A Survey of MPC Offerings Mayank Varia Boston

A Survey of MPC Offerings Mayank Varia Boston University

• Why are people interested in MPC nowadays? • What is it? • How is MPC positively benefitting society? Caveats throughout • • This talk only subsamples the answer to each question! Descriptions + figures are reproduced from original works
Why now? Mechanization Electricity Automation Data & knowledge Source: World Economic Forum 2016, https: //www. weforum. org/centre-for-the-fourth-industrial-
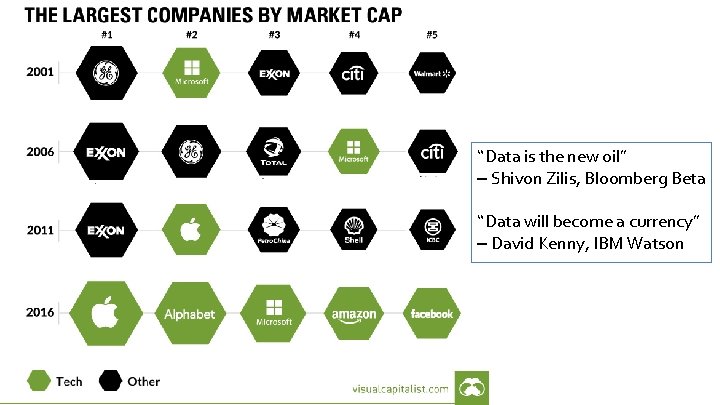
“Data is the new oil” – Shivon Zilis, Bloomberg Beta “Data will become a currency” – David Kenny, IBM Watson
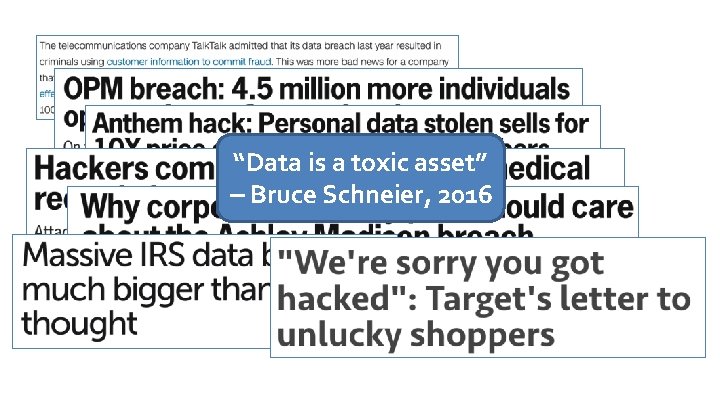
“Data is a toxic asset” – Bruce Schneier, 2016
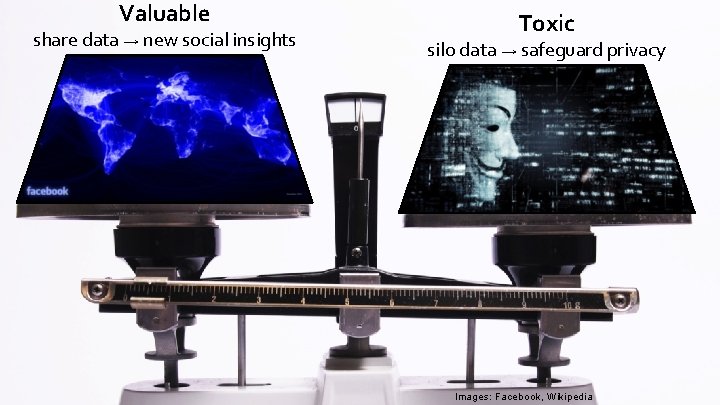
Valuable share data → new social insights Toxic silo data → safeguard privacy Images: Facebook, Wikipedia

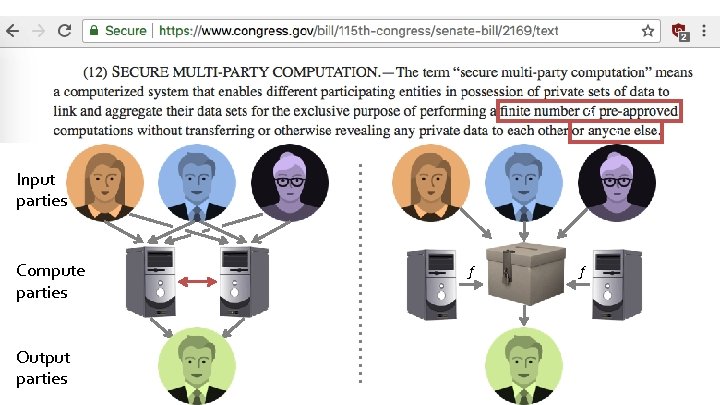
s Input parties Compute parties Output parties f f s
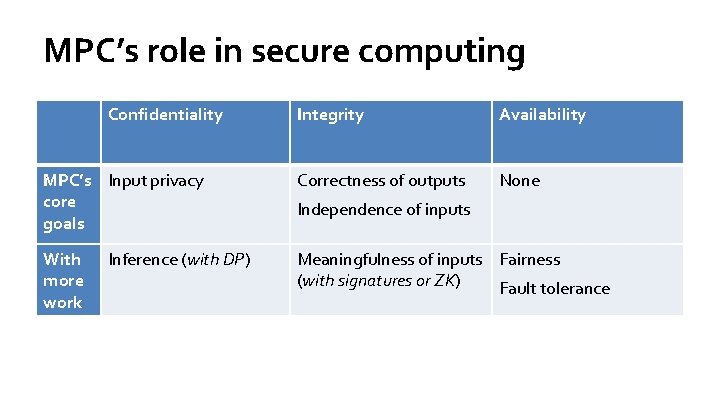
MPC’s role in secure computing Confidentiality Integrity Availability MPC’s Input privacy core goals Correctness of outputs None With more work Meaningfulness of inputs Fairness (with signatures or ZK) Fault tolerance Inference (with DP) Independence of inputs
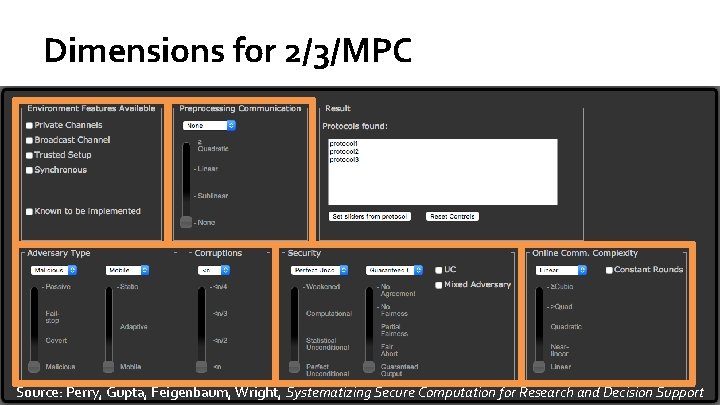
Dimensions for 2/3/MPC Source: Perry, Gupta, Feigenbaum, Wright, Systematizing Secure Computation for Research and Decision Support
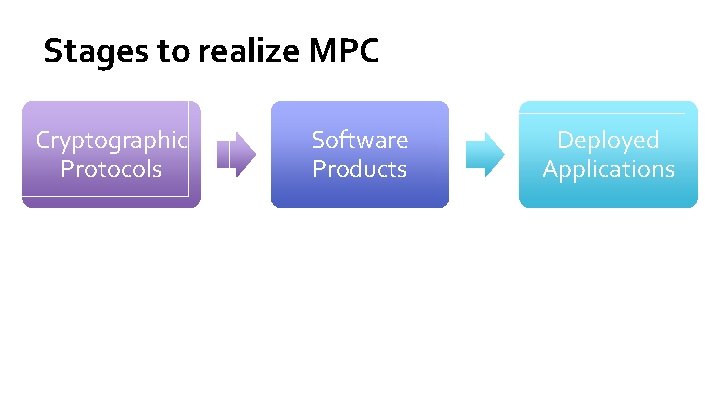
