Wireless Security 802 11 RFID WTLS SMU CSE


























- Slides: 35

Wireless Security 802. 11, RFID, WTLS SMU CSE 5349/7349

802. 11 • 802. 11 a, b, … • Components – Wireless station • A desktop or laptop PC or PDA with a wireless NIC. – Access point • A bridge between wireless and wired networks – Radio – Wired network interface (usually 802. 3) – Bridging software • Aggregates access for multiple wireless stations to wired network. SMU CSE 5349/7349

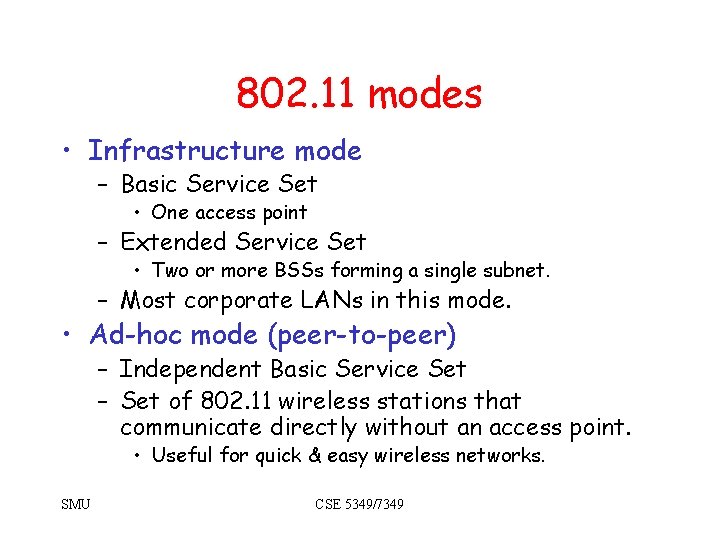
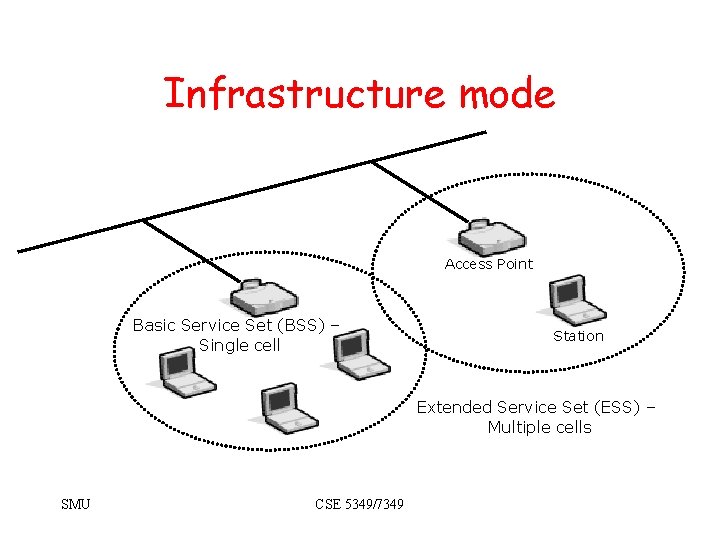
802. 11 modes • Infrastructure mode – Basic Service Set • One access point – Extended Service Set • Two or more BSSs forming a single subnet. – Most corporate LANs in this mode. • Ad-hoc mode (peer-to-peer) – Independent Basic Service Set – Set of 802. 11 wireless stations that communicate directly without an access point. • Useful for quick & easy wireless networks. SMU CSE 5349/7349

Infrastructure mode Access Point Basic Service Set (BSS) – Single cell Station Extended Service Set (ESS) – Multiple cells SMU CSE 5349/7349

Ad-hoc mode Independent Basic Service Set (IBSS) SMU CSE 5349/7349

Open System Authentication • Service Set Identifier (SSID) • Station must specify SSID to Access Point when requesting association. • Multiple APs with same SSID form Extended Service Set. • APs broadcast their SSID. SMU CSE 5349/7349

MAC Address Locking • Access points have Access Control Lists (ACL). • ACL is list of allowed MAC addresses. – E. g. Allow access to: • 00: 01: 42: 0 E: 12: 1 F • 00: 01: 42: F 1: 72: AE • 00: 01: 42: 4 F: E 2: 01 • But MAC addresses are sniffable and spoofable. • Access Point ACLs are ineffective control. SMU CSE 5349/7349

