Wireless Networks Lecture 40 High Rate Wireless Personal






- Slides: 26

Wireless Networks Ü Lecture 40 Ü High Rate Wireless Personal Area Networks (WPAN) Ü Dr. Ghalib A. Shah 1

Outlines Ü Ü Ü IP Over Bluetooth Security WPAN Standards IEEE 802. 15. 3 Overview 802. 15. 3 ► Topology ► Coordination • • • ► ► Starting a Piconet Handing over control of piconet Creating child piconet Ending a Piconent Association/Disassociation Medium Access (Superframe) Channel Time Management Power management MAC Frame format 2

Last Lecture Ü Ü Ü Ü Ü Bluetooth introduction Technical features Access technique Bluetooth topology/scenario Specifications Architecture Core Protocols Packet format Link connections 3

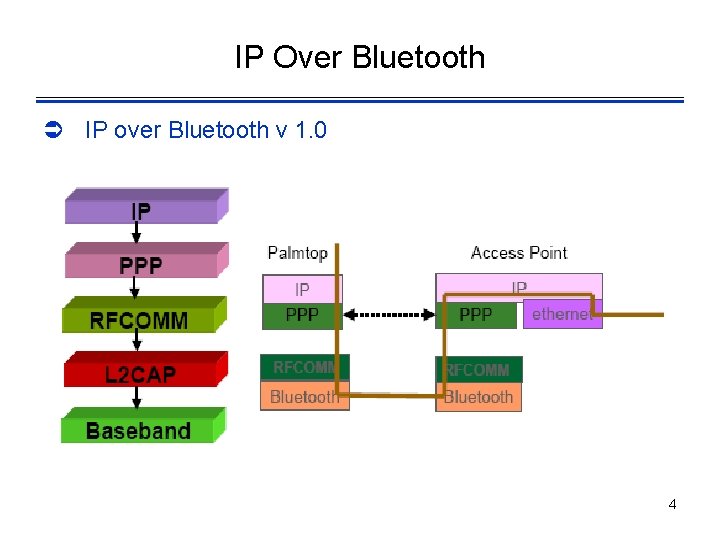
IP Over Bluetooth Ü IP over Bluetooth v 1. 0 4

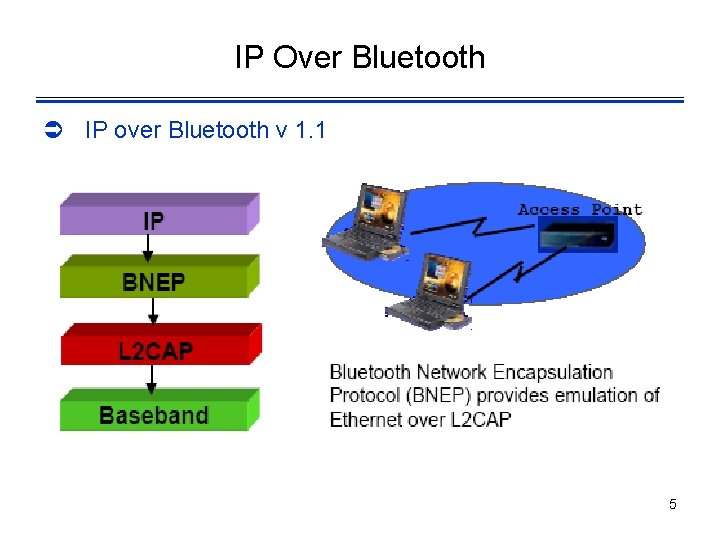
IP Over Bluetooth Ü IP over Bluetooth v 1. 1 5