Stages to realize MPC Cryptographic Protocols Software Products Deployed Applications
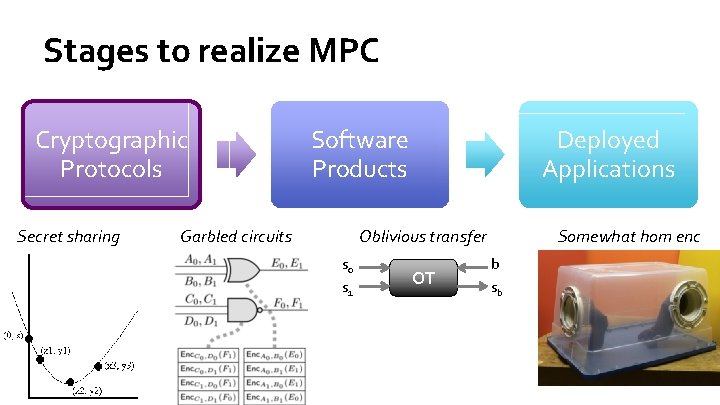
Stages to realize MPC Cryptographic Protocols Secret sharing Software Products Garbled circuits Deployed Applications Oblivious transfer s 0 s 1 OT Somewhat hom enc b sb
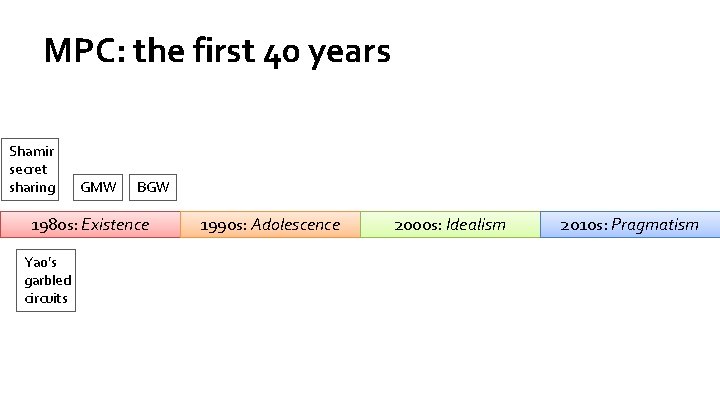
MPC: the first 40 years Shamir secret sharing GMW BGW 1980 s: Existence Yao’s garbled circuits 1990 s: Adolescence 2000 s: Idealism 2010 s: Pragmatism
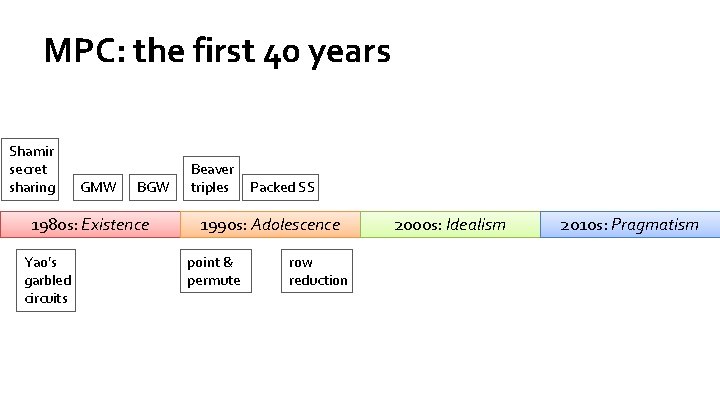
MPC: the first 40 years Shamir secret sharing GMW BGW 1980 s: Existence Yao’s garbled circuits Beaver triples Packed SS 1990 s: Adolescence point & permute row reduction 2000 s: Idealism 2010 s: Pragmatism
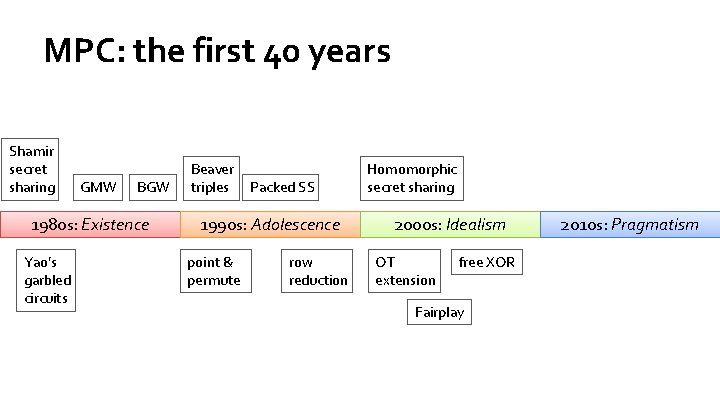
MPC: the first 40 years Shamir secret sharing GMW BGW 1980 s: Existence Yao’s garbled circuits Beaver triples Packed SS 1990 s: Adolescence point & permute row reduction Homomorphic secret sharing 2000 s: Idealism OT extension free XOR Fairplay 2010 s: Pragmatism
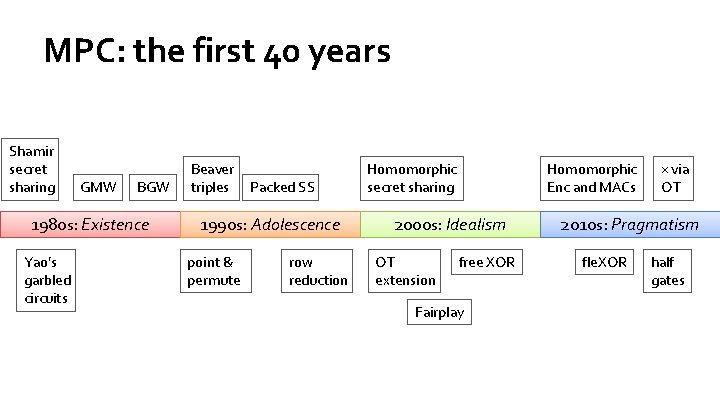
MPC: the first 40 years Shamir secret sharing GMW BGW 1980 s: Existence Yao’s garbled circuits Beaver triples Packed SS 1990 s: Adolescence point & permute row reduction Homomorphic Enc and MACs Homomorphic secret sharing 2000 s: Idealism OT extension free XOR Fairplay × via OT 2010 s: Pragmatism fle. XOR half gates
Stages to realize MPC Cryptographic Protocols Software Products Source: Sharemind blog, Standardisation efforts on secure computing Deployed Applications
