Accessing Google Scholar under Extreme Internet Censorship A







- Slides: 31

Accessing Google Scholar under Extreme Internet Censorship: A Legal Avenue Zhen Lu, VMware Zhenhua Li, Jian Yang, Tianyin Xu, Ennan Zhai, Yao Liu, Christo Wilson, Tsinghua University / Tsinghua University UCSD Yale University Binghamton University Northeastern University luzhen 02@gmail. com Dec. 15, 2017

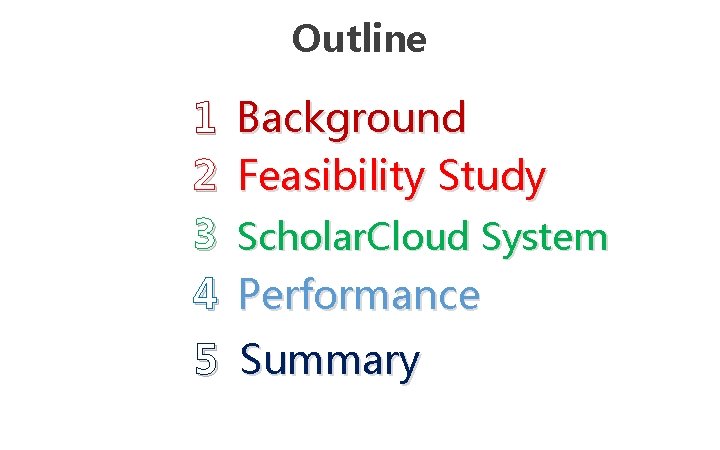
Outline 1 2 3 4 Background Feasibility Study Scholar. Cloud System Performance 5 Summary

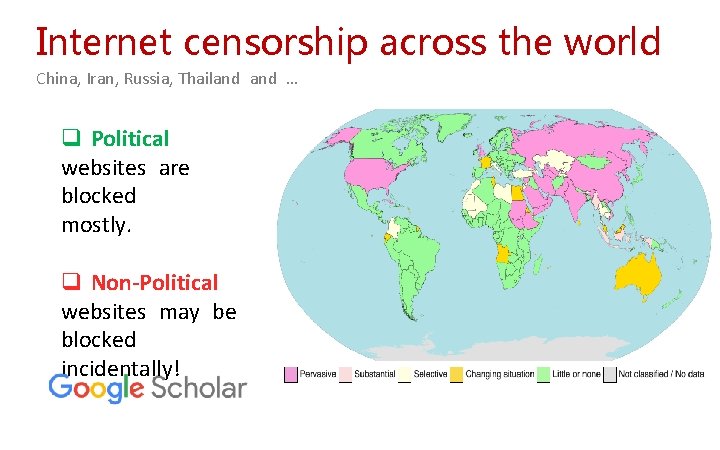
Internet censorship across the world China, Iran, Russia, Thailand … q Political websites are blocked mostly. q Non-Political websites may be blocked incidentally!

Troubles of scholars Find a topic -> Google Scholar search -> Read papers Google Scholar index includes roughly 160 million documents

Troubles of scholars Find a topic -> Google Scholar search -> Read papers Chinese researchers CANNOT access it.

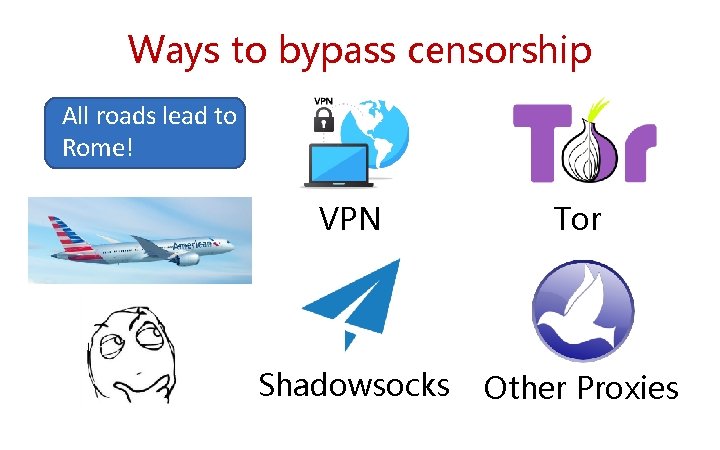
Ways to bypass censorship All roads lead to Rome! VPN Tor Shadowsocks Other Proxies

