C S Ch 3 Underlying Technologies remainder 6





















- Slides: 65

C S Ch 3: Underlying Technologies (remainder) 6 0 2 7 Lecture #5 Project 1 rollout today – posted after lecture Course Dissemination Approach Vote Dr. Clincy Lecture 1

C Internet – Underlying Technologies S • Recall the various types of interconnected networks comprising the Internet: • • LANs, Point-to-Point WANs and Switched WANs We have covered LANS: Ethernet, Token Ring, Wireless and FDDI Ring Let’s cover the Point-to-Point WANs Point-to-Point WANS 6 0 2 7 • Connect devices via a public network line (ie. telephone company) • Telephone company – physical layer • Point-to-Point WAN – data link layer and up • Company services provided to make the connection: • Modem (modem to switching station to ISP) • DSL • Cable Modem Dr. Clincy Lecture • T Lines (ie. T 1, T 3) • SONET (optical carriers) 2

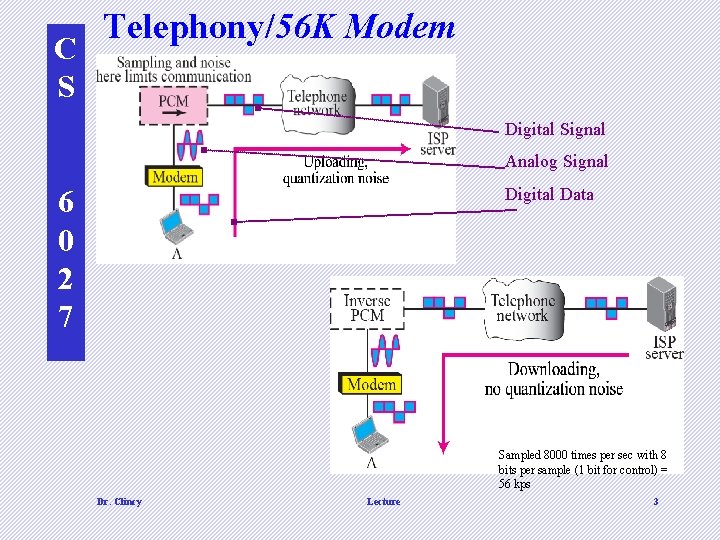
C S Telephony/56 K Modem Digital Signal Analog Signal 6 0 2 7 Digital Data Sampled 8000 times per sec with 8 bits per sample (1 bit for control) = 56 kps Dr. Clincy Lecture 3

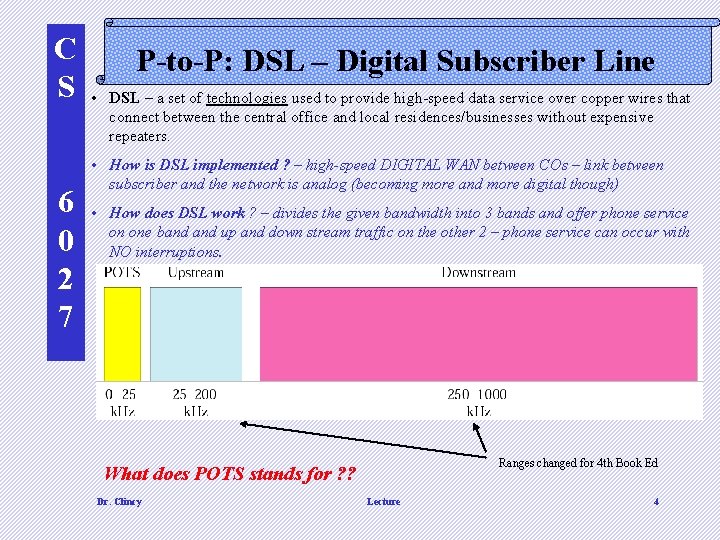
C S 6 0 2 7 P-to-P: DSL – Digital Subscriber Line • DSL – a set of technologies used to provide high-speed data service over copper wires that connect between the central office and local residences/businesses without expensive repeaters. • How is DSL implemented ? – high-speed DIGITAL WAN between COs – link between subscriber and the network is analog (becoming more and more digital though) • How does DSL work ? – divides the given bandwidth into 3 bands and offer phone service on one band up and down stream traffic on the other 2 – phone service can occur with NO interruptions. Ranges changed for 4 th Book Ed What does POTS stands for ? ? Dr. Clincy Lecture 4

C S 6 0 2 7 P-to-P: Other DSL Services • RADSL – rate adaptive asymmetric DSL – scales back the speed of ADSL based on the quality of the wire and distance between the CO and user. • Side Note: A newer version of ADSL called Universal ADSL (or UADSL) is being deployed in an attempt to standardize ADSL to a set of standard speeds – speeds vary across the Country • HDSL – high bit rate DSL – an digital alternative to T-1 analog service (T-1 contains multiple high-speed analog lines) • SDSL – symmetric DSL – same as HDSL however only 1 line is provided (is full-duplex) • VDSL – very high bit rate DSL – similar to ADSL however, in addition to using twisted-pair, coaxial and fiber -optic can be used in getting a much higher bit rate Dr. Clincy Lecture 5

C S P-to-P: Cable Modem • • 6 0 2 7 • • • Still talking about point-to-point WANS Uses the cable TV network How does it work ? . some of the bandwidth dedicated to television signals is used for data traffic. How does it work ? . The data signals are modulated into sine waves and placed on analog channels How does it work ? . Typically, the BW in a neighborhood (or certain proximity) is shared (like a LAN in an office). Therefore, you never know if you have access to all of the BW. The more people using cable modems the worst the performance. Some cable companies can dedicate some BW for phone service therefore offering voice, video/TV and data services on one cable Cable modems are faster than computer modems because they are not limited by the 3000 Hz BW of the telephone line The newer cable systems uses digital cable boxes and digital networks can send/receive data on separate digital channels (draw picture of typical cable/video network – briefly explain history) Dr. Clincy Lecture 6

C S 6 0 2 7 P-to-P: T 1/T 3 Service • Transport carriers originally designed for voice (672 circuits ? ? ? ). • Typical “long haul” or “back bone” network – also used to interconnect WANs we mentioned • T 1 line can send 8000 193 -bit frames in one second • T 3 line can send 224, 000 193 -bit frames in one second or be treated as 28 T 1 lines (we called this a channel T 1) • Fractional T lines – several customers sharing a T 1 line – their data is multiplexed onto a single T 1. Dr. Clincy Lecture 7

C S 6 0 2 7 P-to-P: SONET • SONET means Synchronous Optical Networks – it’s a standard that defines a high-speed fiber-optic data carrier. • Electrical signals (called STSs – synchronous transport signals) are converted to light or optical signals (called optical carriers) • Comes in different rates, OC-1, OC-3, OC-9 …. . OC 48 …. OC-192 • The lowest data rate for SONET (OC-1) is greater than a T 3’s data rate – Wow ! Dr. Clincy Lecture 8

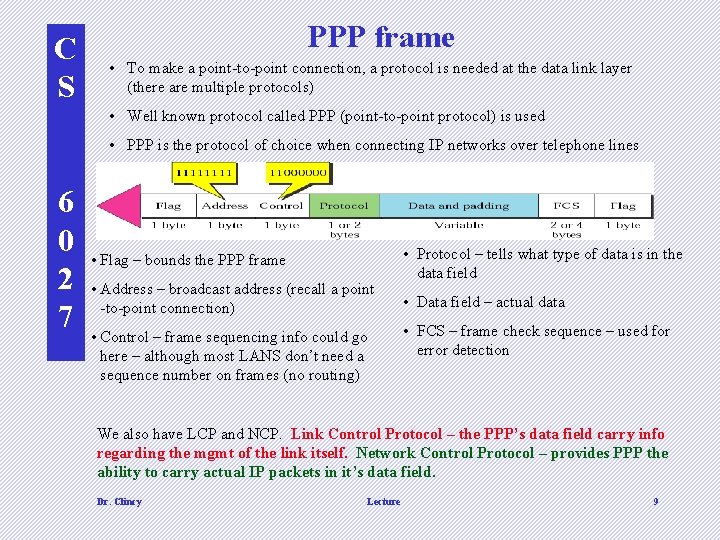
C S PPP frame • To make a point-to-point connection, a protocol is needed at the data link layer (there are multiple protocols) • Well known protocol called PPP (point-to-point protocol) is used • PPP is the protocol of choice when connecting IP networks over telephone lines 6 0 2 7 • Flag – bounds the PPP frame • Address – broadcast address (recall a point -to-point connection) • Control – frame sequencing info could go here – although most LANS don’t need a sequence number on frames (no routing) • Protocol – tells what type of data is in the data field • Data field – actual data • FCS – frame check sequence – used for error detection We also have LCP and NCP. Link Control Protocol – the PPP’s data field carry info regarding the mgmt of the link itself. Network Control Protocol – provides PPP the ability to carry actual IP packets in it’s data field. Dr. Clincy Lecture 9

