Wydzia Elektroniki i Technik Informacyjnych SEMINARY PRESENTATION PROCEDURE

















- Slides: 32

Wydział Elektroniki i Technik Informacyjnych SEMINARY PRESENTATION PROCEDURE OF FIREWALL TESTING AND EVALUATION SUPERVISOR ZBIGNIEW A. KOTULSKI, PH. D. , D. SC.

Agenda Problem definition Goals of work Test environmet description Test structure Results examples Problems Conclusions

Problem definition Not exist any form of such procedure (existence of RFC 3511 but it limits only to pure firewall evaluation), IP throughput Concurrent TCP Connection Capacity Maximum TCP Connection Establishment Rate Maximum TCP Connection Tear Down Rate Denial Of Service Handling HTTP Transfer Rate Maximum HTTP Transaction Rate Illegal Traffic Handling IP Fragmentation Handling Latency

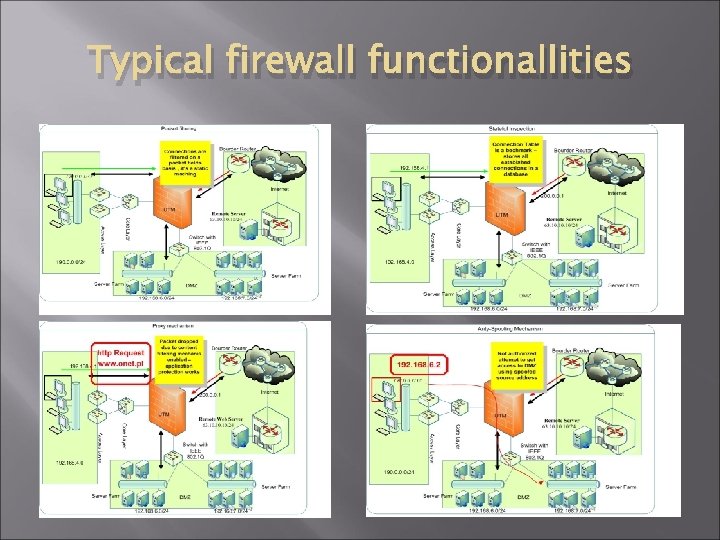
Typical firewall functionallities

Extension introduced by UTM

Problem definition There are speculations not facts, Each vendor convincing about it’s superiority. „Check Point Network Security Solutions are the market-leading choice for securing the network infrastructure” source www. checkpoint. com „Whatever the size, location and function of the network, Juniper Networks solutions deliver secure, best-in-class performance. ” source www. juniper. net

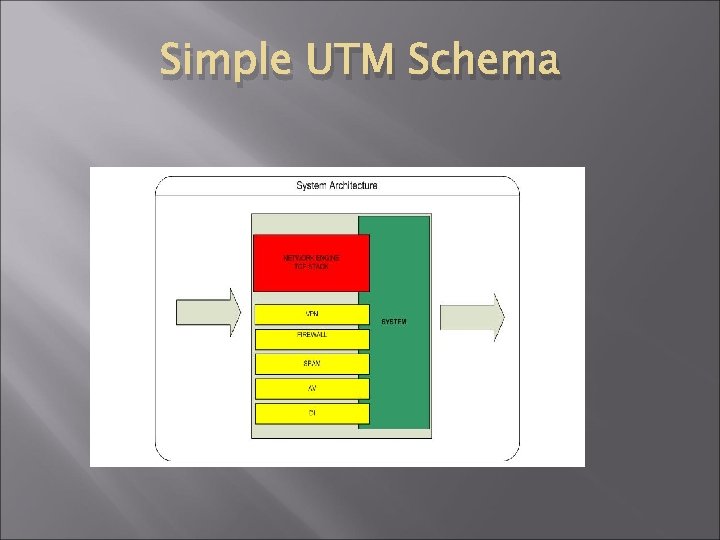
Simple UTM Schema

Goals of the work 1. Analysis of contemporary UTM market in seek of optimal technologies and solutions, I defined following ways to fulfill this aim: analysis of architecture of such kind of devices , comparison particular functionalities with similar standalone appliances , analysis of the market in seek for devices which comply requirements of the highest security requirements ,

