image: Mickey Hidden in The Counterfeit Image: Minnie 4

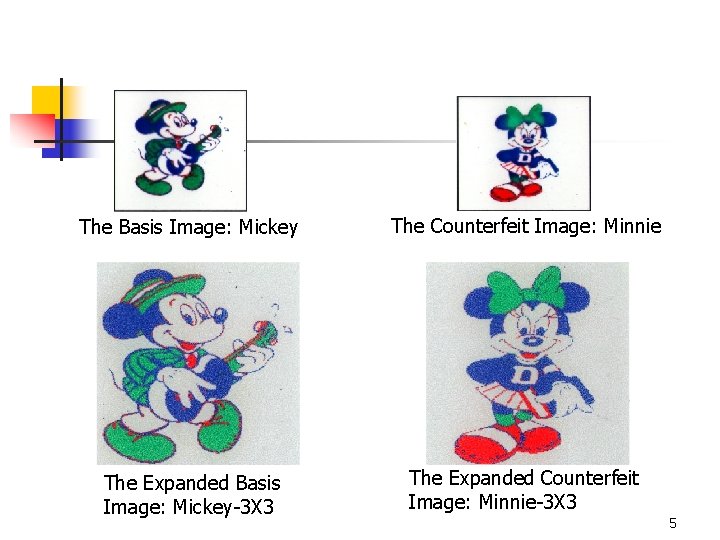
The Basis Image: Mickey The Counterfeit Image: Minnie The Expanded Basis Image: Mickey-3 X 3 The Expanded Counterfeit Image: Minnie-3 X 3 5

Mickey-3 X 3 Minnie-3 X 3 Airplane 6

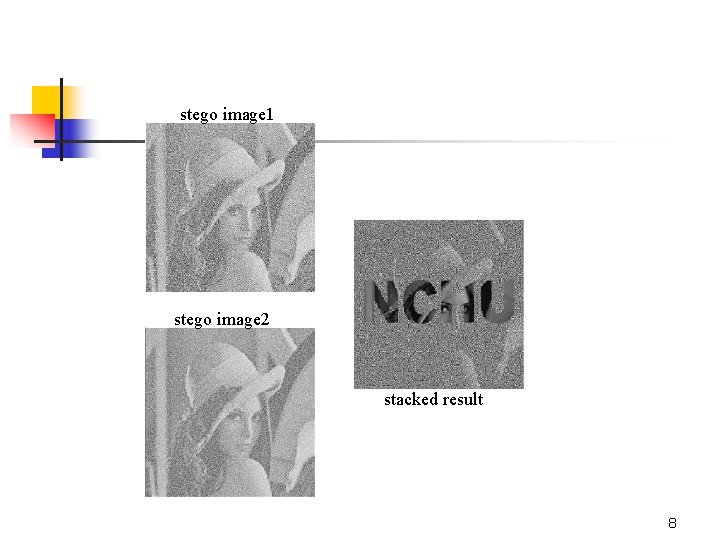
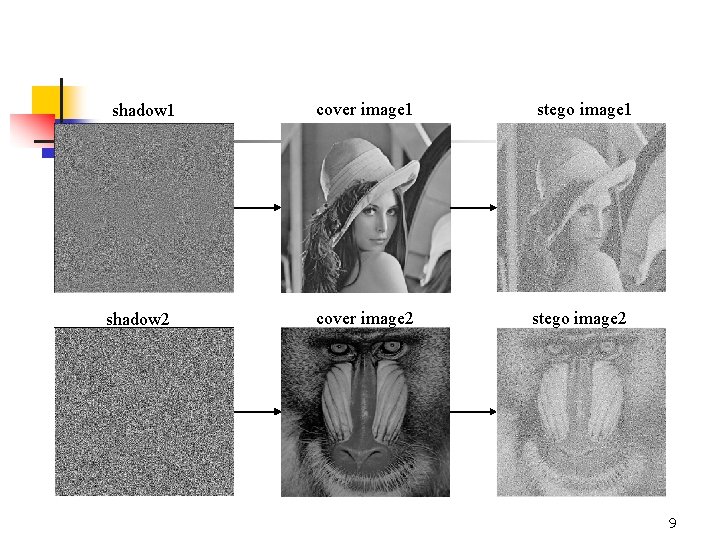
Experimental Results shadow 1 shadow 2 cover image 1 stego image 1 cover image 2 stego image 2 7