C Internet – Underlying Technologies • Internet is comprised of LANs, Point-to-Point WANs and Switched S WANs 6 0 2 7 • We have covered LANS: Ethernet, Token Ring (not in book), Wireless and FDDI Ring (not in book) • We have covered Pt-to-Pt WANs: Telephony Modem, DSL, Cable/Modem, T-Lines and SONET • We will cover Switched WANs: X. 25, Frame Relay and ATM Dr. Clincy Lecture 10

C S Reminder • Quickly illustrate going from LAN-to-LAN via WAN 6 0 2 7 Dr. Clincy Lecture 11

C S SWITCHED WANS • Switched WAN - a mesh of point-to-point networks connected via switches 6 0 2 7 • Unlike LANS – multiple paths are needed between locations • Unlike LANS – no direct relationship between Tx and Rx • Paths are determined upfront and theses paths are used to send and receive (multiple paths for reliability and restoration) – recall that LANS uses Tx/Rx addresses to make the connection • Uses Virtual Circuit concept • 3 well known Switch WANs: X. 25, Frame Relay and ATM Dr. Clincy Lecture 12

C S 6 0 2 7 X. 25 • Developed in 1970 – the first switch WAN – becoming more and more obsolete • X. 25 standard describes all of the functions necessary for communicating with a packet switching network • Divided into 3 levels: • (1) physical level – describes the actual interfaces • (2) frame level – describes the error detection and correction • (3) Packet level – provides network-level addressing (constant BW efficiency problem – but it worked) Because X. 25 was developed before the Internet, the IP packets are encapsulated in the X. 25 packet when you have an IP network on each side of a X. 25 backbone Dr. Clincy Lecture 13

C S Frame Relay Network • Designed to replace X. 25 • Have higher data rates than X. 25 • Can handle “bursty data” by allocating BW as needed versus dedicating constant chucks of BW • Less error checking and overhead needed – more reliable and efficient 6 0 2 7 • DTE – data terminating equipment – devices connecting users to the network (ie routers) • DCE – data circuit-terminating equipment – switches routing the frames through the network Frame Relay Switches in the yellow cloud Dr. Clincy Lecture 14

C S 6 0 2 7 Switched WANs - ATM • • 1. 2. 3. 4. 5. 6. • • ATM – Asynchronous Transfer Mode – is a cell relay protocol Objectives of ATM (upfront initiative): Make better use of high data rate transmission (ie. fiber optics) WAN between various types of packet-switch networks that will not drive a change in the packet-switch networks Must be inexpensive (no barrier to use) – want it to be the international backbone Must be able to support the existing network hierarchies – local loops, long-distance carriers, etc. . ) Must be connection-oriented (high reliability) Make more hardware oriented versus software oriented in speeding up rates (explain this – circuit vs software) Cell – small unit of data of fixed size – basic unit of data exchange Different types of data is loaded into identical cells Cells are multiplexed with other cells and routed By having a static size, the delivery is more predictable and uniform Dr. Clincy Lecture 15

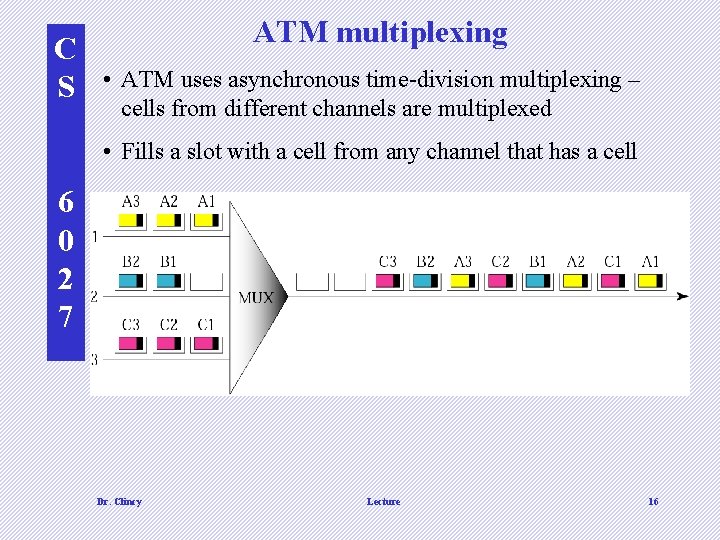
C S ATM multiplexing • ATM uses asynchronous time-division multiplexing – cells from different channels are multiplexed • Fills a slot with a cell from any channel that has a cell 6 0 2 7 Dr. Clincy Lecture 16

C S 6 0 2 7 Architecture of an ATM network • User access devices (called end points) are through a userto-network interface (UNI) to switches in the network • The switches are connected through network-to-network interfaces (NNI) Dr. Clincy Lecture 17

C S Virtual circuits • Connections between points are accomplished using transmission paths (TP), virtual paths (VP) and virtual circuits (VC). • TP – all physical connections between two points • VP – set of connections (a subset of TP) (ie. Highway) 6 0 2 7 • VC – all cells belonging to a single message follow the same VC and remain in original order until reaching Rx (ie. Lane) • The virtual connection is defined by the VP and VC identifiers Dr. Clincy Lecture 18

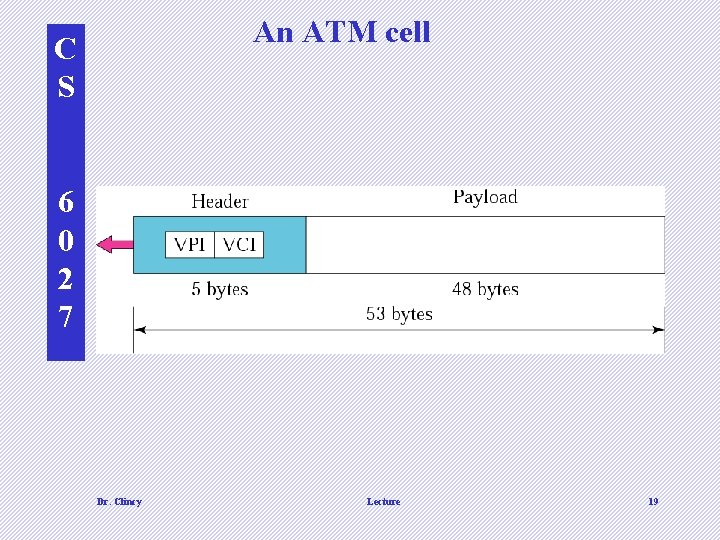
An ATM cell C S 6 0 2 7 Dr. Clincy Lecture 19

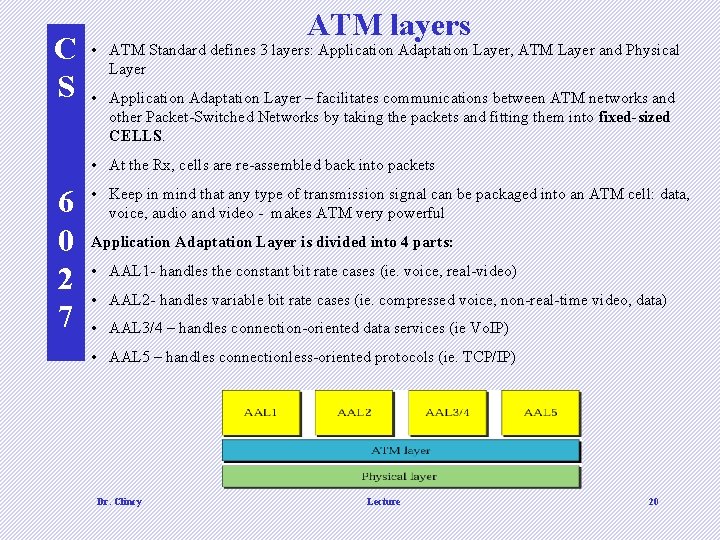
C S ATM layers • ATM Standard defines 3 layers: Application Adaptation Layer, ATM Layer and Physical Layer • Application Adaptation Layer – facilitates communications between ATM networks and other Packet-Switched Networks by taking the packets and fitting them into fixed-sized CELLS. • At the Rx, cells are re-assembled back into packets 6 0 2 7 • Keep in mind that any type of transmission signal can be packaged into an ATM cell: data, voice, audio and video - makes ATM very powerful Application Adaptation Layer is divided into 4 parts: • AAL 1 - handles the constant bit rate cases (ie. voice, real-video) • AAL 2 - handles variable bit rate cases (ie. compressed voice, non-real-time video, data) • AAL 3/4 – handles connection-oriented data services (ie Vo. IP) • AAL 5 – handles connectionless-oriented protocols (ie. TCP/IP) Dr. Clincy Lecture 20