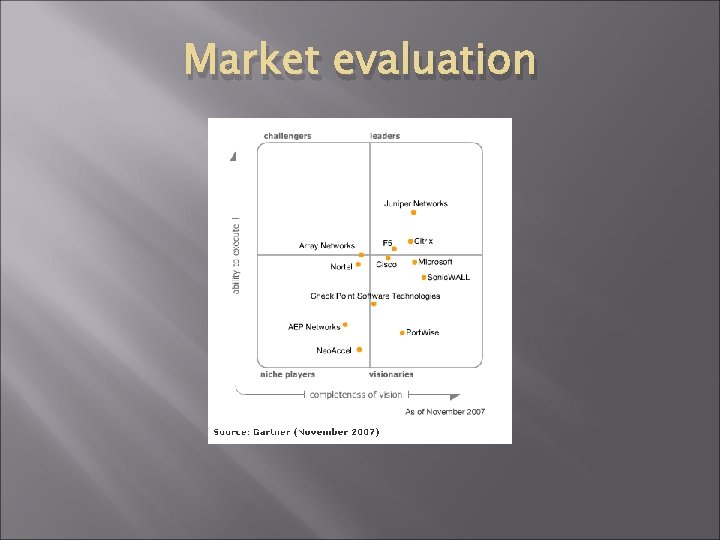
Market evaluation

Goals of the work 2. Evaluation of previously selected devices in specially prepared environment: I defined following steps to fulfill this aim: initial configuration of devices for further tests, preparation of test scenarios seek of auxiliary software needed to fulfill scenarios requirements, preparation of own supplementary scripts, analysis of received results,

Goals of the work 3. Preparation of procedure on a basis of results analysis obtained from previously selected device evaluation. TC 1. 1 TC 1. 2 TC 1. 3 TC 1. 4 TC 2. 1 TC 2. 2 TC 2. 3 - audit sub-procedure, - pen test sub-procedure, - attack resistance sub-procedure, - system scanning sub-procedure, - virtual private network mechanism evaluation subprocedure, - antivirus, spam , content filtering mechanism evaluation sub-procedure, - rule set evaluation sub-procedure.

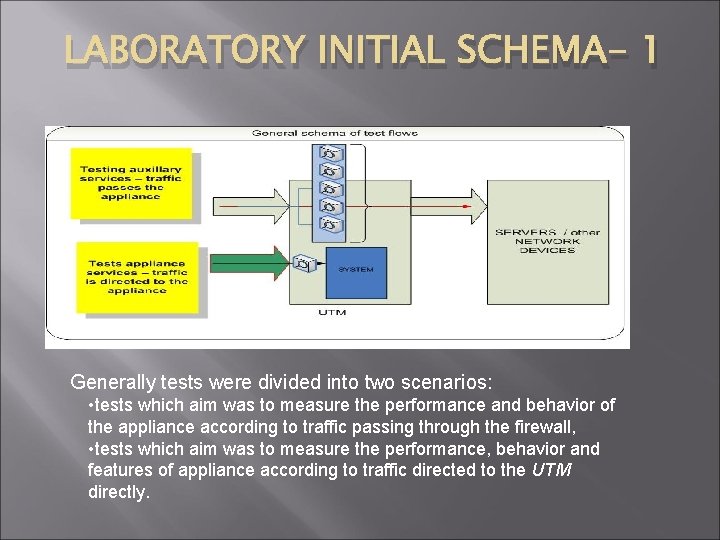
LABORATORY INITIAL SCHEMA- 1 Generally tests were divided into two scenarios: • tests which aim was to measure the performance and behavior of the appliance according to traffic passing through the firewall, • tests which aim was to measure the performance, behavior and features of appliance according to traffic directed to the UTM directly.

