A Communications Security Approach for Uncertain Times Salo



- Slides: 22

A Communications Security Approach for Uncertain Times Salo Fajer Senior Systems Engineer

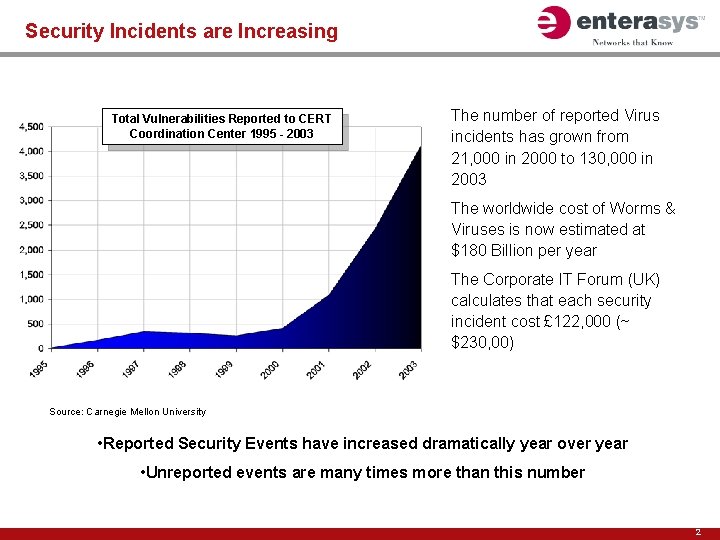
Security Incidents are Increasing Total Vulnerabilities Reported to CERT Coordination Center 1995 - 2003 The number of reported Virus incidents has grown from 21, 000 in 2000 to 130, 000 in 2003 The worldwide cost of Worms & Viruses is now estimated at $180 Billion per year The Corporate IT Forum (UK) calculates that each security incident cost £ 122, 000 (~ $230, 00) Source: Carnegie Mellon University • Reported Security Events have increased dramatically year over year • Unreported events are many times more than this number 2

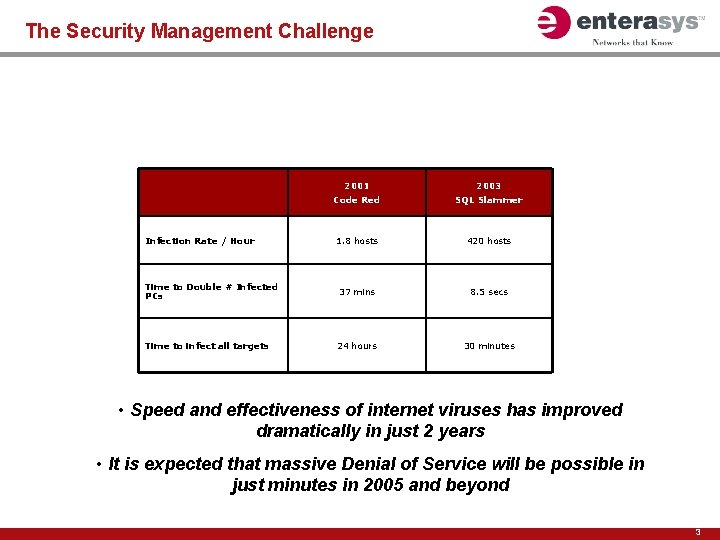
The Security Management Challenge 2001 2003 Code Red SQL Slammer 1. 8 hosts 420 hosts Time to Double # Infected PCs 37 mins 8. 5 secs Time to infect all targets 24 hours 30 minutes Infection Rate / Hour • Speed and effectiveness of internet viruses has improved dramatically in just 2 years • It is expected that massive Denial of Service will be possible in just minutes in 2005 and beyond 3

