Chair Professor ChinChen Chang Feng Chia University National













- Slides: 30

利用網路聊天室傳送機密訊息 Chair Professor Chin-Chen Chang Feng Chia University National Chung Cheng University National Tsing Hua University http: //msn. iecs. fcu. edu. tw/~ccc http: //msn. iecs. fcu. edu. tw/

Information hiding in general text u Synonym substitution u Syntactic transformation u Semantic transformation u Translation u Inter-word spacing schemes Information hiding in binary text Information hiding in hypertext Information hiding in chat text u Text steganography in chat u Emoticon-based steganography in chat 2

Synonym substitution 0 Taichung is a 1 2 3 4 wonderful decent fine great nice little 0 city 1 town Secret message: (3)5(1)2 Taichung is a great little town 3

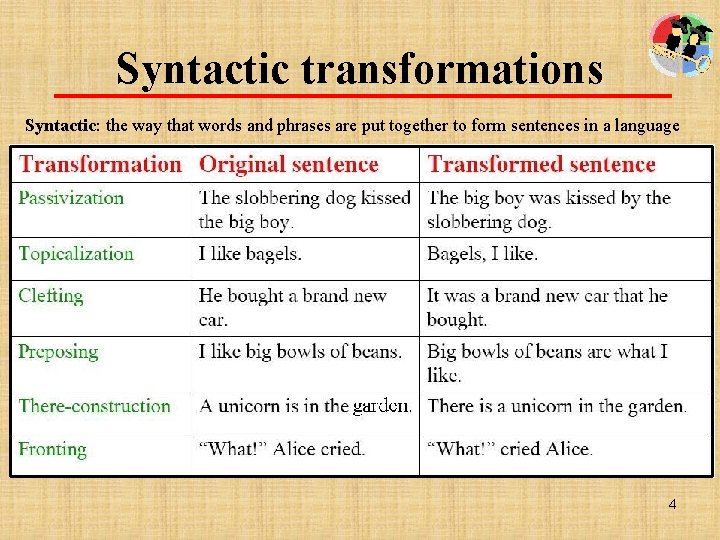
Syntactic transformations Syntactic: the way that words and phrases are put together to form sentences in a language 4

Semantic transformation Semantic : Describe things that deal with the meanings of words and sentences • Grafting: adding or repeating information • Pruning: removing repeated information • Substitution: replacing information 5

Grafting He is detained in Japan. He, an American citizen, is detained in Japan. 6

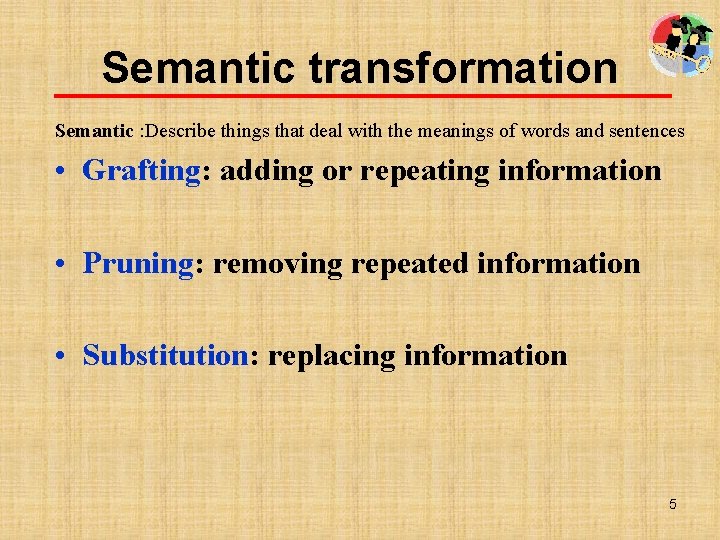
Pruning The Pentagon ordered two new spy planes to the region to start flying over Afghanistan has been under attack since October, and the Pentagon ordered two new spy planes to the region to start flying over there. 7