C S 6 0 2 7 ATM layers • ATM Layer in general – routing, flow control switching & multiplexing • ATM Layer – going down – accepts bytes segments and translate to cells • ATM Layer – going up – translate cells back into byte segments – keep in mind that a node can be acting as both an intermediate and Rx node (and Tx) • ATM Physical Layer – translate cells into a flow of bits (or signals) and vice versa Dr. Clincy Lecture 21

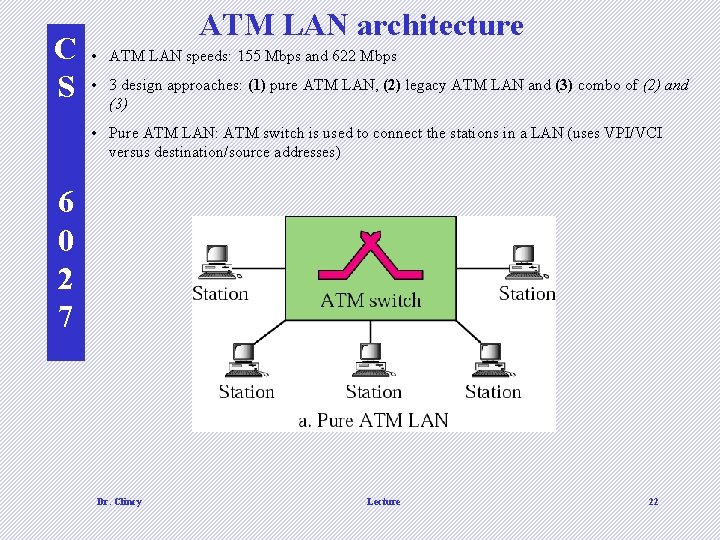
C S ATM LAN architecture • ATM LAN speeds: 155 Mbps and 622 Mbps • 3 design approaches: (1) pure ATM LAN, (2) legacy ATM LAN and (3) combo of (2) and (3) • Pure ATM LAN: ATM switch is used to connect the stations in a LAN (uses VPI/VCI versus destination/source addresses) 6 0 2 7 Dr. Clincy Lecture 22

C S Legacy ATM LAN architecture • Use an ATM LAN as a backbone – frames staying with in a certain network need not be converted • Frames needing to cross to another LAN must be converted and ride the ATM LAN 6 0 2 7 Dr. Clincy Lecture 23

Mixed ATM LAN Architecture C S 6 0 2 7 Dr. Clincy Lecture 24

– Underlying Technologies C • Internet Recall that the Internet is comprised of LANs, Point-to-Point WANs and S Switched WANs • • • 6 0 2 7 We covered LANS: Ethernet, Token Ring, Wireless and FDDI Ring We covered Switched WANs: X. 25, Frame Relay and ATM We covered Pt-to-Pt WANs: Telephony Modem, DSL, Cable/Modem, TLines and SONET How are these networks connected ? Dr. Clincy Lecture 25

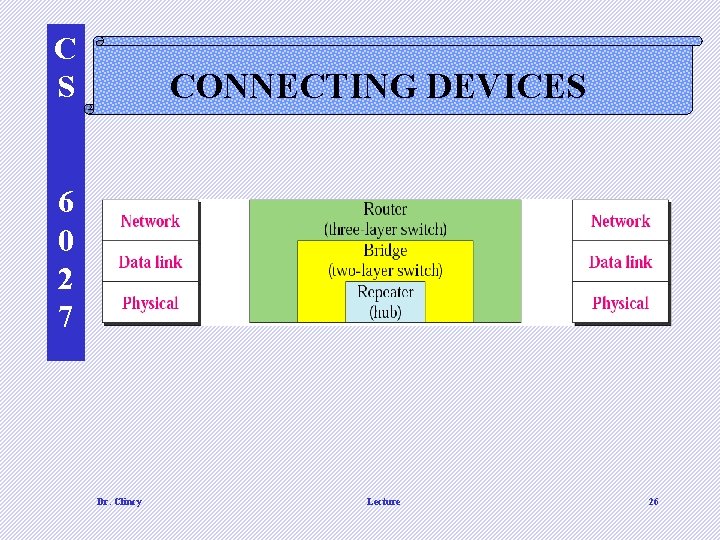
C S CONNECTING DEVICES 6 0 2 7 Dr. Clincy Lecture 26

C S Repeater Operates at the physical layer – layer 1 Receives the signal and regenerates the signal in it’s original pattern 6 0 2 7 A repeater forwards every bit; it has no filtering capability Is there a difference between a regen or repeater and an amp ? ? Dr. Clincy Lecture 27

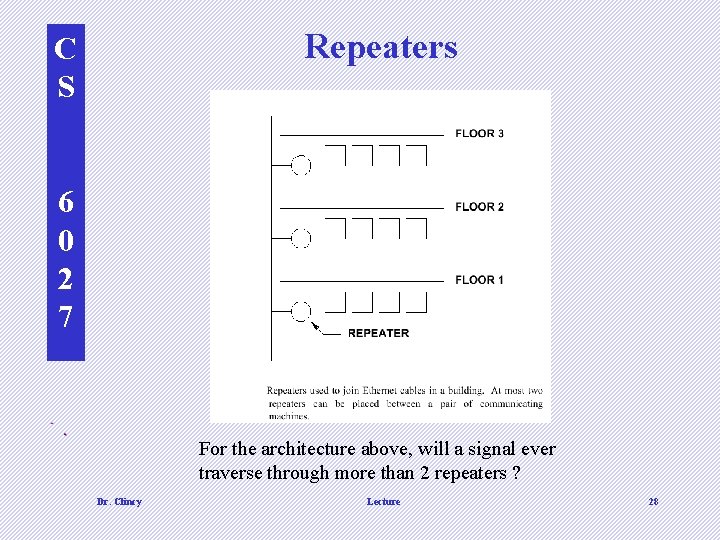
Repeaters C S 6 0 2 7 d For the architecture above, will a signal ever traverse through more than 2 repeaters ? Dr. Clincy Lecture 28

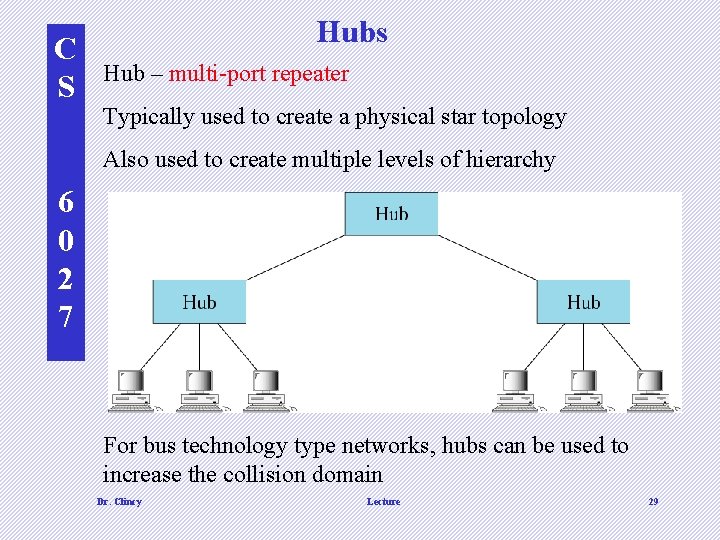
C S Hubs Hub – multi-port repeater Typically used to create a physical star topology Also used to create multiple levels of hierarchy 6 0 2 7 For bus technology type networks, hubs can be used to increase the collision domain Dr. Clincy Lecture 29