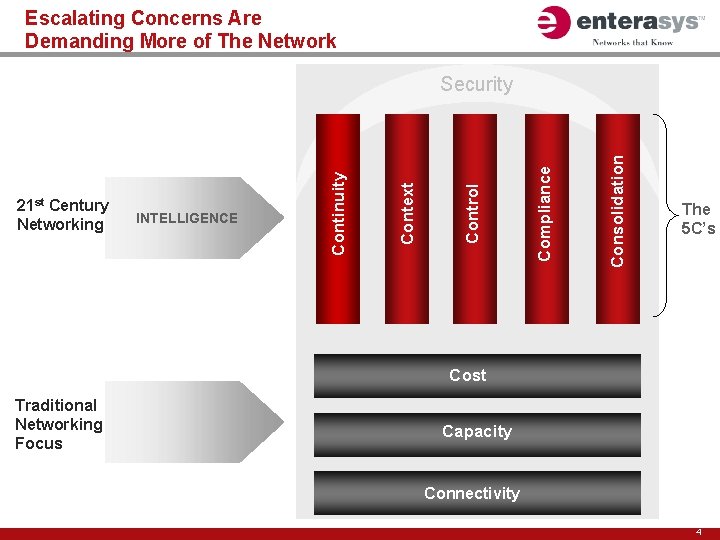
Escalating Concerns Are Demanding More of The Network Consolidation Compliance Control INTELLIGENCE Context 21 st Century Networking Continuity Security The 5 C’s Cost Traditional Networking Focus Capacity Connectivity 4

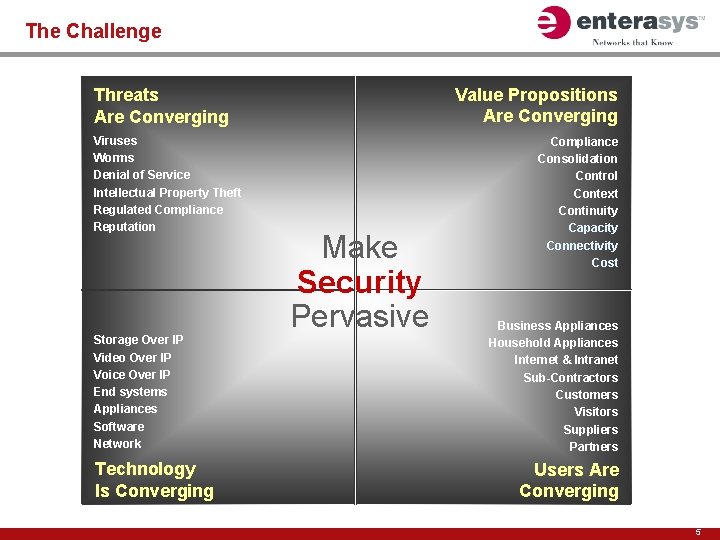
The Challenge Value Propositions Are Converging Threats Are Converging Viruses Worms Denial of Service Intellectual Property Theft Regulated Compliance Reputation Storage Over IP Video Over IP Voice Over IP End systems Appliances Software Network Technology Is Converging Make Security Pervasive Compliance Consolidation Control Context Continuity Capacity Connectivity Cost Business Appliances Household Appliances Internet & Intranet Sub-Contractors Customers Visitors Suppliers Partners Users Are Converging 5

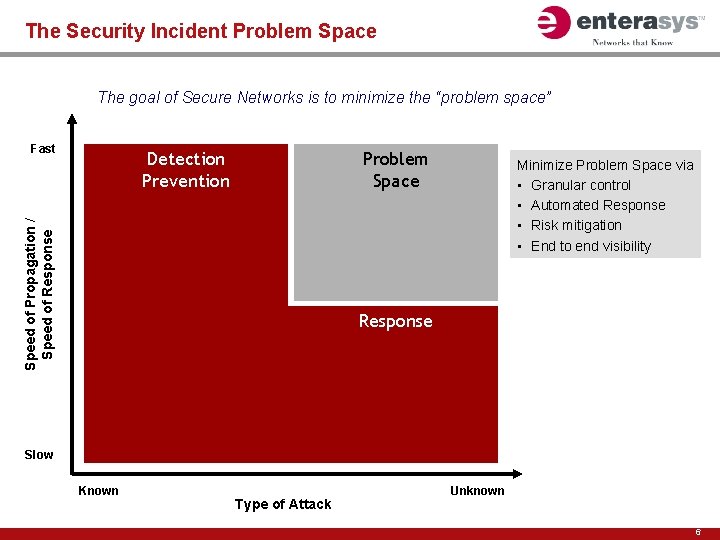
The Security Incident Problem Space The goal of Secure Networks is to minimize the “problem space” Fast Problem Space Speed of Propagation / Speed of Response Detection Prevention Minimize Problem Space via • Granular control • Automated Response • Risk mitigation • End to end visibility Response Slow Known Type of Attack Unknown 6