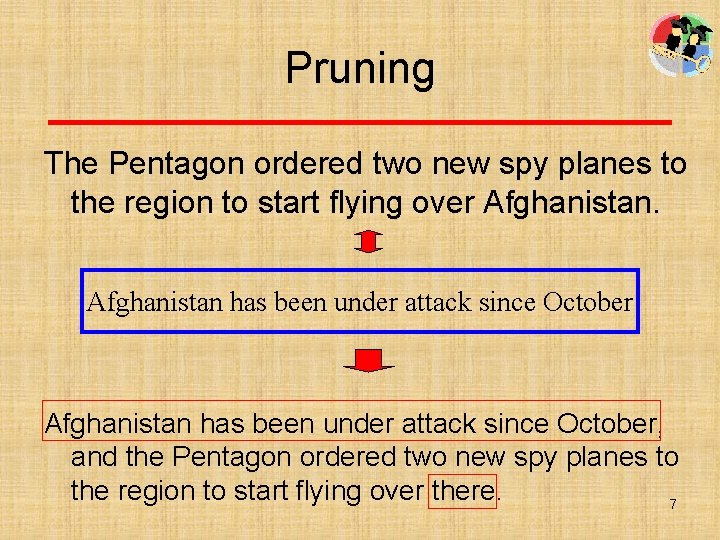
Substitution The Pentagon ordered two new spy planes to the region to start flying over Afghanistan Taliban ruled country The Pentagon ordered two new spy planes to the region to start flying over the Taliban ruled country. 8

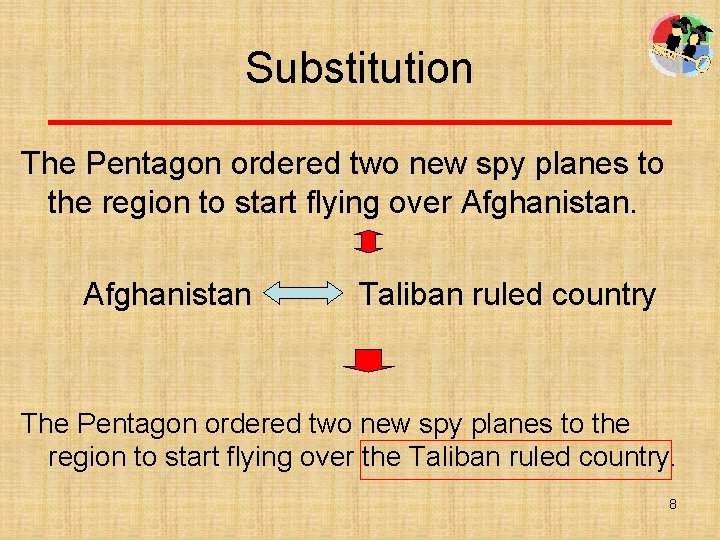
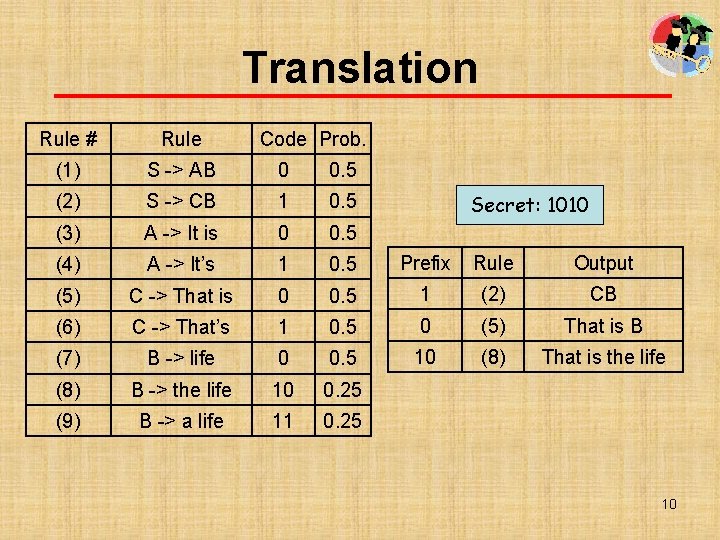
Translation 法文: C’est la vie Message 英文: That’s life. That is the life. It’s life. Stego object Alice Bob Cover object 9

Translation Rule # Rule Code Prob. (1) S -> AB 0 0. 5 (2) S -> CB 1 0. 5 (3) A -> It is 0 0. 5 (4) A -> It’s 1 0. 5 Prefix Rule Output (5) C -> That is 0 0. 5 1 (2) CB (6) C -> That’s 1 0. 5 0 (5) That is B (7) B -> life 0 0. 5 10 (8) That is the life (8) B -> the life 10 0. 25 (9) B -> a life 11 0. 25 Secret: 1010 10