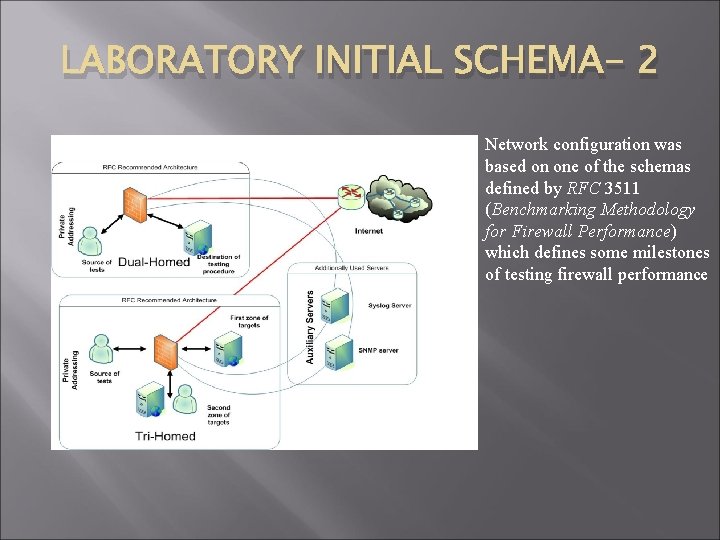
LABORATORY INITIAL SCHEMA- 2 Network configuration was based on one of the schemas defined by RFC 3511 (Benchmarking Methodology for Firewall Performance) which defines some milestones of testing firewall performance