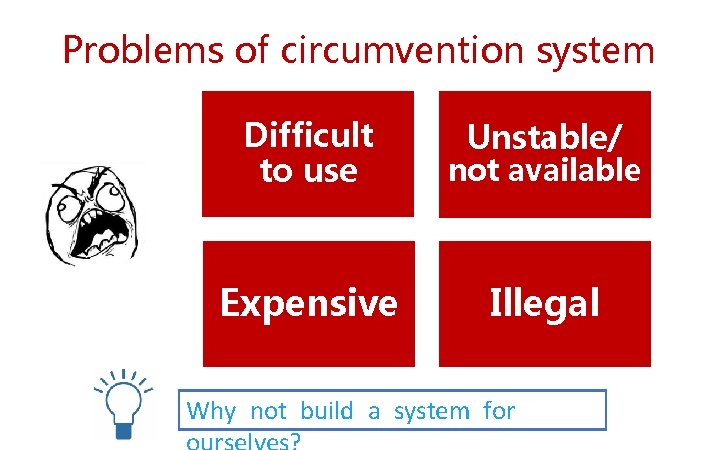
Problems of circumvention system Difficult to use not available Expensive Illegal Unstable/ Why not build a system for

2 Feasibility Study 8

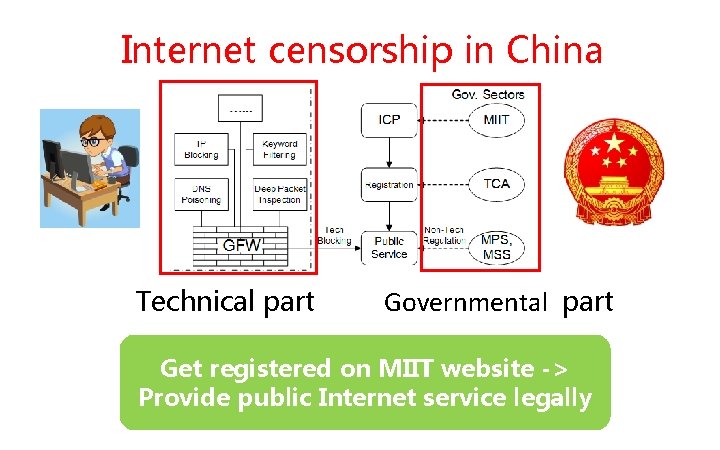
Internet censorship in China Technical part Governmental part Get registered on MIIT website -> Provide public Internet service legally

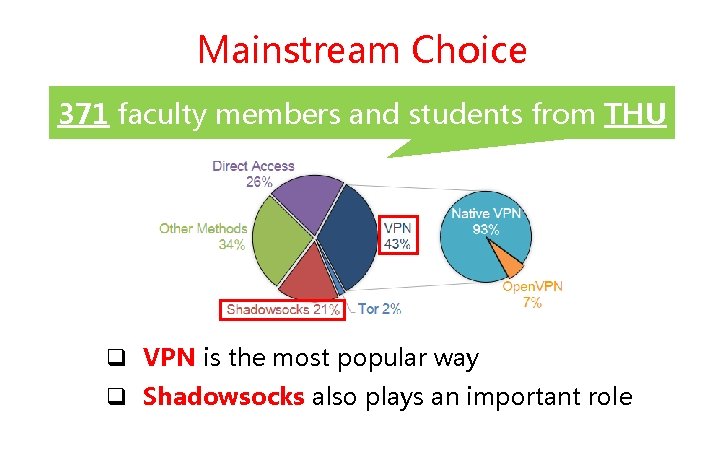
Mainstream Choice 371 faculty members and students from THU q VPN is the most popular way q Shadowsocks also plays an important role