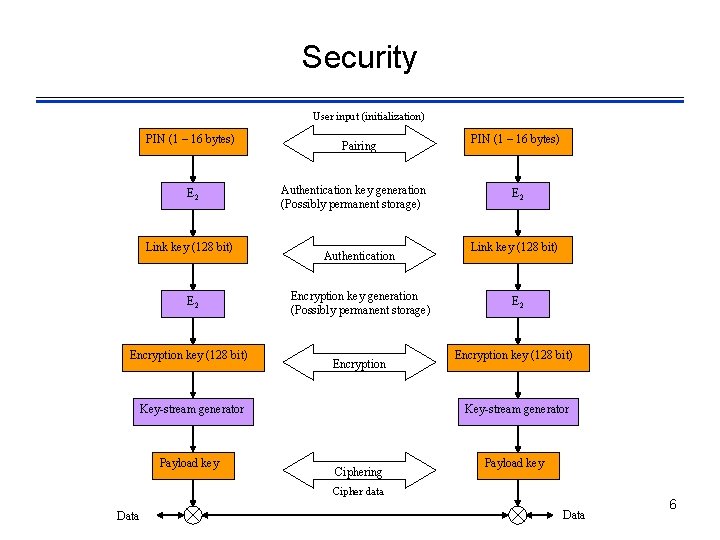
Security User input (initialization) PIN (1 – 16 bytes) E 2 Link key (128 bit) E 2 Encryption key (128 bit) Pairing Authentication key generation (Possibly permanent storage) Authentication Encryption key generation (Possibly permanent storage) Encryption Key-stream generator Payload key PIN (1 – 16 bytes) E 2 Link key (128 bit) E 2 Encryption key (128 bit) Key-stream generator Ciphering Payload key Cipher data Data 6

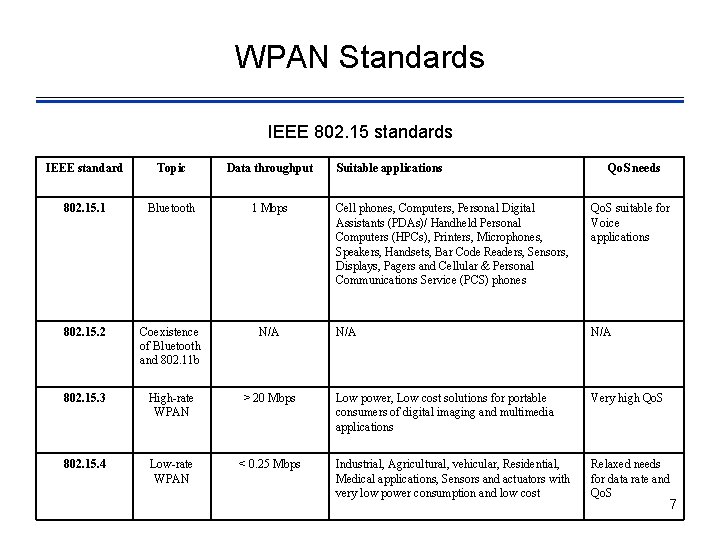
WPAN Standards IEEE 802. 15 standards IEEE standard Topic Data throughput 802. 15. 1 Bluetooth 1 Mbps 802. 15. 2 Coexistence of Bluetooth and 802. 11 b N/A 802. 15. 3 High-rate WPAN > 20 Mbps 802. 15. 4 Low-rate WPAN < 0. 25 Mbps Suitable applications Qo. S needs Cell phones, Computers, Personal Digital Assistants (PDAs)/ Handheld Personal Computers (HPCs), Printers, Microphones, Speakers, Handsets, Bar Code Readers, Sensors, Displays, Pagers and Cellular & Personal Communications Service (PCS) phones Qo. S suitable for Voice applications N/A Low power, Low cost solutions for portable consumers of digital imaging and multimedia applications Very high Qo. S Industrial, Agricultural, vehicular, Residential, Medical applications, Sensors and actuators with very low power consumption and low cost Relaxed needs for data rate and Qo. S 7

IEEE 802. 15. 3 - Overview Ü High data rate WPAN Ü Potential future standard Ü Motivation: Data, High quality TV, Home cinema Ü Dynamic topology ► Mobile devices often join and leave the piconet ► Short connection times Ü Multiple Power Management modes Ü Secure Network 8