Stages to realize MPC Cryptographic Protocols Software Products Deployed Applications
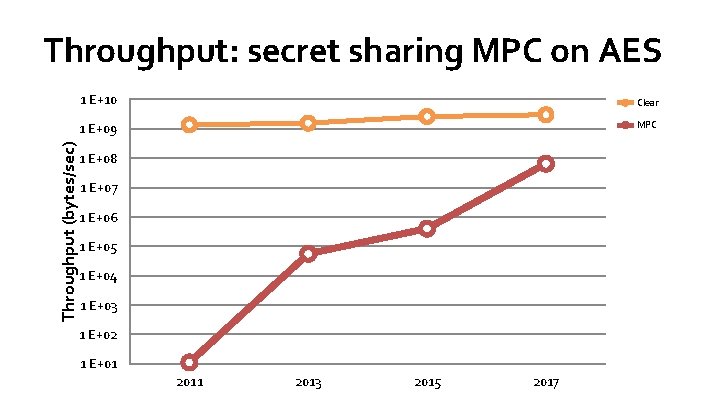
Throughput (bytes/sec) Throughput: secret sharing MPC on AES 1 E+10 Clear 1 E+09 MPC 1 E+08 1 E+07 1 E+06 1 E+05 1 E+04 1 E+03 1 E+02 1 E+01 2013 2015 2017
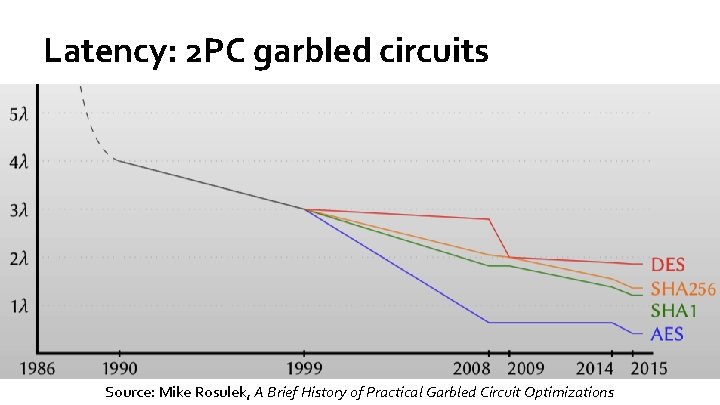
Latency: 2 PC garbled circuits Source: Mike Rosulek, A Brief History of Practical Garbled Circuit Optimizations
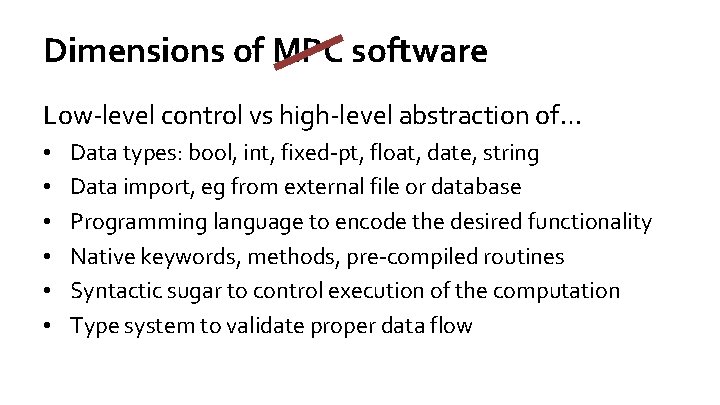
Dimensions of MPC software Low-level control vs high-level abstraction of… • • • Data types: bool, int, fixed-pt, float, date, string Data import, eg from external file or database Programming language to encode the desired functionality Native keywords, methods, pre-compiled routines Syntactic sugar to control execution of the computation Type system to validate proper data flow
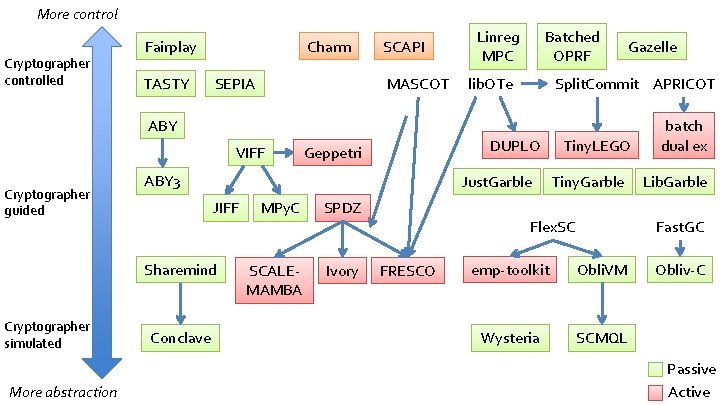
More control Cryptographer controlled Charm Fairplay TASTY SEPIA SCAPI MASCOT Linreg MPC Batched OPRF lib. OTe Gazelle Split. Commit APRICOT ABY VIFF Cryptographer guided ABY 3 Just. Garble JIFF Sharemind Cryptographer simulated More abstraction DUPLO Geppetri Conclave MPy. C SPDZ SCALEMAMBA Ivory Tiny. LEGO Tiny. Garble Flex. SC FRESCO batch dual ex Lib. Garble Fast. GC emp-toolkit Obli. VM Wysteria SCMQL Obliv-C Passive Active
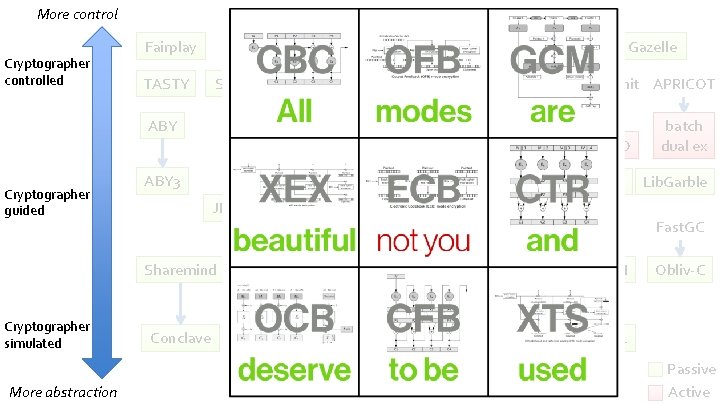