Secure Networks Technical Vision 7

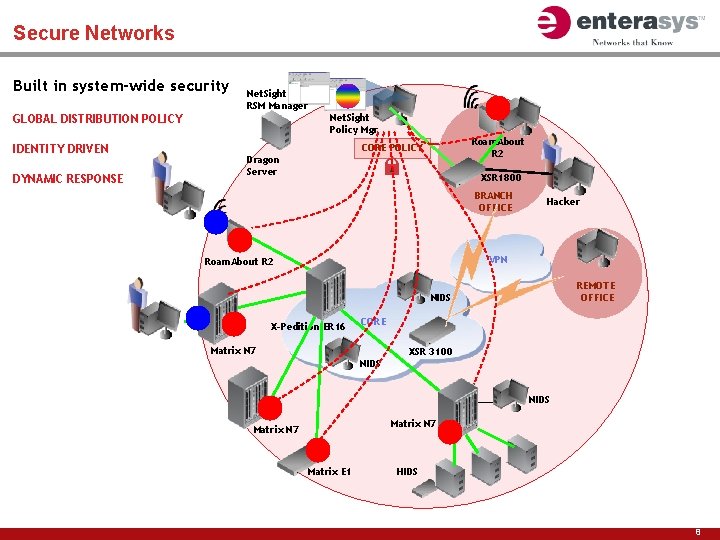
Secure Networks Built in system-wide security Net. Sight RSM Manager Net. Sight Policy Mgr GLOBAL DISTRIBUTION POLICY IDENTITY DRIVEN DYNAMIC RESPONSE Roam. About R 2 CORE POLICY Dragon Server XSR 1800 BRANCH OFFICE Hacker VPN Roam. About R 2 REMOTE OFFICE NIDS X-Pedition ER 16 CORE Matrix N 7 XSR 3100 NIDS Matrix N 7 Matrix E 1 HIDS 8

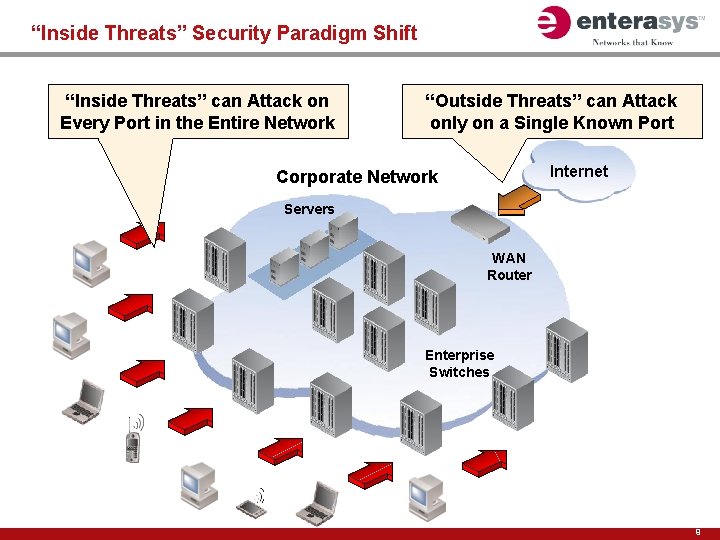
“Inside Threats” Security Paradigm Shift “Inside Threats” can Attack on Every Port in the Entire Network “Outside Threats” can Attack only on a Single Known Port Internet Corporate Network Servers WAN Router Enterprise Switches 9