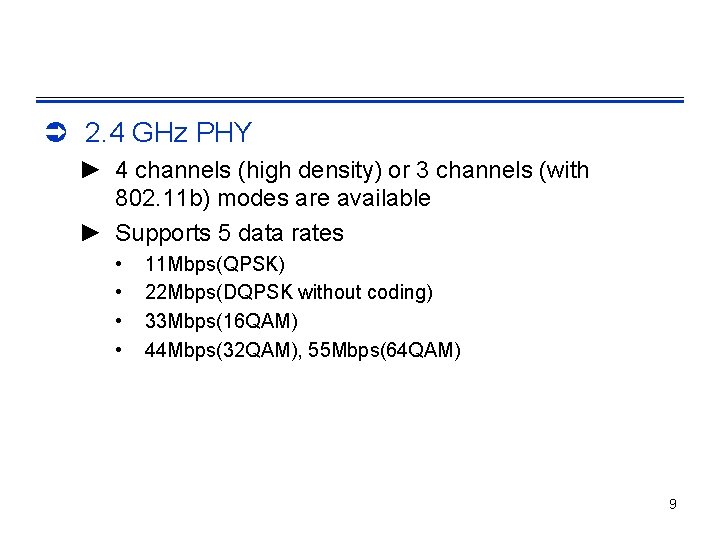
Ü 2. 4 GHz PHY ► 4 channels (high density) or 3 channels (with 802. 11 b) modes are available ► Supports 5 data rates • • 11 Mbps(QPSK) 22 Mbps(DQPSK without coding) 33 Mbps(16 QAM) 44 Mbps(32 QAM), 55 Mbps(64 QAM) 9

IEEE 802. 15. 3 - Overview Ü Based on piconets in a person space analogous to LAN in larger area Ü Data Devices (DEV) establish peer-to-peer communication Ü Includes also a Piconet Coordinator (PNC) ► PNC manages the quality of service (Qo. S) requirements, power save modes and access control to the piconet. Ü A new piconet created with same channel as of the existing PNC is called child/neighbor piconet ► If channel access is also controlled by the parent PNC then it is called dependent piconet 10

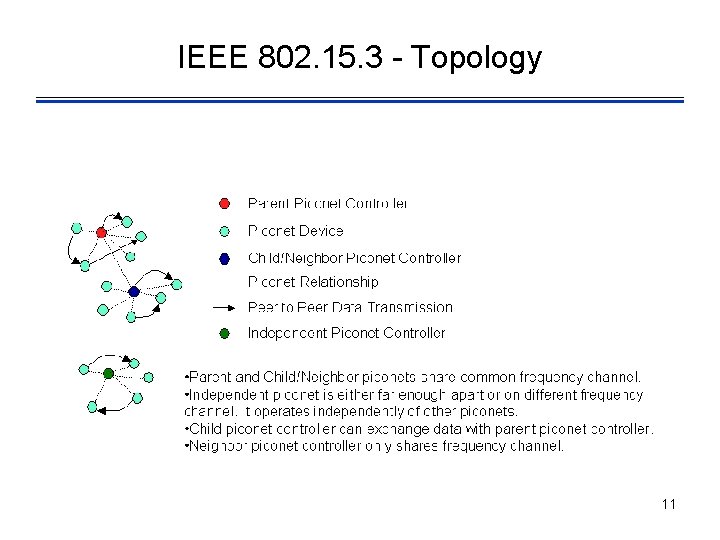
IEEE 802. 15. 3 - Topology 11

802. 15. 3 Ü IEEE 803. 15. 3 MAC is designed to support the following goals: ► ► ► Fast connection time Ad hoc networks Data transport with quality of service (Qo. S) Security Dynamic membership Efficient data transfer 12

Coordination in IEEE 802. 15. 3 Ü Starting a piconet ► DEV scans for the best channel and sends out beacons -> the DEV becomes PNC ► If no channels available: Establishes a child or neighbor piconet instead ► While the process of starting a piconet does not ensure that the “most capable” PNC is initially selected Ü Handing over control of the piconet ► When a DEV associates, PNC checks the capabilities of the new DEV to see if it is more capable to be the PNC of the piconet ► In handover process, it maintains all existing time allocations so that there is no interruption in the delivery 13

Ü Creating a child piconet ► A child piconet is one that is formed under an established piconet. The established piconet then becomes the parent piconet. ► The child piconet functionality is useful for either extending the area of coverage of the piconet or shifting some computational or memory requirements to another PNC capable DEV. ► The child piconet uses a distinct piconet ID (PNID) and acts as an autonomous piconet except that it is dependent on a private CTA from the parent piconet. 14