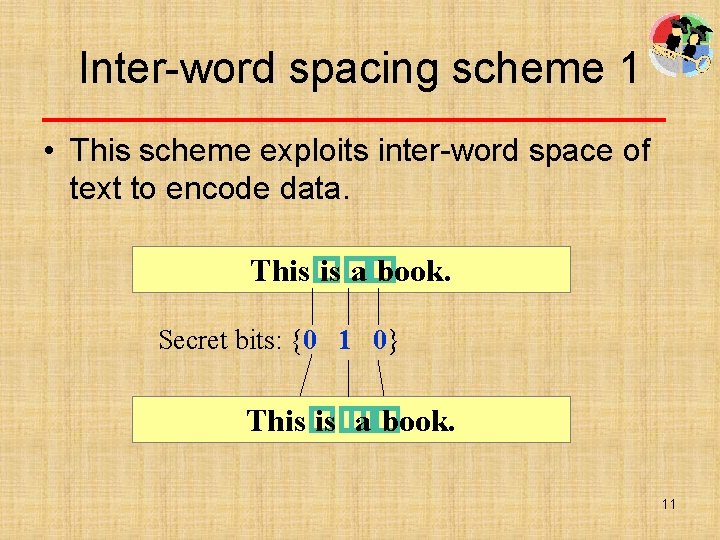
Inter-word spacing scheme 1 • This scheme exploits inter-word space of text to encode data. This� a� book. Secret bits: {0 1 0} This� � a� book. 11

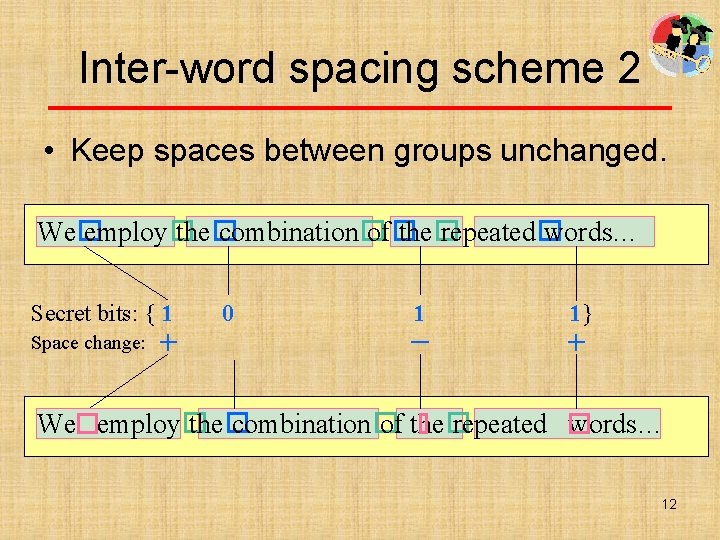
Inter-word spacing scheme 2 • Keep spaces between groups unchanged. We� employ� the� combination� of� the� repeated� words… Secret bits: { 1 Space change: + 0 1 1} - + We employ� the� combination� of the� repeated words… 12

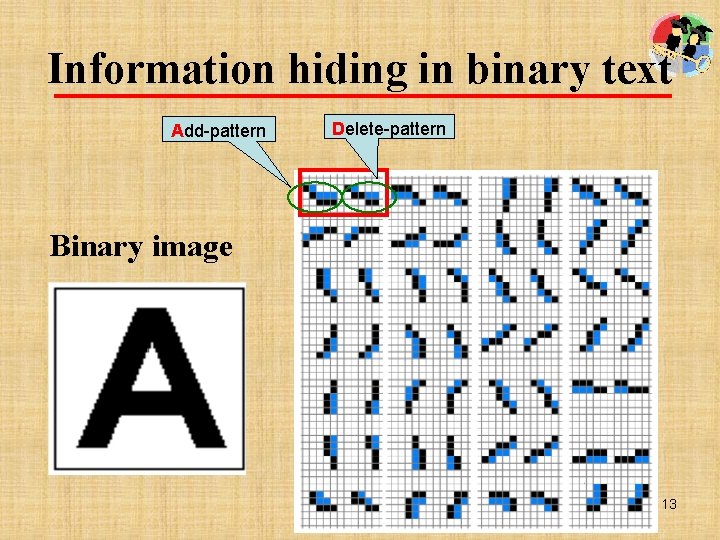
Information hiding in binary text Add-pattern Delete-pattern Binary image 13