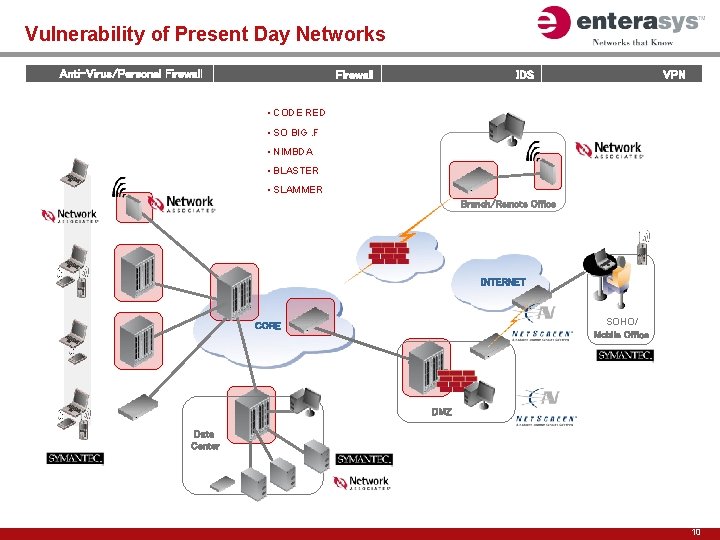
Vulnerability of Present Day Networks Anti-Virus/Personal Firewall VPN IDS • CODE RED • SO BIG. F • NIMBDA • BLASTER • SLAMMER Branch/Remote Office VPN INTERNET SOHO/ Mobile Office CORE DMZ Data Center 10

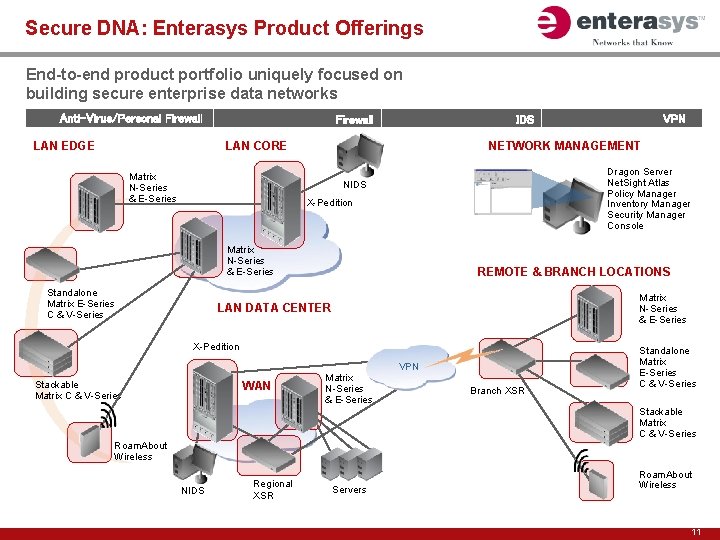
Secure DNA: Enterasys Product Offerings End-to-end product portfolio uniquely focused on building secure enterprise data networks Anti-Virus/Personal Firewall LAN EDGE Firewall LAN CORE Matrix N-Series & E-Series NETWORK MANAGEMENT Dragon Server Net. Sight Atlas Policy Manager Inventory Manager Security Manager Console NIDS X-Pedition Matrix N-Series & E-Series Standalone Matrix E-Series C & V-Series REMOTE & BRANCH LOCATIONS Matrix N-Series & E-Series LAN DATA CENTER X-Pedition Stackable Matrix C & V-Series WAN VPN IDS Matrix N-Series & E-Series VPN Branch XSR Standalone Matrix E-Series C & V-Series Stackable Matrix C & V-Series Roam. About Wireless NIDS Regional XSR Servers Roam. About Wireless 11