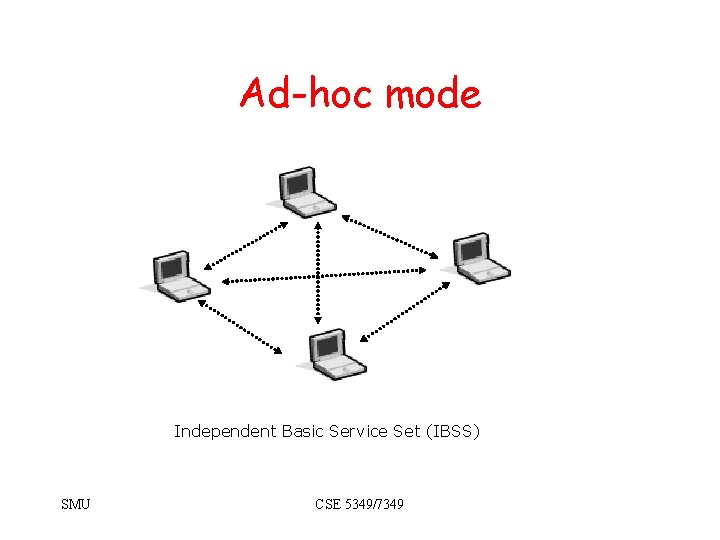
Interception Range Station outside building perimeter. tres 100 me Basic Service Set (BSS) – Single cell SMU CSE 5349/7349

Interception • Wireless LAN uses radio signal. • Not limited to physical building. • Signal is weakened by: – Walls – Floors – Interference • Directional antenna allows interception over longer distances. SMU CSE 5349/7349

Directional Antenna • Directional antenna provides focused reception. • D-I-Y plans available. – Aluminium cake tin. – 11 Mbps at 750 meters. – http: //www. saunalahti. fi/~elepal/antennie. html SMU CSE 5349/7349

802. 11 b Security Services • Two security services provided: – Authentication • Shared Key Authentication – Encryption • Wired Equivalence Privacy SMU CSE 5349/7349

Wired Equivalence Privacy • Shared key between – Stations. – An Access Point. • Extended Service Set – All Access Points will have same shared key. • No key management – Shared key entered manually into • Stations • Access points • Key management a problem in large wireless LANs SMU CSE 5349/7349

RC 4 Refresher: – RC 4 uses key sizes from 1 bit to 2048 bits. – RC 4 generates a stream of pseudo random bits • XORed with plaintext to create ciphertext. SMU CSE 5349/7349

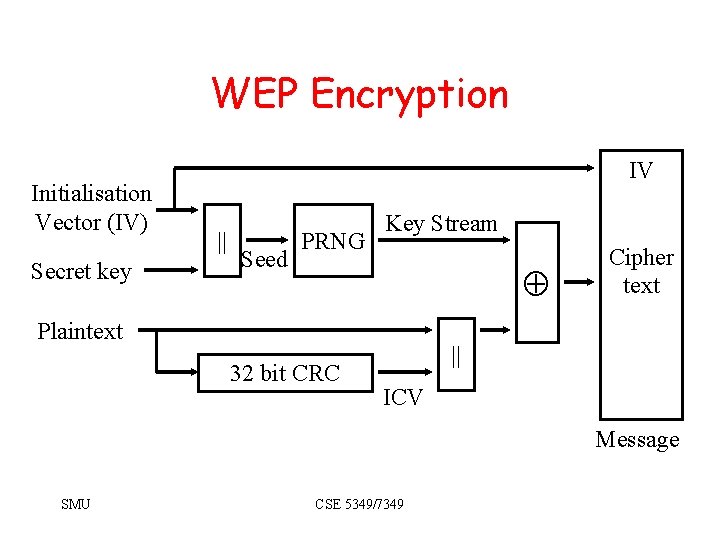
WEP – Sending • Compute Integrity Check Vector (ICV). – Provides integrity – 32 bit Cyclic Redundancy Check. – Appended to message to create plaintext. • Plaintext encrypted via RC 4 – Provides confidentiality. – Plaintext XORed with long key stream of pseudo random bits. – Key stream is function of • 40 -bit secret key • 24 bit initialisation vector (more later) • Ciphertext is transmitted. SMU CSE 5349/7349

Initialization Vector • IV must be different for every message transmitted. • 802. 11 standard doesn’t specify how IV is calculated. • Wireless cards use several methods – Some use a simple ascending counter for each message. – Some switch between alternate ascending and descending counters. – Some use a pseudo random IV generator. SMU CSE 5349/7349

WEP Encryption Initialisation Vector (IV) Secret key IV || Seed PRNG Key Stream Plaintext 32 bit CRC Cipher text || ICV Message SMU CSE 5349/7349

WEP – Receiving • Ciphertext is received. • Ciphertext decrypted via RC 4 – Ciphertext XORed with long key stream of pseudo random bits. • Check ICV – Separate ICV from message. – Compute ICV for message – Compare with received ICV SMU CSE 5349/7349

Shared Key Authentication • When station requests association with Access Point – AP sends random number to station – Station encrypts random number • Uses RC 4, 40 bit shared secret key & 24 bit IV – Encrypted random number sent to AP – AP decrypts received message • Uses RC 4, 40 bit shared secret key & 24 bit IV – AP compares decrypted random number to transmitted random number SMU CSE 5349/7349