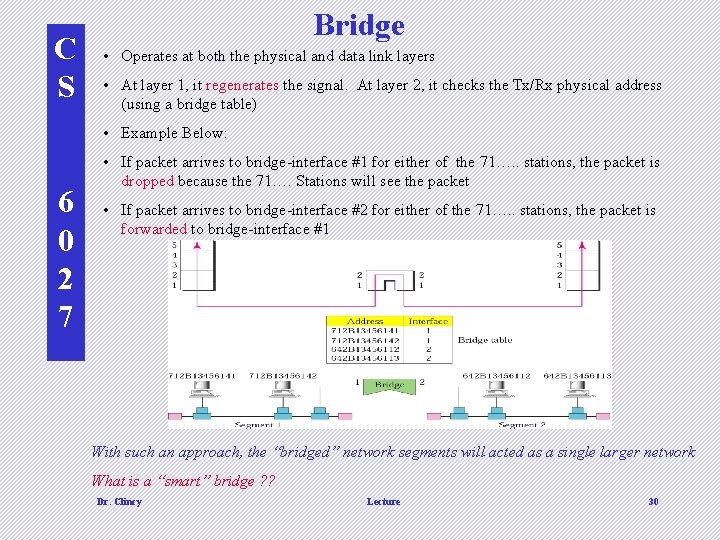
C S Bridge • Operates at both the physical and data link layers • At layer 1, it regenerates the signal. At layer 2, it checks the Tx/Rx physical address (using a bridge table) • Example Below: 6 0 2 7 • If packet arrives to bridge-interface #1 for either of the 71…. . stations, the packet is dropped because the 71…. Stations will see the packet • If packet arrives to bridge-interface #2 for either of the 71…. . stations, the packet is forwarded to bridge-interface #1 With such an approach, the “bridged” network segments will acted as a single larger network What is a “smart” bridge ? ? Dr. Clincy Lecture 30

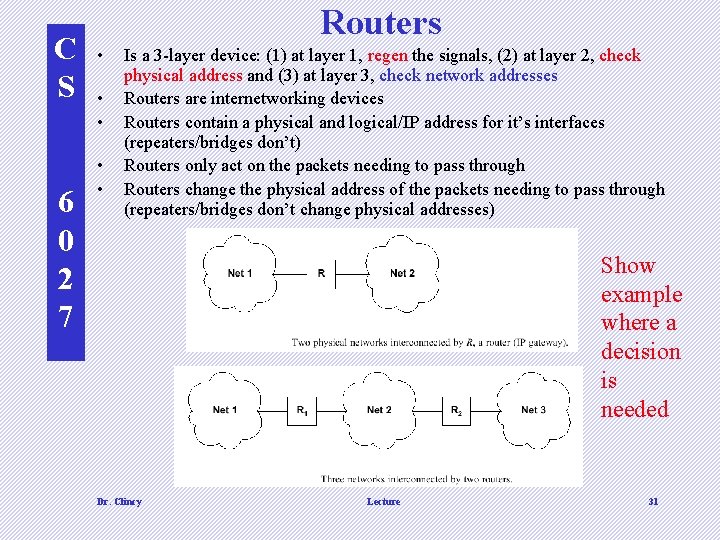
C S 6 0 2 7 Routers • • • Is a 3 -layer device: (1) at layer 1, regen the signals, (2) at layer 2, check physical address and (3) at layer 3, check network addresses Routers are internetworking devices Routers contain a physical and logical/IP address for it’s interfaces (repeaters/bridges don’t) Routers only act on the packets needing to pass through Routers change the physical address of the packets needing to pass through (repeaters/bridges don’t change physical addresses) Show example where a decision is needed d d Dr. Clincy Lecture 31

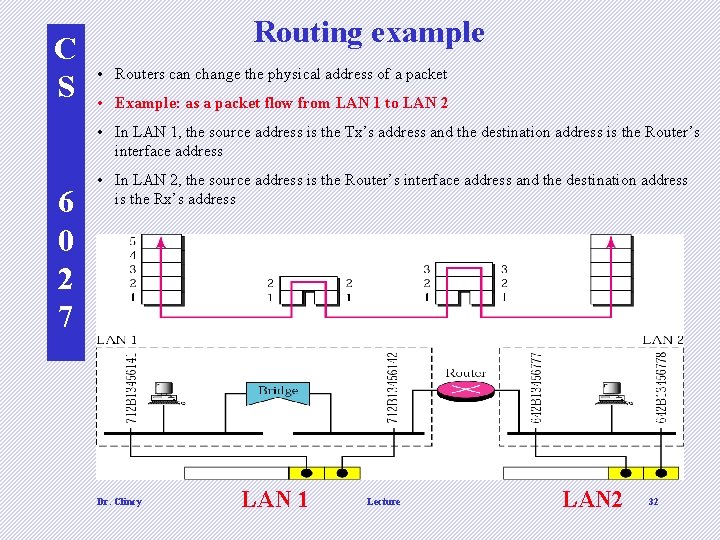
C S Routing example • Routers can change the physical address of a packet • Example: as a packet flow from LAN 1 to LAN 2 • In LAN 1, the source address is the Tx’s address and the destination address is the Router’s interface address 6 0 2 7 • In LAN 2, the source address is the Router’s interface address and the destination address is the Rx’s address Dr. Clincy LAN 1 Lecture 32 LAN 2

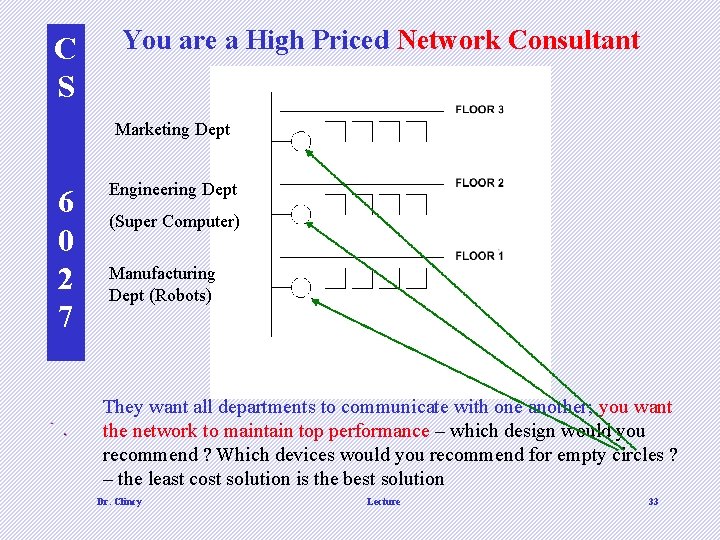
C S You are a High Priced Network Consultant Marketing Dept 6 0 2 7 Engineering Dept (Super Computer) Manufacturing Dept (Robots) d They want all departments to communicate with one another; you want the network to maintain top performance – which design would you recommend ? Which devices would you recommend for empty circles ? – the least cost solution is the best solution Dr. Clincy Lecture 33

C S Note: Lectures for Exam 1 just ended. We now start lectures for Exam 2 6 0 2 7 Dr. Clincy Lecture 34

C S Chapters 4 & 5 Addressing 6 0 2 7 Dr. Clincy Lecture 35

C S 6 0 2 7 IP ADDRESSING (Ch 4) Dr. Clincy Lecture 36

C S 6 0 2 7 IP Addresses • Internetworking Protocol (IP) of the Network Layer is responsible for uniquely identifying all devices and connections on the Internet • The unique identifier is called an IP address • IP address consist of 32 bits (for version 4) • Keep in mind that, if a single device had multiple connections to the Internet, you would need an IP address for each connection • Address space is 232 = 4, 294, 967, 296 32 -bit addresses • In theoretical terms, 4, 294, 967, 296 connections can be made to the Internet (not really true in real life) Dr. Clincy Lecture 37

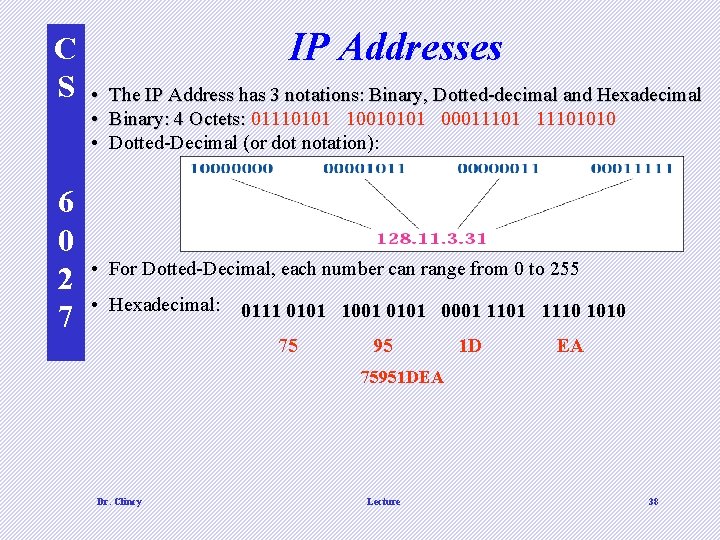
C S 6 0 2 7 IP Addresses • The IP Address has 3 notations: Binary, Dotted-decimal and Hexadecimal • Binary: 4 Octets: 01110101 10010101 00011101 11101010 Binary: 4 Octets: • Dotted-Decimal (or dot notation): • For Dotted-Decimal, each number can range from 0 to 255 • Hexadecimal: 0111 0101 1001 0101 0001 1110 1010 75 95 1 D EA 75951 DEA Dr. Clincy Lecture 38