Ü Ending a piconet ► If the PNC is going to stop operation and there are no other PNC capable DEVs in the piconet, the PNC places the PNC Shutdown information element (IE) into the beacon to notify the members of the piconet. ► In the case that the PNC abruptly leaves the piconet without handing over control to another PNC capable DEV in the piconet, the piconet stops operation. ► After the association timeout period (ATP) expires, a PNC capable DEV from the old piconet will be able to start a new piconet using the normal process, ► In the case of dependent piconets, the parent PNC is able to end the dependent piconet via the Disassociation Request command, 15

Ü Association and disassociation ► Associating with the piconet provides the DEV with a unique identifier, the DEVID, for that piconet ► The DEVID, one octet in length, is used instead of the DEV’s address, 8 octets in length, to save overhead in the system. ► The association process optionally provides information about the services available in the piconet as well as the services provided or PNC capabilities ► PNC broadcasts the information about all of the DEVs in the piconet, and places information in the beacon about the new DEV. ► When a DEV wants to leave the piconet or if the PNC wants to remove a DEV from the piconet, the disassociation process is used. ► The DEVID of the disassociated DEV is no longer valid, until reissued by the PNC. ► However, the PNC is not allowed to reissue the DEVID until a waiting period hasexpired 16

Security Ü Security for the piconet is one of two modes ► Mode 0 Open: • Security membership is not required and payload protection (either data integrity or data encryption) is not used by the MAC. The PNC is allowed to use a list of DEV addresses to admit or deny entry to the piconet. ► Mode 1—Secure membership and payload protection: 17

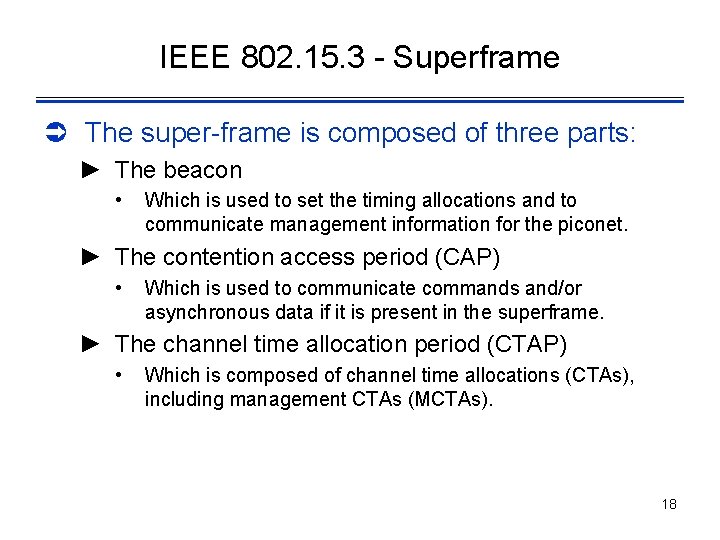
IEEE 802. 15. 3 - Superframe Ü The super-frame is composed of three parts: ► The beacon • Which is used to set the timing allocations and to communicate management information for the piconet. ► The contention access period (CAP) • Which is used to communicate commands and/or asynchronous data if it is present in the superframe. ► The channel time allocation period (CTAP) • Which is composed of channel time allocations (CTAs), including management CTAs (MCTAs). 18