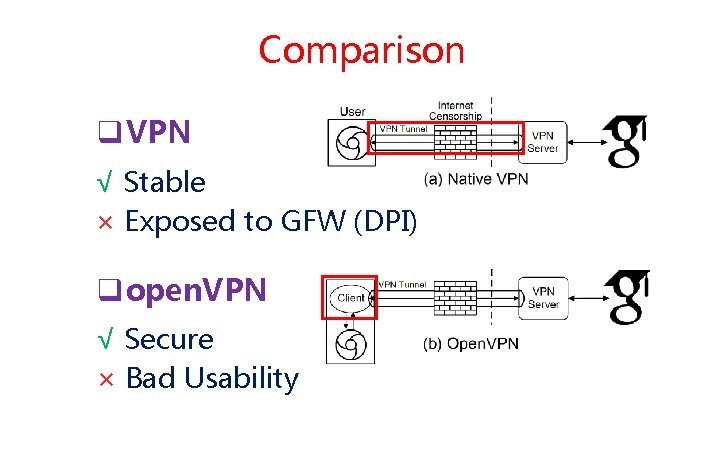
Comparison q VPN √ Stable × Exposed to GFW (DPI) q open. VPN √ Secure × Bad Usability

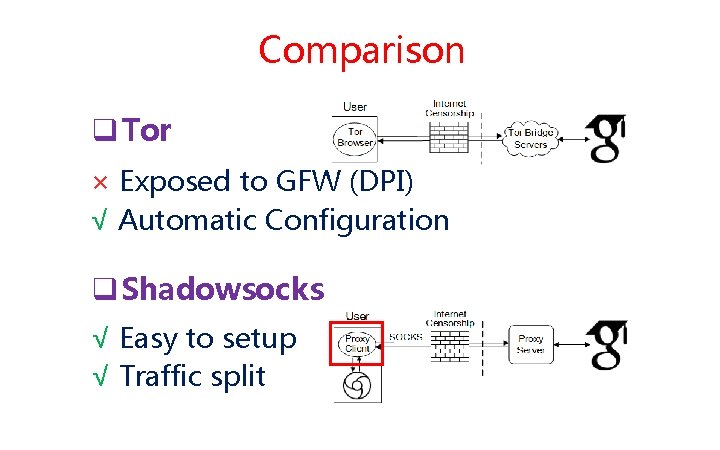
Comparison q Tor × Exposed to GFW (DPI) √ Automatic Configuration q Shadowsocks √ Easy to setup √ Traffic split

3 Scholar. Cloud System 13

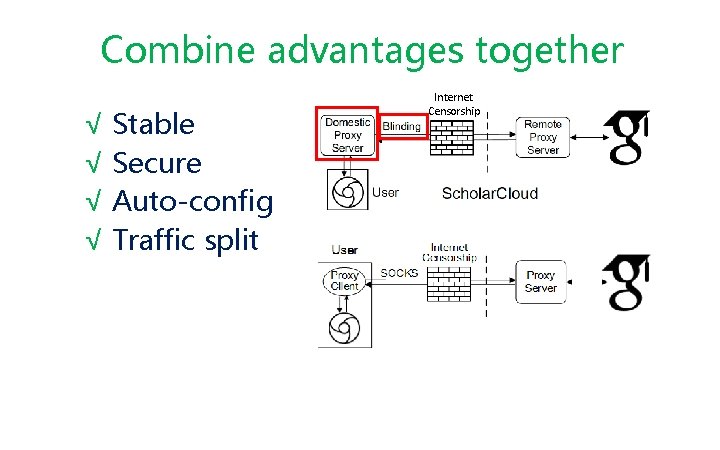
Combine advantages together √ Stable √ Secure √ Auto-config √ Traffic split Internet Censorship

Combine advantages together √ Stable √ Secure √ Auto-config √ Traffic split Internet Censorship http: //scholar. thucloud. com