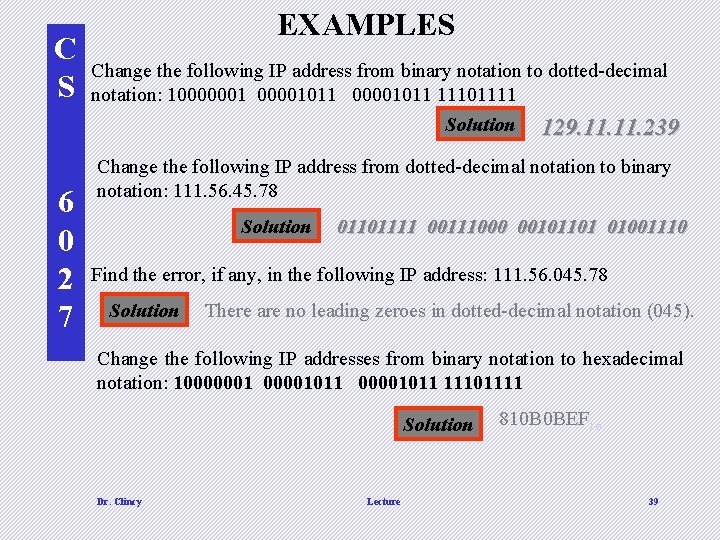
C S 6 0 2 7 EXAMPLES Change the following IP address from binary notation to dotted-decimal notation: 10000001011 11101111 Solution 129. 11. 239 Change the following IP address from dotted-decimal notation to binary notation: 111. 56. 45. 78 Solution 01101111 00111000 00101101 01001110 Find the error, if any, in the following IP address: 111. 56. 045. 78 Solution There are no leading zeroes in dotted-decimal notation (045). Change the following IP addresses from binary notation to hexadecimal notation: 10000001011 11101111 Solution Dr. Clincy Lecture 810 B 0 BEF 16 39

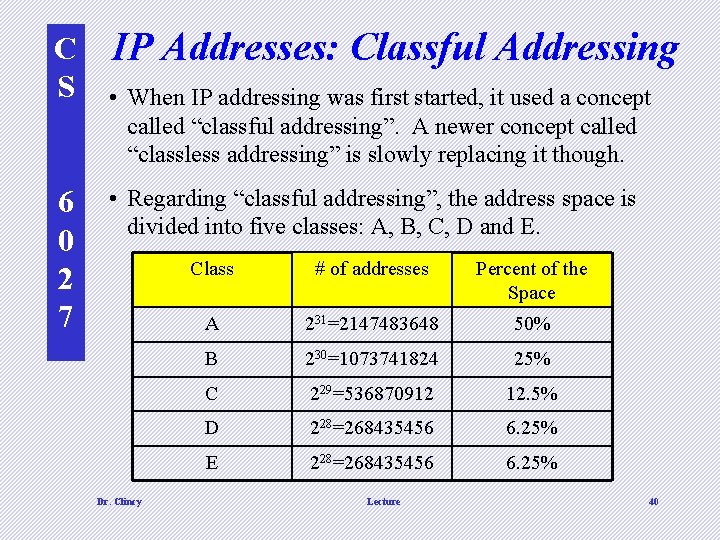
C S 6 0 2 7 IP Addresses: Classful Addressing • When IP addressing was first started, it used a concept called “classful addressing”. A newer concept called “classless addressing” is slowly replacing it though. • Regarding “classful addressing”, the address space is divided into five classes: A, B, C, D and E. Dr. Clincy Class # of addresses Percent of the Space A 231=2147483648 50% B 230=1073741824 25% C 229=536870912 12. 5% D 228=268435456 6. 25% E 228=268435456 6. 25% Lecture 40

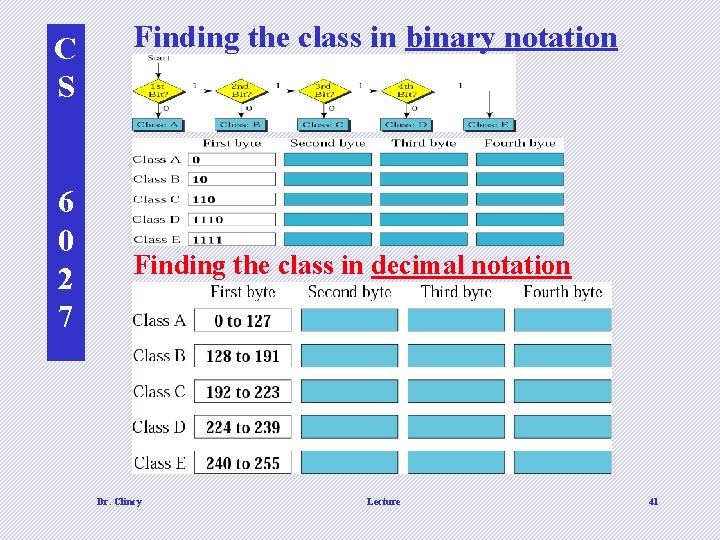
C S 6 0 2 7 Finding the class in binary notation Finding the class in decimal notation Dr. Clincy Lecture 41

EXAMPLES C S 6 0 2 7 Solution Find the class of the address: The first bit is 0. This is a 00000001011 11101111 class A address . Solution Find the class of the address: 110000011 00011011 1111 Solution Find the class of the address: The first byte is 227 (between 224 and 239); the class is D. 227. 12. 14. 87 Dr. Clincy The first 2 bits are 1; the third bit is 0. This is a class C address. Lecture 42

C S Netid and hostid • A, B and C class-addresses are divided into network id and host id • For Class A, Netid=1 byte, Hostid = 3 bytes 6 0 2 7 • For Class B, Netid=2 bytes, Hostid = 2 bytes • For Class C, Netid=3 bytes, Hostid = 1 byte Dr. Clincy Lecture 43

C S Blocks in class A • Class A has 128 blocks or network ids • First byte is the same (netid), the remaining 3 bytes can change (hostids) • Network id 0 (first), Net id 127 (last) and Net id 10 are reserved – leaving 125 ids to be assigned to organizations/companies 6 0 2 7 • Each block contains 16, 777, 216 addresses – this block should be used by large organizations. How many Host can be addressed ? ? • The first address in the block is called the “network address” – defines the network of the organization Example • Netid 73 is assigned • Last address is reserved • Recall: routers have addressees Dr. Clincy Lecture 44

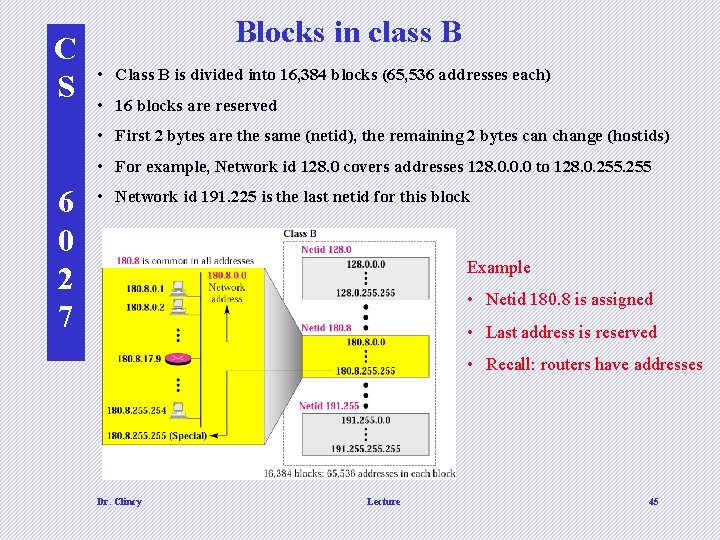
C S Blocks in class B • Class B is divided into 16, 384 blocks (65, 536 addresses each) • 16 blocks are reserved • First 2 bytes are the same (netid), the remaining 2 bytes can change (hostids) • For example, Network id 128. 0 covers addresses 128. 0. 0. 0 to 128. 0. 255 6 0 2 7 • Network id 191. 225 is the last netid for this block Example • Netid 180. 8 is assigned • Last address is reserved • Recall: routers have addresses Dr. Clincy Lecture 45