More control Cryptographer controlled Charm Fairplay TASTY SEPIA SCAPI MASCOT Linreg MPC Batched OPRF lib. OTe Gazelle Split. Commit APRICOT ABY VIFF Cryptographer guided ABY 3 Just. Garble JIFF Sharemind Cryptographer simulated More abstraction DUPLO Geppetri Conclave MPy. C SPDZ SCALEMAMBA Ivory Tiny. LEGO Tiny. Garble Flex. SC FRESCO batch dual ex Lib. Garble Fast. GC emp-toolkit Obli. VM Wysteria SCMQL Obliv-C Passive Active
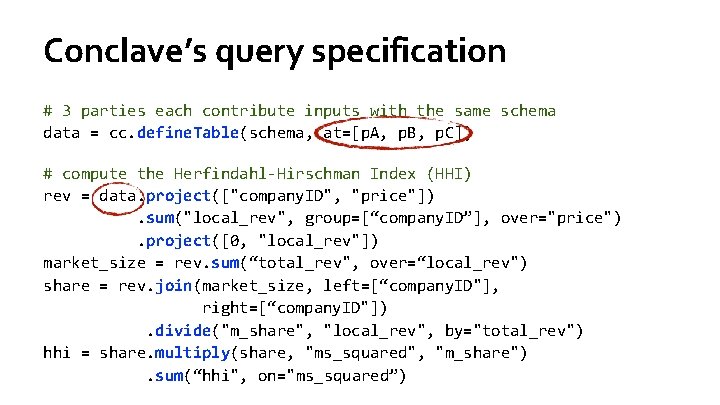
Conclave’s query specification # 3 parties each contribute inputs with the same schema data = cc. define. Table(schema, at=[p. A, p. B, p. C]) # compute the Herfindahl-Hirschman Index (HHI) rev = data. project(["company. ID", "price"]). sum("local_rev", group=[“company. ID”], over="price"). project([0, "local_rev"]) market_size = rev. sum(“total_rev", over=“local_rev") share = rev. join(market_size, left=[“company. ID"], right=[“company. ID"]). divide("m_share", "local_rev", by="total_rev") hhi = share. multiply(share, "ms_squared", "m_share"). sum(“hhi", on="ms_squared”)
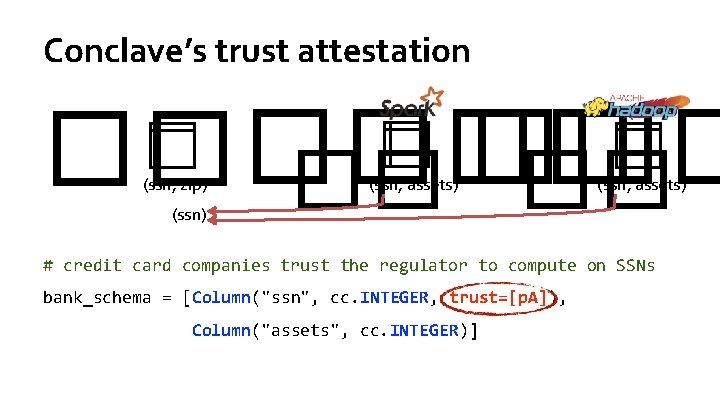
Conclave’s trust attestation ������ �� �� (ssn, zip) (ssn, assets) (ssn) # credit card companies trust the regulator to compute on SSNs bank_schema = [Column("ssn", cc. INTEGER, trust=[p. A]), Column("assets", cc. INTEGER)]
How is MPC being used for social good? Cryptographic Protocols Mechanization Software Products Electricity Automation Deployed Applications Data & knowledge

Financial markets: Partisia • Auctions (eg sugar beets) Source: Bogetoft, Christensen, Damgard, Geisler, Jakobsen, Krøigaard, Nielsen, Pagter, Schwartzbach, and Toft, Secure Multiparty Computation Goes Live