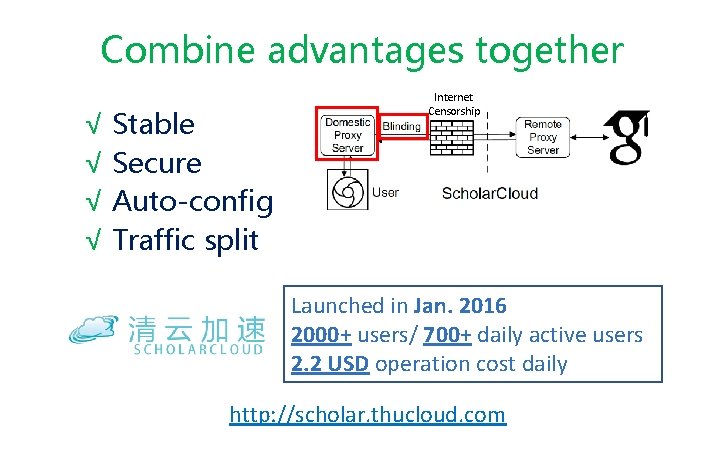
Combine advantages together √ Stable √ Secure √ Auto-config √ Traffic split Internet Censorship Launched in Jan. 2016 2000+ users/ 700+ daily active users 2. 2 USD operation cost daily http: //scholar. thucloud. com

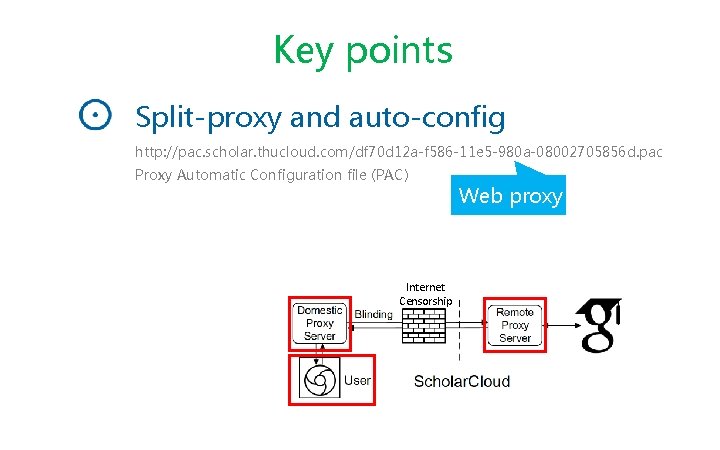
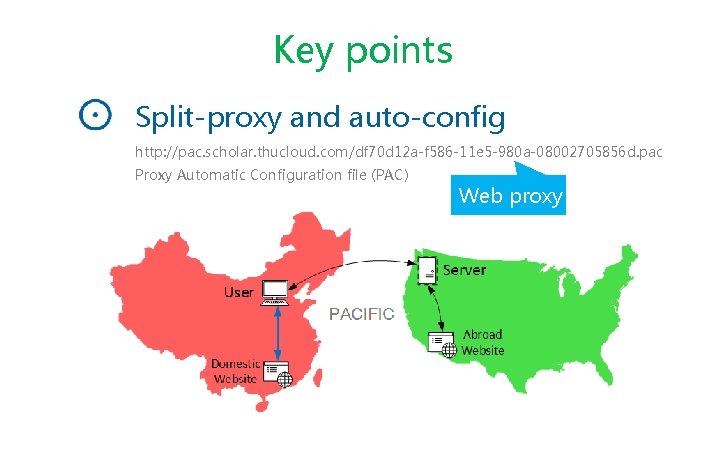
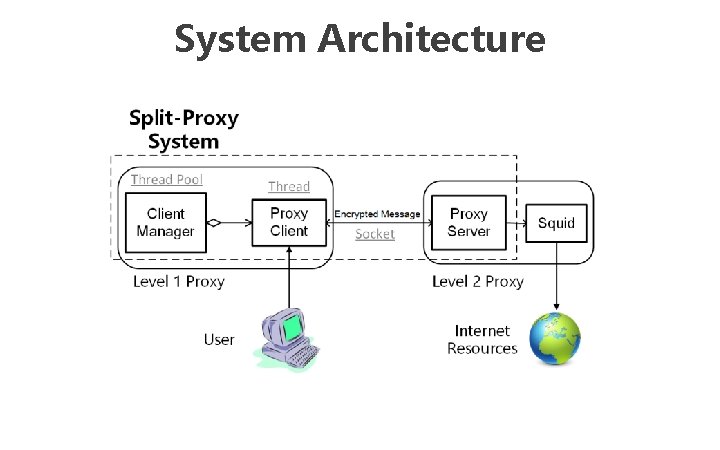
Key points Split-proxy and auto-config http: //pac. scholar. thucloud. com/df 70 d 12 a-f 586 -11 e 5 -980 a-08002705856 d. pac Proxy Automatic Configuration file (PAC) Internet Censorship Web proxy