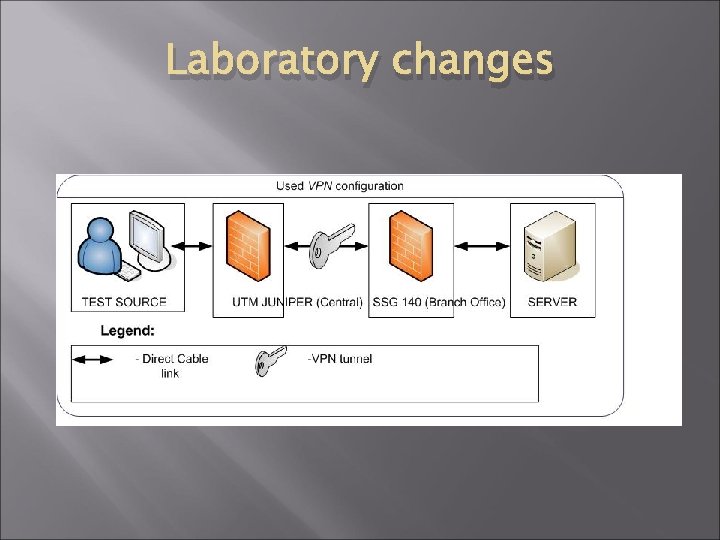
Laboratory changes

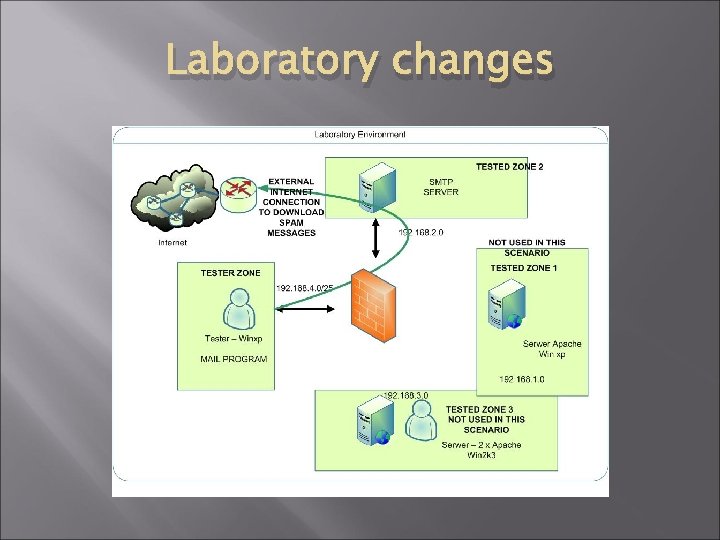
Laboratory changes

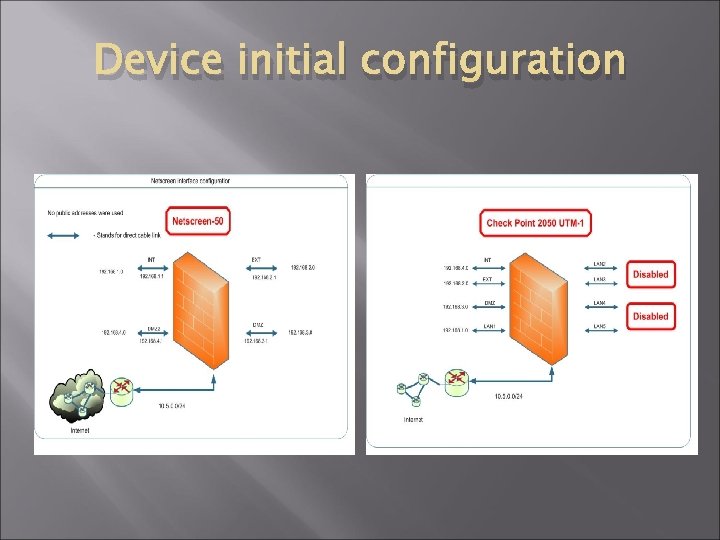
Device initial configuration

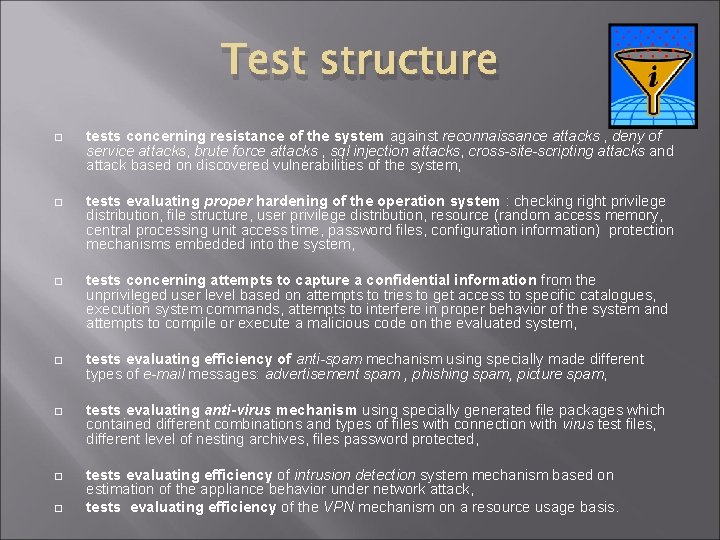
Test structure tests concerning resistance of the system against reconnaissance attacks , deny of service attacks, brute force attacks , sql injection attacks, cross-site-scripting attacks and attack based on discovered vulnerabilities of the system, tests evaluating proper hardening of the operation system : checking right privilege distribution, file structure, user privilege distribution, resource (random access memory, central processing unit access time, password files, configuration information) protection mechanisms embedded into the system, tests concerning attempts to capture a confidential information from the unprivileged user level based on attempts to tries to get access to specific catalogues, execution system commands, attempts to interfere in proper behavior of the system and attempts to compile or execute a malicious code on the evaluated system, tests evaluating efficiency of anti-spam mechanism using specially made different types of e-mail messages: advertisement spam , phishing spam, picture spam, tests evaluating anti-virus mechanism using specially generated file packages which contained different combinations and types of files with connection with virus test files, different level of nesting archives, files password protected, tests evaluating efficiency of intrusion detection system mechanism based on estimation of the appliance behavior under network attack, tests evaluating efficiency of the VPN mechanism on a resource usage basis.