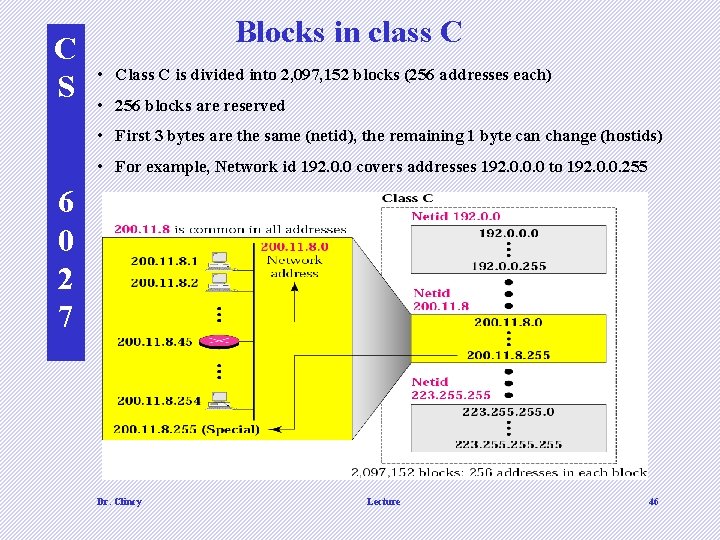
C S Blocks in class C • Class C is divided into 2, 097, 152 blocks (256 addresses each) • 256 blocks are reserved • First 3 bytes are the same (netid), the remaining 1 byte can change (hostids) • For example, Network id 192. 0. 0 covers addresses 192. 0. 0. 0 to 192. 0. 0. 255 6 0 2 7 Dr. Clincy Lecture 46

C S Class D addresses are used for multicasting; there is only one block in this class. 6 0 2 7 Class E addresses are reserved for special purposes; most of the block is wasted. Dr. Clincy Lecture 47

C S Network Addresses The network address is the first address. The network address defines the network to the rest of the Internet. 6 0 2 7 Given the network address, we can find the class of the address, the block, and the range of the addresses in the block Given the network address 17. 0. 0. 0, find the class, the block, and the range of the addresses. Solution The class is A because the first byte is between 0 and 127. The block has a netid of 17. The addresses range from 17. 0. 0. 0 to 17. 255. Given the network address 132. 21. 0. 0, find the class, the block, and the range of the addresses. Solution The class is B because the first byte is between 128 and 191. The block has a netid of 132. 21. The addresses range from 132. 21. 0. 0 to 132. 21. 255. Given the network address 220. 34. 76. 0, find the class, the block, and the range of the addresses. The class is C because the first byte is between 192 and 223. The block has a netid of 220. 34. 76. The addresses range from 220. 34. 76. 0 to Solution 220. 34. 76. 255. Dr. Clincy Lecture 48

C S REMINDER: Go Over Converting Binary to Decimal and Vice Versa 6 0 2 7 Dr. Clincy Lecture 49

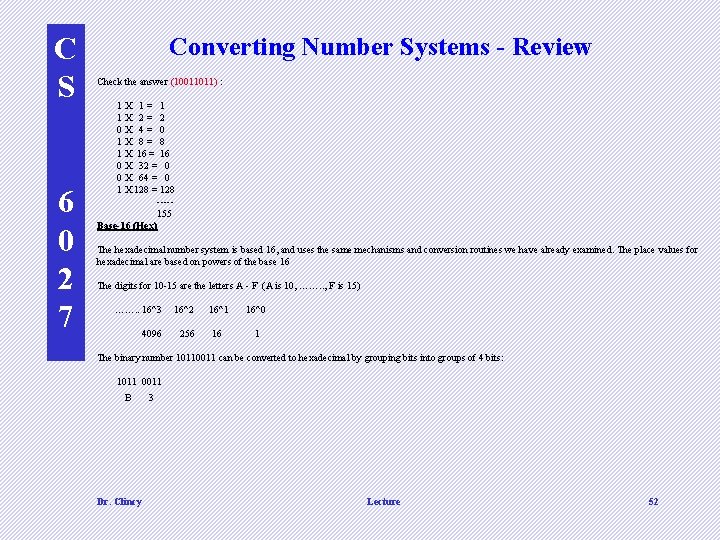
C S 6 0 2 7 Converting Number Systems - Review Base-10 The decimal number system is based on power of the base 10. For example, for the number 1259, the 9 is in the 10^0 column - 1 s column the 5 is in the 10^1 column - 10 s column the 2 is in the 10^2 column - 100 s column the 1 is in the 10^3 column - 1000 s column 1259 is 9 X 1 = 9 + 5 X 10 = 50 + 2 X 100 = 200 + 1 X 1000 = 1000 ---- 1259 Base-2 (Binary) The Binary number system uses the same mechanism and concept however, the base is 2 versus 10 The place values for binary are based on powers of the base 2: … 2^7 2^6 2^5 2^4 2^3 2^2 2^1 2^0 128 64 32 16 8 4 2 1 Dr. Clincy Lecture 50

C S 6 0 2 7 Converting Number Systems - Review So, the binary number 10110011 can be converted to a decimal number 1 X 1 = 1 (right most bit or position) 1 X 2 = 2 0 X 4 = 0 0 X 8 = 0 1 X 16 = 16 1 X 32 = 32 0 X 64 = 0 1 X 128 = 128 (left most bit or position) ----- 179 in decimal To convert from decimal to binary requires a different method called the division/remainder method. The idea is to repeatedly divide the decimal number and resulting quotients by 2. The answer will be the remainders. Example: convert 155 to binary (Start from the top and work down) 155/2 Q = 77, R = 1 (Start) 77/2 Q = 38, R = 1 38/2 Q = 19, R = 0 19/2 Q = 9, R = 1 9/2 Q = 4, R = 1 4/2 Q = 2, R = 0 2/2 Q = 1, R = 0 1/2 Q = 0, R = 1 (Stop) Answer is 10011011. Be careful to place the digits in the correct order. Dr. Clincy Lecture 51

C S 6 0 2 7 Converting Number Systems - Review Check the answer (10011011) : 1 X 1 = 1 X 2 = 2 0 X 4 = 0 1 X 8 = 8 1 X 16 = 16 0 X 32 = 0 X 64 = 0 1 X 128 = 128 ---- 155 Base-16 (Hex) The hexadecimal number system is based 16, and uses the same mechanisms and conversion routines we have already examined. The place values for hexadecimal are based on powers of the base 16 The digits for 10 -15 are the letters A - F (A is 10, ……. . , F is 15) ……. . 16^3 16^2 16^1 16^0 4096 256 16 1 The binary number 10110011 can be converted to hexadecimal by grouping bits into groups of 4 bits: 1011 0011 B 3 Dr. Clincy Lecture 52

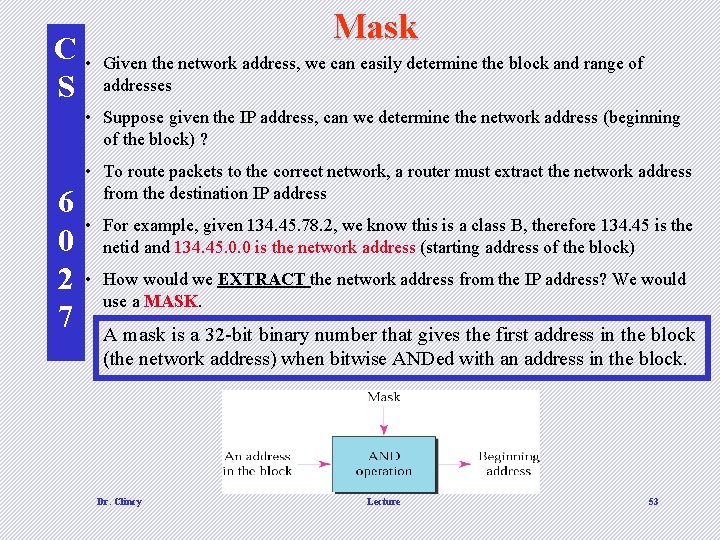
C • S Mask Given the network address, we can easily determine the block and range of addresses • Suppose given the IP address, can we determine the network address (beginning of the block) ? 6 0 2 7 • To route packets to the correct network, a router must extract the network address from the destination IP address • For example, given 134. 45. 78. 2, we know this is a class B, therefore 134. 45 is the netid and 134. 45. 0. 0 is the network address (starting address of the block) • How would we EXTRACT the network address from the IP address? We would use a MASK. A mask is a 32 -bit binary number that gives the first address in the block (the network address) when bitwise ANDed with an address in the block. Dr. Clincy Lecture 53