Key points Split-proxy and auto-config http: //pac. scholar. thucloud. com/df 70 d 12 a-f 586 -11 e 5 -980 a-08002705856 d. pac Proxy Automatic Configuration file (PAC) Web proxy

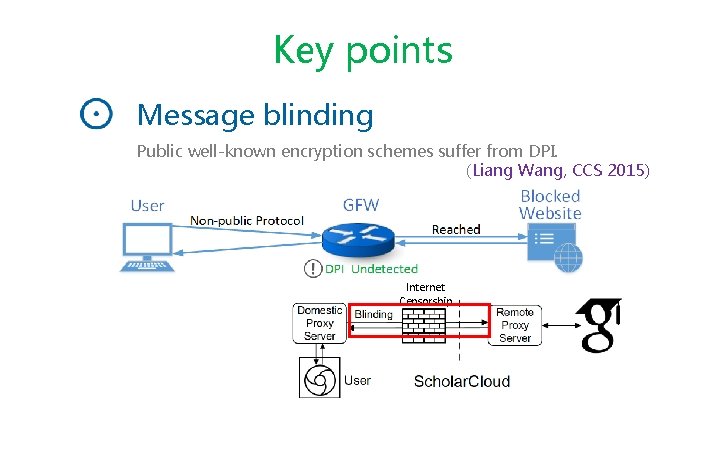
Key points Message blinding Public well-known encryption schemes suffer from DPI. (Liang Wang, CCS 2015) Internet Censorship

Key points Service legalization ICP Reg. #15063437 in China Internet Censorship

4 Performance 21

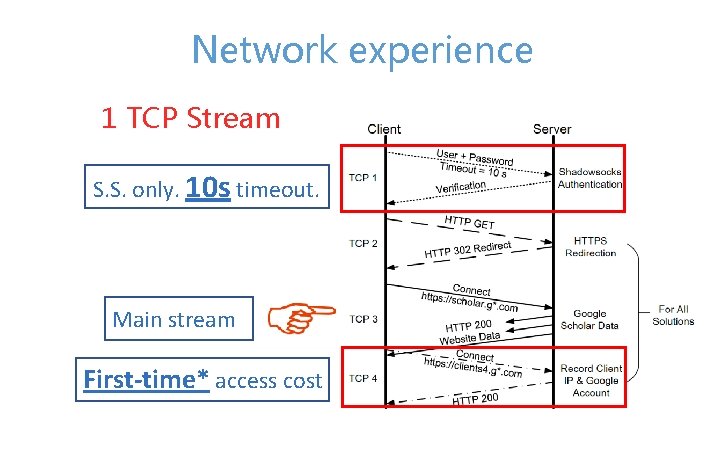
Network experience 1 TCP Stream S. S. only. 10 s timeout. Main stream First-time* access cost

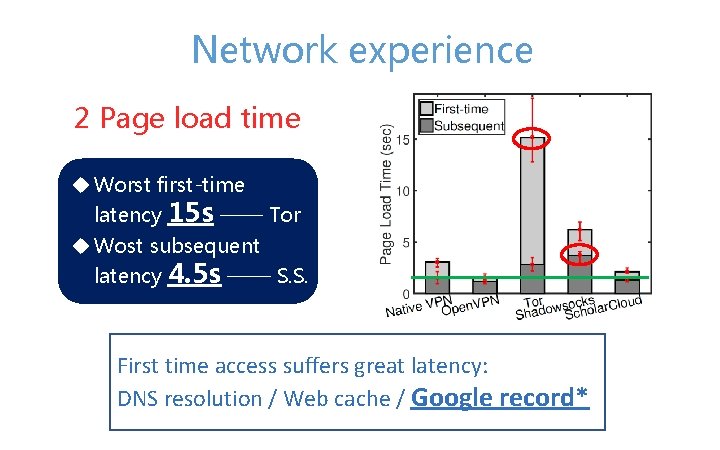
Network experience 2 Page load time u Worst first-time latency 15 s —— Tor u Wost subsequent latency 4. 5 s —— S. S. First time access suffers great latency: DNS resolution / Web cache / Google record*