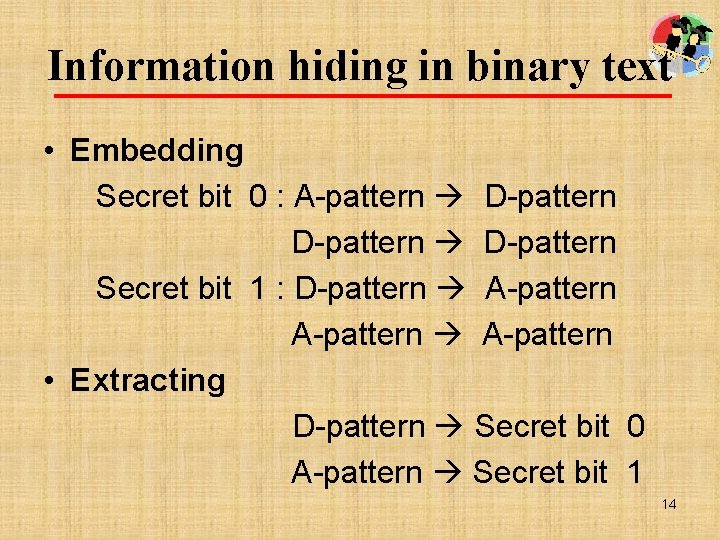
Information hiding in binary text • Embedding Secret bit 0 : A-pattern D-pattern Secret bit 1 : D-pattern A-pattern • Extracting D-pattern Secret bit 0 A-pattern Secret bit 1 14

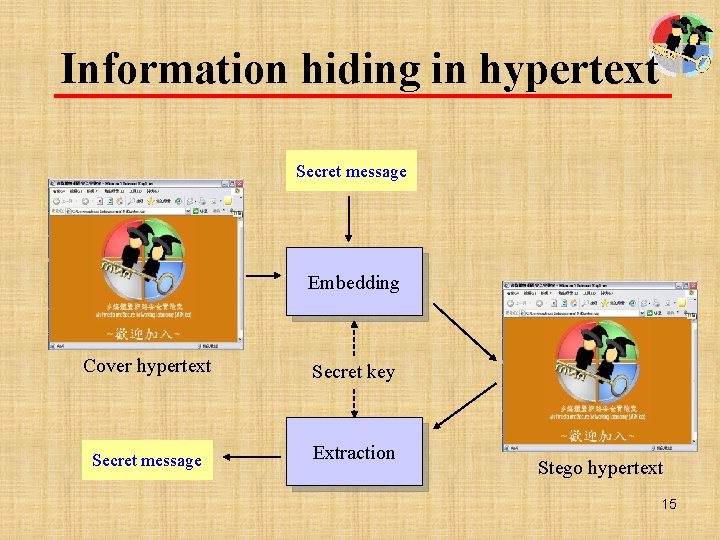
Information hiding in hypertext Secret message Embedding Cover hypertext Secret key Secret message Extraction Stego hypertext 15

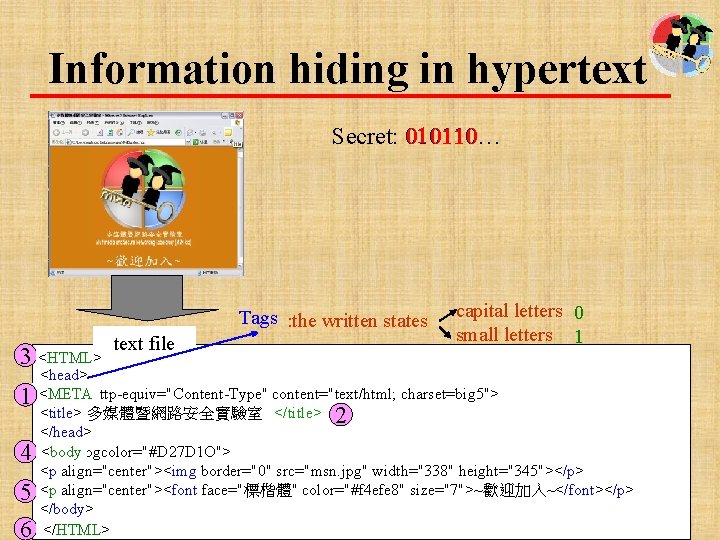
Information hiding in hypertext 010110 Secret: 010110… Tags : the written states <html> 3 <HTML> 1 4 5 6 text file capital letters 0 small letters 1 <head> <META <meta http-equiv="Content-Type" content="text/html; charset=big 5"> </title> 2 <title> 多媒體暨網路安全實驗室 </title> </head> <body bgcolor="#D 27 D 1 O"> <p align="center"><img border="0" src="msn. jpg" width="338" height="345"></p> <p align="center"><font face="標楷體" color="#f 4 efe 8" size="7">~歡迎加入~</font></p> </body> </html> </HTML> 16