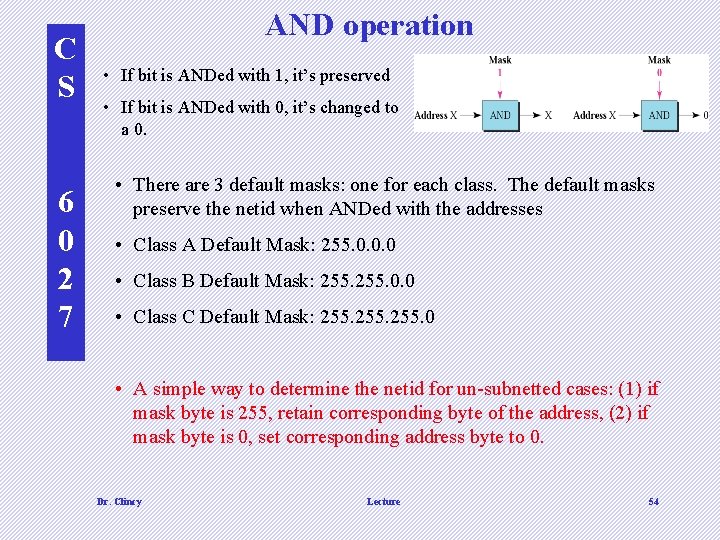
C S 6 0 2 7 AND operation • If bit is ANDed with 1, it’s preserved • If bit is ANDed with 0, it’s changed to a 0. • There are 3 default masks: one for each class. The default masks preserve the netid when ANDed with the addresses • Class A Default Mask: 255. 0. 0. 0 • Class B Default Mask: 255. 0. 0 • Class C Default Mask: 255. 0 • A simple way to determine the netid for un-subnetted cases: (1) if mask byte is 255, retain corresponding byte of the address, (2) if mask byte is 0, set corresponding address byte to 0. Dr. Clincy Lecture 54

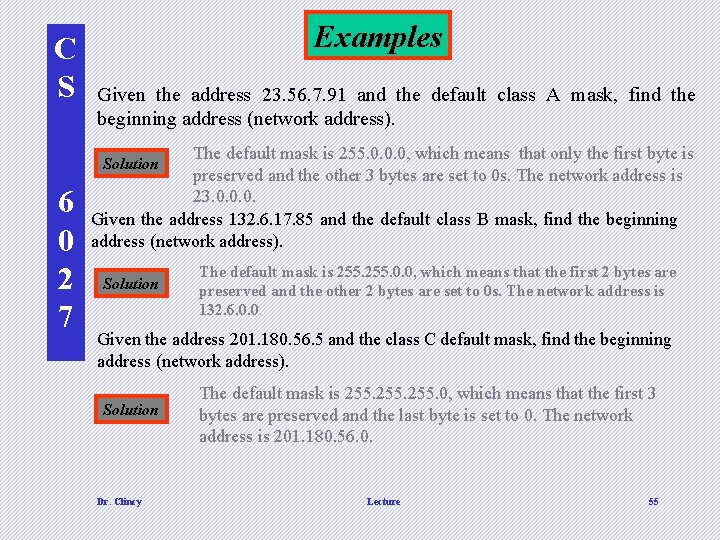
C S Examples Given the address 23. 56. 7. 91 and the default class A mask, find the beginning address (network address). The default mask is 255. 0. 0. 0, which means that only the first byte is preserved and the other 3 bytes are set to 0 s. The network address is 23. 0. 0. 0. Given the address 132. 6. 17. 85 and the default class B mask, find the beginning address (network address). Solution 6 0 2 7 Solution The default mask is 255. 0. 0, which means that the first 2 bytes are preserved and the other 2 bytes are set to 0 s. The network address is 132. 6. 0. 0. Given the address 201. 180. 56. 5 and the class C default mask, find the beginning address (network address). Solution Dr. Clincy The default mask is 255. 0, which means that the first 3 bytes are preserved and the last byte is set to 0. The network address is 201. 180. 56. 0. Lecture 55

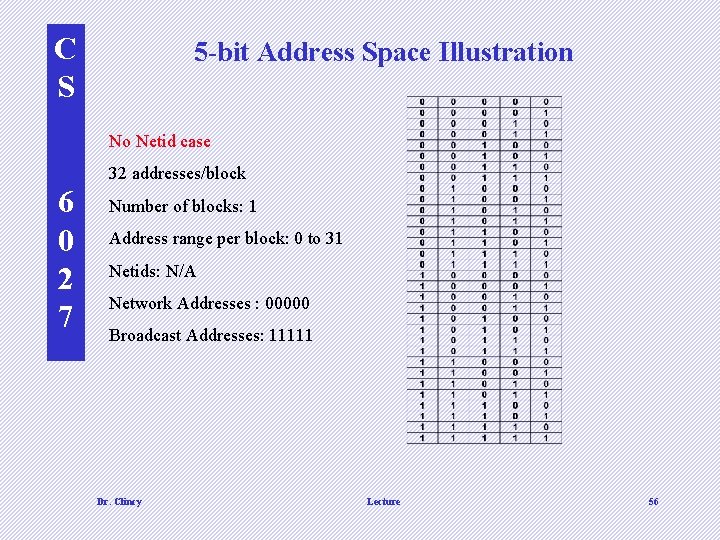
C S 5 -bit Address Space Illustration No Netid case 32 addresses/block 6 0 2 7 Number of blocks: 1 Address range per block: 0 to 31 Netids: N/A Network Addresses : 00000 Broadcast Addresses: 11111 Dr. Clincy Lecture 56

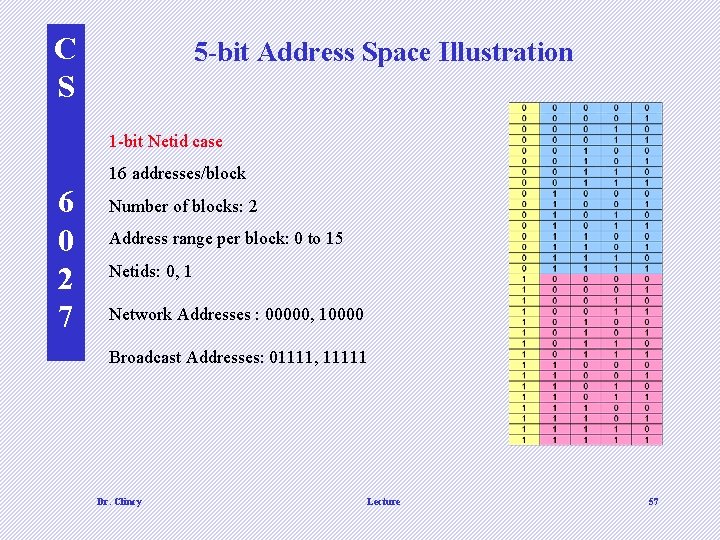
C S 5 -bit Address Space Illustration 1 -bit Netid case 16 addresses/block 6 0 2 7 Number of blocks: 2 Address range per block: 0 to 15 Netids: 0, 1 Network Addresses : 00000, 10000 Broadcast Addresses: 01111, 11111 Dr. Clincy Lecture 57

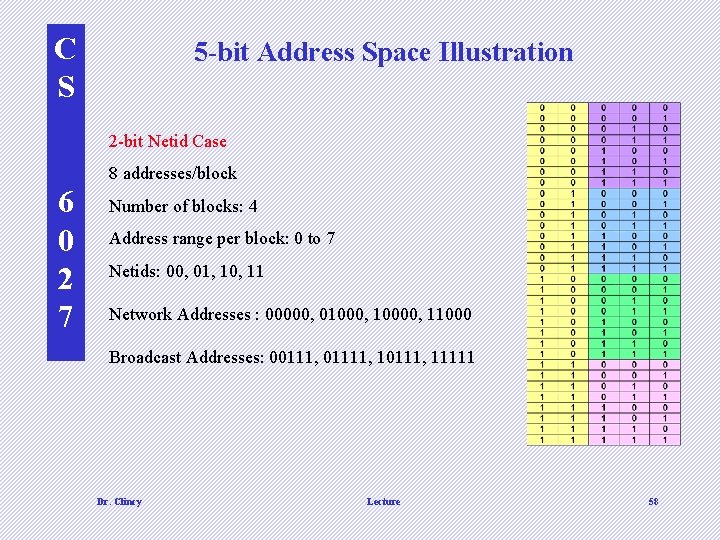
C S 5 -bit Address Space Illustration 2 -bit Netid Case 8 addresses/block 6 0 2 7 Number of blocks: 4 Address range per block: 0 to 7 Netids: 00, 01, 10, 11 Network Addresses : 00000, 01000, 10000, 11000 Broadcast Addresses: 00111, 01111, 10111, 11111 Dr. Clincy Lecture 58