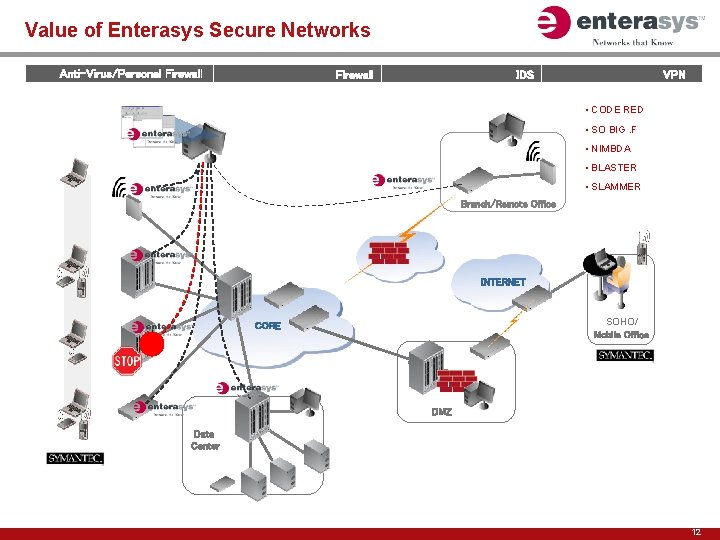
Value of Enterasys Secure Networks Anti-Virus/Personal Firewall VPN IDS • CODE RED • SO BIG. F • NIMBDA • BLASTER • SLAMMER Branch/Remote Office VPN INTERNET SOHO/ Mobile Office CORE DMZ Data Center 12

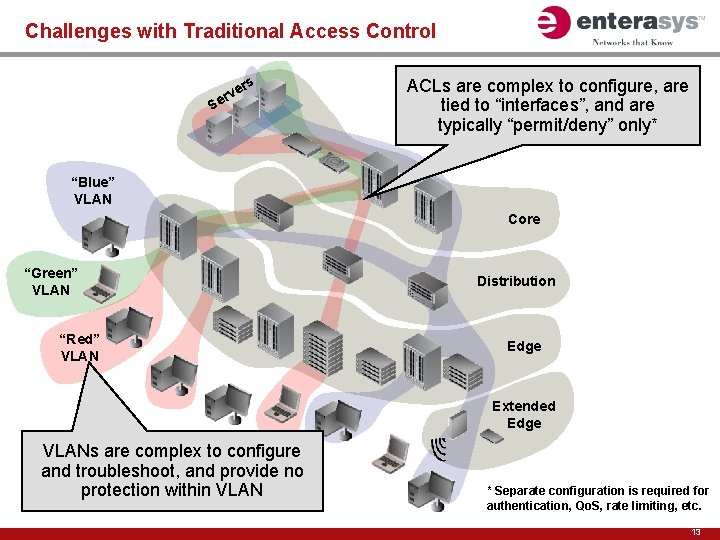
Challenges with Traditional Access Control ers v r e S ACLs are complex to configure, are tied to “interfaces”, and are typically “permit/deny” only* “Blue” VLAN Core “Green” VLAN “Red” VLAN Distribution Edge Extended Edge VLANs are complex to configure and troubleshoot, and provide no protection within VLAN * Separate configuration is required for authentication, Qo. S, rate limiting, etc. 13

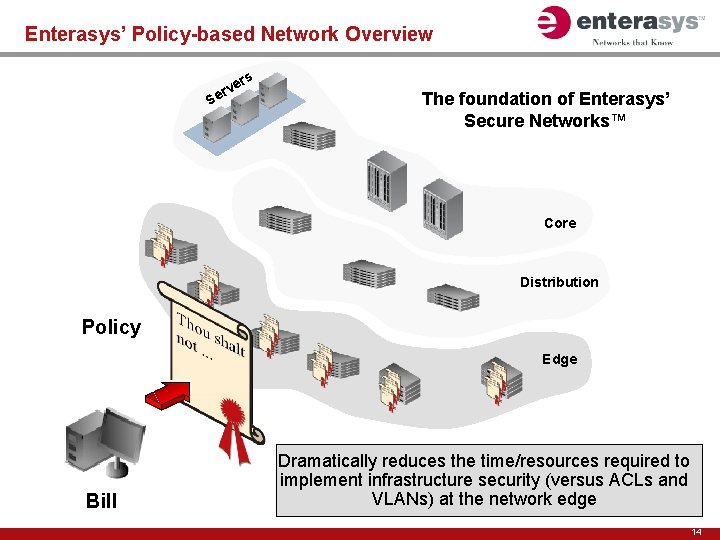
Enterasys’ Policy-based Network Overview rs e v er S The foundation of Enterasys’ Secure Networks™ Core Distribution Policy Edge Bill Dramatically reduces the time/resources required to implement infrastructure security (versus ACLs and VLANs) at the network edge 14