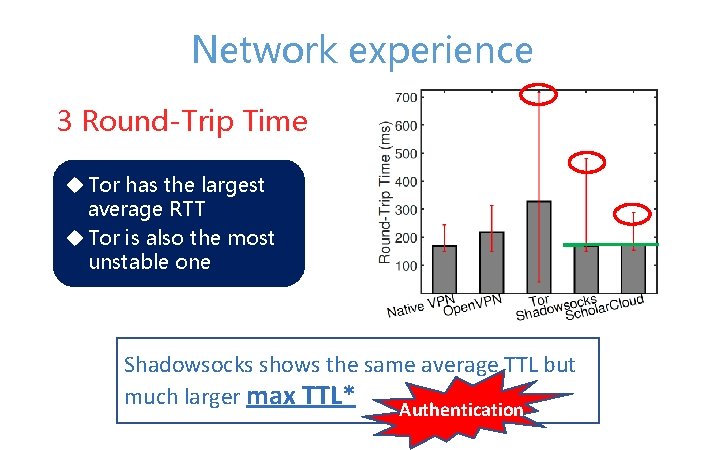
Network experience 3 Round-Trip Time u Tor has the largest average RTT u Tor is also the most unstable one Shadowsocks shows the same average TTL but much larger max TTL* Authentication

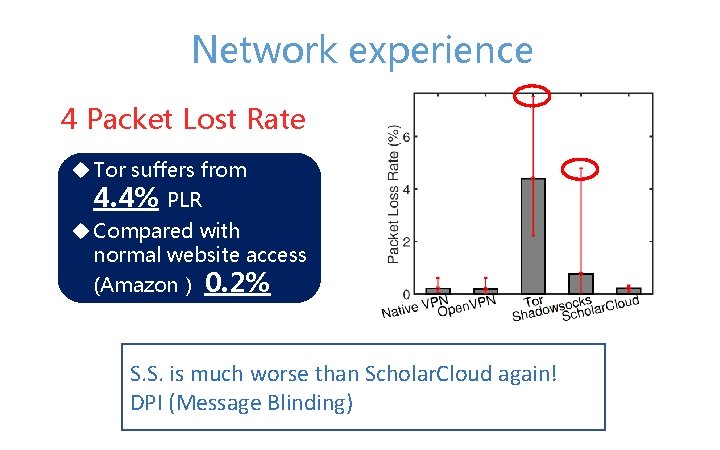
Network experience 4 Packet Lost Rate u Tor suffers from 4. 4% PLR u Compared with normal website access (Amazon) 0. 2% S. S. is much worse than Scholar. Cloud again! DPI (Message Blinding)

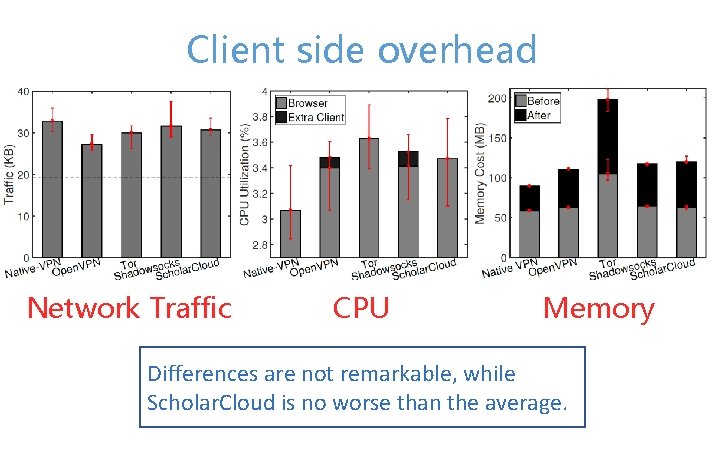
Client side overhead Network Traffic CPU Memory Differences are not remarkable, while Scholar. Cloud is no worse than the average.