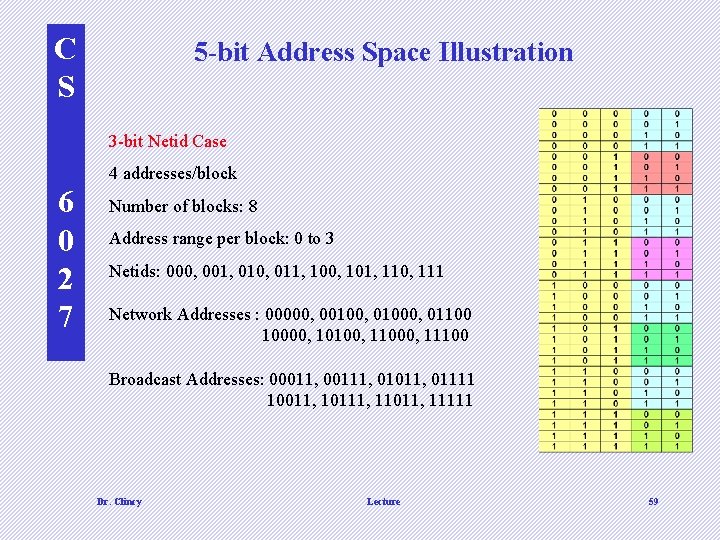
C S 5 -bit Address Space Illustration 3 -bit Netid Case 4 addresses/block 6 0 2 7 Number of blocks: 8 Address range per block: 0 to 3 Netids: 000, 001, 010, 011, 100, 101, 110, 111 Network Addresses : 00000, 00100, 01000, 01100 10000, 10100, 11000, 11100 Broadcast Addresses: 00011, 00111, 01011, 01111 10011, 10111, 11011, 11111 Dr. Clincy Lecture 59

C S Mixing 3 -bit & 2 -bit Cases (think of the 32 -bit case) 4 addresses/block and 8 addresses/block Number of blocks: 6 6 0 2 7 Address range per block: 0 to 3 and 0 to 7 Netids: 000, 001, 010, 011, 10, 11 Network Addresses : 00000, 00100, 01000, 01100 10000, 11000 Broadcast Addresses: 00011, 00111, 01011, 01111 10111, 11111 Dr. Clincy Lecture 60

C S Multihomed devices • As we mentioned that, any device with one or more connections to the Internet will need an IP address for EACH connection – such devices are called “multihomed” devices. • A Router could be a multihomed device 6 0 2 7 Dr. Clincy Lecture 61

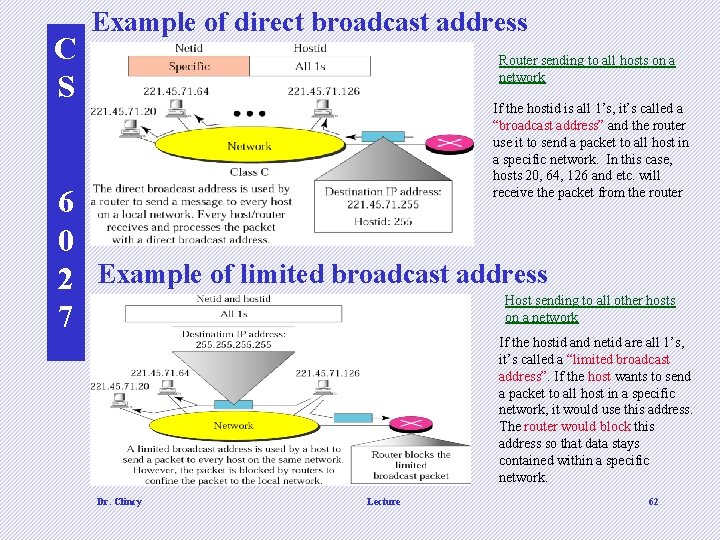
C S Example of direct broadcast address Router sending to all hosts on a network If the hostid is all 1’s, it’s called a “broadcast address” and the router use it to send a packet to all host in a specific network. In this case, hosts 20, 64, 126 and etc. will receive the packet from the router 6 0 2 Example of limited broadcast address Host sending to all other hosts on a network 7 If the hostid and netid are all 1’s, it’s called a “limited broadcast address”. If the host wants to send a packet to all host in a specific network, it would use this address. The router would block this address so that data stays contained within a specific network. Dr. Clincy Lecture 62

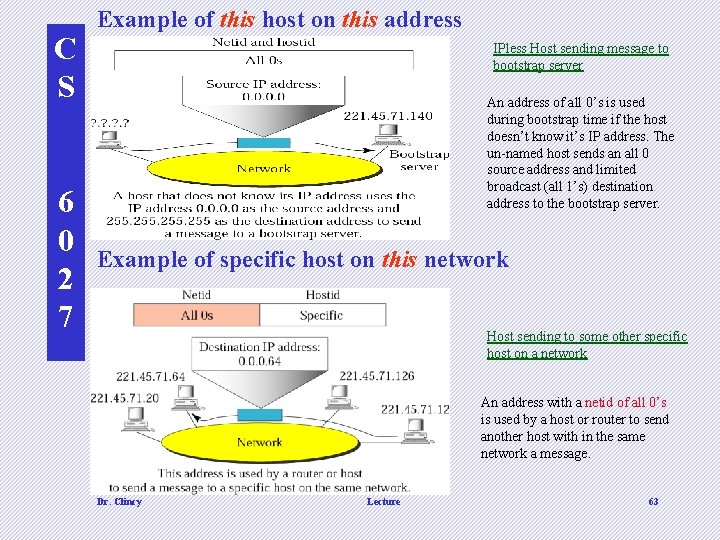
C S 6 0 2 7 Example of this host on this address IPless Host sending message to bootstrap server An address of all 0’s is used during bootstrap time if the host doesn’t know it’s IP address. The un-named host sends an all 0 source address and limited broadcast (all 1’s) destination address to the bootstrap server. Example of specific host on this network Host sending to some other specific host on a network An address with a netid of all 0’s is used by a host or router to send another host with in the same network a message. Dr. Clincy Lecture 63

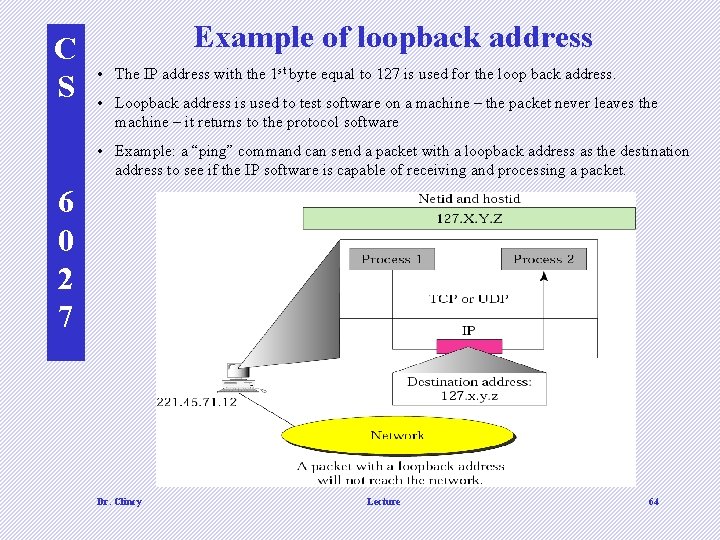
C S Example of loopback address • The IP address with the 1 st byte equal to 127 is used for the loop back address. • Loopback address is used to test software on a machine – the packet never leaves the machine – it returns to the protocol software • Example: a “ping” command can send a packet with a loopback address as the destination address to see if the IP software is capable of receiving and processing a packet. 6 0 2 7 Dr. Clincy Lecture 64

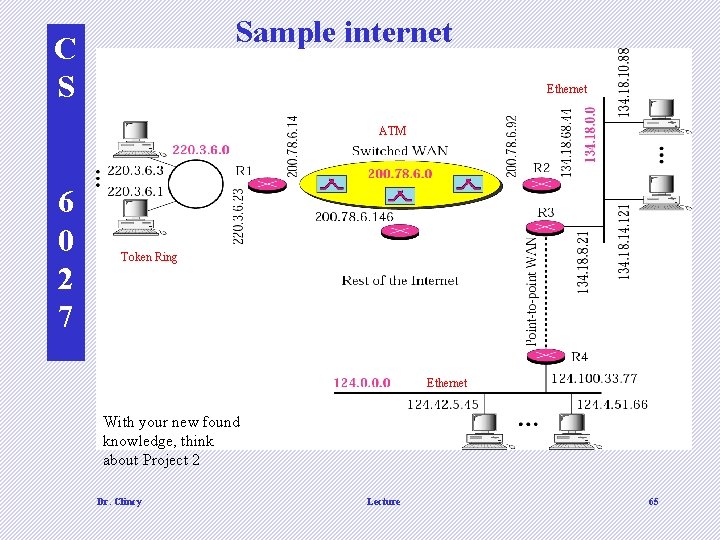
Sample internet C S Ethernet ATM 6 0 2 7 Token Ring Ethernet With your new found knowledge, think about Project 2 Dr. Clincy Lecture 65