Secure Networks™ Solutions Acceptable Use Policy • A security policy solution for acceptable use of network resources Secure Application Provisioning • A Role-based security policy solution for business application usage Secure Guest Access • A security driven visitor networking solution Single Sign-On • A consolidated user credential solution for network and application access Dynamic Intrusion Response • An automated security response solution for identified threats to the enterprise network 15

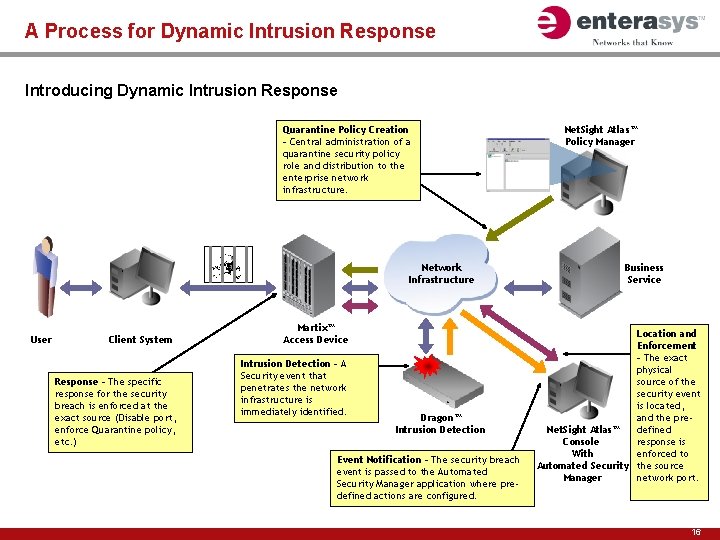
A Process for Dynamic Intrusion Response Introducing Dynamic Intrusion Response Quarantine Policy Creation – Central administration of a quarantine security policy role and distribution to the enterprise network infrastructure. Network Infrastructure User Client System Response – The specific response for the security breach is enforced at the exact source (Disable port, enforce Quarantine policy, etc. ) Martix™ Access Device Intrusion Detection – A Security event that penetrates the network infrastructure is immediately identified. Dragon™ Intrusion Detection Event Notification – The security breach event is passed to the Automated Security Manager application where predefined actions are configured. Net. Sight Atlas™ Policy Manager Business Service Location and Enforcement – The exact physical source of the security event is located, and the predefined Net. Sight Atlas™ response is Console enforced to With Automated Security the source network port. Manager 16