stego image 1 stego image 2 stacked result 8

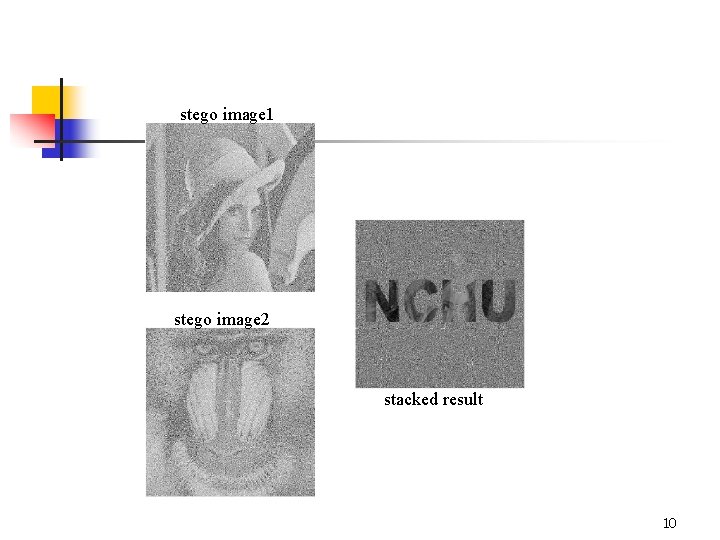
shadow 1 shadow 2 cover image 1 cover image 2 stego image 1 stego image 2 9

stego image 1 stego image 2 stacked result 10

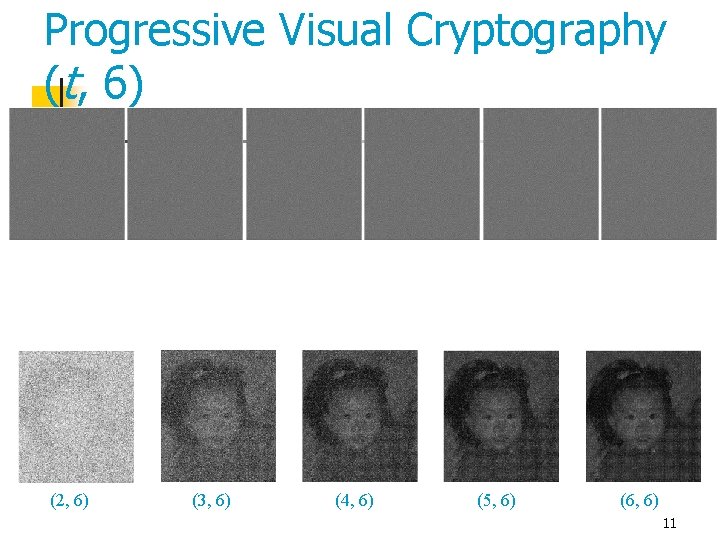
Progressive Visual Cryptography (t, 6) (2, 6) (3, 6) (4, 6) (5, 6) (6, 6) 11

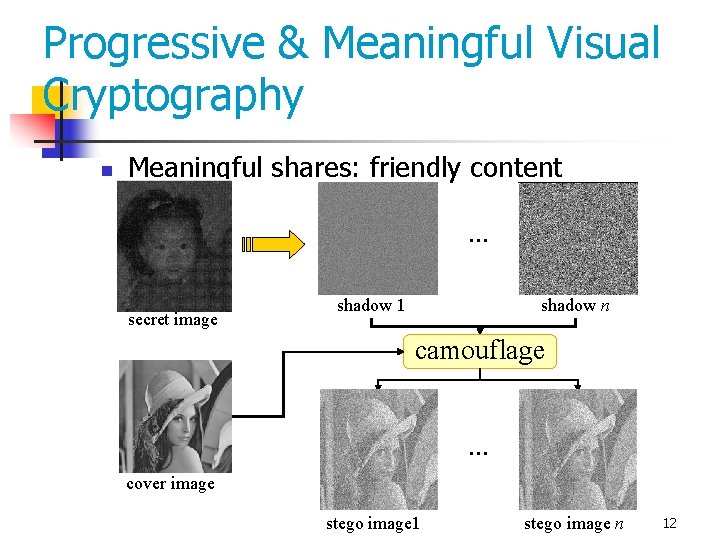
Progressive & Meaningful Visual Cryptography n Meaningful shares: friendly content … secret image shadow 1 shadow n camouflage … cover image stego image 1 stego image n 12