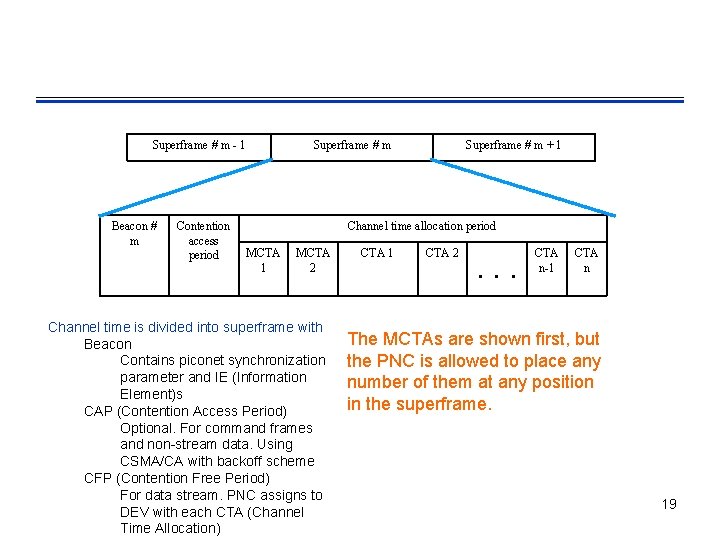
Superframe # m - 1 Beacon # m Contention access period Superframe # m + 1 Channel time allocation period MCTA 1 MCTA 2 Channel time is divided into superframe with Beacon Contains piconet synchronization parameter and IE (Information Element)s CAP (Contention Access Period) Optional. For command frames and non-stream data. Using CSMA/CA with backoff scheme CFP (Contention Free Period) For data stream. PNC assigns to DEV with each CTA (Channel Time Allocation) CTA 1 CTA 2 . . . CTA n-1 CTA n The MCTAs are shown first, but the PNC is allowed to place any number of them at any position in the superframe. 19

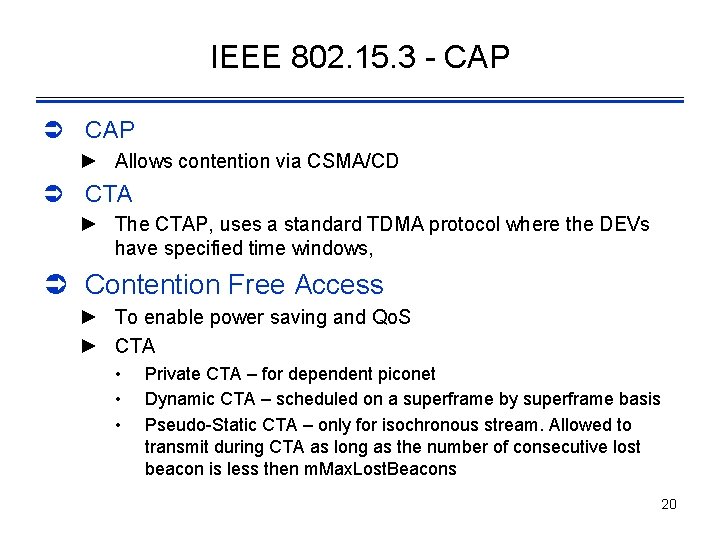
IEEE 802. 15. 3 - CAP Ü CAP ► Allows contention via CSMA/CD Ü CTA ► The CTAP, uses a standard TDMA protocol where the DEVs have specified time windows, Ü Contention Free Access ► To enable power saving and Qo. S ► CTA • • • Private CTA – for dependent piconet Dynamic CTA – scheduled on a superframe by superframe basis Pseudo-Static CTA – only for isochronous stream. Allowed to transmit during CTA as long as the number of consecutive lost beacon is less then m. Max. Lost. Beacons 20

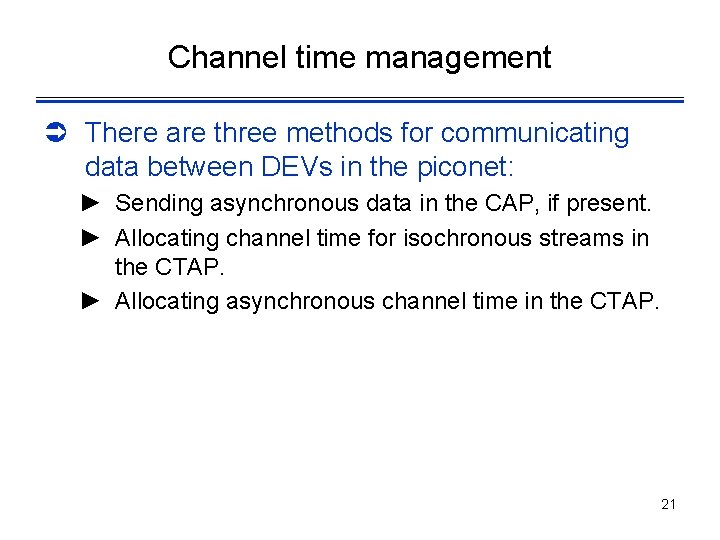
Channel time management Ü There are three methods for communicating data between DEVs in the piconet: ► Sending asynchronous data in the CAP, if present. ► Allocating channel time for isochronous streams in the CTAP. ► Allocating asynchronous channel time in the CTAP. 21