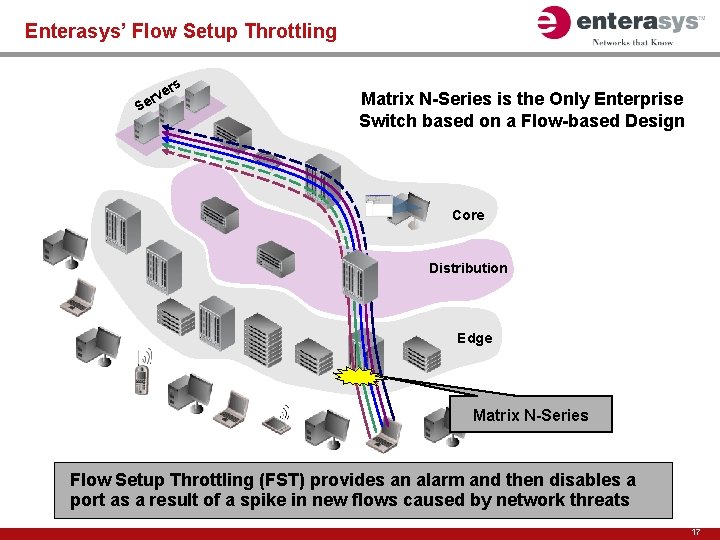
Enterasys’ Flow Setup Throttling ers v r Se Matrix N-Series is the Only Enterprise Switch based on a Flow-based Design Core Distribution Edge Matrix N-Series Flow Setup Throttling (FST) provides an alarm and then disables a port as a result of a spike in new flows caused by network threats 17

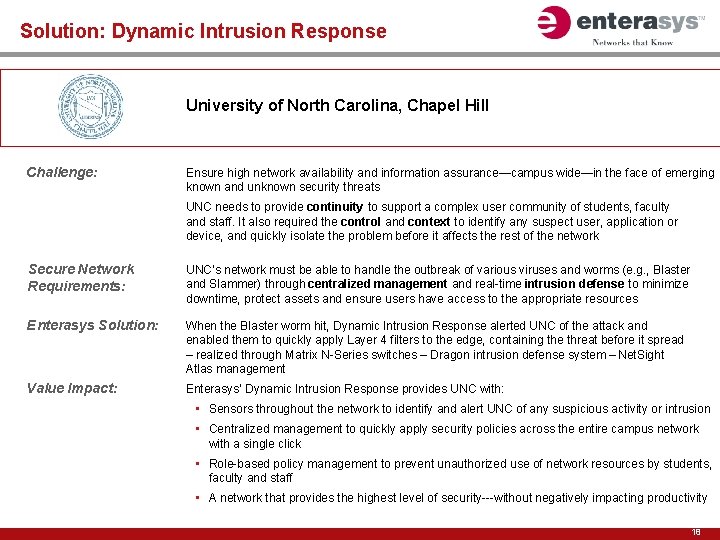
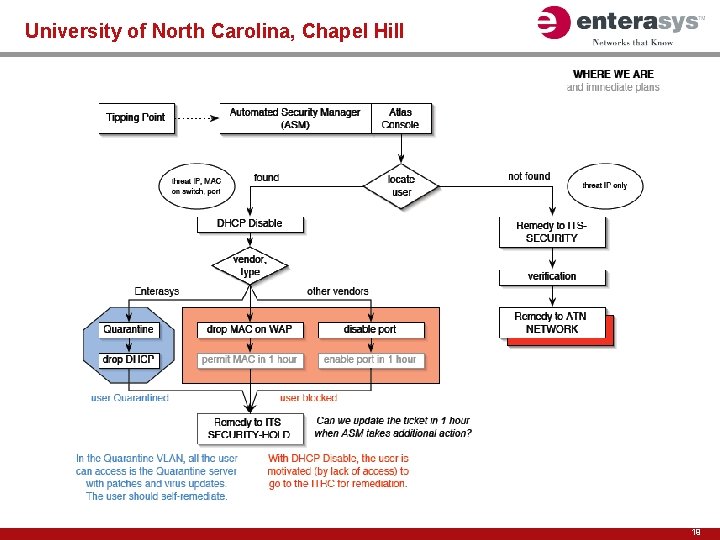
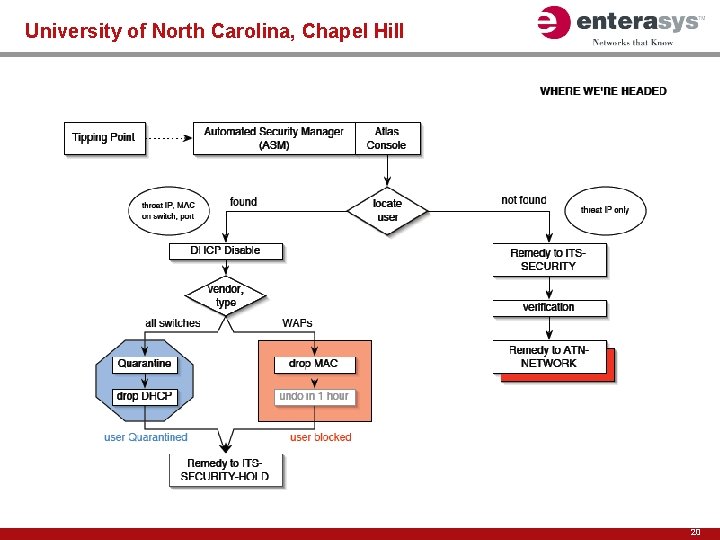
Solution: Dynamic Intrusion Response University of North Carolina, Chapel Hill Challenge: Ensure high network availability and information assurance—campus wide—in the face of emerging known and unknown security threats UNC needs to provide continuity to support a complex user community of students, faculty and staff. It also required the control and context to identify any suspect user, application or device, and quickly isolate the problem before it affects the rest of the network Secure Network Requirements: UNC’s network must be able to handle the outbreak of various viruses and worms (e. g. , Blaster and Slammer) through centralized management and real-time intrusion defense to minimize downtime, protect assets and ensure users have access to the appropriate resources Enterasys Solution: When the Blaster worm hit, Dynamic Intrusion Response alerted UNC of the attack and enabled them to quickly apply Layer 4 filters to the edge, containing the threat before it spread – realized through Matrix N-Series switches – Dragon intrusion defense system – Net. Sight Atlas management Value Impact: Enterasys’ Dynamic Intrusion Response provides UNC with: • Sensors throughout the network to identify and alert UNC of any suspicious activity or intrusion • Centralized management to quickly apply security policies across the entire campus network with a single click • Role-based policy management to prevent unauthorized use of network resources by students, faculty and staff • A network that provides the highest level of security---without negatively impacting productivity 18