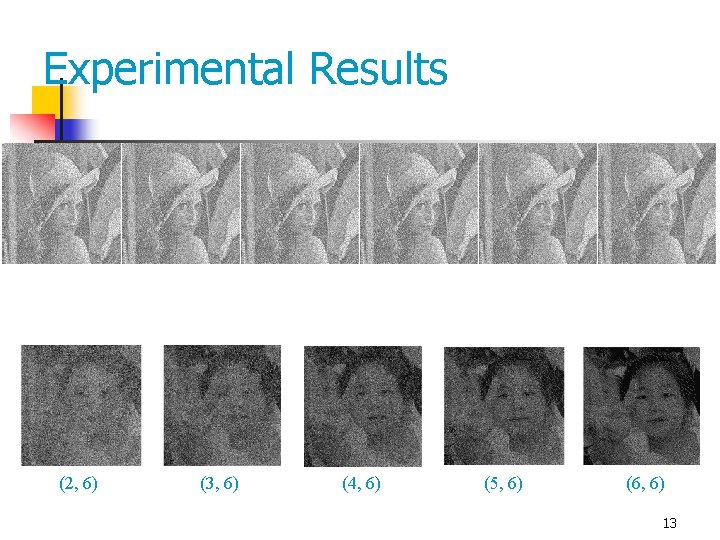
Experimental Results (2, 6) (3, 6) (4, 6) (5, 6) (6, 6) 13

Experimental Results shadow image 1 shadow image 2 stacked image 2 14

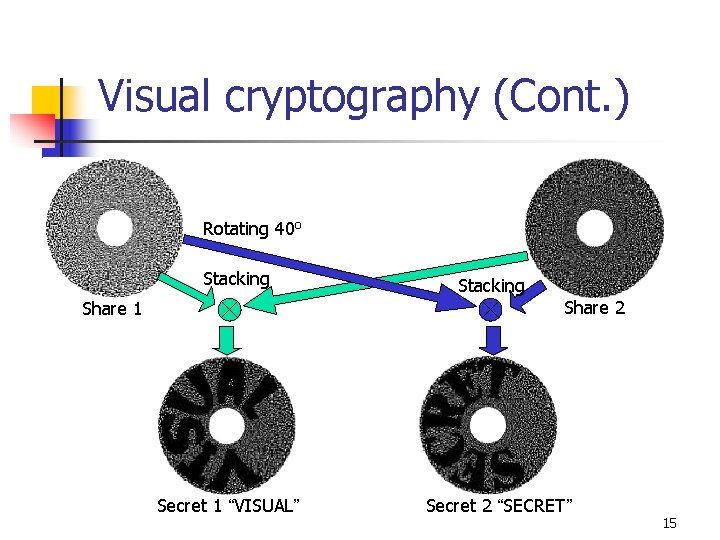
Visual cryptography (Cont. ) Rotating 40 o Stacking Share 2 Share 1 Secret 1 “VISUAL” Secret 2 “SECRET” 15