Ü Dynamic channel selection ► Due to ISM bands, piconet is subject to interference from unlicensed users or other 802. 15. 3 piconets ► PNC has the capability to dynamically change the channel that the piconet is using without requiring either user intervention or the disruption of services in the piconet. ► To evaluate the status of the current channel as well as other channels, the PNC is able to use many methods including: • • • Gathering information about the current channel from other DEVs in the piconet using the Channel Status Request command. Performing a passive scan of the channels. Requesting other DEVs to perform a channel scan using the Remote Scan Request command, 22

Power Management Ü standard provides three techniques to enable DEVs to turn off for one or more superframes: ► device synchronized power save (DSPS) mode ► piconet-synchronized power save (PSPS) mode ► asynchronous power save (APS) mode. Ü PSPS ► PSPS mode allows DEVs to sleep at intervals defined by the PNC. ► The DEV sends a request to the PNC when it wants to enter the PSPS mode. 23

Ü DSPS ► Besides allowing the DEVs to wake up and exchange traffic at the same time, the use of DSPS sets makes it easy for other DEVs in the piconet to determine exactly when a DSPS DEV will be available to receive traffic. Ü APS ► The only responsibility of a DEV in APS mode is to communicate with the PNC before the end of its ATP in order to preserve its membership in the piconet. 24

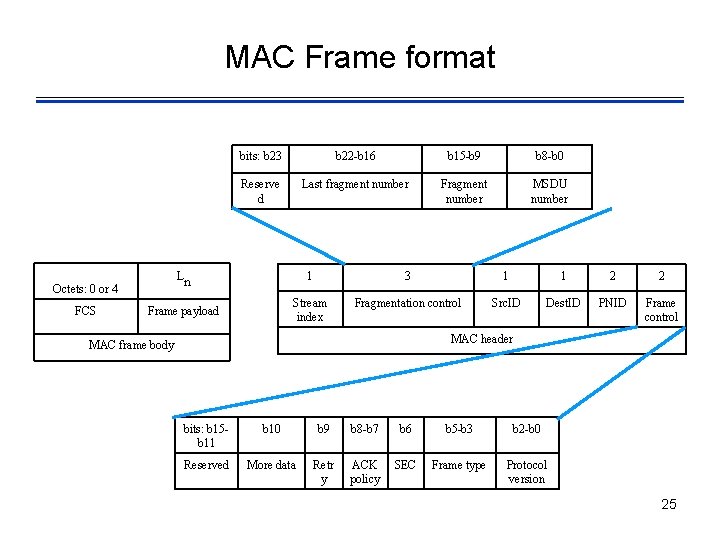
MAC Frame format b 22 -b 16 b 15 -b 9 b 8 -b 0 Reserve d Last fragment number Fragment number MSDU number Ln 1 3 1 1 2 2 Frame payload Stream index Fragmentation control Src. ID Dest. ID PNID Frame control Octets: 0 or 4 FCS bits: b 23 MAC header MAC frame body bits: b 15 b 11 b 10 b 9 b 8 -b 7 b 6 b 5 -b 3 b 2 -b 0 Reserved More data Retr y ACK policy SEC Frame type Protocol version 25

ACK Policy Ü If the source DEV wishes to verify the delivery of a frame, then one of the acknowledgement (ACK) policies ► NO ACK • The no-ACK policy, is appropriate for frames that do not require guaranteed delivery, where the retransmitted frame would arrive too late or where an upper layer protocol is handling the ACK and retransmission protocol. ► The immediate-ACK (Imm-ACK) policy, • it provides an ACK process in which each frame is individually ACKed following the reception of the frame. ► The delayed-ACK (Dly-ACK) policy, • • it lets the source send multiple frames without the intervening ACKs. Instead, the ACKs of the individual frames are grouped into a single response frame that is sent when requested by the source DEV. The Dly-ACK process decreases the overhead in the Imm-ACK process while allowing the source DEV to verify the delivery of frames to the destination. 26