Information hiding in hypertext : the written states <html> 3 <HTML> 1 4 5 6 text file capital letters 0 small letters 1 <head> <META <meta http-equiv="Content-Type" content="text/html; charset=big 5"> <title> 多媒體暨網路安全實驗室 </title> 2 </head> <body bgcolor="#D 27 D 1 O"> <p align="center"><img border="0" src="msn. jpg" width="338" height="345"></p> <p align="center"><font face="標楷體" color="#f 4 efe 8" size="7">~歡迎加入~</font></p> </body> </html> </HTML> Secret: 010110… 17

Text steganography in chat Shirali-Shahreza, M. H. , Shirali-Shahreza, M. , “Text Steganography in Chat, ” Proceedings of the Third IEEE/IFIP International Conference in Central Asia on Internet the Next Generation of Mobile, Wireless and Optical Communications Networks, Tashkent, Uzbekistan, Sep. 2007, pp. 1 -5. 18

Text steganography in chat SMS-Texting 19

Text steganography in chat Usual abbreviated words • university • PC Personal Computer • M. S. master of science • UN United Nations • Dr doctor 20

Text steganography in chat • SMS list + abbreviated words list Check list • 0 full form, form 1 abbreviated form 21

Text steganography in chat Embedding : “Please call me when you feel upset. ” secret “ 10” “Please CM when you feel upset. ” Extracting : “Please CM when you feel upset. ” Check list secret bits “ 10” 22

Emoticon-based steganography in chat Emoticon-based Text Steganography in Chat 23

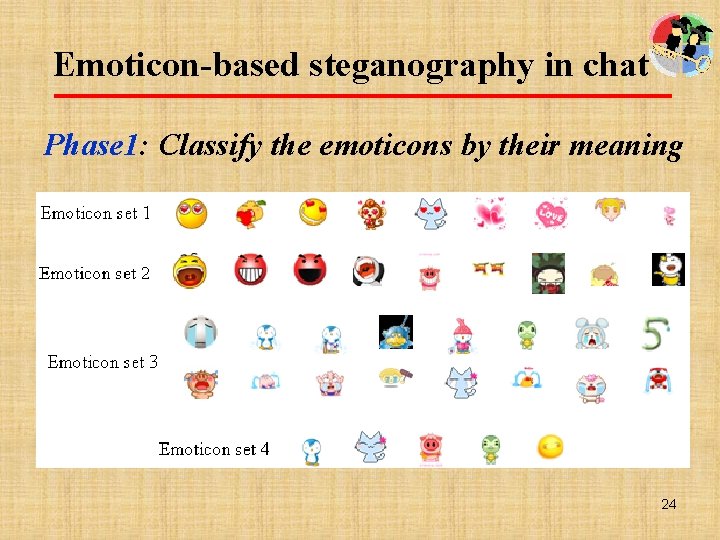
Emoticon-based steganography in chat Phase 1: Classify the emoticons by their meaning 24

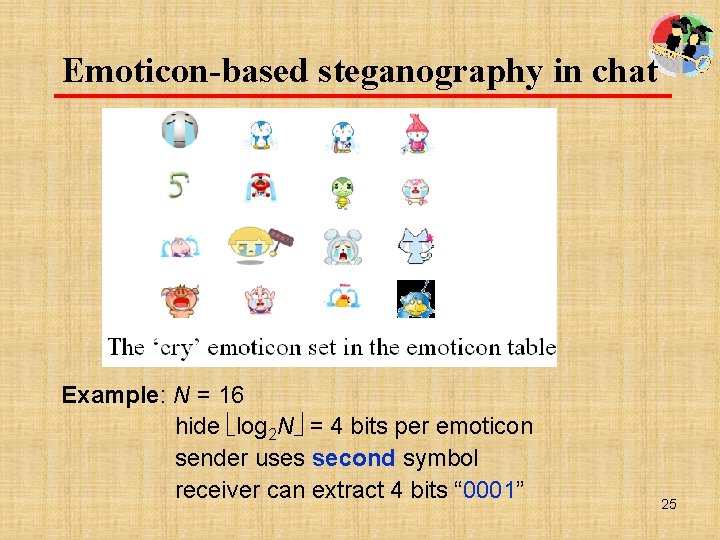
Emoticon-based steganography in chat Example: N = 16 hide log 2 N = 4 bits per emoticon sender uses second symbol receiver can extract 4 bits “ 0001” 25