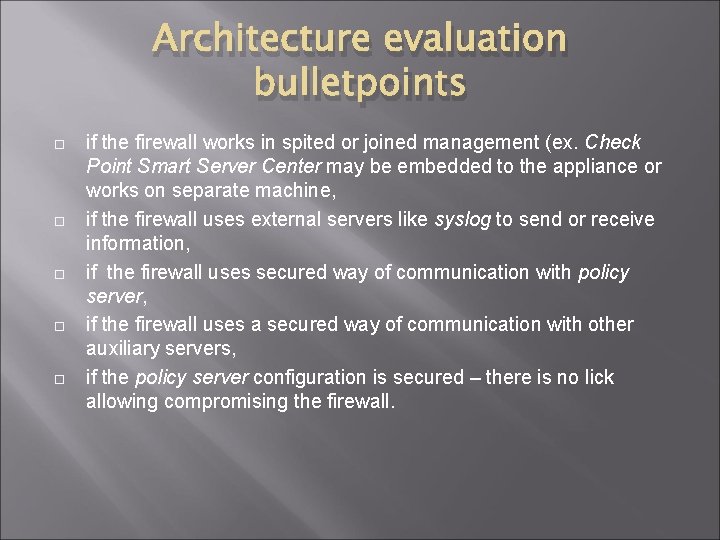
Architecture evaluation bulletpoints if the firewall works in spited or joined management (ex. Check Point Smart Server Center may be embedded to the appliance or works on separate machine, if the firewall uses external servers like syslog to send or receive information, if the firewall uses secured way of communication with policy server, if the firewall uses a secured way of communication with other auxiliary servers, if the policy server configuration is secured – there is no lick allowing compromising the firewall.

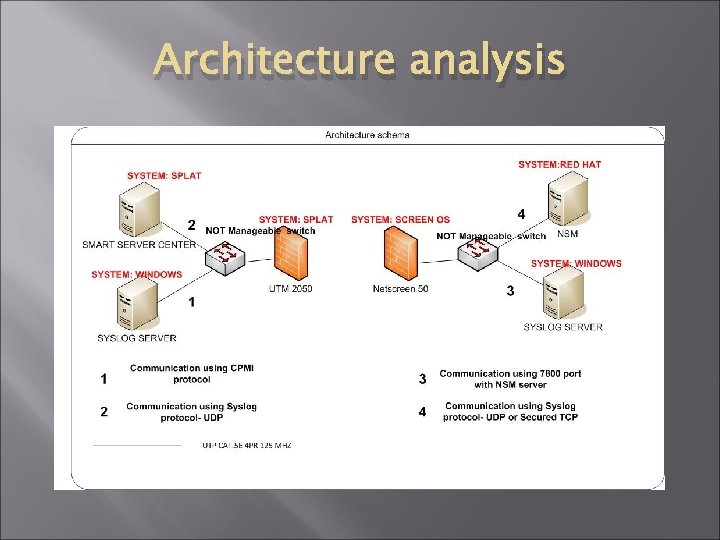
Architecture analysis

Rule set validation pre-assimptions what (if defined ) is the number of rules recommended, what is the order in which the firewall proceeds the rules set ( to the first match ex. Checkpoint , to group match ex. ISA server, if the rules ale proceed in groups (zones ) ex. Juniper, if any particular actions are prioritized over the others, how the additional actions are impacting the performance (ex. counting in Check Point firewall rules can significantly decrease the performance), how the traffic is spread over the rule set – if the most used are placed on the start of firewall proceed path, if the rule set is optimized – do not exist divided rules which can spitted together, if there do not exist implied rules which do not officially appear in the rule set but filter the traffic additionally, if there exist firewall protecting hidden rule set filtrating the traffic directed to firewall itself

Auditung of the system name of the system, analysis of how the space of the disk is distributed through the partitions, analysis of the starting scripts, analysis of services started from xinetd. conf, users and groups defined in the system, analysis of unmask value parameter, analysis of shells in the system, configuration of PATH variable configuration, analysis of restrictions set in PAM module, analysis of system logging module (if exist), analysis of system auditing module (if exist),

Auditing of the system analysis of system privileges access to catalogues (generally files with bit SUID enabled), analysis of privileges to most valuable to the system files, analysis of privileges of accessing the cron’s files, analysis of processes working in the system, analysis of network configuration.