Security - Summary • Shared secret key required for: – Associating with an access point. – Sending data. – Receiving data. • Messages are encrypted. – Confidentiality. • Messages have checksum. – Integrity. • But SSID still broadcast in clear. SMU CSE 5349/7349

Security Attacks • Targeted network segment • Malicious association • Interference Jamming • Attack against MAC authentication • Vulnerability through ad hoc mode – Free Internet – Malicious use of identity – Access to other network resources – Host AP – Easy to jam the signals – DOS through repeated, albeit unsuccessful access requests (management messages are not authenticated. Egs. Wlan-jack) – Do. S through disassociation commands – Interference with other appliances (2. 4 G spectrum) SMU – Can spoof MAC with loadable firmware – Defense? CSE 5349/7349

802. 11 Insecurities • Authentication – two options – Open – Shared-key more insecure? • Static key management – If one device is compromised/stolen, everyone should change the key – Hard to detect • WEP keys – 40 or 128 can be cracked in less than 15 minutes SMU CSE 5349/7349

IV Collision attack • If 24 bit IV is an ascending counter, – If Access Point transmits at 11 Mbps, IVs exhausted in roughly 5 hours. • Passive attack: – Attacker collects all traffic – Attacker could collect two encrypted messages: • If two messages EM 1, EM 2, both encrypted with same key stream ( same key and same IV) • EM 1 EM 2 = M 1 M 2 • Effectively removes the key stream • Can now try to derive plaintext messages SMU CSE 5349/7349

Limited WEP keys • Some vendors allow limited WEP keys – User types in a password – WEP key is generated from passphrase – Passphrases creates only 21 bits of 40 bit key. • Reduces key strength to 21 bits = 2, 097, 152 • Remaining 19 bits are predictable. • 21 bit key can be brute forced in minutes. SMU CSE 5349/7349

Brute Force Key Attack • Capture ciphertext. – IV is included in message. • Search all 240 possible secret keys. – 1, 099, 511, 627, 776 keys – ~200 days on a modern laptop • Find which key decrypts ciphertext to plaintext. SMU CSE 5349/7349

128 bit WEP • Vendors have extended WEP to 128 bit keys. – 104 bit secret key. – 24 bit IV. • Brute force takes 10^19 years for 104 -bit key. • Effectively safeguards against brute force attacks. SMU CSE 5349/7349

IV weakness • WEP exposes part of PRNG input. – IV is transmitted with message. • Initial keystream can be derived – TCP/IP has fixed structure at start of packets • Attack is practical. • Passive attack. – Non-intrusive. – No warning. SMU CSE 5349/7349

Wepcrack • First tool to demonstrate attack using IV weakness. – Open source • Three components – Weaker IV generator. – Search sniffer output for weaker IVs & record 1 st byte. – Cracker to combine weaker IVs and selected 1 st bytes. SMU CSE 5349/7349

Airsnort • Automated tool – – – SMU Does it all! Sniffs Searches for weaker IVs Records encrypted data Until key is derived. CSE 5349/7349

Safeguards • • Security Policy & Architecture Design Treat as untrusted LAN Discover unauthorised use Access point audits Station protection Access point location Antenna design SMU CSE 5349/7349

Wireless as Untrusted LAN • Treat wireless as untrusted. – Similar to Internet. • Firewall between WLAN and Backbone. • Extra authentication required. • Intrusion Detection – WLAN / Backbone junction. • Vulnerability assessments SMU CSE 5349/7349

Discover Unauthorised Use • Search for unauthorised access points or ad-hoc networks • Port scanning – For unknown SNMP agents. – For unknown web or telnet interfaces. • Warwalking! – – SMU Sniff 802. 11 packets Identify IP addresses Detect signal strength May sniff your neighbours… CSE 5349/7349

Location of AP • Ideally locate access points – In centre of buildings. • Try to avoid access points – By windows – On external walls – Line of sight to outside • Use directional antenna to “point” radio signal. SMU CSE 5349/7349

IPSec VPN • IPSec client placed on every PC connected to the WLAN • Filters to prevent traffic from reaching anywhere other than VPN gateway and DHCP/DNS server • Can combine user authentication also SMU CSE 5349/7349

IEEE 802. 11 i • A new framework for wireless security – Centralized authentication – Dynamic key distribution – Will apply to 802. 11 a, b & g • Uses 802. 1 X as authentication framework – Extensible Authentication Protocol (EAP), RFC 2284 (EAP -TLS & LEAP) – Mutual authentication between client and authentication server (RADIUS) – Encryption keys dynamically derived after authentication – Session timeout triggers reauthentication SMU CSE 5349/7349

802. 11 i – Encryption Enhancements • Temporal Key Integrity Protocol (TKIP) – – RC 4 still used Per-packet keys Hash functions for MIC instead of CRC 32 Only firmware upgrade required • AES – AES cipher replaces RC 4 – Will require new hardware SMU CSE 5349/7349