Financial markets: Partisia • Auctions (eg sugar beets) • Market clearinghouse – Match incoming orders – Compare with price signals from realized trades Source: Archer, Bogdanov, Lindell, Kamm, Nielsen, Pagter, Smart, and Wright, From Keys to Databases – Real-World Applications of Secure MPC

Financial markets: Partisia • Auctions (eg sugar beets) • Market clearinghouse – Match incoming orders – Compare with price signals from realized trades • Credit rating – Uses linear programming – Input: farmers of all banks Source: Damgard, Nielsen, Nordholt, and Toft, Confidential Benchmarking based on Multiparty Computation

Financial markets (1): Sharemind • ITL economic benchmarks – Collection of Estonian companies – Aggregate economic indicators: profit, # employees, salaries Source: Talviste, Practical Applications of Secure Multiparty Computation
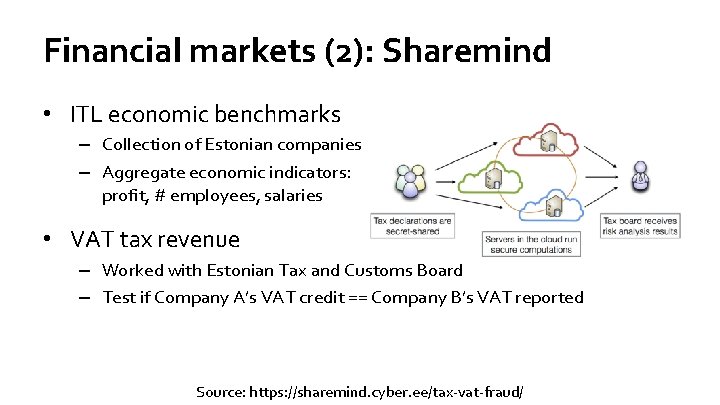
Financial markets (2): Sharemind • ITL economic benchmarks – Collection of Estonian companies – Aggregate economic indicators: profit, # employees, salaries • VAT tax revenue – Worked with Estonian Tax and Customs Board – Test if Company A’s VAT credit == Company B’s VAT reported Source: https: //sharemind. cyber. ee/tax-vat-fraud/
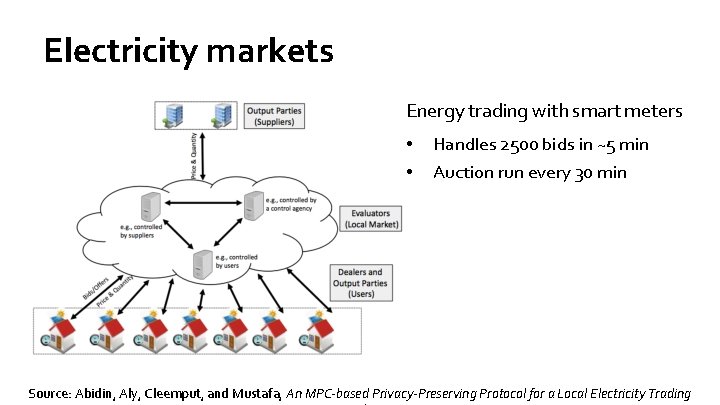
Electricity markets Energy trading with smart meters • • Handles 2500 bids in ~5 min Auction run every 30 min Source: Abidin, Aly, Cleemput, and Mustafa, An MPC-based Privacy-Preserving Protocol for a Local Electricity Trading