Spam files examples Goodday Sir/Madam, On Sunday December 26 th 2004 at about 9: 00 am, the world witnessed a natural disaster. A quake measuring 9. 0 on the ritcher scale occurred at the bottom of the Indian Ocean close to the Island of Sumatra, North East Indonesia. Resulting Tsunamis from the quake caused destruction of lives and properties never before experienced in modern history. Reports say this is the strongest quake in 40 years with its energy equal to 9, 500 Hiroshima bombs. So far 155, 000 people have been officially reported dead, of this figure 27 are Britons, 79, 900 Indonesians and 27, 268 from Sri Lanka. India recorded over 6, 000 dead and Thailand over 10, 000. The Swedish Prime Minister says about 1, 000 Swedish tourists have died so far, and the death toll is still on the increase. The British public has so far donated 21 million pounds, with 10 million raised overnight. The British government has also pledged 15 million pounds; the EU has pledged $4 m dollars and other International organizations pledging sums of money. Your financial contribution towards getting medical supplies and food {which are the most important needs} now is highly solicited. We alongside over 30 emergency relief agencies irrespective of race or religion are working in conjunction with the W. H. O to avert an epidemic of cholera and other water borne diseases. Presently, over 5 million people in South Asia are without food or water. The UN health agency requires over 68 million pounds to forestall an outbreak of disease in a couple of days, which could be an even bigger disaster. Please send your Contributions/Donations no matter how small, via WESTERN UNION MONEY TRANSFER TO Name: GREGORY OVIENRIA Address: Netherland.