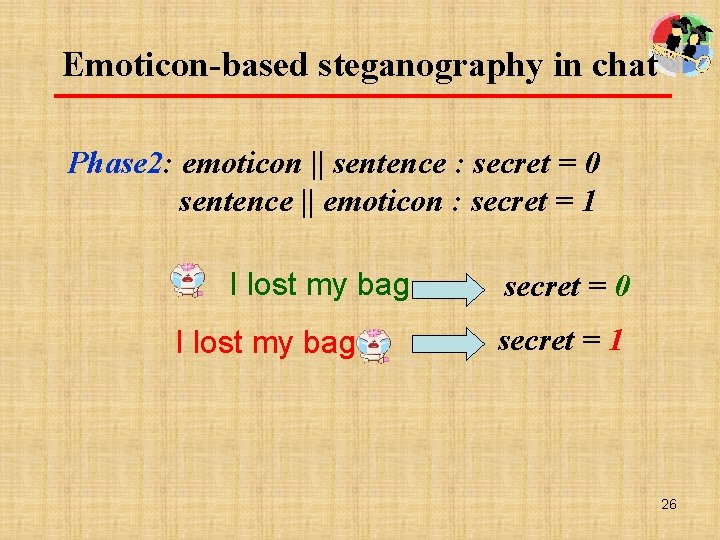
Emoticon-based steganography in chat Phase 2: emoticon || sentence : secret = 0 sentence || emoticon : secret = 1 I lost my bag secret = 0 secret = 1 26

Emoticon-based steganography in chat Phase 3: emoticon , sentence : secret = 0 emoticon , sentence : secret = 1 , I lost my bag secret = 0 I lost my bag secret = 1 27

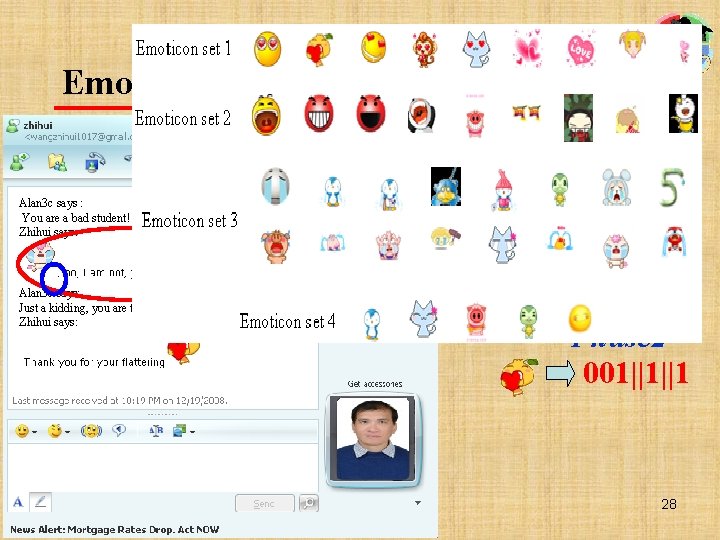
Emoticon-based steganography in chat Alan 3 c says : You are a bad student! Zhihui says: Alan 3 c says: Just a kidding, you are the nicest guy I know in the world. Zhihui says: Zhihui wants to send secret bits “ 11100000111” to Alan 3 c. 1110 0 0 Phase 1 Phase 3 Phase 2 001||1||1 28


30
 Chia hui chang
Chia hui chang Chia hui chang
Chia hui chang Promotion from assistant to associate professor
Promotion from assistant to associate professor National professor
National professor Muôốn tìm số chia
Muôốn tìm số chia 28,5:2,5
28,5:2,5 Bảng chia 7
Bảng chia 7 Workforce cerner
Workforce cerner Social media trend analysis
Social media trend analysis 37648 chia 4
37648 chia 4 26345 chia 752
26345 chia 752 Corrycom chia
Corrycom chia Thử lại phép chia
Thử lại phép chia 42546:37
42546:37 Bảng nhân chia
Bảng nhân chia Chia liang cheng
Chia liang cheng Chia seedw
Chia seedw Chia seeds
Chia seeds Exodus chia
Exodus chia Tcp timers
Tcp timers Osdi charts
Osdi charts Chia 3 threads
Chia 3 threads Fractal dimension definition
Fractal dimension definition Factorake
Factorake Interpolated
Interpolated Feng doolittle algorithm
Feng doolittle algorithm Feng doolittle algorithm
Feng doolittle algorithm Feng guo symmetry
Feng guo symmetry Victor van der veen
Victor van der veen Joseph yu
Joseph yu Shun-feng su
Shun-feng su