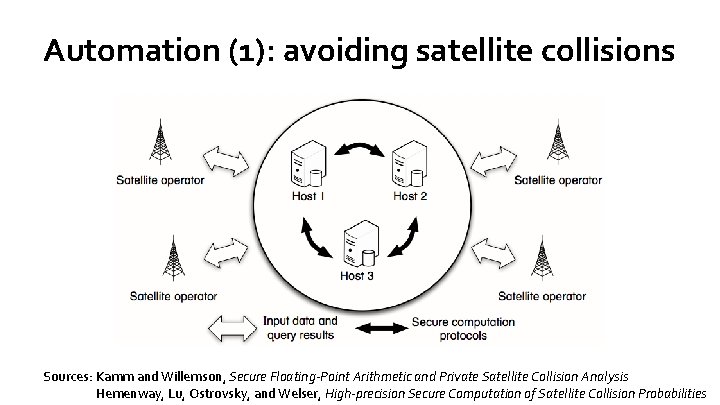
Automation (1): avoiding satellite collisions Sources: Kamm and Willemson, Secure Floating-Point Arithmetic and Private Satellite Collision Analysis Sources: Hemenway, Lu, Ostrovsky, and Welser, High-precision Secure Computation of Satellite Collision Probabilities
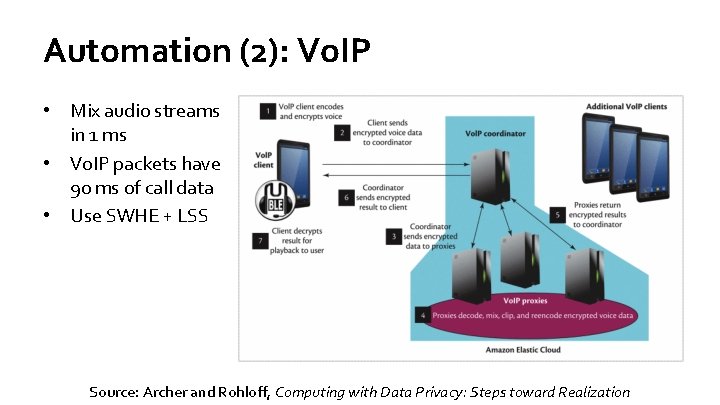
Automation (2): Vo. IP • Mix audio streams in 1 ms • Vo. IP packets have 90 ms of call data • Use SWHE + LSS Source: Archer and Rohloff, Computing with Data Privacy: Steps toward Realization
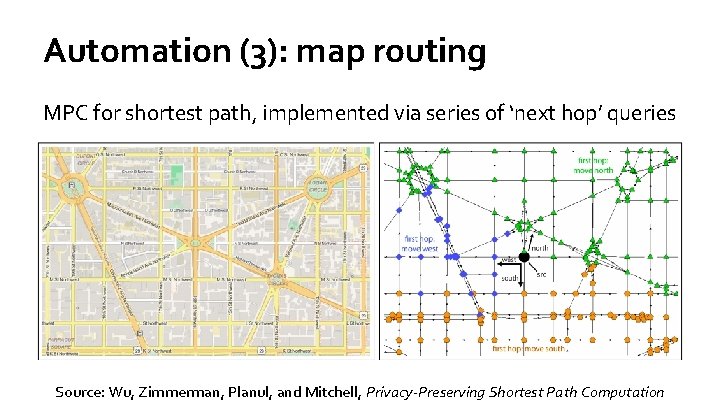
Automation (3): map routing MPC for shortest path, implemented via series of ‘next hop’ queries Source: Wu, Zimmerman, Planul, and Mitchell, Privacy-Preserving Shortest Path Computation

Automation (4): location services Source: https: //sharemind. cyber. ee/location-services/
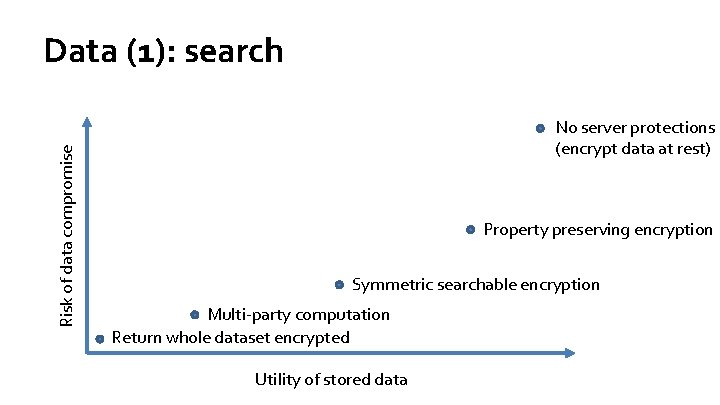
Risk of data compromise Data (1): search No server protections (encrypt data at rest) Property preserving encryption Symmetric searchable encryption Multi-party computation Return whole dataset encrypted Utility of stored data
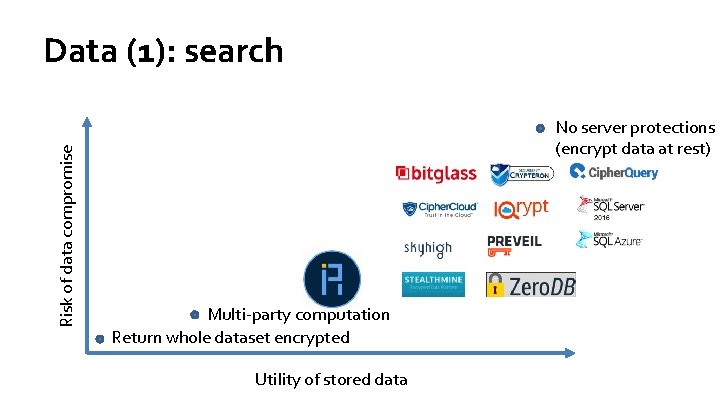
Risk of data compromise Data (1): search No server protections (encrypt data at rest) Multi-party computation Return whole dataset encrypted Utility of stored data
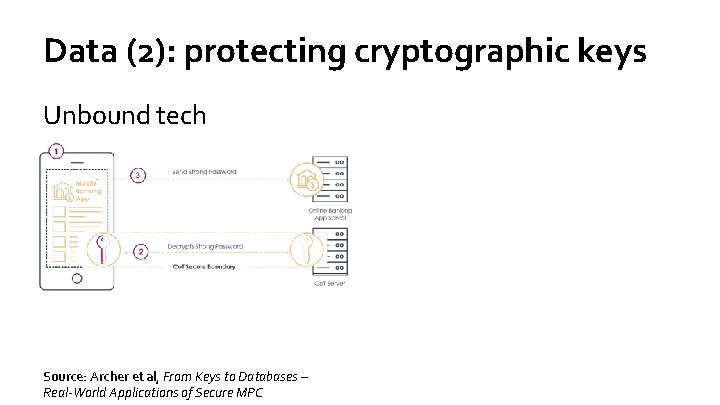
Data (2): protecting cryptographic keys Unbound tech Source: Archer et al, From Keys to Databases – Real-World Applications of Secure MPC