Spam files examples

Test procedure example

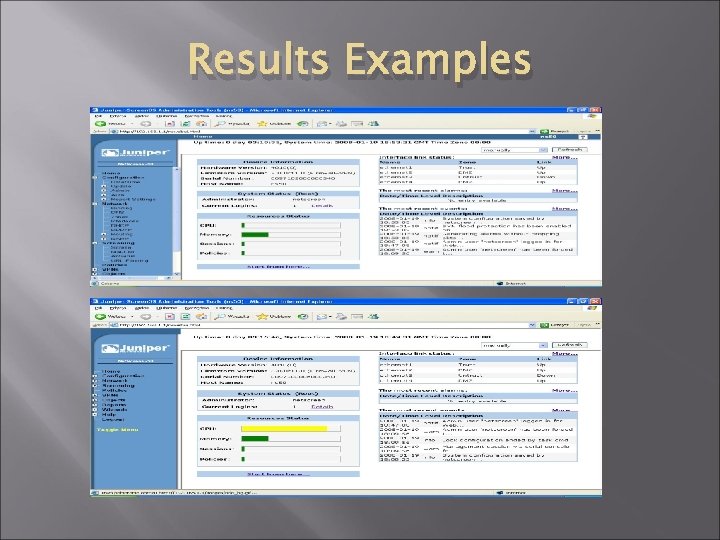
Results Examples

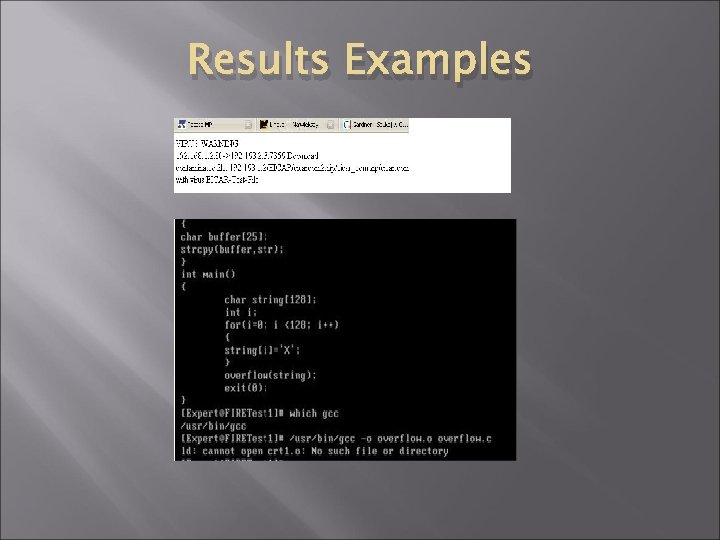
Results Examples

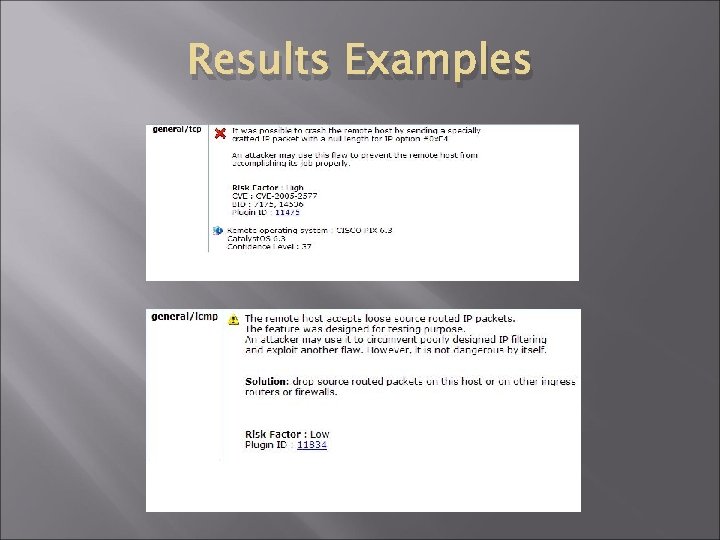
Results Examples

Problems Difficulty in hiring needed equipment Difficulty in getting evaluation licenses Problems with suiting proper test software Problems with lab establishment 1)Netscreen has a predefined labels - functions binded to interfaces and I needed 4 so I had to change the default function of one of the interfaces to make possible syslog mechanism to work 2) device didn't accepted the licenses - upgrade of os was needed 3) device didn't want to load database of DI

Conclusions Obtained: Market evaluation Test software found or created Benchamark lab environment created and tested Benchamark scenarios created Benchamark results obtained Advanced methodology created Clear and precise procedure created

Questions

THANK YOU.
 Katedra elektroniki agh
Katedra elektroniki agh Katedra elektroniki agh
Katedra elektroniki agh Kurs elektroniki
Kurs elektroniki Katedra elektroniki agh
Katedra elektroniki agh Himalayan graduate school of theology
Himalayan graduate school of theology Institute enrollment lds
Institute enrollment lds Seminary without bachelors
Seminary without bachelors Trinity theological seminary of south florida
Trinity theological seminary of south florida Mints international seminary
Mints international seminary Lds seminary attendance requirements
Lds seminary attendance requirements Trinity theological seminary of south florida
Trinity theological seminary of south florida President of dallas theological seminary
President of dallas theological seminary Eric d richards
Eric d richards Ofakim seminary
Ofakim seminary Bangkok bible seminary
Bangkok bible seminary Technik ochrony środowiska
Technik ochrony środowiska Rodzaje technik plastycznych
Rodzaje technik plastycznych Technika graficzna druku wypukłego
Technika graficzna druku wypukłego Grimm aerosol technik
Grimm aerosol technik Langstreckenschwimmen technik
Langstreckenschwimmen technik Halder norm technik
Halder norm technik Technik dentystyczny forum
Technik dentystyczny forum Technik cyfrowych procesów graficznych praca
Technik cyfrowych procesów graficznych praca Columbo technik psychologie
Columbo technik psychologie Czym zajmuje się technik ekonomista
Czym zajmuje się technik ekonomista Efbs polizei
Efbs polizei Metaplan tematy
Metaplan tematy Technik stewardessa
Technik stewardessa Grubo nałożona na obrazie jasna farba
Grubo nałożona na obrazie jasna farba Czym zajmuje sie technik pojazdów samochodowych
Czym zajmuje sie technik pojazdów samochodowych Fuchs technik innichen
Fuchs technik innichen 5 spalten technik
5 spalten technik Vermittlungskonzepte sport
Vermittlungskonzepte sport
























