University of North Carolina, Chapel Hill 19

University of North Carolina, Chapel Hill 20

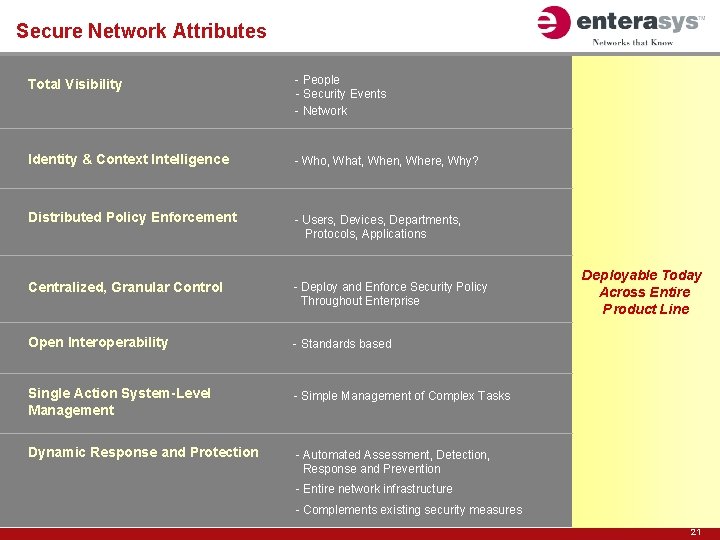
Secure Network Attributes Total Visibility - People - Security Events - Network Identity & Context Intelligence - Who, What, When, Where, Why? Distributed Policy Enforcement - Users, Devices, Departments, Protocols, Applications Centralized, Granular Control - Deploy and Enforce Security Policy Throughout Enterprise Open Interoperability - Standards based Single Action System-Level Management - Simple Management of Complex Tasks Dynamic Response and Protection - Automated Assessment, Detection, Response and Prevention Deployable Today Across Entire Product Line - Entire network infrastructure - Complements existing security measures 21

Thank You