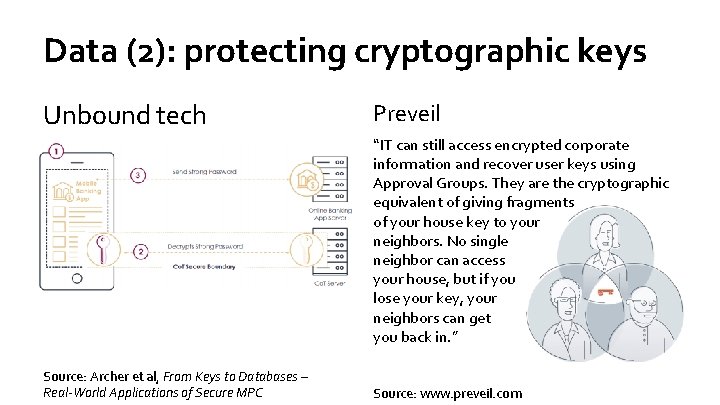
Data (2): protecting cryptographic keys Unbound tech Preveil “IT can still access encrypted corporate information and recover user keys using Approval Groups. They are the cryptographic equivalent of giving fragments of your house key to your neighbors. No single neighbor can access your house, but if you lose your key, your neighbors can get you back in. ” Source: Archer et al, From Keys to Databases – Real-World Applications of Secure MPC Source: www. preveil. com
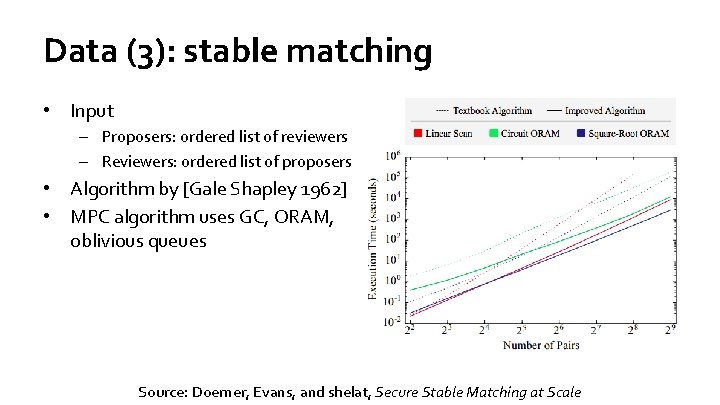
Data (3): stable matching • Input – Proposers: ordered list of reviewers – Reviewers: ordered list of proposers • Algorithm by [Gale Shapley 1962] • MPC algorithm uses GC, ORAM, oblivious queues Source: Doerner, Evans, and shelat, Secure Stable Matching at Scale
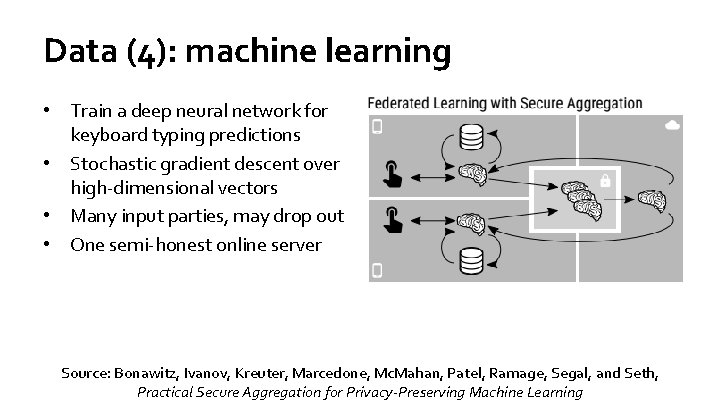
Data (4): machine learning • Train a deep neural network for keyboard typing predictions • Stochastic gradient descent over high-dimensional vectors • Many input parties, may drop out • One semi-honest online server Source: Bonawitz, Ivanov, Kreuter, Marcedone, Mc. Mahan, Patel, Ramage, Segal, and Seth, Practical Secure Aggregation for Privacy-Preserving Machine Learning
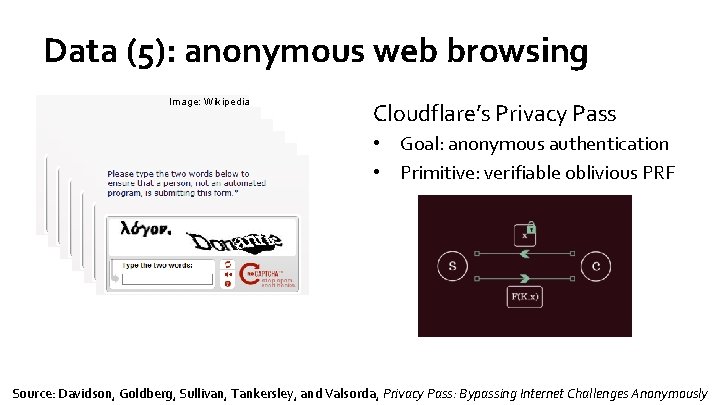
Data (5): anonymous web browsing Image: Wikipedia Cloudflare’s Privacy Pass • Goal: anonymous authentication • Primitive: verifiable oblivious PRF Source: Davidson, Goldberg, Sullivan, Tankersley, and Valsorda, Privacy Pass: Bypassing Internet Challenges Anonymously