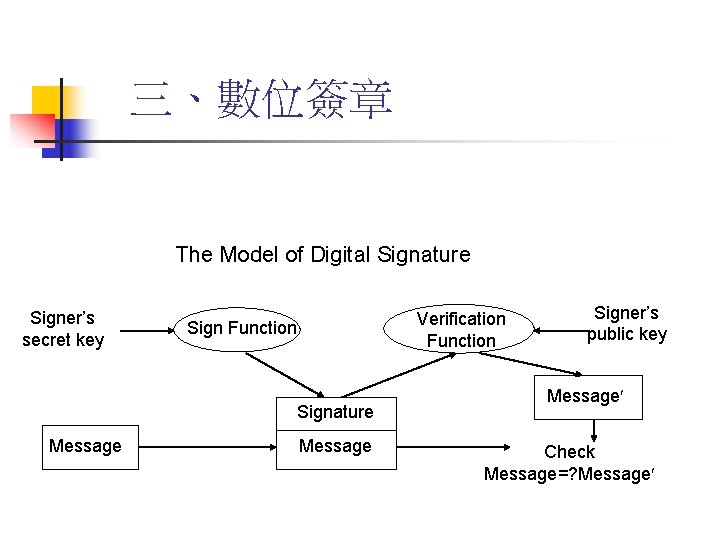
三、數位簽章 The Model of Digital Signature Signer’s secret key Verification Function Signature Message Signer’s public key Message Check Message=? Message

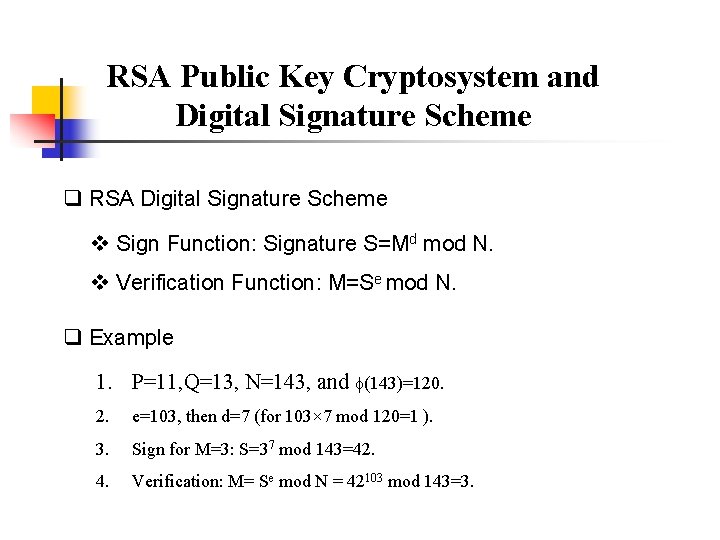
RSA Public Key Cryptosystem and Digital Signature Scheme q RSA Digital Signature Scheme v Sign Function: Signature S=Md mod N. v Verification Function: M=Se mod N. q Example 1. P=11, Q=13, N=143, and (143)=120. 2. e=103, then d=7 (for 103× 7 mod 120=1 ). 3. Sign for M=3: S=37 mod 143=42. 4. Verification: M= Se mod N = 42103 mod 143=3.


27
 Tsing tsing prison
Tsing tsing prison Anna lowenhaupt tsing
Anna lowenhaupt tsing Promotion from associate professor to professor
Promotion from associate professor to professor Logo smjk yu hua kajang
Logo smjk yu hua kajang Spectral decomposition
Spectral decomposition Chung hua middle school no.4
Chung hua middle school no.4 Tsuridaiko instrument
Tsuridaiko instrument Mont hua
Mont hua Tom hua
Tom hua Hua
Hua Hua
Hua Tom hua
Tom hua Portrait parle means
Portrait parle means Kien a
Kien a The w's in statistics
The w's in statistics National professor
National professor Joe chang
Joe chang Dr tc chang
Dr tc chang Jichuan chang
Jichuan chang Darrick chang icfo
Darrick chang icfo Mark liberman
Mark liberman Brief chang brendan playerunknownjaewon
Brief chang brendan playerunknownjaewon Sanjay ghemawat
Sanjay ghemawat Khởi nghĩa chàng lía nổ ra ở đâu
Khởi nghĩa chàng lía nổ ra ở đâu Xavier rival
Xavier rival Ching chang walla walla bing bang meaning
Ching chang walla walla bing bang meaning Chang pao chinese clothing
Chang pao chinese clothing Yuyen chang
Yuyen chang

















