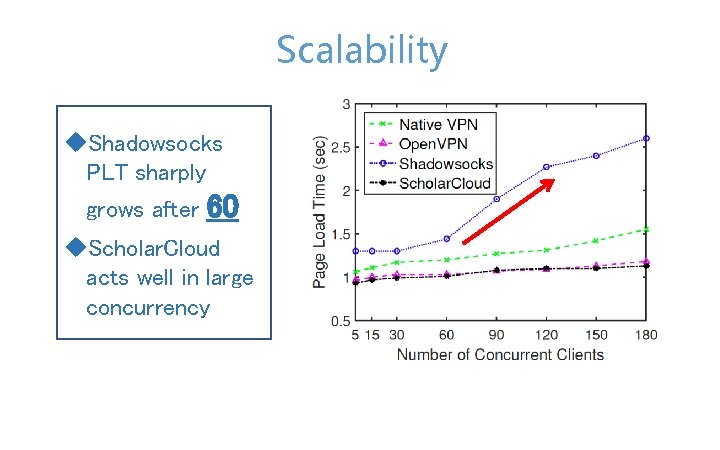
Scalability u. Shadowsocks PLT sharply grows after 60 u. Scholar. Cloud acts well in large concurrency

Summary p. Legally accessing Google Scholar under extreme censorship p. Design and deploy Scholar. Cloud to provide web proxy service to thousands of users, with high performance, usability, robustness against censorship, and low overhead p. Measure and analyze five main circumvention system on network performance, client side overhead, robustness against censorship and scalability. We provide a new perspective to Internet censorship in China. We hope that our experiences will help the community better understand China’s Internet censorship ecosystem.

The End Thank you!

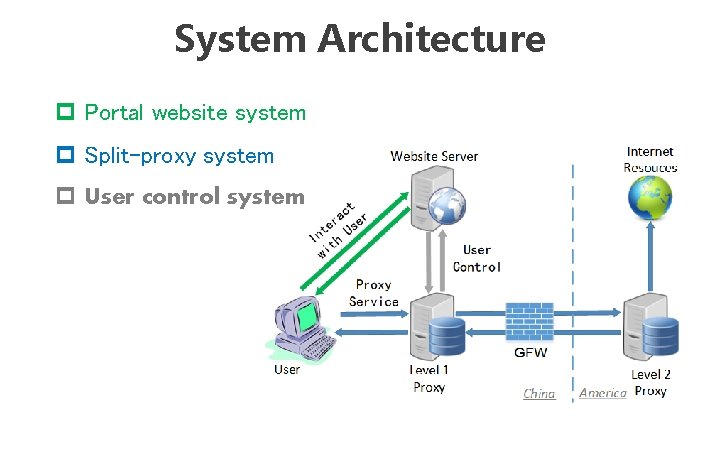
System Architecture p Portal website system p Split-proxy system p User control system

System Architecture
 Scholar
Scholar Google acadêmico (https //scholar.google.com.br/)
Google acadêmico (https //scholar.google.com.br/) Ews shot
Ews shot Gmailgmailgmailgmail
Gmailgmailgmailgmail Hard core science
Hard core science Scholar google
Scholar google Google scholar
Google scholar Scholar
Scholar Conflict of interest penelitian adalah
Conflict of interest penelitian adalah Scholar google
Scholar google Googlen classroom
Googlen classroom Googlr znalac
Googlr znalac Google scholar
Google scholar Google scholar
Google scholar Google scholar
Google scholar Google scholar tricks
Google scholar tricks Googlel calender
Googlel calender Google scholar hinari
Google scholar hinari /partnerdash google scholar
/partnerdash google scholar Google scholar
Google scholar Google scholar
Google scholar Google scholar
Google scholar Google scholarly search engine
Google scholarly search engine Pub uc
Pub uc Scholar google profile search
Scholar google profile search Anurag acharya google
Anurag acharya google Google scholar
Google scholar Google scholar
Google scholar Google scholar
Google scholar My learning essentials
My learning essentials Scholar google
Scholar google Googlel translat
Googlel translat