Public good (1): CRA Taulbee Survey • Measure faculty salaries in computer science departments • Input data for each department – # people at each faculty rank: full, associate, assistant, non-tenure – Min, median, mean, and max salary at each rank • Output: aggregate results at each tier Source: Feigenbaum, Pinkas, Ryger, Saint Jean, Secure Computation of Surveys

Public good (2): Wage (dis)parity

Public good (2): Wage (dis)parity Goal 3: Evaluating Success Employers agree to contribute data to a report compiled by a third party on the Compact’s success to date. Employer-level data would not be identified in the report.
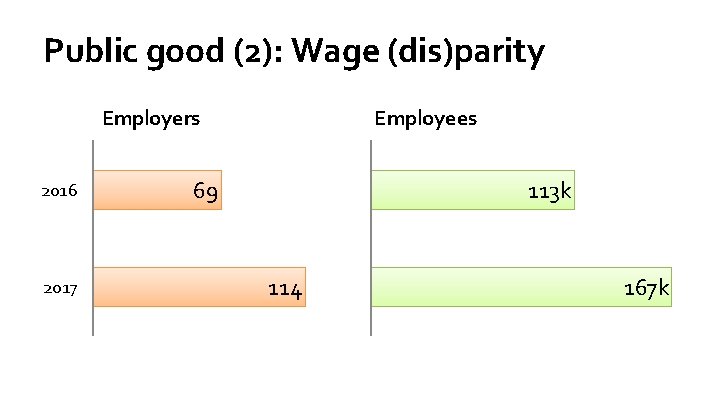
Public good (2): Wage (dis)parity Employers 2016 2017 Employees 69 113 k 114 167 k
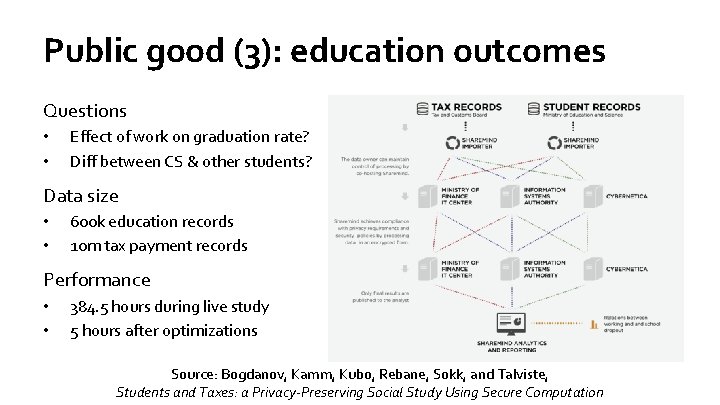
Public good (3): education outcomes Questions • • Effect of work on graduation rate? Diff between CS & other students? Data size • • 600 k education records 10 m tax payment records Performance • • 384. 5 hours during live study 5 hours after optimizations Source: Bogdanov, Kamm, Kubo, Rebane, Sokk, and Talviste, Students and Taxes: a Privacy-Preserving Social Study Using Secure Computation

“establishment of a shared service to facilitate data sharing, enable data linkage, and develop privacy enhancing techniques” “in designing, establishing, and maintaining the higher education data system, … the Commissioner shall use secure multiparty computation technologies”
- Slides: 50